Image Encryption Method Based on Hybrid Equilibrium Second-Order Reversible Two-dimensional Cellular Automata
An encryption method and hybrid technology, applied in the field of information security, can solve problems such as high redundancy, encryption efficiency and performance can not achieve the desired effect, large data volume, etc., to achieve a huge key space, increase diffusion and confusion Sexuality, the effect of increasing confusion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
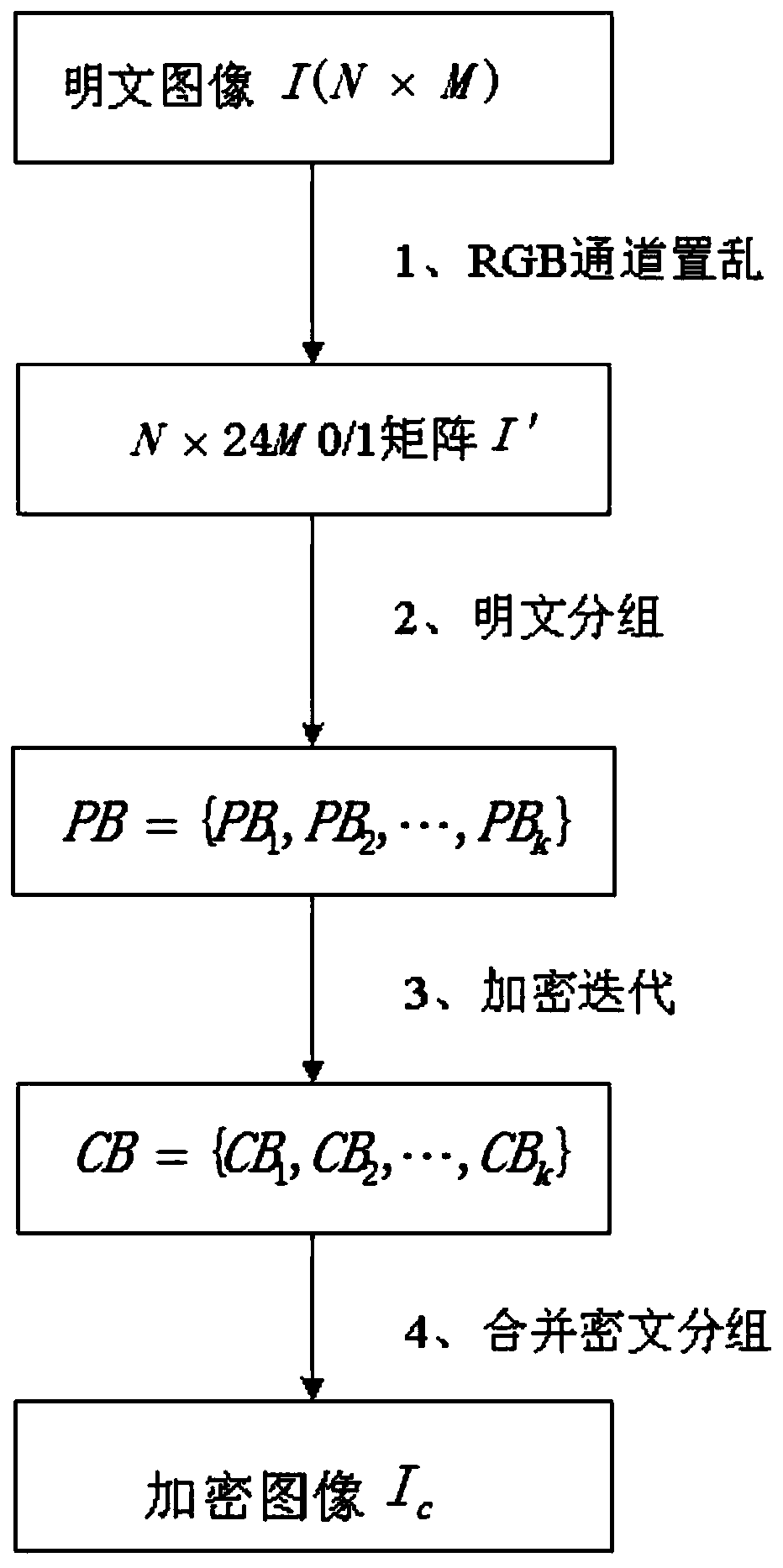
[0037] Such as figure 1 As shown, an image encryption method based on a hybrid equilibrium second-order reversible two-dimensional cellular automata includes the following steps:
[0038] S1: Perform pixel scrambling on the three RGB channels of the image I to be encrypted to obtain a 0-1 matrix I' of N×24M;
[0039] S2: divide the 0-1 matrix I' matrix of N * 24M into several 0-1 matrix groups of 8 * 16;
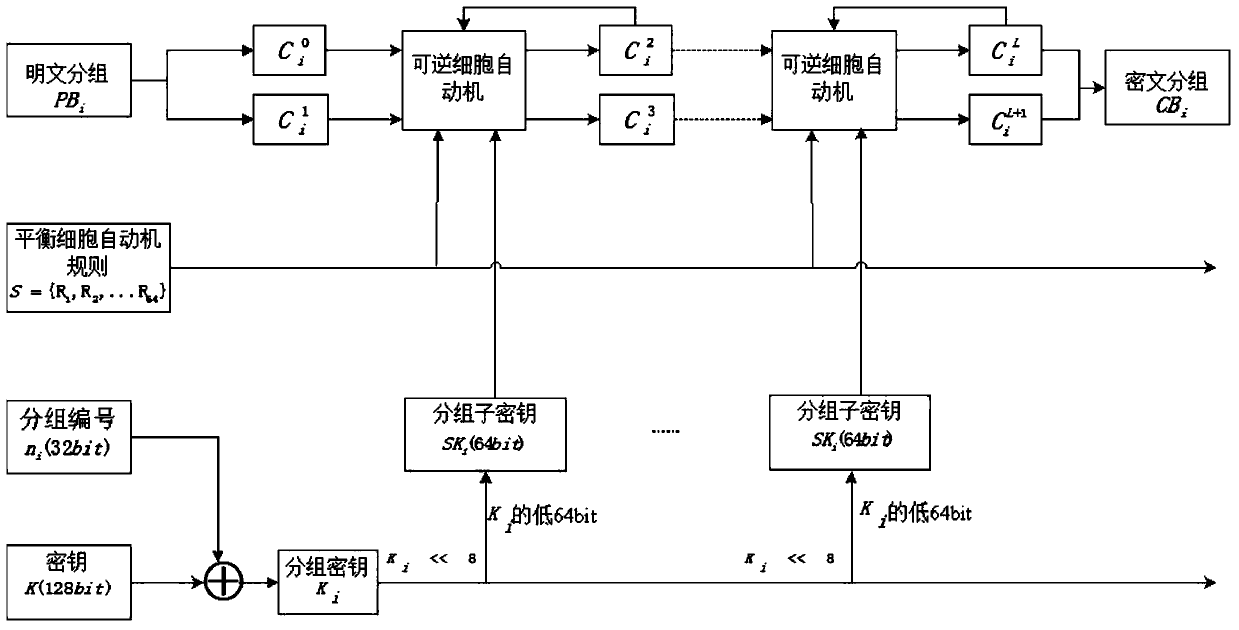
[0040] S3: Construct a hybrid balanced second-order reversible two-dimensional cellular automaton to perform encryption iterations on each matrix group;
[0041] S4: Combine the encrypted packets into an encrypted image.
[0042] The specific process of step S1 is as follows:
[0043] Use 8bit to represent a pixel value in a color channel, and arrange the pixel values in the image I with a size of N×M in the order of R channel-G channel-B channel until the end of the pixel byte sequence of image I to obtain a N×24M 0-1 matrix I'.
[0044] The specific process of step ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com