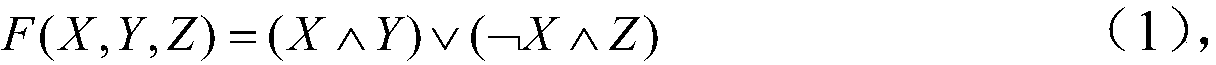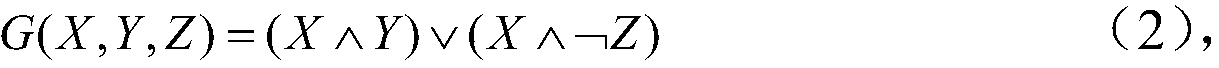A Secure Communication Protocol Based on Stream Cipher
A secure communication and stream cipher technology, applied in the fields of stream cipher, data verification, and finite field calculation, can solve the problems of high key operation cost, large packet length, and low encryption speed, and achieve large and fast key space. The effect of encryption and calculation is simple
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] Below in conjunction with specific embodiment, the present invention will be further described:
[0052] In the stream cipher system, there are two ways to generate keys: one is a true random number generator based on physical information, and the other is a pseudo-random number generator based on mathematical functions. The present invention uses a pseudo-random number generator to generate non-subjective keys. Depending on the nature of pseudo-random numbers, different seeds will generate different random sequences. Traditional cryptography changes the position by means of replacement, which cannot fundamentally solve the problem of data security. However, using GF(2 8 ) can provide a higher level of security guarantees. At the same time, in terms of data processing, MD5 is added, which doubles the data volume and has fault tolerance.
[0053] A secure communication protocol based on stream ciphers, characterized in that the communication is encrypted once, the key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com