Anti-replaying method and device based on time
An anti-replay and time technology, applied in electrical components, transmission systems, etc., can solve problems such as message packet loss, and achieve the effect of avoiding false packet loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The technical solutions of the present invention will be described in detail below with reference to the accompanying drawings.
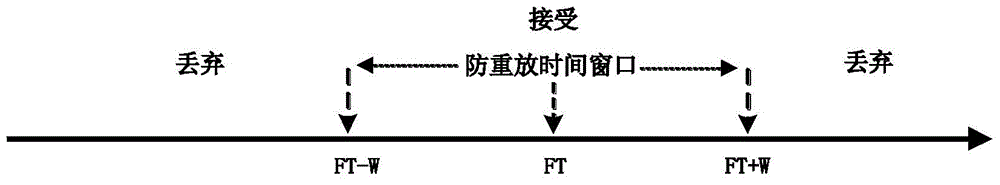
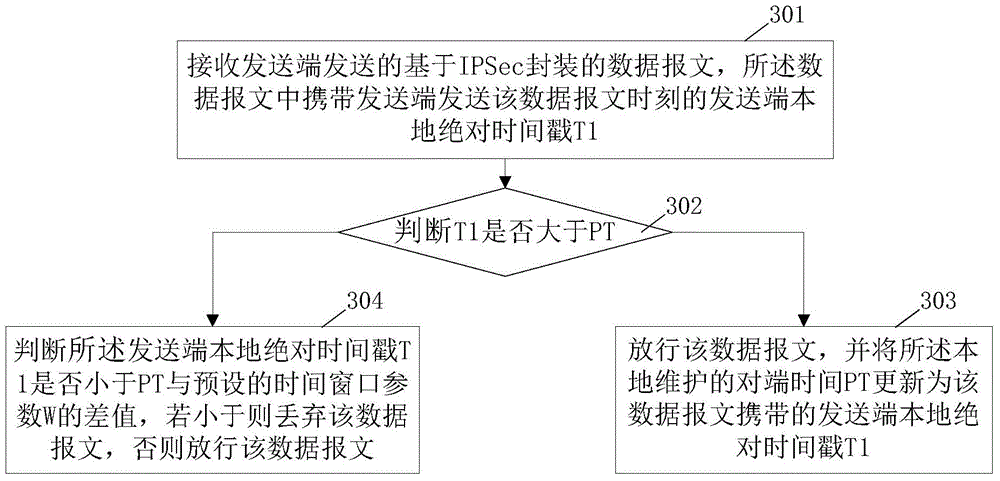
[0043] figure 1 A flow chart of the steps of a time-based anti-replay method provided by an embodiment of the present invention. The steps in this embodiment are described with the network device at the receiving end as the main body of the steps, and the sending end and the receiving end are transmitted through an IPsec tunnel. data message, the method includes:
[0044] Step 101, receiving the data message based on IPSec encapsulation sent by the sending end, recording the local absolute time stamp T2 of the receiving end at the time when the data message is received, and carrying the time stamp of the time when the data message is sent by the sending end in the data message The sender's local absolute timestamp T1;
[0045]This embodiment uses the AH header of the IPSec protocol and / or the sequence number (Sequence Number) field in the E...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com