Method and system for extended use of quantum keys in IPSec VPN (internet protocol security-virtual private network)
A quantum key and secret key technology, applied in the field of virtual private network, can solve the problems of complex processing process and difficult to effectively improve the update frequency of IPSecSA session key
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
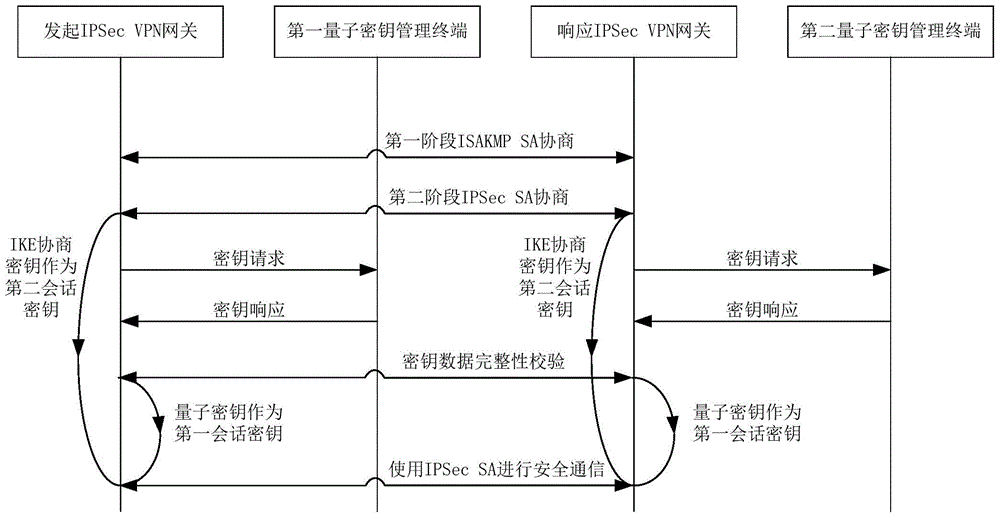
[0081] see image 3 , an embodiment of the present invention provides a method for supporting a quantum key as a session key in an IPSec VPN, which includes initiating an IPSec VPN gateway, responding to an IPSec VPN gateway, a first quantum key management terminal, and a second quantum key management terminal , the method includes:
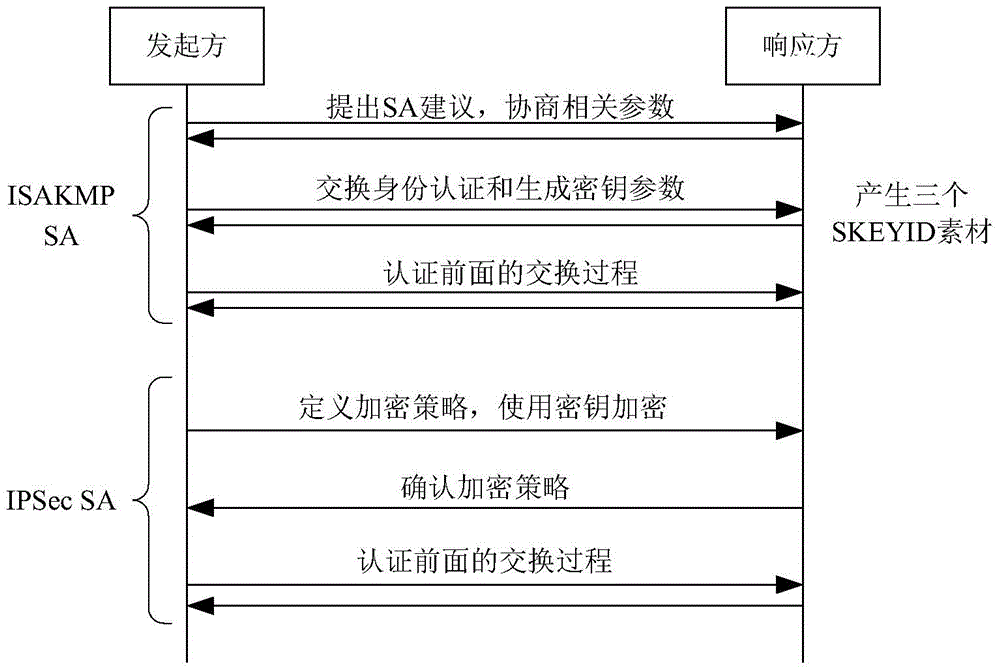
[0082] Step 1. Initiate and respond to the IPSec VPN gateway to carry out ISAKMP SA negotiation, and establish ISAKMP SA, which is the shared strategy and key used by gateways to establish IPSec SA;
[0083] Step 2. Initiate and respond to the IPSec VPN gateway to conduct IPSec SA negotiation, and establish IPSec SA, which is a shared policy and key used to protect the security of data communication between gateways, wherein the quantum key and IKE negotiation key are processed in parallel Negotiation, the quantum key is used as the first session key for priority use, and the IKE negotiation key is used as the second session key; moreover, the i...
Embodiment 2
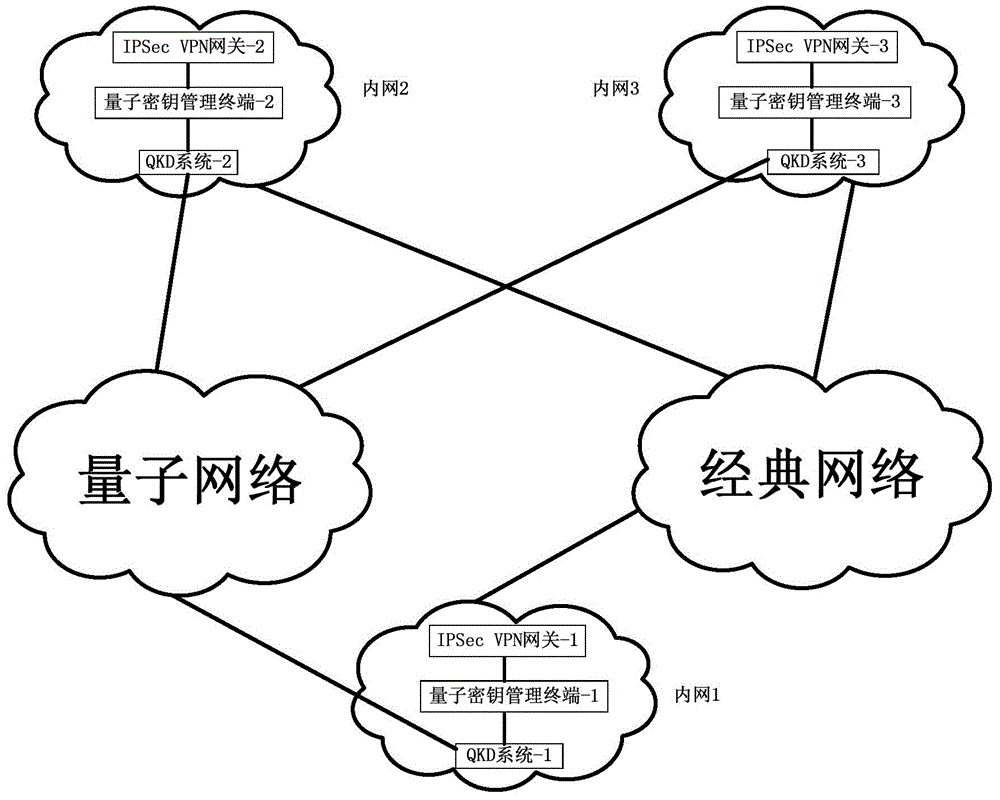
[0131] Such as Figure 12 As shown, the embodiment of the present invention provides a kind of IPSec VPN system, and this system comprises initiation IPSec VPN gateway and response IPSec VPN gateway, the first quantum key management terminal and the second quantum key management terminal, it is characterized in that:
[0132] The initiating IPSec VPN gateway is used to initiate and respond to the ISAKMP SA negotiation and IPSec SA negotiation of the IPSec VPN gateway, wherein the negotiation of the quantum key and the IKE negotiation key is processed in parallel, and according to the negotiation parameters, the first quantum key management terminal is requested and Obtain the quantum key, use the quantum key as the first session key for priority use, and use the IKE negotiation key as the second session key;
[0133] Responding to the IPSec VPN gateway, used to respond to the ISAKMP SA negotiation and IPSec SA negotiation initiated by the initiating IPSec VPN gateway, wherein ...
Embodiment 3
[0145] see Figure 12a , the embodiment of the present invention provides an IPSec VPN gateway, which is used to expand the use of quantum keys between an IPSec VPN system and at least one other IPSec VPN gateway, and the IPSec VPN gateway includes:
[0146] The key negotiation IKE module is used for traditional IKE key negotiation with at least one other IPSec VPN gateway and related parameter negotiation when expanding the use of quantum keys, wherein the negotiation of quantum keys and IKE negotiation keys is processed in parallel, and quantum encryption The key is used as the first session key for priority use, and the IKE negotiation key is used as the second session key, and the established IPSec SA is sent to the IPSec protocol stack module;
[0147] A quantum key interaction module, configured to request and obtain a quantum key from the quantum key management terminal according to the negotiation parameters;
[0148] The IPSec protocol stack module is used to receive...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com