Virtual genome-based cryptosystem (VGC)
A virtual gene and cryptographic system technology, applied in the field of information security, can solve problems such as fragile coding methods, transmission, and easy pollution of DNA operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
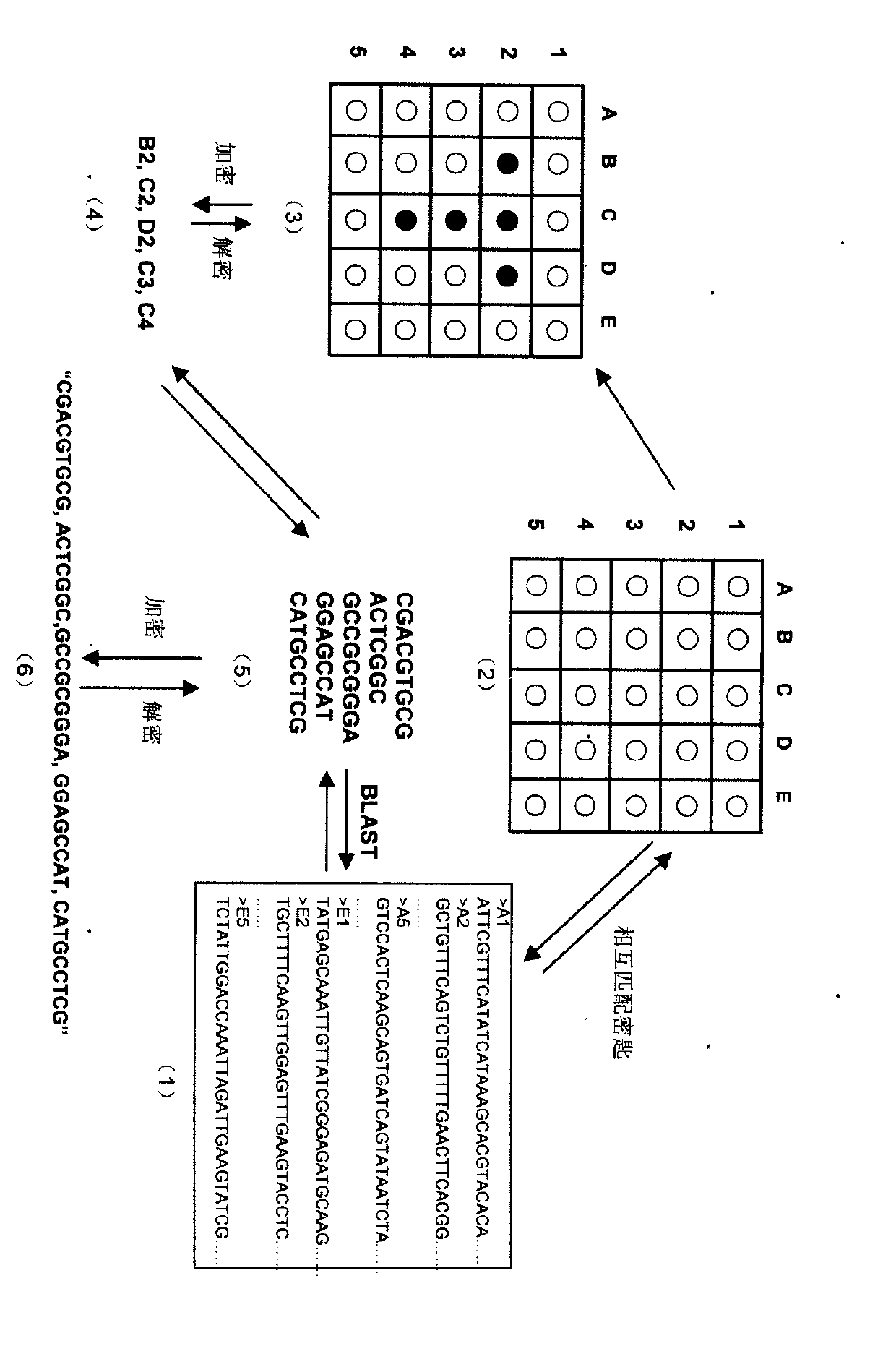
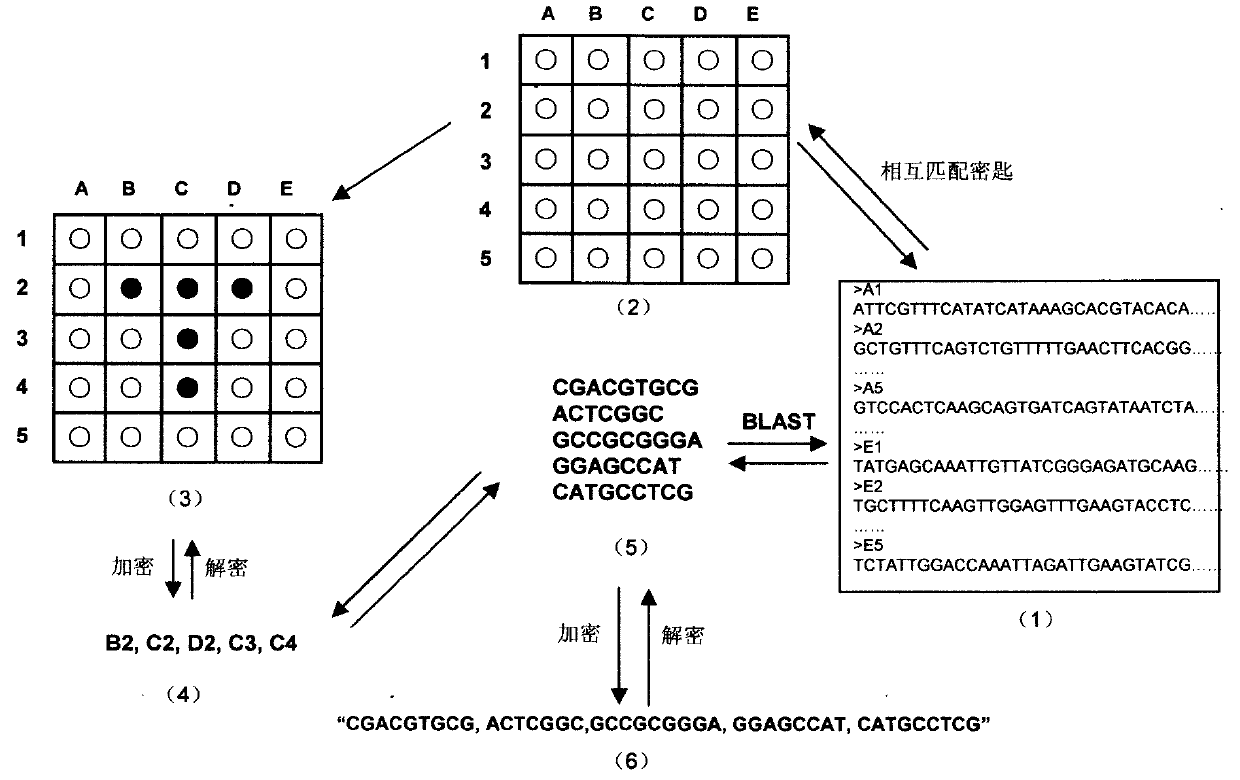
[0027] Embodiment 1 establishes the VGC cryptographic system, and sends and receives a letter " T " ( figure 1 )
[0028] (1) First, randomly generate a large number (tens of thousands, even millions of tens of millions) of several kb or even longer DNA sequences, and randomly number or name them (each random DNA sequence is numbered or named as a virtual gene) , each virtual gene adopts the FASTA format, and all these virtual genes form a "virtual genome" to generate a "virtual genome database" (Virtual Genome Database, VGDB).
[0029](2) Then, all the virtual genes in the "virtual genome database" are randomly assigned on a 2-dimensional array table to obtain a table of virtual gene distribution positions, which is the "virtual DNA Microarray Chip" (Virtual DNA Microarray Chip, VDMC ).
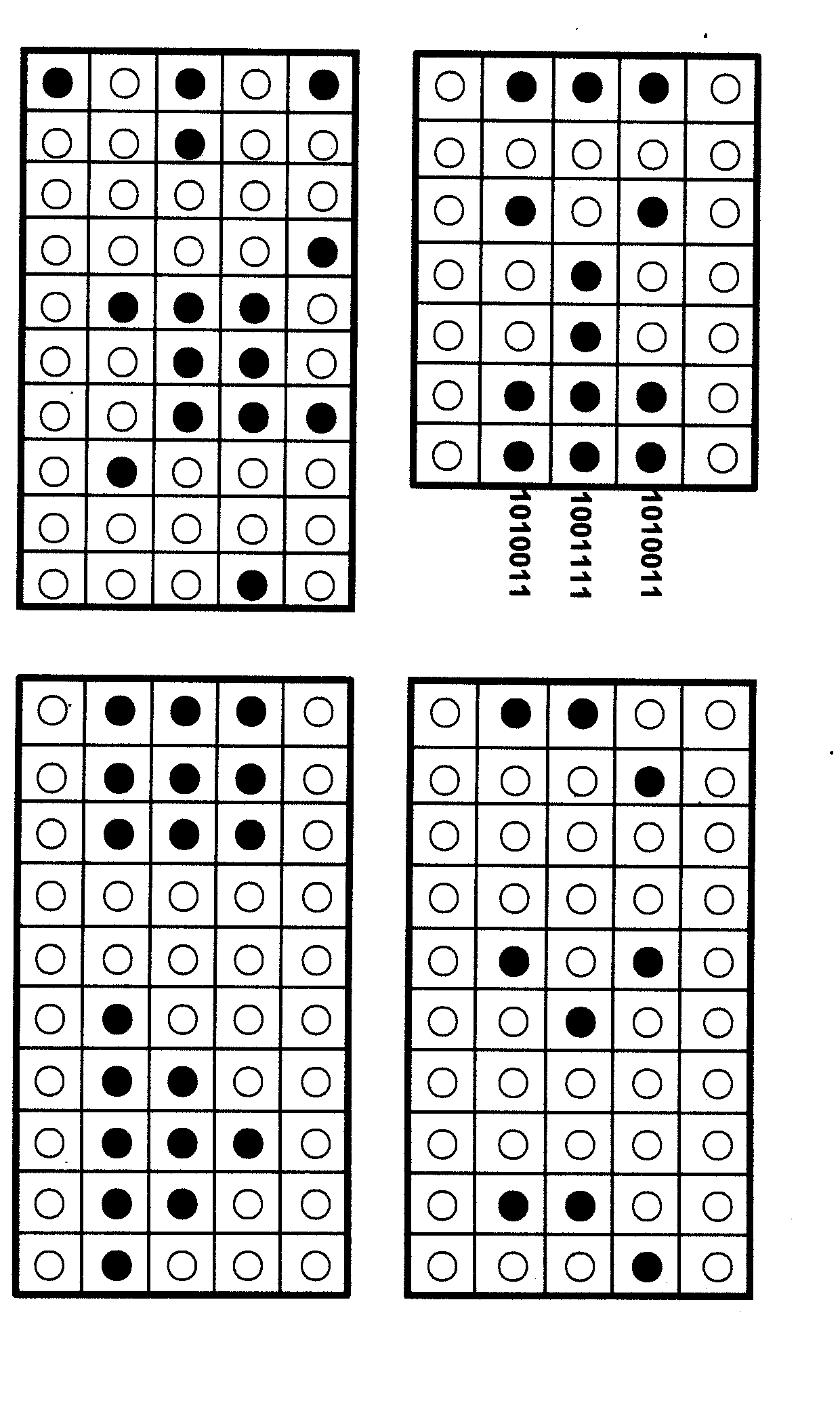
[0030] (3) Write the letter "T" on the "virtual gene chip" (VDMC), that is, select the "points" used to form the letter "T" on the VDMC.
[0031] (4) Find out that these points should cor...
Embodiment 2
[0035] Embodiment 2 digital signature
[0036] The VGC system has a special signature method for digital signatures. Since the VGC system uses image recognition information input and output, that is, "write" and restore information on the VDMC, the information transmitted by the VGC itself is very personalized. VGC digital signature can truly be a handwritten authentic signature. It is also possible to make some special marks on special positions of the VDMC, so that the ciphertext cannot be forged at all.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com