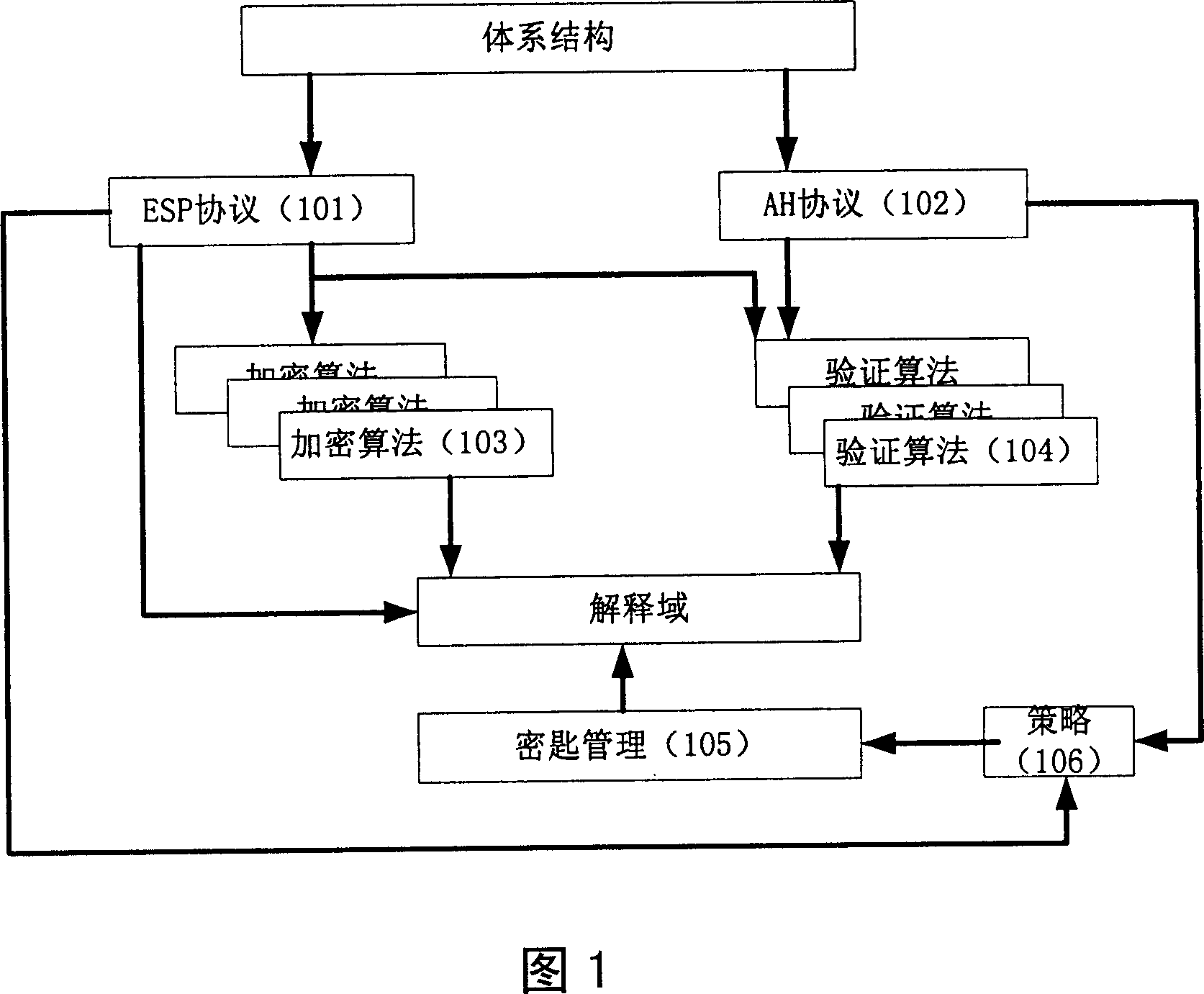
Patents
Literature
99 results about "Ipsec protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
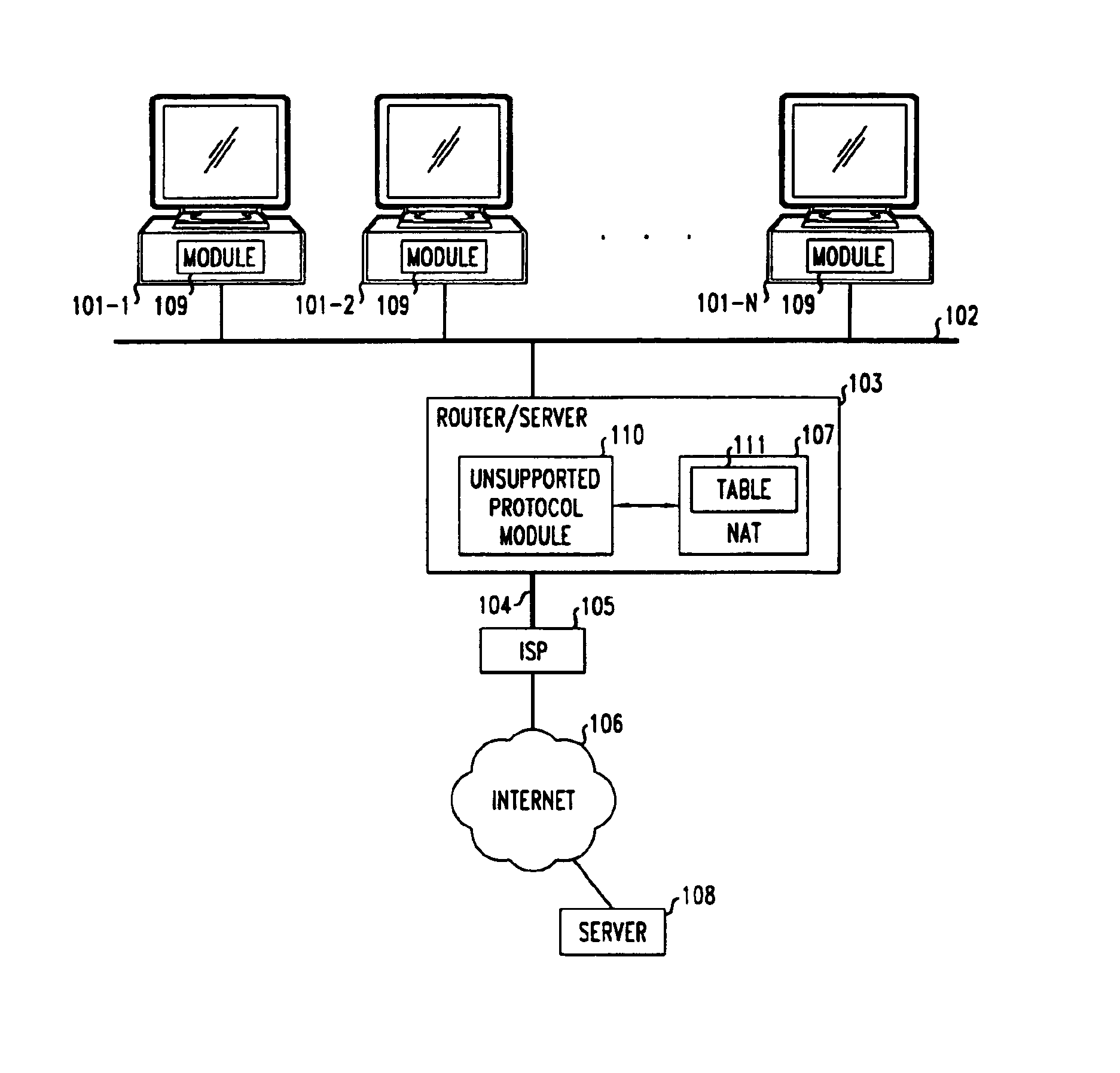
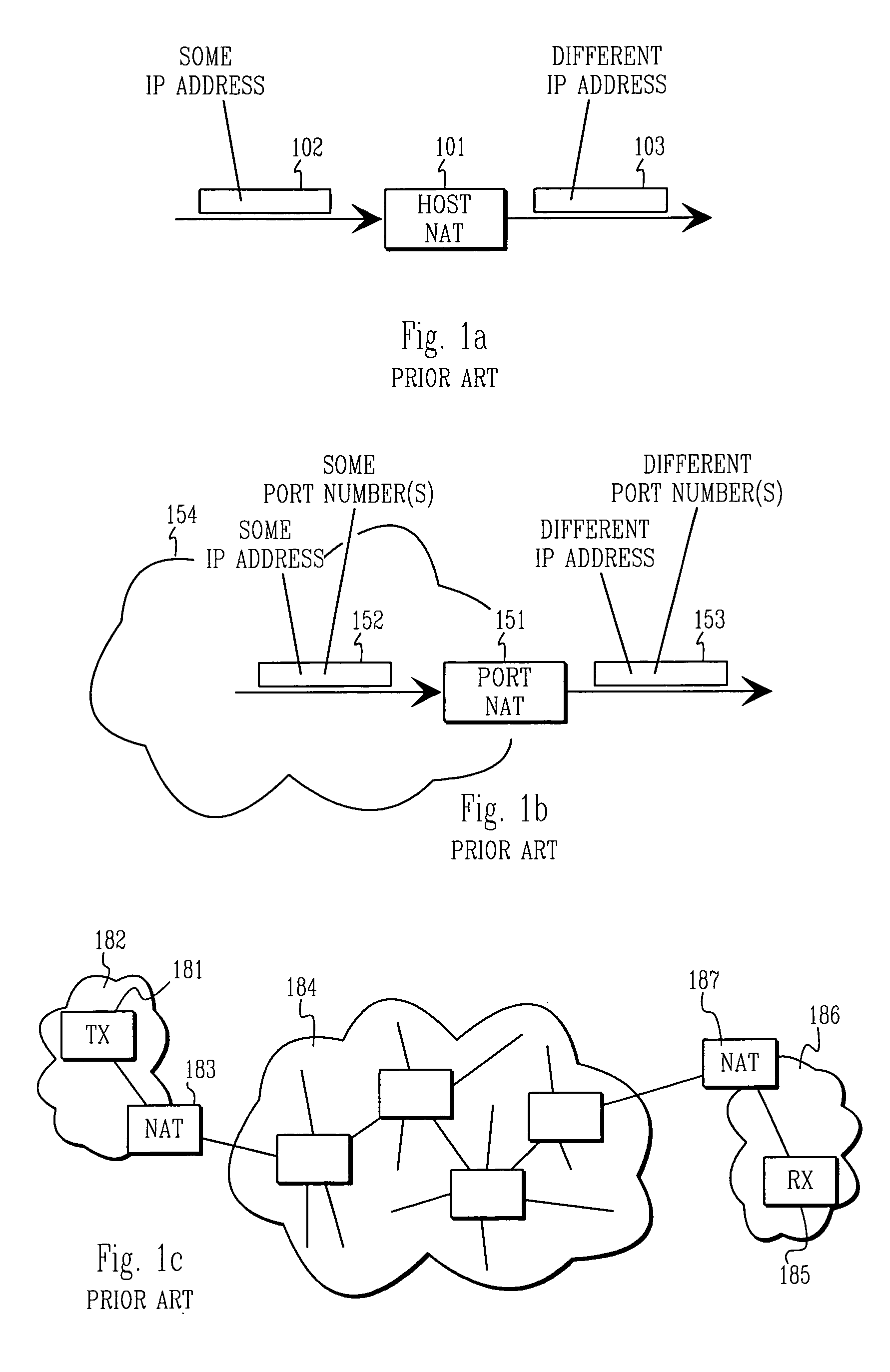
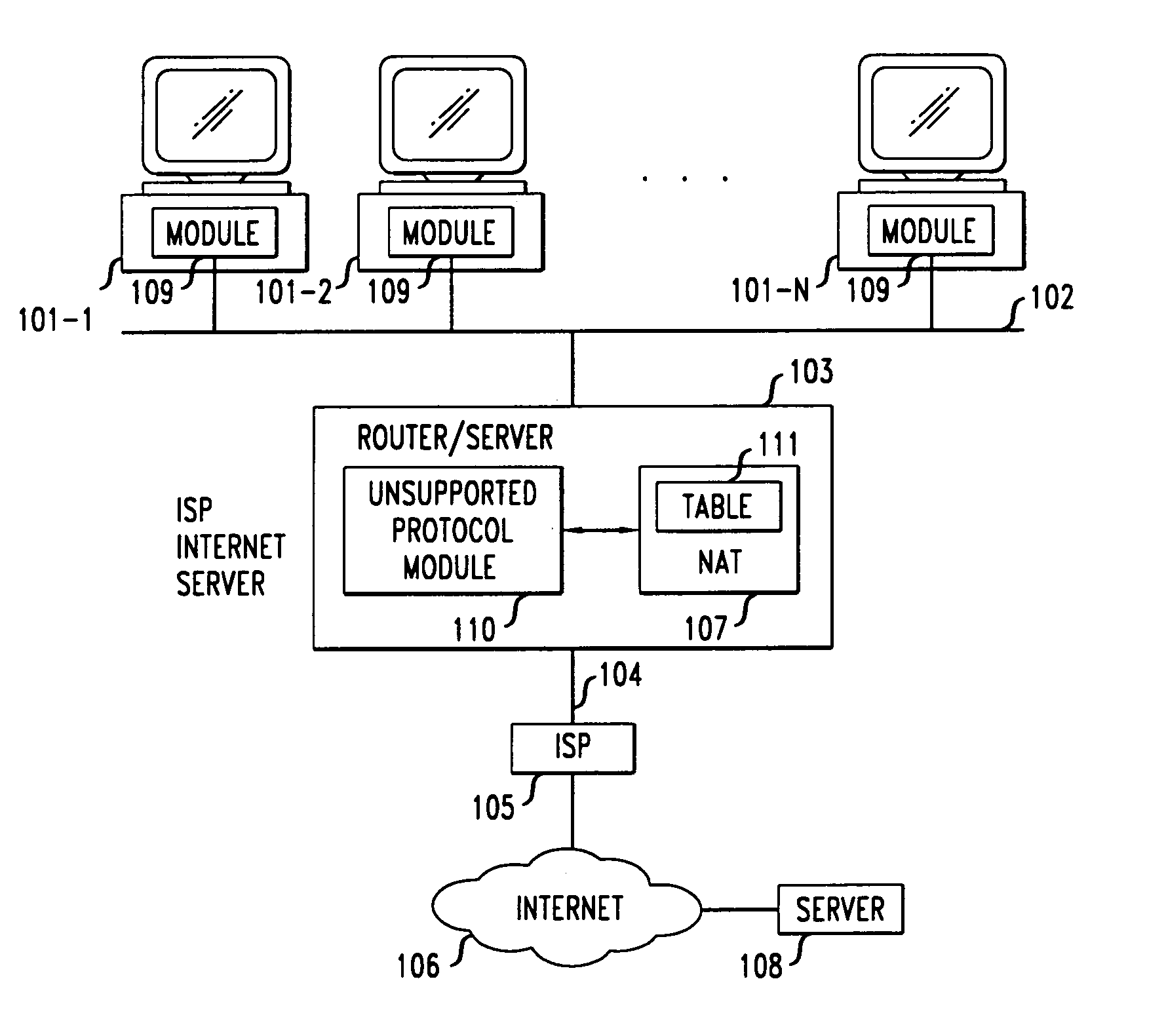
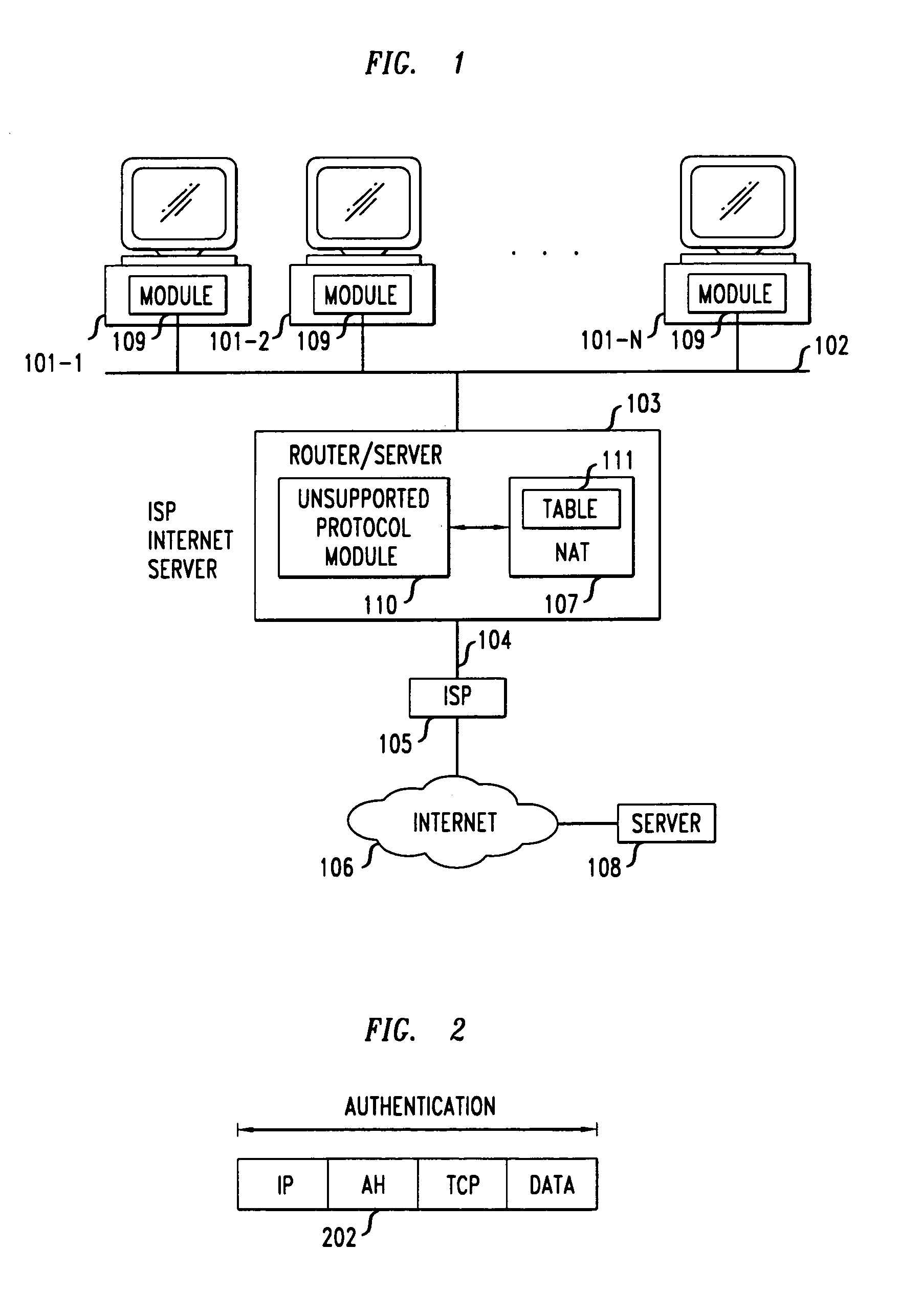
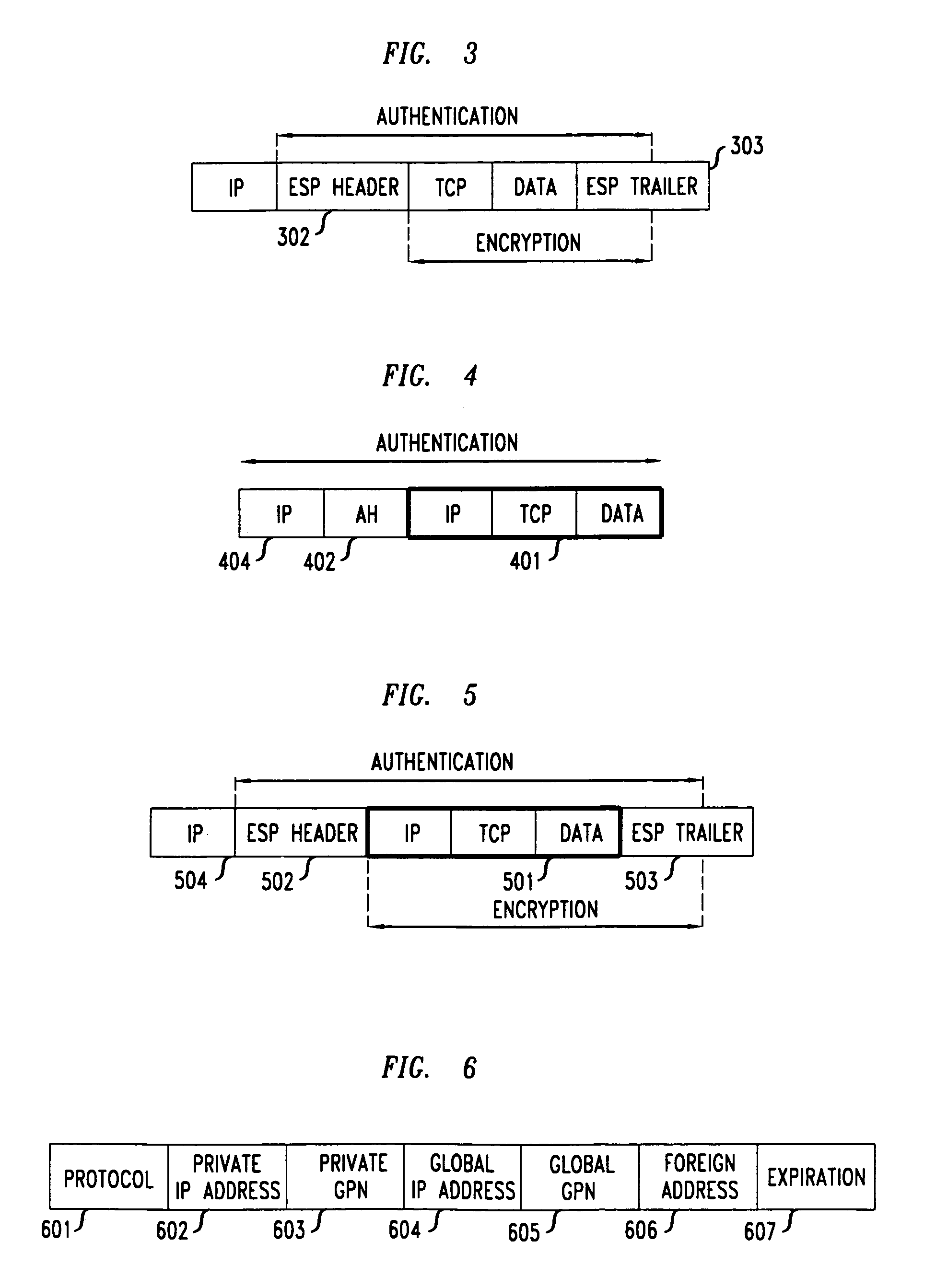
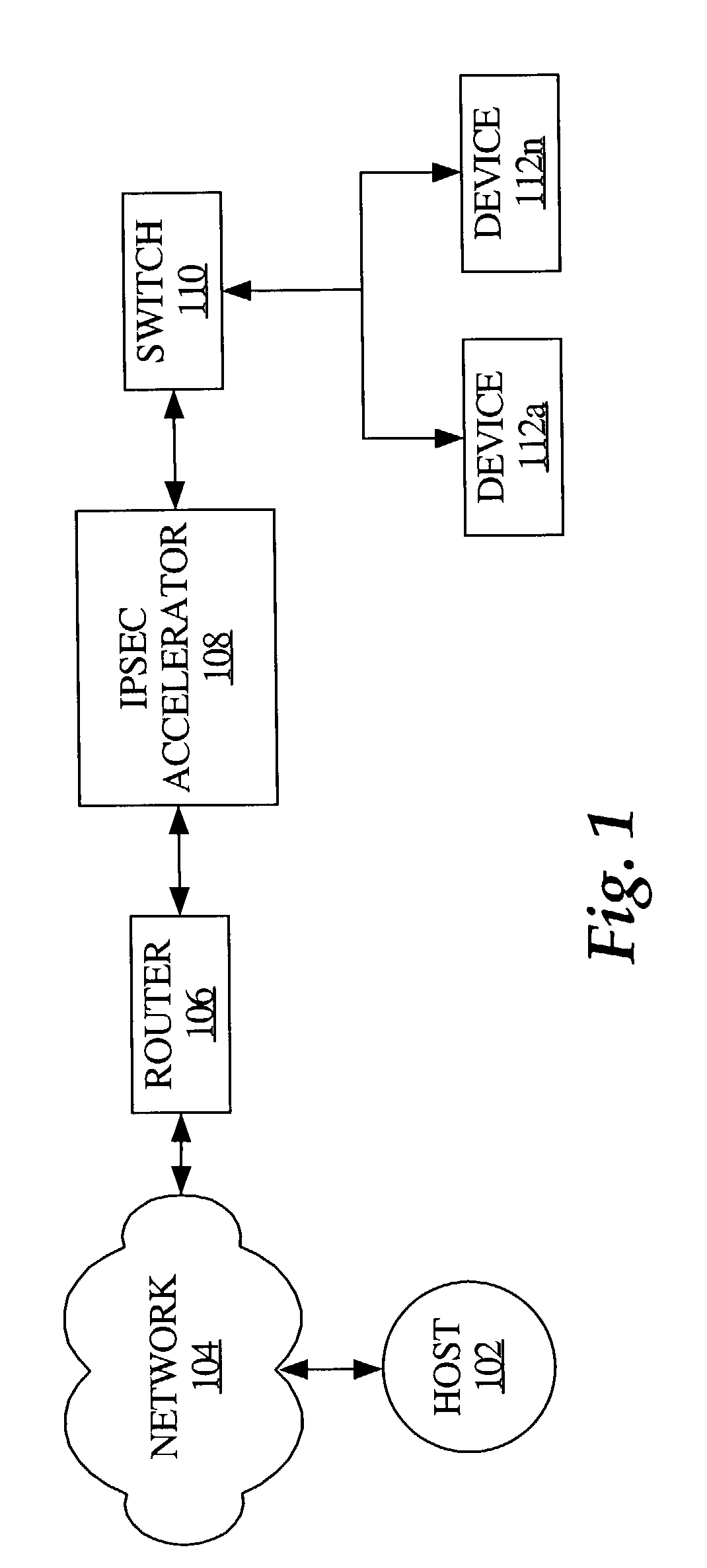
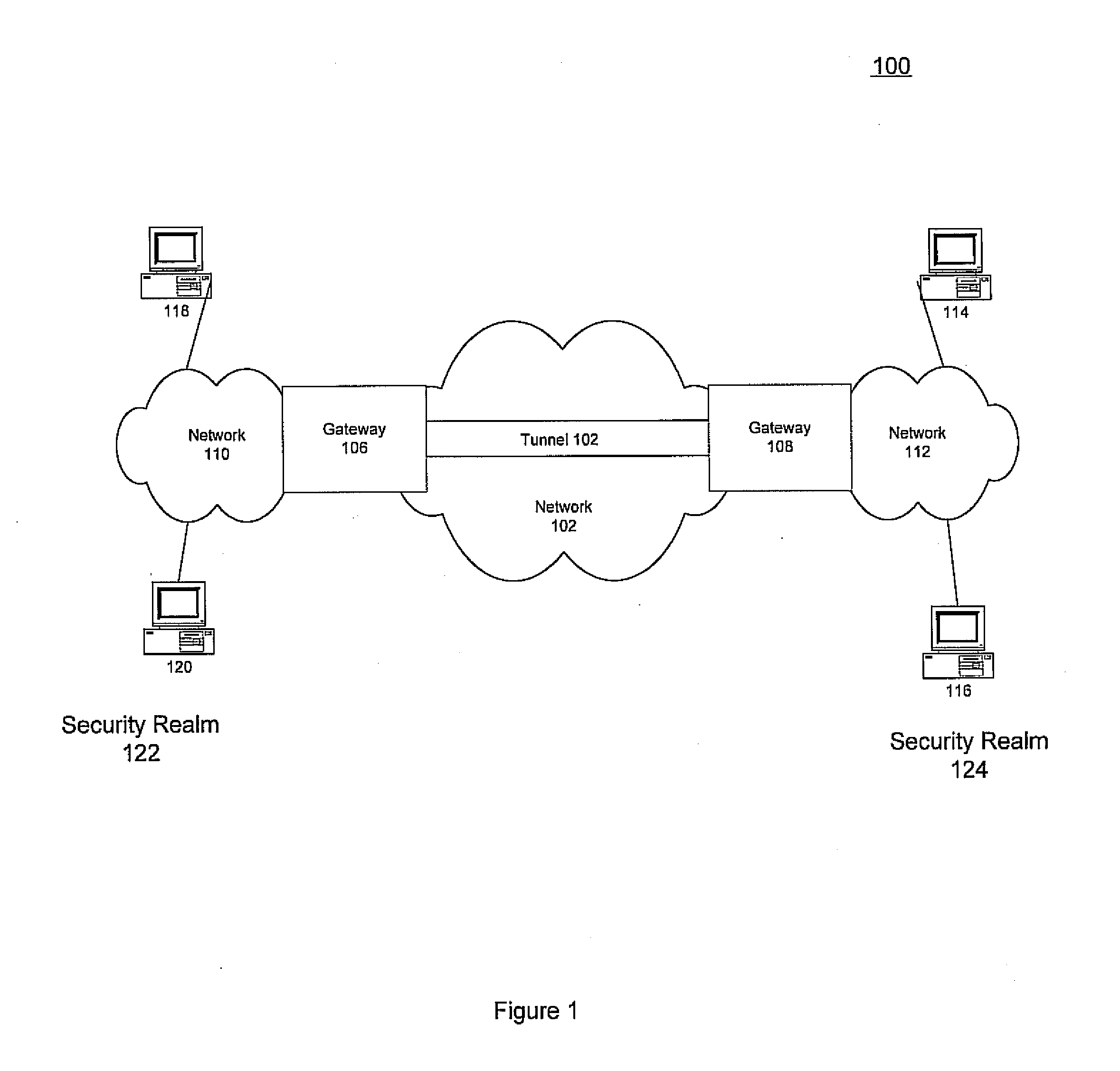
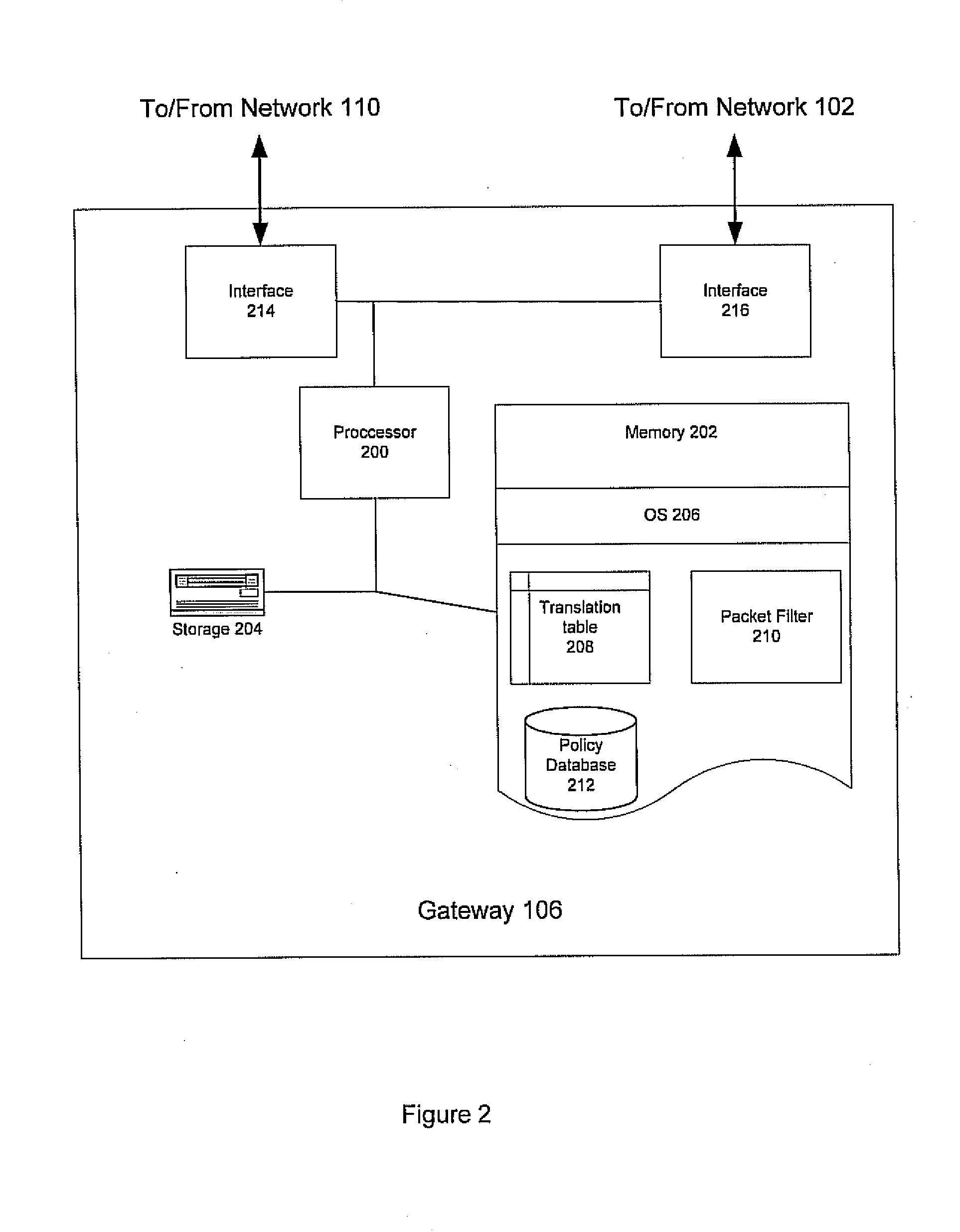
Method and apparatus for extending network address translation for unsupported protocols
InactiveUS6886103B1Ensure safetyMultiple digital computer combinationsProgram controlExpiration TimeIp address
Clients that are connected on a private network and which are assigned a private IP address that is not routable on the Internet can connect to the Internet through a router / server that includes a network address translator (NAT). For outgoing packets, the NAT translates the client's private source IP address and generalized port number (GPN) to the NAT's global IP address and GPN. For incoming packets sent to the NAT's global IP address and GPN, the NAT translates the global destination IP address and GPN to the client's private IP address and GPN. For protocols which cannot be directly supported by the NAT, such as those in the IPSec security protocol suite, the NAT is extended by creating in the NAT's translation table an entry that associates, for a specific unsupported protocol, a client's private IP address and GPN, the NAT's global IP address and GPN, and a foreign address on the Internet, that is valid until a specified or default expiration time. Outgoing packets from the client to that foreign address and incoming packets from that foreign address to the NAT's global IP address and GPN are translated according to the entry until the entry expires. In associations with these translations to outgoing and incoming packets, the client implements any Application Layer Gateway (ALG) that would otherwise be implemented at the NAT. Further, at the client, outgoing packets are modified before being transmitted so as to pre-compensate for the effects of the translations. Incoming packets at the client from the NAT are similarly modified so as to post-compensate for the effects of the translations. For the IPSec protocol, these modification include adjusting the checksum in the TCP or UDP header to account for IP address and TCP or UDP port number translations.
Owner:ALCATEL-LUCENT USA INC
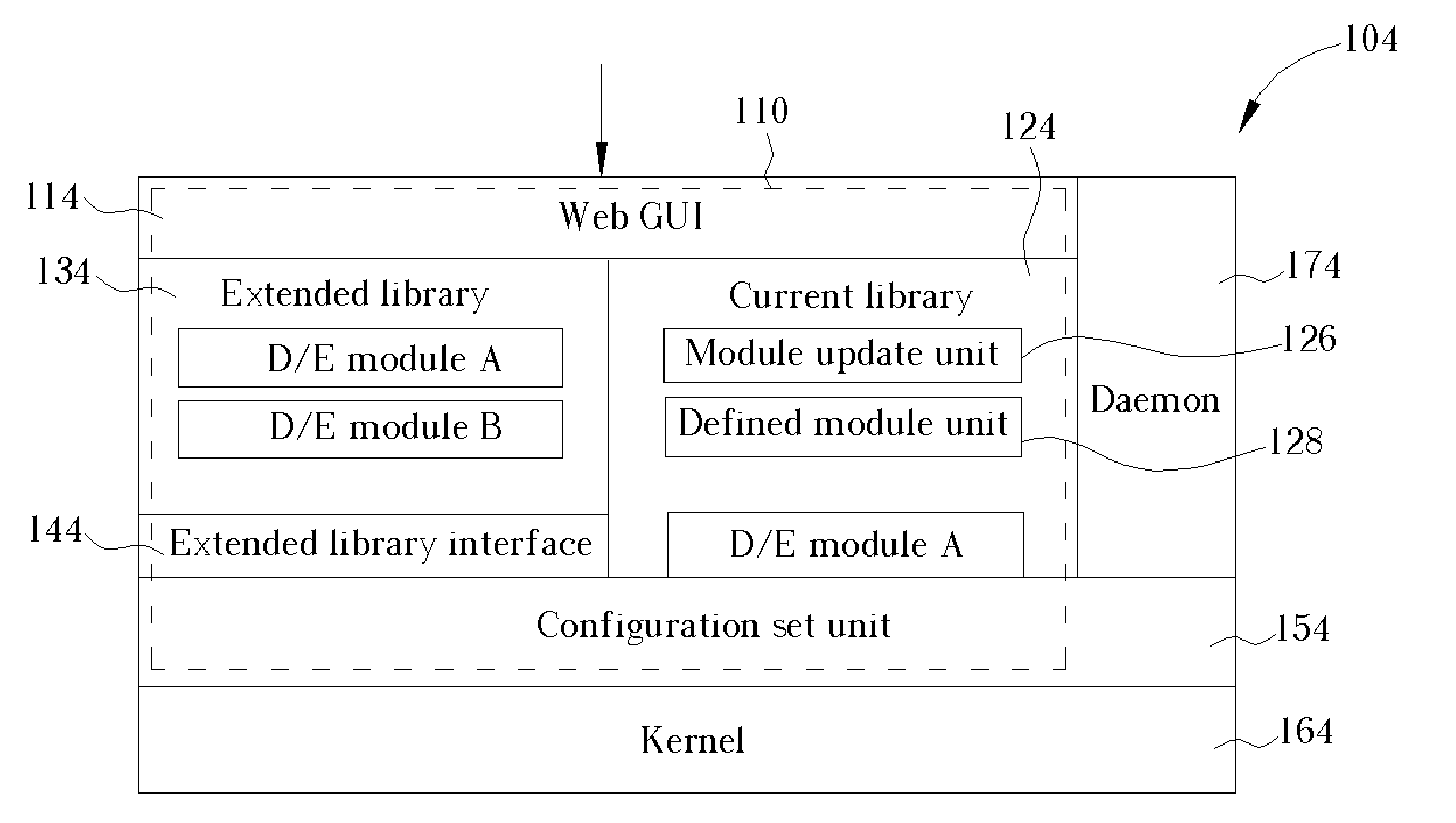
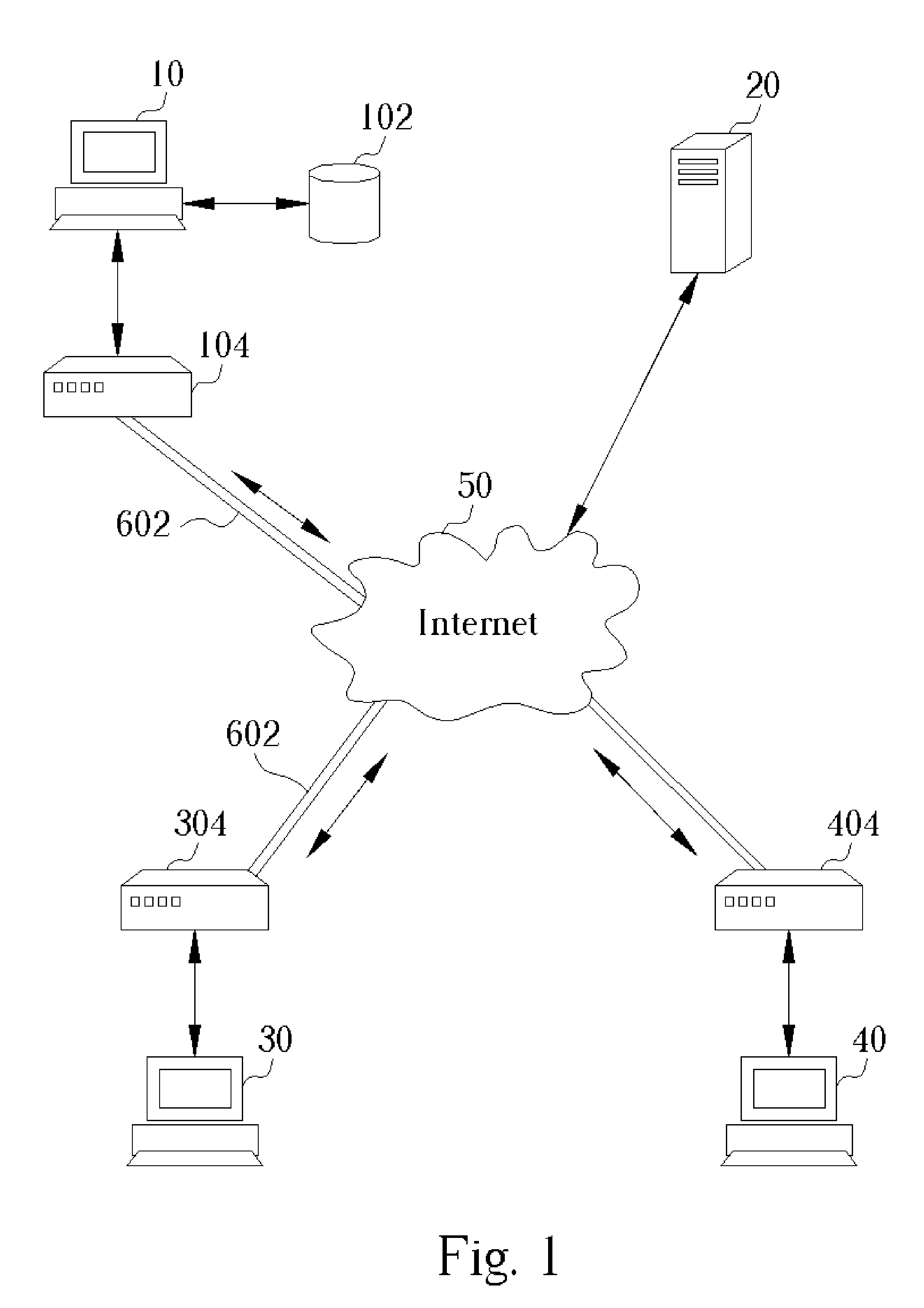
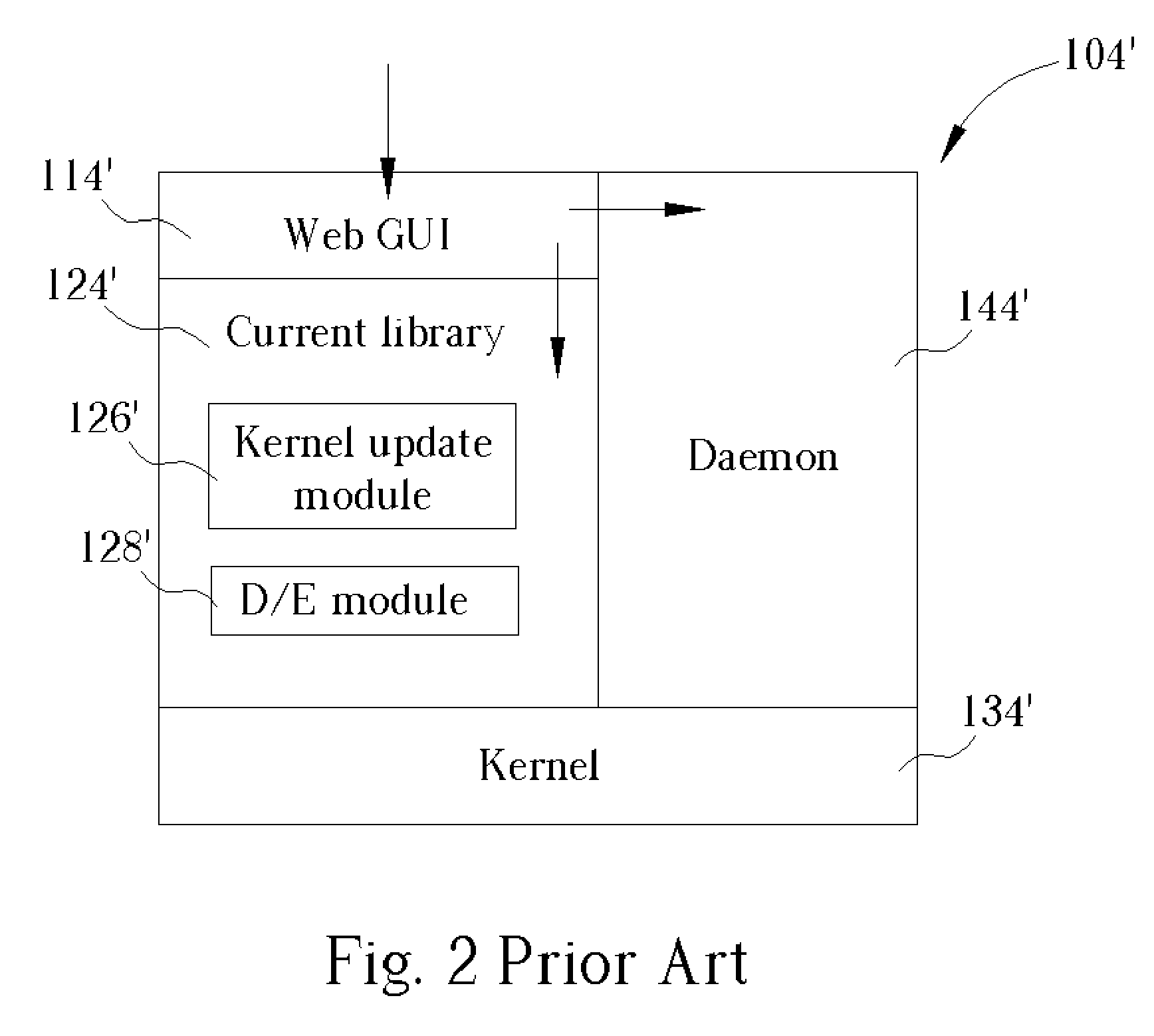
System for actively updating a cryptography module in a security gateway and related method
InactiveUS20050149746A1Time expendedImprove operational efficiencyDigital data processing detailsUser identity/authority verificationComputer scienceIpsec protocol
A system for actively updating a cryptography module in a security gateway and related method is used in a security gateway, such as a VPN gateway according to an IPSEC protocol, which is connected between at least one user computer system and a network system. The system includes a Web GUI, a module update unit, a defined module unit, and an extended library. A user can easily update or add decryption / encryption modules into the extended library of the gateway through the Web GUI and the module update unit instead of updating the decryption / encryption modules along with the entire kernel firmware. This can reduce the setting time, increase the efficiency of operation, reduce the maintenance cost, and promote the expansion of decryption / encryption modules of the gateway so that network transmission can become much safer.
Owner:ICP ELECTRONICS
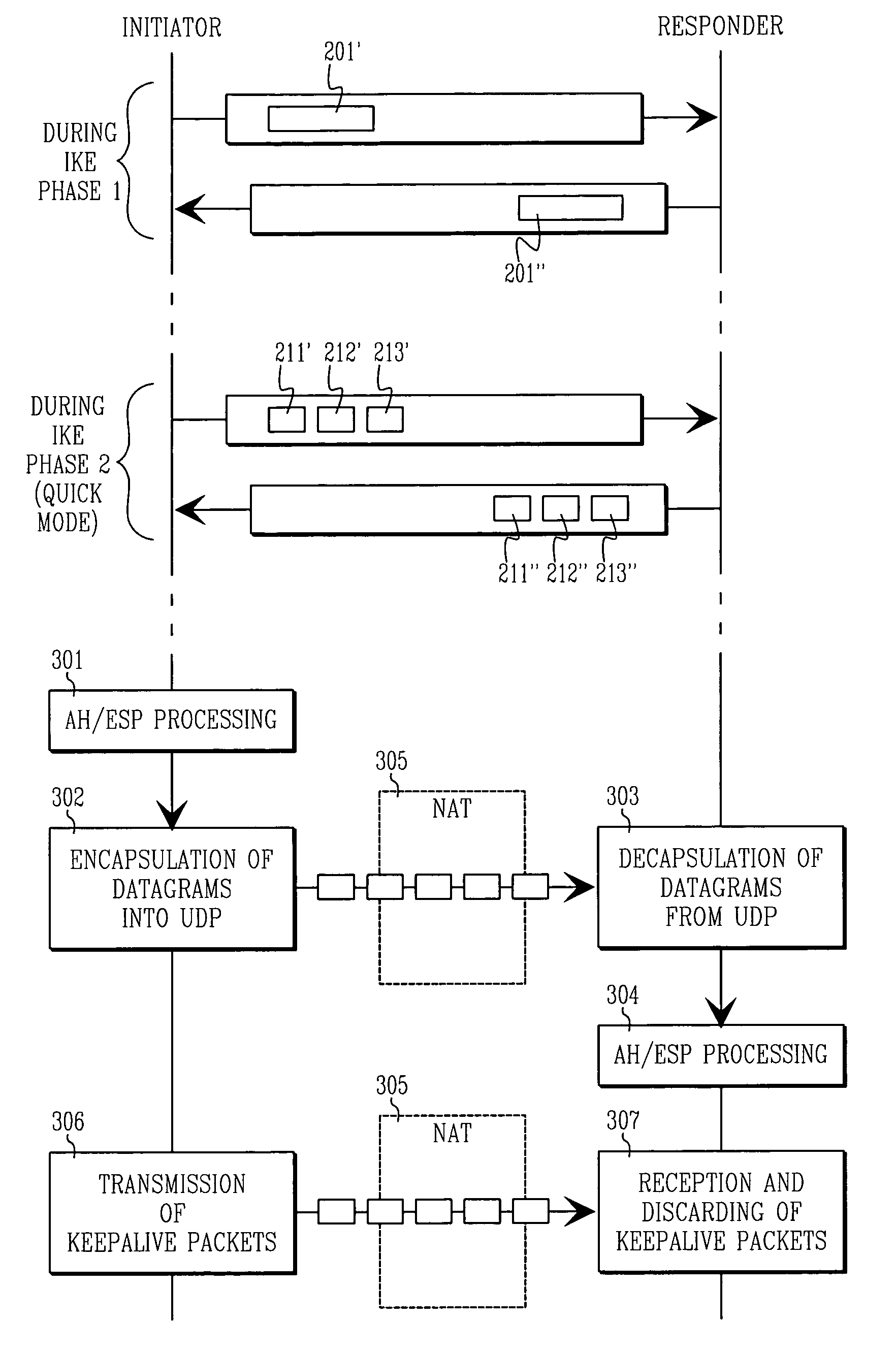
Method and arrangement for providing security through network address translations using tunneling and compensations
InactiveUS6957346B1Hardware monitoringNetworks interconnectionNetwork addressingNetwork address translation
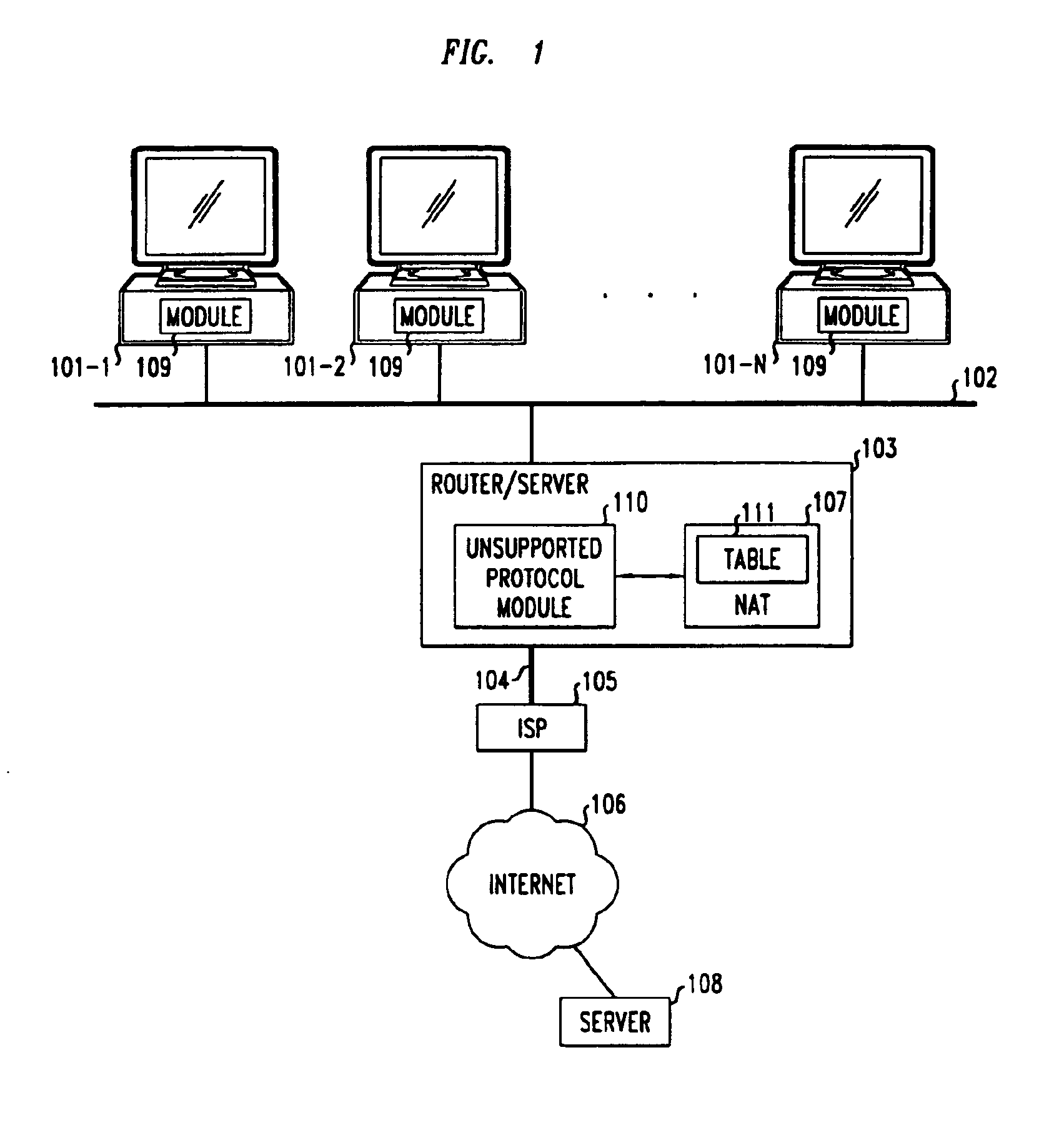
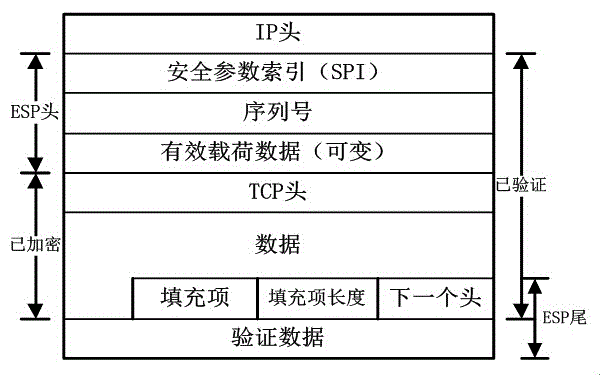
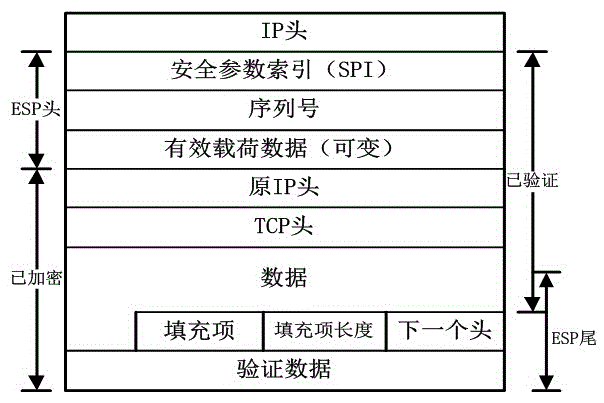
This invention provides a method for providing network security services, such as those provided by the IPSEC protocol, through network address translation (NAT). The method is based on determining the transformations that occur on a packet and compensating for the transformations. Because only TCP and UDP protocols work through NATs, the IPSEC AH / ESP packets are encapsulated into UDP packets for transport. Special operations are performed to allow reliable communications in such environments.
Owner:SSH COMMUNICATIONS SECURITY
Method and apparatus for preserving data in a system implementing Diffserv and IPsec protocol
InactiveUS7746781B1Reduce the possibilityTransmission systemsFrequency-division multiplex detailsTraffic capacityDifferentiated services
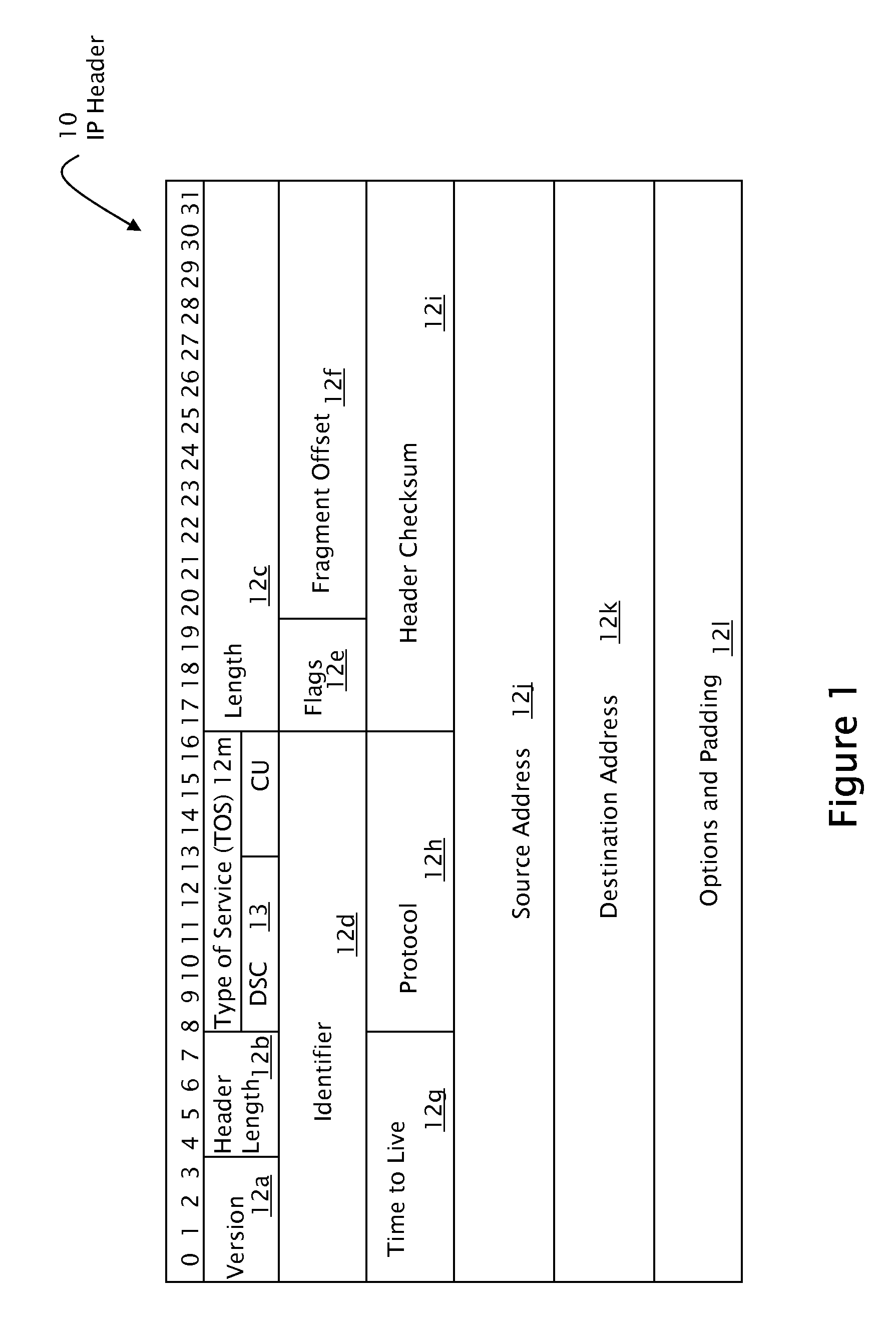
An improved method is described for providing Differentiated Services (Diffserv) traffic to a node in a network that implements a security method that discards duplicate packets received at the node. The method includes the step of identifying at least two service levels to be provided to received traffic and assigning separate sequential sequence numbers and different anti-replay bitmasks to each of the service levels. The anti-replay bitmask indicates the sequence numbers of packets that have been previously received at the node that should be compared against a received packet to determine whether a duplicate packet has been received. Such an arrangement reduces the possibility that traffic having lower priority is dropped as a security measure.
Owner:RPX CLEARINGHOUSE
Method and apparatus for establishing a dynamic multipoint encrypted virtual private network
ActiveUS7447901B1Multiple digital computer combinationsProgram controlTraffic capacityPrivate network
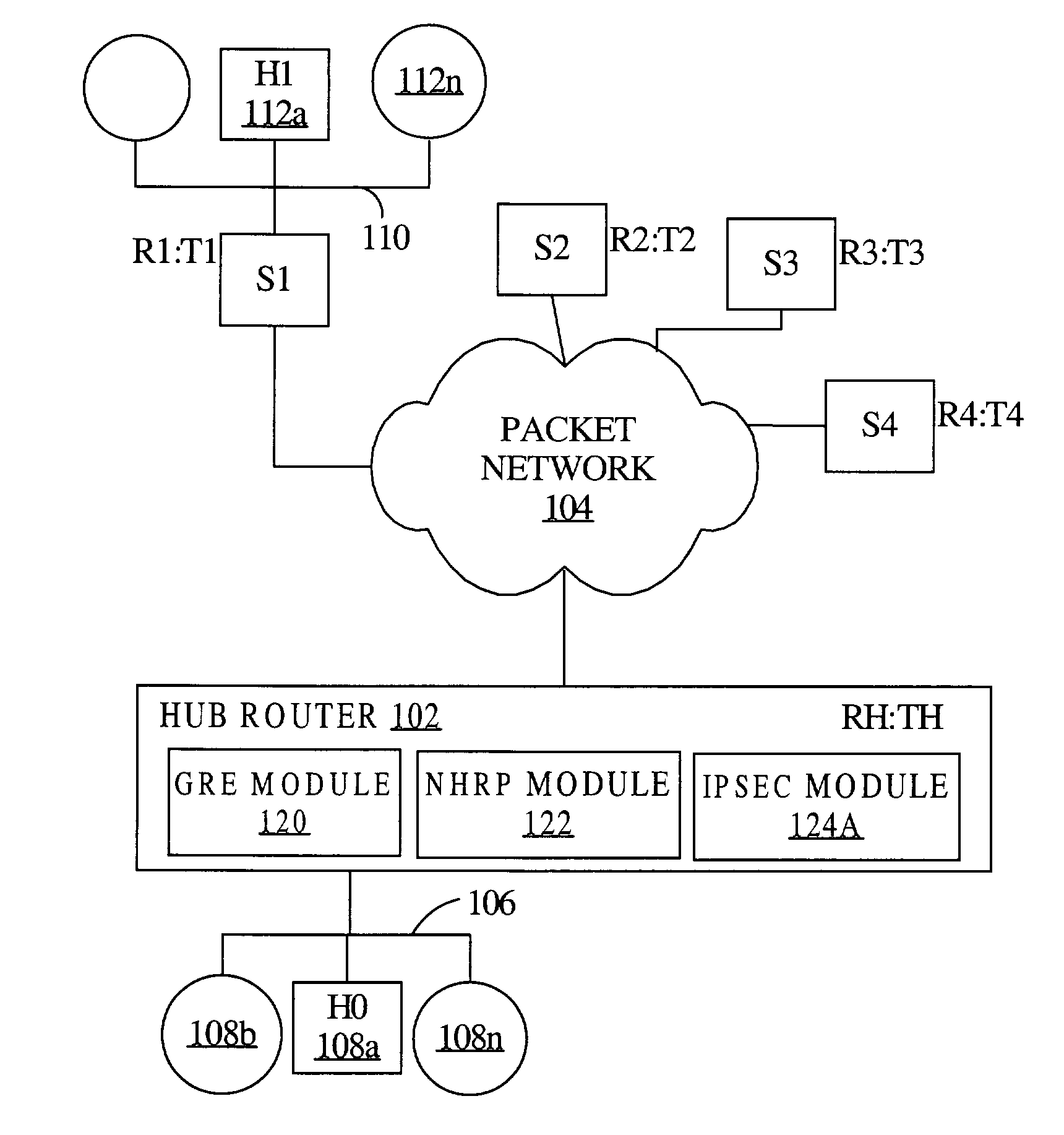
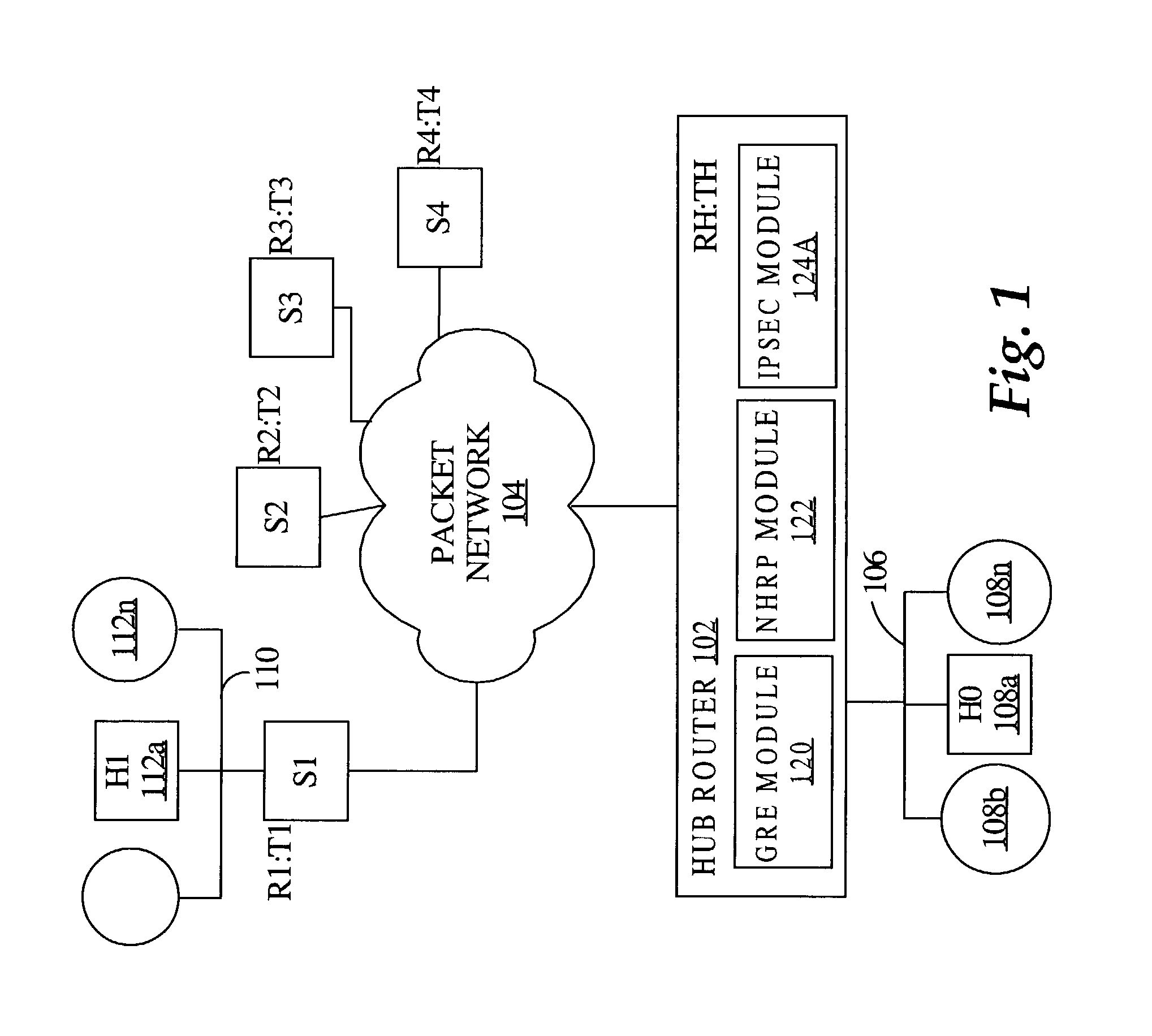
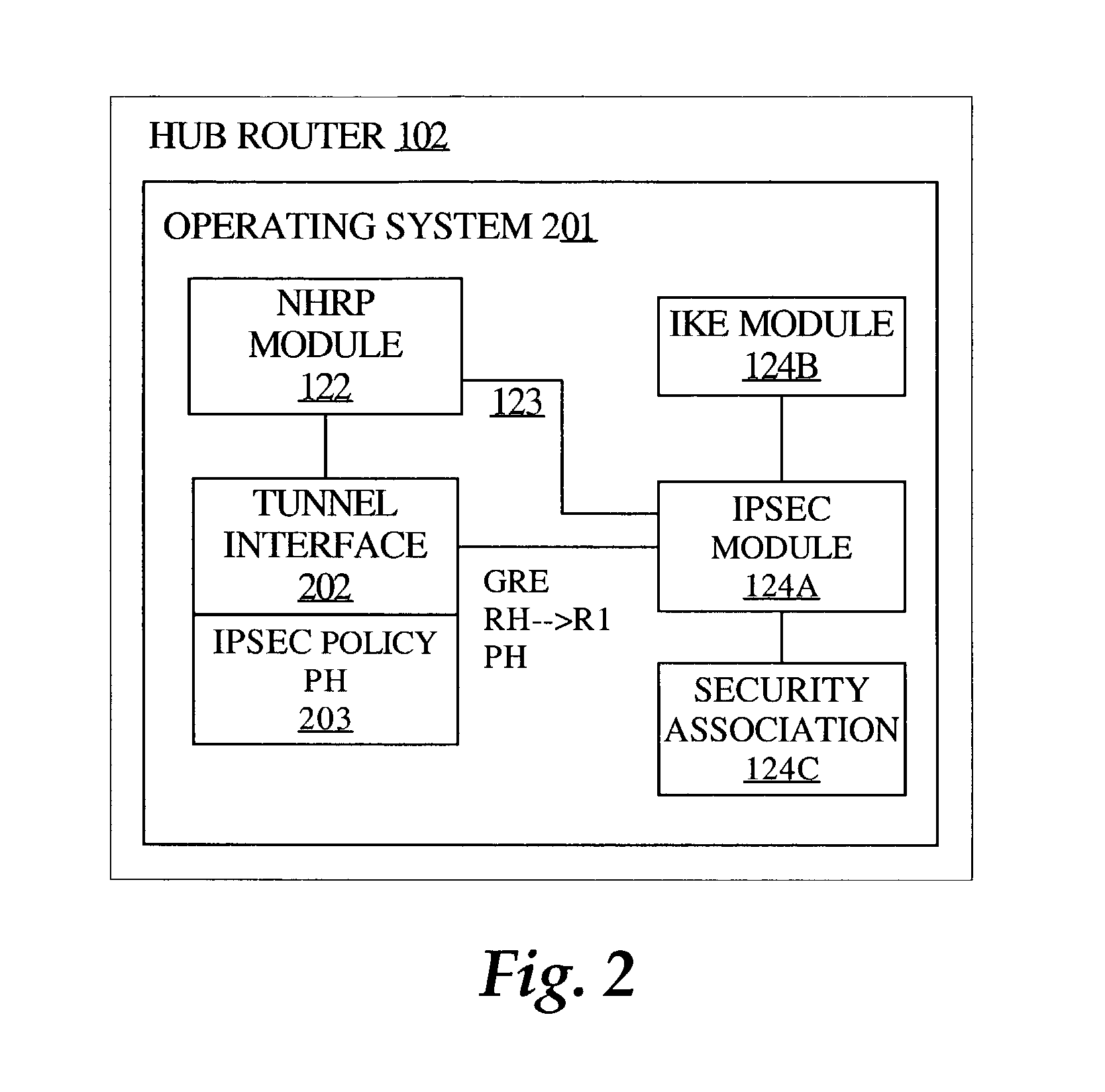
A process is disclosed in which a security policy is associated with a virtual private network (VPN) interface at a first device, for example, a router. Input is received specifying an association of a VPN endpoint address to a corresponding routable network address of a second device. A message is issued to a security module at the first device, the message including the routable network address of the second device and the security policy. Encryption state information is generated for network traffic from the first device to the second device, based on the message. The process is applicable to a hub-and-spoke network architecture that utilizes a point-to-multipoint GRE tunnel and the IPsec protocol for security. The process is dynamic in that the encryption state is generated for traffic over a VPN link, in response to notification of a virtual address-to-real address mapping, i.e., the association. In an embodiment, the association is an NHRP mapping.
Owner:CISCO TECH INC
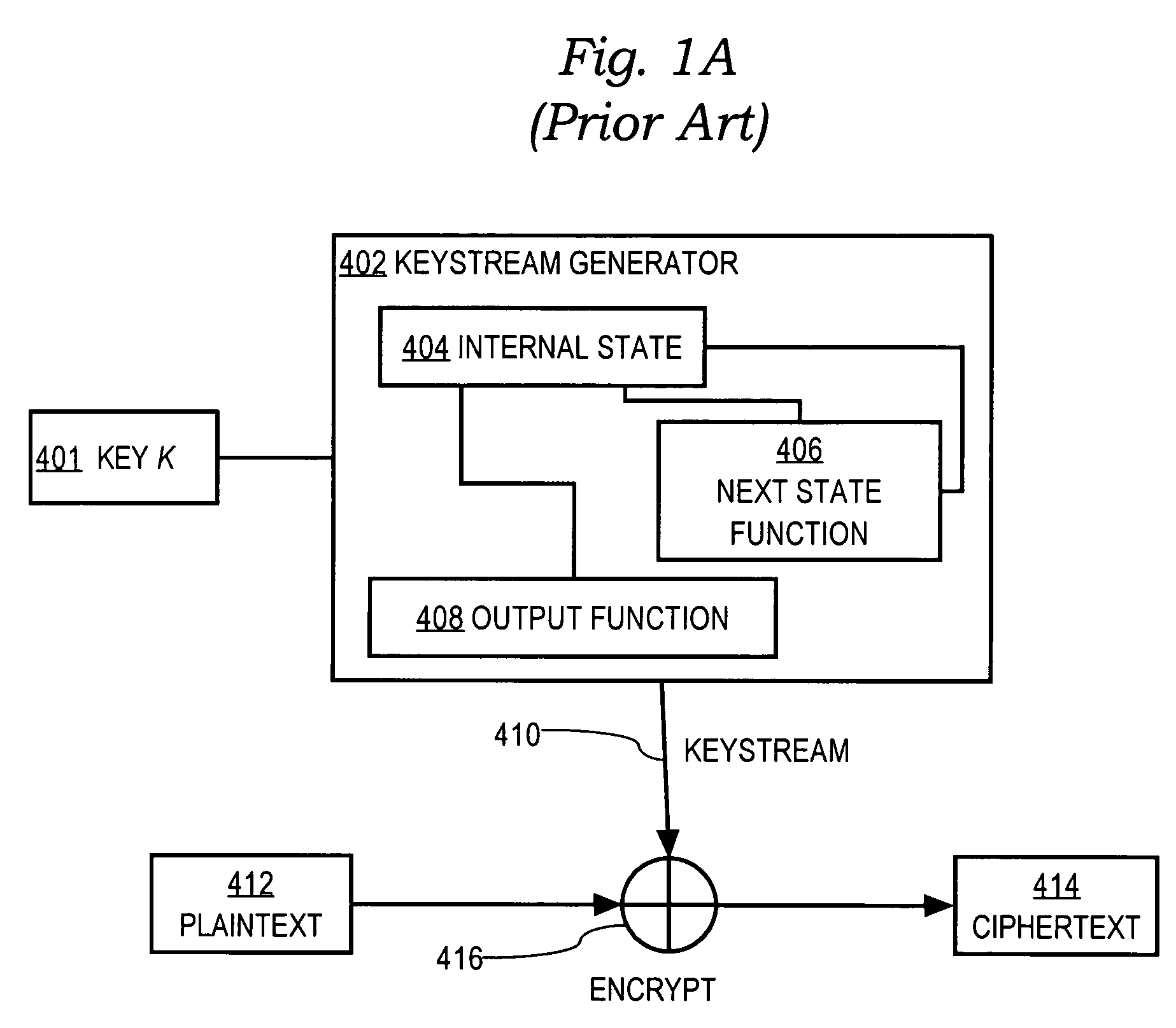
Encryption method and apparatus with forward secrecy and random-access key updating method
InactiveUS7095850B1Generate efficientlyComputationally efficientData stream serial/continuous modificationSecret communicationOne-way functionRekeying
An encryption method and apparatus that provides forward secrecy, by updating the key using a one-way function after each encryption. By providing forward secrecy within a cipher, rather than through a key management system, forward secrecy may be added to cryptographic systems and protocols by using the cipher within an existing framework. A random-access key updating method can efficiently generate one or more future keys in any order. Embodiments are applicable to forward secret ciphers that are used to protect protocols with unreliable transport, to ciphers that are used in multicast or other group settings, and to protection of packets using the IPSec protocols.
Owner:CISCO TECH INC
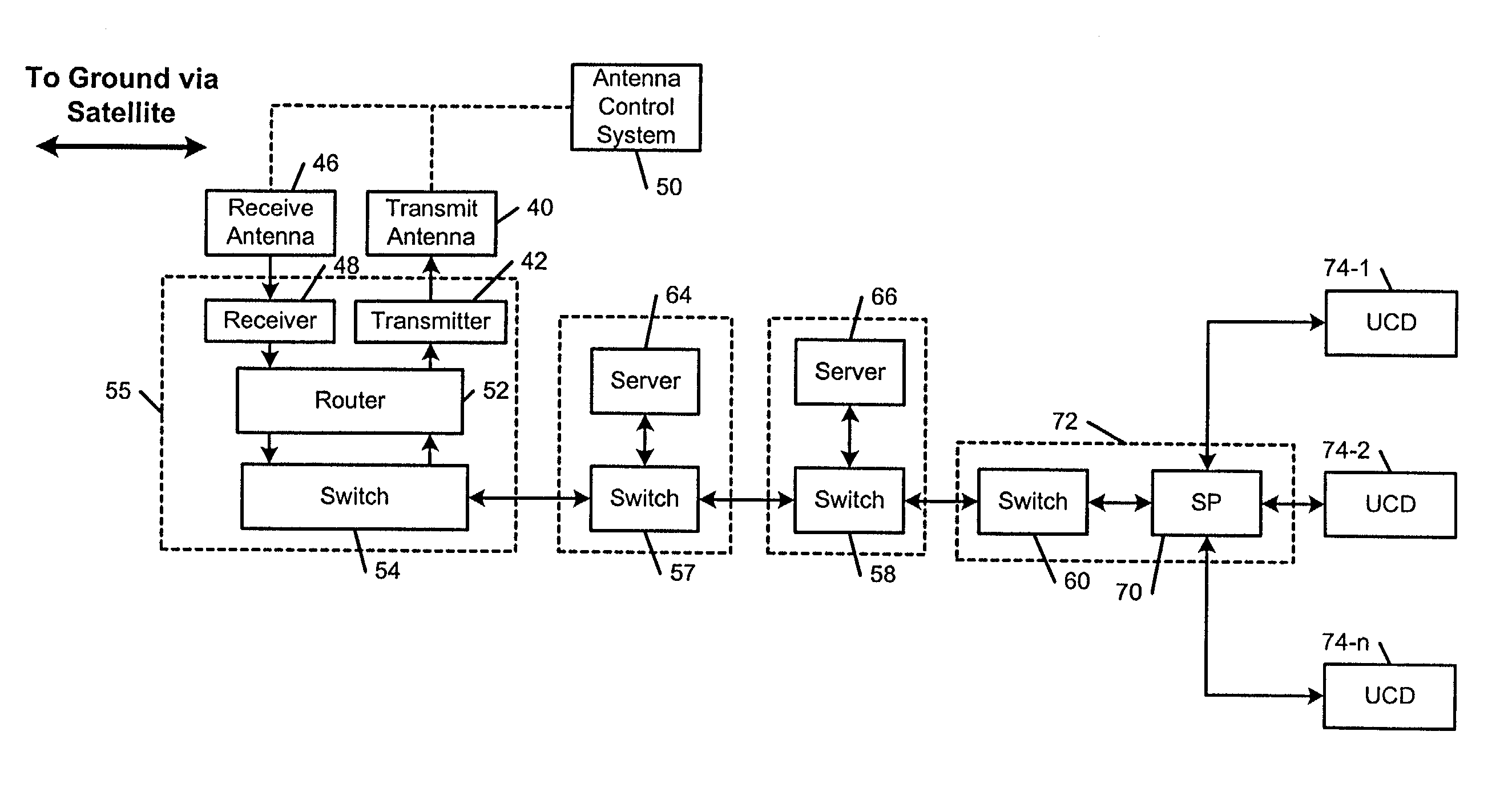
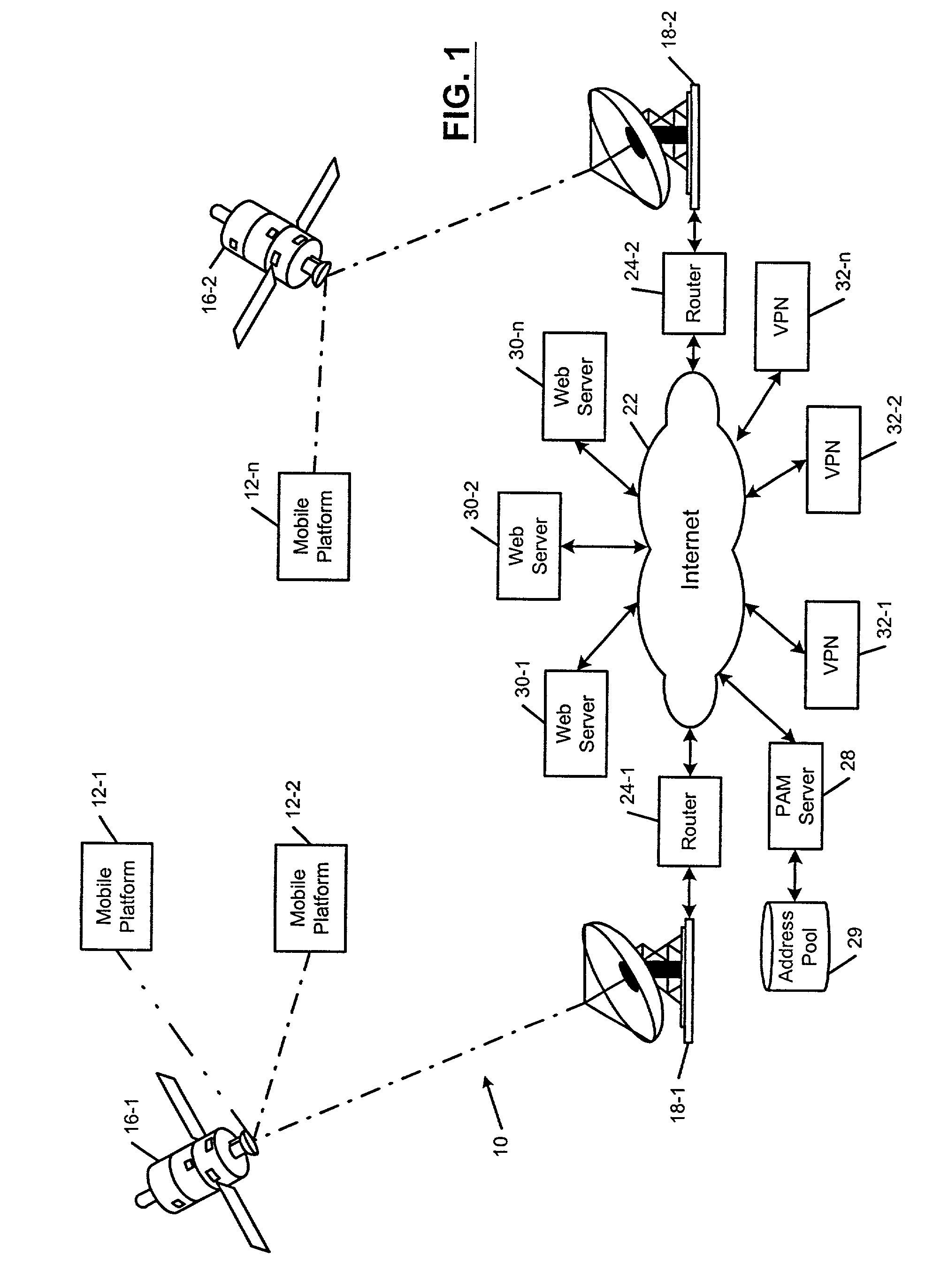
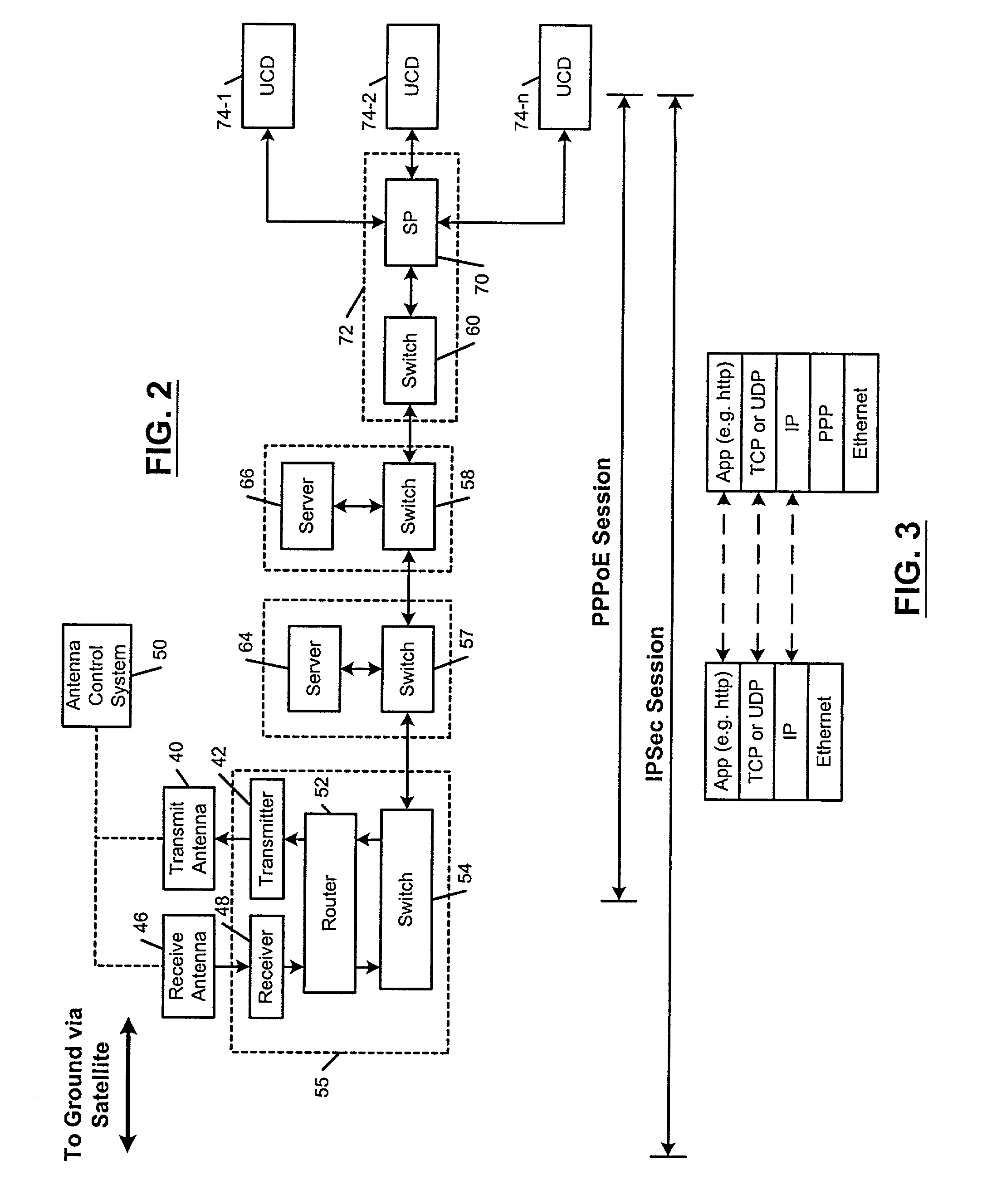
Mobile communications network using point-to-point protocol over ethernet
A communications system that provides broadband access to passengers of mobile platforms includes a router located on the mobile platform. A network is connected to the router. User communication devices (UCDs) connected to the network, wherein the UCDs establish point-to-point over Ethernet (PPPoE) sessions with the router. A transmitter and a receiver are connected to the router. A satellite and a ground station are in communication with the transmitter and the receiver. A distributed communications system includes virtual private networks (VPN) and is connected to the ground station. A first address manager leases the use of public IP addresses by the mobile platform. A second address manager assigns the public IP addresses to UCDs when the UCDs request access to the VPNs and private IP addresses for other network service. The UCDs employ IPSec protocol when accessing the VPNs.
Owner:THE BOEING CO
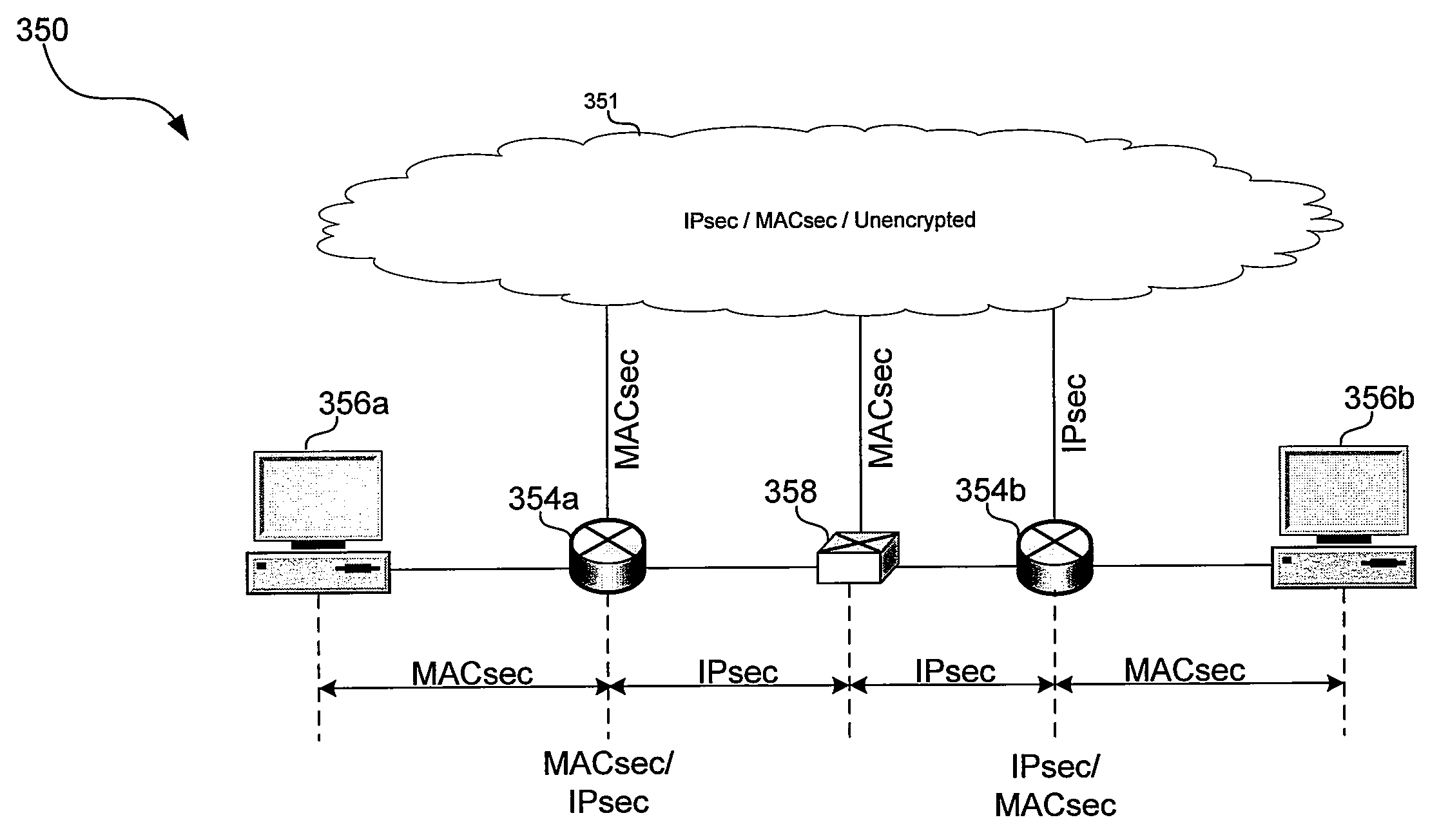
METHOD AND SYSTEM FOR SECURING A NETWORK UTILIZING IPSEC and MACSEC PROTOCOLS
ActiveUS20080126559A1Multiple digital computer combinationsTransmissionEtherTypeProtocol for Carrying Authentication for Network Access
Aspects of a method and system for securing a network utilizing IPsec and MACsec protocols are provided. In one or more network nodes, aspects of the invention may enable conversion between Ethernet packets comprising payloads secured utilizing IPsec protocols and Ethernet packets secured utilizing MACsec protocols. For example, IPsec connections may be terminated at an ingress network node and IPsec connections may be regenerated at an egress network node. Packets secured utilizing MACsec protocols may be detected based on an Ethertype. Packets comprising payloads secured utilizing IPsec protocols may be detected based on a protocol field or a next header field. The conversion may be based on a data structure stored by and / or accessible to the network nodes. Aspects of the invention may enable securing data utilizing MACsec protocols when tunneling IPsec secured data through non-IPsec enabled nodes.
Owner:AVAGO TECH INT SALES PTE LTD
Method and apparatus for application-independent end-to-end security in shared-link access networks
InactiveUS6963982B1Multiple digital computer combinationsProgram controlExpiration TimeEnd to end security
Clients that are connected on a private network and which are assigned a private IP address that is not routable on the Internet can connect to the Internet through a router / server that includes a network address translator (NAT). For outgoing packets, the NAT translates the client's private source IP address and generalized port number (GPN) to the NAT's global IP address and GPN. For incoming packets sent to the NAT's global IP address and GPN, the NAT translates the global destination IP address and GPN to the client's private IP address and GPN. For protocols which cannot be directly supported by the NAT, such as those in the IPSec security protocol suite, the NAT is extended by creating in the NAT's translation table an entry that associates, for a specific unsupported protocol, a client's private IP address and GPN, the NAT's global IP address and GPN, and a foreign address on the Internet, that is valid until a specified or default expiration time. Outgoing packets from the client to that foreign address and incoming packets from that foreign address to the NAT's global IP address and GPN are translated according to the entry until the entry expires. In associations with these translations to outgoing and incoming packets, the client implements any Application Layer Gateway (ALG) that would otherwise be implemented at the NAT. Further, at the client, outgoing packets are modified before being transmitted so as to pre-compensate for the effects of the translations. Incoming packets at the client from the NAT are similarly modified so as to post-compensate for the effects of the translations. For the IPSec protocol, these modification include adjusting the checksum in the TCP or UDP header to account for IP address and TCP or UDP port number translations.
Owner:ALCATEL-LUCENT USA INC
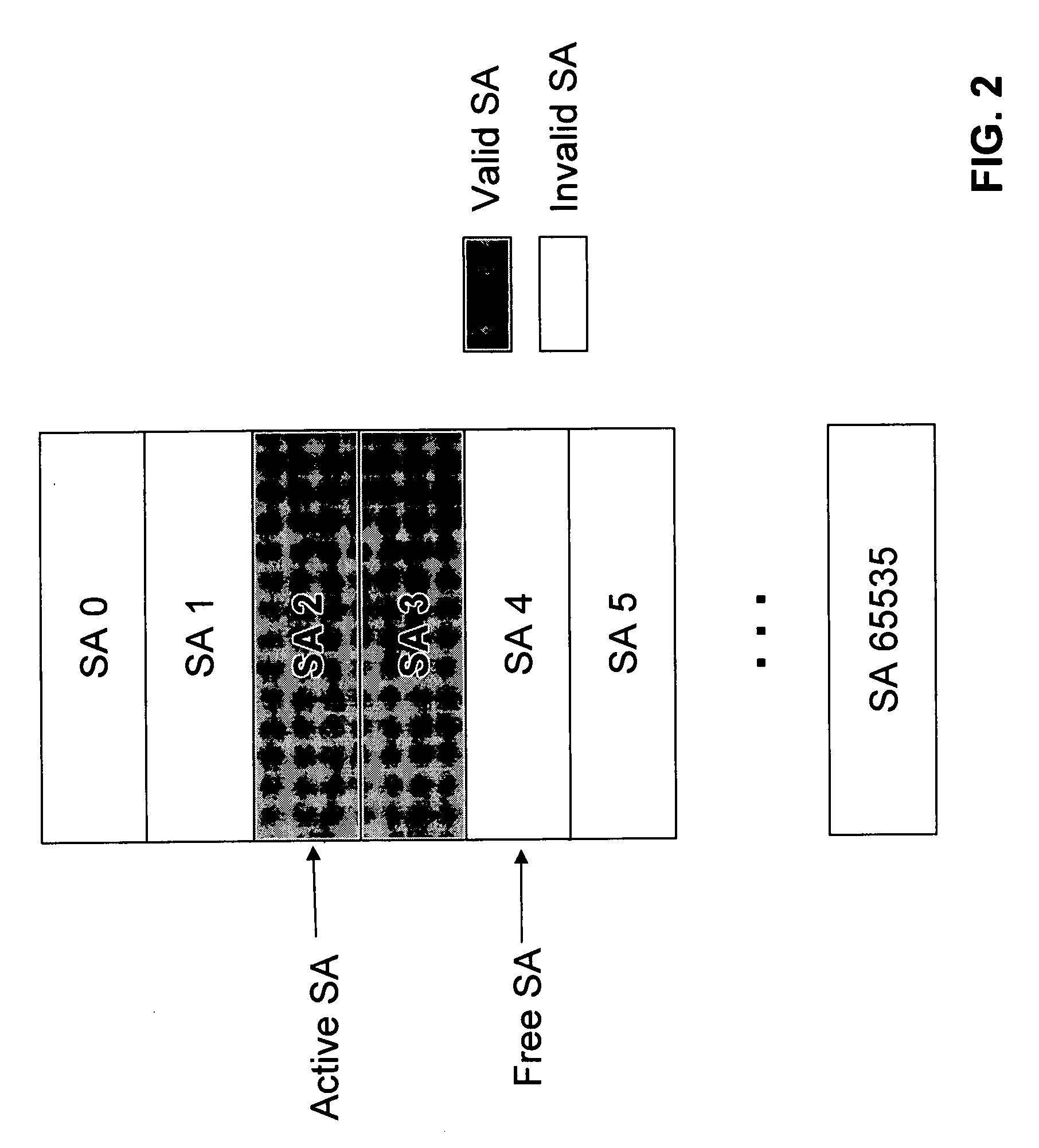
Method and apparatus for indexing an inbound security association database
ActiveUS7434045B1Digital data processing detailsSpecial data processing applicationsComputer networkSecurity association
Processes are disclosed in which an index value is generated for locating a security association in a security association database, such as an inbound SAD associated with the IPsec set of protocols. The index value is specified for insertion into a Security Parameter Index (SPI) field of a packet header, such as an IPsec header. For packets that are to be secured according to the policies and protocols identified in the header and the security association and that are transmitted to a particular network device or host, the index value is inserted into the SPI field of the packets by a packet sender. The packet is then parsed by a packet receiver, the index value determined from the SPI and used to identify the security association in the SAD, based solely on the index value determined from the SPI. Hence, a simple and efficient mechanism is provided for fast inbound security association lookups.
Owner:CISCO TECH INC
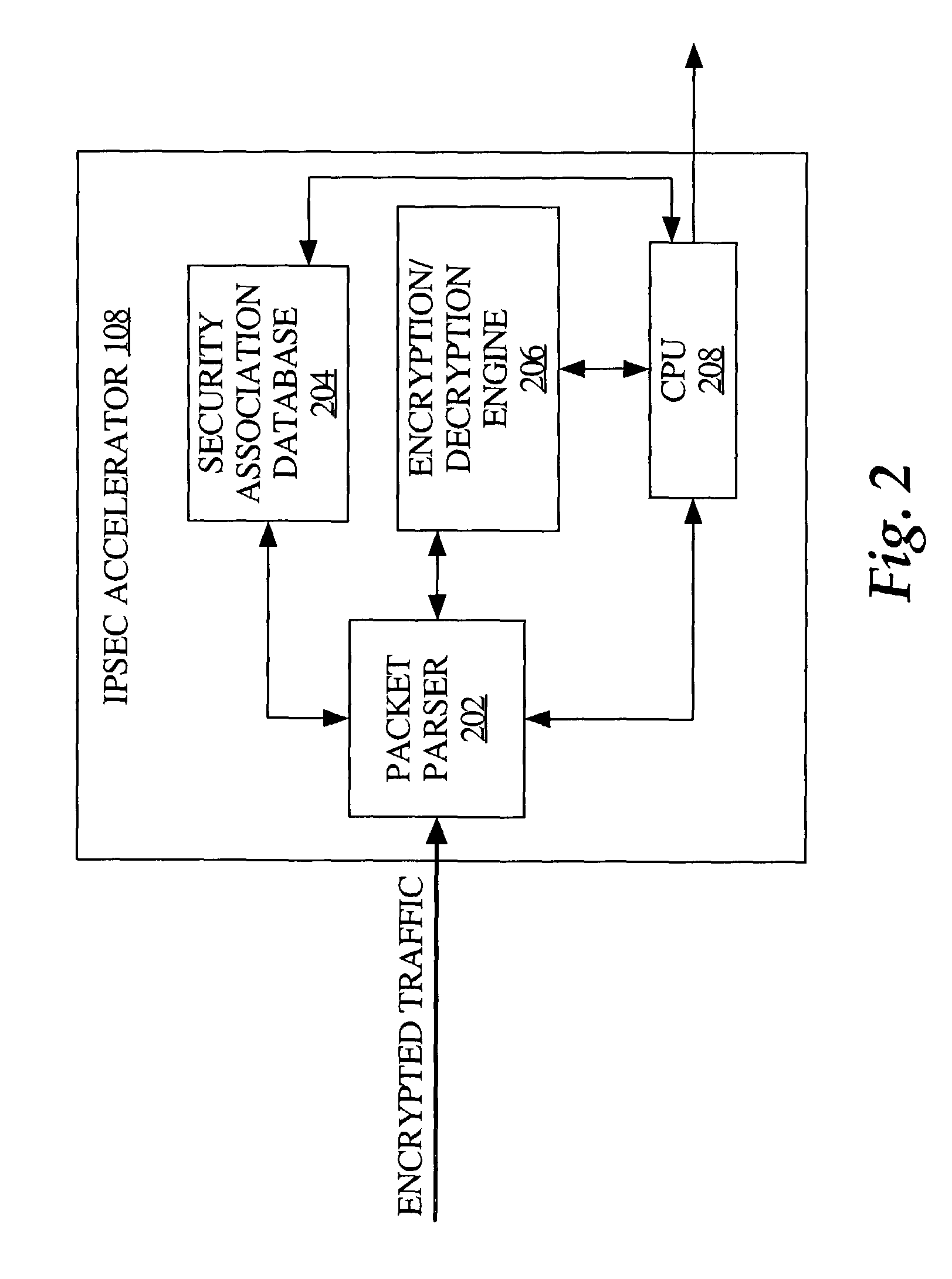
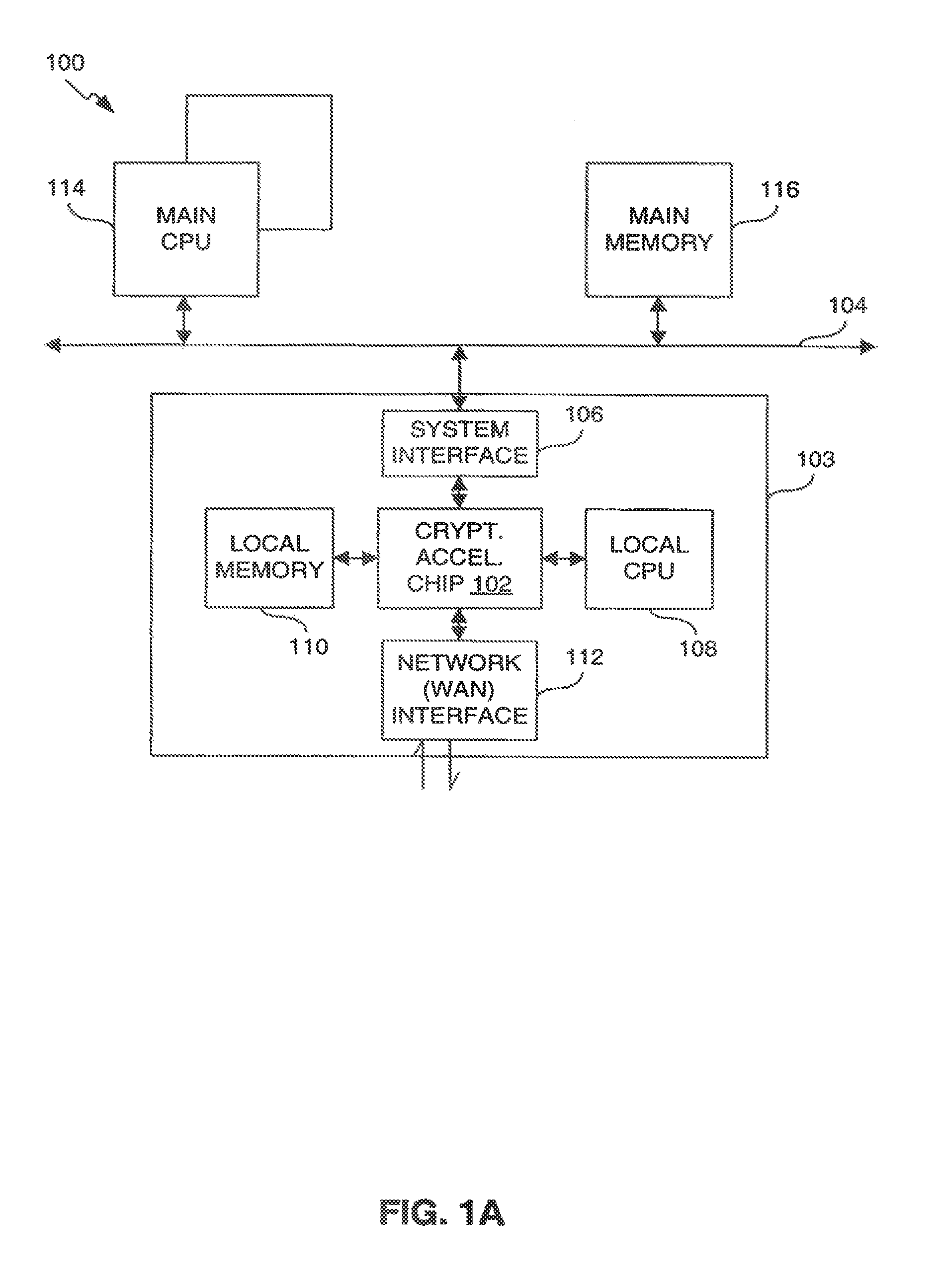
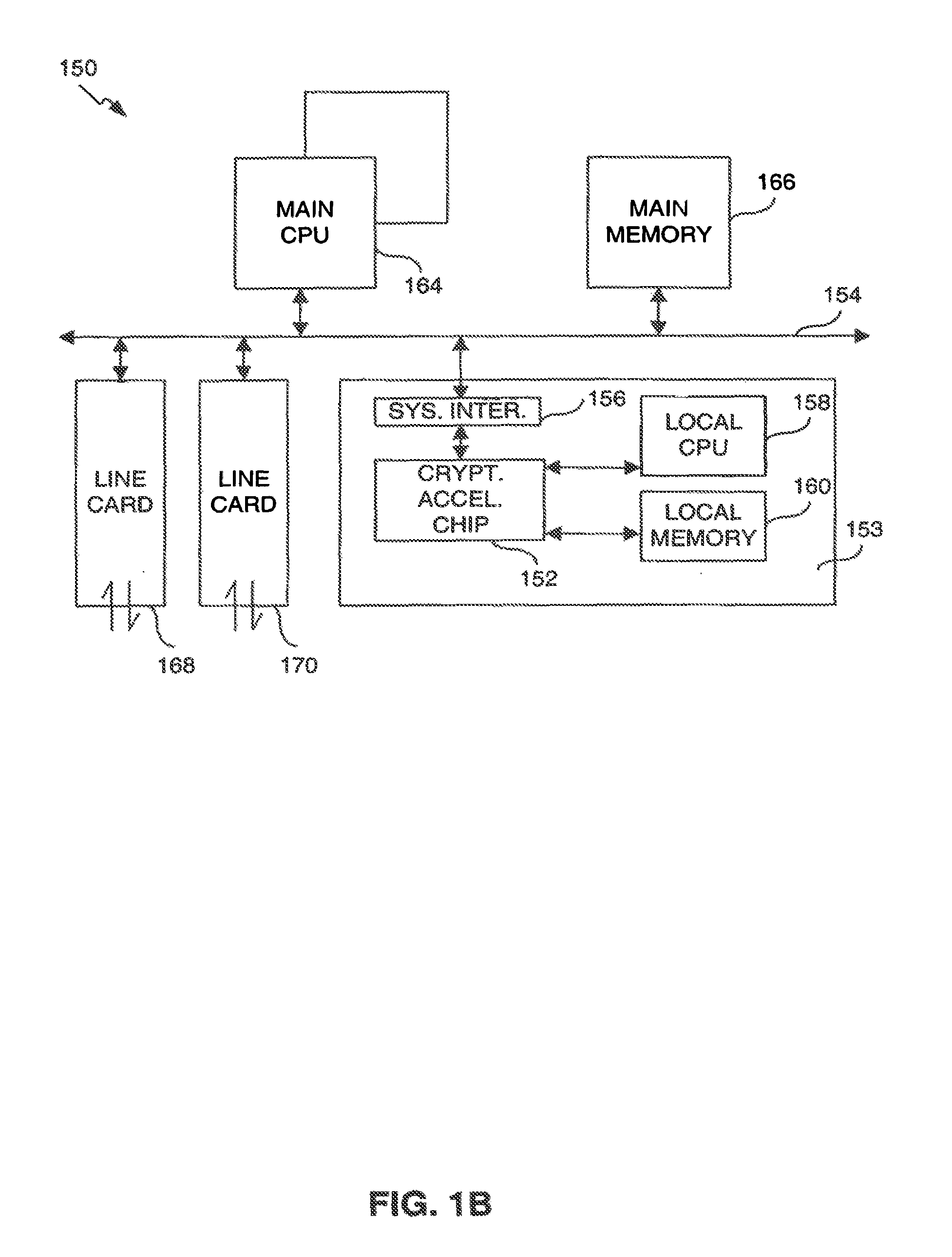
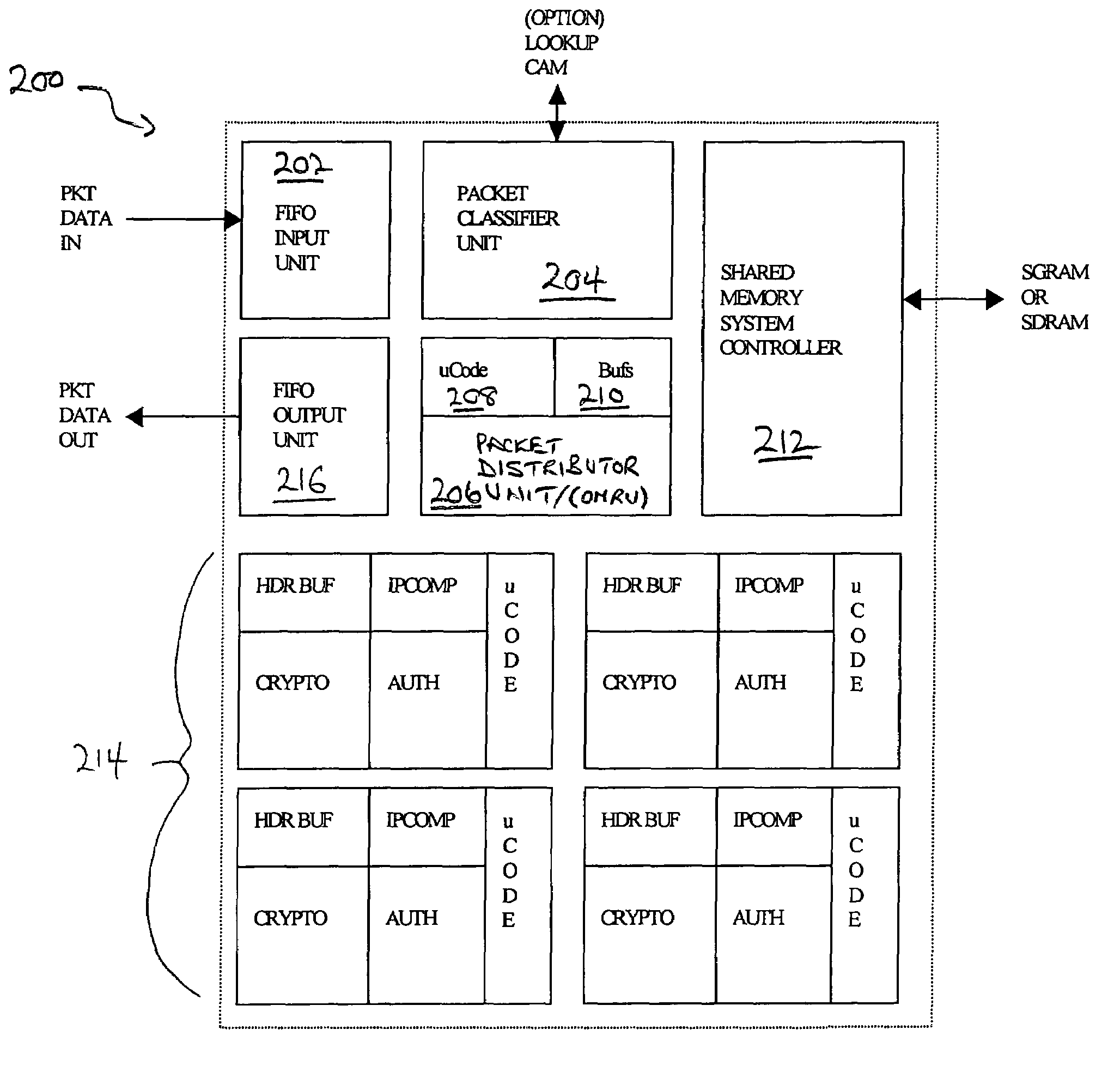
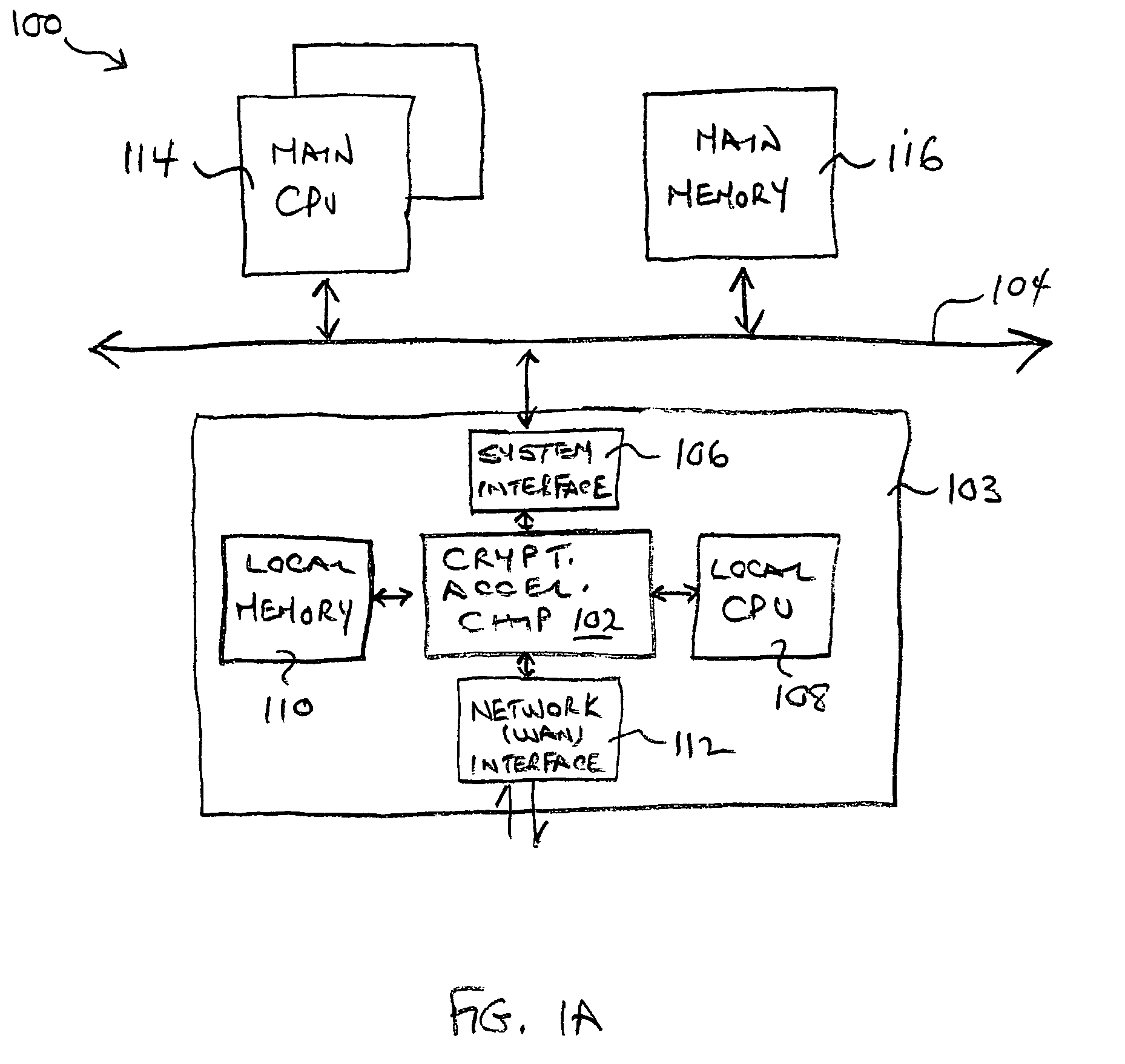
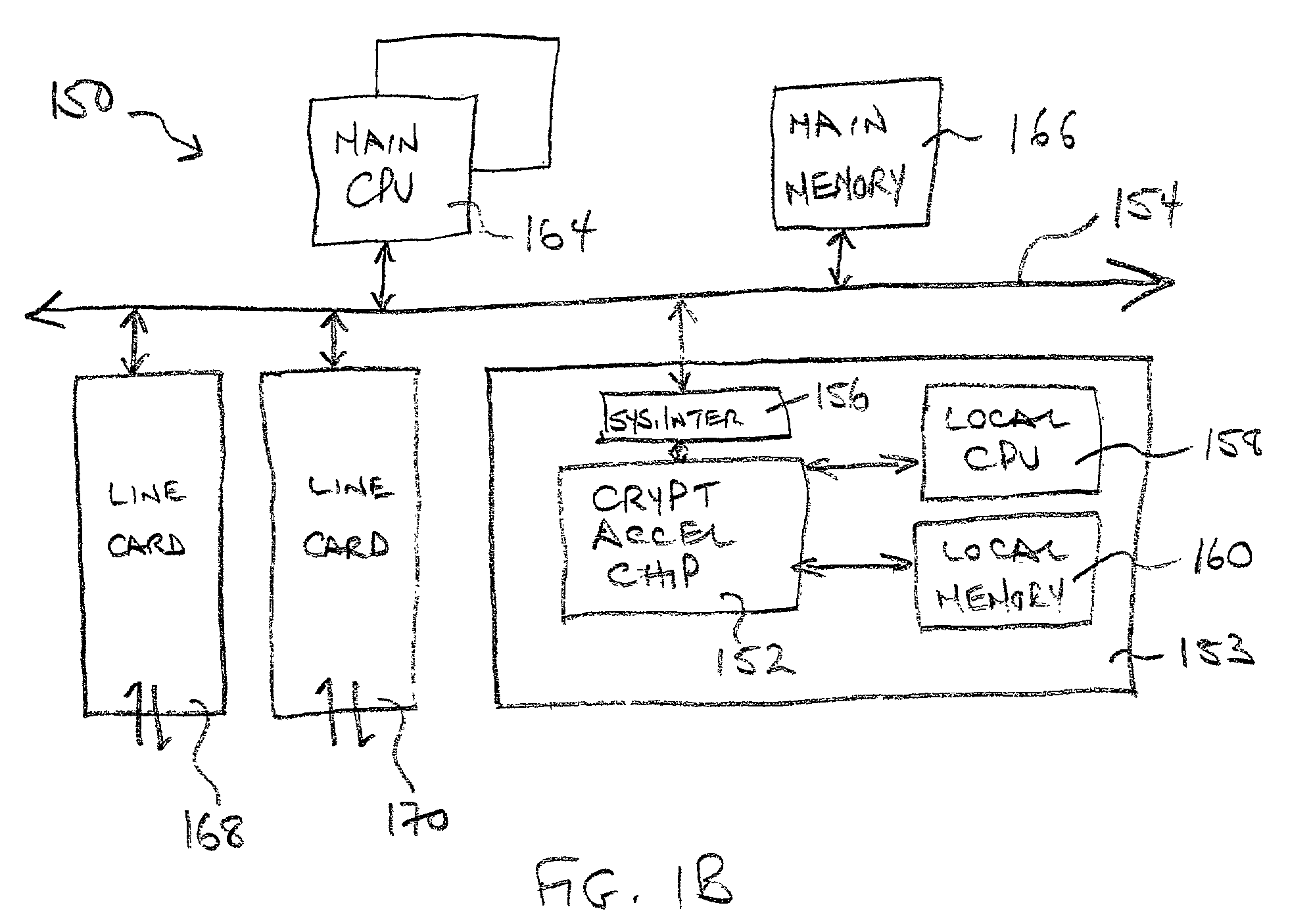
Classification engine in a cryptography acceleration chip
InactiveUS7996670B1Efficient processingMaximum performanceDigital data processing detailsConcurrent instruction executionCryptographic acceleratorNetwork service
Provided is an architecture for a cryptography accelerator chip that allows significant performance improvements over previous prior art designs. In various embodiments, the architecture enables parallel processing of packets through a plurality of cryptography engines and includes a classification engine configured to efficiently process encryption / decryption of data packets. Cryptography acceleration chips in accordance may be incorporated on network line cards or service modules and used in applications as diverse as connecting a single computer to a WAN, to large corporate networks, to networks servicing wide geographic areas (e.g., cities). The present invention provides improved performance over the prior art designs, with much reduced local memory requirements, in some cases requiring no additional external memory. In some embodiments, the present invention enables sustained full duplex Gigabit rate security processing of IPSec protocol data packets.
Owner:AVAGO TECH INT SALES PTE LTD
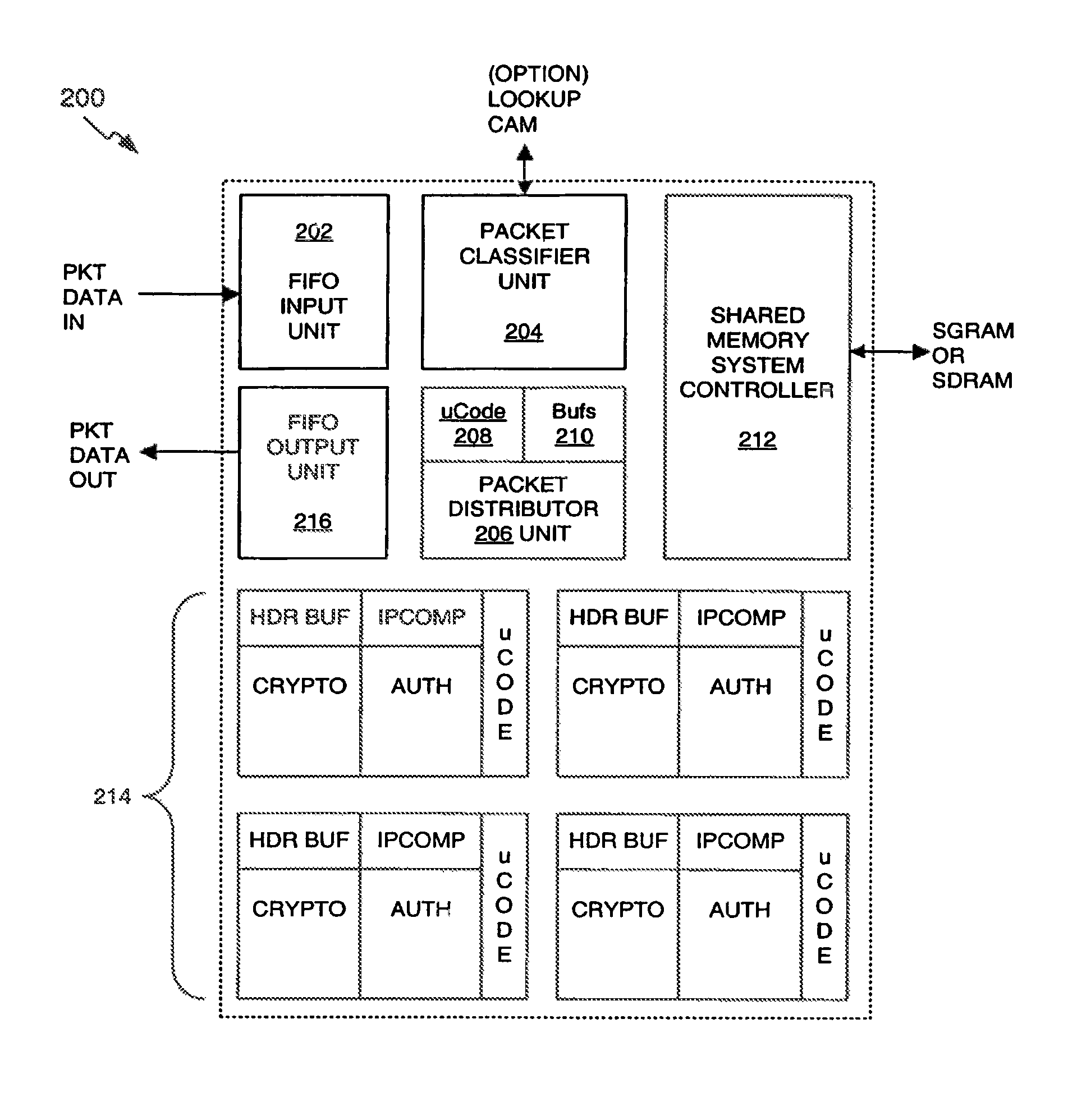
Distributed processing in a cryptography acceleration chip
InactiveUS7600131B1Efficient processingImprove performanceDigital data processing detailsUnauthorized memory use protectionCryptographic acceleratorNetwork service
Provided is an architecture for a cryptography accelerator chip that allows significant performance improvements over previous prior art designs. In various embodiments, the architecture enables parallel processing of packets through a plurality of cryptography engines and includes a classification engine configured to efficiently process encryption / decryption of data packets. Cryptography acceleration chips in accordance may be incorporated on network line cards or service modules and used in applications as diverse as connecting a single computer to a WAN, to large corporate networks, to networks servicing wide geographic areas (e.g., cities). The present invention provides improved performance over the prior art designs, with much reduced local memory requirements, in some cases requiring no additional external memory. In some embodiments, the present invention enables sustained full duplex Gigabit rate security processing of IPSec protocol data packets.
Owner:AVAGO TECH INT SALES PTE LTD
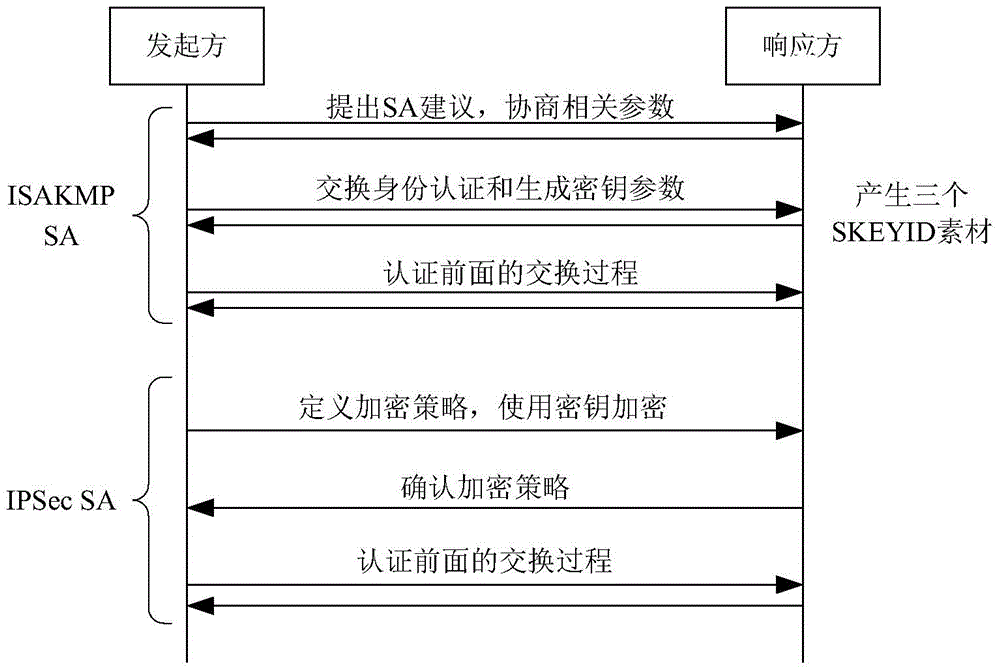
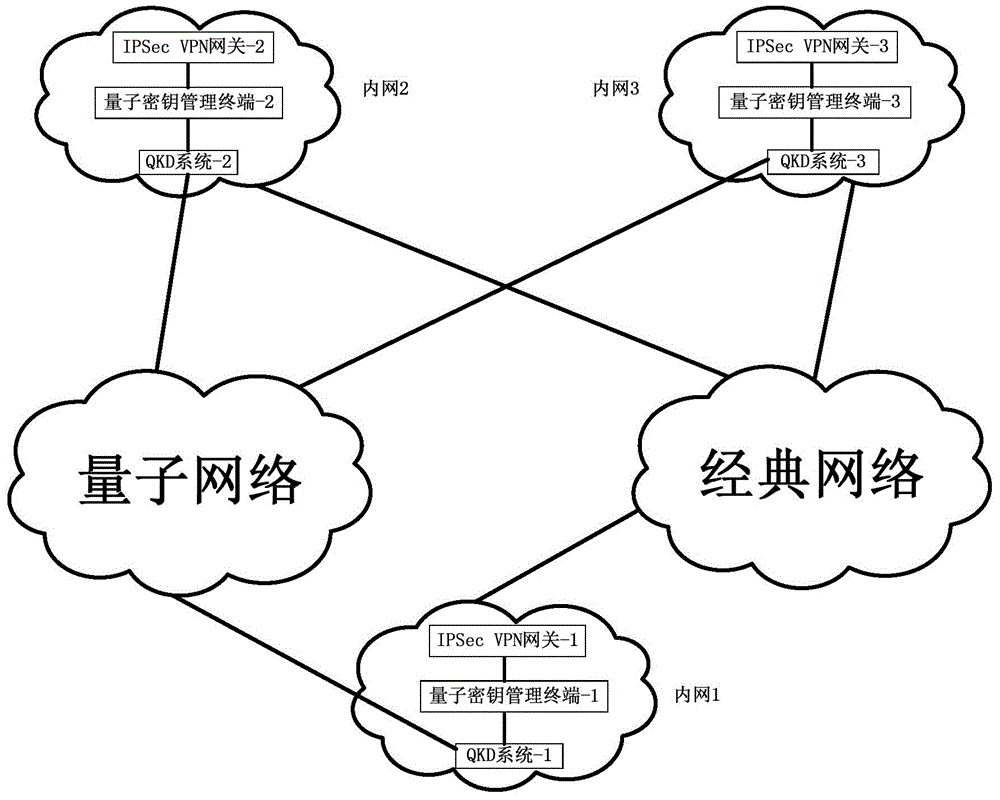
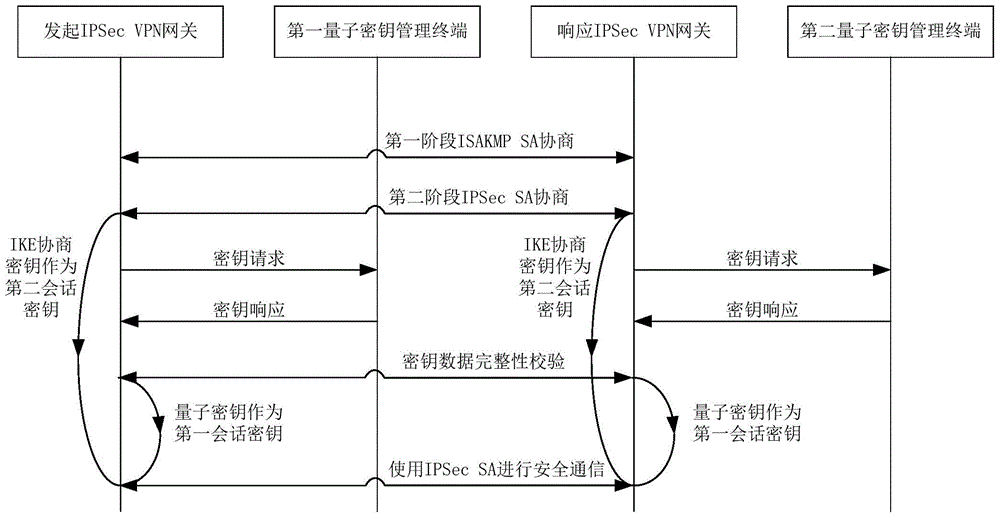
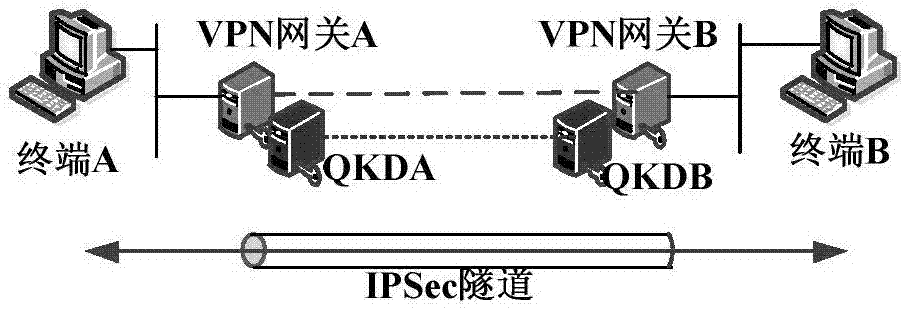
Method and system for extended use of quantum keys in IPSec VPN (internet protocol security-virtual private network)
ActiveCN104660603ANovel structureIncrease update frequencyKey distribution for secure communicationData switching networksSession keyKey management
The invention discloses a method and a system for extended use of quantum keys in an IPSec VPN (internet protocol security-virtual private network) system. The IPSec VPN system comprises at least two IPSec VPN gateways including an initiating IPSec VPN gateway and a responding IPSec VPN gateway as well as corresponding quantum key management terminals. The method comprises steps as follows: through parallel processing of negotiation of the quantum keys and IKE (internet key exchange) negotiated keys, the quantum keys are taken as first session keys for preferential use, and the IKE negotiated keys are taken as second session keys for safety communication. Besides, the invention further provides the corresponding IPSec VPN gateway, the quantum key management terminals and the IPSec VPN system. The quantum keys are taken as the session keys through extended use, so that the session key updating frequency is greatly increased and the safety communication performance of conventional IPSec VPN is guaranteed under the condition that an original IPSec VPN is compatible.
Owner:SHANDONG INST OF QUANTUM SCI & TECH +1
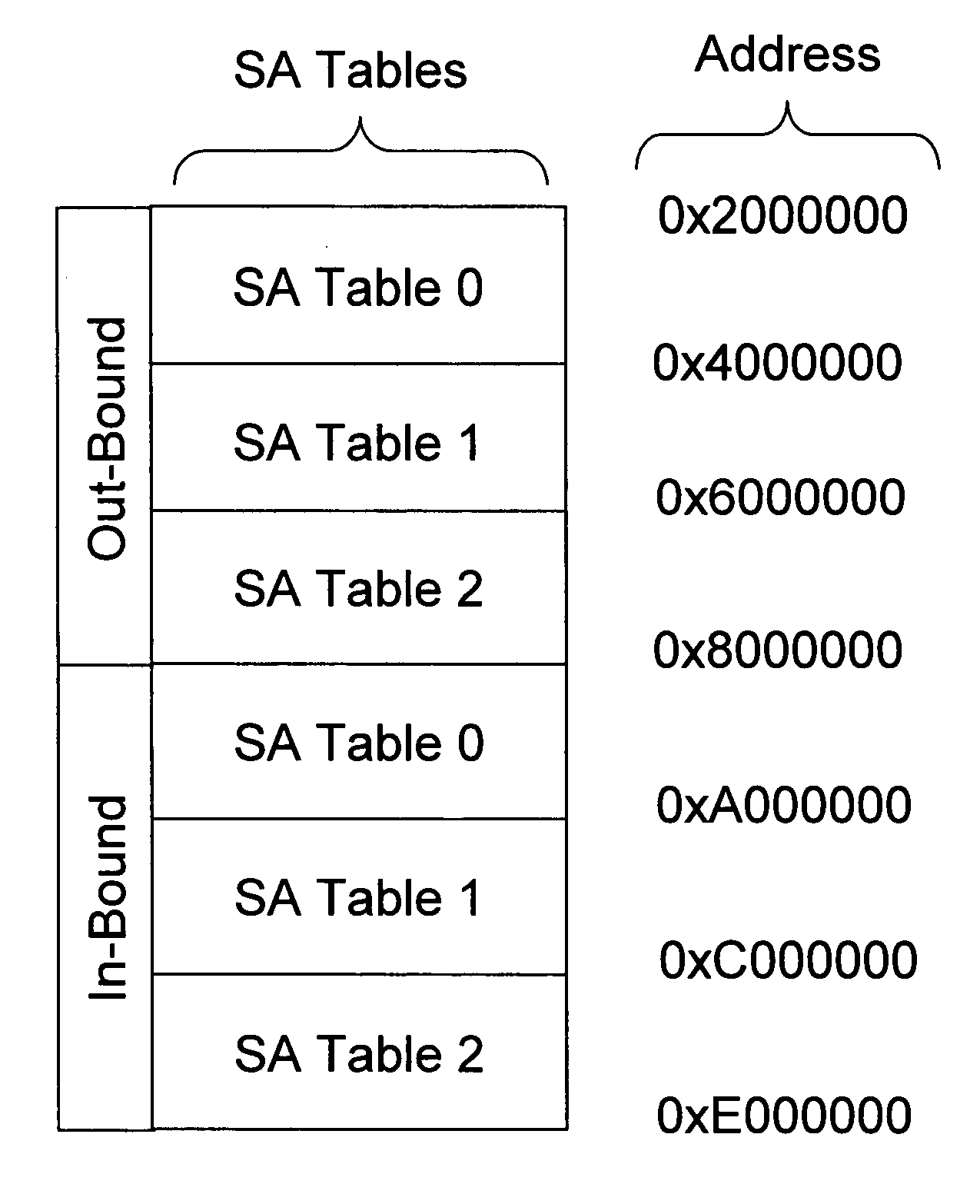
Method of integrating QKD with IPSec
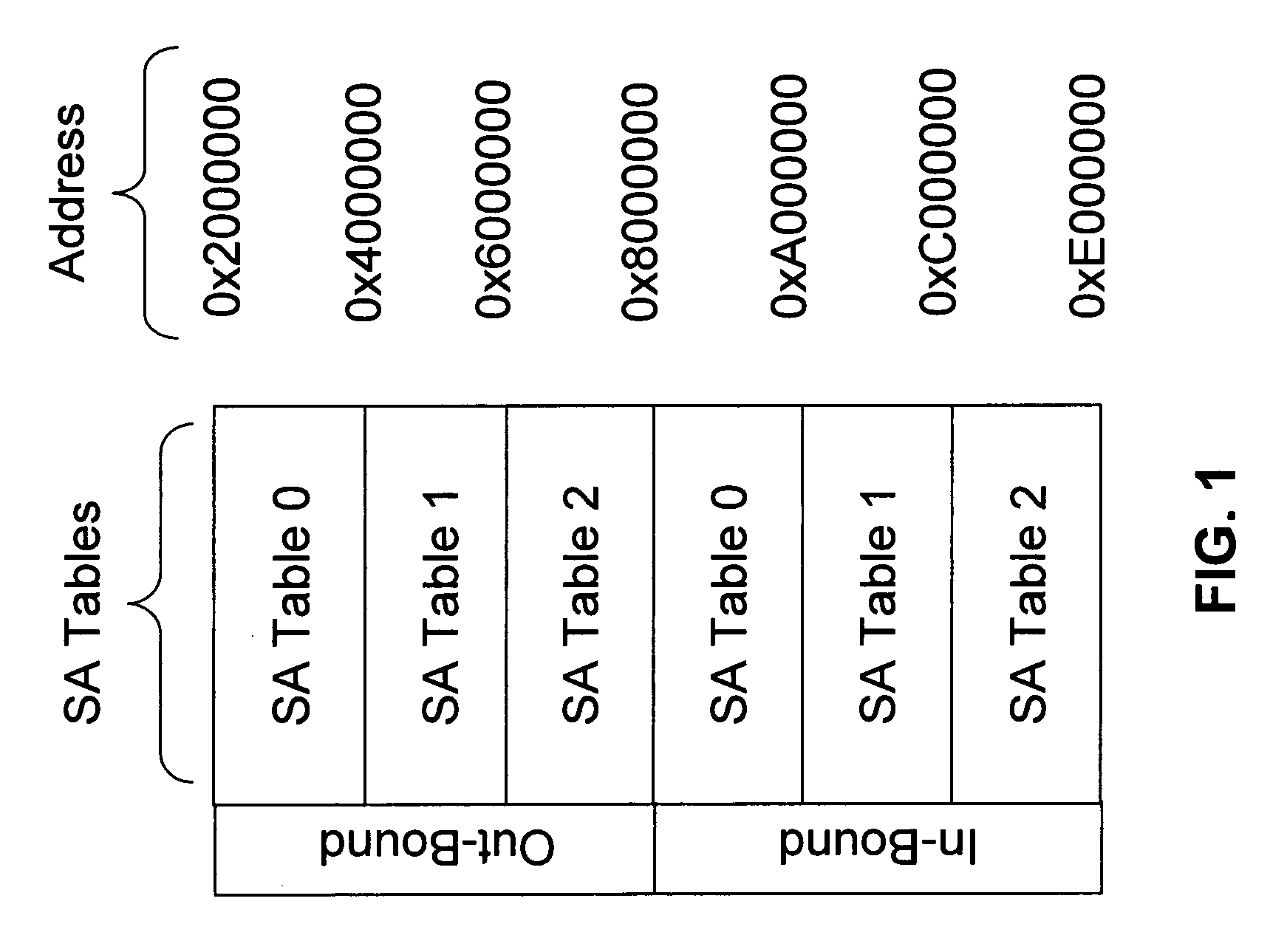
ActiveUS20060212936A1Increase in sizeFast key flippingKey distribution for secure communicationMultiple digital computer combinationsInternet Key ExchangeSecurity association
A method of integrating quantum key distribution (QKD) with Internet protocol security (IPSec) to improve the security of IPSec. Standard IPSec protocols impose limits on the frequency at which keys can be changed. This makes efforts to improve the security of IPSec by employing quantum keys problematic. The method includes increasing the size of the Security Association (SA) Table in a manner that enables a high key change rate so that the quantum keys can be combined with the classical keys generated by Internet Key Exchange (IKE). The invention includes a method of creating the SA Table by combining quantum keys generated by the QKD process with classical keys generated by the IKE process, thereby enabling QKD-based IPSec.
Owner:MAGIQ TECH INC
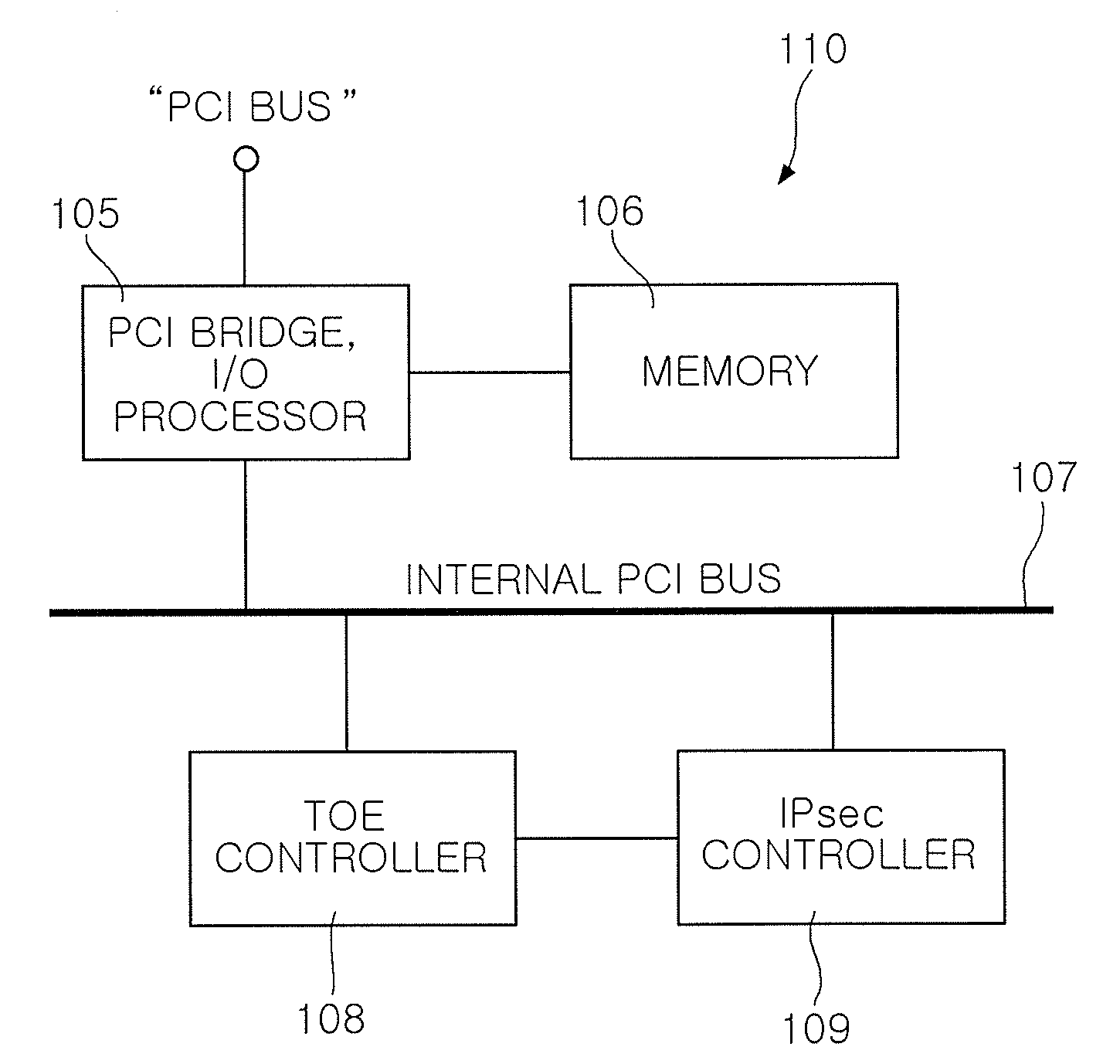
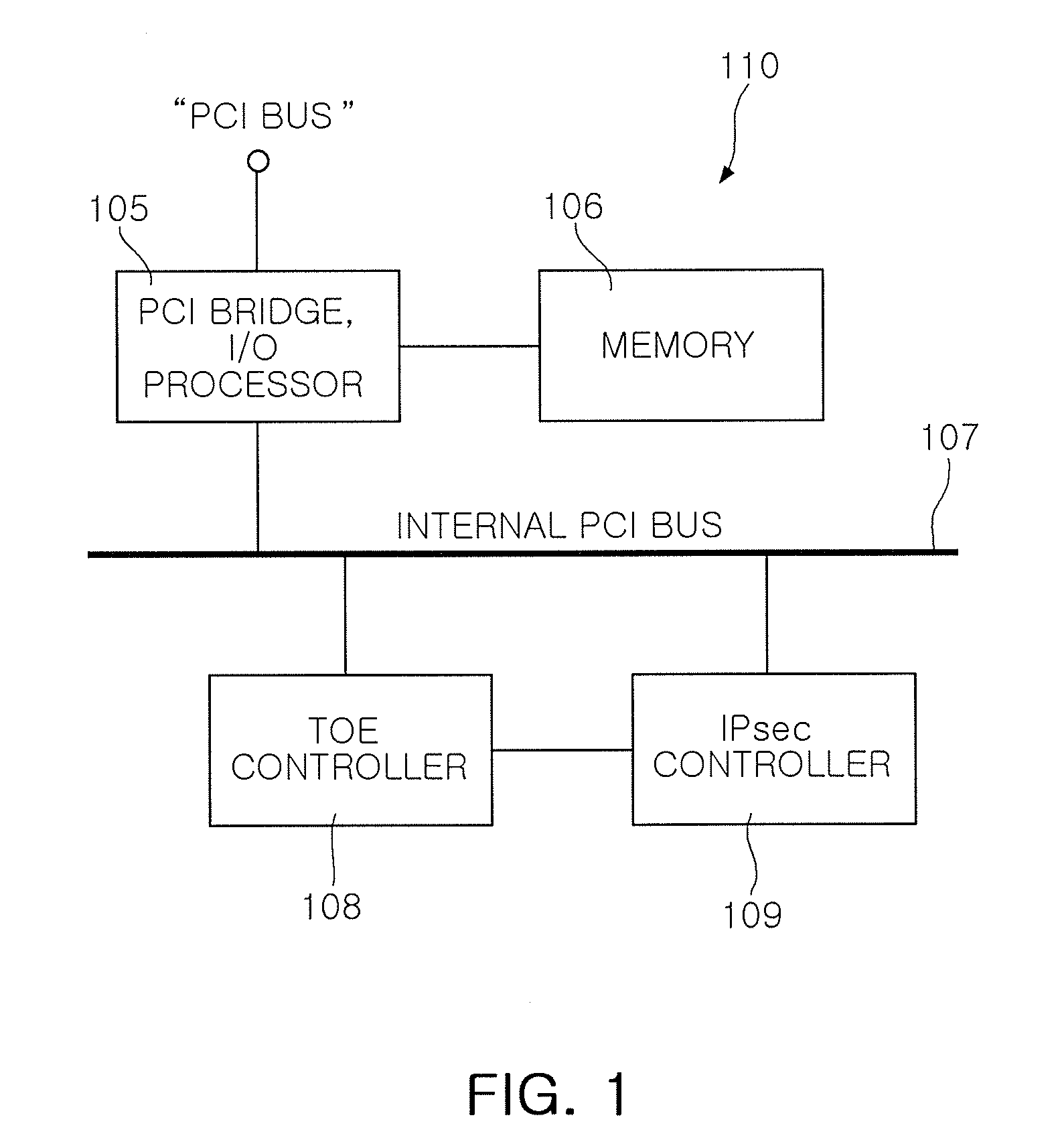
DATA ACCELERATION APPARATUS FOR iSCSI AND iSCSI STORAGE SYSTEM USING THE SAME
InactiveUS20080008205A1Reduce loadImprove processing speedComputer security arrangementsData switching by path configurationSCSIData store
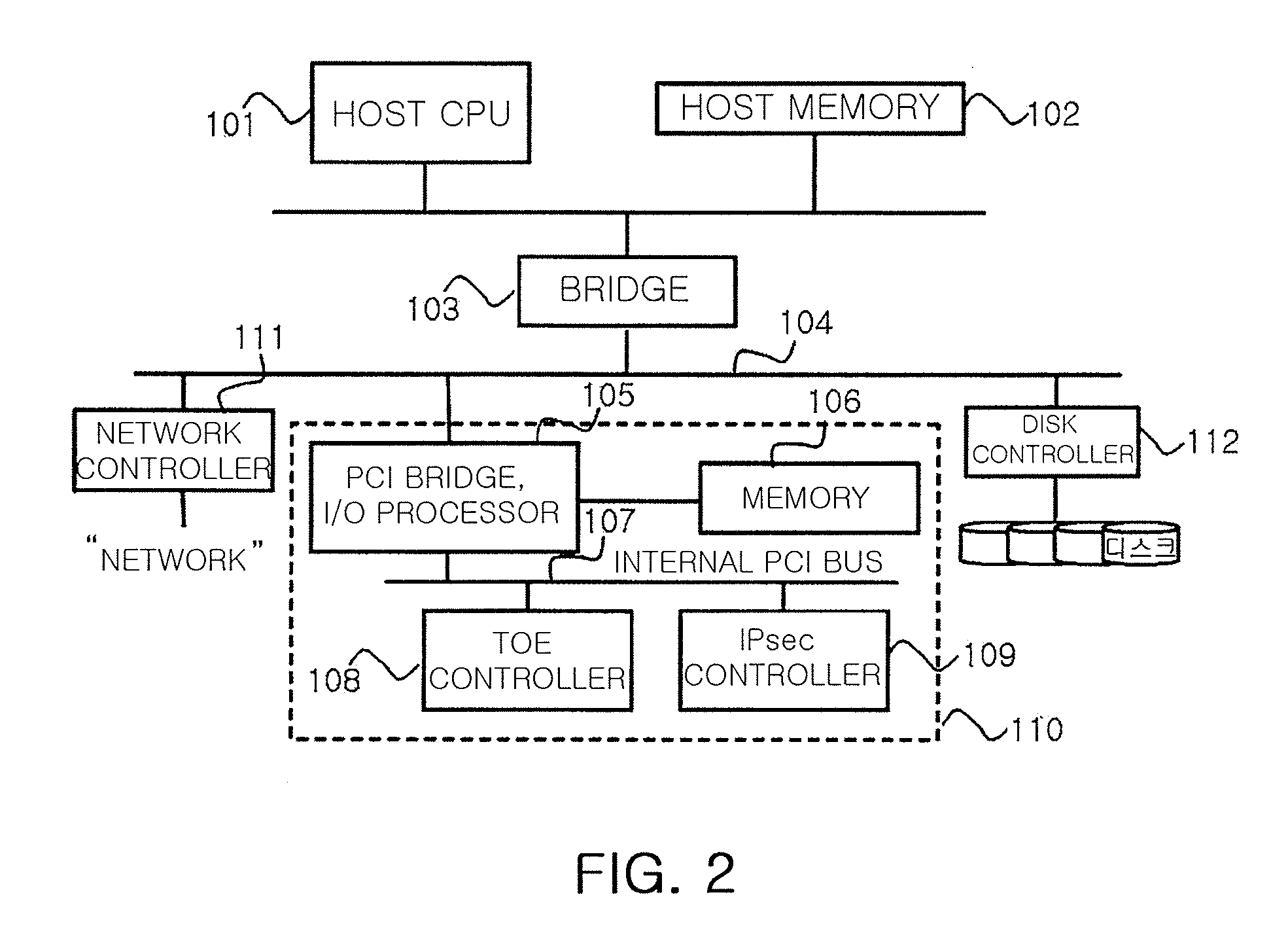
A data acceleration apparatus for Internet small computer system interface (iSCSI) and an iSCSI storage system using the same are provided. A data acceleration apparatus comprises an I / O processor, a memory, a TOE controller, and an IPsec controller. The I / O processor is connected to an iSCSI storage system through a PCI bus and controls a PCI bridge and the memory. The memory stores data according to the control by the I / O processor, serves as a buffer for processing a TCP / IP and an IPsec protocol, and provides a data storage space. The TOE controller receives data to be read or written through the I / O processor, offloads a stack of the TCP / IP, and processes the TCP / IP. The IPsec controller processes the IPsec protocol for the inputted and outputted data.
Owner:ELECTRONICS & TELECOMM RES INST
Authentication engine architecture and method
InactiveUS7177421B2Improve performanceIncrease speedRandom number generatorsPublic key for secure communicationComputer hardwareHardware implementations
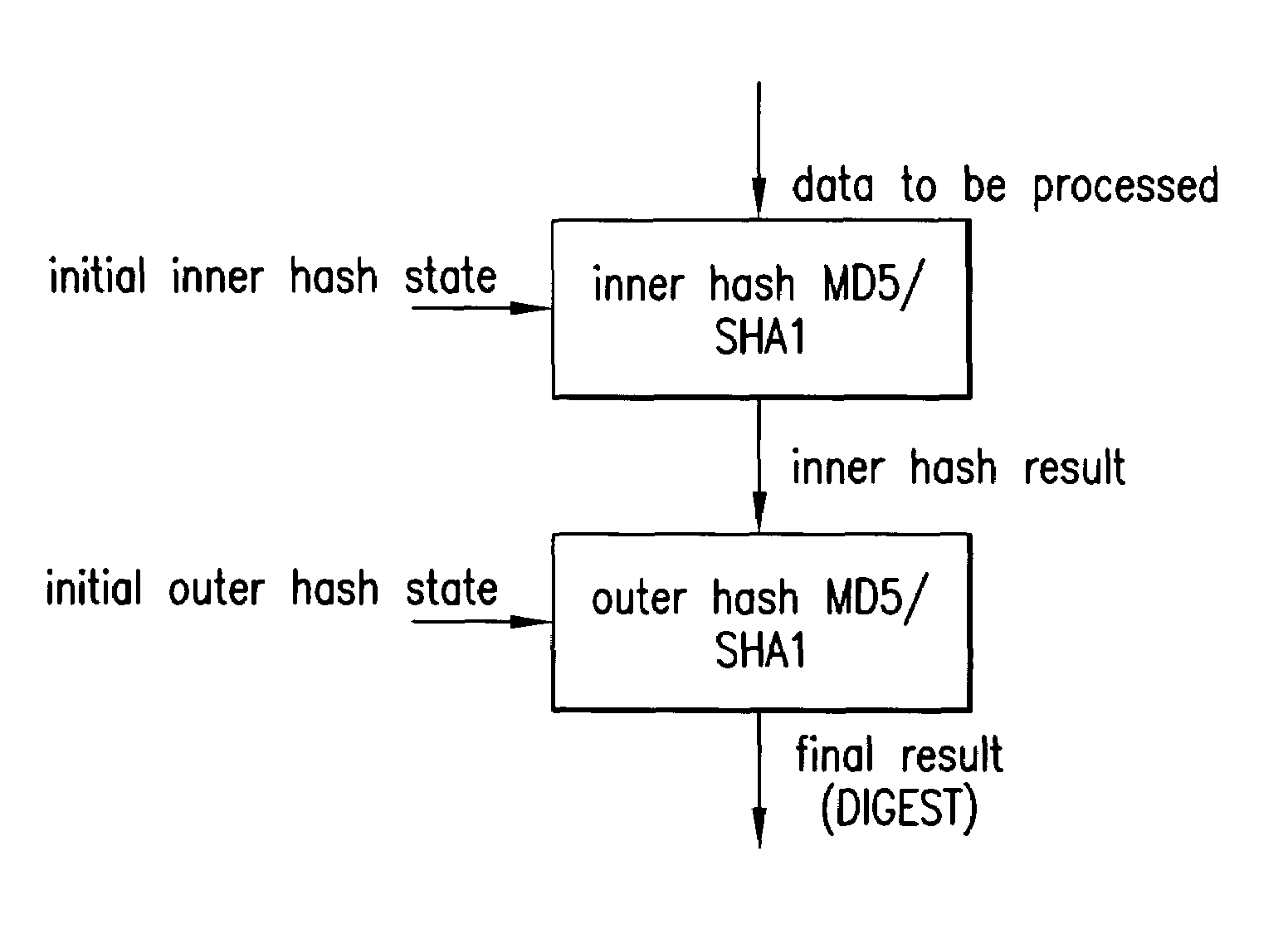
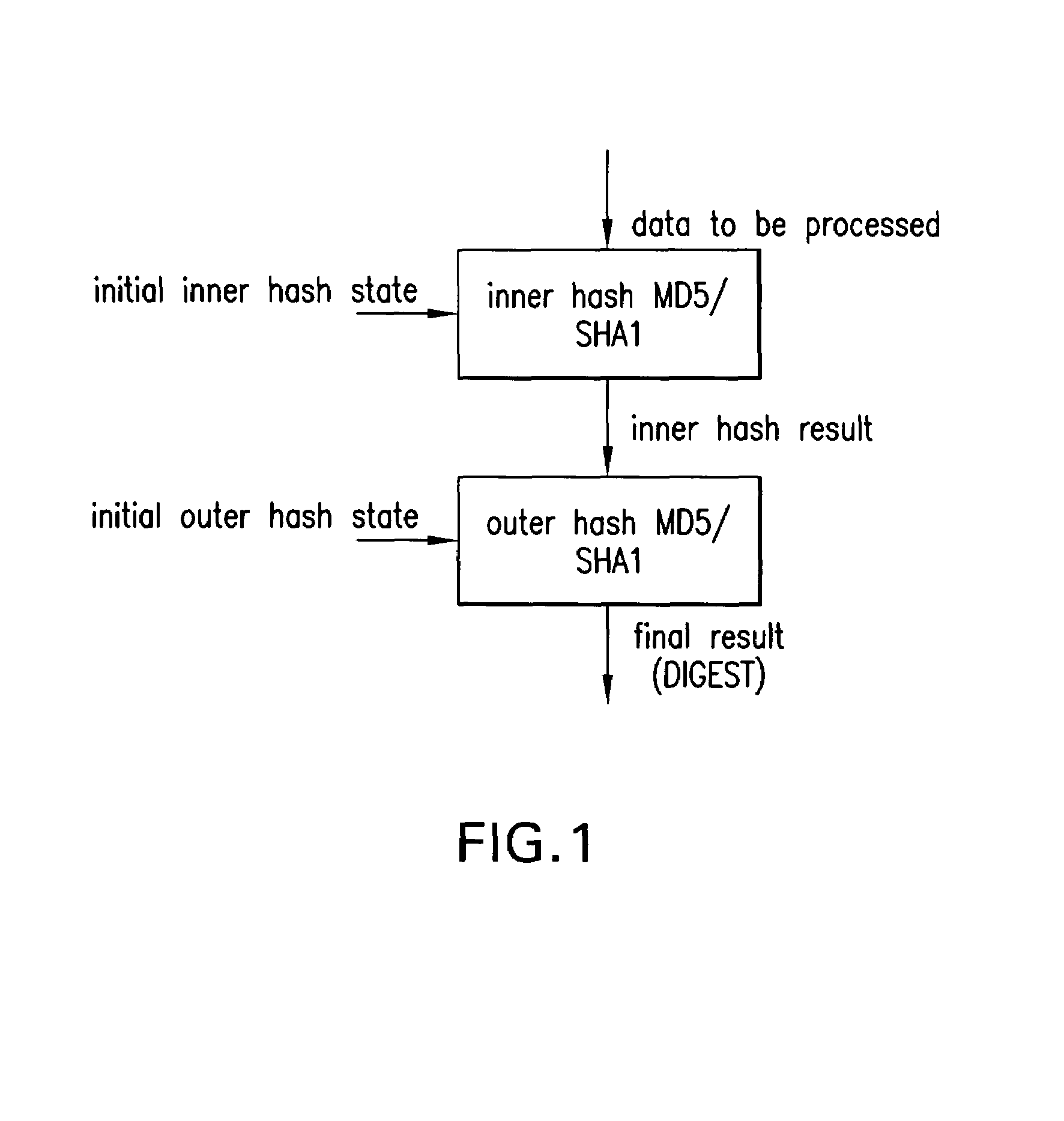
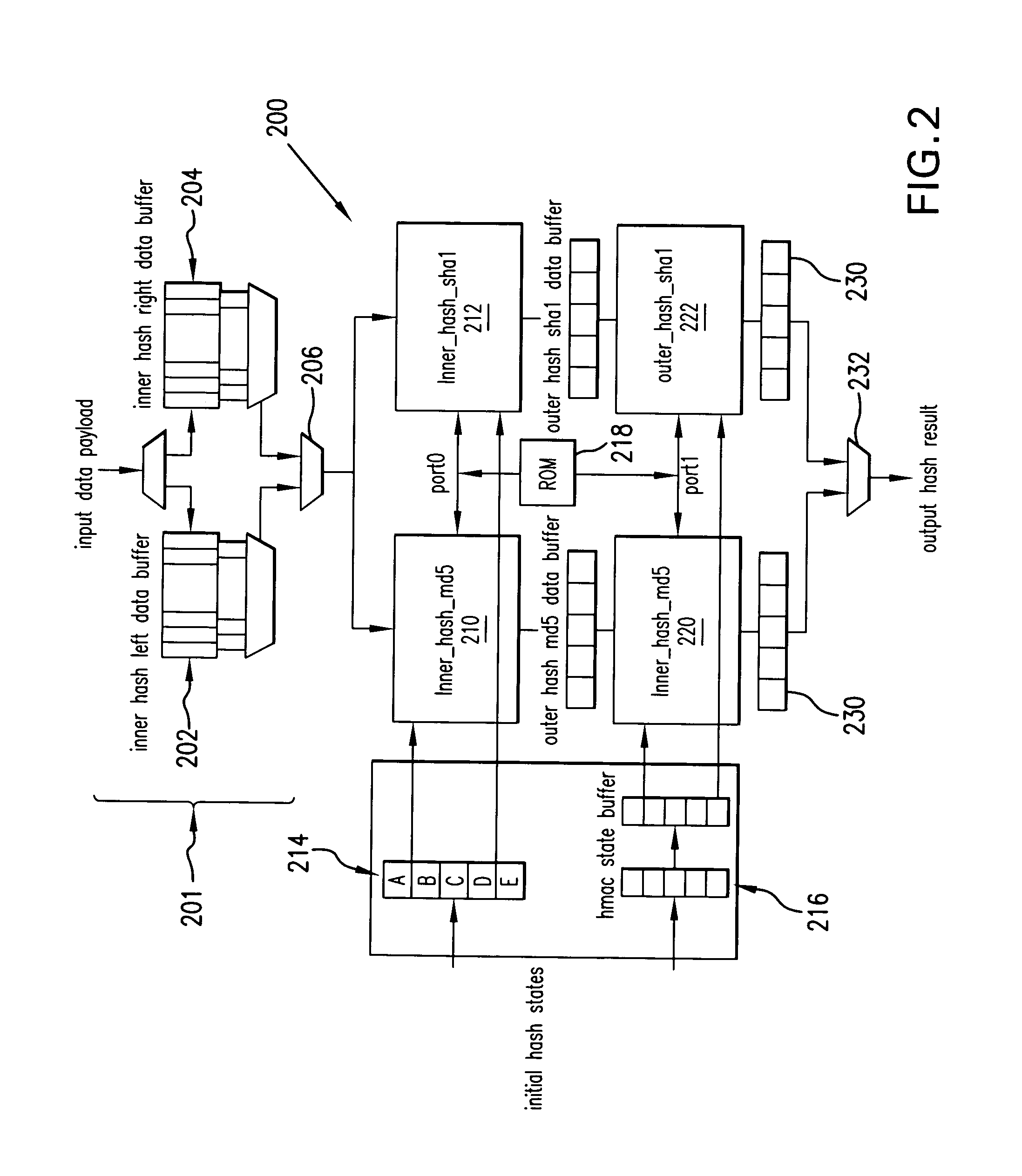
Provided is an architecture (hardware implementation) for an authentication engine to increase the speed at which multi-loop and / or multi-round authentication algorithms may be performed on data packets transmitted over a computer network. Authentication engines in accordance with the present invention apply a variety of techniques that may include, in various applications, collapsing two multi-round authentication algorithm (e.g., SHA1 or MD5 or variants) processing rounds into one; reducing operational overhead by scheduling the additions required by a multi-round authentication algorithm in such a matter as to reduce the overall critical timing path (“hiding the ads”); and, for a multi-loop (e.g., HMAC) variant of a multi-round authentication algorithm, pipelining the inner and outer loops. In one particular example of applying the invention in an authentication engine using the HMAC-SHA1 algorithm of the IPSec protocol, collapsing of the conventional 80 SHA1 rounds into 40 rounds, hiding the ads, and pipelining the inner and outer loops allows HMAC-SHA1 to be conducted in approximately the same time as conventional SHA1.
Owner:AVAGO TECH INT SALES PTE LTD
SERVER SIDE CONFIGURATION OF CLIENT IPSec LIFETIME SECURITY PARAMETERS
InactiveUS20040049585A1Multiple digital computer combinationsTransmissionSecurity associationClient-side
Abstract of the Disclosure A method of server side configuration of client IPSec security association parameters is compliant with the IPSec protocol and entails configuring the client IKE module to use default lifetimes and configuring the server IKE module to append a ResponderLifetimeNotify to a Quick Mode security association proposal proposed by the client IKE module. In this manner, a Quick Mode security association is established in the client computer IKE module in keeping with the lifetime values submitted by the server IKE module in the ResponderLifetimeNotify.
Owner:MICROSOFT TECH LICENSING LLC
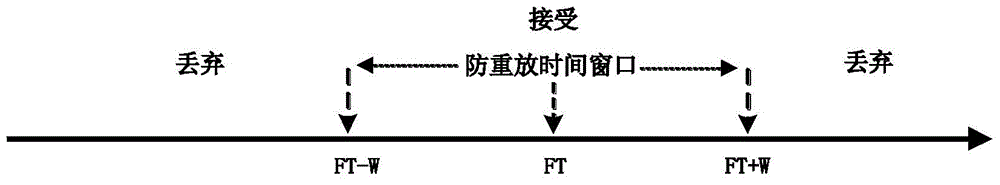
Anti-replaying method and device based on time
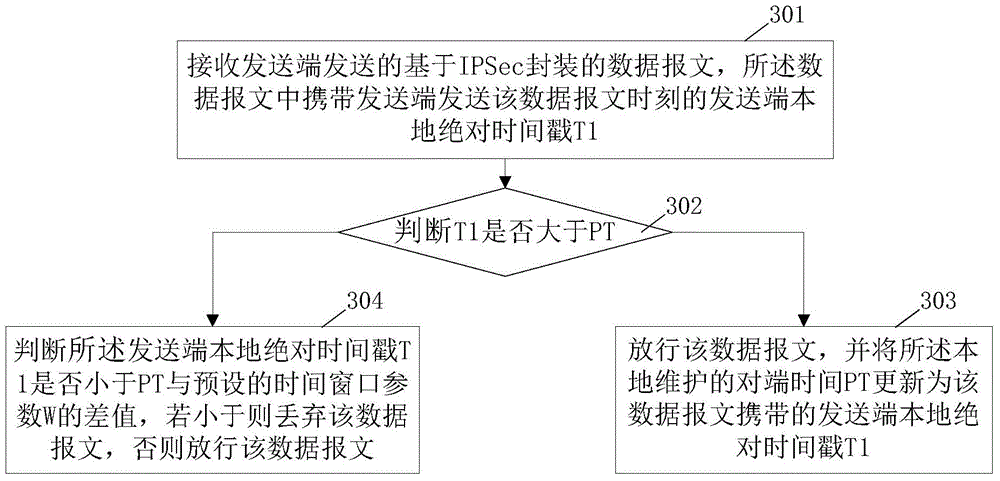
The invention discloses an anti-replaying method and device based on time. The anti-replaying method and device are based on an IPSec protocol, timestamps are carried in a field of an original serial number when IPSec encapsulation is carried out at a sending end, a receiving end determines whether messages are replayed messages or not by combining local time and an anti-replaying time window on the basis of the timestamps in the messages, and time synchronization does not need to be maintained by the sending end and the receiving end through a time synchronization protocol. The anti-replaying method and device based on the time can effectively avoid packet losses by mistake under the conditions that the packet sending speed of the sending end is high and the messages are sent in a multi-core parallel sending mode.
Owner:NEW H3C TECH CO LTD
Method and arrangement for providing security through network address translations using tunneling and compensations
InactiveUS20060256815A1Time-division multiplexNetworks interconnectionNetwork addressingNetwork address translation
This invention provides a method for providing network security services, such as those provided by the IPSEC protocol, through network address translation (NAT). The method is based on determining the transformations that occur on a packet and compensating for the transformations. Because only TCP and UDP protocols work through NATs, the IPSEC AH / ESP packets are encapsulated into UDP packets for transport. Special operations are performed to allow reliable communications in such environments.
Owner:SSH COMMUNICATIONS SECURITY
Reliable IKE message negotiation method, device and system thereof
InactiveCN101527729ABuild reliableError prevention/detection by using return channelData switching networksReliable transmissionIpsec protocol
The invention discloses a reliable IKE message negotiation method, a device and a system thereof, wherein, the method is applied to a system comprising first equipment and second equipment. The method comprises the following steps: a. the first equipment judges whether a response message from the second equipment is received within a preset cycle after the first equipment sends a last negotiation message to the second equipment; and b. if the response message from the second equipment is judged to be received within the preset cycle, the first equipment establishes a security alliance (SA) immediately. The method, the device and the system can guarantee reliable establishment of IKE SA and IPsec SA and reliable transmission of data message encrypted according to an IPsec Protocol when a network is in poor state, and the last message of message negotiation in a first stage or a second stage of the IKE misses or is delayed.
Owner:NEW H3C TECH CO LTD
Administration mechanism for standard way access control list (ACL) rule under internet protocol security (IPsec) protocol
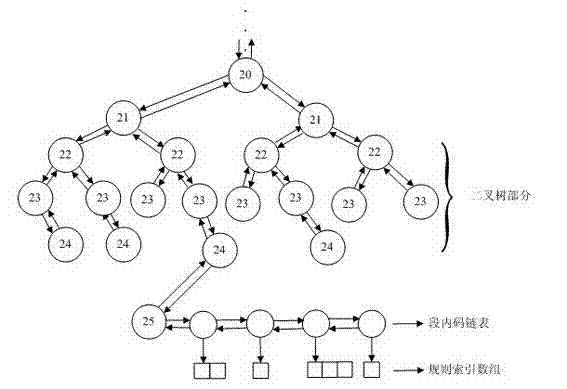
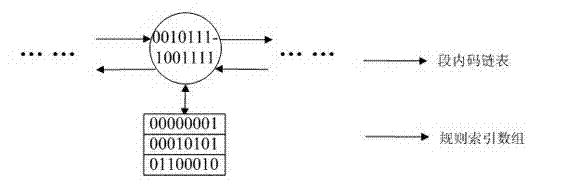
InactiveCN102811227AAvoid managementSimple structureTransmissionSpecial data processing applicationsArray data structureBinary tree
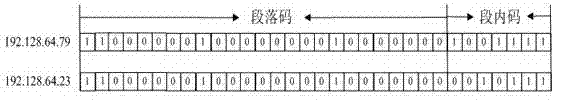
The invention discloses an administration mechanism for a standard way access control list (ACL) under an IPsec (internet protocol security) protocol, which belongs to the data communication field. The method is characterized in that address information in the standard way ACL rule is divided into a paragraph code and a segment code, a rule index of the standard way ACL rule is defined, administration of the standard way ACL rule is divided into two independent parts, i.e., source address range rule index and destination address range rule index, and the administration of the standard way ACL rule is performed in the same binary tree data structure. A data structure involved by the method comprises three parts including a binary tree, a segment code link table and a rule index digit group. The administration mechanism has the remarkable characteristics that for the standard way ACL rule with any address range, overlapped address range and multilevel address range, convenience and rapidness in operations of addition, searching and deletion can be realized, and the system expenditure is small.
Owner:CHONGQING UNIV
IPSec VPN method used for realizing quantum safety
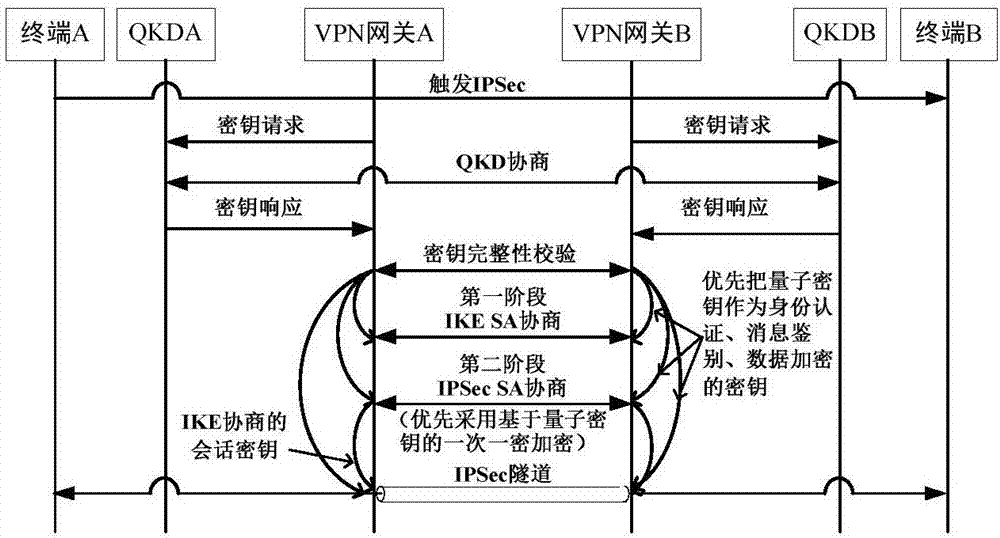
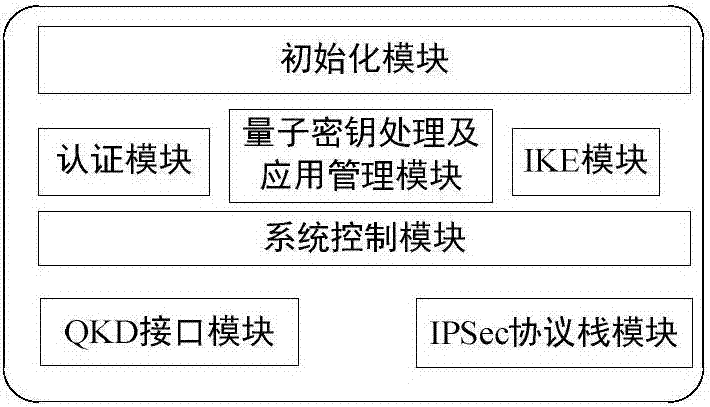
ActiveCN107453869AImproving Quantum SecurityImplement converged applicationsKey distribution for secure communicationOne-time padQuantum
The invention discloses an IPSec VPN method used for realizing quantum safety. The method is characterized by adding a safe interface of QKD in an IPSec VPN gateway; adding a quantum key access and application mechanism in an IPSec VPN safety strategy; adding a one-time pad encryption option based on a quantum key in an IPSec encryption component and adding a strategy which preferentially adopts the quantum key as a pre-shared key, and adopts a session key of a data encryption algorithm and a shared key of an HMAC algorithm; and realizing fusion application of the QKD, quantum encryption and an IPSec protocol, and increasing quantum safety of identity authentication, message authentication and data encryption of an IPSec VPN system. The safety of the system is high, application access is flexible, and a good application prospect is possessed in fields of party, government, industrial control, finance, military and the like.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
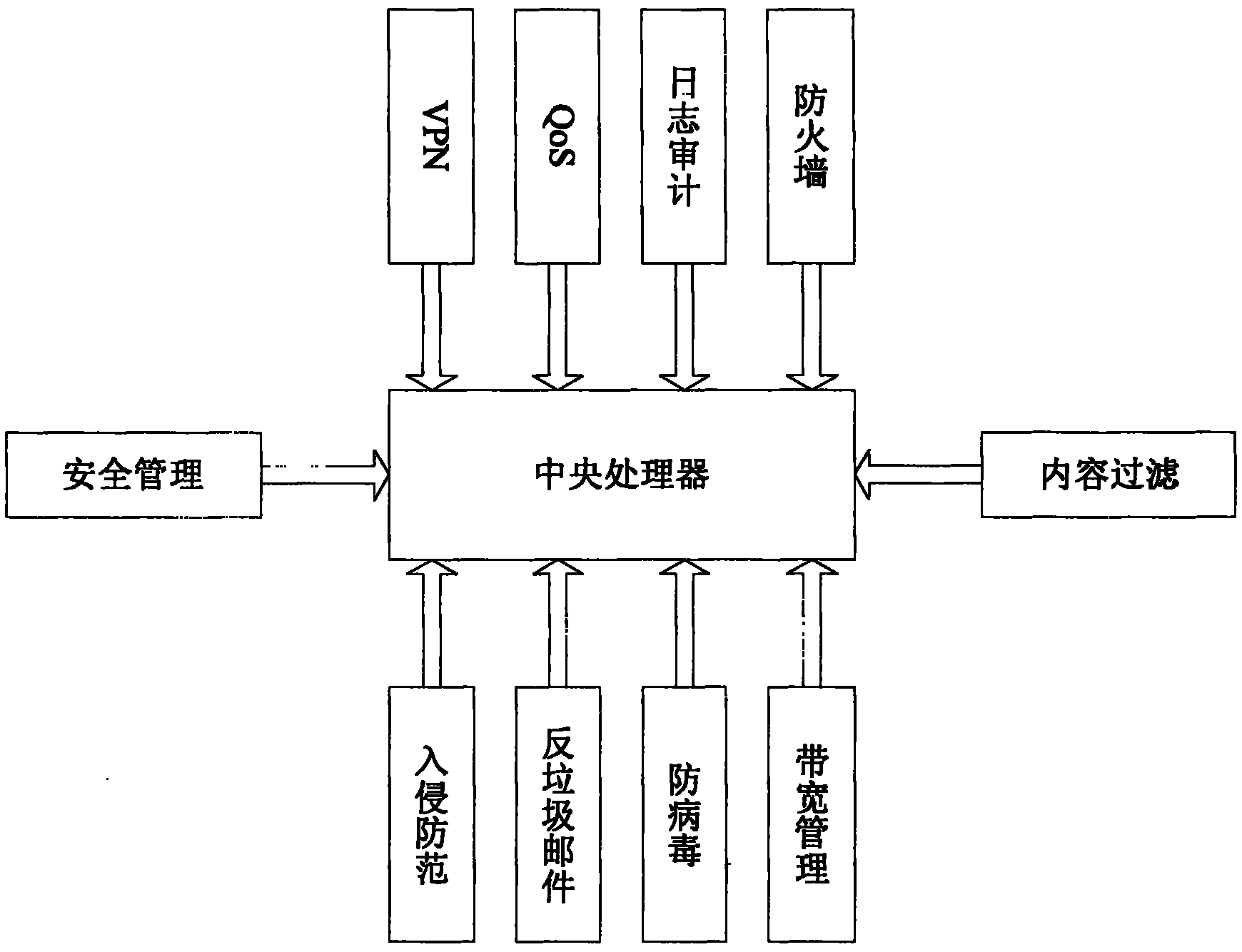
Home gateway
InactiveCN101969413AEasy to manageSave on high costsData switching by path configurationNetwork connectionsFiltrationPrivate network
The embodiment of the invention discloses a home gateway. The home gateway comprises a central processor, a virtual private network (VPN) module, a QoS module, a firewall function module, a log audit module and a network management module, wherein the central processor is used to communicate with each module and process the signals between the modules; the VPN module is used to adopt the standard IPSec protocol to set up a tunnel with another VPN gateway device supporting the standard IPSec protocol; the QoS module is used to realize the control function of the bandwidth flow, control the flow converted by a UTM physical interface and set up bandwidth policies to set the bandwidth limit and priority level of data messages; the firewall function module is used to identify and match the data messages from the angles of region, VLAN, address, user, connection and time and perform deep content inspection and filtration to various application layer protocols; the log audit module is used to provide a perfect log and alarm service function; and the network management module is used to realize network visualization and real-time monitoring and analysis. By implementing the invention, the deployment, management and maintenance costs of devices can be greatly reduced.
Owner:东莞环亚高科电子有限公司 +2
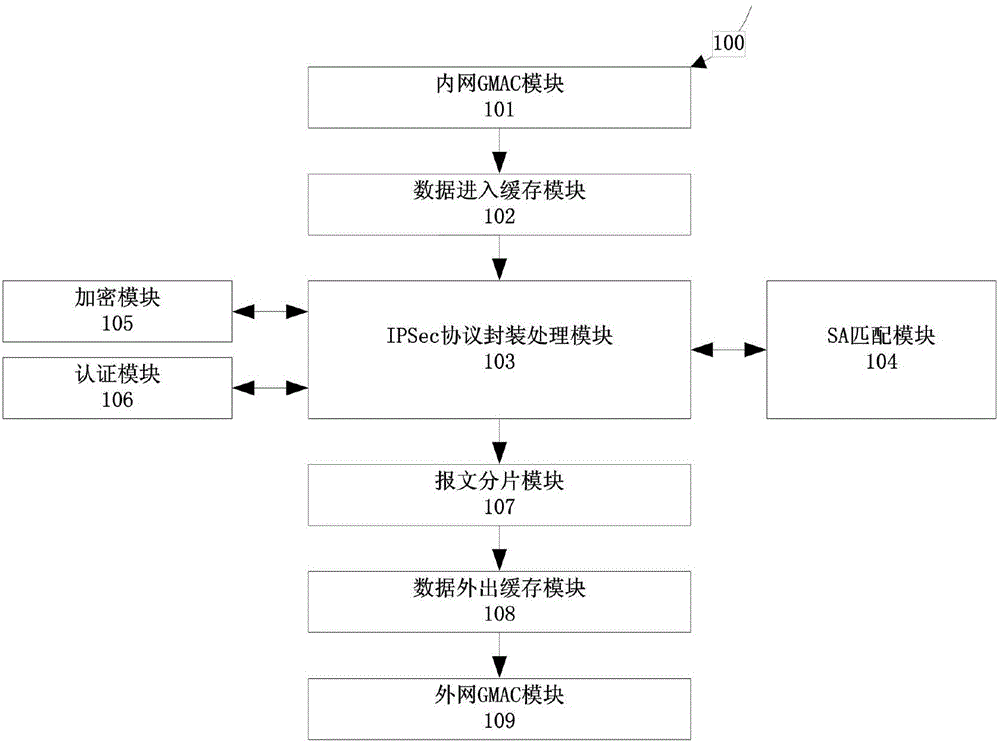
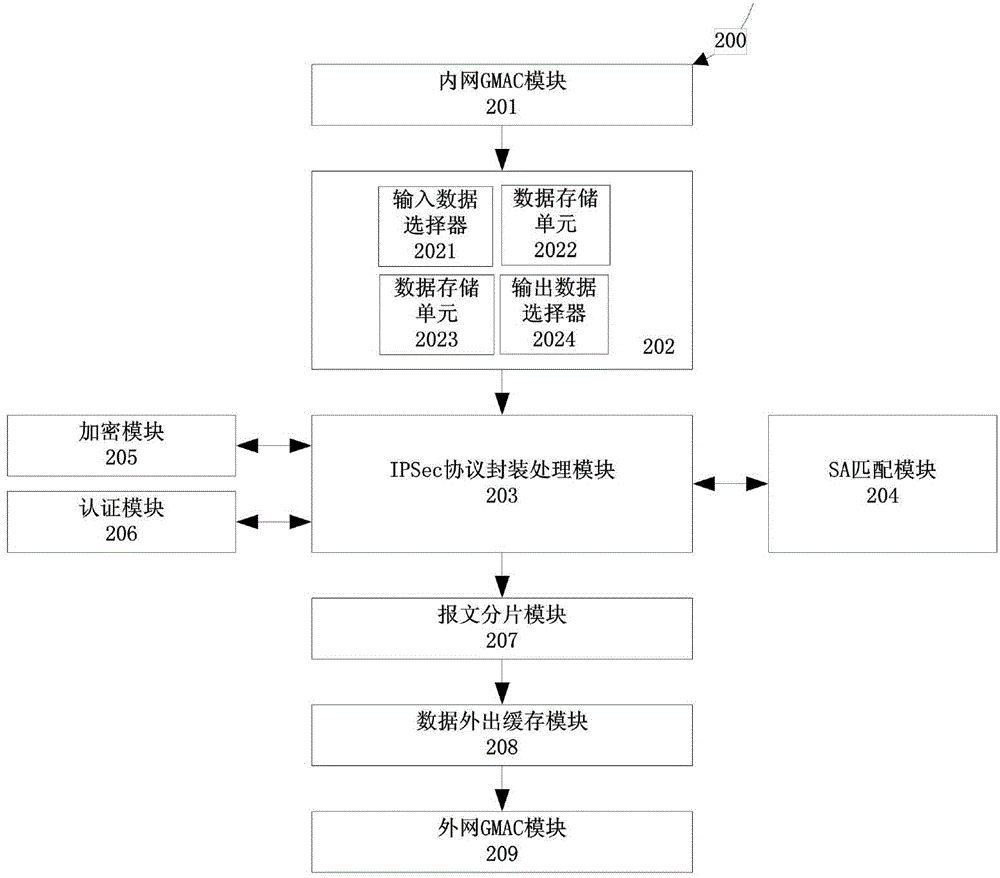
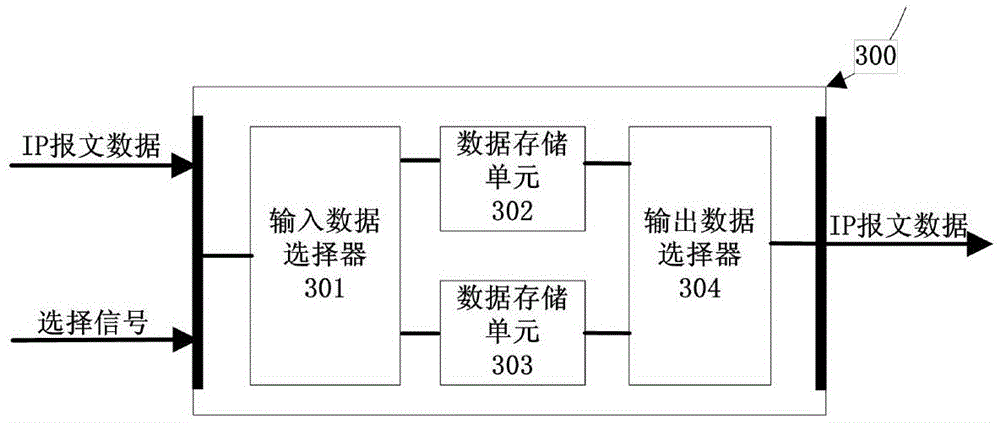
IPSec (Internet Protocol Security) protocol outgoing processing hardware implementation system under IPv6 (Internet Protocol version 6)
The invention provides an IPSec (Internet Protocol Security) protocol outgoing processing hardware implementation system under an IPv6 (Internet Protocol version 6). The IPSec protocol outgoing processing hardware implementation system comprises an internal network GMAC module, a data-in cache module, an IPSec protocol encapsulation processing module, an SA matching module, an encryption module, an authentication module, a message fragmentation module, a data-out cache module and an external network GMAC module. According to the IPSec protocol outgoing processing hardware implementation system under the IPv6, the IPSec protocol outgoing processing on the network layer IP (Internet Protocol) datagram under the IPv6 environment is implemented through hardware and accordingly the IP datagram source point identification and the data integrity and confidentiality are achieved, the software based IPSec protocol outgoing processing speed is effectively improved, and a CPU (Central Processing Unit) can be completely released out in the processing process.
Owner:SOUTHEAST UNIV
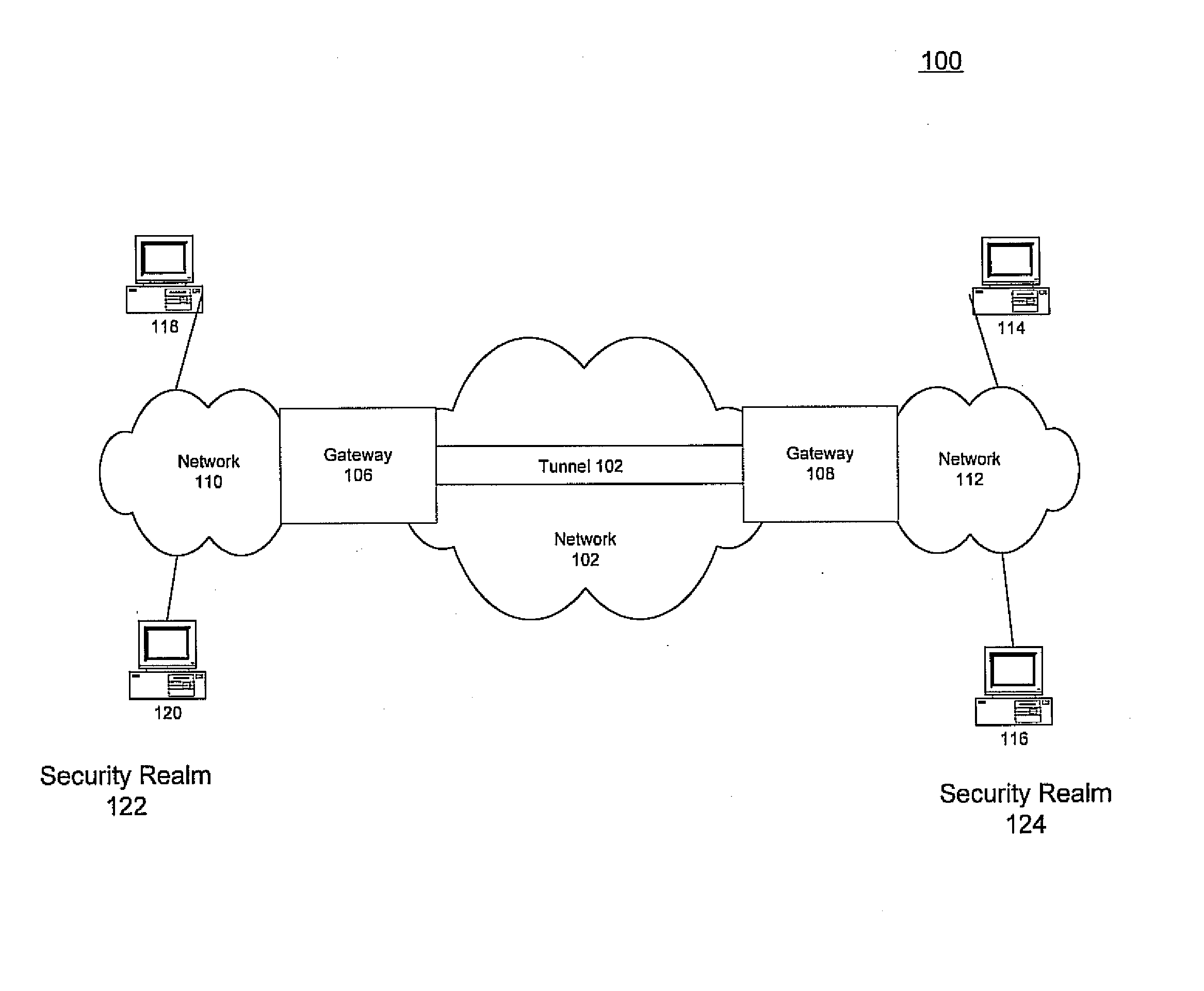
Method and system for sharing labeled information between different security realms
ActiveUS20080127297A1Key distribution for secure communicationUnauthorized memory use protectionTraffic capacitySecurity association
Embodiments of the present invention extend protection of network traffic between different security realms based on security labeling. In particular, embodiments of the present invention label provide for implicit labeling of traffic shared between different security realms. The traffic may be shared using IPsec protocols. A gateway inspects the IPsec traffic and identifies security associations (SAs) of the IPsec traffic. The gateway then determines a security label of the SA. Various access control policies may then be applied to the traffic based on its security label.
Owner:RED HAT
Path quality analysis method of encrypted network based on flow analysis
The invention discloses a path quality analysis method of the encrypted network based on flow analysis. The method comprises that A) a random intermediate node in the communication process of the encrypted network is selected as a measurement point, and the network flow is collected; B) an encrypted data packet received by the measurement point is analyzed to obtain source and target addresses of an IP header and an SPI of an IPsec header, and the source and target addresses of the IP header and the SPI of the IPsec header determine a session; and C) all data packets of the same session are analyzed, the packet loss number is calculated according to serial number information in the IPsec protocol headers of the data packets, and the packet loss index of the whole link is calculated finally. The method can obtain quality information of encrypted IPsec communication paths by analyzing the encrypted IPsec data packets.
Owner:COMP APPL RES INST CHINA ACAD OF ENG PHYSICS +1
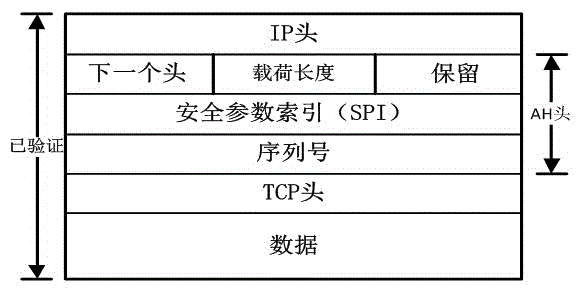
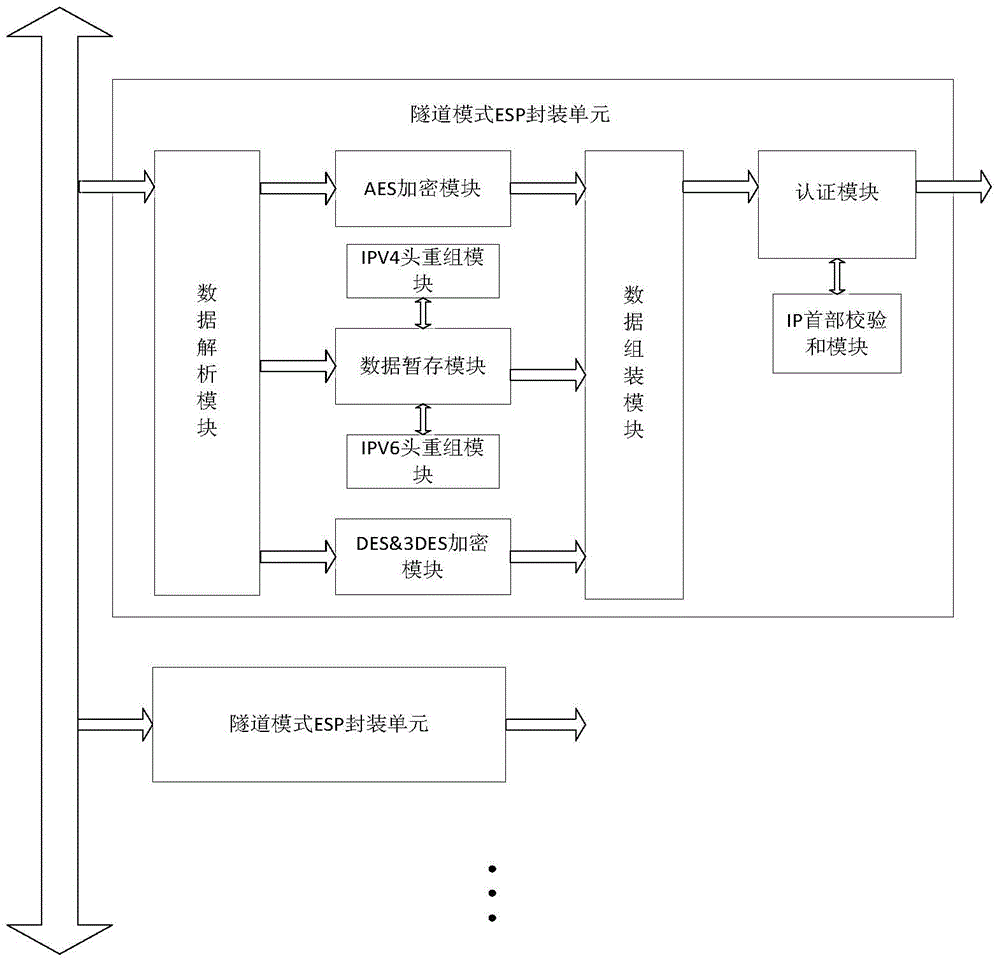
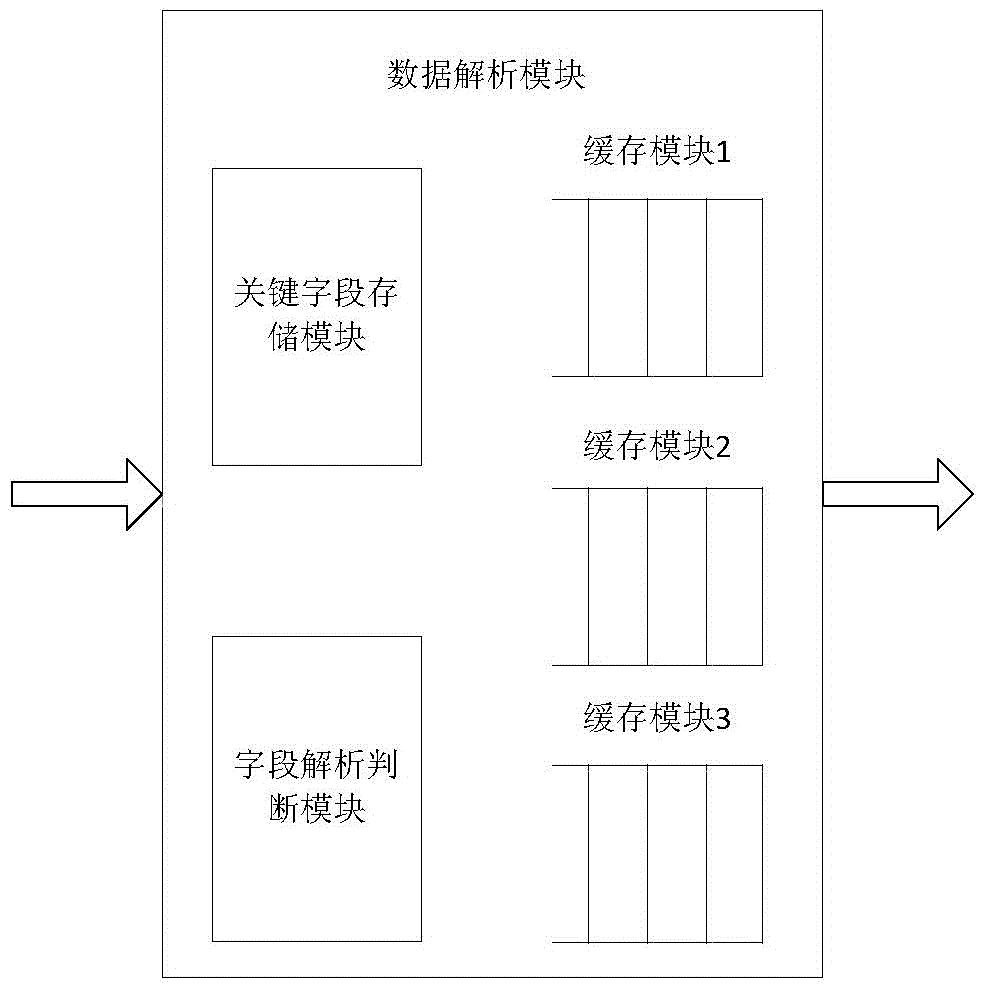
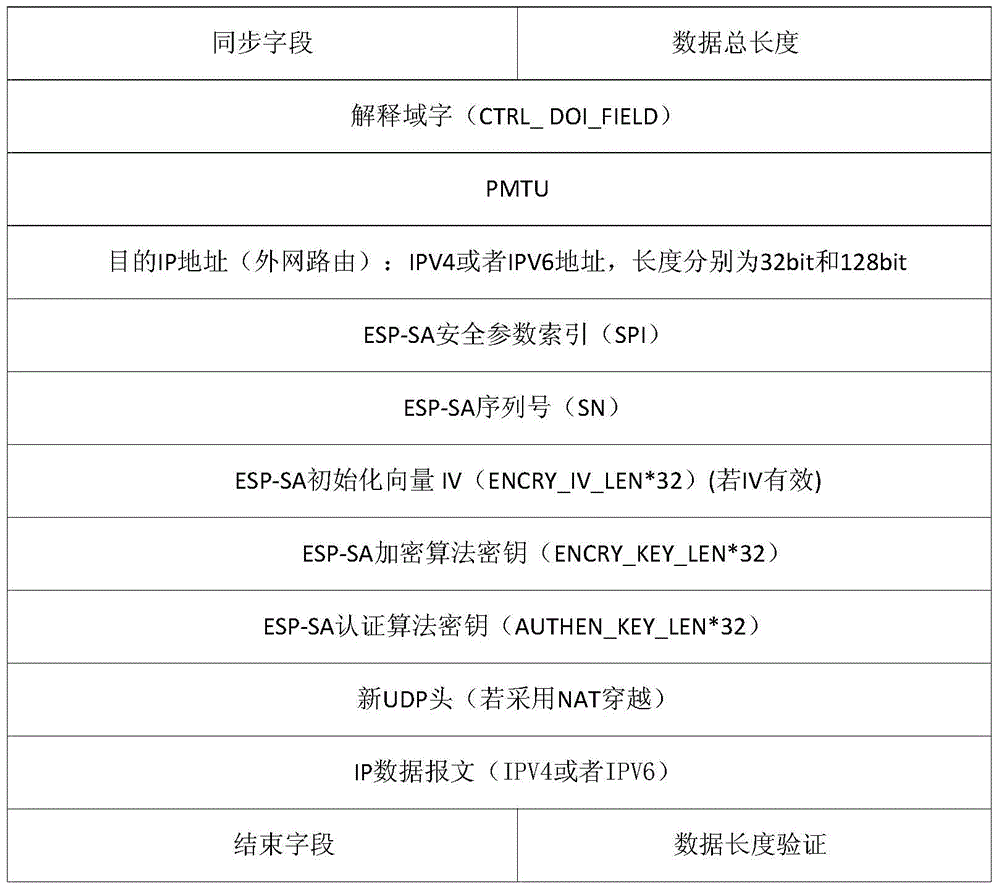
Tunnel-mode ESP (electronic stability program) hardware encapsulating device on basis of IPSEC (internet protocol security) protocols
InactiveCN104954222ASecure and Efficient Data EncapsulationFast packingEncryption apparatus with shift registers/memoriesNetworks interconnectionComputer hardwareOperation mode
The invention discloses a tunnel-mode ESP (electronic stability program) hardware encapsulating device on the basis of IPSEC (internet protocol security) protocols, and belongs to the field of network data security. The tunnel-mode ESP hardware encapsulating device comprises a plurality of tunnel-mode ESP encapsulating units. The tunnel-mode ESP encapsulating units are connected with one another by buses and work in ping-pong modes, and each tunnel-type ESP encapsulating unit comprises a data analysis module, a group of encryption modules, an IPV4 (internet protocol version 4) header regrouping module, an IPV6 (internet protocol version 6) regrouping module, a data temporary storage module, a data assembling module, an authentication module and an IP (internet protocol) header checksum module. Compared with the prior art, the tunnel-mode ESP hardware encapsulating device has the advantages that data packets to be encapsulated are segmented, formats of each segment of data are changed, accordingly, start bits or length verification fields are added to the data packets, and the data can be safely and efficiently encapsulated; a plurality of encapsulating modules are mounted, so that the ping-pong operation modes can be implemented, and the encapsulating speeds further can be increased.
Owner:SOUTHEAST UNIV
Method and system for securing a network utilizing IPsec and MACsec protocols
ActiveUS7853691B2Key distribution for secure communicationDigital data processing detailsEtherTypeProtocol for Carrying Authentication for Network Access
Aspects of a method and system for securing a network utilizing IPsec and MACsec protocols are provided. In one or more network nodes, aspects of the invention may enable conversion between Ethernet packets comprising payloads secured utilizing IPsec protocols and Ethernet packets secured utilizing MACsec protocols. For example, IPsec connections may be terminated at an ingress network node and IPsec connections may be regenerated at an egress network node. Packets secured utilizing MACsec protocols may be detected based on an Ethertype. Packets comprising payloads secured utilizing IPsec protocols may be detected based on a protocol field or a next header field. The conversion may be based on a data structure stored by and / or accessible to the network nodes. Aspects of the invention may enable securing data utilizing MACsec protocols when tunneling IPsec secured data through non-IPsec enabled nodes.
Owner:AVAGO TECH INT SALES PTE LTD
Method for processing distributed IPSec
InactiveCN1984131AAchieve high redundancyImprove reliabilityData switching networksExtensibilitySupporting system
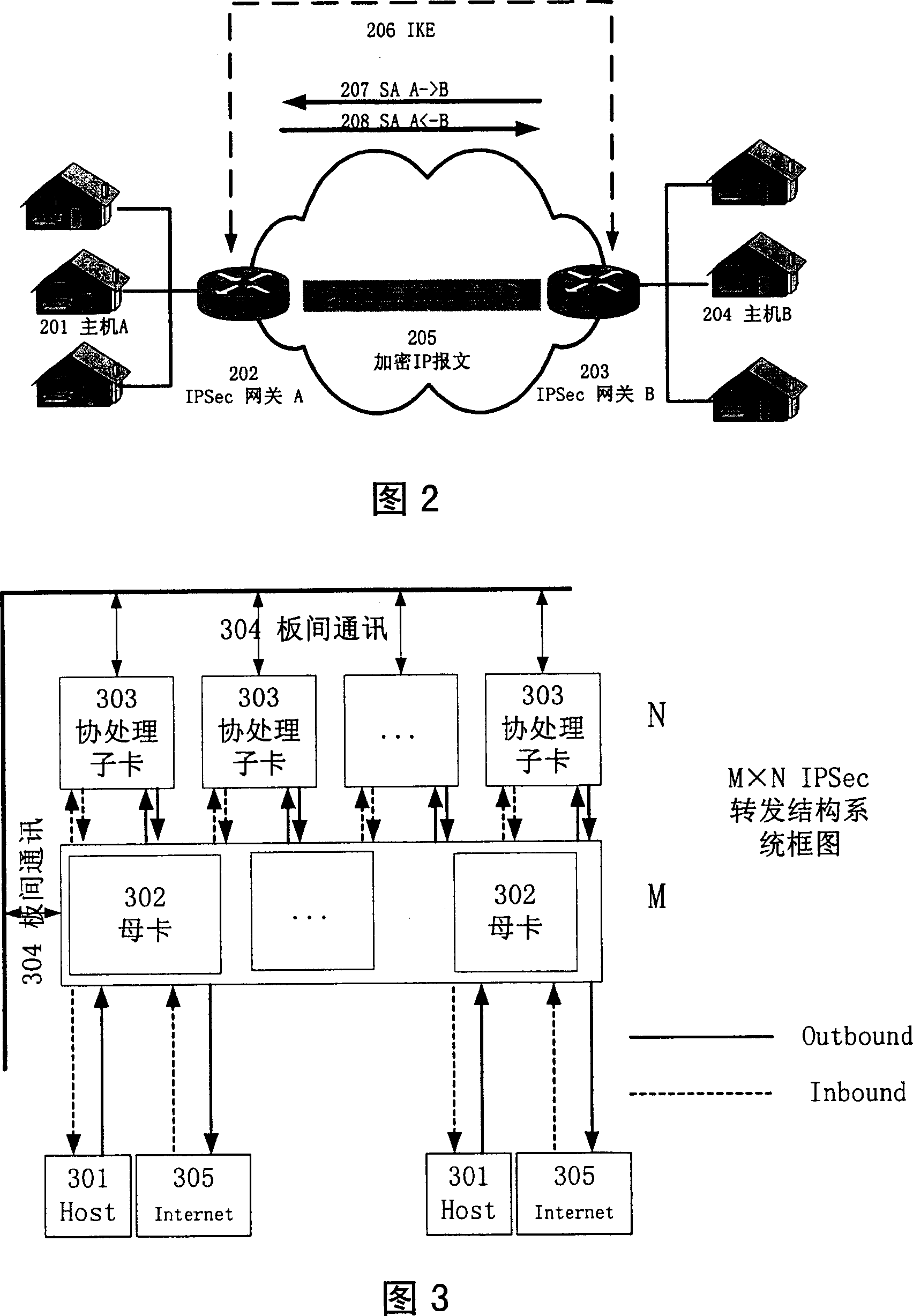
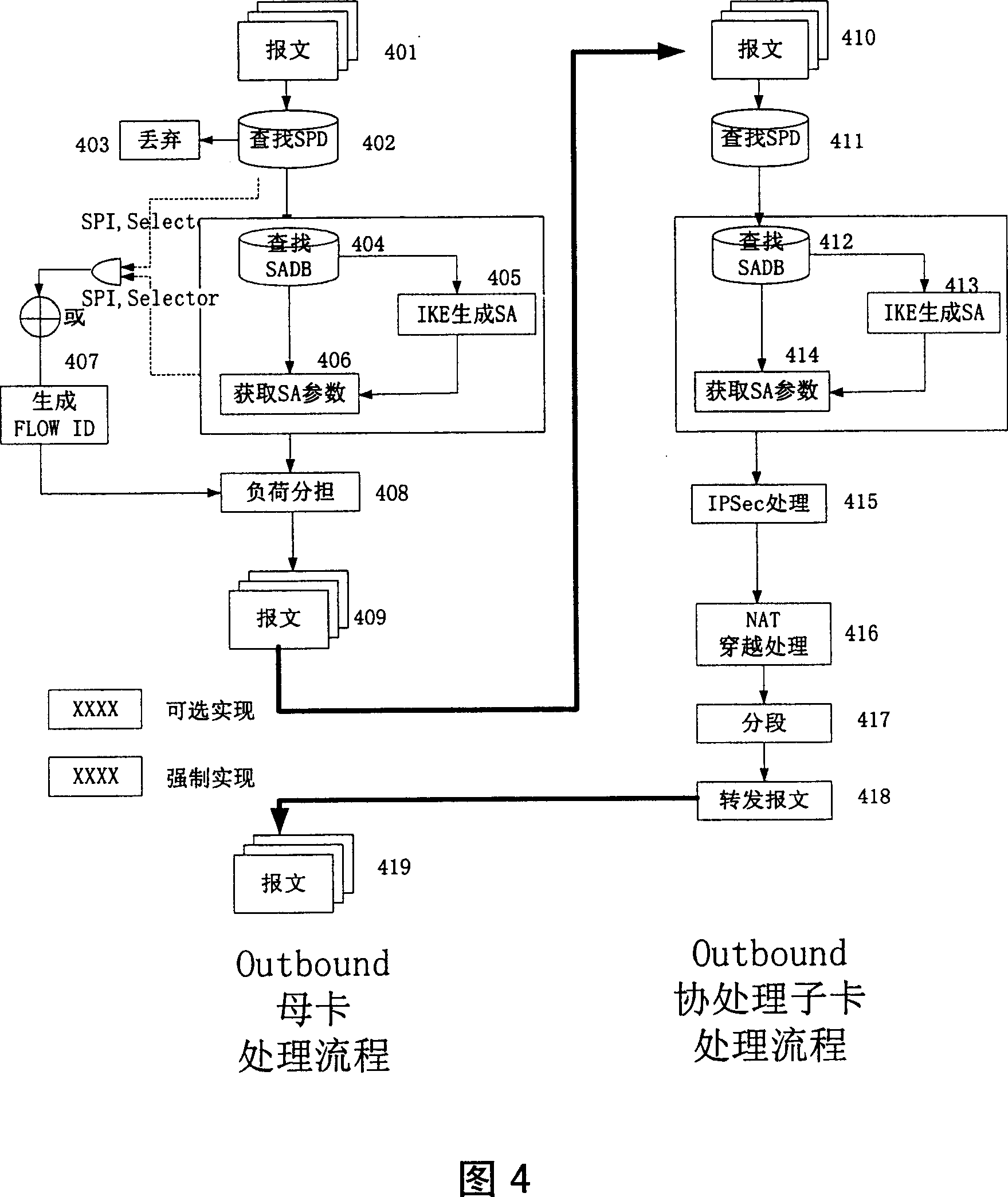
A distributed IPSec processing method includes the following steps: several mother cards generate Flow ID according to IP Packet, then it will have the load sharing operations according to Flow ID and transmit IPSec to many subcards; after subcard receives the transmitted original encrypted IP packet and IPSec packet, it will have an IPSec handling and transmit to mother cards; the mother cards and subcards have an interactive information through the board. This invention transplants IPSec protocol to M * N Distributed Computing Architecture which is composed with M mother cards and N subcards. Through mother cards and subcards' distributed computing, it achieves the high performance of IPSec transmitting. It realizes high performance of IPSec transmitting, high redundancy, high reliability. It supports system capacity smooth upgrading, it has good expansibility, simple physical logic, and it is easy to realize.
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
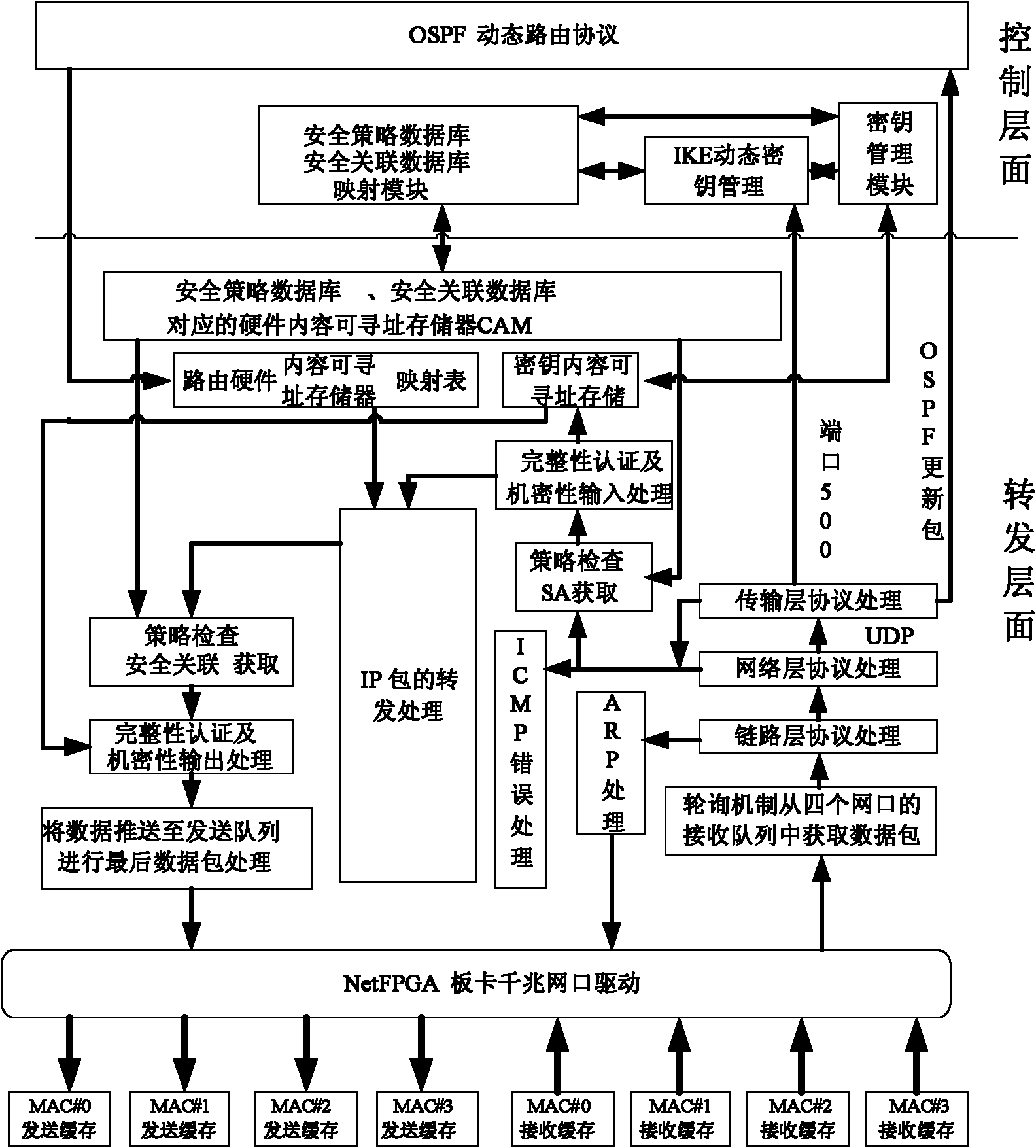
IPSecVPN (Internet Protocol Security Virtual Private Network) realizing system and method based on NetFPGA (Net Field Programmable Gate Array)
ActiveCN102065021AImprove processing speedRealize forwarding functionNetworks interconnectionData streamControl layer
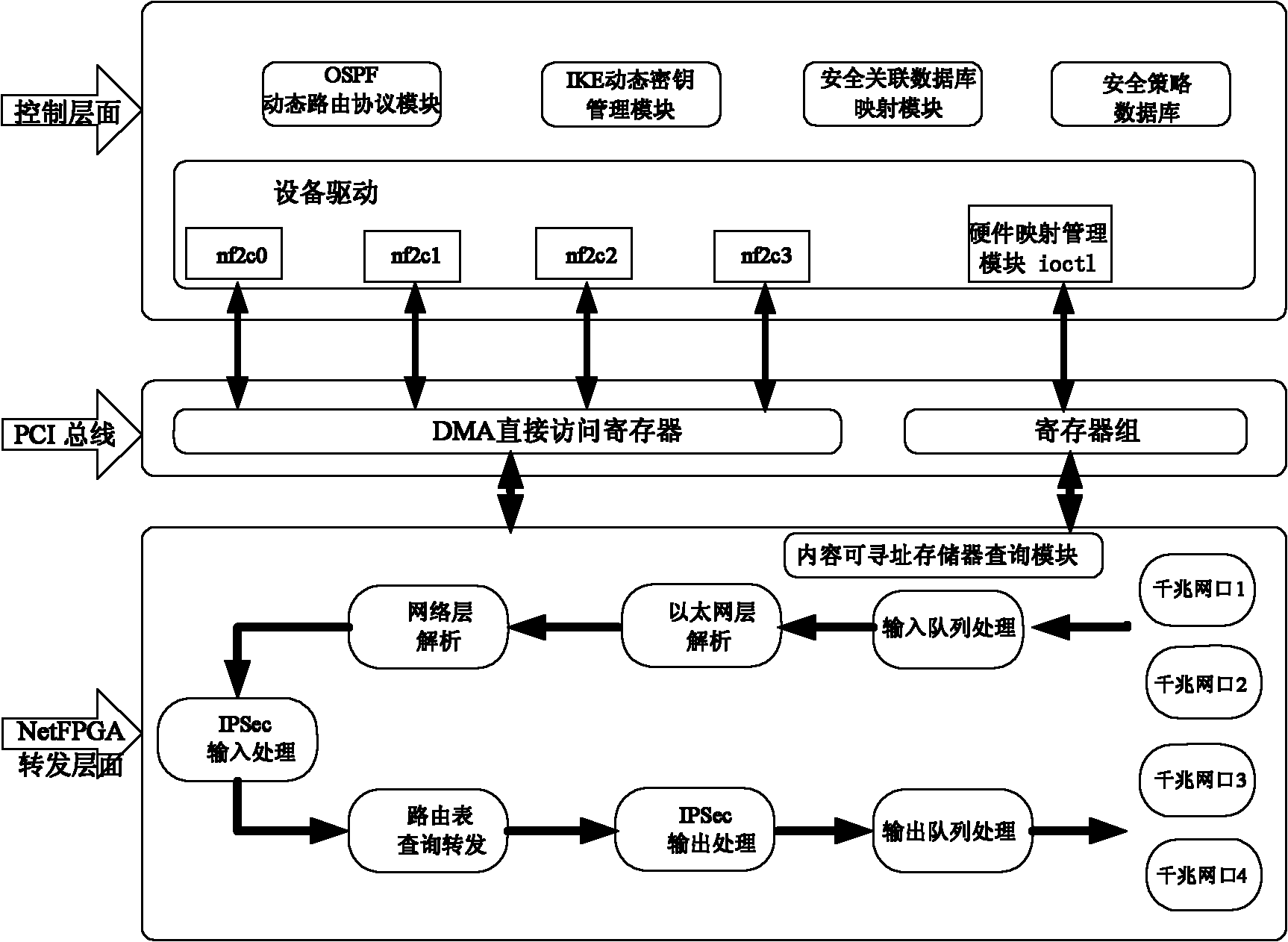
The invention relates an IPSec VPN (Internet Protocol Security Virtual Private Network) realizing system and method based on a NetFPGA (Net Field Programmable Gate Array), wherein a control layer of a router is additively provided with an IKE (Internet Key Exchange) module, a security relation database mapping module and a security policy database, and a key management module is used for dynamically managing the key, the security relation and the security policy; and a forward layer is additionally provided with two independently designed IPSec input and output process modules in the originalNetFPGA standard router architecture by sufficiently utilizing the modularization reusable idea of a NetPGA development board. The scheme of the invention can realize the route forward function of the data flow in a hardware manner, and can also realize the great mass of calculation functions required by the IPSecVPN in a hardware manner, such as safe detaching / packing load and completeness authentication; in addition, the invention can effectively make a compromise on the data flow forward performance and the IPSec protocol processing performance.
Owner:北京地平线轨道技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com