Method for processing distributed IPSec
A distributed and co-processing technology, applied in the field of Internet security, can solve the problems of poor scalability, complex implementation, and low processing capacity, and achieve the effect of simple physical logic, smooth capacity upgrade, and good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
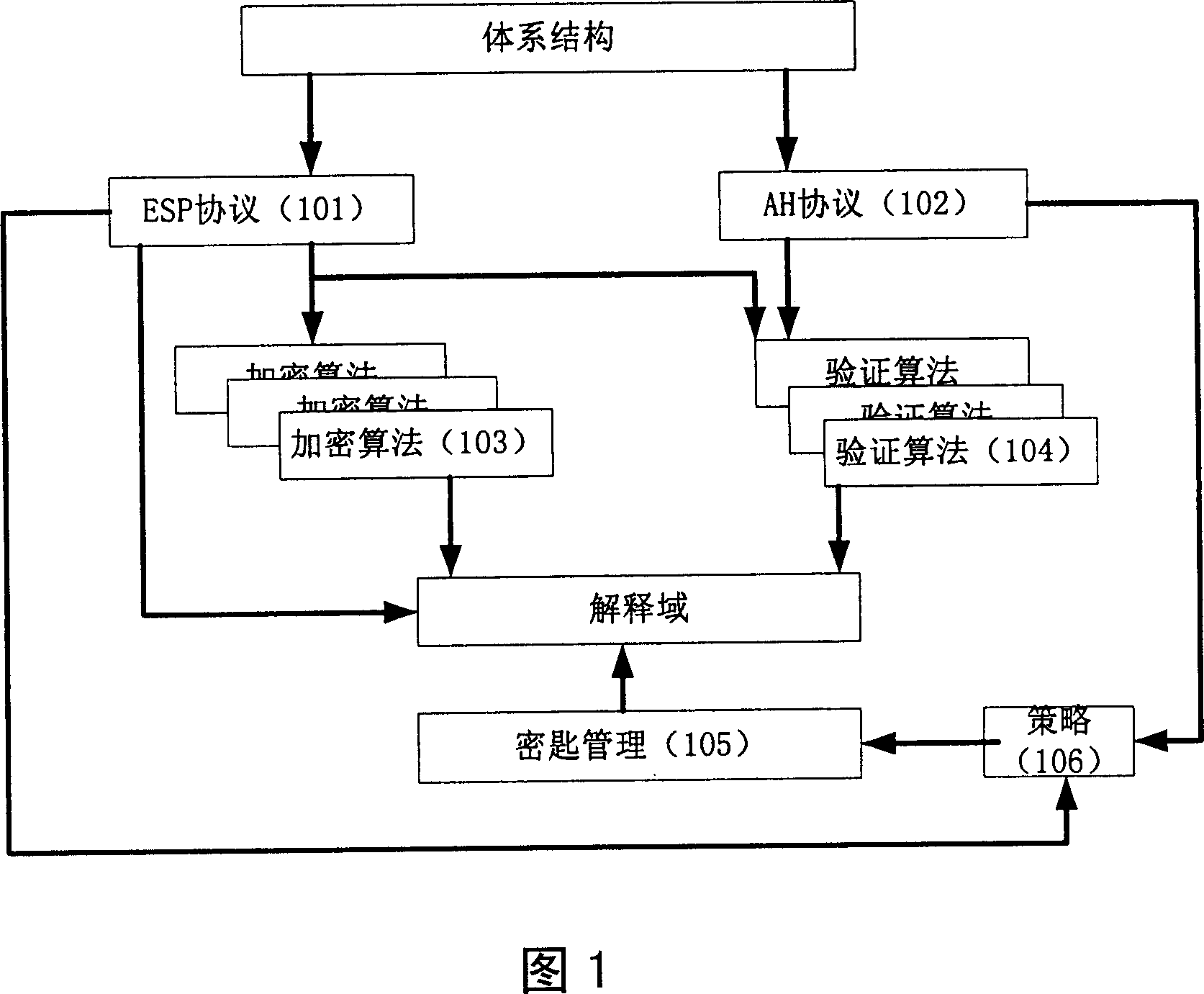
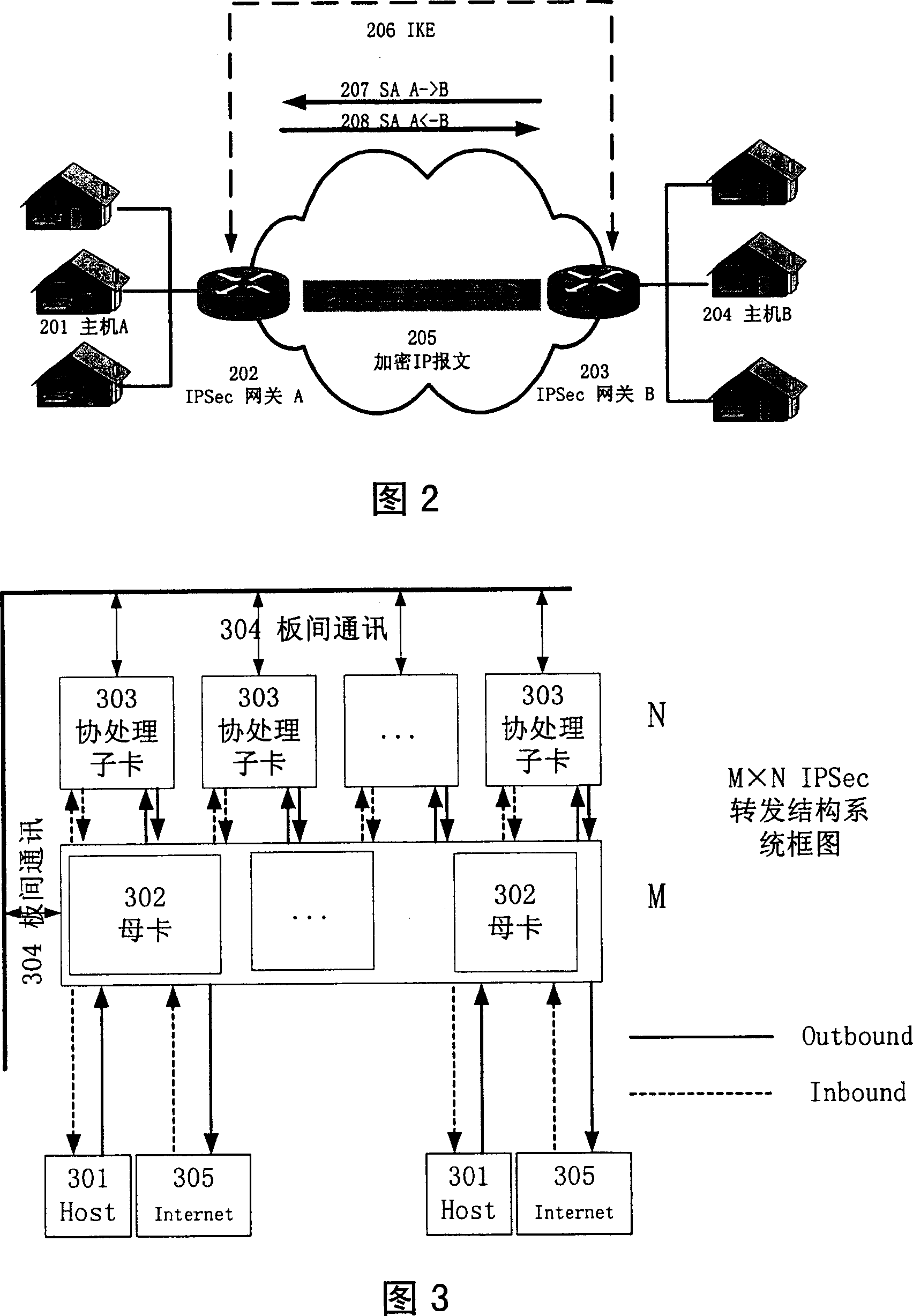
[0024] The present invention transplants the IPSec protocol to an M×N distributed computing structure composed of M mother cards and N co-processing sub-cards. The main card and co-processing sub-cards jointly complete IPSec forwarding through distributed computing. The design method is as follows :
[0025] 1. The main card and the co-processing daughter card jointly complete the IPSec forwarding task.
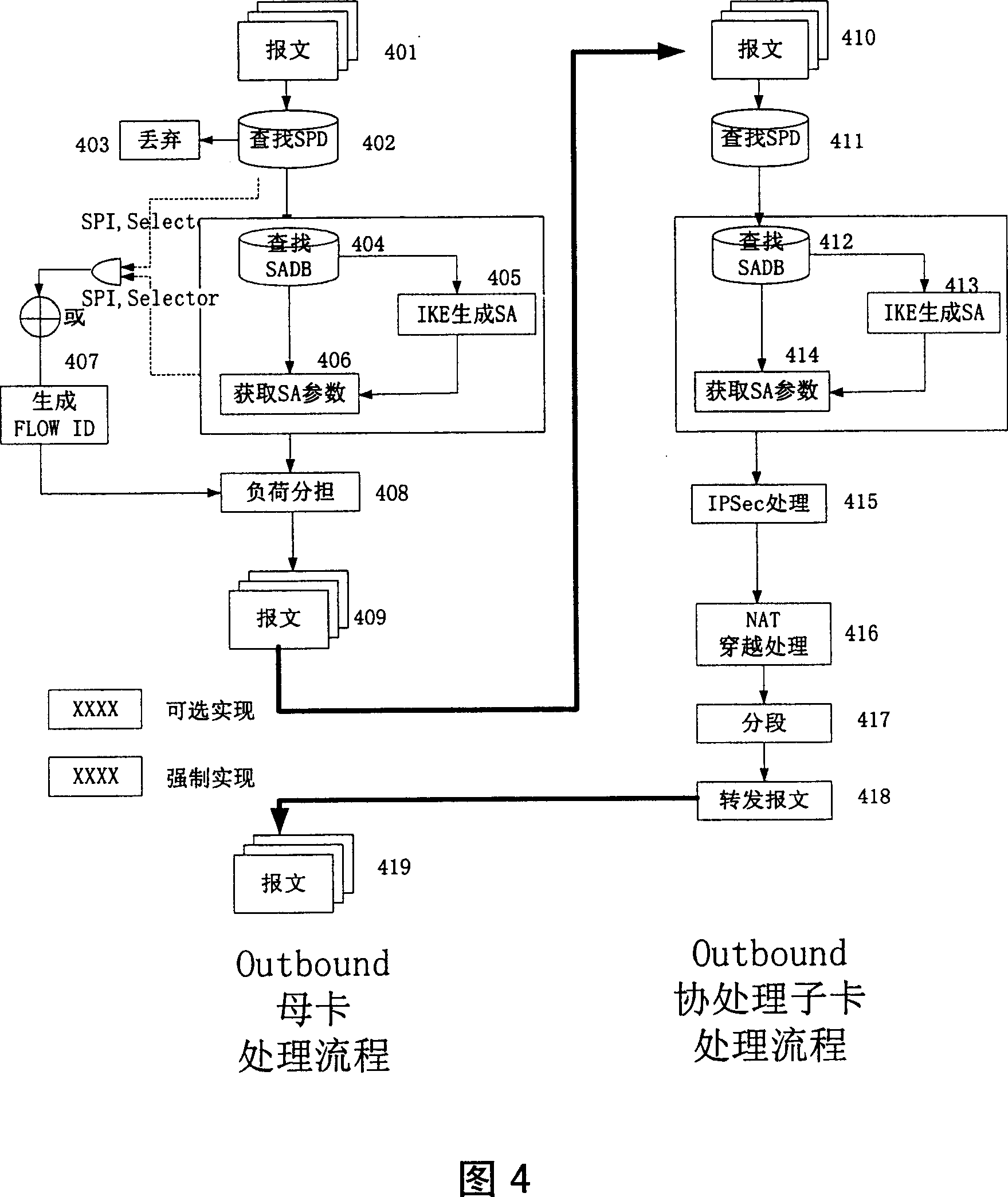
[0026] 2. The IPSec message processing process in the master card is: receive the message flow of the IPSec protocol stack inbound and outbound directions; analyze the message header, search the SPD policy database, classify the message for the flow, and assign a unique flow label; According to the flow label, the load sharing calculation is performed, and the message flow is shared to the respective co-processing sub-cards; after the co-processing sub-cards process the messages, they will be summarized by the main card and output.
[0027] 3. The co-processing sub-card IPSe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com