Reliable IKE message negotiation method, device and system thereof
A packet negotiation and device technology, applied in the communication field, can solve the problems of packet loss, the responder device cannot receive, and IKESA or IPsecSA cannot be established normally.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
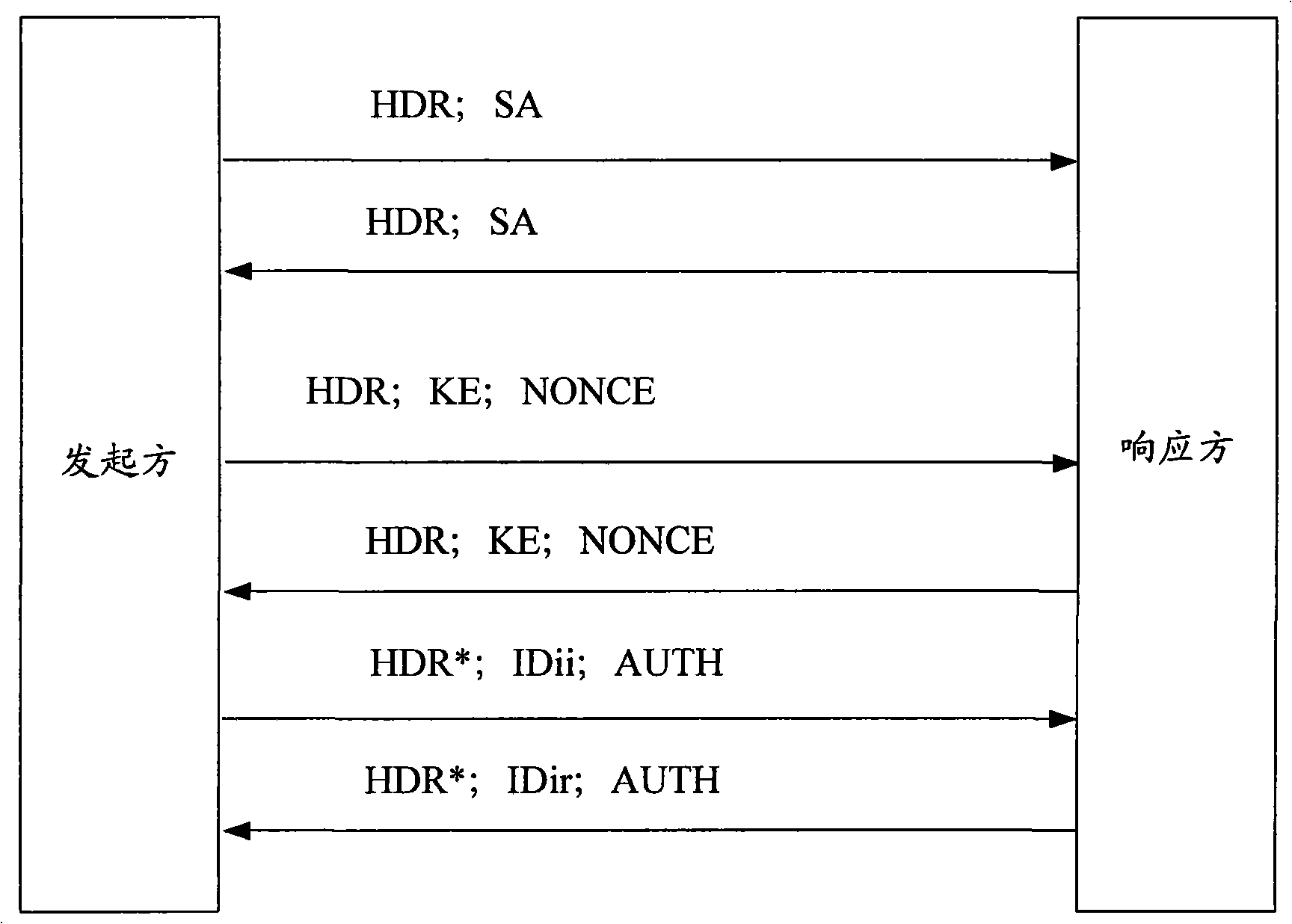
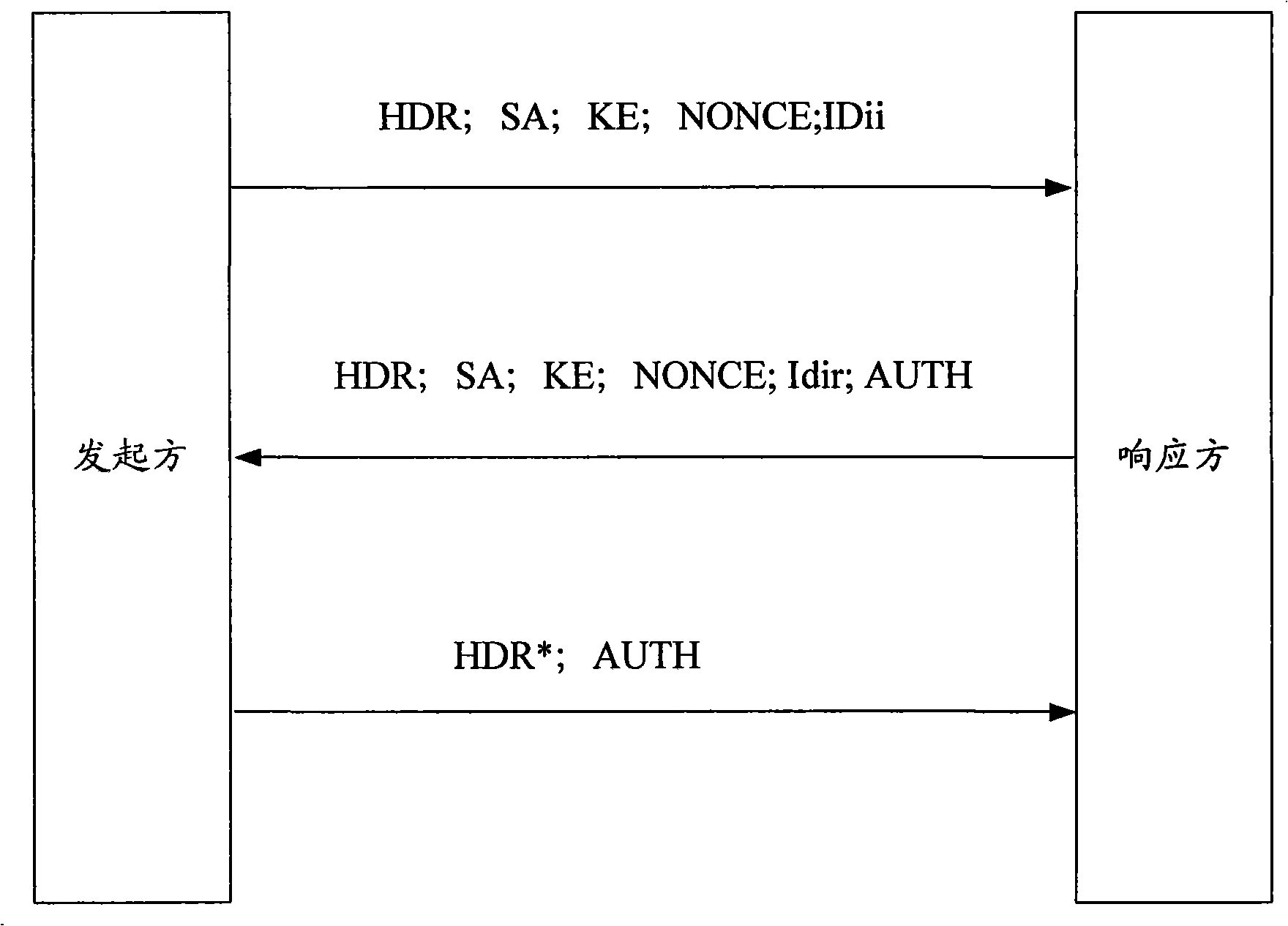
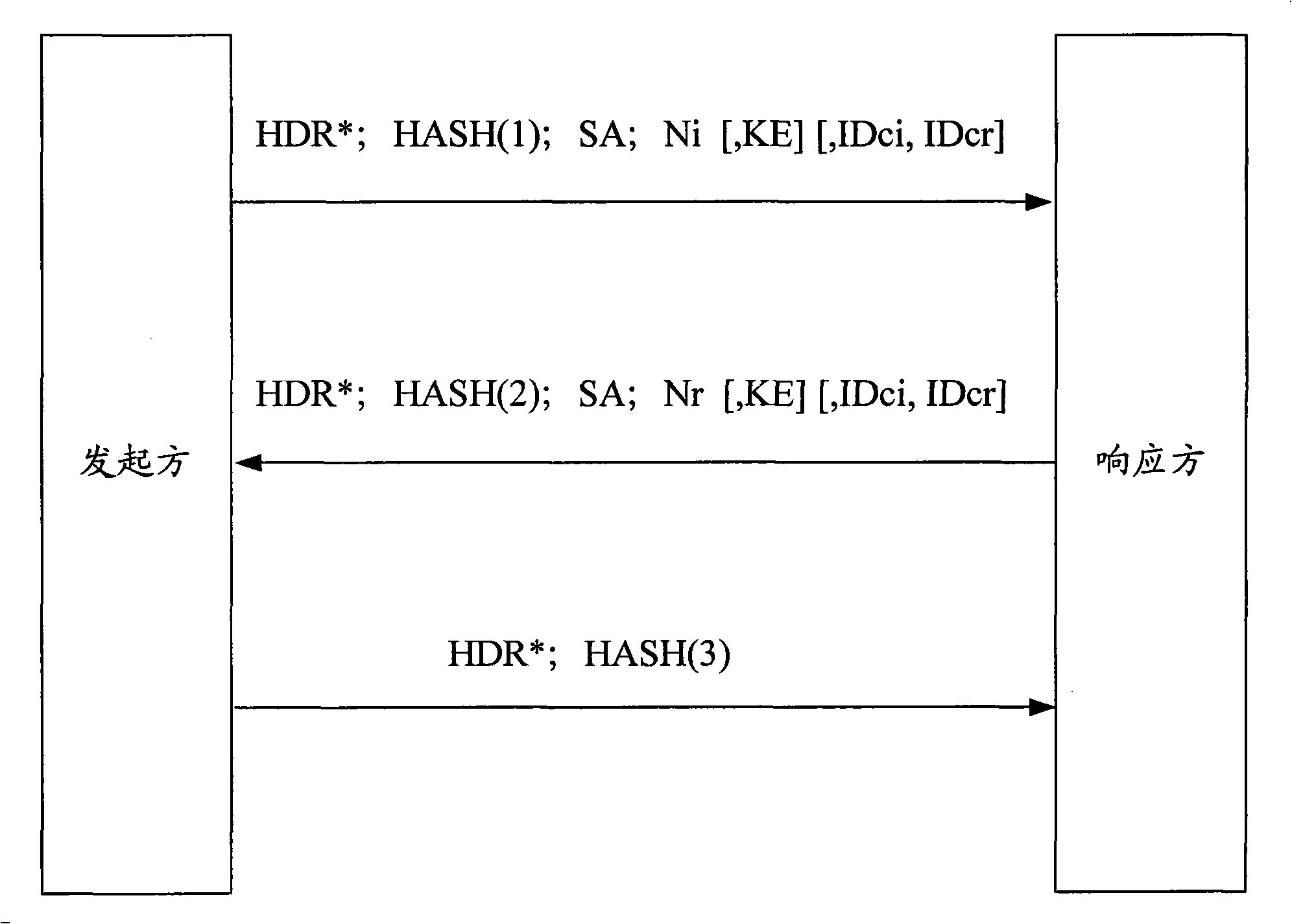
[0091] The core content of the present invention is that, during the process of IKE message negotiation, when the responder device receives the last negotiation message sent by the initiator device, the responder device returns an ACK (ACKnowledge, confirmation) message to the initiator device , to inform the initiator device that the responder device has received the last negotiation message sent by the initiator device, and the initiator device establishes the initiator device SA after receiving the ACK message. In the present invention, before the reliable message negotiation is performed in the first stage, the initiator device and the responder device perform capability negotiation to determine that both parties have the ability to carry out subsequent reliable IKE negotiation. The technical scheme of the present invention effectively protects the one-way IKE or IPsec SA caused by the loss or delayed sending of the last negotiation message during the establishment process ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com