Patents
Literature
272 results about "Behaviour pattern" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
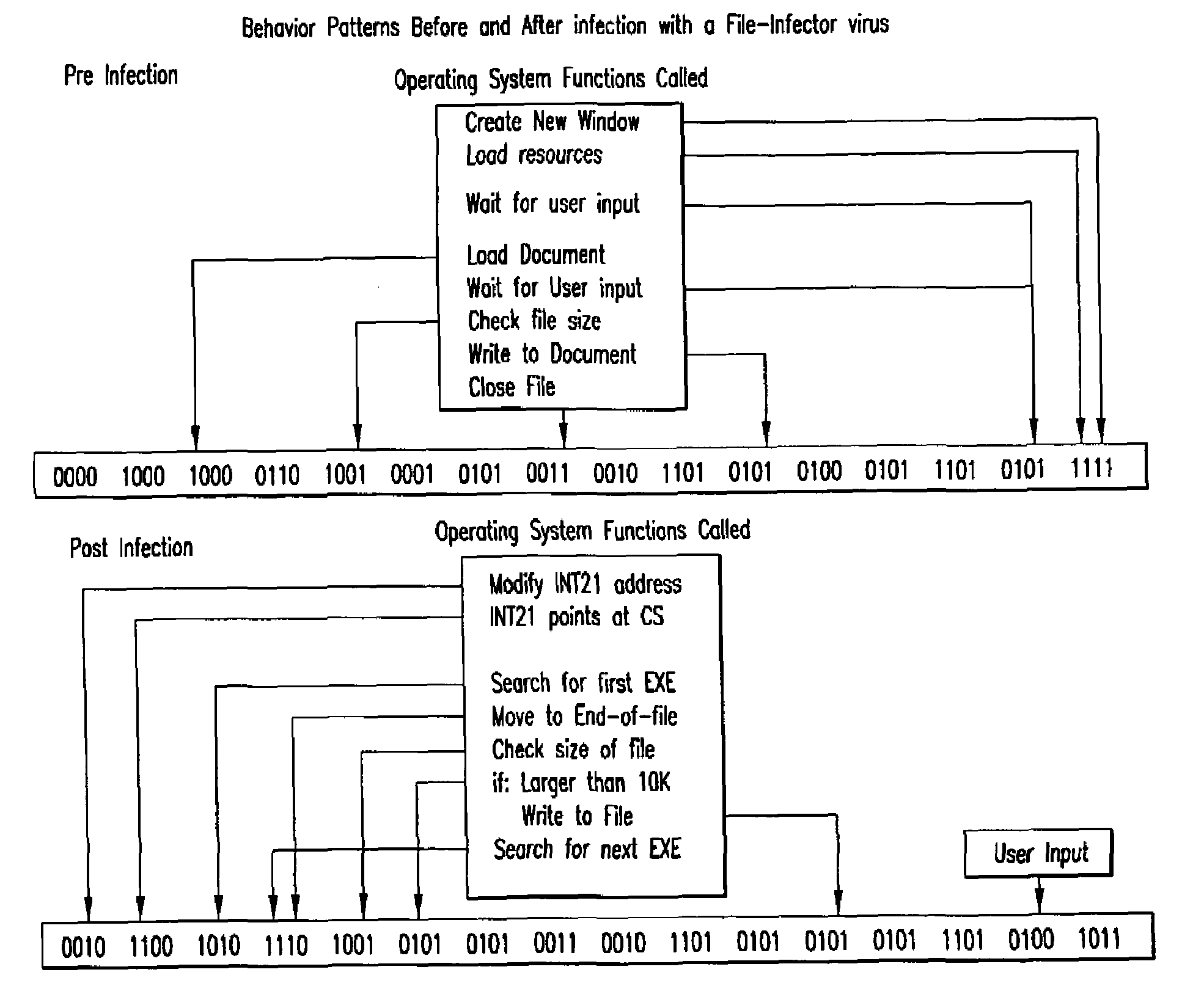
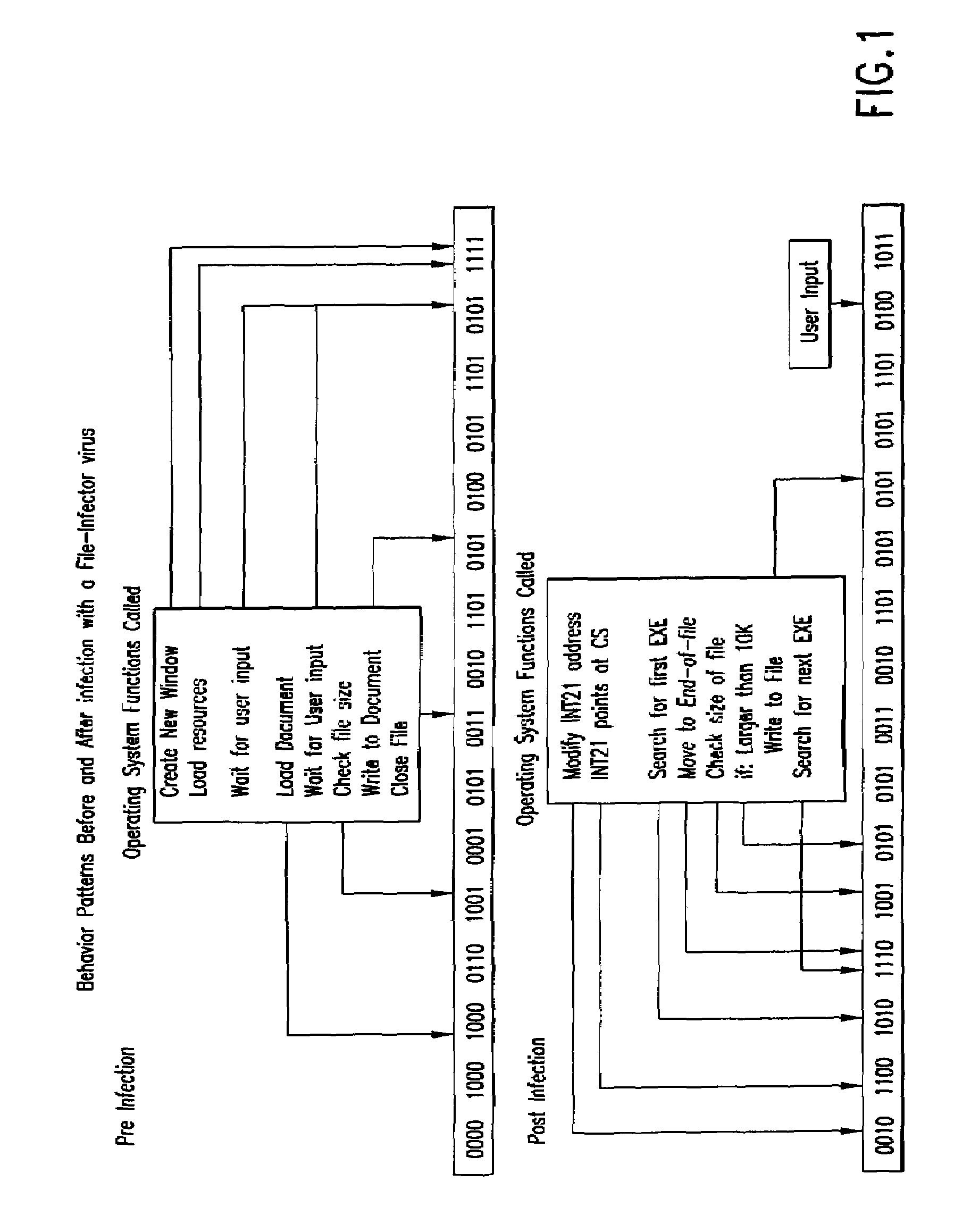
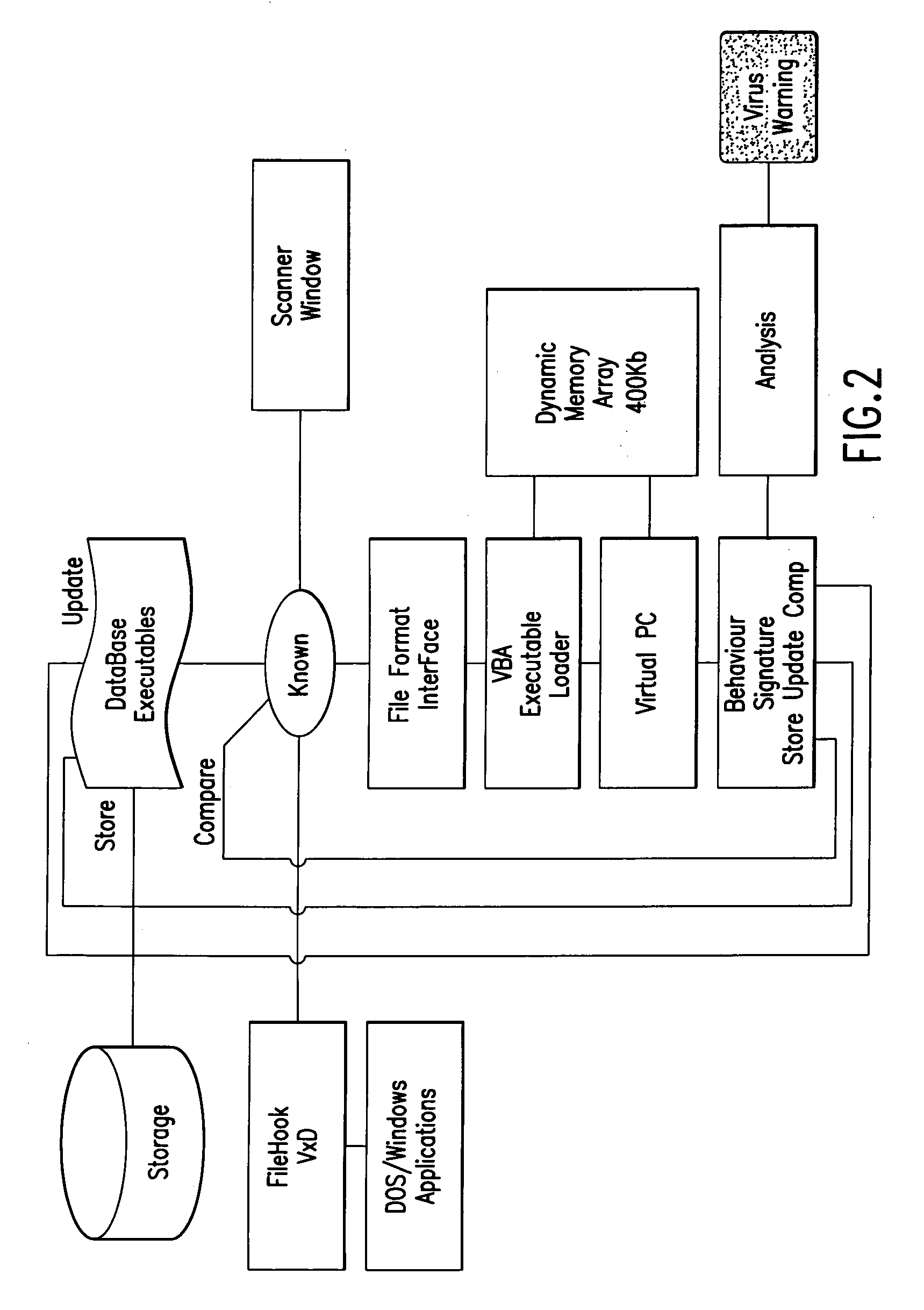
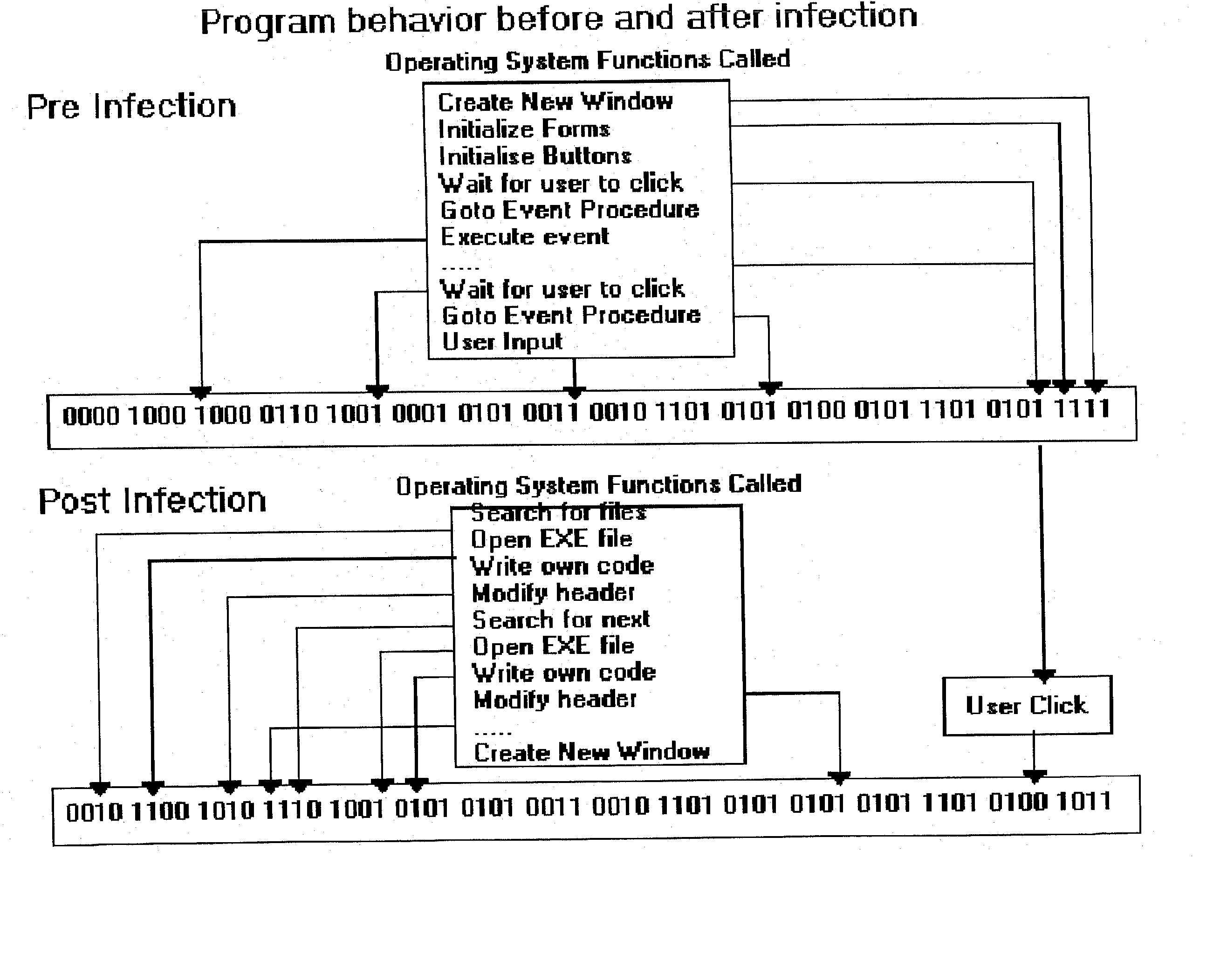
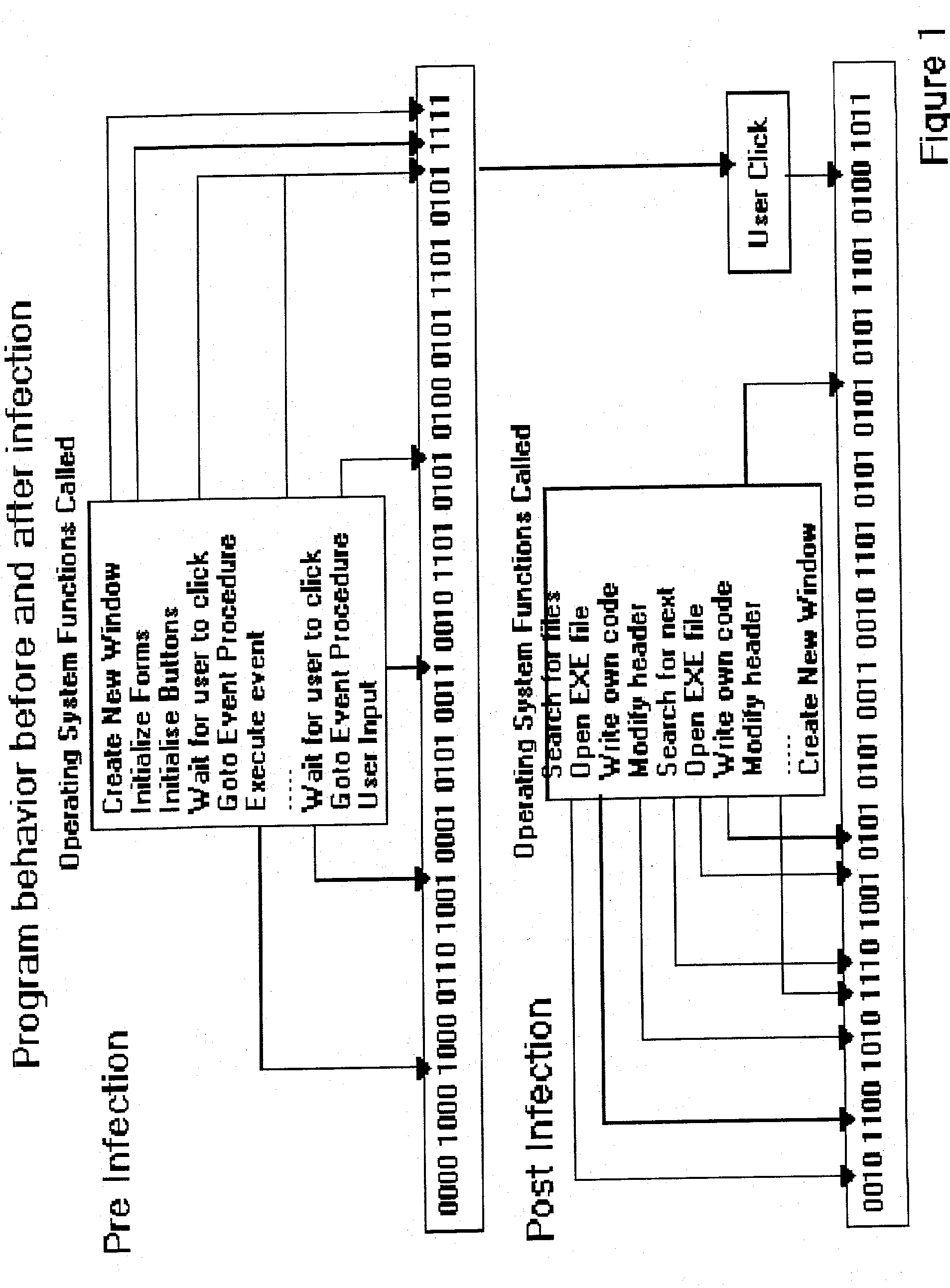
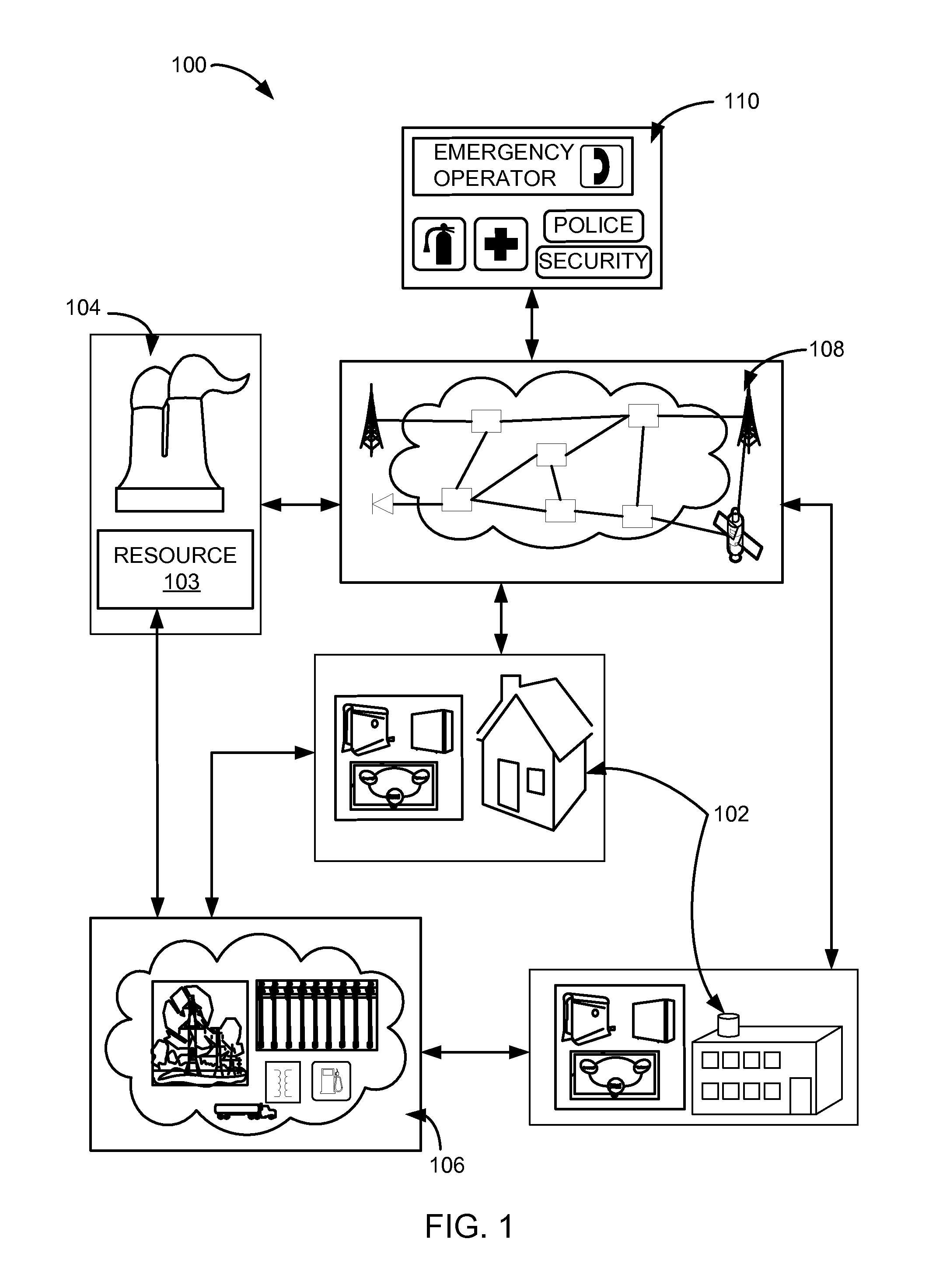
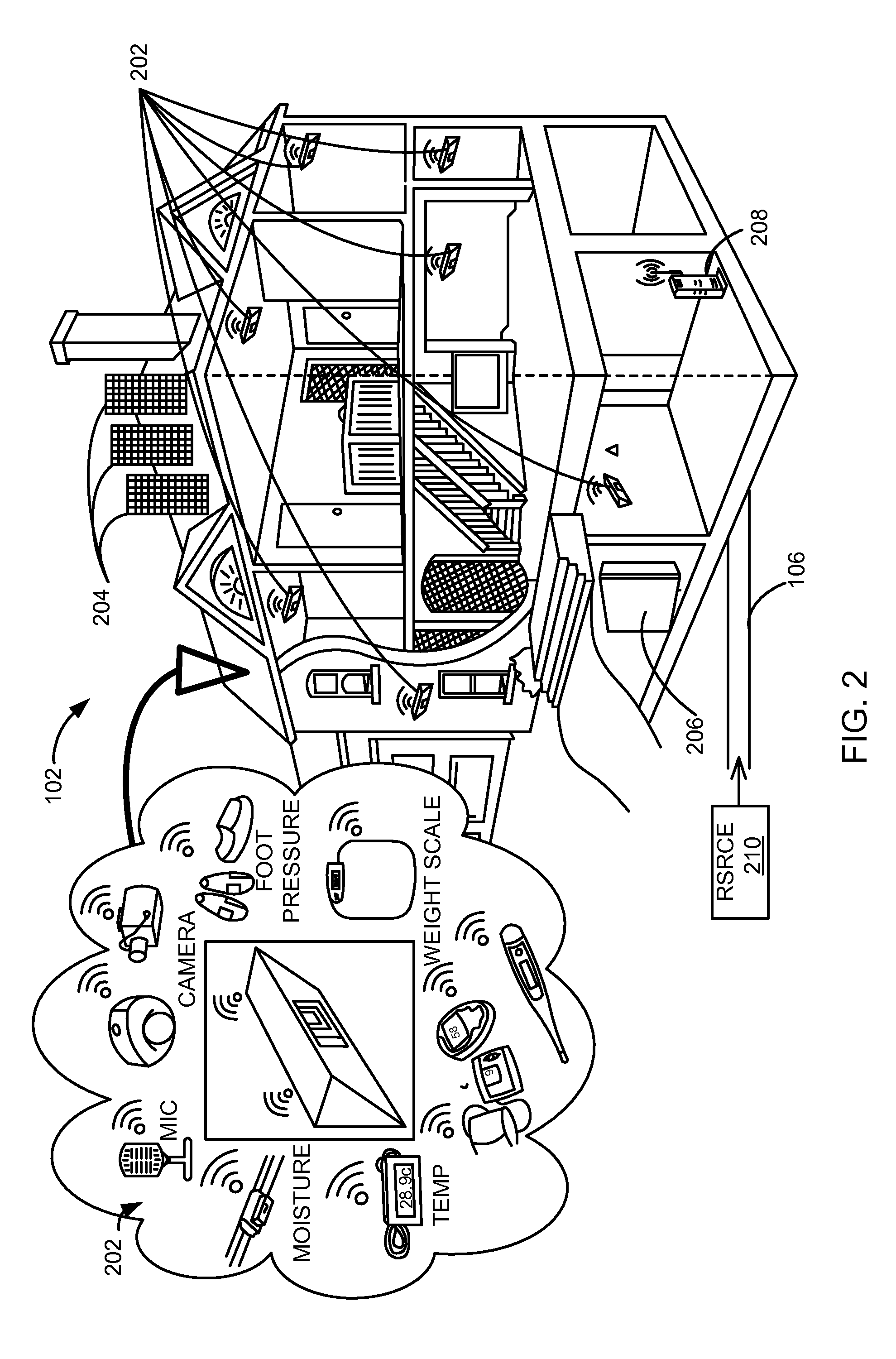
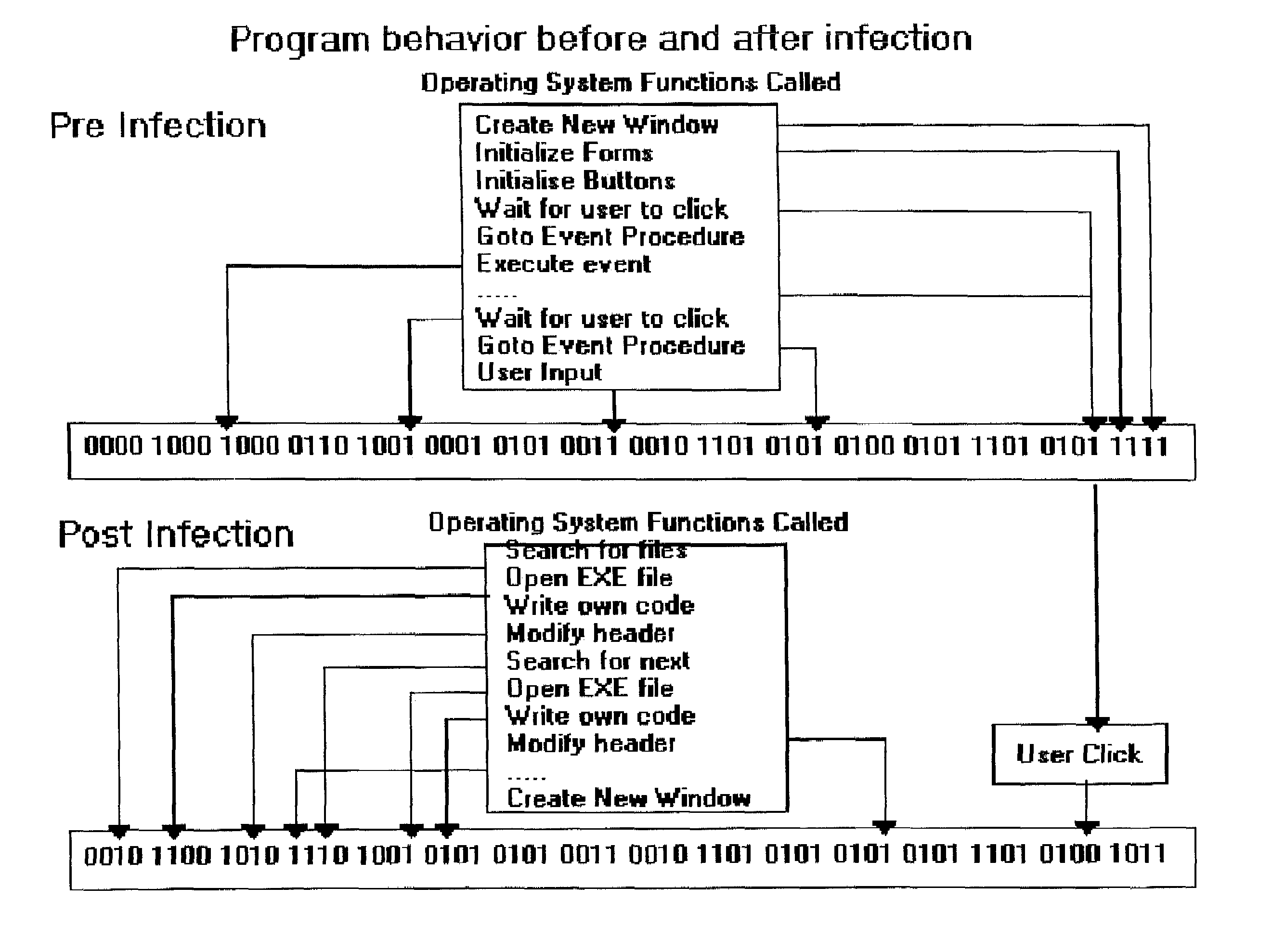
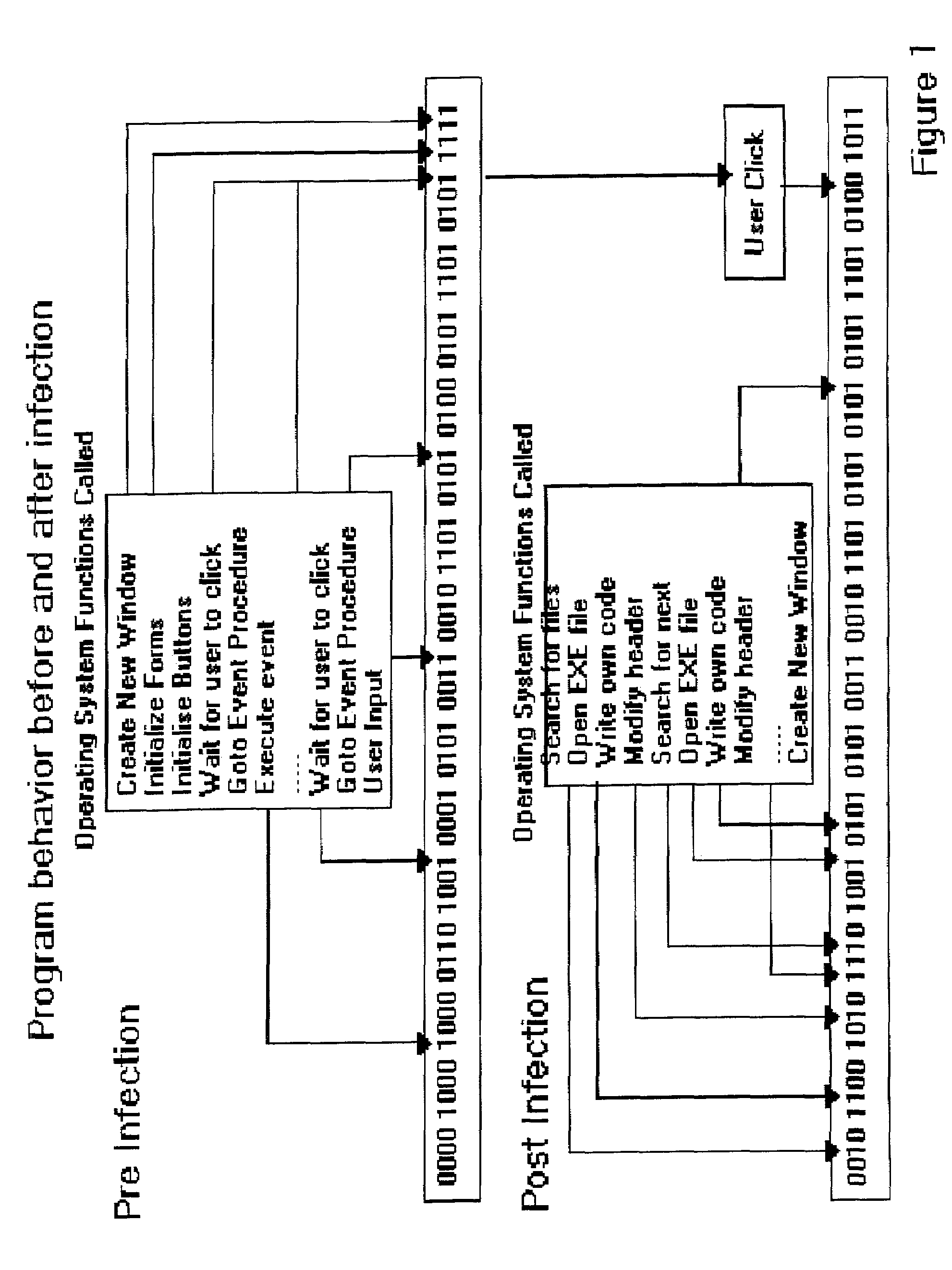
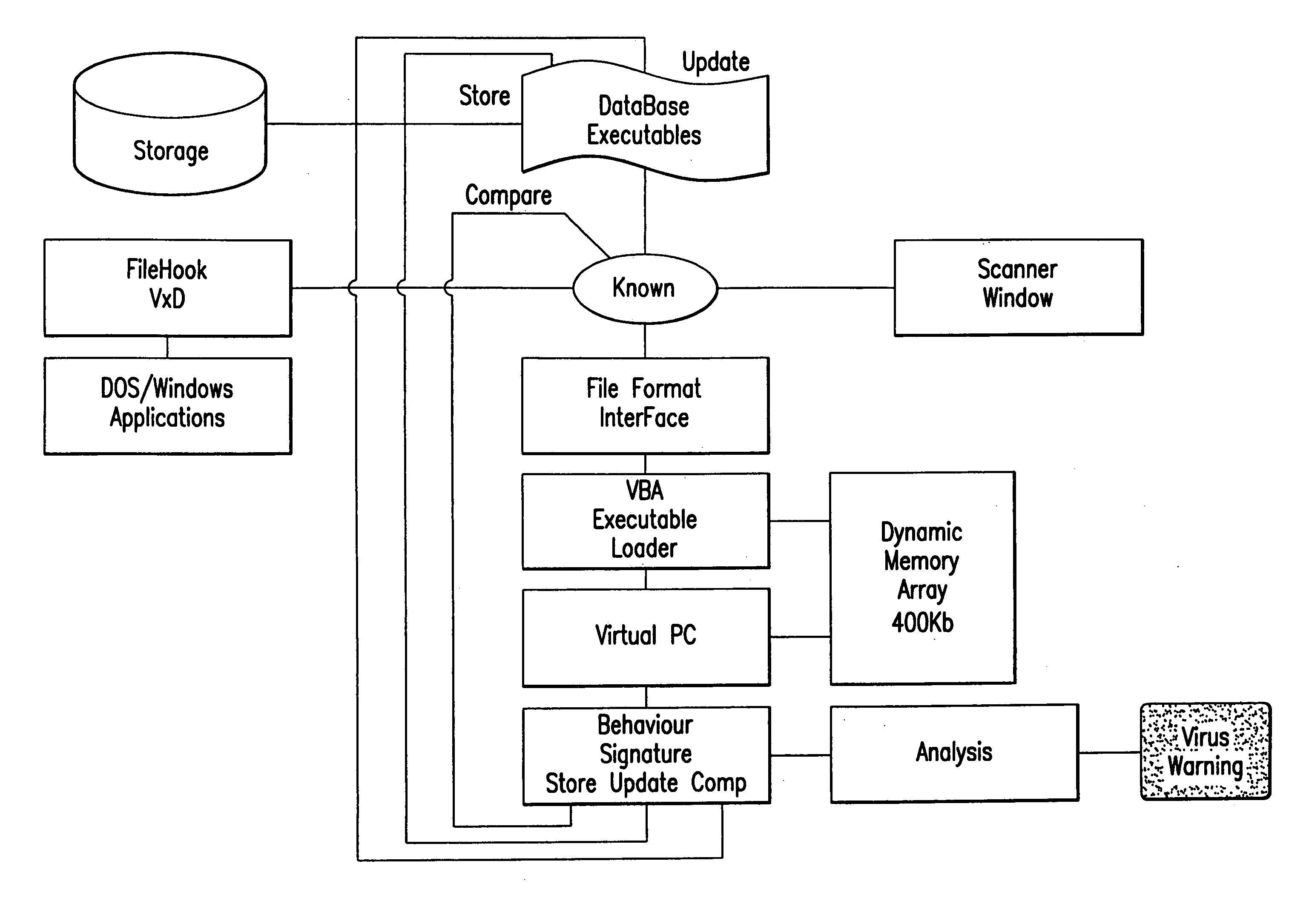
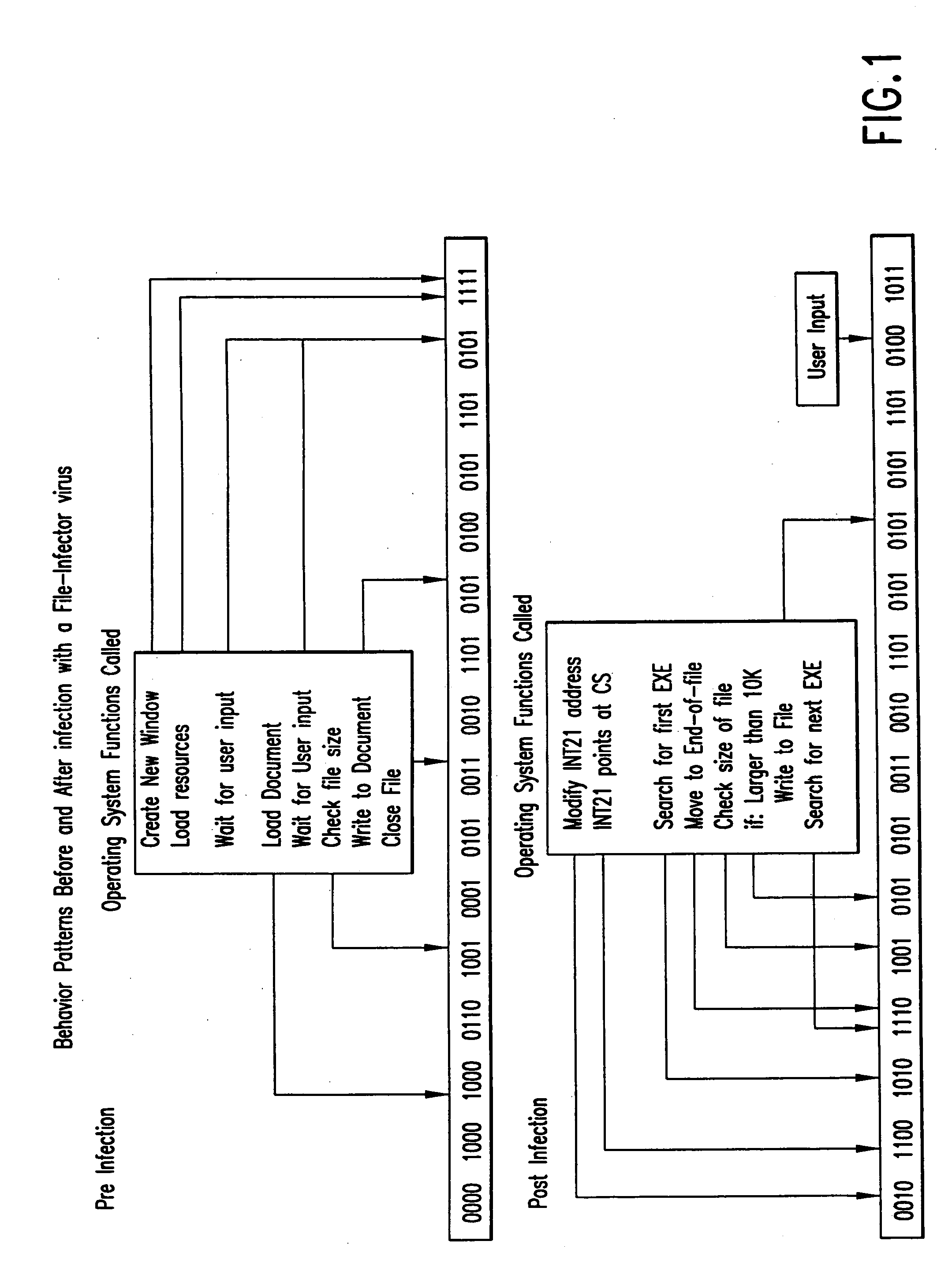
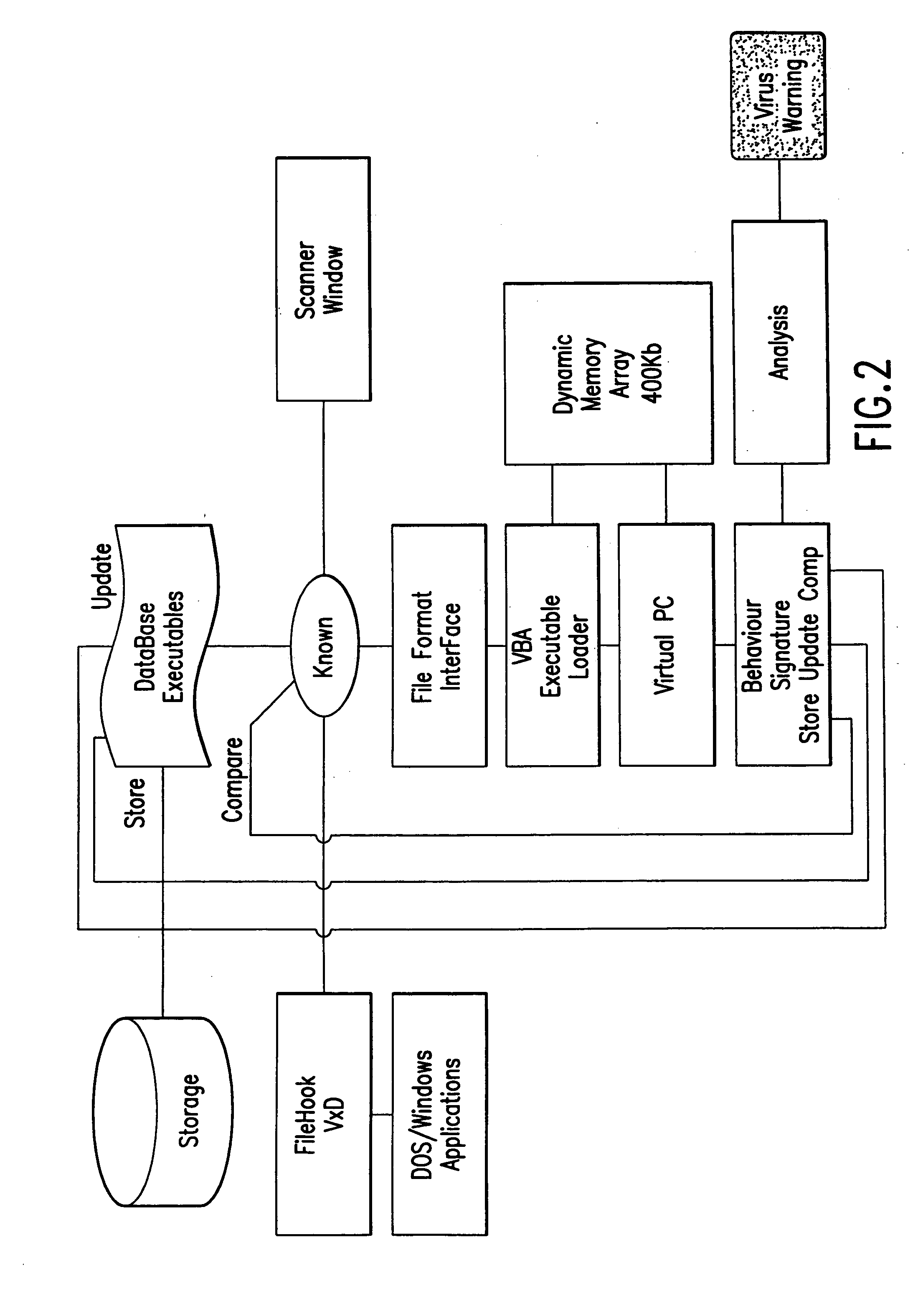
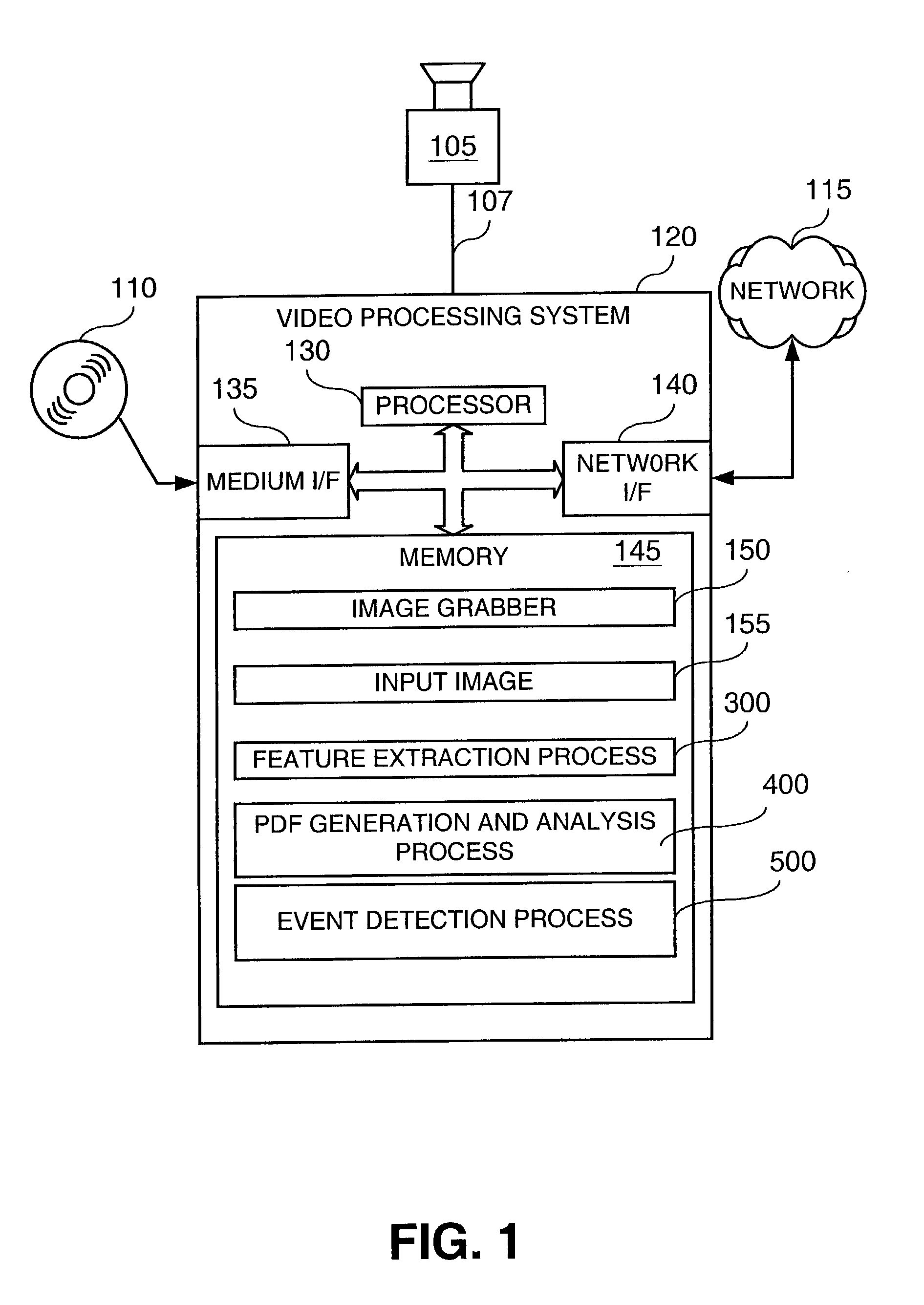
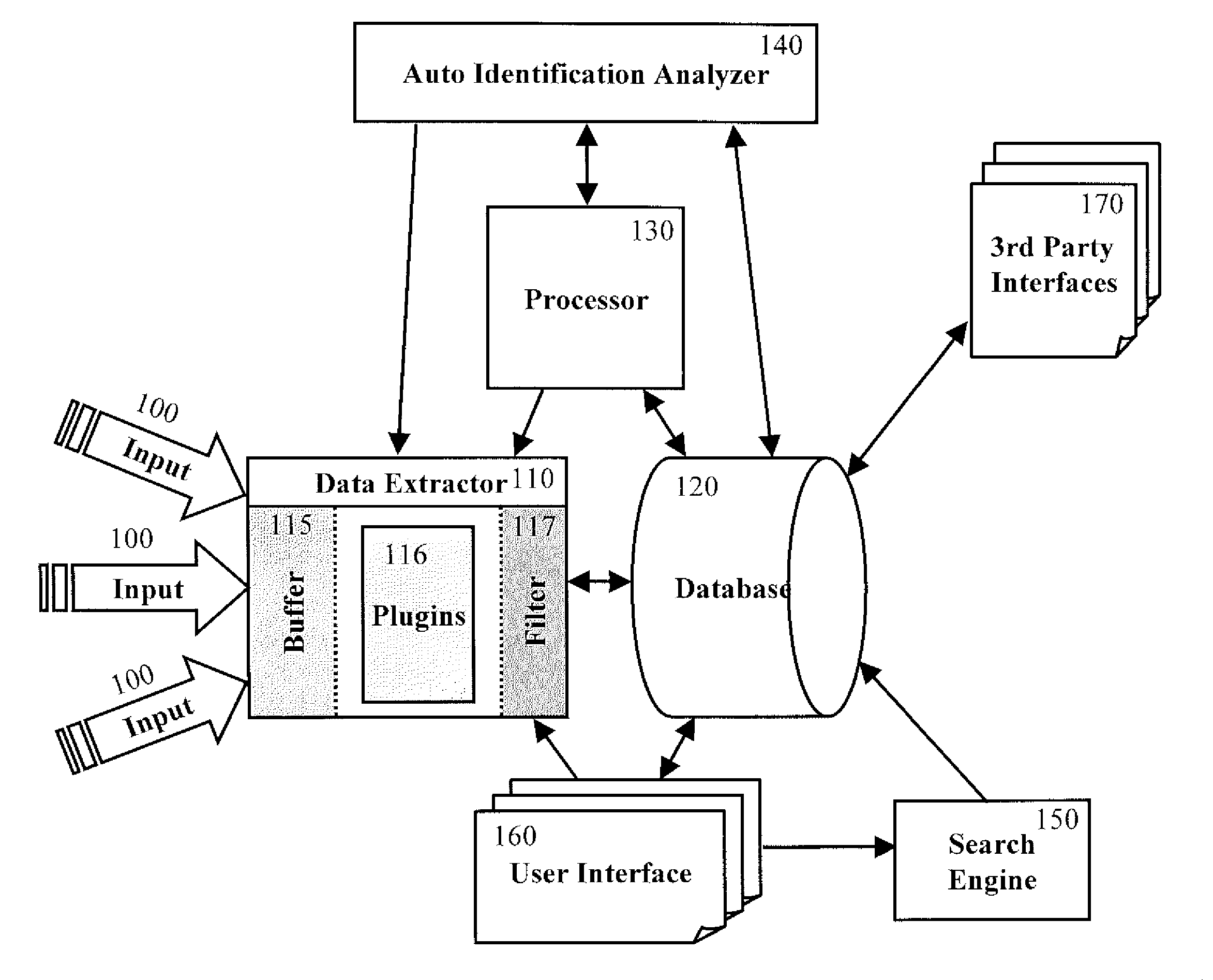
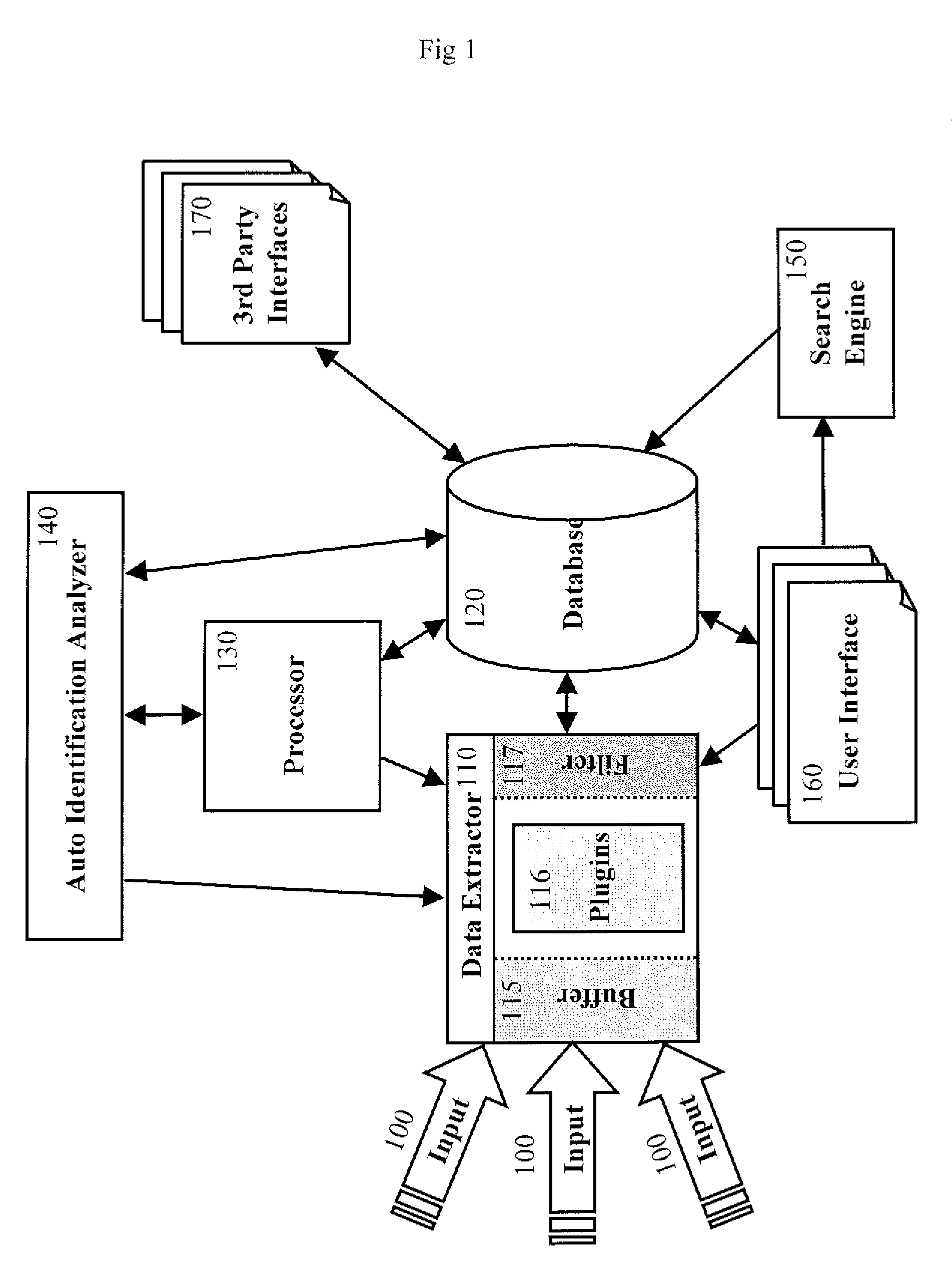
Computer immune system and method for detecting unwanted code in a computer system
InactiveUS7093239B1Memory loss protectionDigital data processing detailsTheoretical computer scienceComputerized system
An automated analysis system detects malicious code within a computer system by generating and subsequently analyzing a behavior pattern for each computer program introduced to the computer system. Generation of the behavior pattern is accomplished by a virtual machine invoked within the computer system. An initial analysis may be performed on the behavior pattern to identify infected programs on initial presentation of the program to the computer system. The analysis system also stores behavior patterns and sequences with their corresponding analysis results in a database. Newly infected programs can be detected by analyzing a newly generated behavior pattern for the program with reference to a stored behavior pattern to identify presence of an infection or payload pattern.
Owner:PALO ALTO NETWORKS INC
Detecting Behavioral Patterns and Anomalies Using Activity Profiles
ActiveUS20080059474A1Potential security breachError detection/correctionDigital data processing detailsBehaviour patternActivity profile
Activity data is analyzed or evaluated to detect behavioral patterns and anomalies. When a particular pattern or anomaly is detected, a system may send a notification or perform a particular task. This activity data may be collected in an information management system, which may be policy based. Notification may be by way e-mail, report, pop-up message, or system message. Some tasks to perform upon detection may include implementing a policy in the information management system, disallowing a user from connecting to the system, and restricting a user from being allowed to perform certain actions. To detect a pattern, activity data may be compared to a previously defined or generated activity profile.
Owner:NEXTLABS
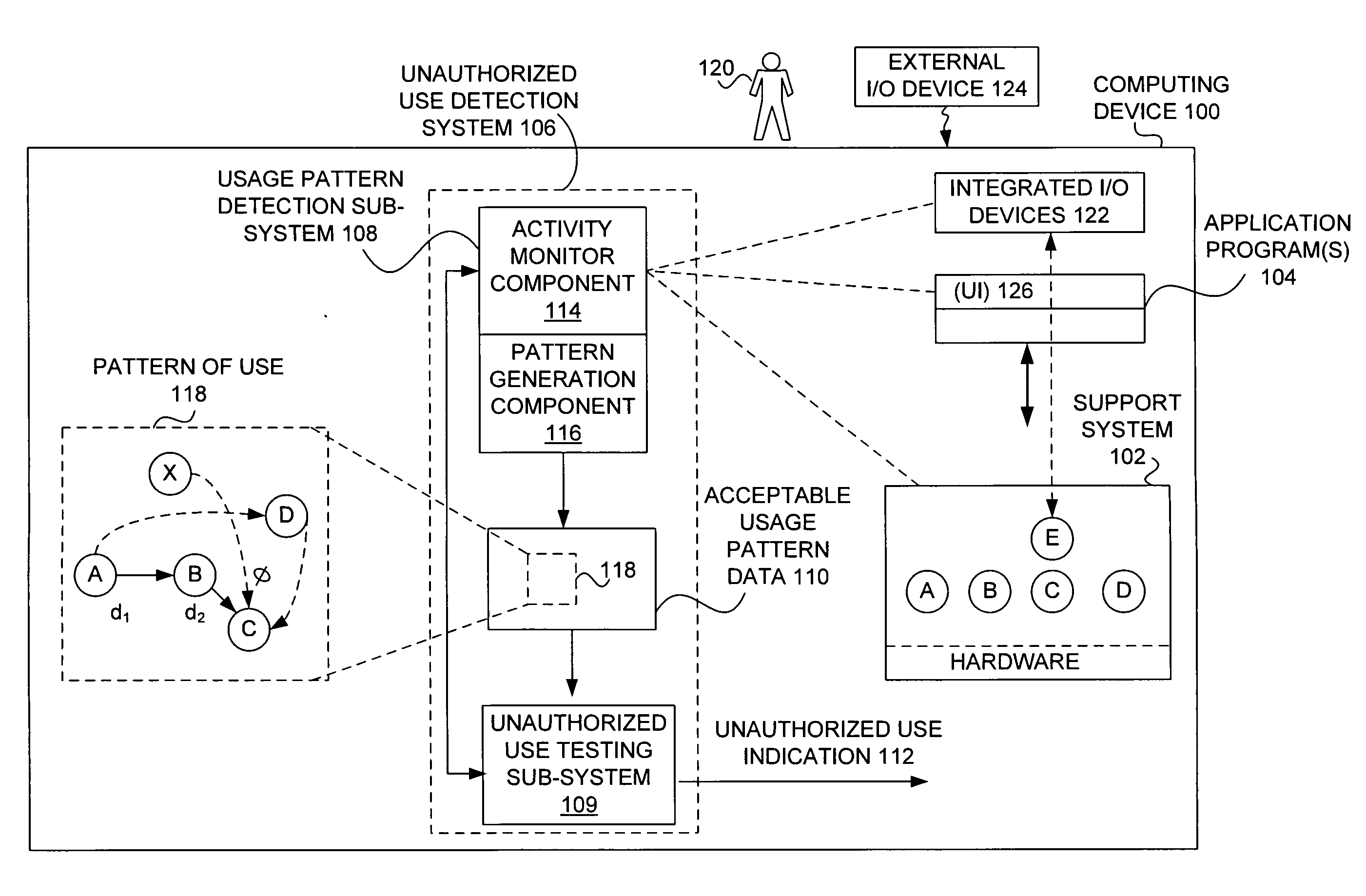
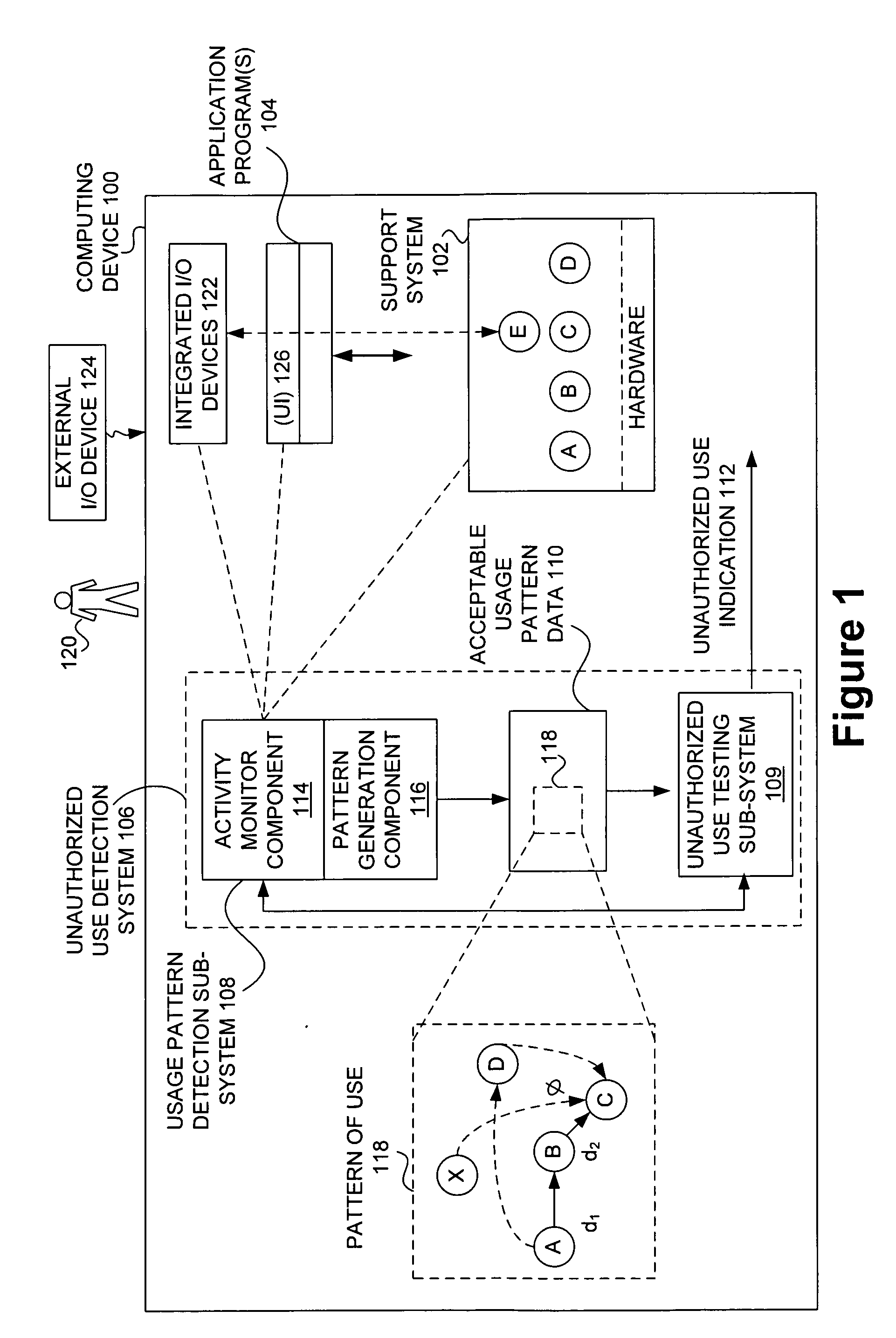
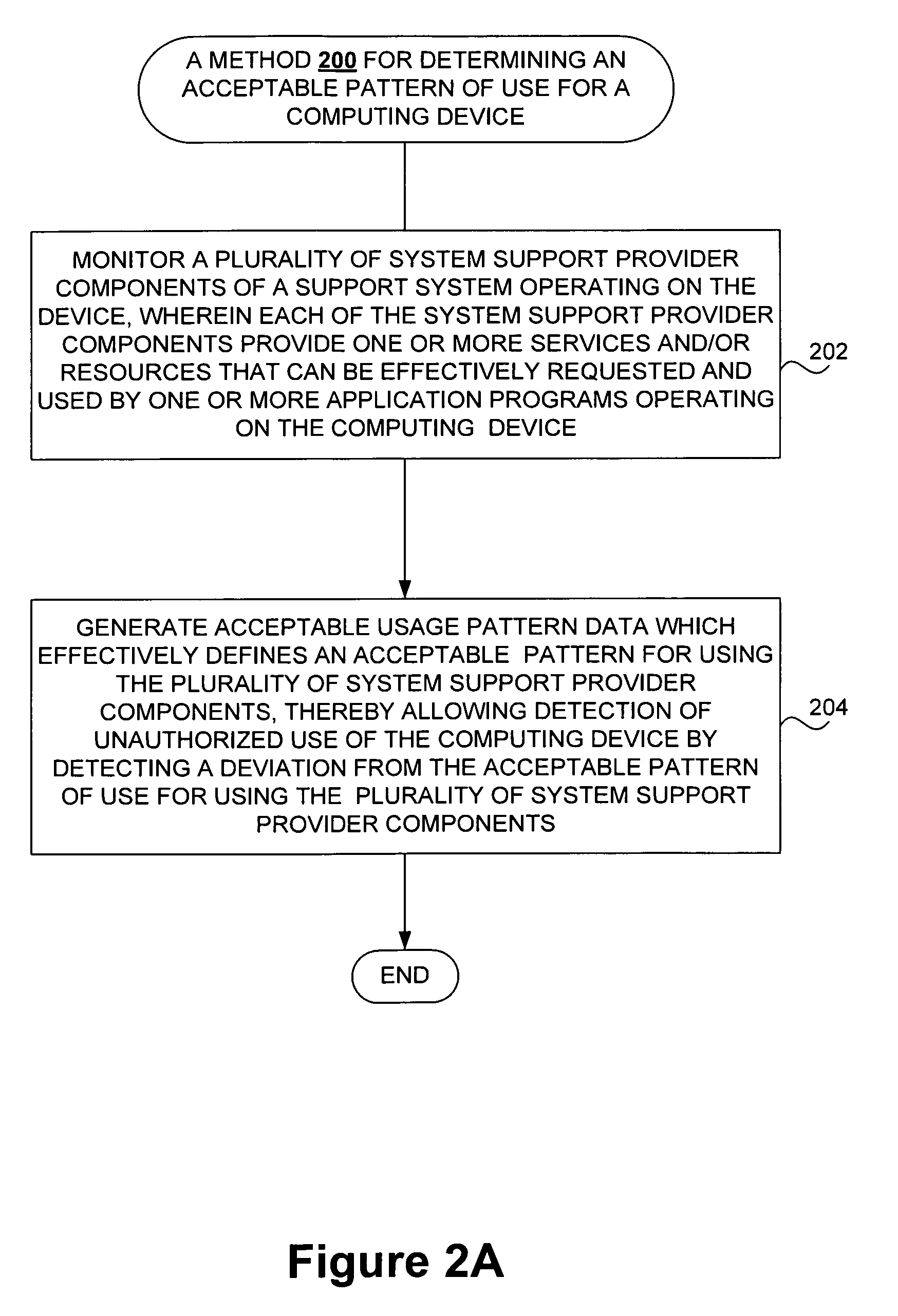
Detecting unauthorized use of computing devices based on behavioral patterns
InactiveUS20090199296A1Efficiently definedMemory loss protectionError detection/correctionSupporting systemOperational system
Techniques for detecting unauthorized use (e.g., malicious attacks) of the computing systems (e.g., computing devices) are disclosed. Unauthorized use can be detected based on patterns of use (e.g., behavioral patterns of use typically associated with a human being) of the computing systems. Acceptable behavioral pattern data can be generated for a computing system by monitoring the use of a support system (e.g., an operating system, a virtual environment) operating on the computing system. For example, a plurality of system support provider components of a support system (e.g., system calls, device drivers) can be monitored in order to generate the acceptable behavioral pattern data in a form which effectively defines an acceptable pattern of use (usage pattern) for the monitored system support provider components, thereby allowing detection of unauthorized use of a computing system by detecting any deviation from the acceptable pattern of use of the monitored system support provider components.
Owner:SAMSUNG ELECTRONICS CO LTD
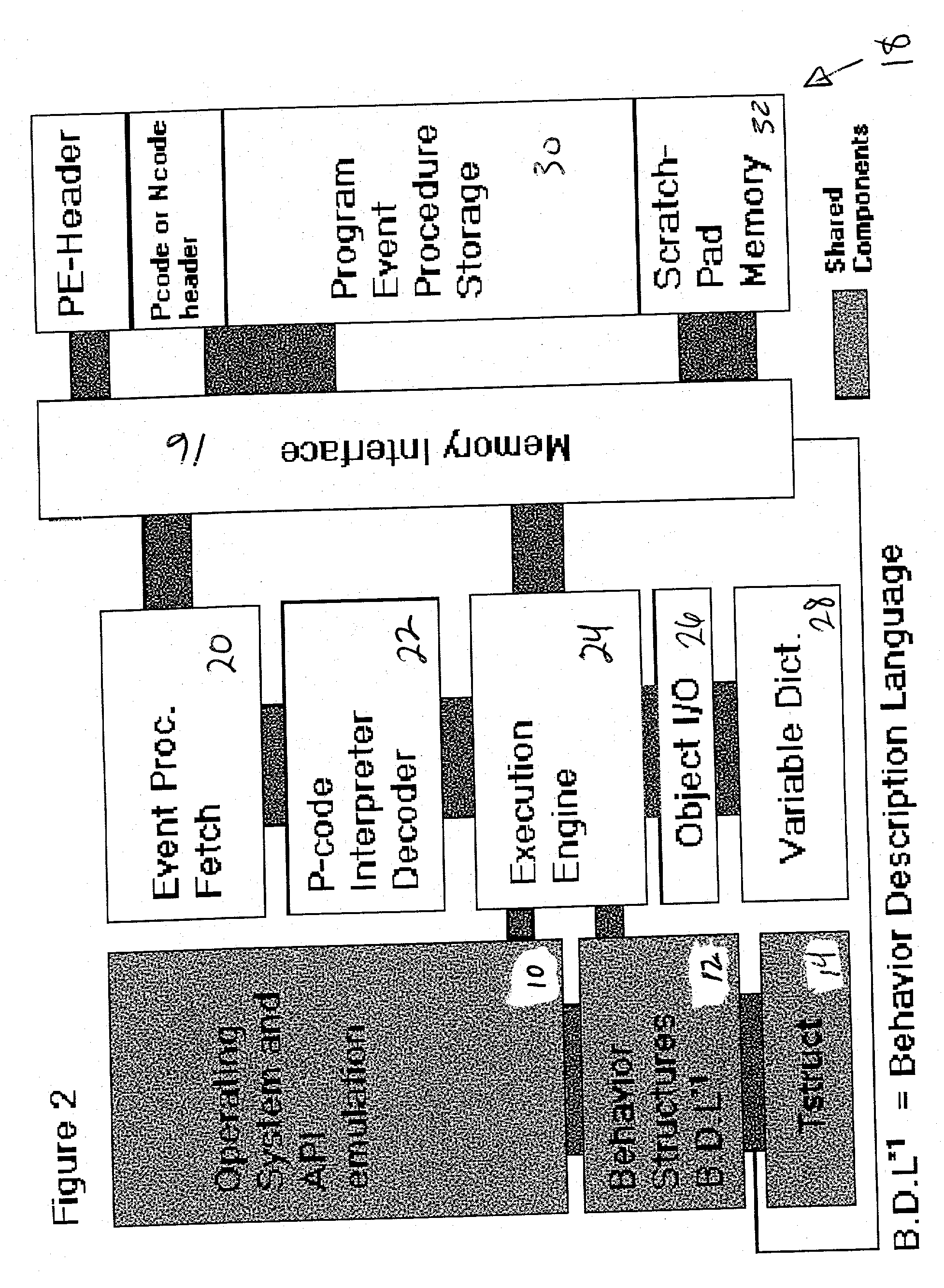
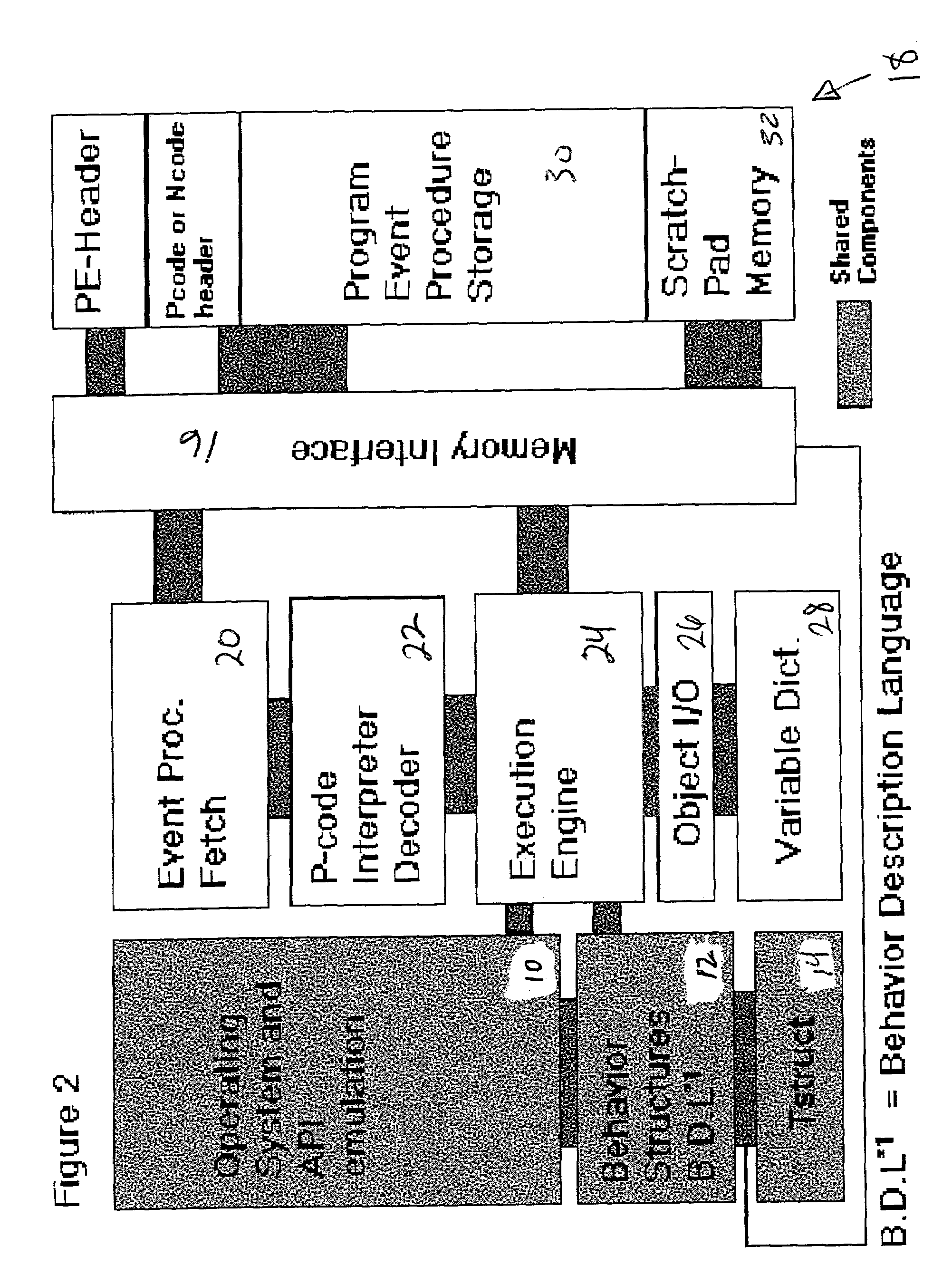
Computer immune system and method for detecting unwanted code in a P-code or partially compiled native-code program executing within a virtual machine
InactiveUS20030212902A1Memory loss protectionDigital data processing detailsComputerized systemBehaviour pattern
An automated analysis system identifies the presence of malicious P-code or N-code programs in a manner that limits the possibility of the malicious code infecting a target computer. The target computer system initializes an analytical virtual P-code engine (AVPE). As initialized, the AVPE comprises software simulating the functionality of a P-code or intermediate language engine as well as machine language facilities simulating the P-code library routines that allow the execution of N-code programs. The AVPE executes a target program so that the target program does not interact with the target computer. The AVPE analyzes the behavior of the target program to identify occurrence of malicious code behavior and to indicate in a behavior pattern the occurrence of malicious code behavior. The AVPE is terminated at the end of the analysis process, thereby removing from the computer system the copy of the target program that was contained within the AVPE.
Owner:PALO ALTO NETWORKS INC
Systems and Methods for Application-Level Security
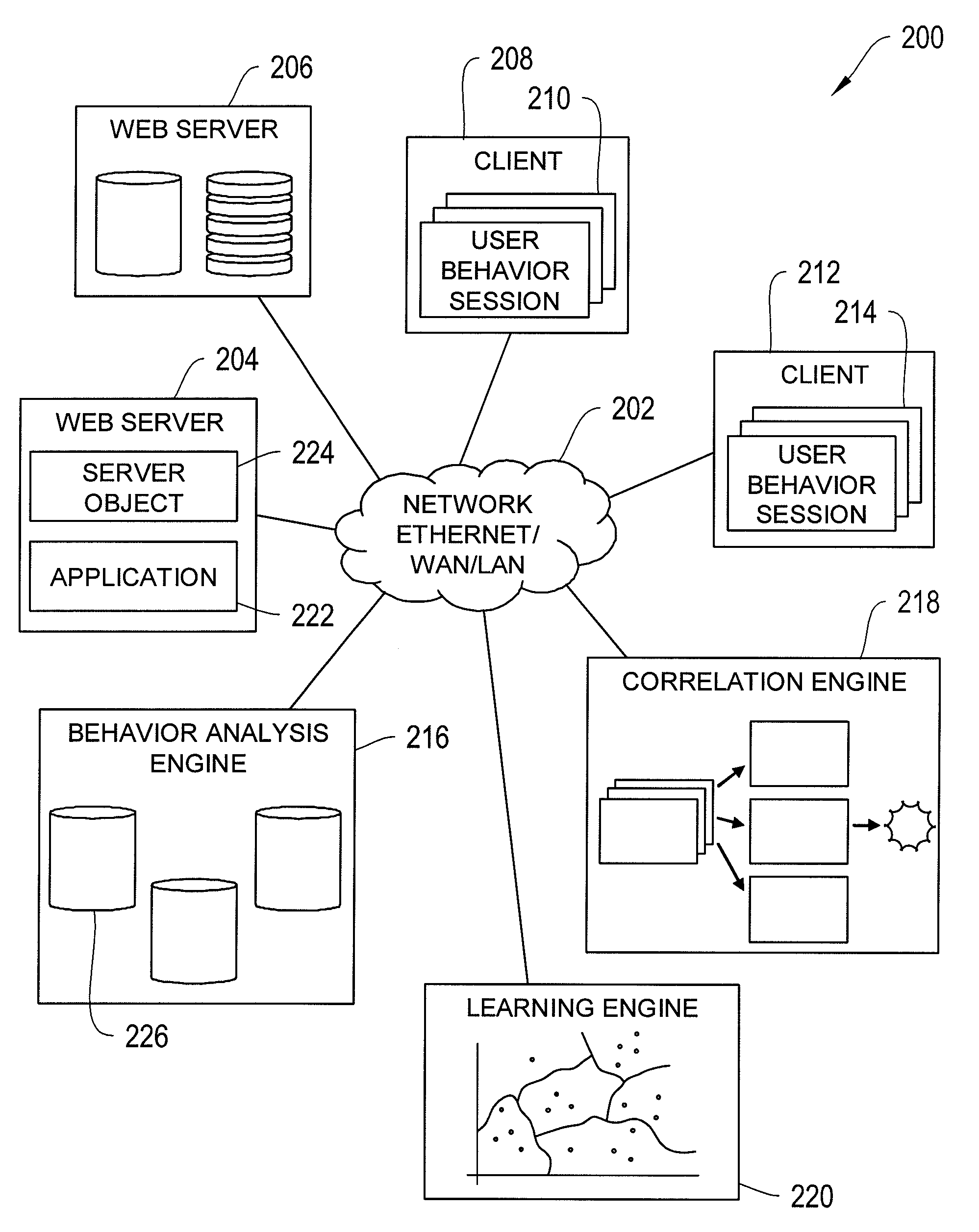
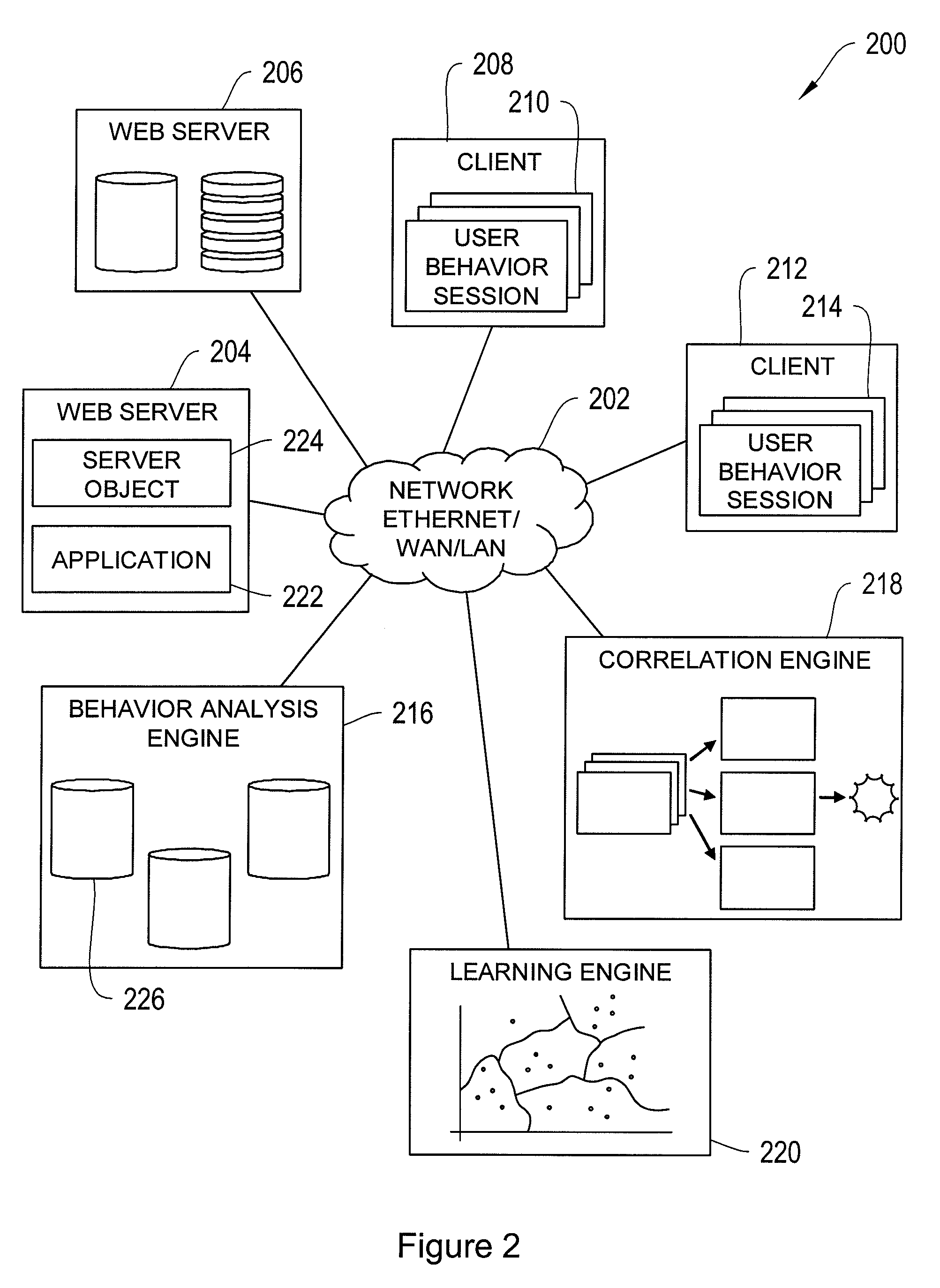
InactiveUS20100299292A1Easily correlatedReduce settingsMemory loss protectionError detection/correctionInternet privacyBehaviour pattern
A system and method for application-level security is disclosed. Application-level security refers to detecting security threats from functional user behavior. Information about functional user behavior is transformed into a behavior session. The behavior session is transformed into a behavior pattern. The behavior pattern is correlated with evaluation patterns to detect potential security threats. Behavior patterns are collected over time to improve analysis.
Owner:XYBERSHIELD INC
Building management system with privacy-guarded assistance mechanism and method of operation thereof
ActiveUS20130257626A1Signalling system detailsVisible signalling systemsPrivacy protectionBehaviour pattern
A method for operating a building management system includes: identifying a movement-pattern from a sensed attribute at a first sensor; determining a behavior-pattern at the first sensor when the movement-pattern matches a template-pattern; transmitting the behavior-pattern and the sensed attribute from the first sensor to a second sensor; and tracking the sensed attribute at the second sensor for displaying on a device.
Owner:SONY CORP
Computer immune system and method for detecting unwanted code in a P-code or partially compiled native-code program executing within a virtual machine
InactiveUS7370360B2Memory loss protectionDigital data processing detailsComputerized systemBehaviour pattern
An automated analysis system identifies the presence of malicious P-code or N-code programs in a manner that limits the possibility of the malicious code infecting a target computer. The target computer system initializes an analytical virtual P-code engine (AVPE). As initialized, the AVPE comprises software simulating the functionality of a P-code or intermediate language engine as well as machine language facilities simulating the P-code library routines that allow the execution of N-code programs. The AVPE executes a target program so that the target program does not interact with the target computer. The AVPE analyzes the behavior of the target program to identify occurrence of malicious code behavior and to indicate in a behavior pattern the occurrence of malicious code behavior. The AVPE is terminated at the end of the analysis process, thereby removing from the computer system the copy of the target program that was contained within the AVPE.
Owner:PALO ALTO NETWORKS INC
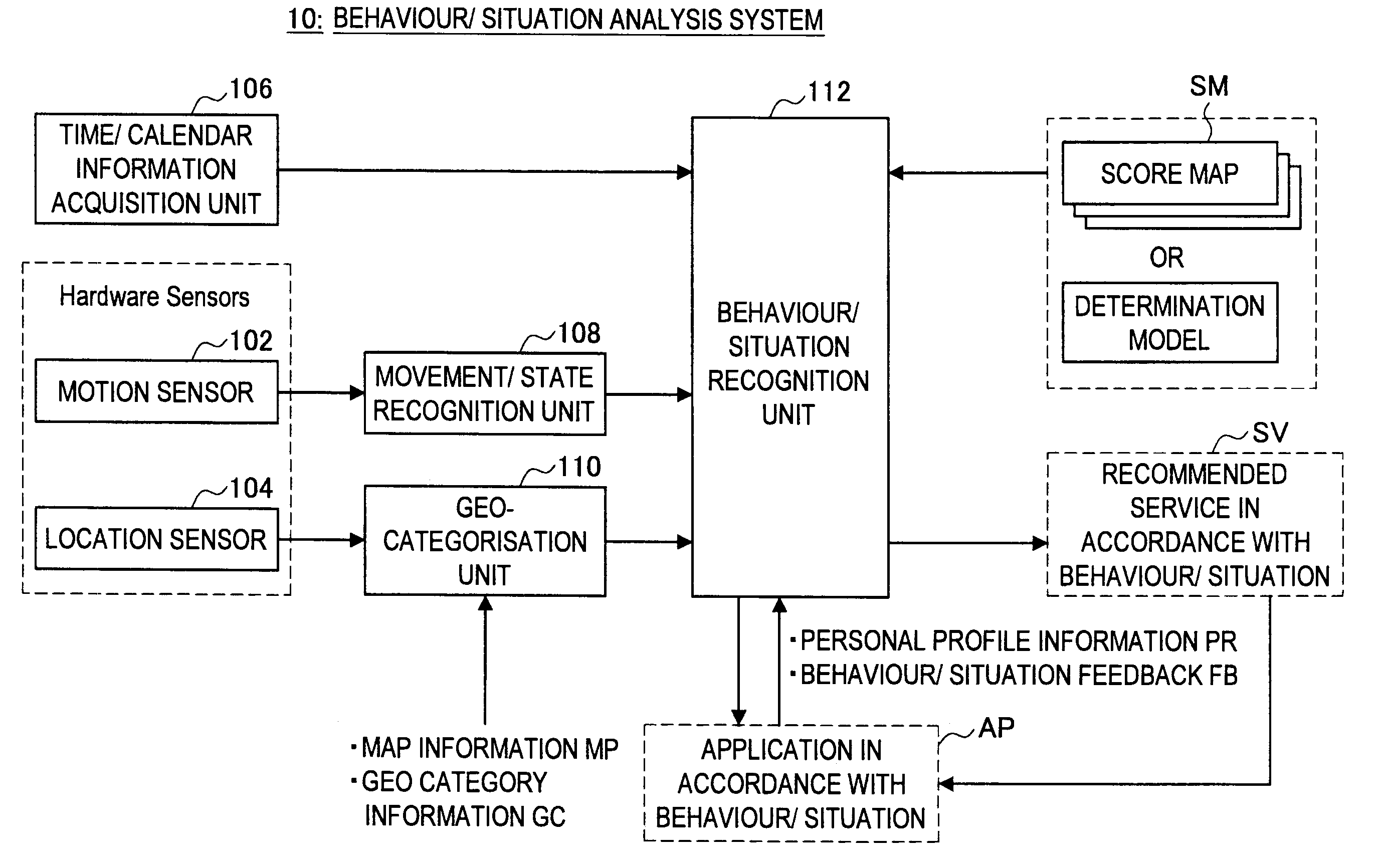
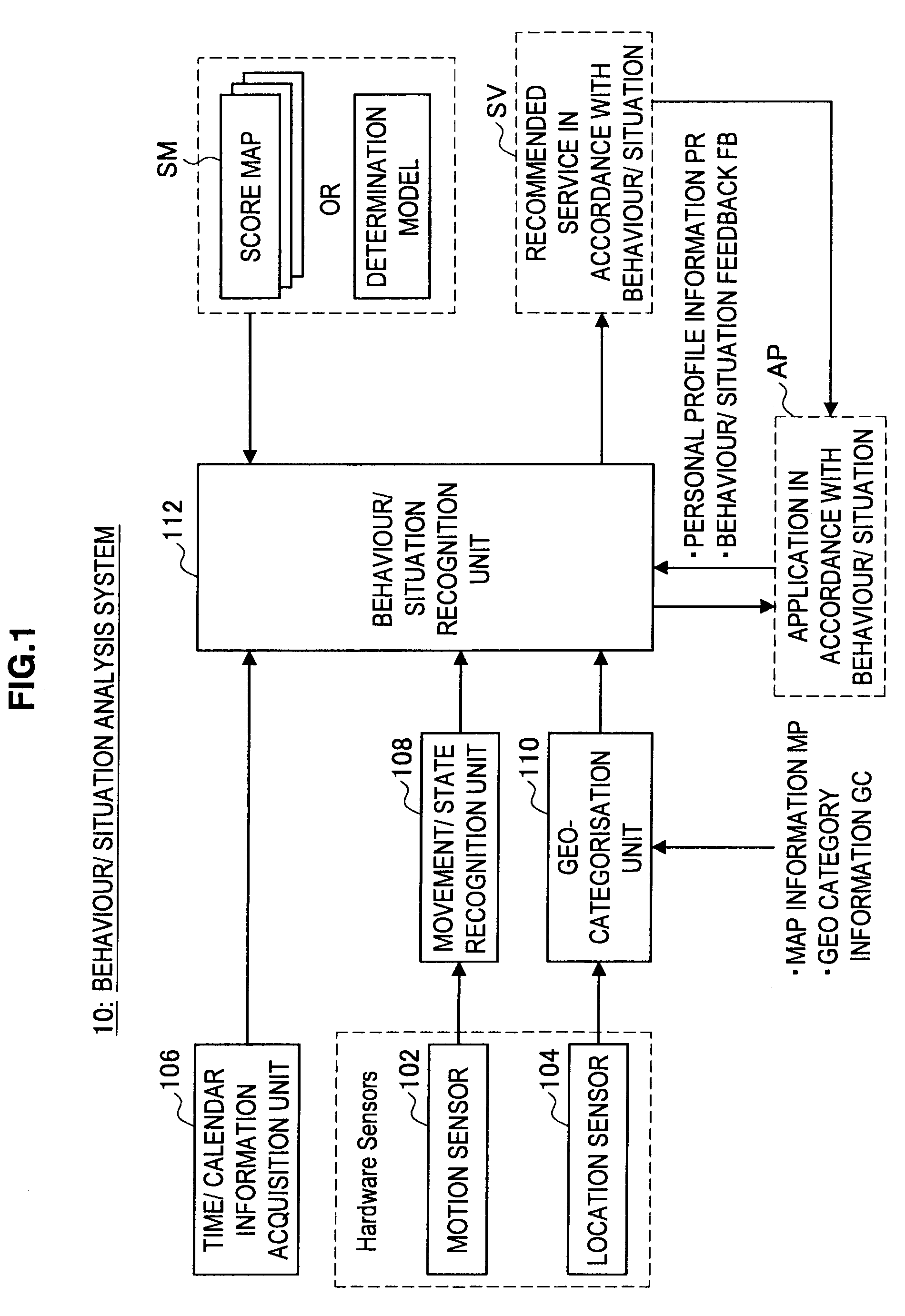
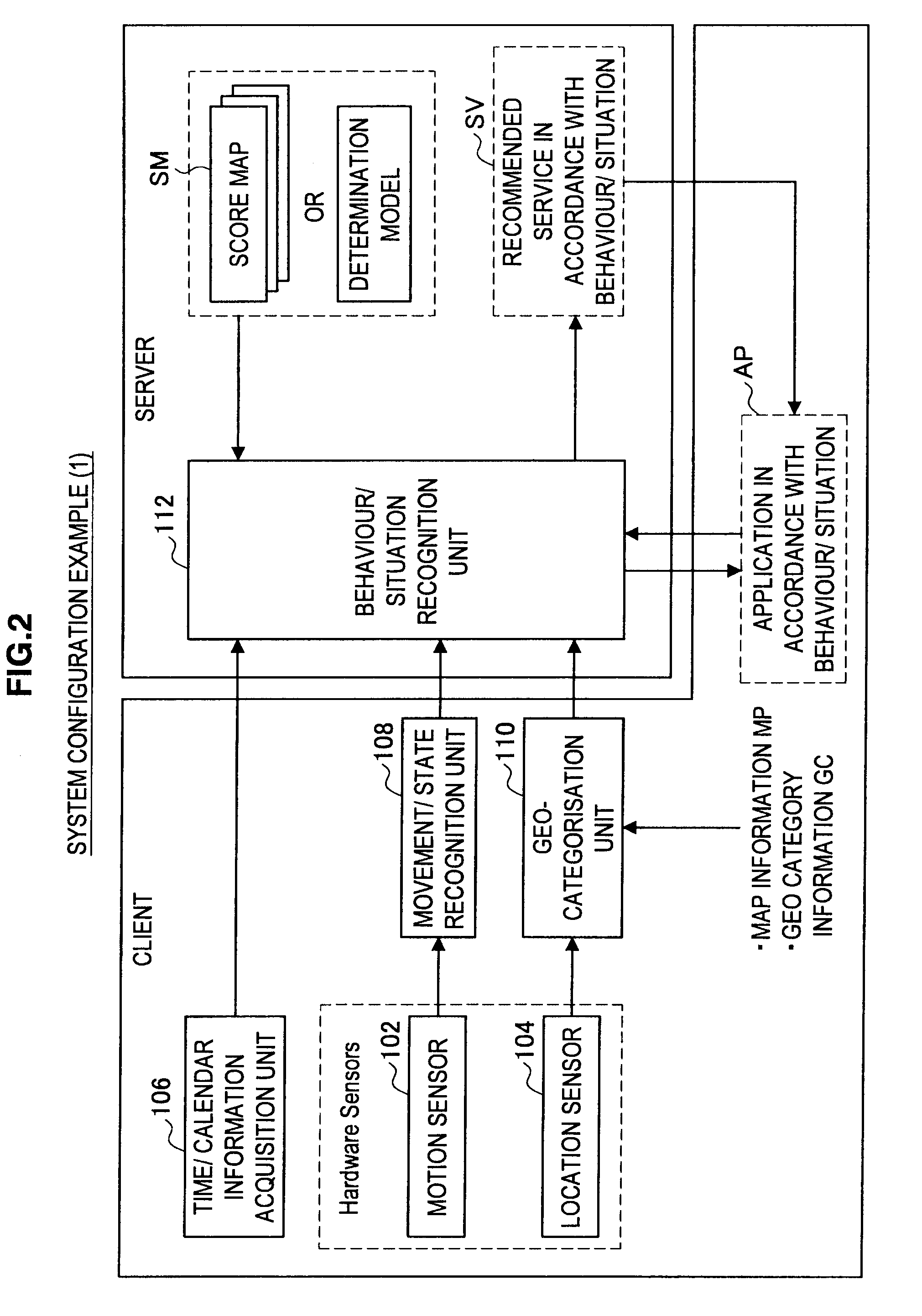
Behaviour Pattern Analysis System, Mobile Terminal, Behaviour Pattern Analysis Method, and Program
ActiveUS20110081634A1Data processing applicationsNavigational calculation instrumentsComputer visionBehaviour pattern
Provided is a mobile terminal including a movement sensor that detects a movement of a user and outputs movement information, acquires information on a building existing at a current location or information on buildings existing in a vicinity of the current location, analyses the movement information output from the movement sensor, and detects a first behaviour pattern corresponding to the movement information from multiple first behaviour patterns obtained by classifying behaviours performed by the user over a relatively short period of time, and analyses the information on a building or buildings and the first behaviour pattern, and detects a second behaviour pattern corresponding to the information on a building or buildings and the first behaviour pattern from multiple second behaviour patterns obtained by classifying behaviours performed by the user over a relatively long period of time.
Owner:SONY CORP
Method and system for detecting malicious behavioral patterns in a computer, using machine learning
InactiveUS20080184371A1Memory loss protectionError detection/correctionComputer wormTheoretical computer science
Method for detecting malicious behavioral patterns which are related to malicious software such as a computer worm in computerized systems that include data exchange channels with other systems over a data network. According to the proposed method, hardware and / or software parameters that can characterize known behavioral patterns in the computerized system are determined. Known malicious code samples are learned by a machine learning process, such as decision trees, Naïve Bayes, Bayesian Networks, and artificial neural networks, and the results of the machine learning process are analyzed in respect to these behavioral patterns. Then, known and unknown malicious code samples are identified according to the results of the machine learning process.
Owner:DEUTSCHE TELEKOM AG
System and method for behavioural modelling
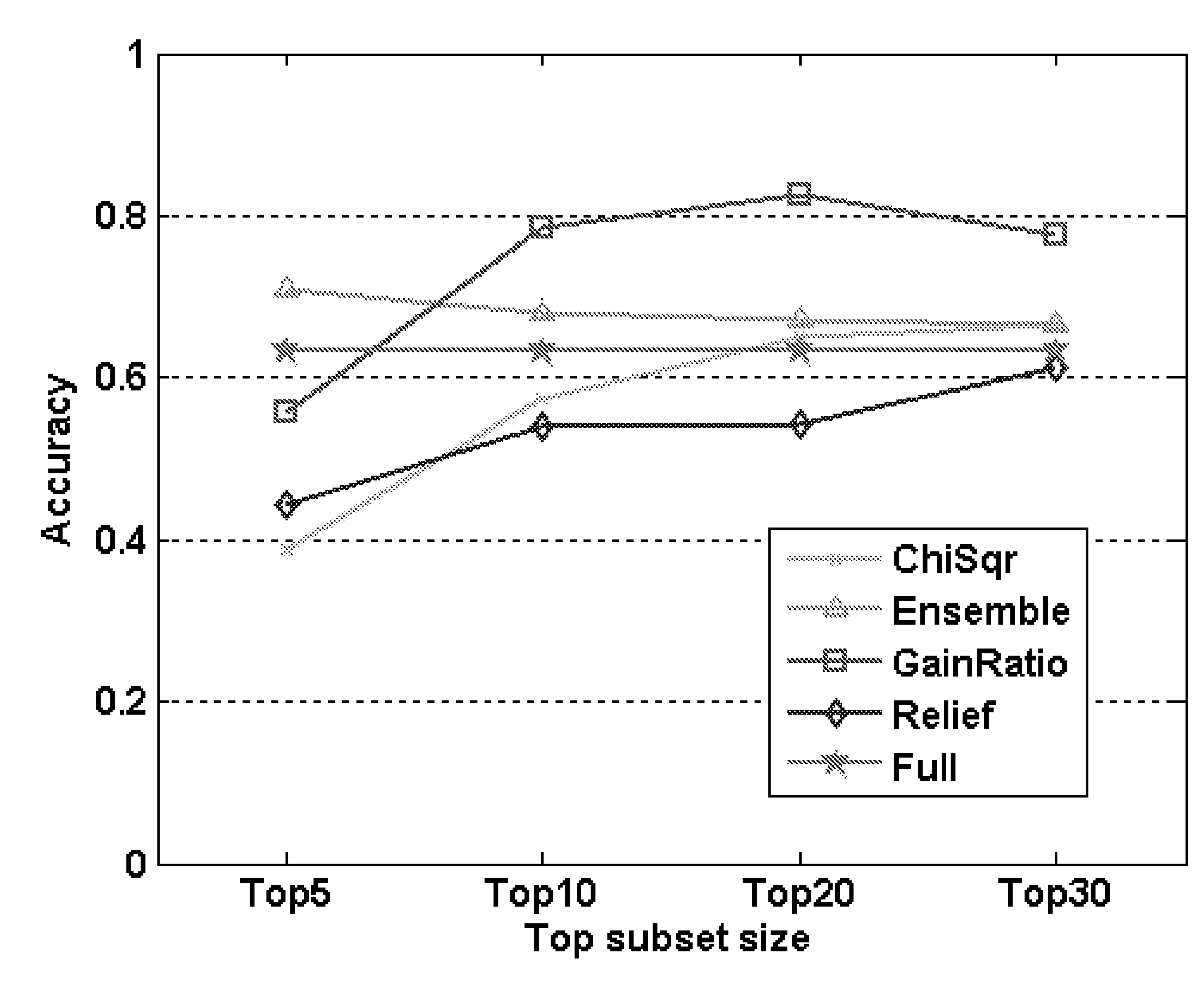
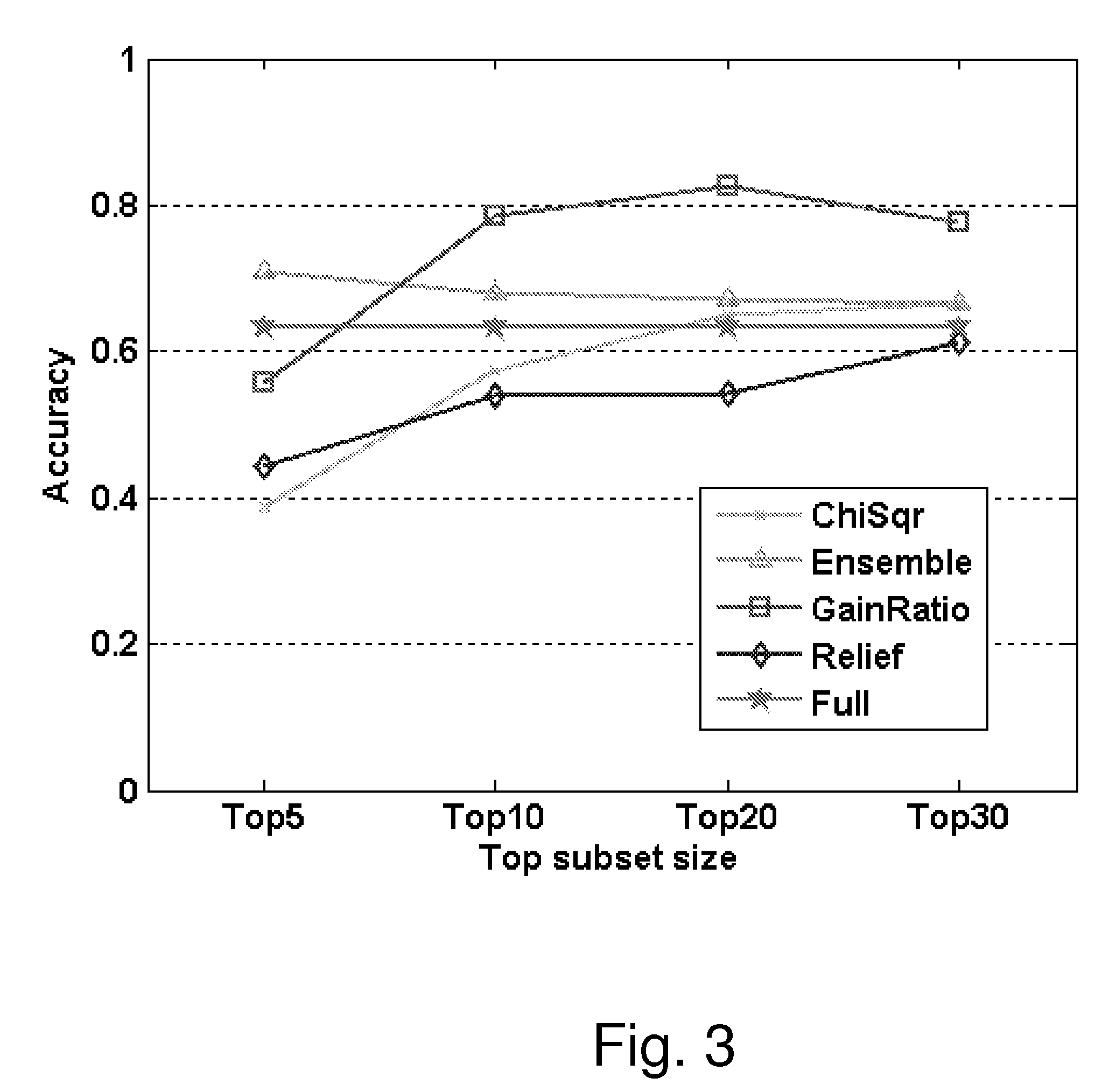
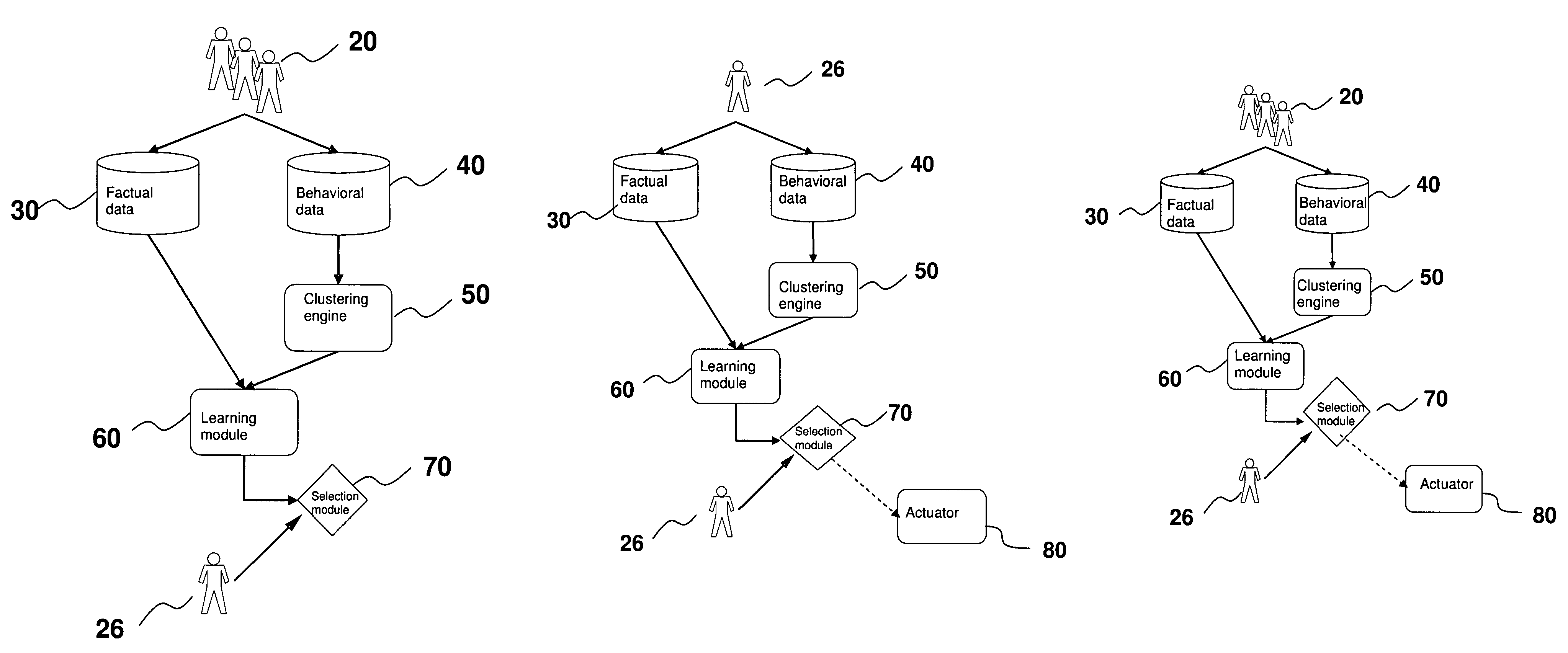
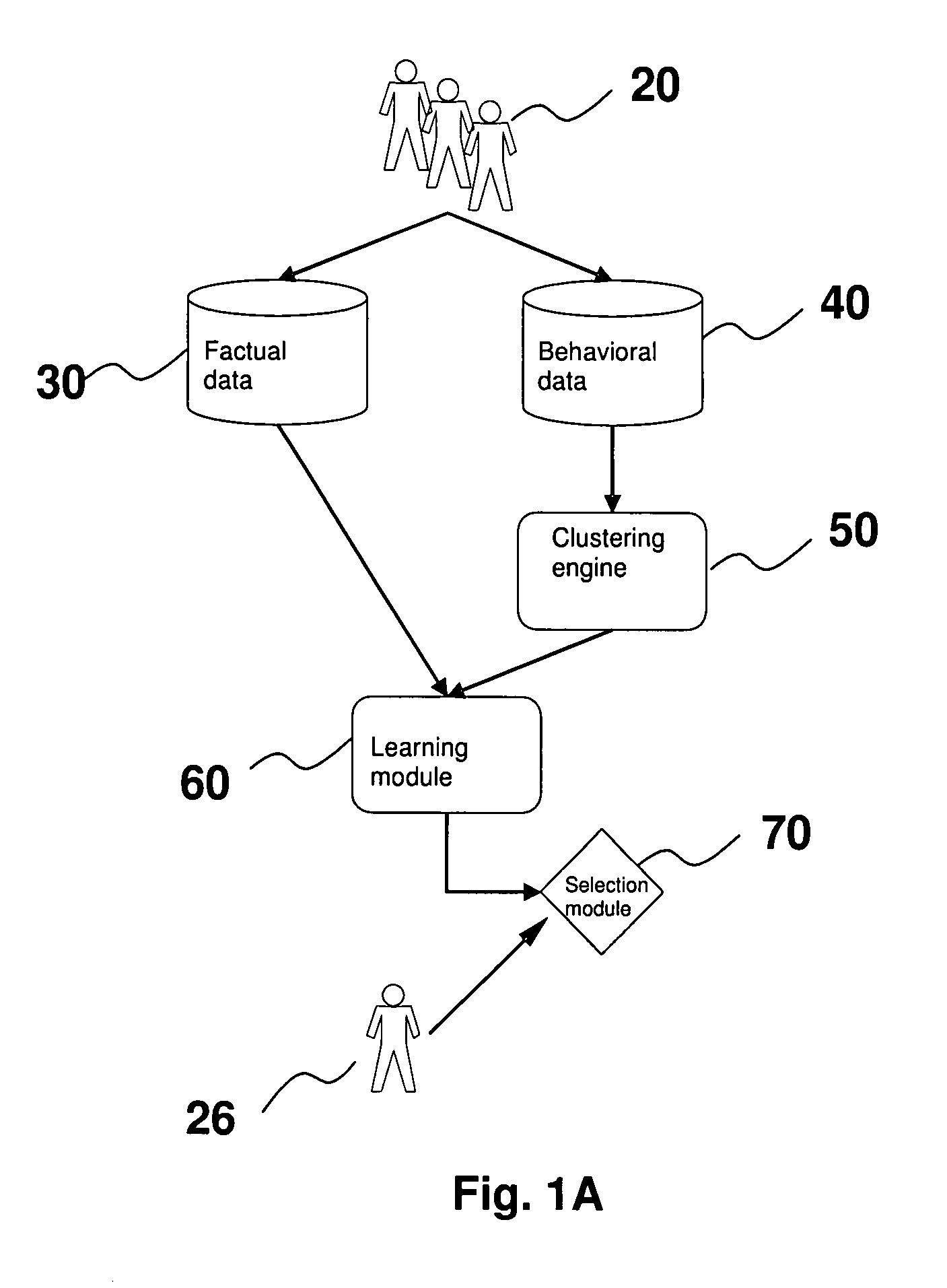
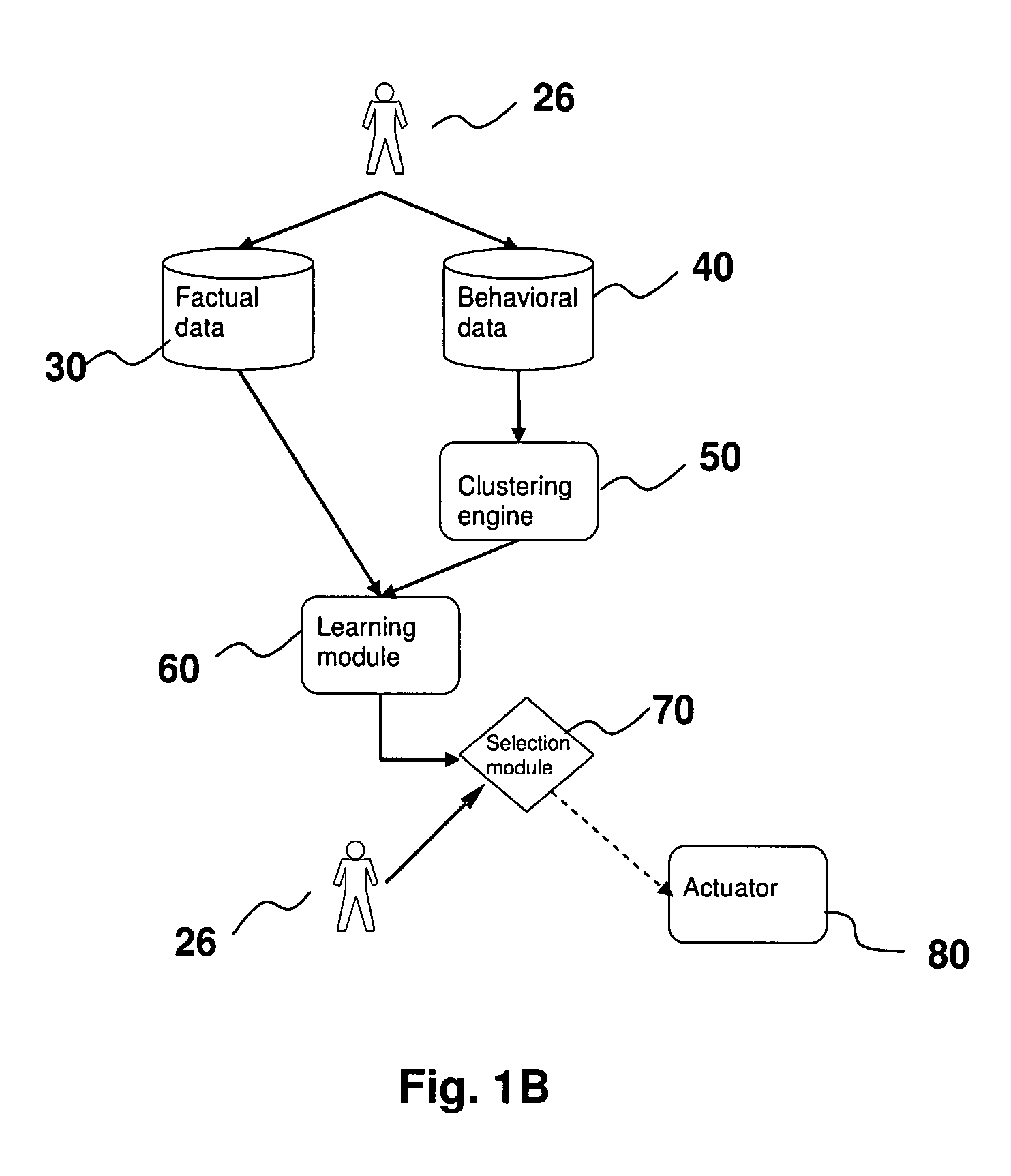
ActiveUS7340060B2Good forecastEasy to fillDigital computer detailsDigital dataSubject matterComputerized system
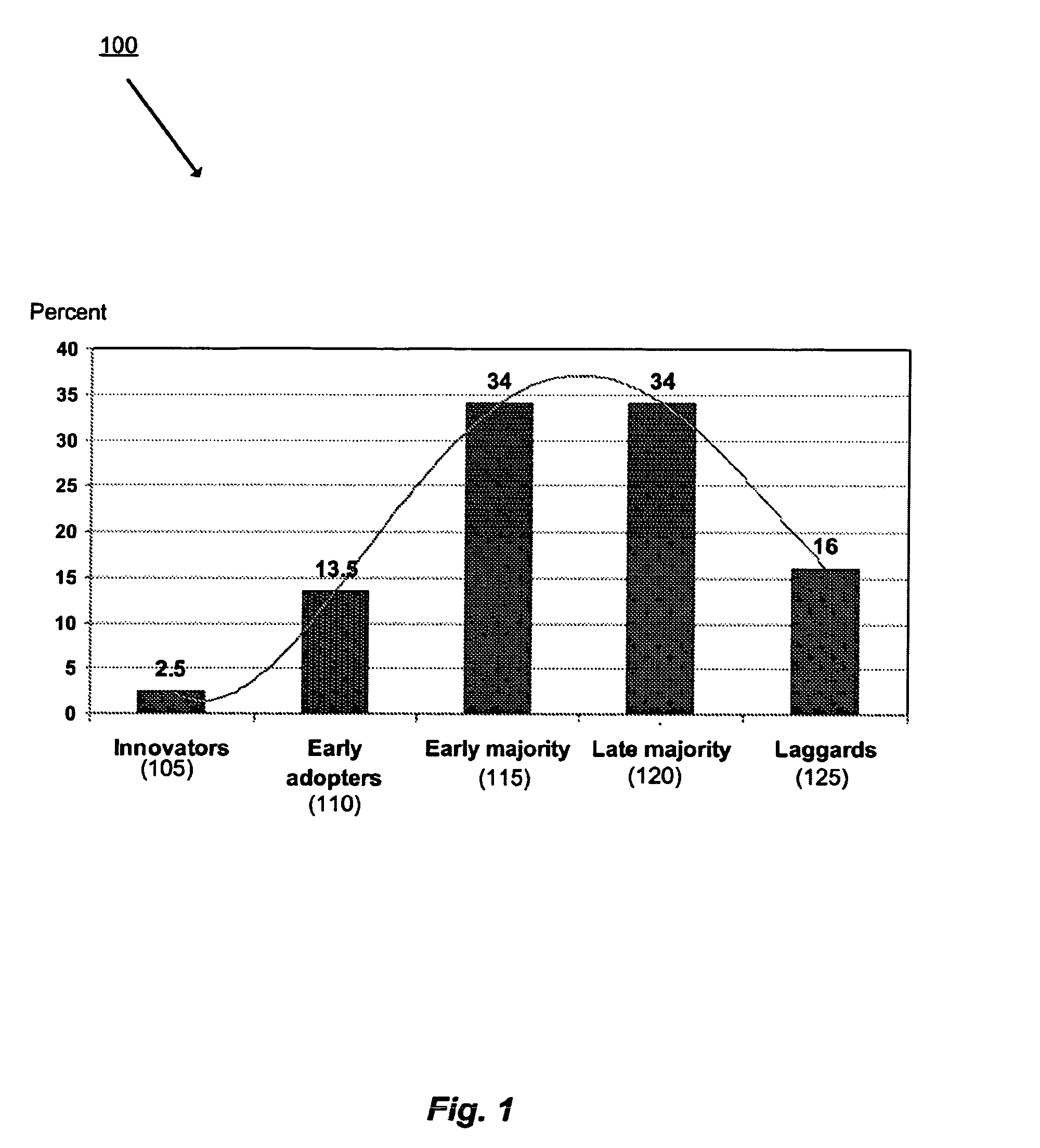
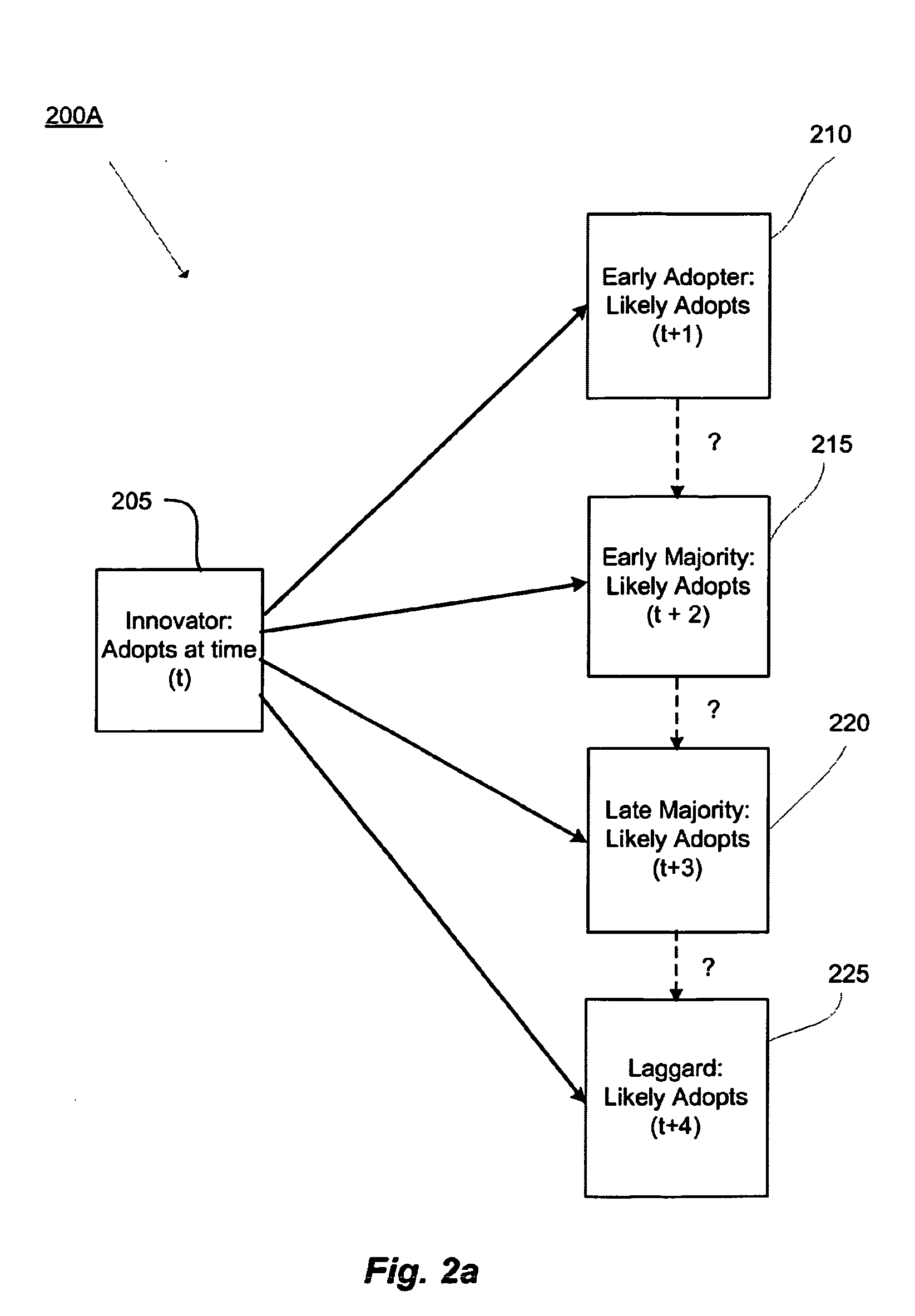
The present invention is a computer system that analyses the factual and behavioural data of a group of subjects, extracts the common behavioural patterns from the collection, and is capable of forecasting the behaviour of a new subject when his or her factual data are inputted to the system. It does so by first taking a collection of both the factual data and behavioural data from a group of subjects. A clustering engine is employed to compute a set of exemplars that concisely represent the population. Afterwards, the factual data of a subject, and the corresponding behavioural exemplar that he or she belongs, are fed to a learning module so that it can learn the mapping between the subject's factual data and behavioural exemplar. After learning, the system is able to predict the behaviour patterns when factual data of a new subject is presented.
Owner:BLACK BOX INTELLIGENCE
Computer immune system and method for detecting unwanted code in a computer system
InactiveUS20050268338A1Memory loss protectionError detection/correctionBehaviour patternVirtual machine
An automated analysis system detects malicious code within a computer system by generating and subsequently analyzing a behavior pattern for each computer program introduced to the computer system. Generation of the behavior pattern is accomplished by a virtual machine invoked within the computer system. An initial analysis may be performed on the behavior pattern to identify infected programs on initial presentation of the program to the computer system. The analysis system also stores behavior patterns and sequences with their corresponding analysis results in a database. Newly infected programs can be detected by analyzing a newly generated behavior pattern for the program with reference to a stored behavior pattern to identify presence of an infection or payload pattern.
Owner:PALO ALTO NETWORKS INC
Method and system for detecting malicious behavioral patterns in a computer, using machine learning
InactiveUS20070294768A1Memory loss protectionUnauthorized memory use protectionComputer wormComputerized system
Method for detecting malicious behavioral patterns which are related to malicious software such as a computer worm in computerized systems that include data exchange channels with other systems over a data network. Accordingly, hardware and / or software parameters are determined in the computerized system that is can characterize known behavioral patterns thereof. Known malicious code samples are learned by a machine learning process, such as decision trees and artificial neural networks, and the results of the machine learning process are analyzed in respect to the behavioral patterns of the computerized system. Then known and unknown malicious code samples are identified according to the results of the machine learning process.
Owner:DEUTSCHE TELEKOM AG
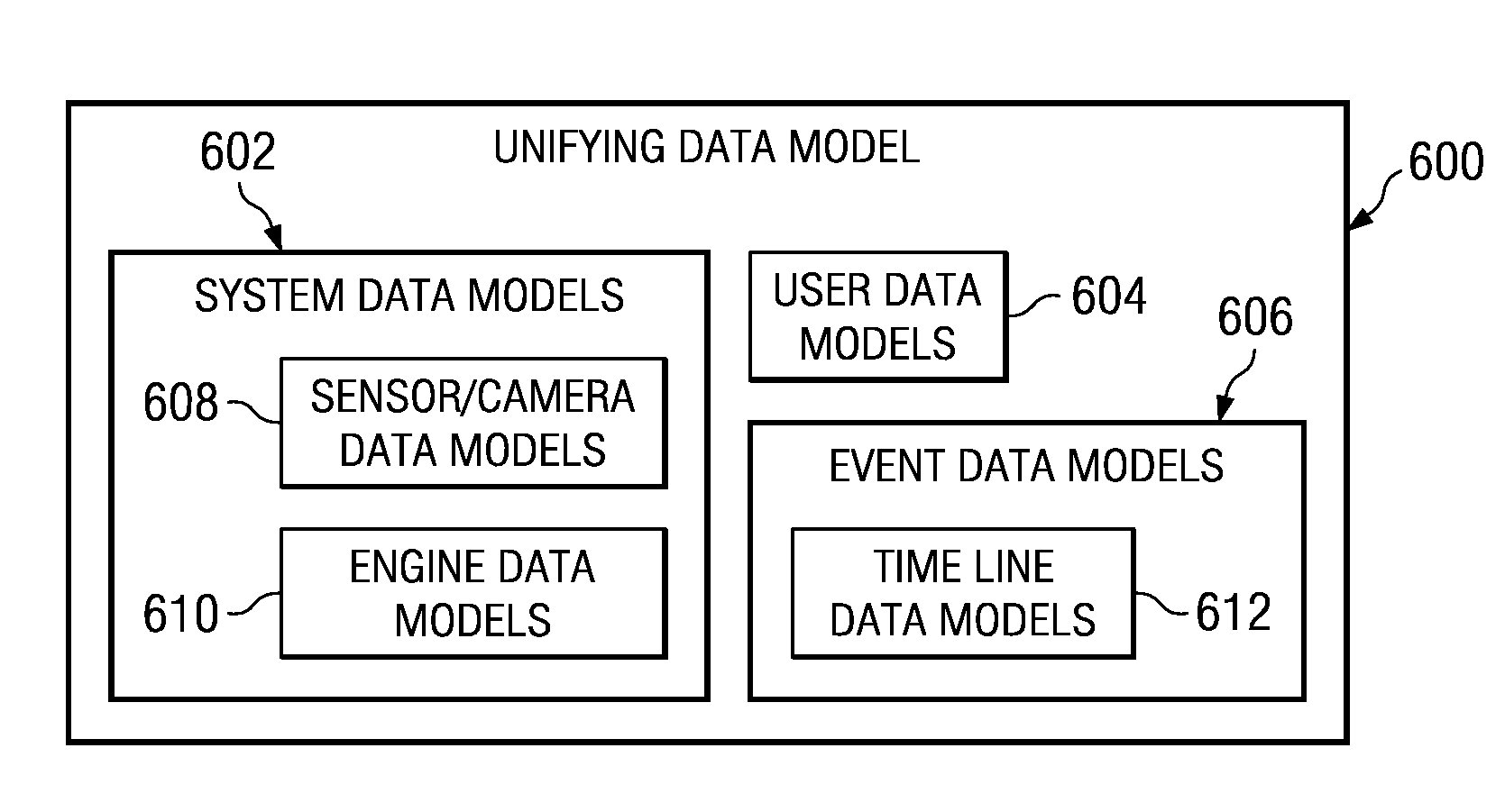
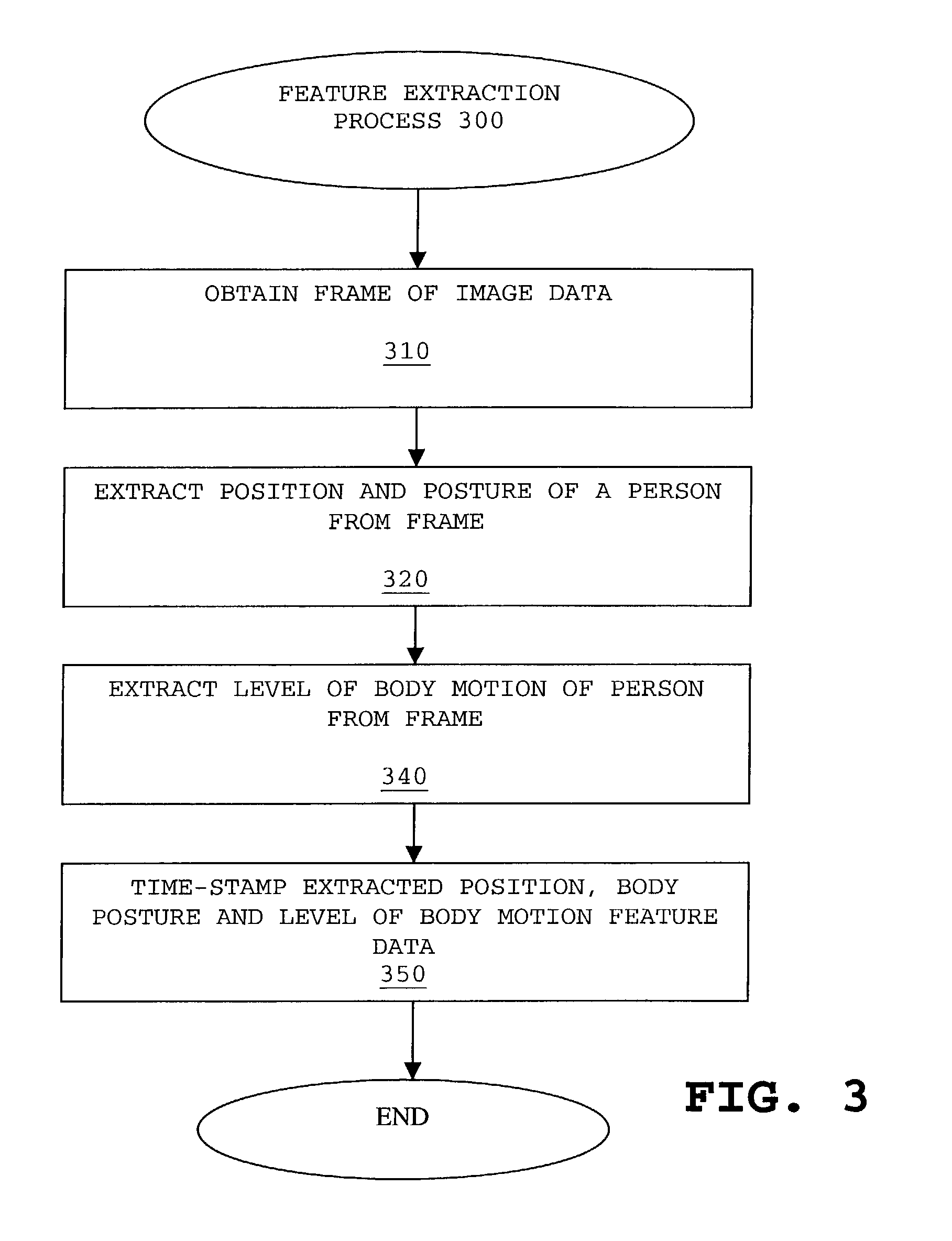
Method and apparatus for implementing digital video modeling to identify unexpected behavior
A computer implemented method, apparatus, and computer usable program product for identifying unexpected behavioral patterns. The process parses event data derived from video data to identify behavioral patterns, wherein the event data comprises metadata describing events occurring in a selected environment. The process analyzes the behavioral patterns to identify a set of expected behavioral patterns occurring in the selected environment, and generates an expected behavioral model using the expected behavioral patterns. Thereafter, the process forms a set of unexpected behavioral patterns from the behavioral patterns inconsistent with the expected behavioral model.
Owner:IBM CORP
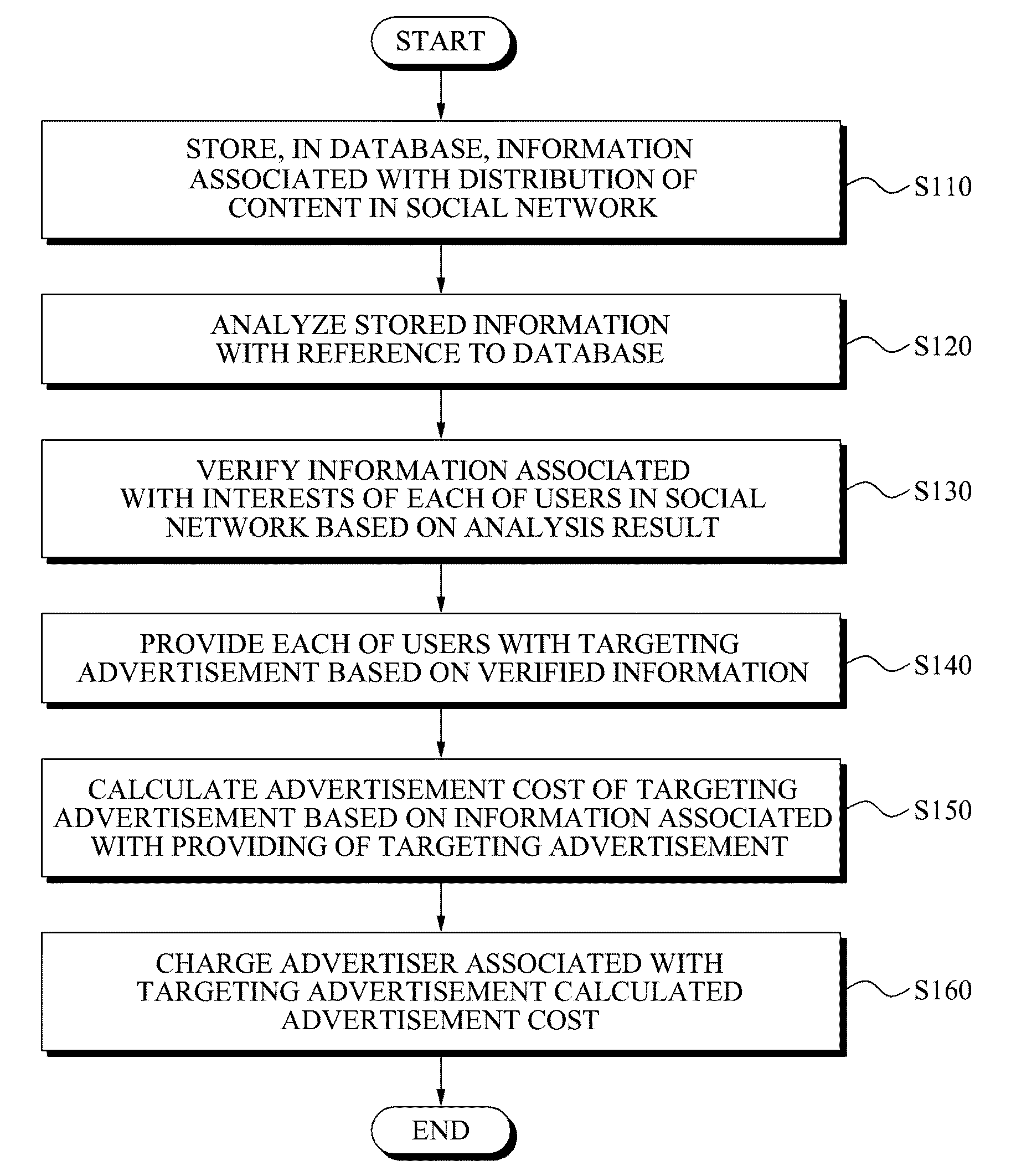
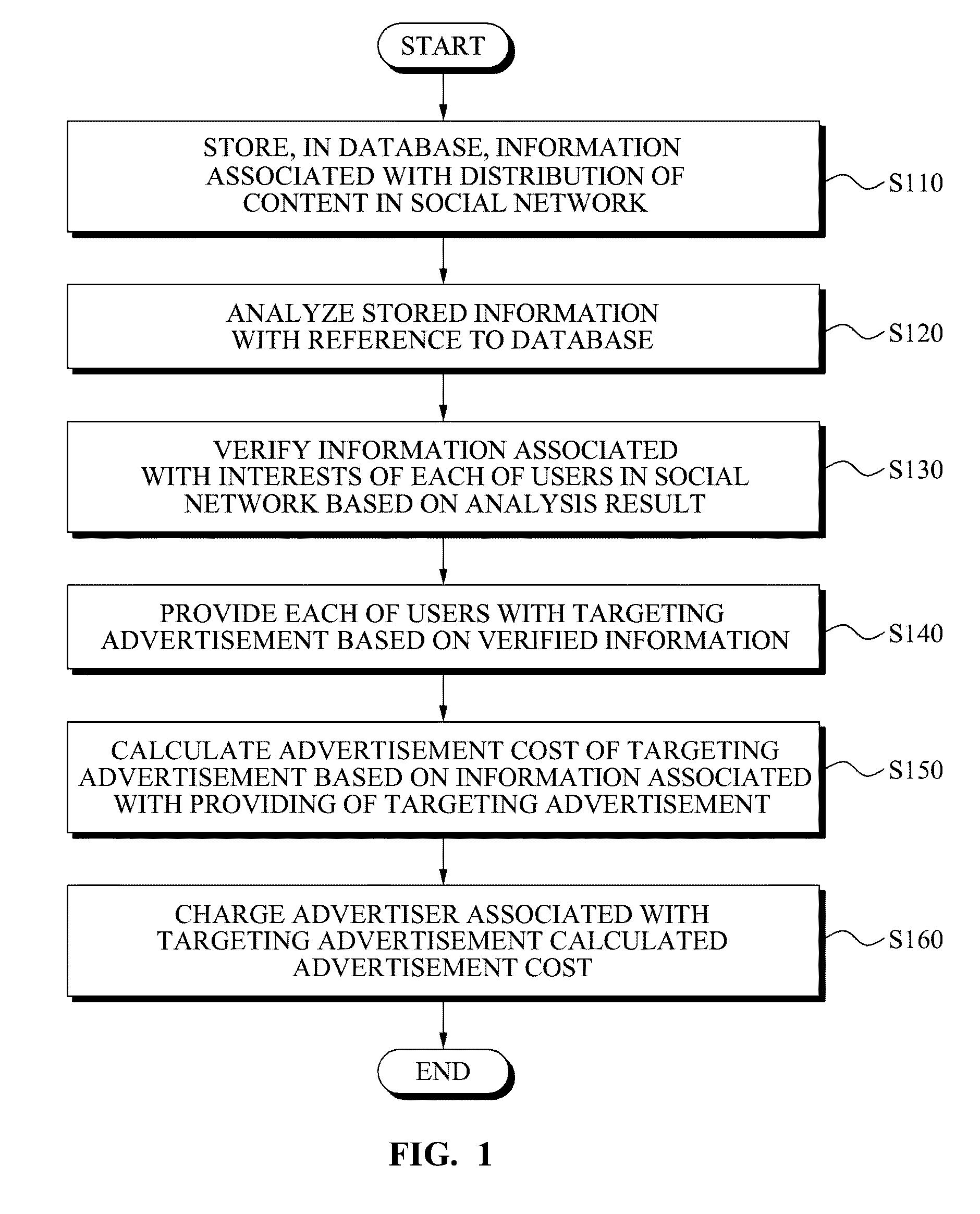
Method and system for providing targeting advertisement service in social network
InactiveUS20090216620A1Advertisement revenueMarket data gatheringReference databaseBehaviour pattern
Provided is a system for providing a targeting advertisement service in a social network, the system including: a database to store information associated with a distribution of a content in the social network; an analysis unit to analyze the stored information with reference to the database, and to verify a behavioral pattern or a matter of concern of each of users in the social network based on the analysis result; and an advertisement unit to provide each of the users with a targeting advertisement, based on the verified behavioral pattern or the matter of concern.
Owner:SAMJIN LND +1
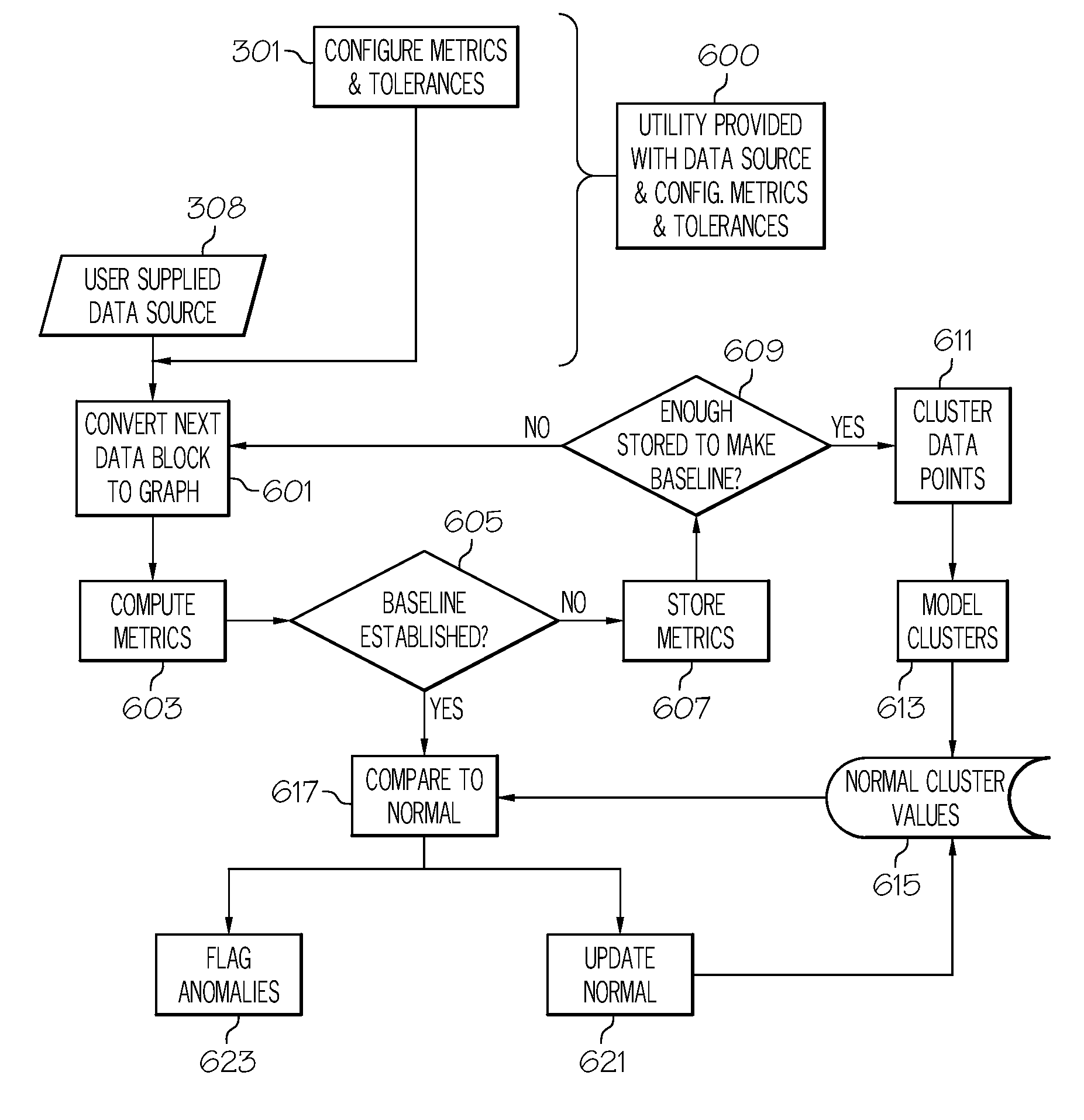
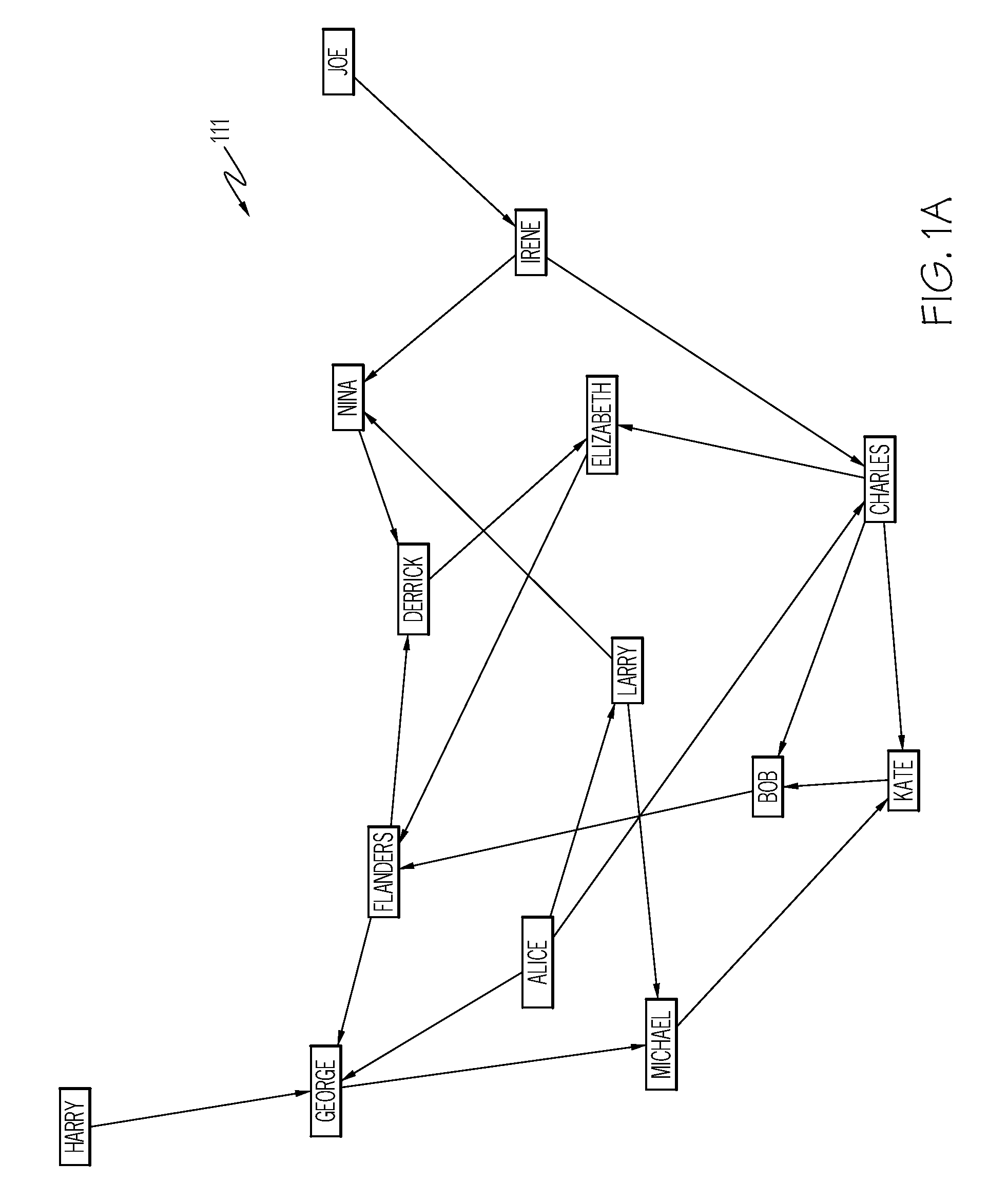
Dynamic SNA-based anomaly detection using unsupervised learning
ActiveUS7739211B2Easy to detectMemory loss protectionError detection/correctionAnomaly detectionBehaviour pattern
A method, system, and computer program product for enabling dynamic detection of anomalies occurring within an input graph representing a social network. More specifically, the invention provides an automated computer simulation technique that implements the combination of Social Network Analysis (SNA) and statistical pattern classification for detecting abnormal social patterns or events through the expanded use of SNA Metrics. The simulation technique further updates the result sets generated, based on observed occurrences, to dynamically determine what constitutes abnormal behavior, within the overall context of observed patterns of behavior.
Owner:NORTHROP GRUMMAN SYST CORP
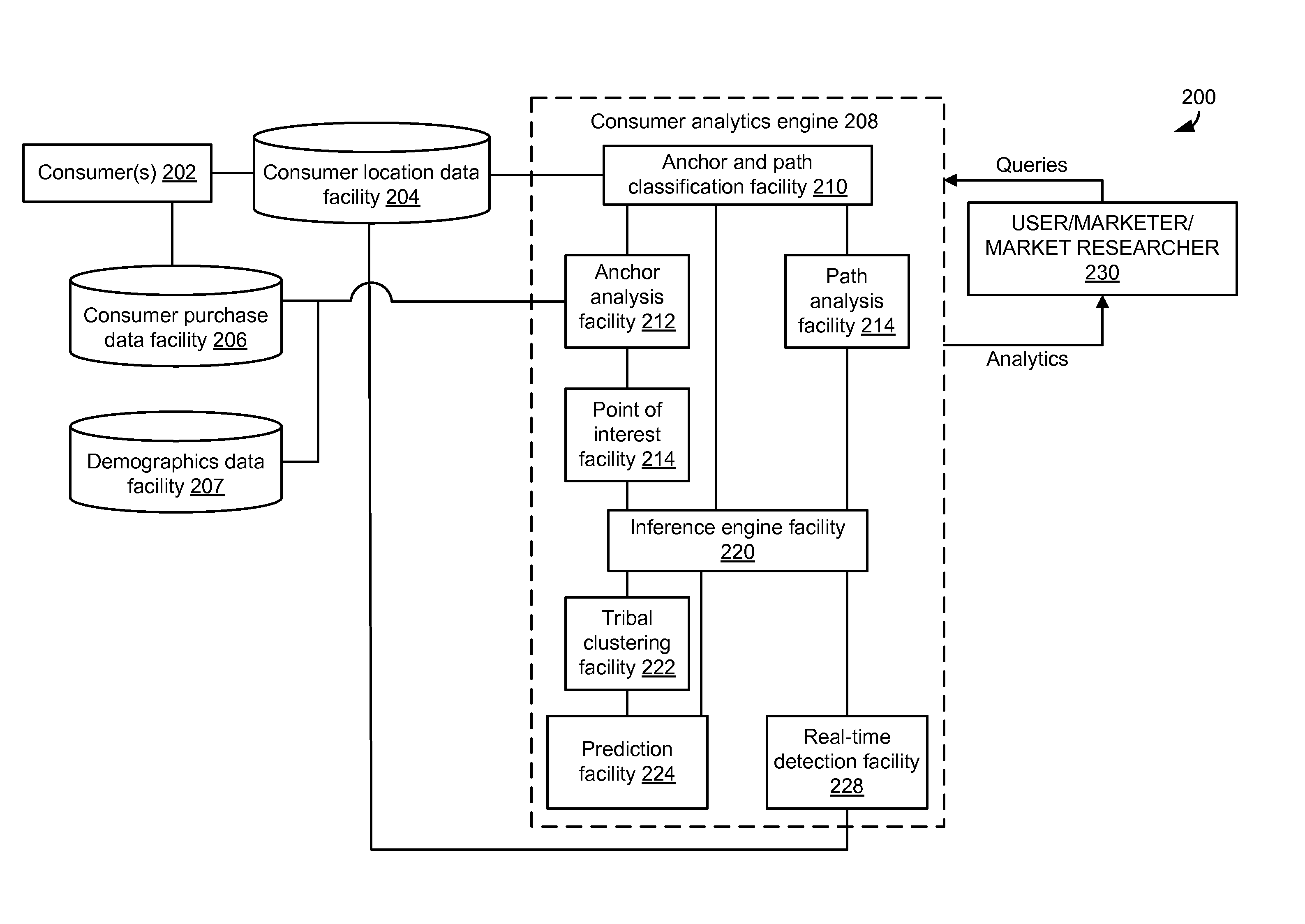
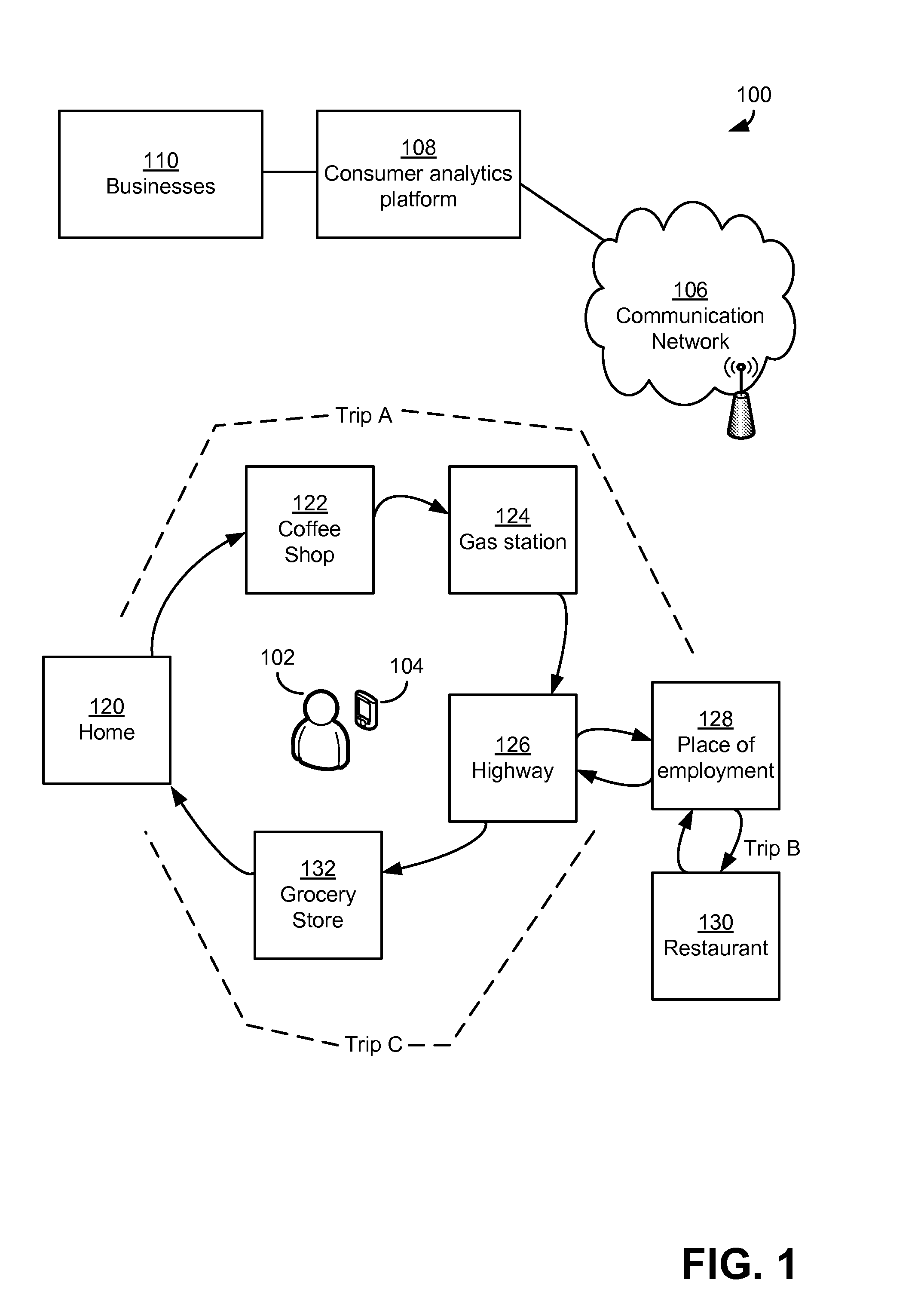
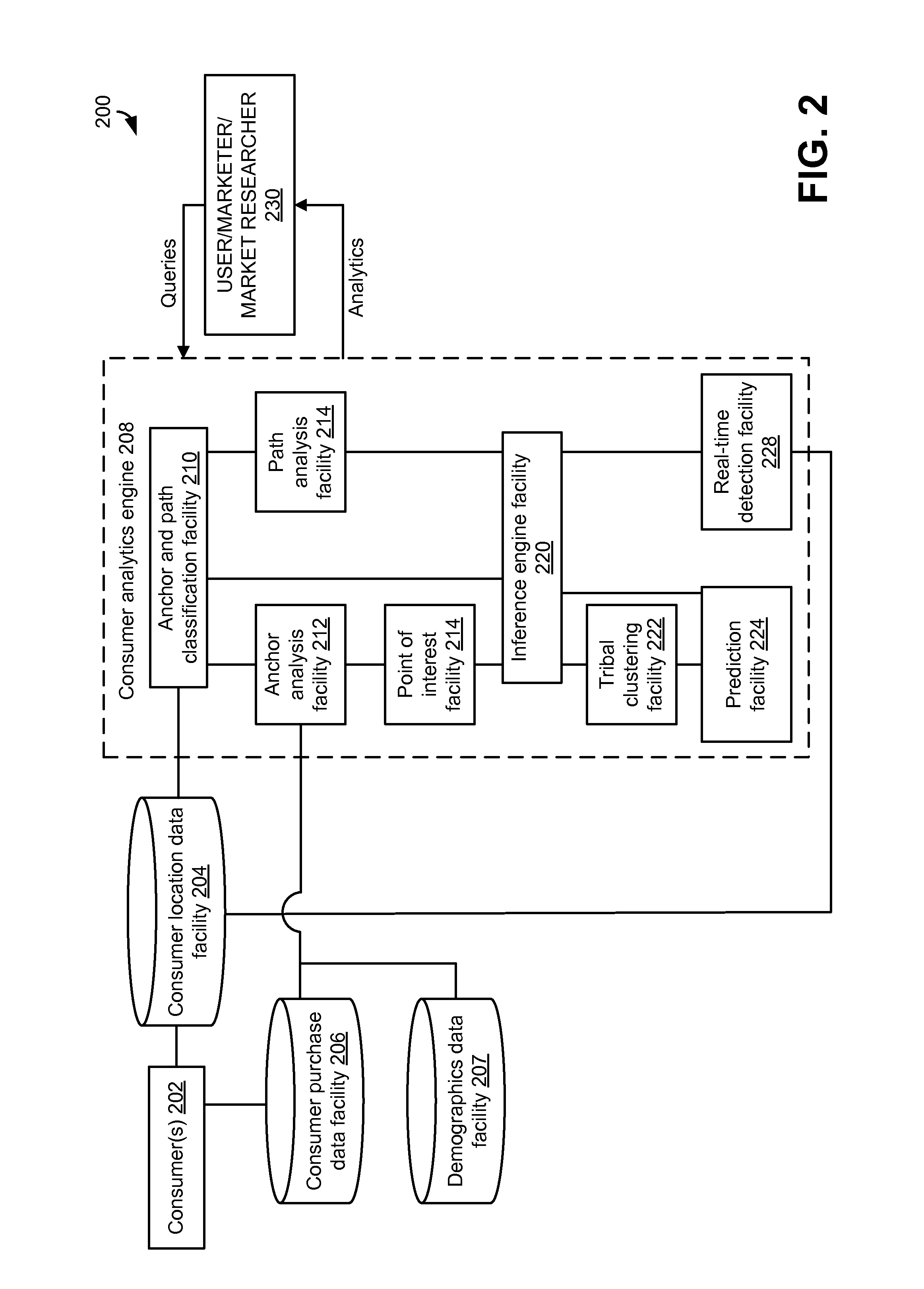
Analyzing consumer behavior using electronically-captured consumer location data
ActiveUS20110099046A1Location information based serviceMarketingBehavioral analyticsBehaviour pattern
In embodiments, methods and systems for consumer behavior analysis using electronically-captured consumer location data may be provided. The location data may be gathered for one or more consumers. The gathered data may be analyzed to determine behavior patterns or other characteristics of the one or more consumers. Further, inferences or predictions about consumers may be derived based on the characteristics. The inferences and predictions may be the basis of consumer analytics supplied to a business or other entity.
Owner:SERVICE MANAGEMENT GRP LLC
Detecting Behavioral Patterns and Anomalies Using Activity Data
ActiveUS20070156696A1Potential security breachSpecific access rightsError detection/correctionBehaviour patternComputer science
Activity data is analyzed or evaluated to detect behavioral patterns and anomalies. When a particular pattern or anomaly is detected, a system may send a notification or perform a particular task. This activity data may be collected in an information management system, which may be policy based. Notification may be by way e-mail, report, pop-up message, or system message. Some tasks to perform upon detection may include implementing a policy in the information management system, disallowing a user from connecting to the system, and restricting a user from being allowed to perform certain actions. To detect a pattern, activity data may be compared to a previously defined or generated activity profile.
Owner:NEXTLABS
Methods and systems for utilizing a time factor and/or asymmetric user behavior patterns for data analysis
Methods and systems for data mining and analysis that may be used for capturing user / entity behavior, providing influence filtering and / or providing recommendations. One particular use may be for providing, among other things, personalized recommendations. The methods and systems may include generating an influence network. The influence network may include a user's adoption behavior of items. The influence network may further include temporal aspects of information flow or diffusion of information through the network. The influence network may also include adoption time(s) of one or more item(s) between users / entities. Further, the influence network may include asymmetric user / entity adoption behavior. Methods and systems of influence filtering are provided that include generating asymmetric relationship(s) between users and providing a filtering module utilizing the asymmetric relationship(s) between user / entity.
Owner:NEC LAB AMERICA
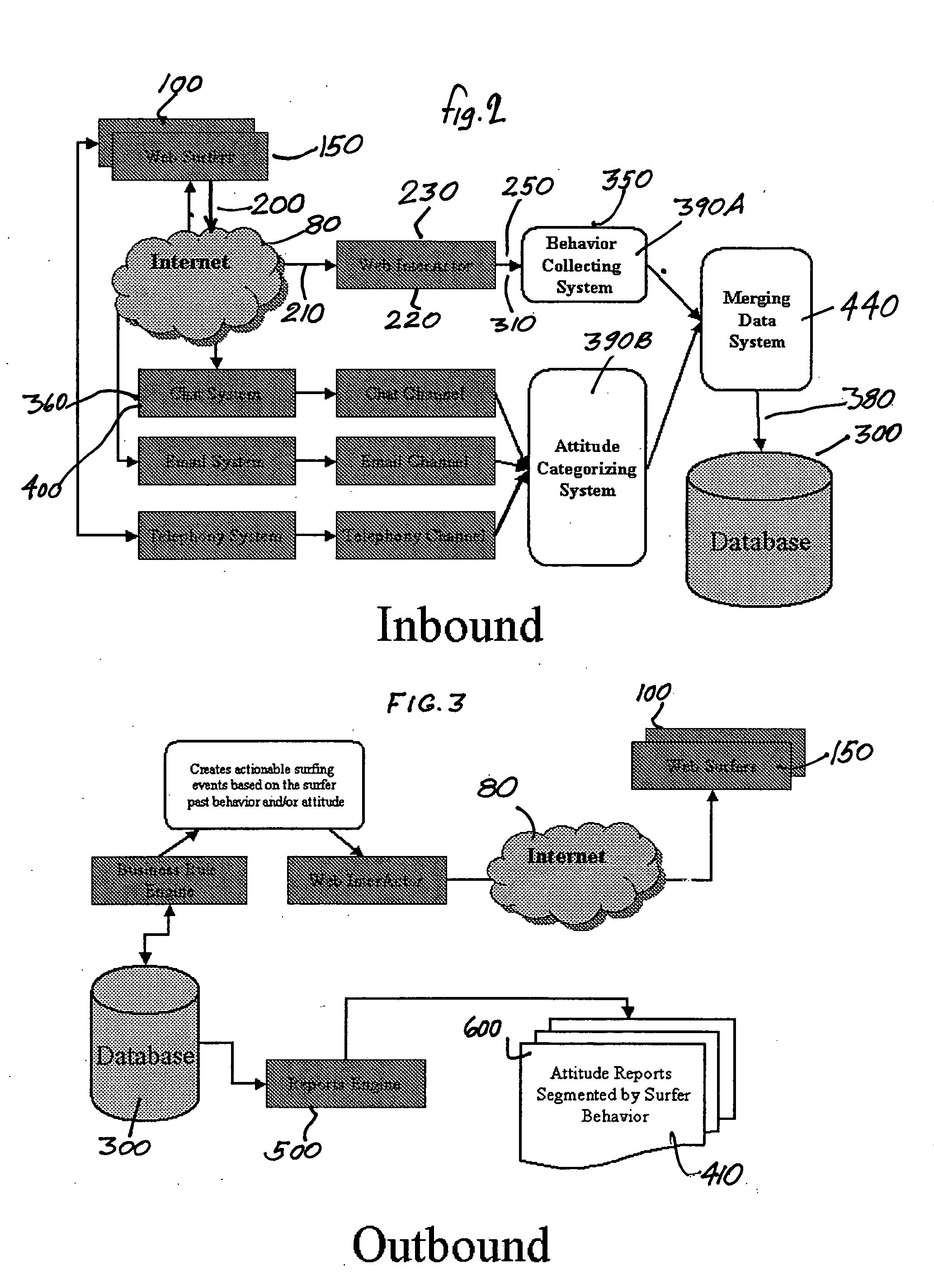
Process for determining recording, and utilizing characteristics of website users
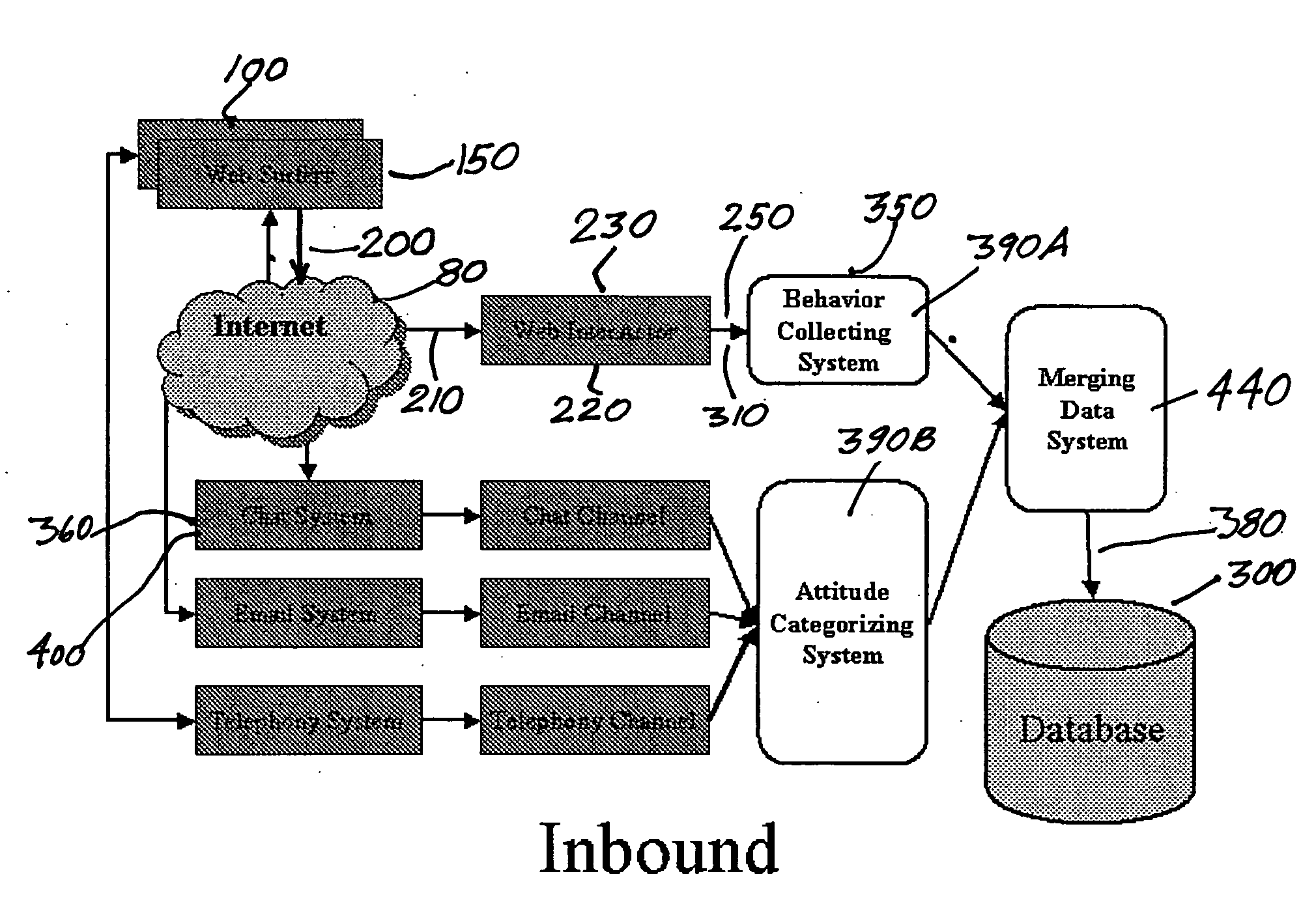
The subject invention comprises a process that provides for analyzing characteristics of website users, indicating the behavior modes and attitudes of particular individuals or entities using a given website on the internet from a perspective of both real-time and historical time, with attitude attributes and other relevant attributes extracted from characteristics of verbal colloquy on such website, where such attitude data relative to such website is extracted and interpreted and stored on an individual basis and potentially on a group basis for future reference use purposes. Among other means, attitude is obtained in this process from interactive real-time communications, usually bi-directional live communication, that the website user conducts on website visits, or through emails or telephone callings, or any other mode of communication.
Owner:KLAWON KEVIN
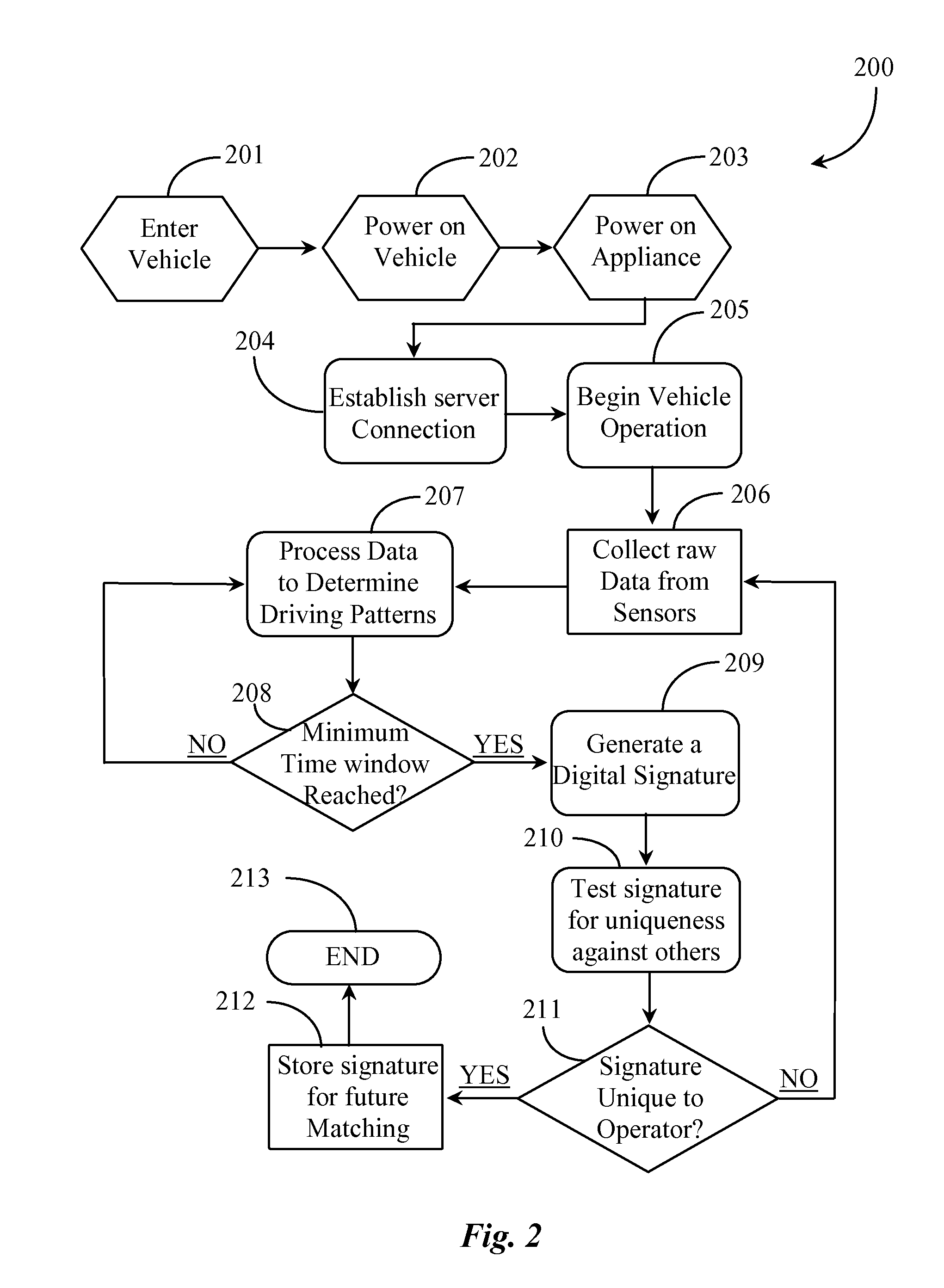
Driver Identification System and Methods
ActiveUS20120226421A1Improve securityReliable informationFinanceRegistering/indicating working of vehiclesAnalysis dataDriver/operator
A system for developing a digital signature identifying a specific person operating a vehicle uses a computerized appliance and software or firmware executing from a non-transitory medium on the computerized appliance and providing a first function collecting raw data regarding vehicle operation from sensors implemented in the vehicle during operation by the specific person, a second function analyzing the raw data and identifying at least one pattern of behavior associated with the specific person; and a third function developing a digital signature from the analyzed data for that specific person.
Owner:AUTOMATIC LABS
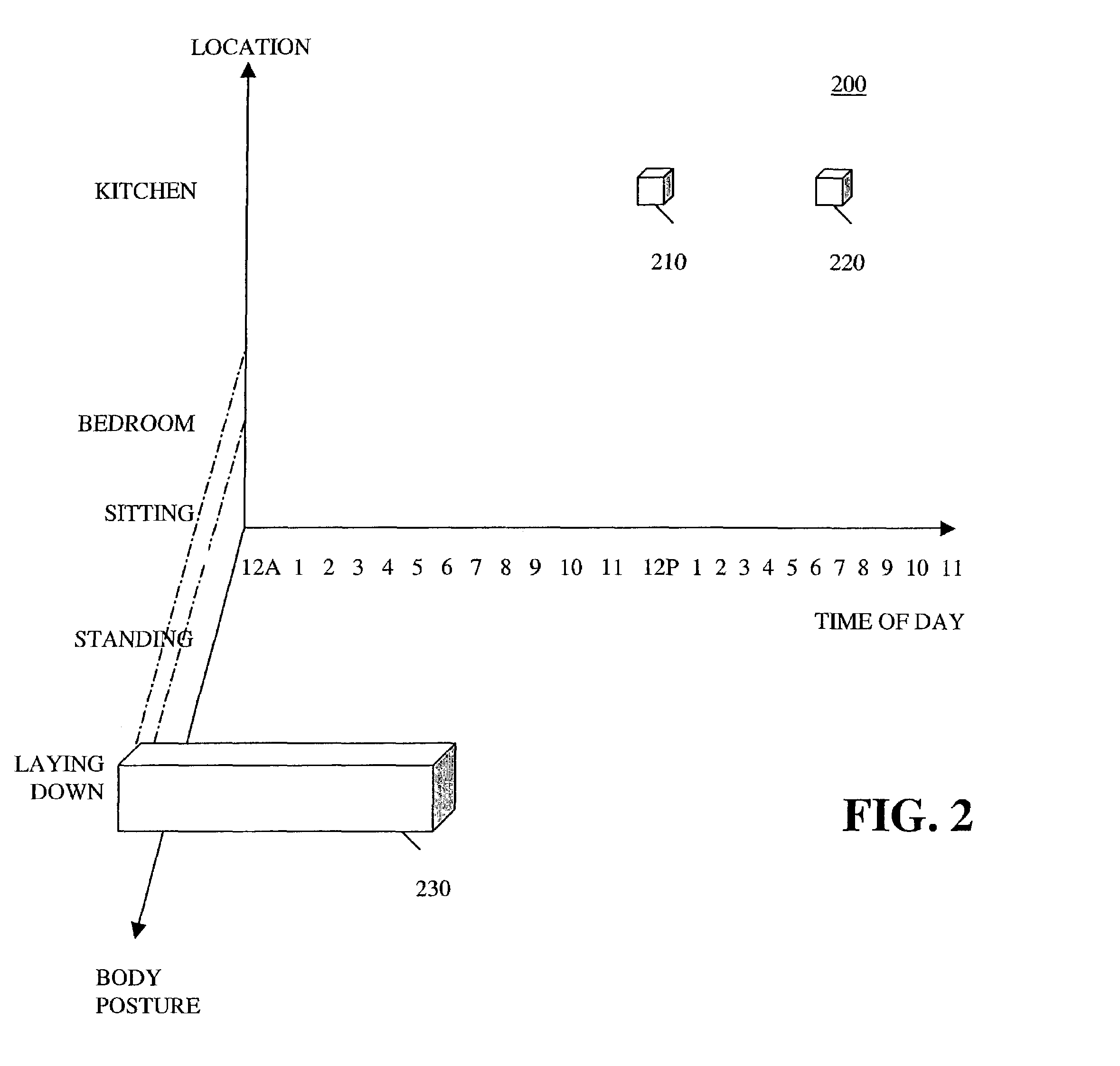
Method and apparatus for detecting an event based on patterns of behavior
A system and apparatus are disclosed for modeling patterns of behavior of humans or other animate objects and detecting a violation of a repetitive pattern of behavior. The behavior of one or more persons is observed over time and features of the behavior are recorded in a multi-dimensional space. Over time, the multi-dimensional data provides an indication of patterns of human behavior. Activities that are repetitive in terms of time, location and activity, such as sleeping and eating, would appear as a Gaussian distribution or cluster in the multi-dimensional data. Probability distribution functions can be analyzed using known Gaussian or clustering techniques to identify repetitive patterns of behavior and characteristics thereof, such as a mean and variance. Deviations from repetitive patterns of behavior can be detected and an alarm can be triggered, if appropriate.
Owner:SIGNIFY HLDG BV
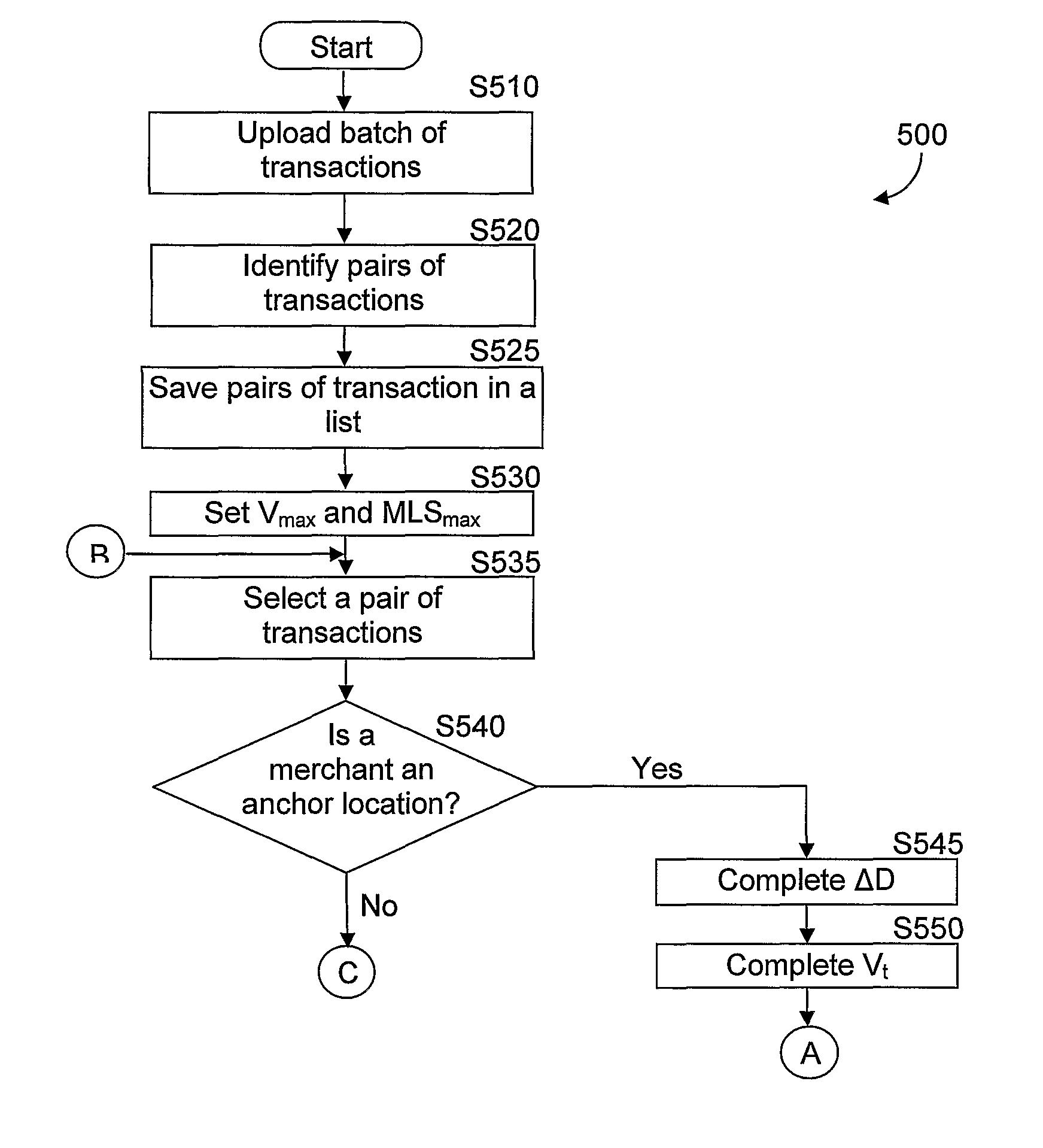
Location based authentication system
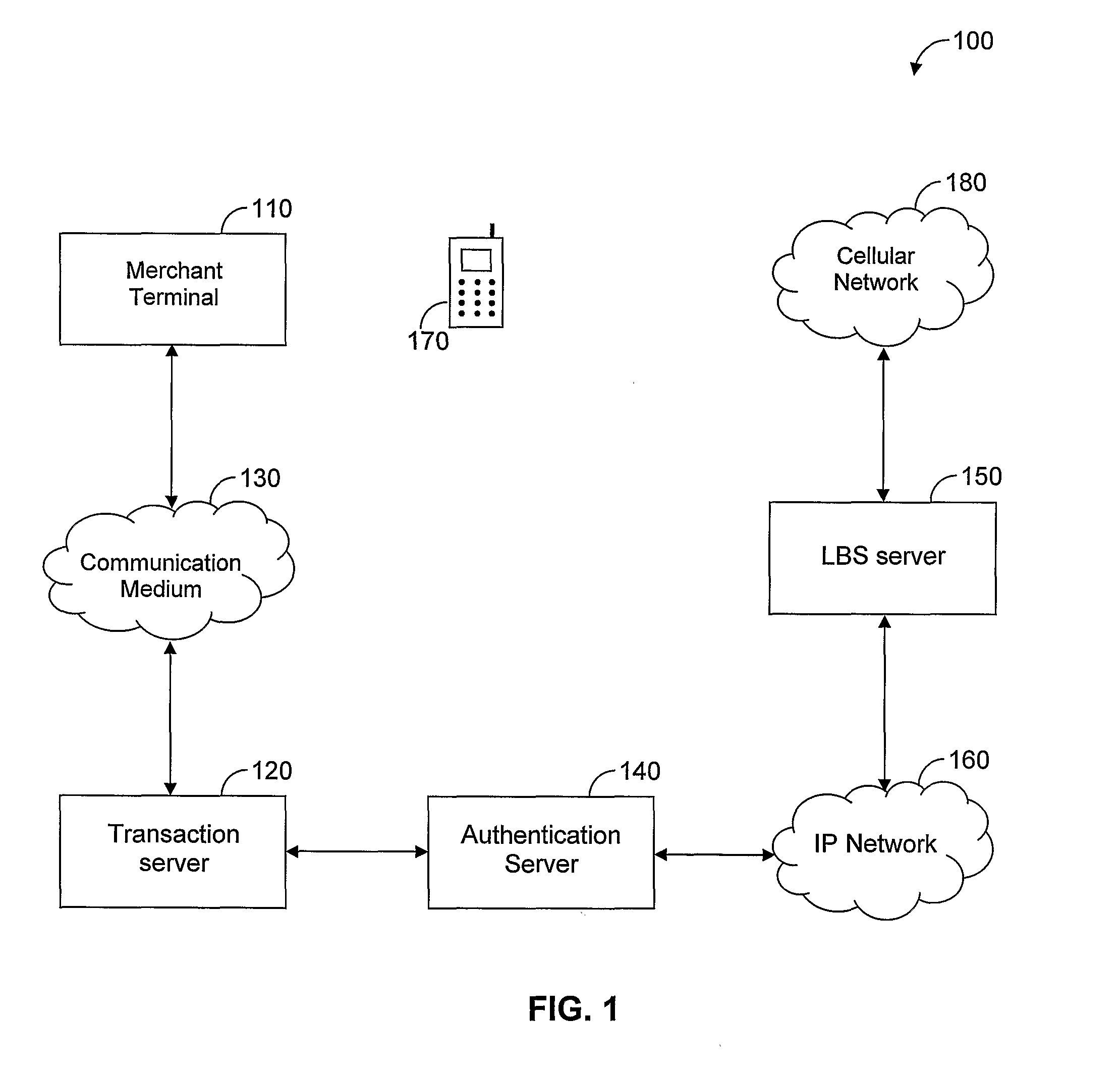
InactiveUS8285639B2Optimize locationFinanceBuying/selling/leasing transactionsBehaviour patternCard holder
An improved location based authentication (LBA) system for detecting fraudulent transactions committed by means of misuse of payment cards is disclosed. The improved LBA system performs a series of transaction analysis and generates a fraud-score which provides an indication as whether to authorize an attempted transaction. The system is designed to increase profitability of credit card companies by reducing the accumulated losses due to fraud. In one embodiment, the system detects fraud by analyzing the behavior patterns of card holders and merchants.
Owner:MCONFIRM
System and method for monitoring behavior patterns
A system and method for monitoring behavior patterns which effectively distinguishes between alarming and non-alarming behavior patterns, includes at least one sensor for detecting behavior patterns, a memory device coupled to the sensor, for storing standard behavior patterns, and a processor, coupled to the memory device, for comparing standard behavior patterns with detected behavior patterns, and causing a response to be activated when standard behavior patterns and detected behavior patterns have a predetermined relationship.
Owner:IBM CORP
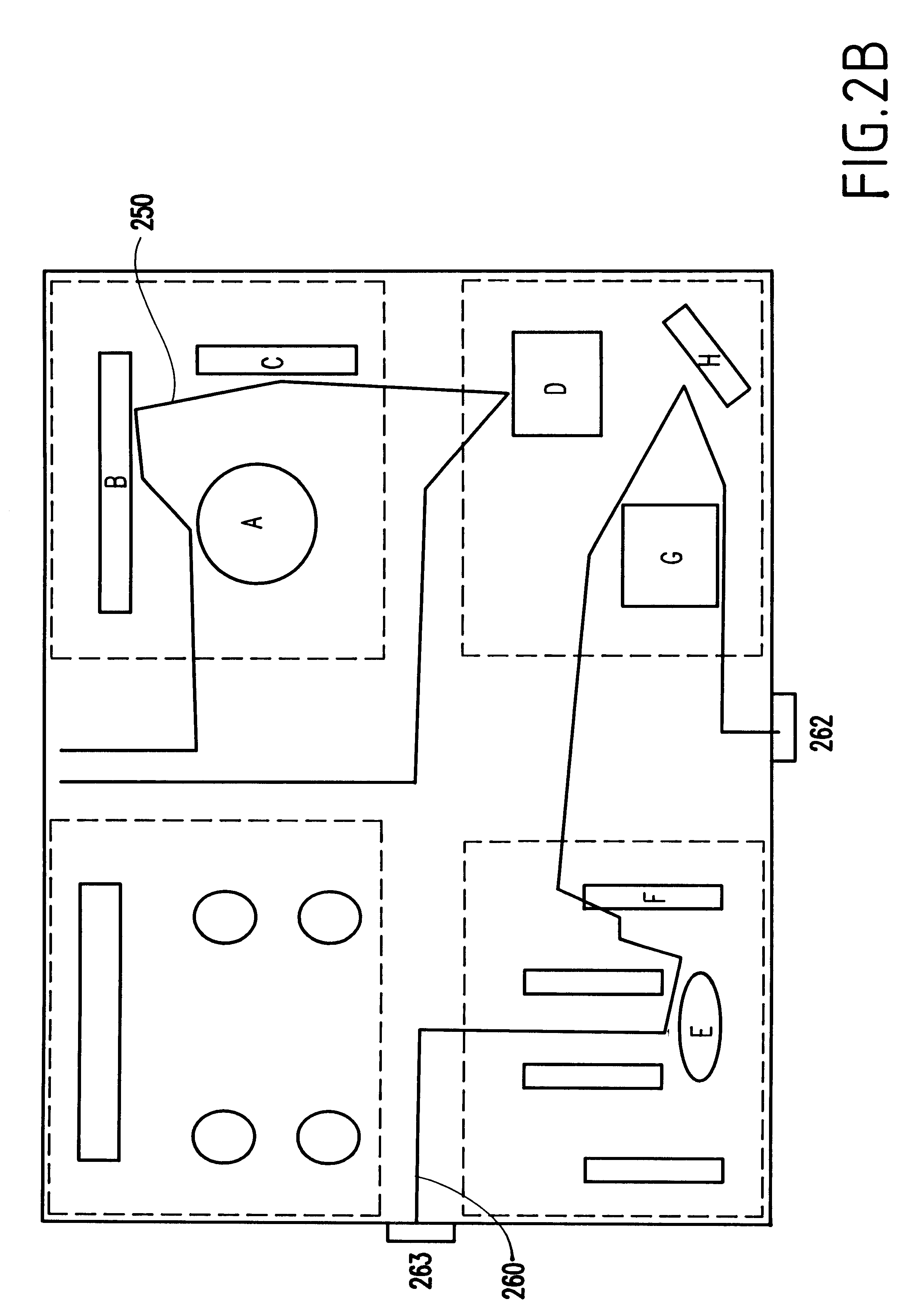
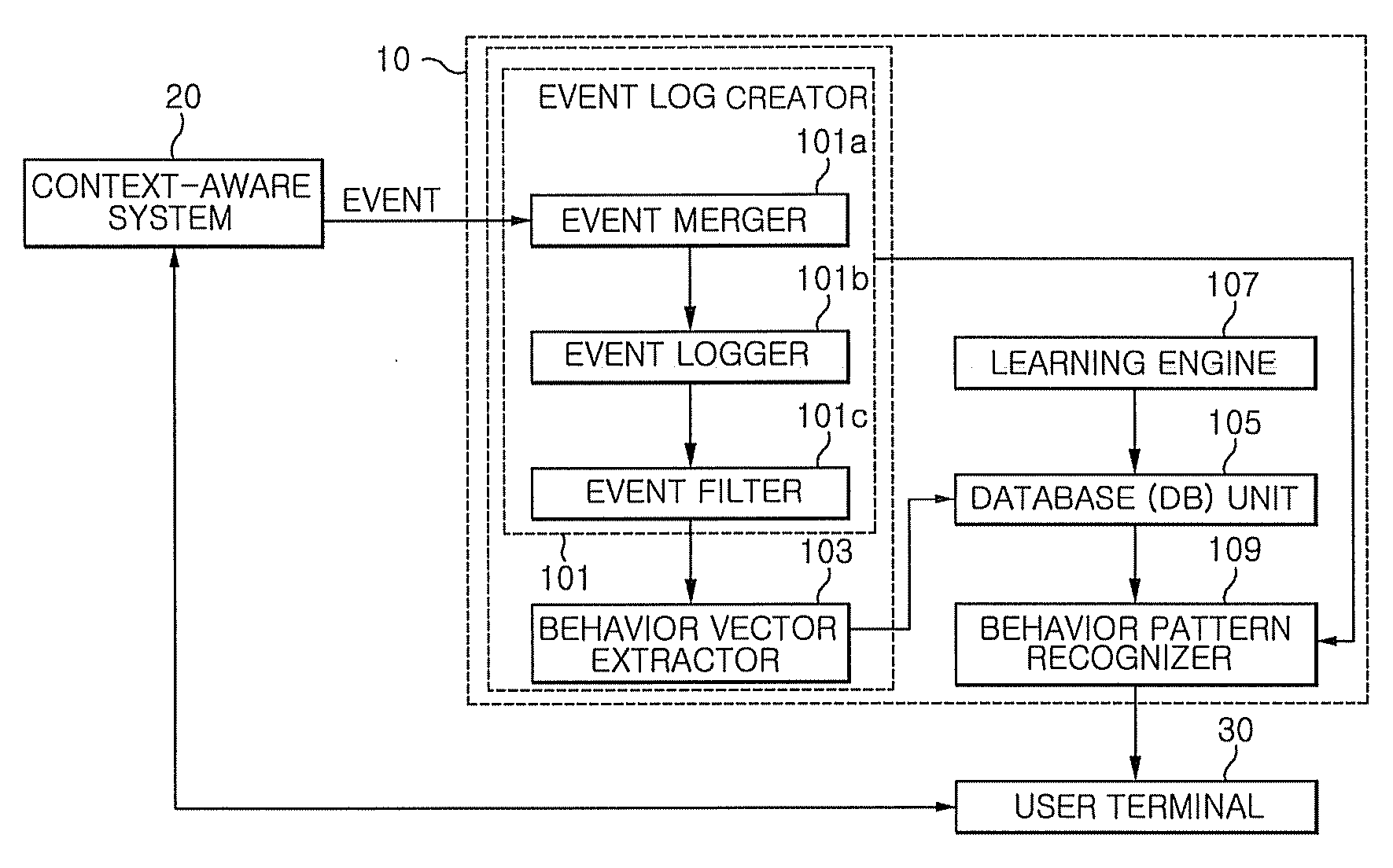
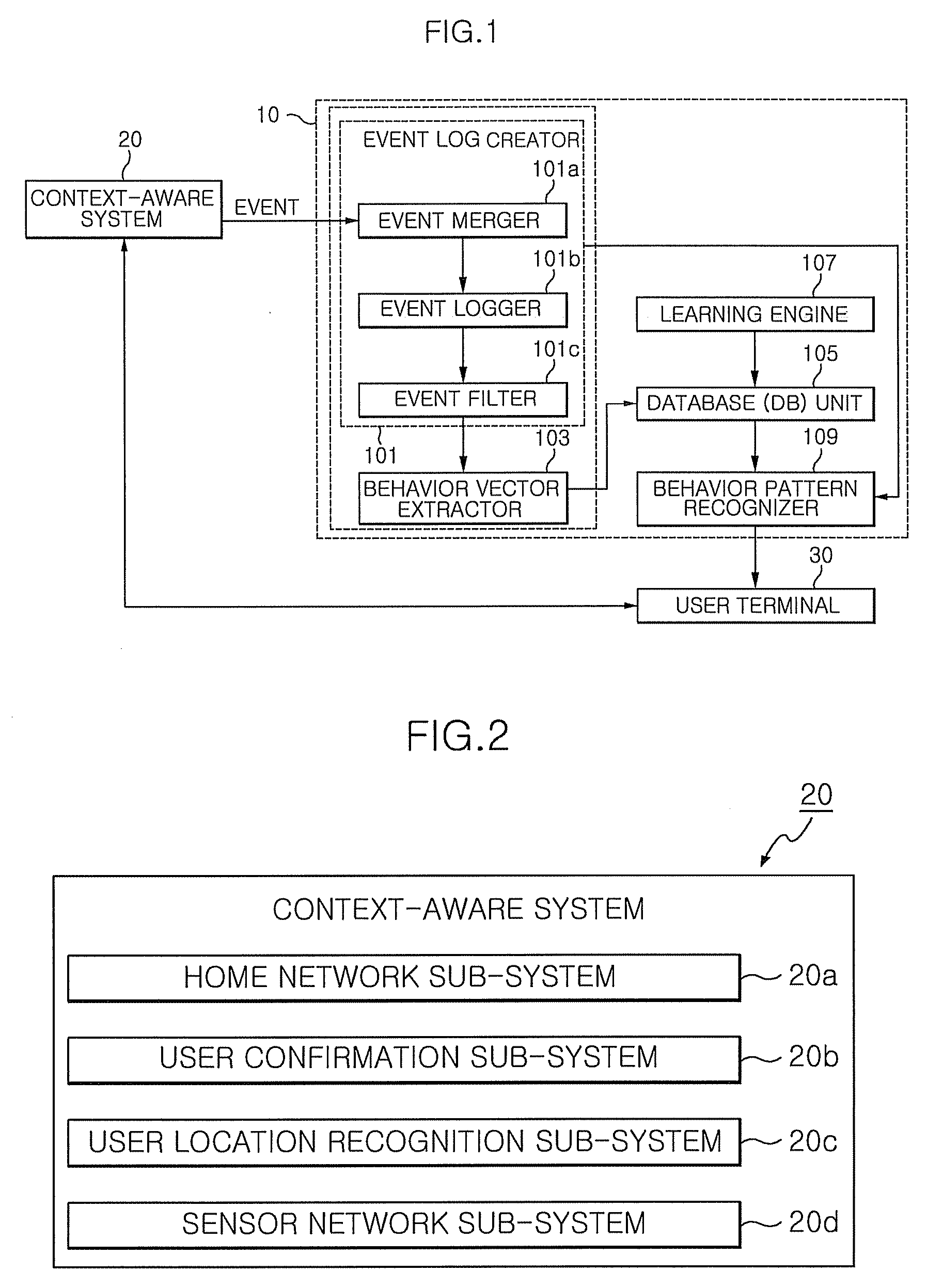
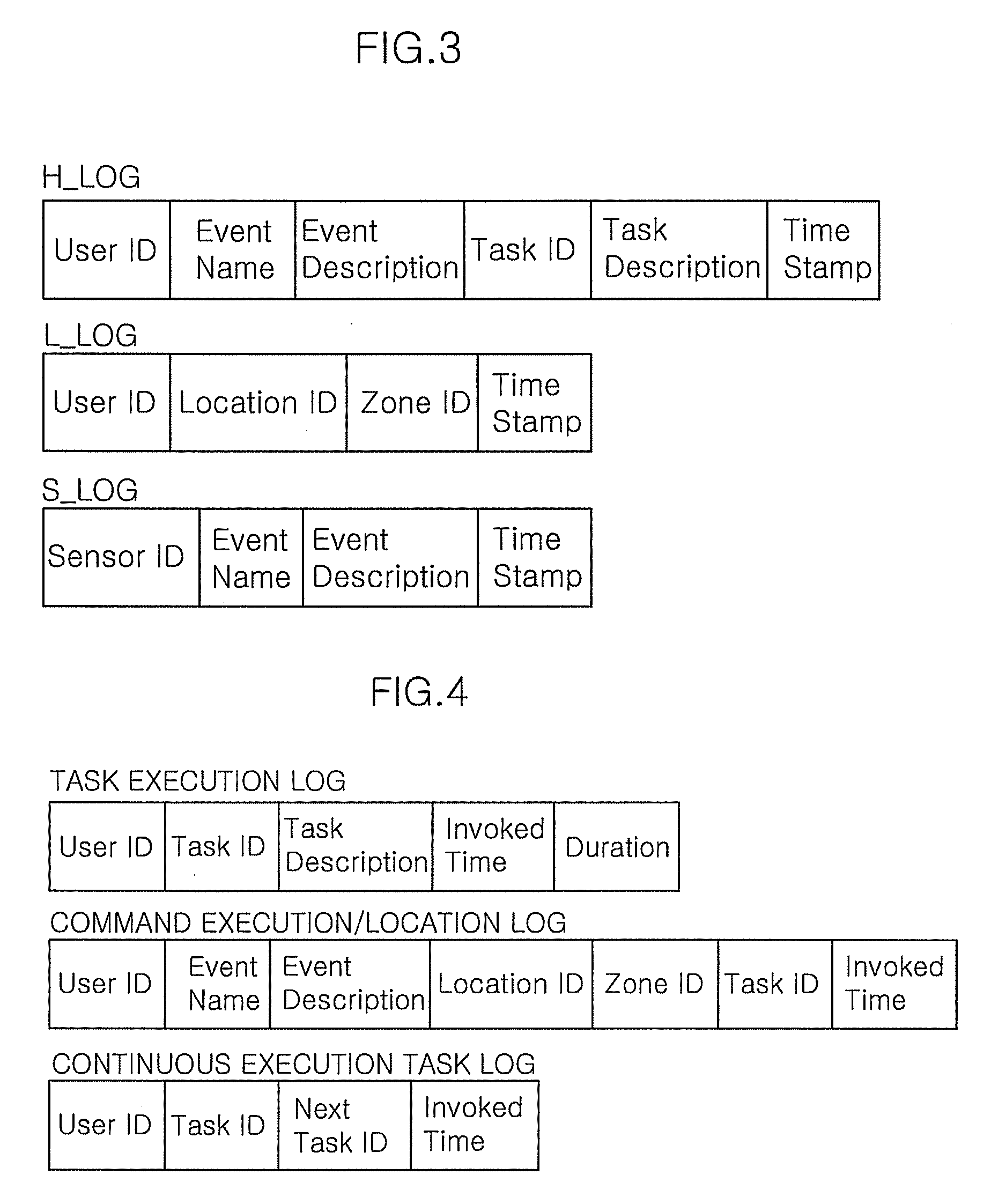
Apparatus and method of constructing user behavior pattern based on event log generated from context-aware system environment
InactiveUS20090070283A1Easy and fast constructionError detection/correctionMachine learningBehaviour patternData mining
Disclosed is an apparatus and method of constructing a user behavior pattern based on an event log that is a record of events generated in a context-aware system environment. An apparatus and method of constructing a user behavior pattern based on an event log according to an embodiment of the invention intelligently and actively provides the most applicable service in consideration of a specific user and a location thereof to a user, on the basis of a constructed user behavior pattern.
Owner:ELECTRONICS & TELECOMM RES INST
Device and Method for Remotely Monitoring Animal Behavior
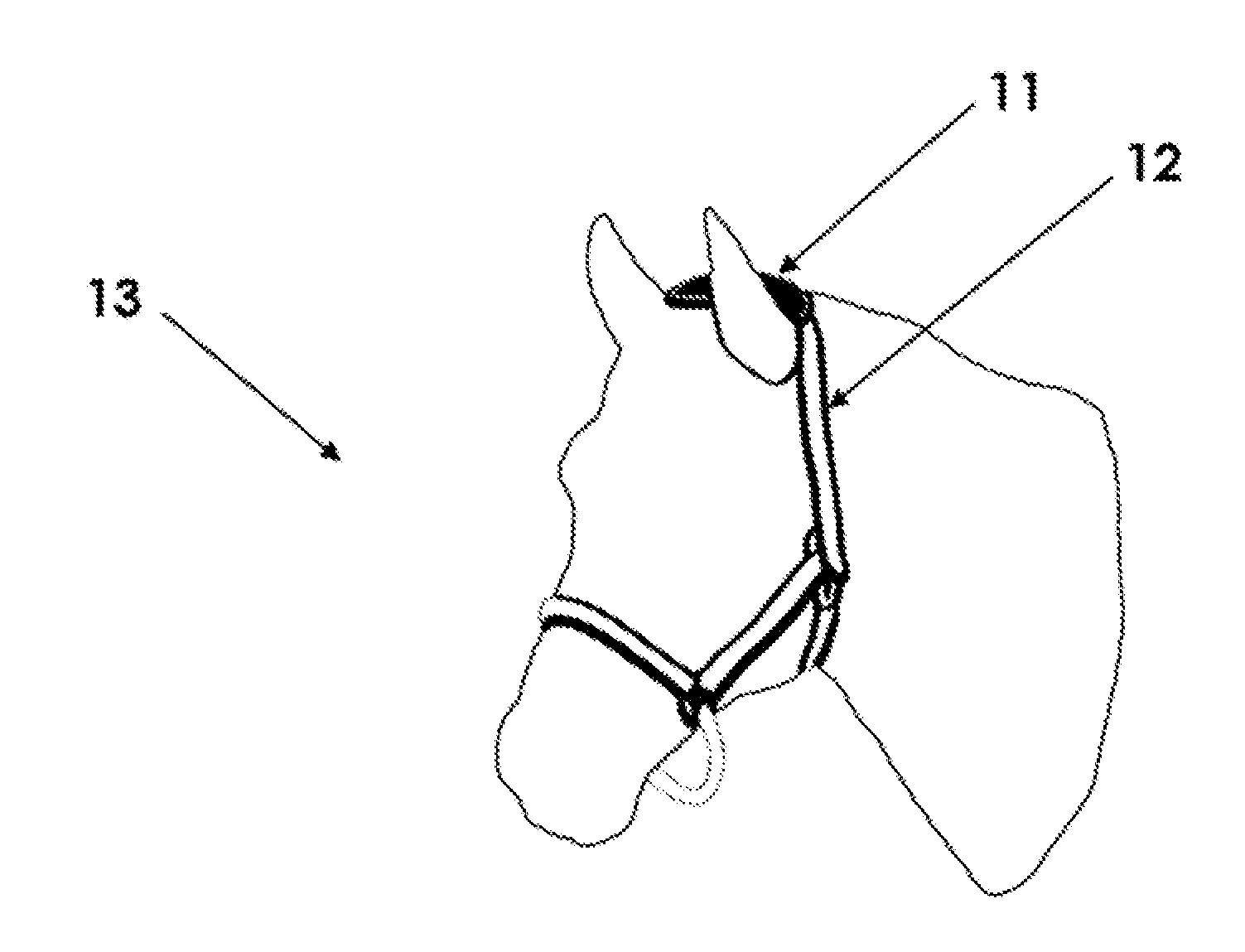
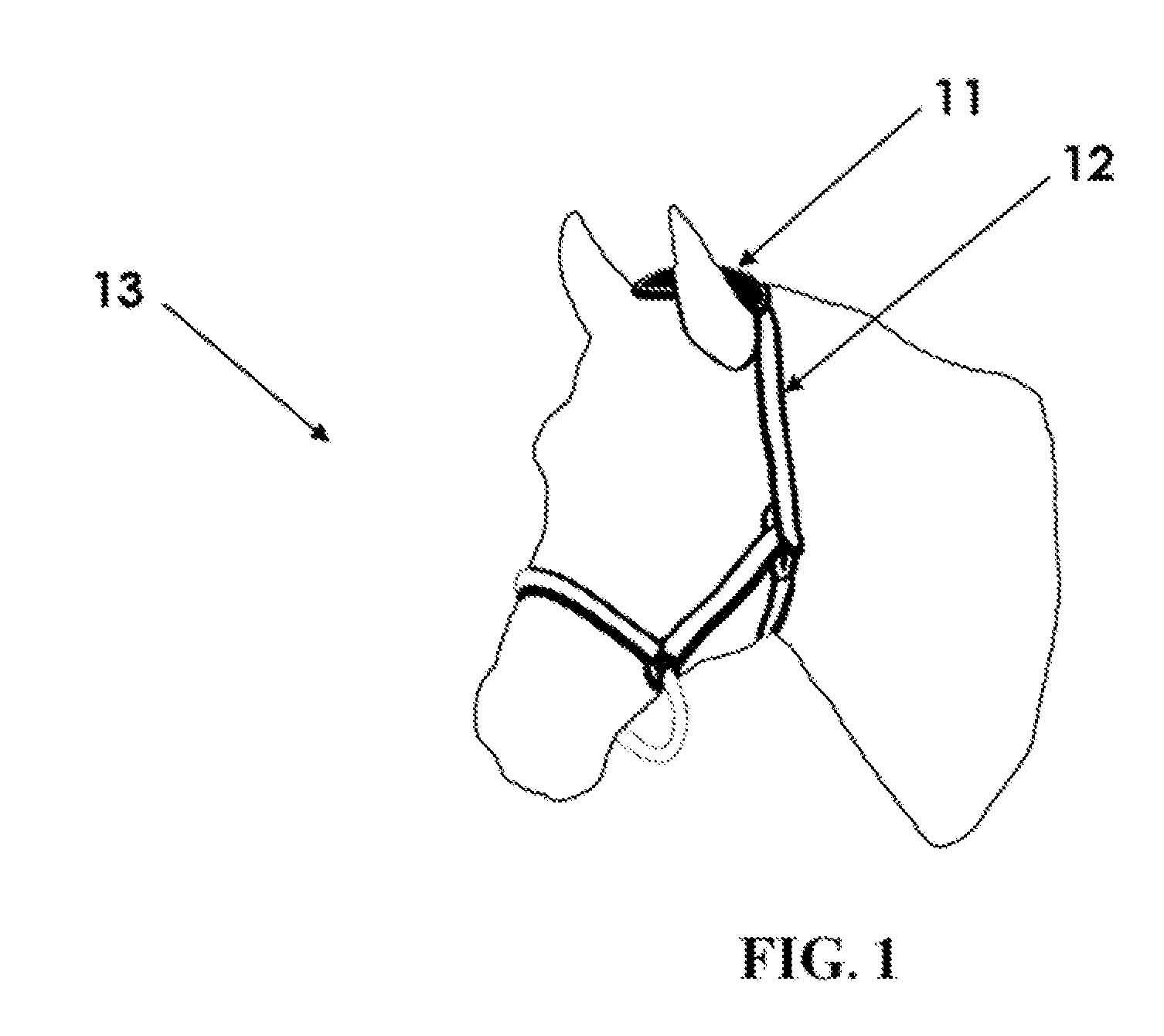
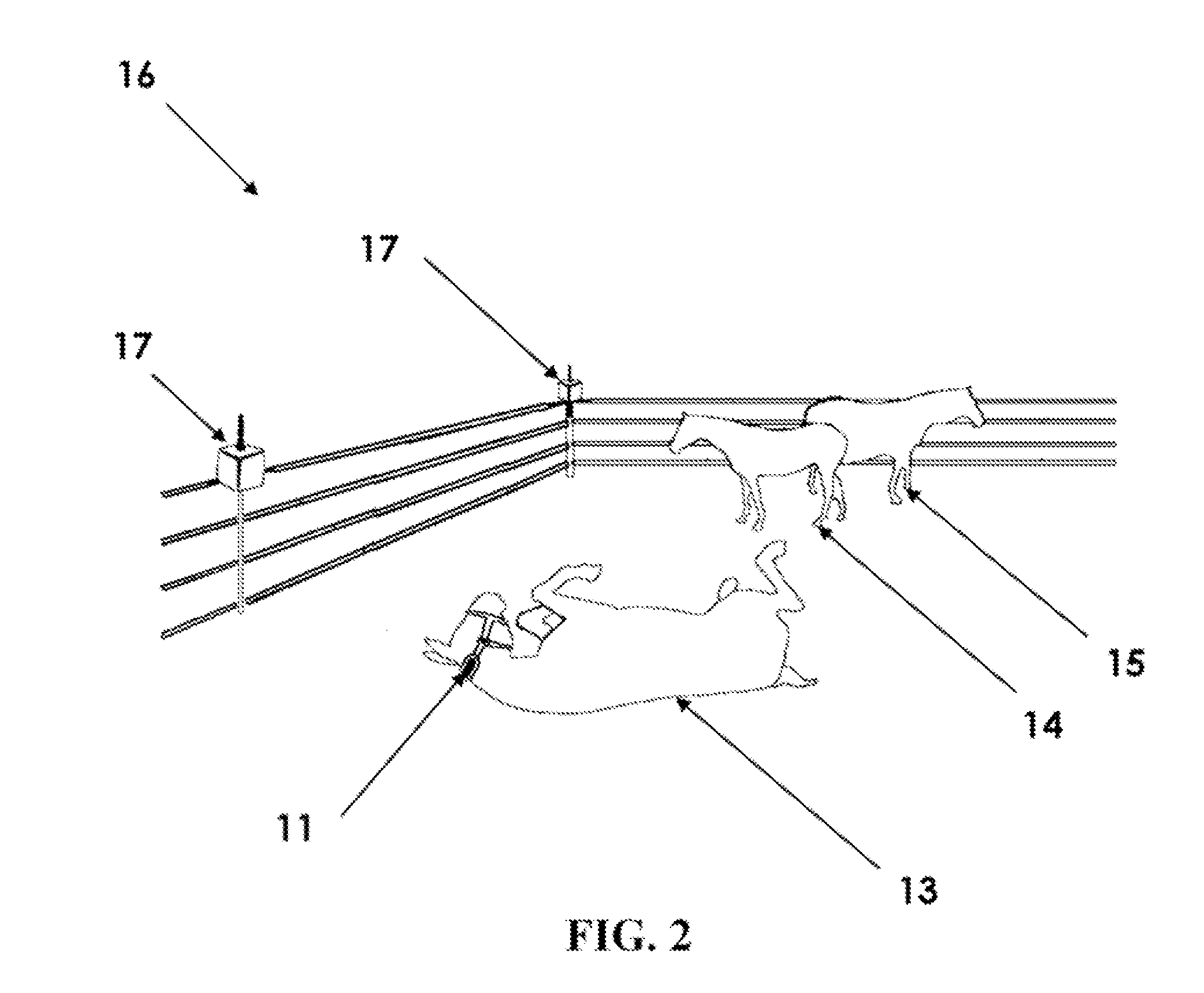
InactiveUS20100302004A1Increase chances of survivalLow costSafety beltsFrequency-division multiplex detailsAnimal behaviorBehaviour pattern
The device and method for remotely monitoring animal behavior consists of a sensor unit mounted on an animal. The sensor unit utilizes motion sensors to monitor the specific behavioral patterns of the animal. Power management is controlled to turn the system on when specific types of motion are detected. Motion data is wirelessly transmitted to a base station for analysis. Data analysis functions are used to detect and identify the occurrence of characteristic motions. Network decision algorithms analyze the characteristic motions and compute weighted indicators and weighted counter-indicators which are combined into a final diagnostic score. When the final diagnostic score exceeds a threshold value, a specific behavioral pattern is confirmed which may indicate the animal is in a distress situation or experiencing another type of behavior that requires intervention. If distress is detected, the system sends a communication to notify the appropriate personnel that a distress condition exists.
Owner:UTAH STATE UNIVERSITY
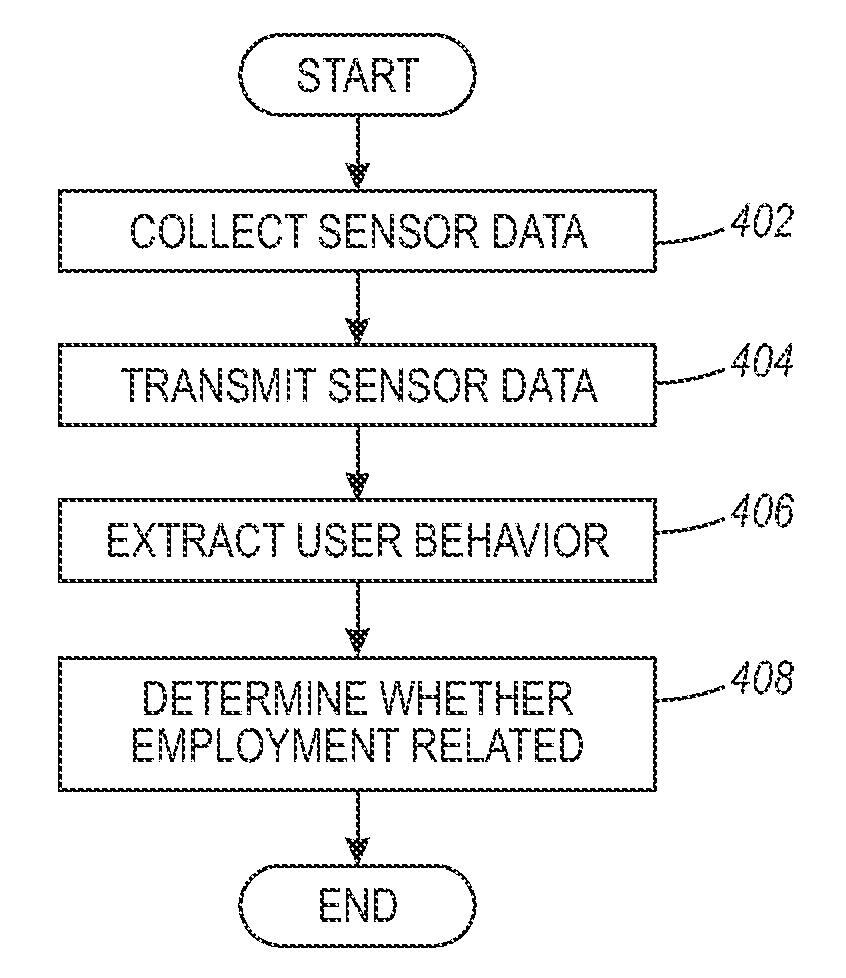
Employment inference from mobile device data
One embodiment of the present invention provides a system for inferring a user's activity. During operation, the system collects contextual information recorded by a plurality of components located on a mobile device associated with the user. The system then extracts the user's behavior pattern based on the collected contextual information, and determines whether the user is engaged in an employment-related activity.
Owner:PALO ALTO RES CENT INC
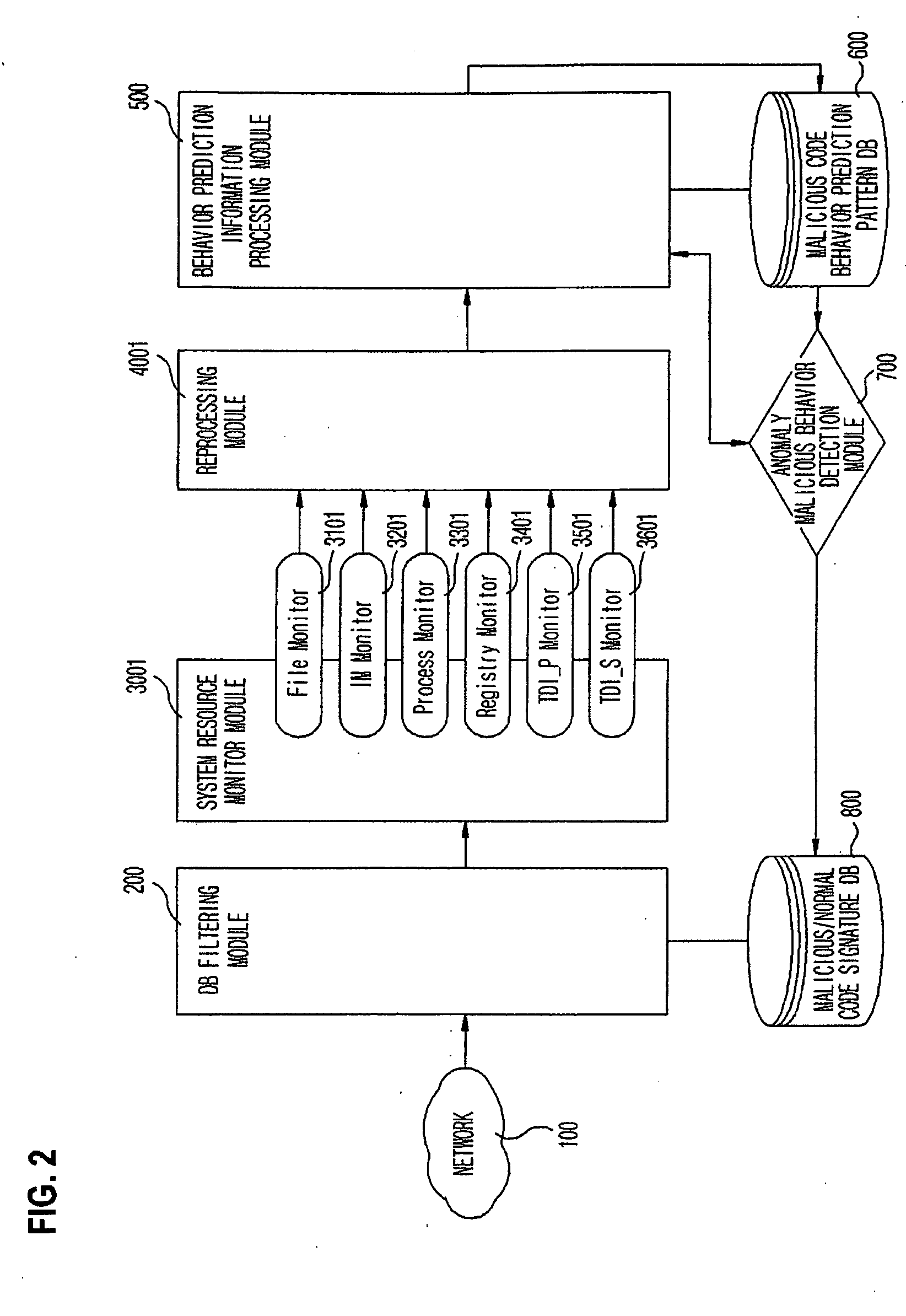
System and method of detecting anomaly malicious code by using process behavior prediction technique
InactiveUS20080127346A1Memory loss protectionUser identity/authority verificationProcess behaviorBehaviour pattern
Provided are a pattern analyzing / detecting method and a system using the same that are capable of detecting and effectively preventing an unknown malicious code attack. To detect such an attack, the method monitors the system to combine all behaviors exhibited within the system due to corresponding malicious codes, reprocess and learn the behaviors, analyze existing malicious behavior feature values (prediction patterns), and compare them with a behavior pattern exhibited by an execution code.
Owner:F1 SECURITY INC
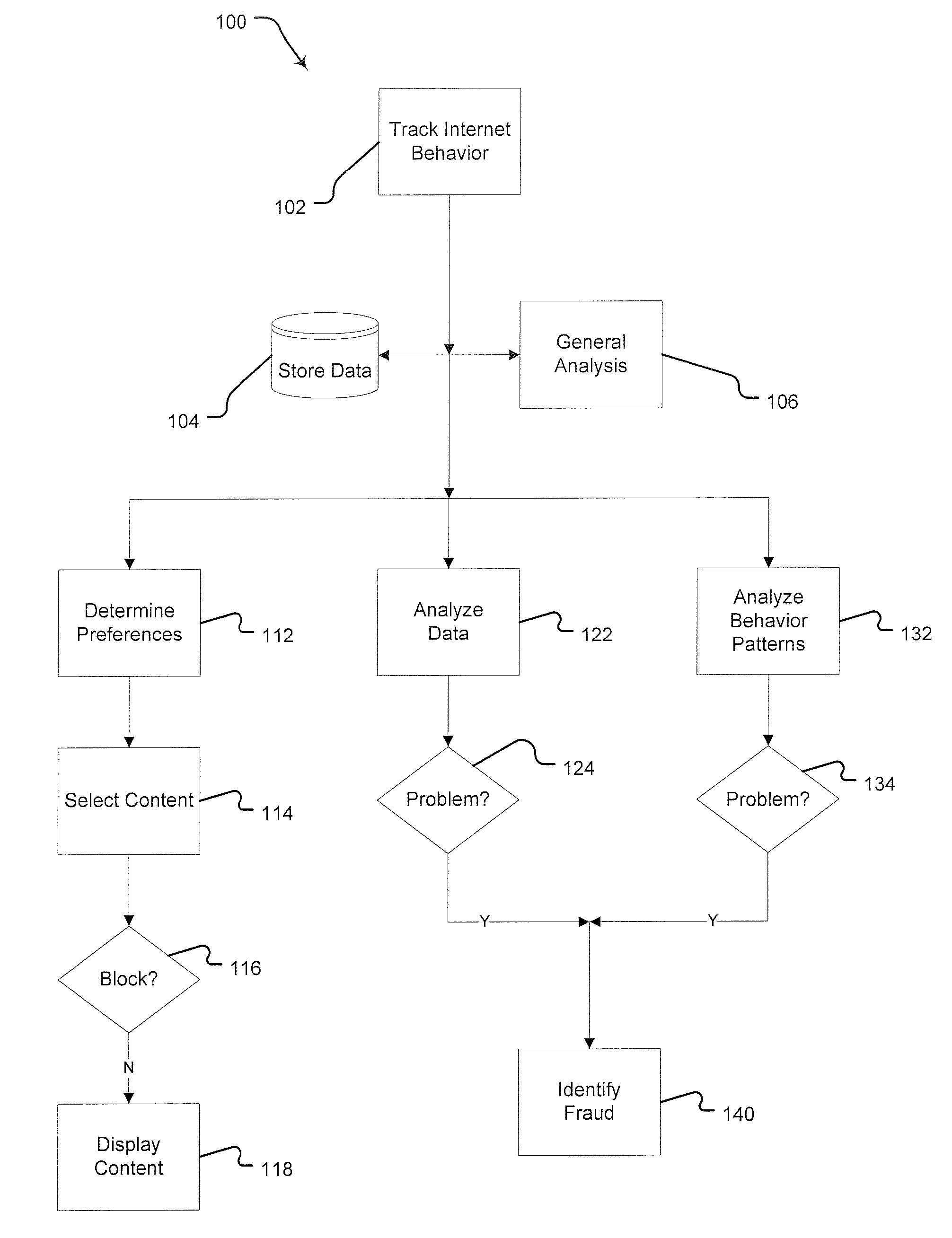
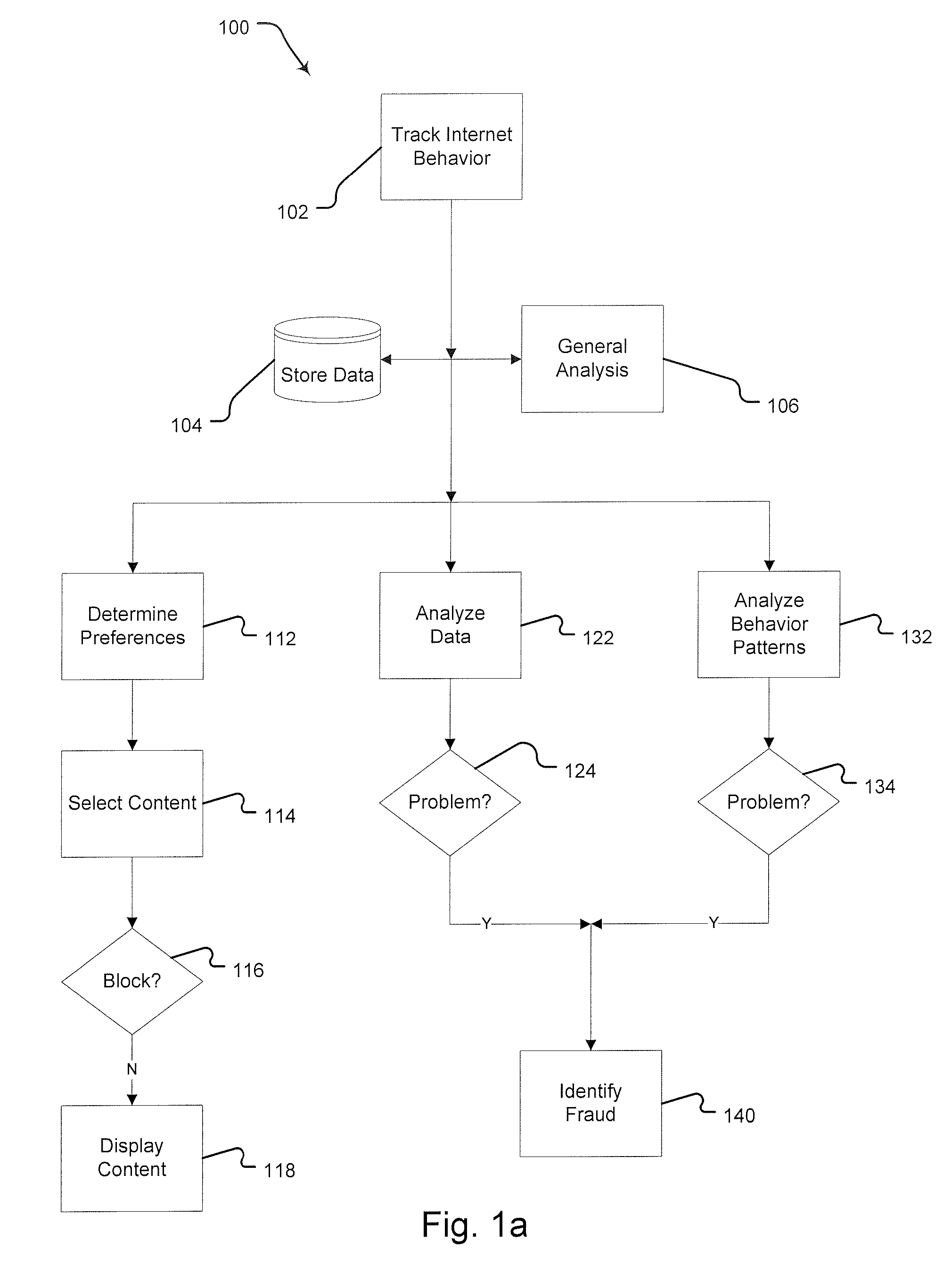
Method for Detecting and Preventing Fraudulent Internet Advertising Activity
InactiveUS20080288303A1Prevent fraudPlatform integrity maintainanceMarket data gatheringInternet privacyBehaviour pattern
A method for preventing fraud in Internet-based advertising. The first step of this method is providing behavior-tracking software on a user computer. That software tracks and analyzes the user's activity across multiple content providers. Next, the system displays content, including advertising, based on preferences inferred from previous activity. Finally, the system identifies behavior patterns consistent with fraudulent activity.
Owner:CARHAMM
Method for Analyzing Activities Over Information Networks
InactiveUS20080162397A1Knowledge representationData switching networksLawful interceptionInformation networks
The present invention is a method for analyzing large volumes of network information for the purpose of identifying particular patterns of behavior in a plurality of connections. It enables identifying unique digital fingerprints of particular users, be it individuals, groups or organizations, and tracks their activities in large scale information networks such as corporate wide area networks or the public internet despite attempts on the part of the users to hide their identity. By recognizing unique identifiers and distinguishing patterns of behavior the method may differentiate between different users all using a single connection, or identify a single entity across multiple connections. The method may be applicable for tracking hostile entities inside an organizational network. Advertisers may uniquely and anonymously track the activities of users. The method may also be used to track and identify suspicious activities by law enforcement agencies via lawful interception of network data.
Owner:ZALTZMAN ORI
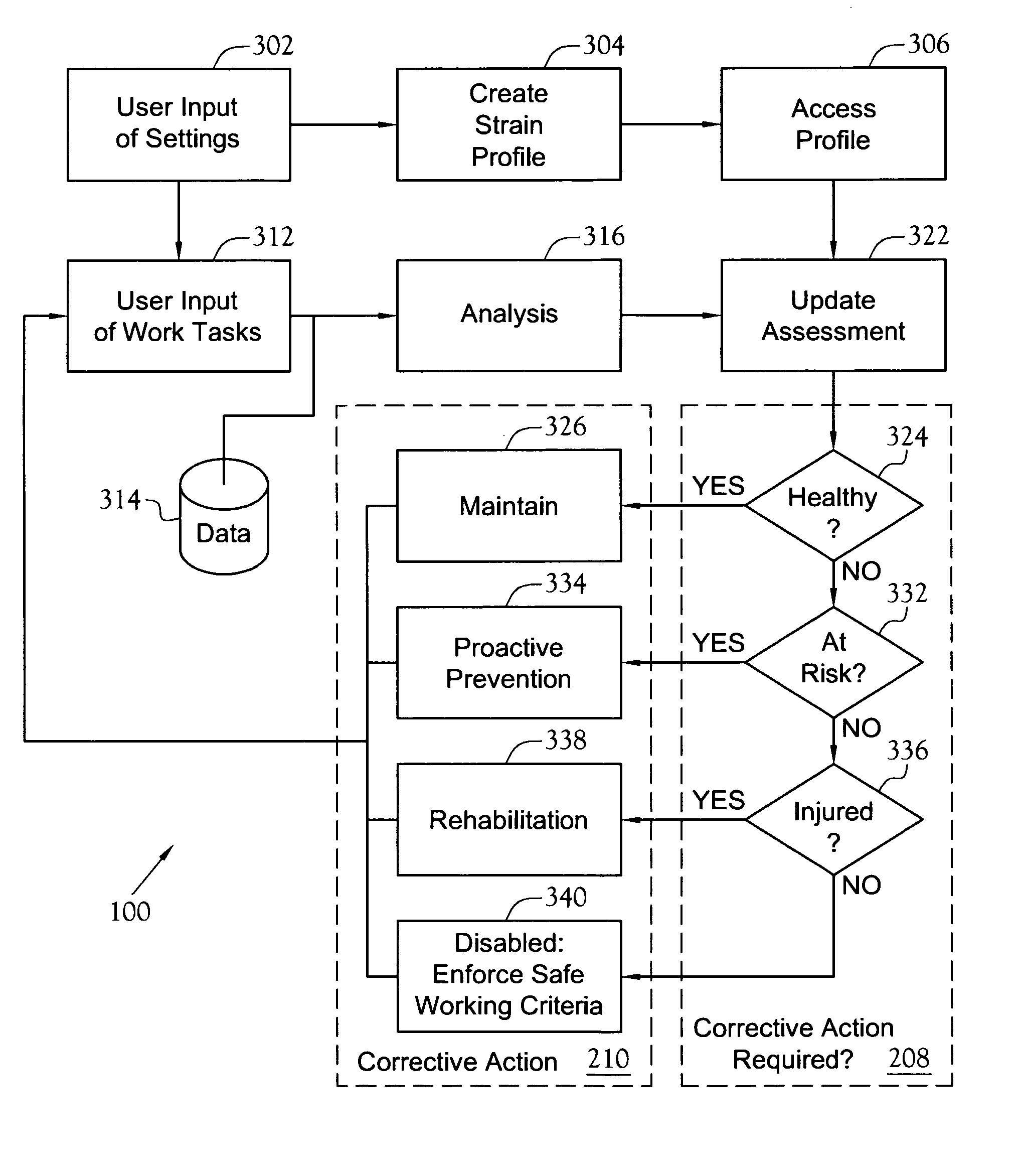
Health management system for personal computer users
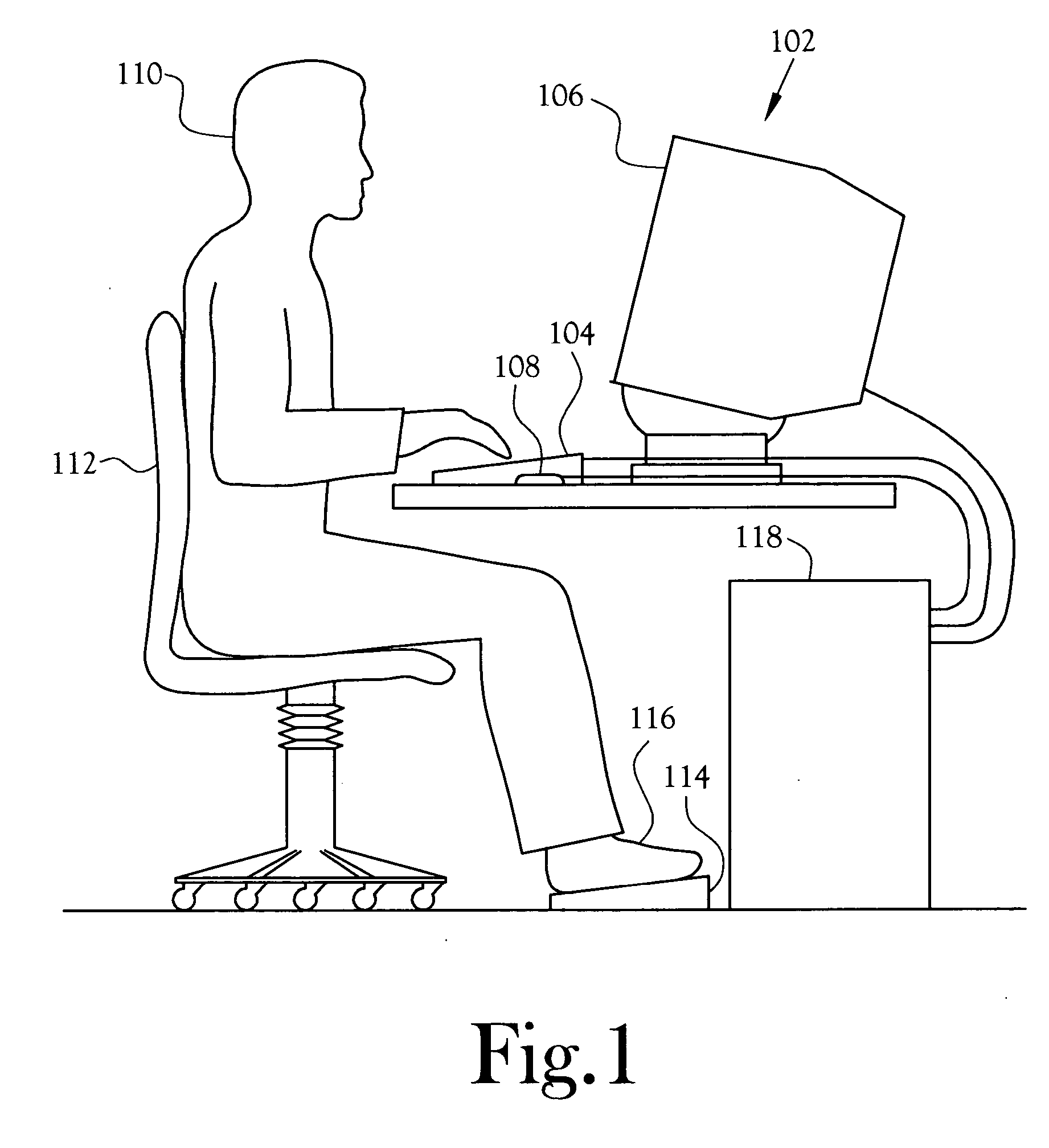
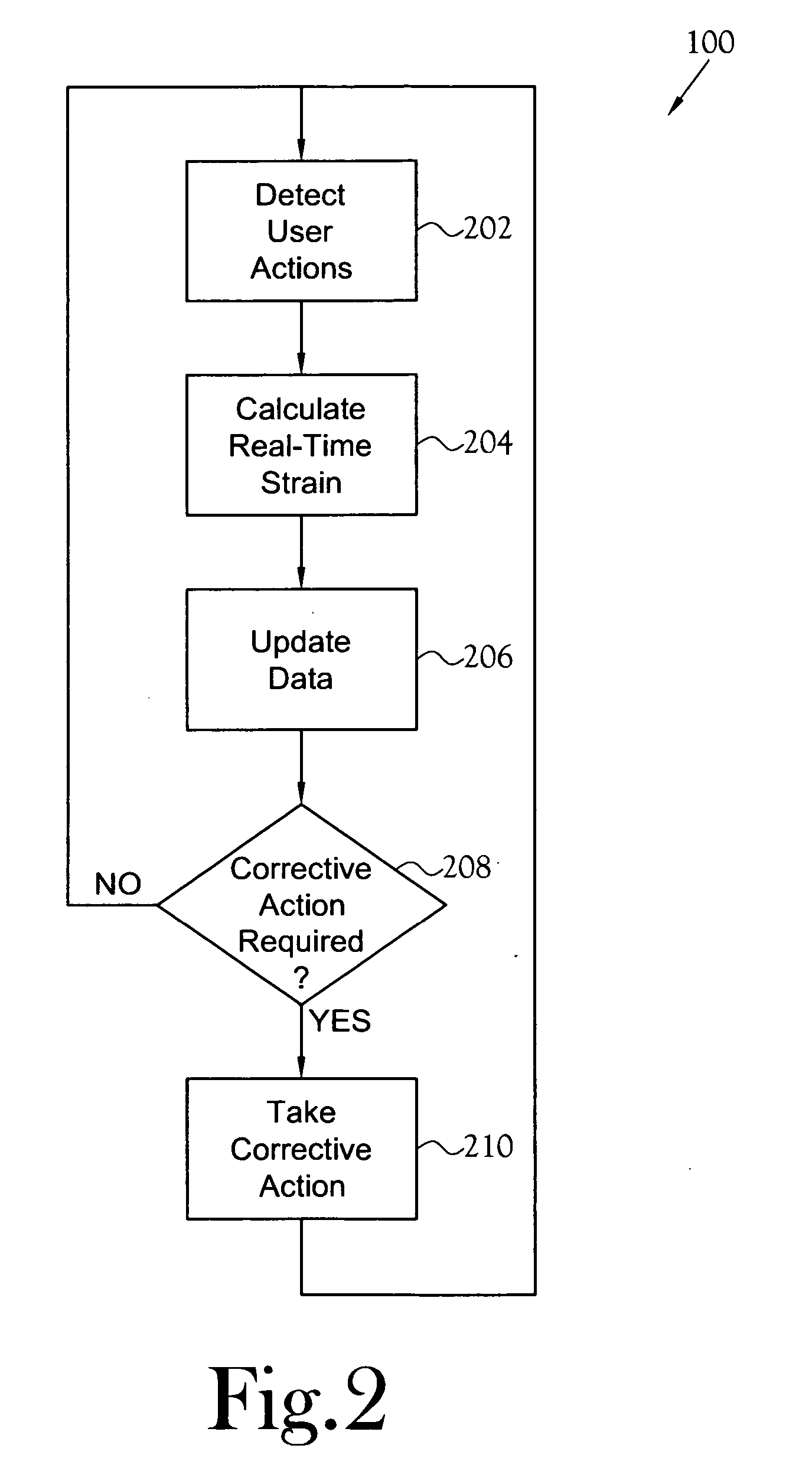
InactiveUS20070139362A1Minimized risk of injuryInhibit deteriorationInput/output for user-computer interactionPhysical therapies and activitiesComputer usersUser input
A monitoring and corrective action system for computer users. The system monitors the real-time interactions of a user with a computer workstation's keyboard, mouse, and video display unit to determine the strain induced in the user. The induced strain value also is based upon setting entered by the user indicating the users discomfort level, recovery level, and typing proficiency. The system provides feedback to the user to allow the user to modify behavior in order to reduce the induced strain. The feedback includes, in various embodiments, displaying safe-tips, displaying exercises, displaying real-time strain graphs, and forced breaks. The system also includes provisions for reporting induced strain levels and behavior patterns to others through electronic messages such as e-mail.
Owner:BINARY LOGIC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com