Patents
Literature
149 results about "Behavioral pattern" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In software engineering, behavioral design patterns are design patterns that identify common communication patterns among objects and realize these patterns. By doing so, these patterns increase flexibility in carrying out this communication.
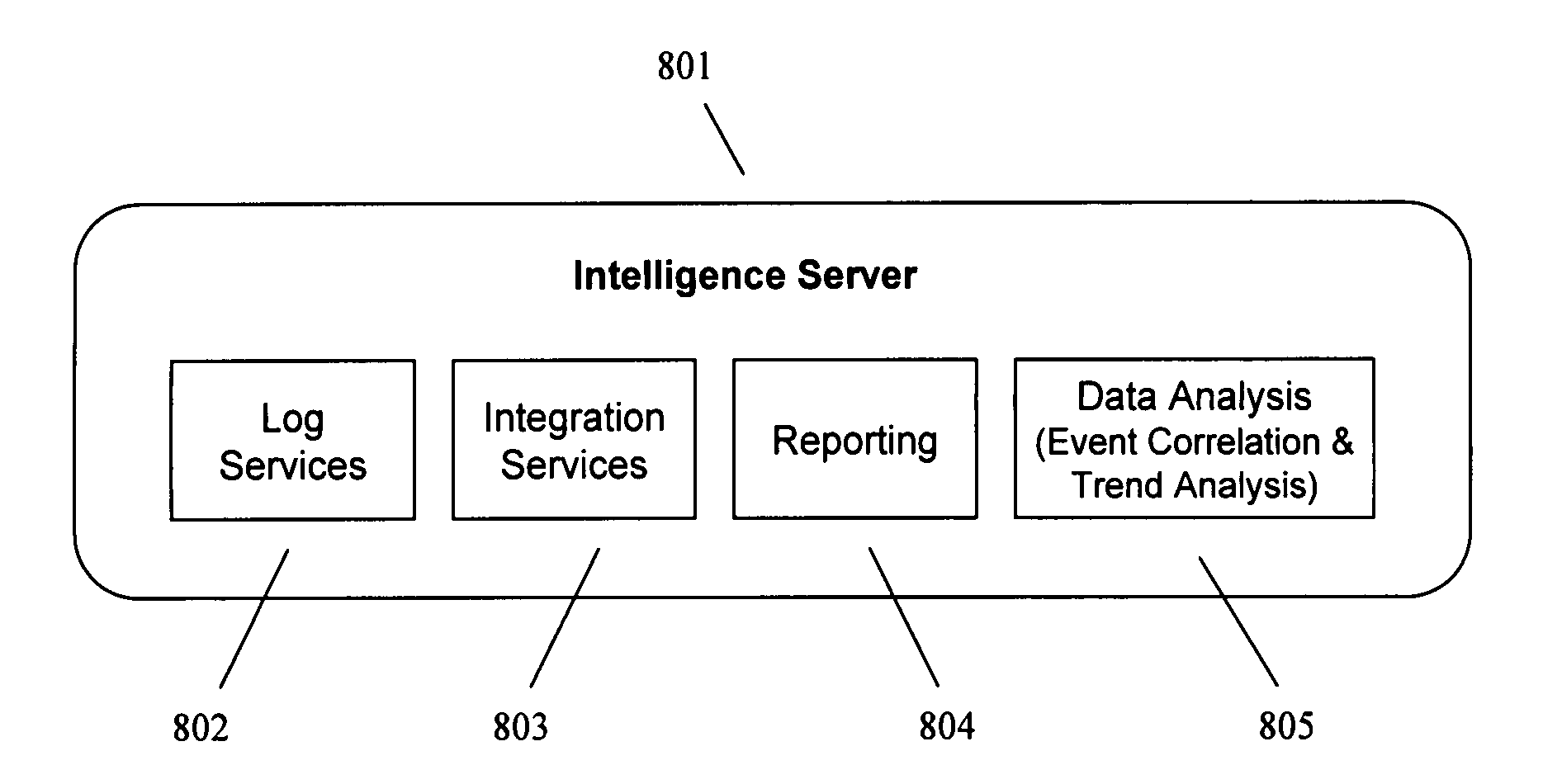
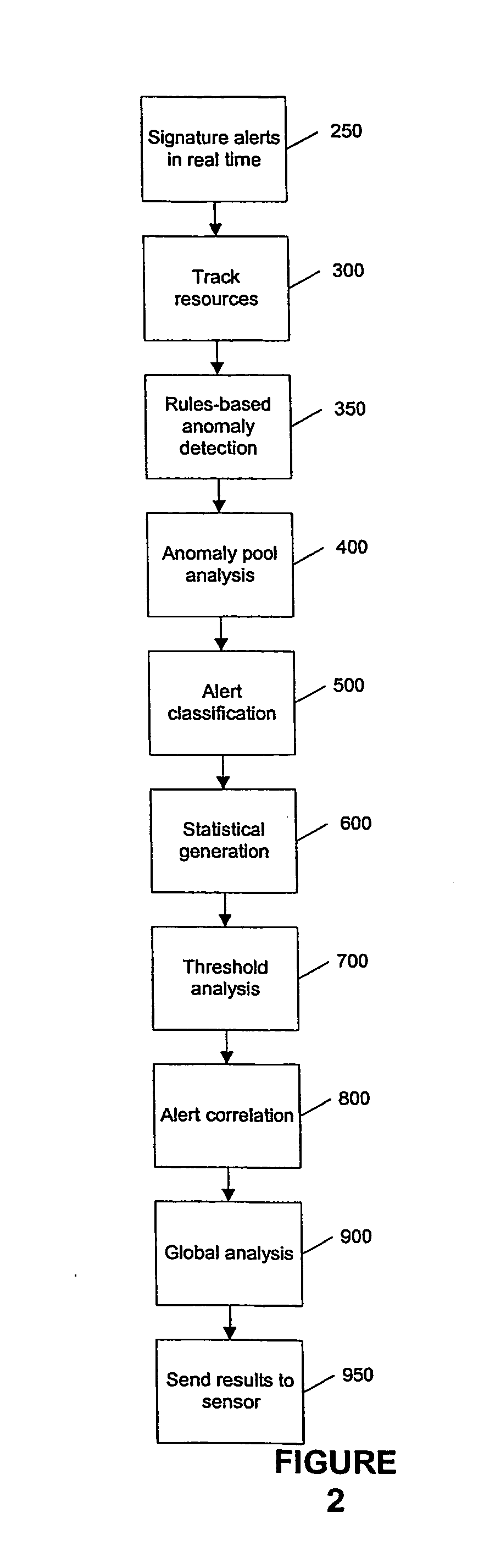
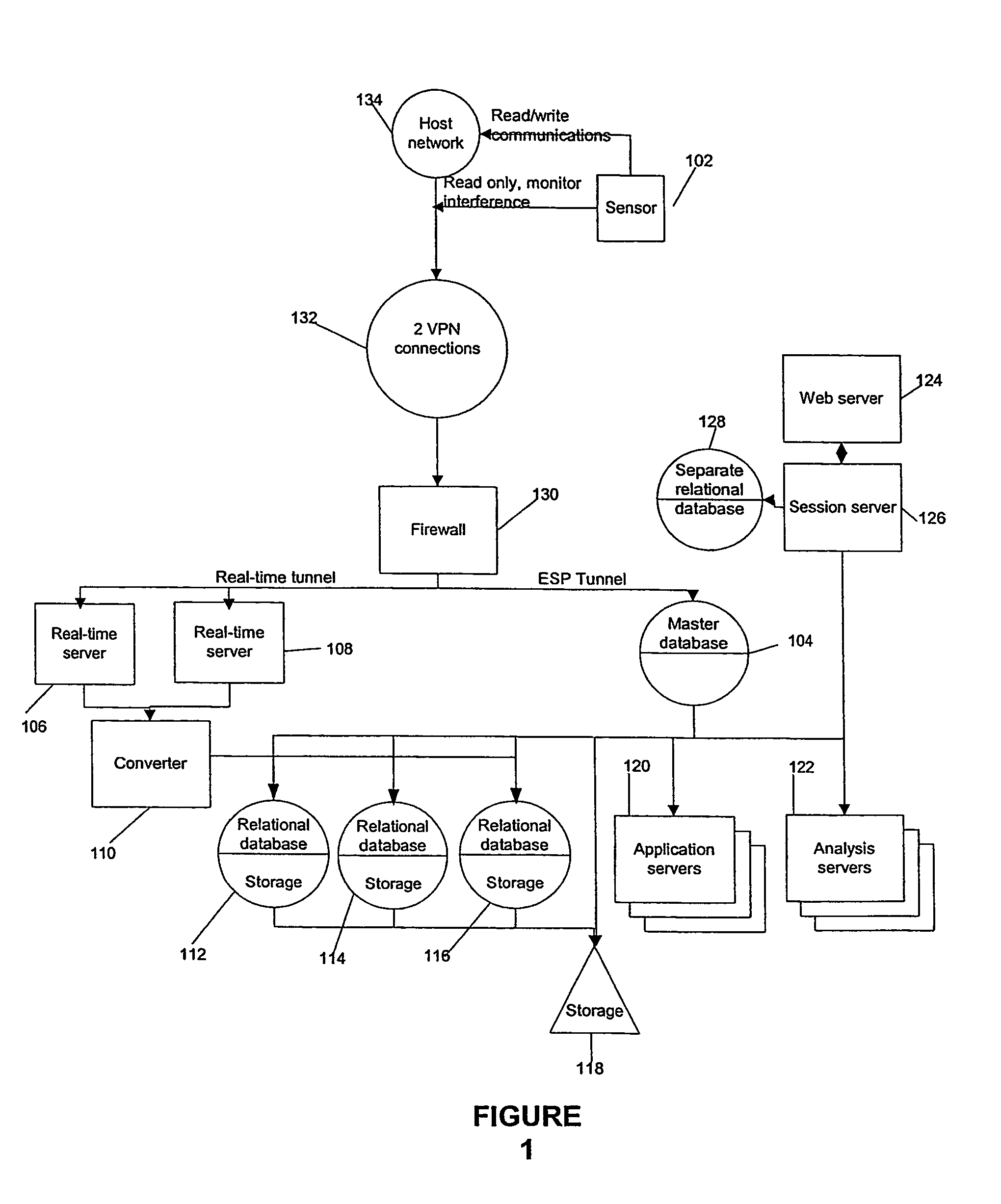
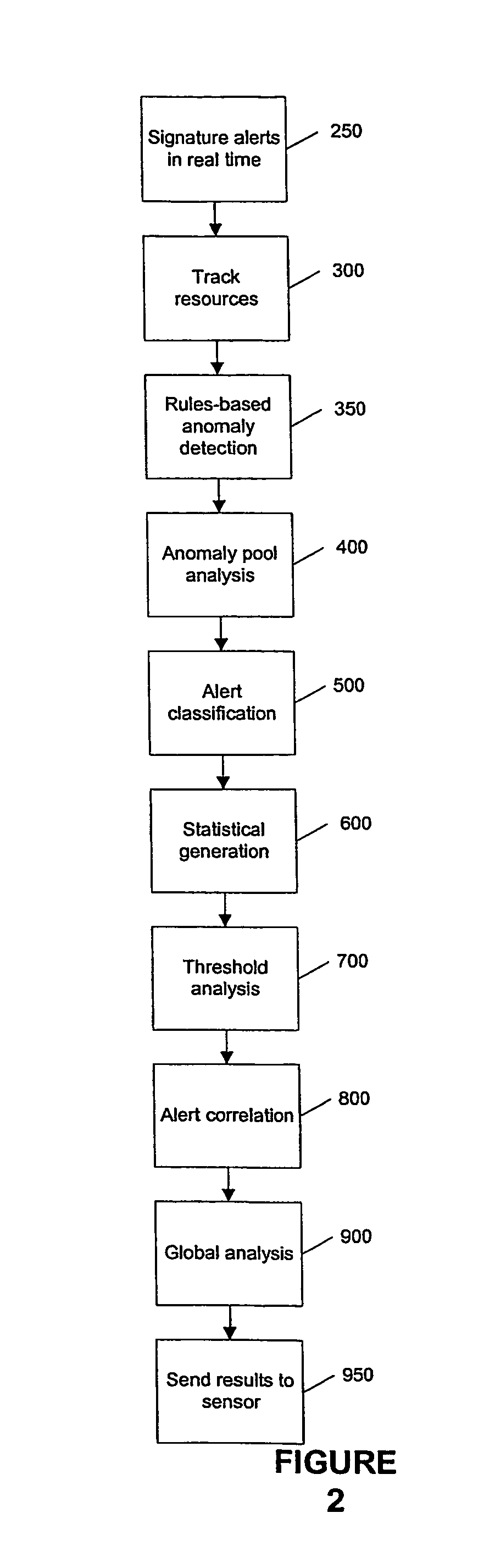
Detecting Behavioral Patterns and Anomalies Using Activity Profiles
ActiveUS20080059474A1Potential security breachError detection/correctionDigital data processing detailsBehaviour patternActivity profile
Activity data is analyzed or evaluated to detect behavioral patterns and anomalies. When a particular pattern or anomaly is detected, a system may send a notification or perform a particular task. This activity data may be collected in an information management system, which may be policy based. Notification may be by way e-mail, report, pop-up message, or system message. Some tasks to perform upon detection may include implementing a policy in the information management system, disallowing a user from connecting to the system, and restricting a user from being allowed to perform certain actions. To detect a pattern, activity data may be compared to a previously defined or generated activity profile.
Owner:NEXTLABS
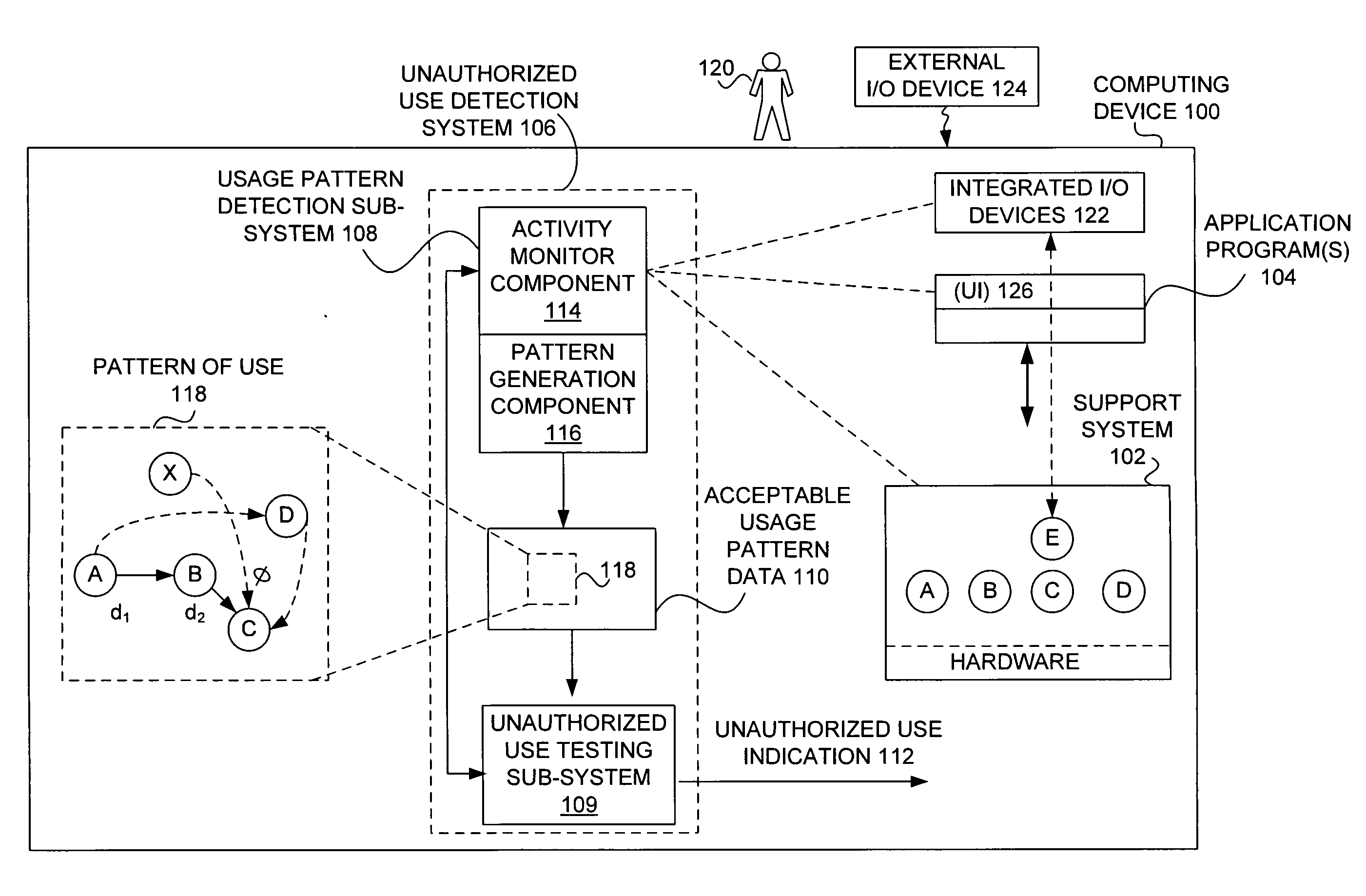
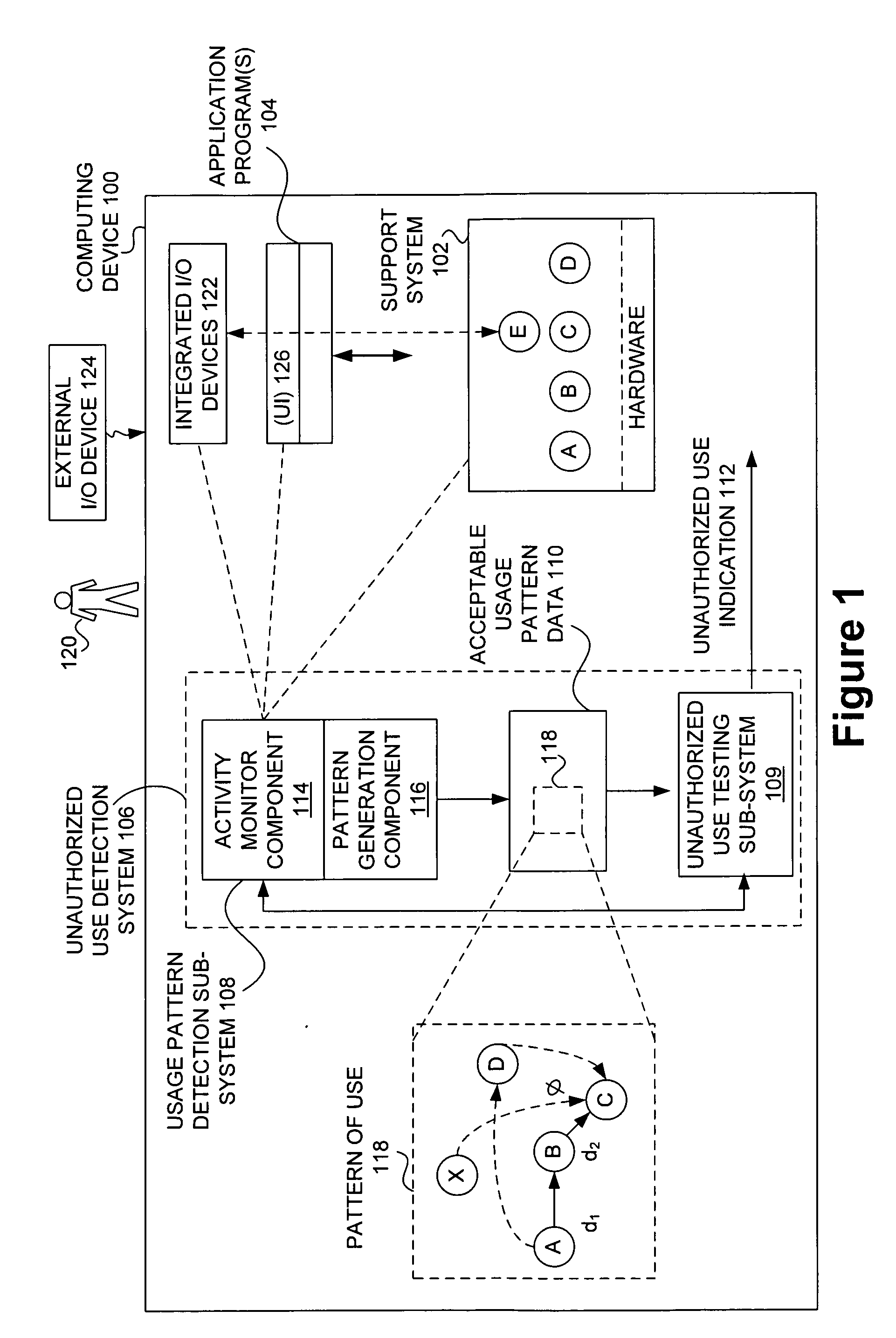
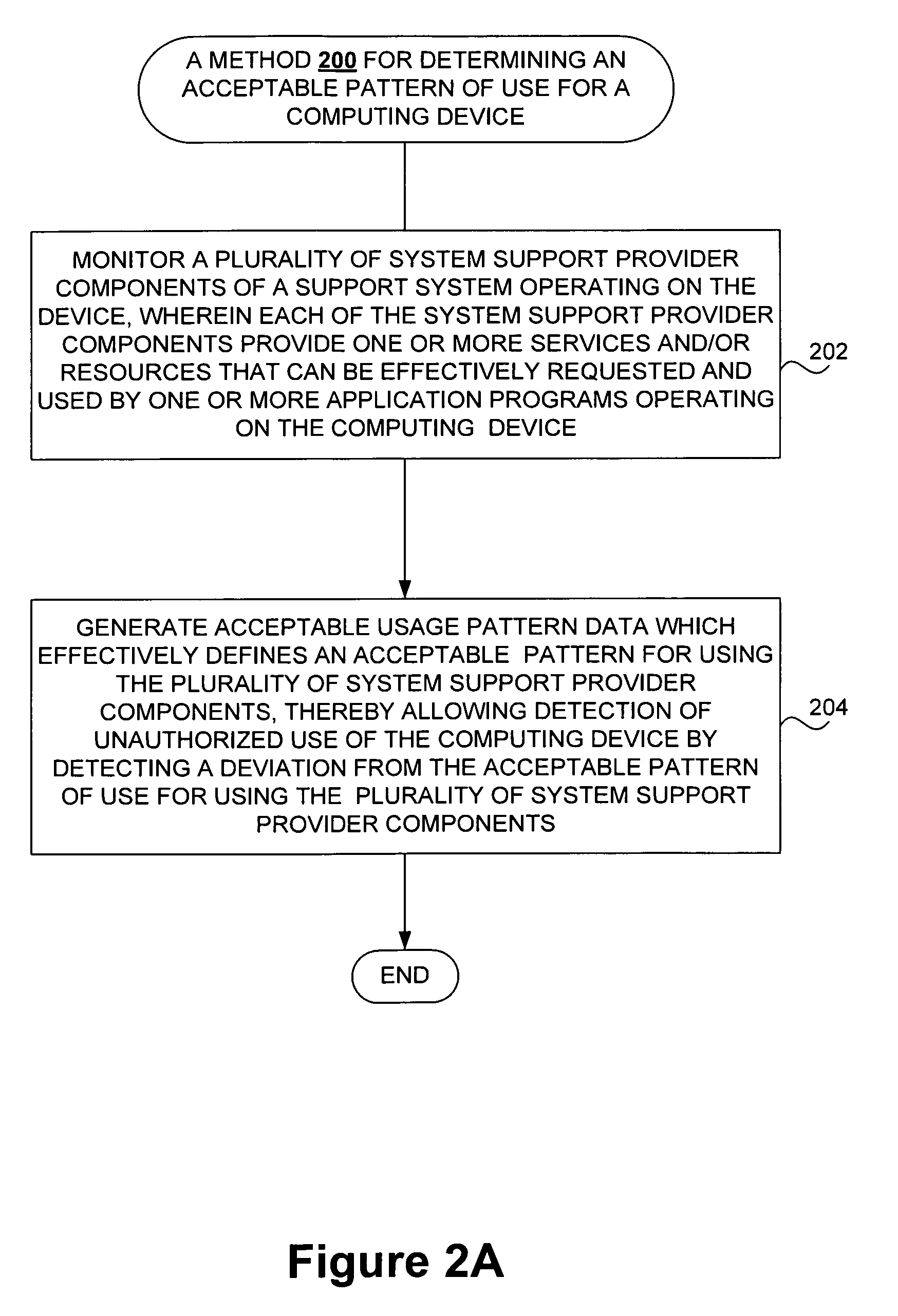
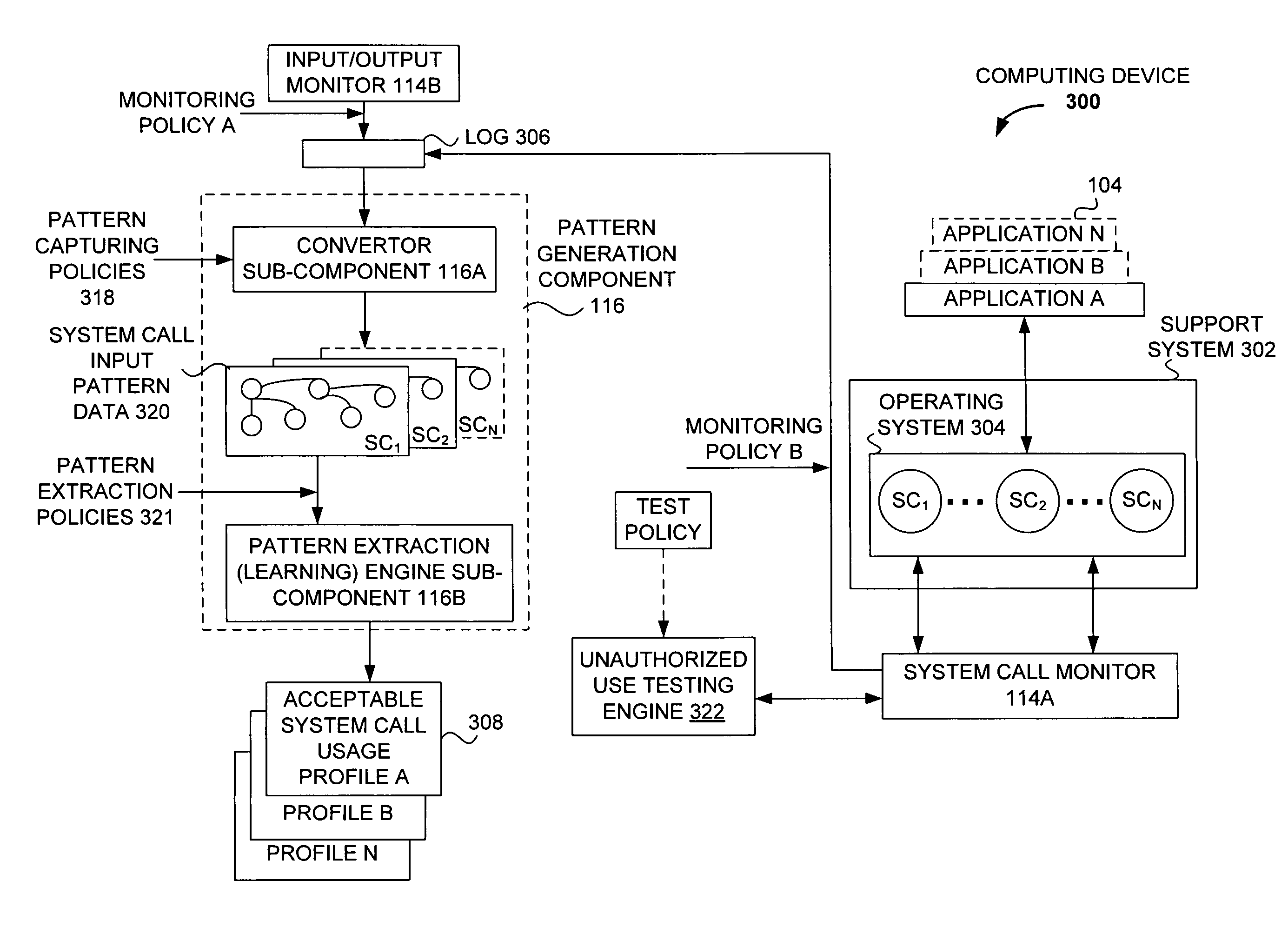
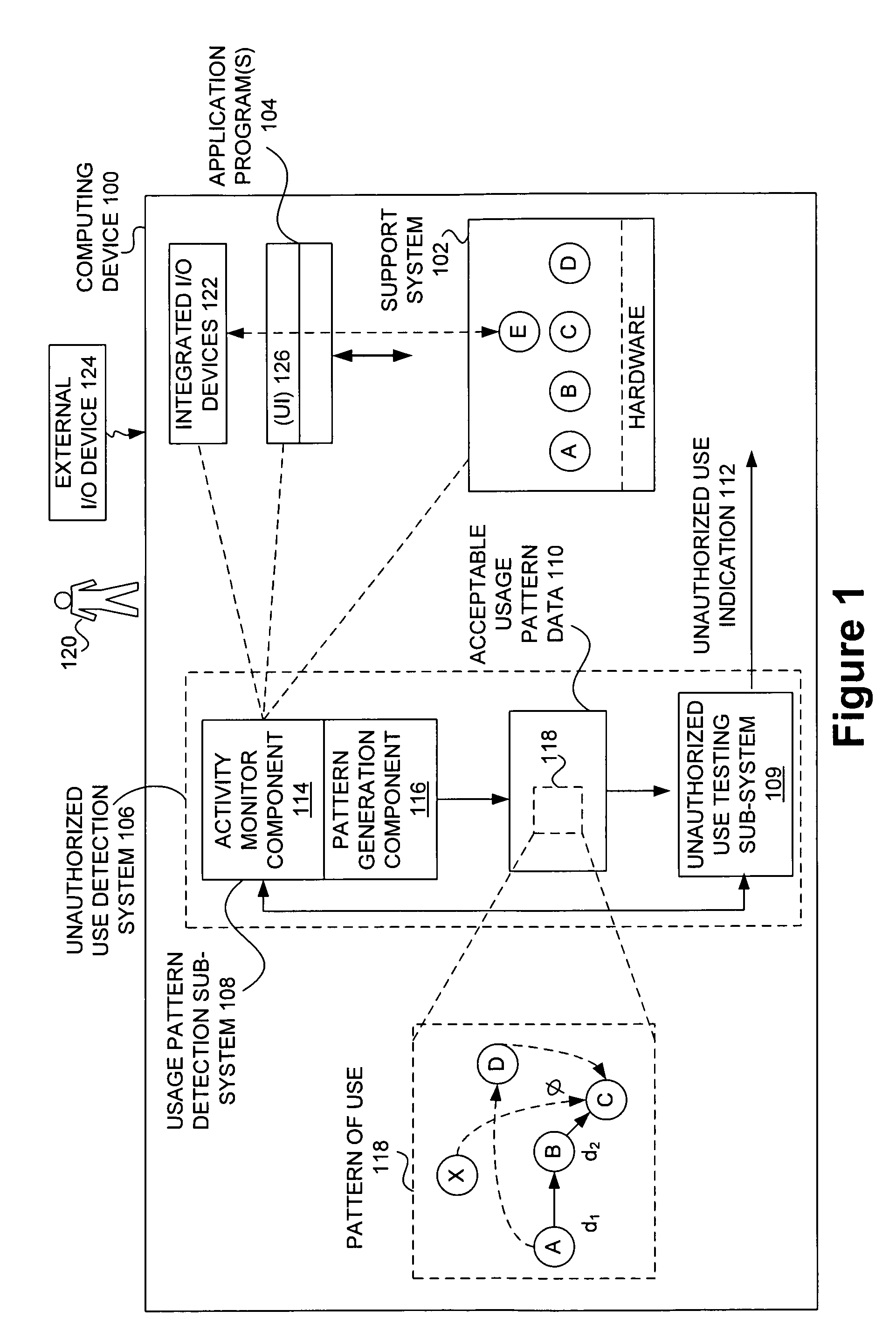
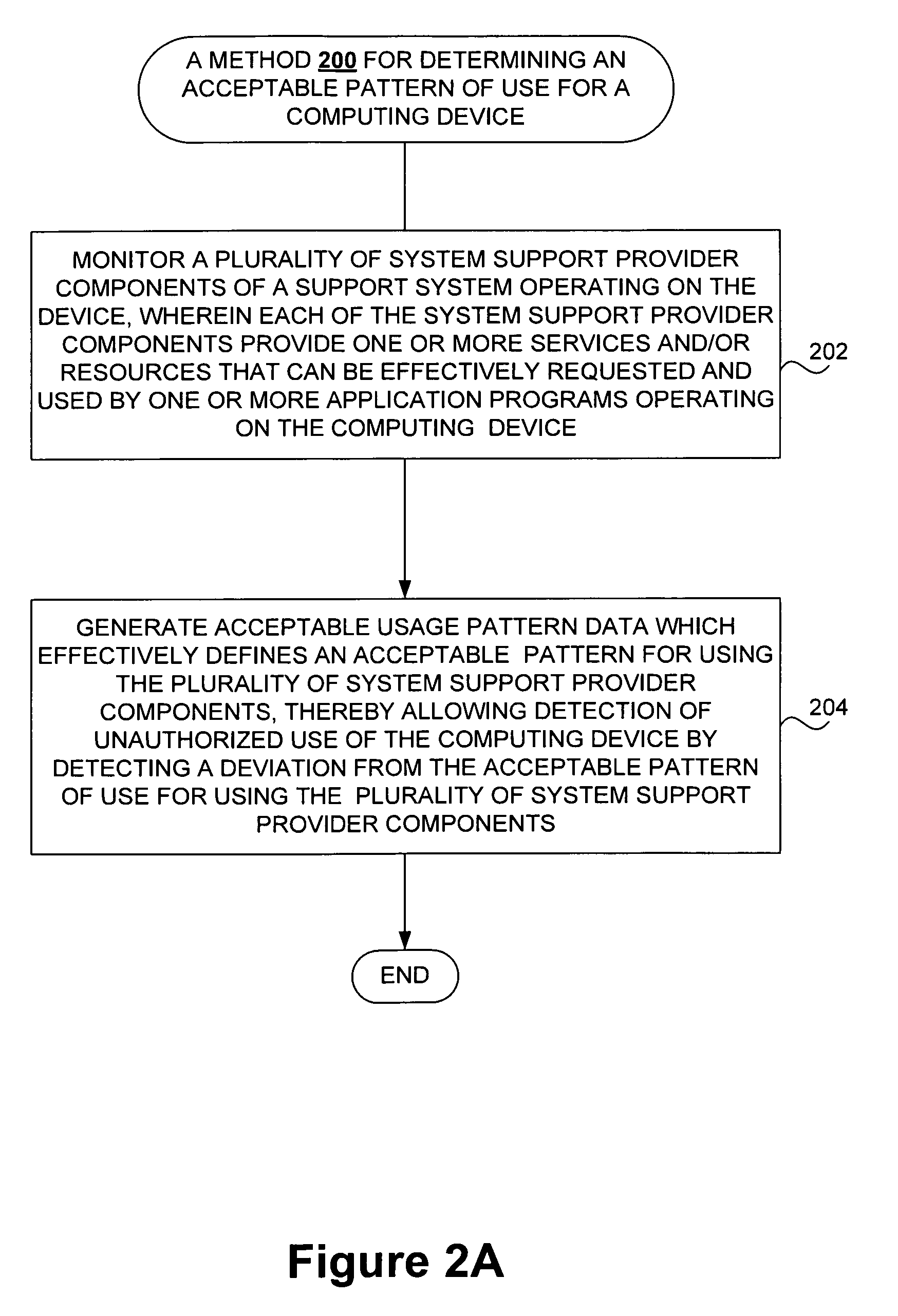
Detecting unauthorized use of computing devices based on behavioral patterns
InactiveUS20090199296A1Efficiently definedMemory loss protectionError detection/correctionSupporting systemOperational system
Techniques for detecting unauthorized use (e.g., malicious attacks) of the computing systems (e.g., computing devices) are disclosed. Unauthorized use can be detected based on patterns of use (e.g., behavioral patterns of use typically associated with a human being) of the computing systems. Acceptable behavioral pattern data can be generated for a computing system by monitoring the use of a support system (e.g., an operating system, a virtual environment) operating on the computing system. For example, a plurality of system support provider components of a support system (e.g., system calls, device drivers) can be monitored in order to generate the acceptable behavioral pattern data in a form which effectively defines an acceptable pattern of use (usage pattern) for the monitored system support provider components, thereby allowing detection of unauthorized use of a computing system by detecting any deviation from the acceptable pattern of use of the monitored system support provider components.
Owner:SAMSUNG ELECTRONICS CO LTD
Adaptive behavioral intrusion detection systems and methods
ActiveUS20050044406A1Increase opportunitiesMicrobiological testing/measurementDigital data processing detailsApplication serverInternet traffic
Systems and methods for analyzing historical network traffic and determining which traffic does not belong in a network are disclosed. Intrusion detection is performed over a period of time, looking for behavioral patterns within networks or information systems and generating alerts when these patterns change. The intrusion detection system intelligently forms correlations between disparate sources to find traffic anomalies. Over time, behaviors are predictive, and the intrusion detection system attempts to predict outcomes, becoming proactive instead of just reactive. Intrusions occur throughout whole information systems, including both network infrastructure and application servers. By treating the information system as a whole and performing intrusion detection across it, the chances of detection are increased significantly.
Owner:MASERGY COMMUNICATIONS
Detecting unauthorized use of computing devices based on behavioral patterns
InactiveUS8595834B2Memory loss protectionError detection/correctionSupporting systemMonitoring system
Techniques for detecting unauthorized use (e.g., malicious attacks) of the computing systems (e.g., computing devices) are disclosed. Unauthorized use can be detected based on patterns of use (e.g., behavioral patterns of use typically associated with a human being) of the computing systems. Acceptable behavioral pattern data can be generated for a computing system by monitoring the use of a support system (e.g., an operating system, a virtual environment) operating on the computing system. For example, a plurality of system support provider components of a support system (e.g., system calls, device drivers) can be monitored in order to generate the acceptable behavioral pattern data in a form which effectively defines an acceptable pattern of use (usage pattern) for the monitored system support provider components, thereby allowing detection of unauthorized use of a computing system by detecting any deviation from the acceptable pattern of use of the monitored system support provider components.
Owner:SAMSUNG ELECTRONICS CO LTD
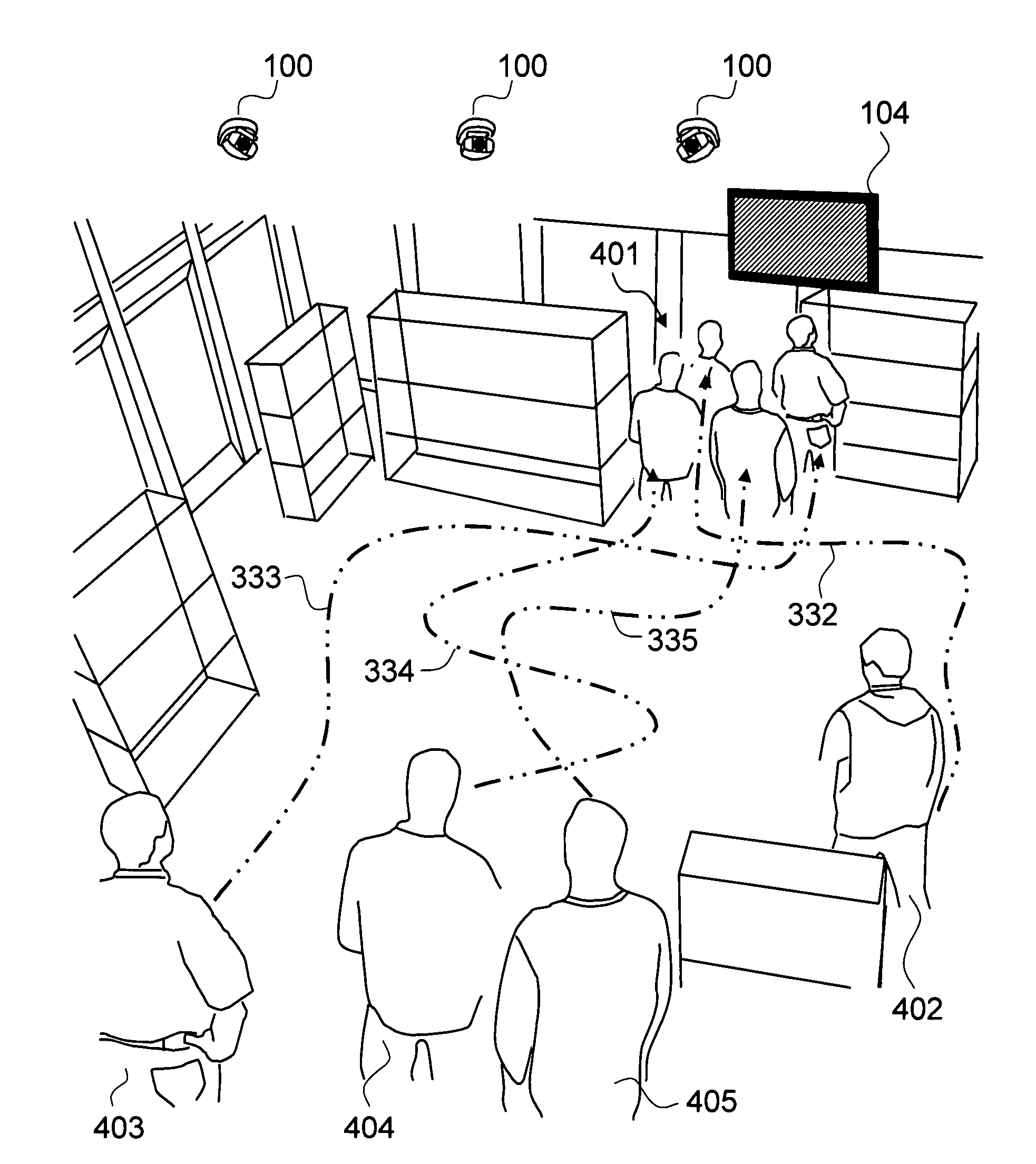
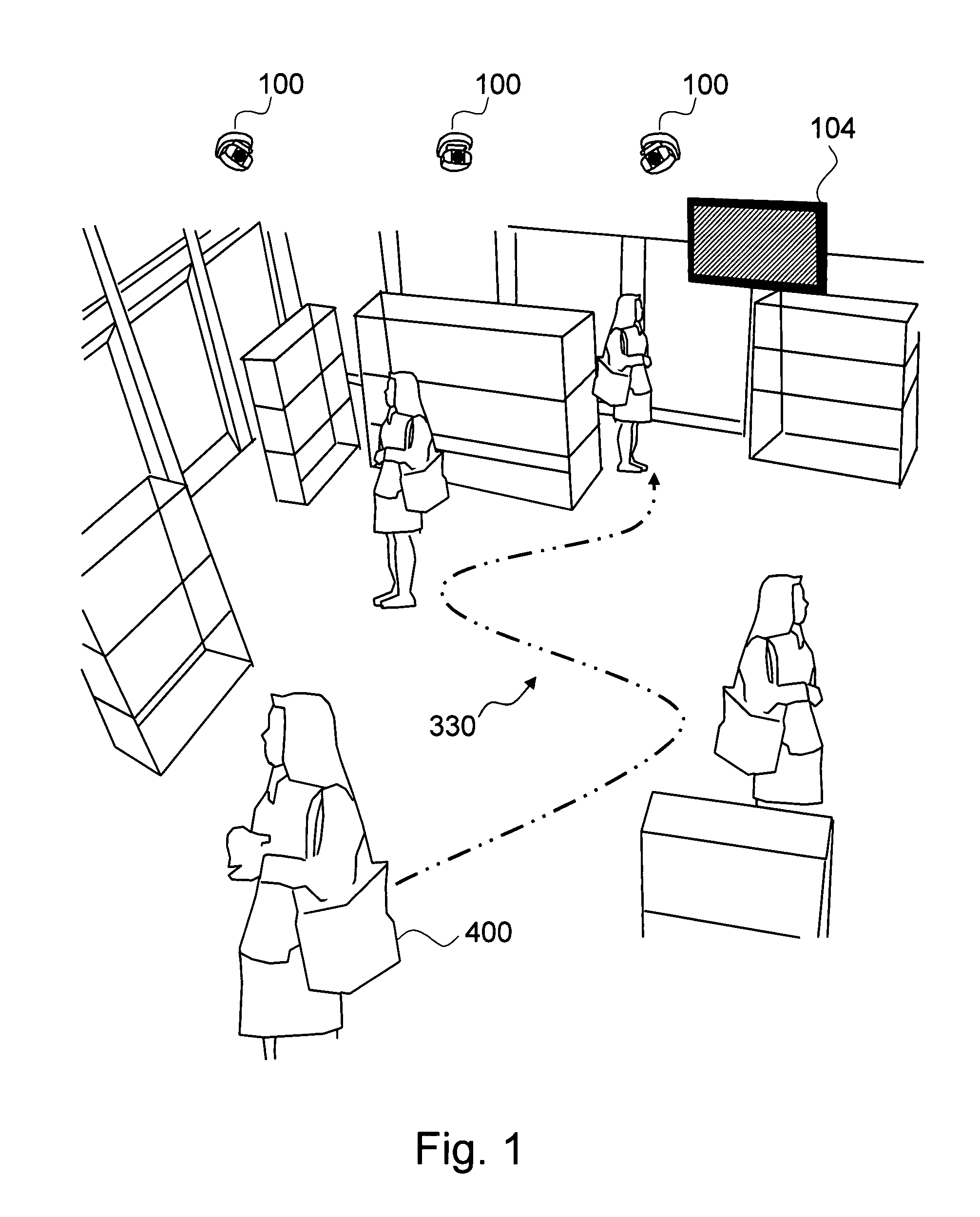
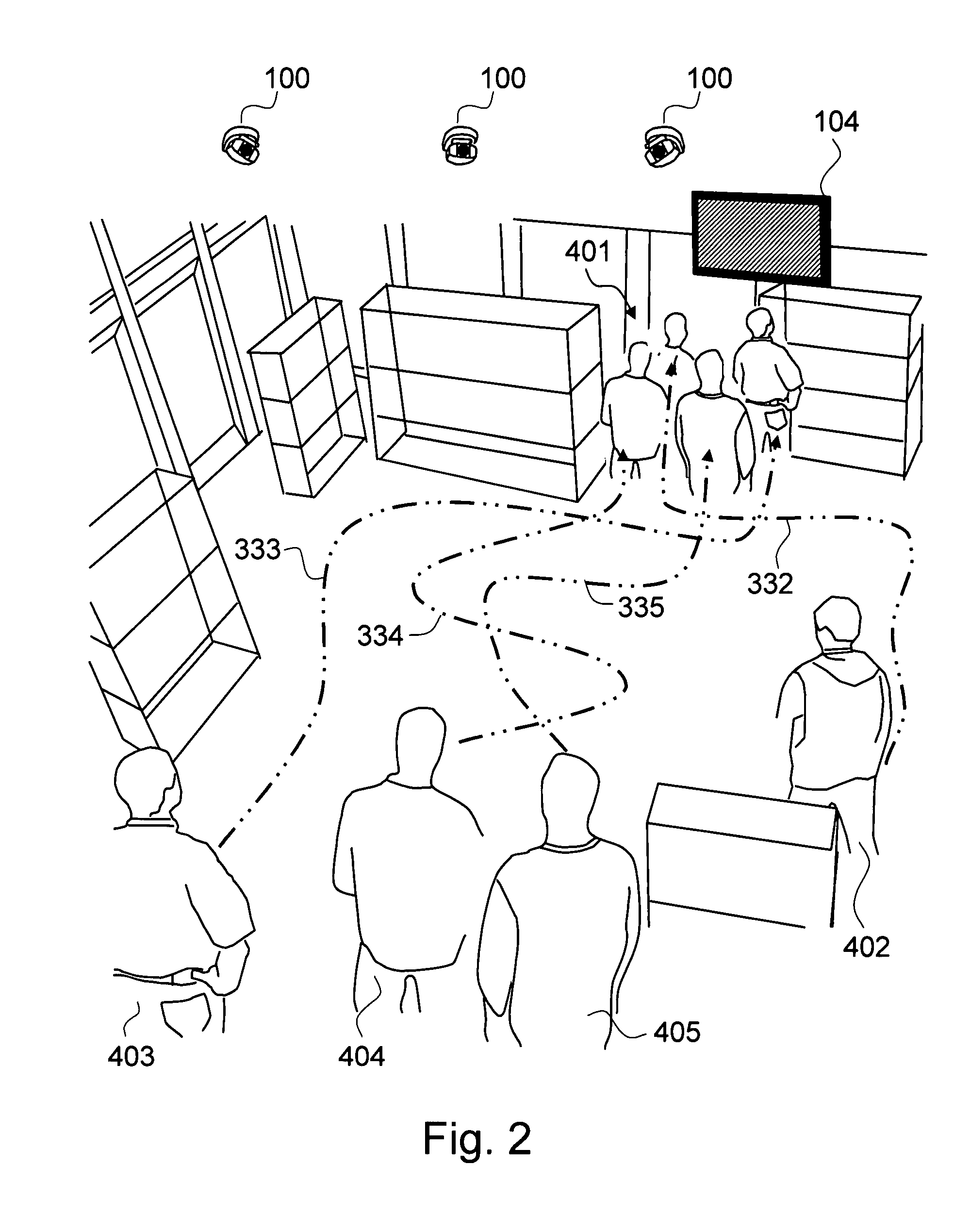
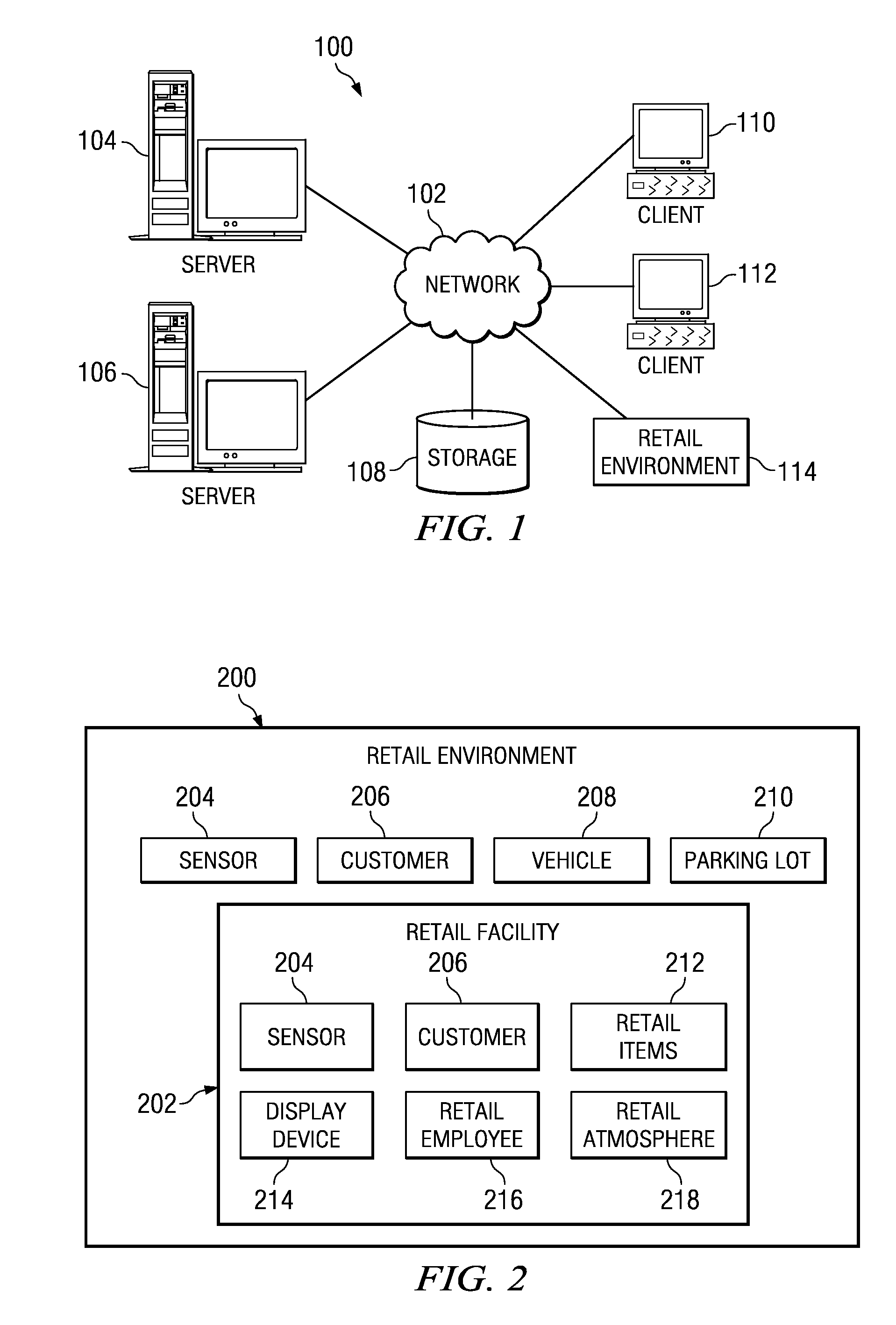
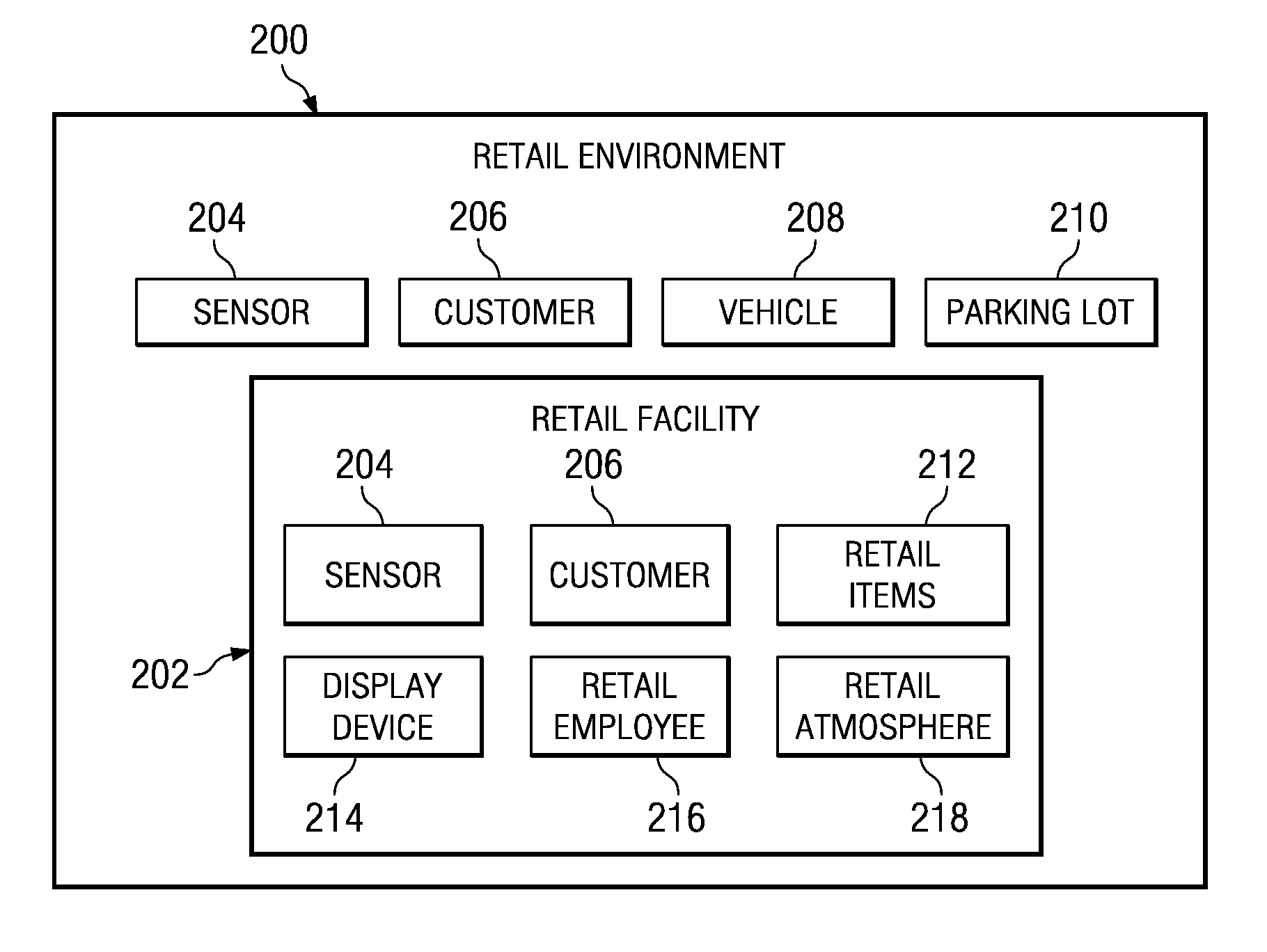
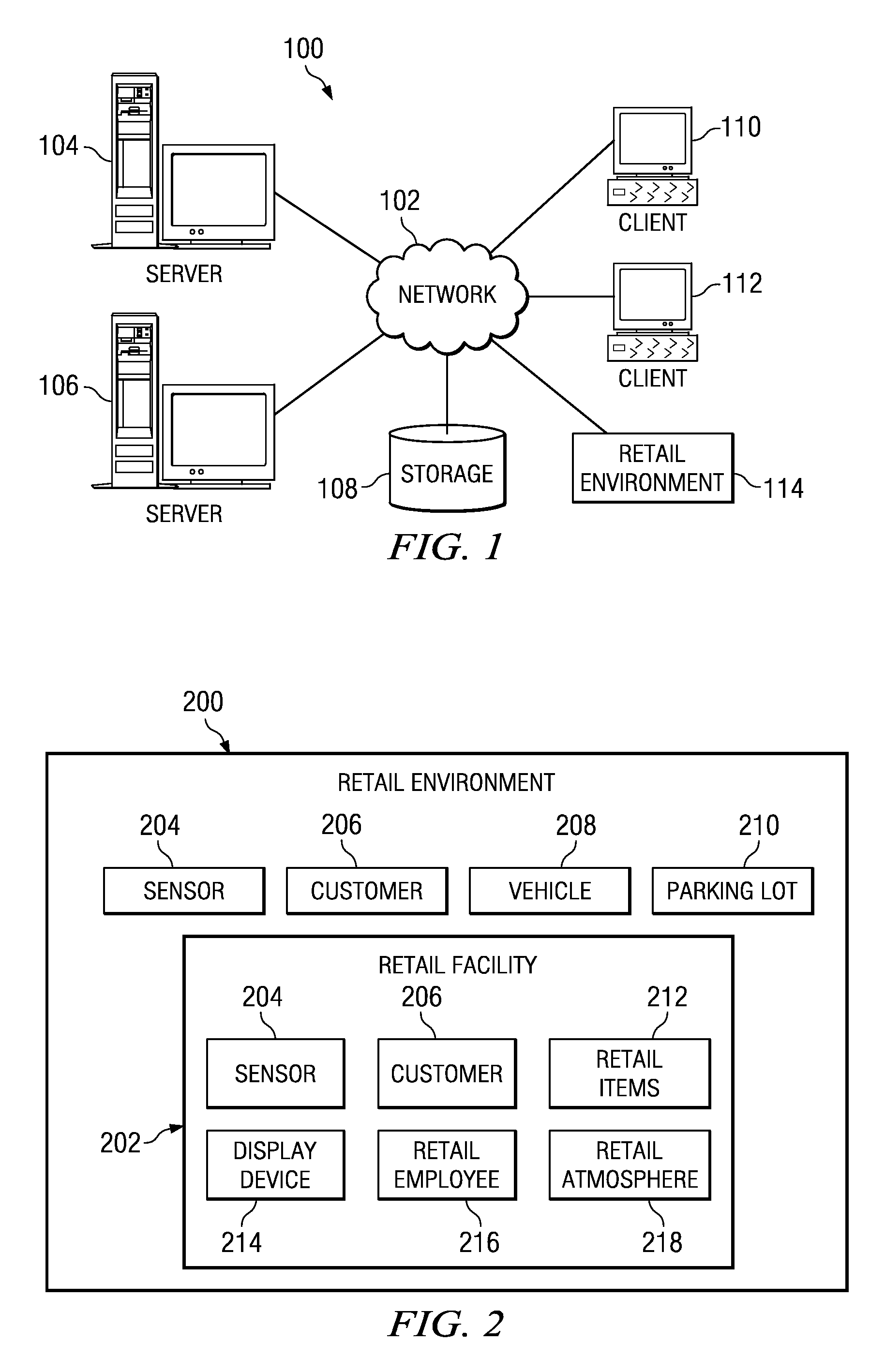
Method and system for narrowcasting based on automatic analysis of customer behavior in a retail store
ActiveUS7930204B1Efficient targetingGenerate interestMarket predictionsVisual perceptionBehavioral pattern
The present invention is a method and system for automatically changing the advertisement contents on a means for displaying the contents based on a customer's behavior or a group of customers' behavior in a retail store. The analysis of behavioral pattern is performed automatically and in real-time based on the visual information from the shopping and walkthrough history of a customer or a group of customers, using arrays of sensing devices, such as a plurality of means for capturing images, and a plurality of computer vision technologies on the visual information.
Owner:NYTELL SOFTWARE LLC
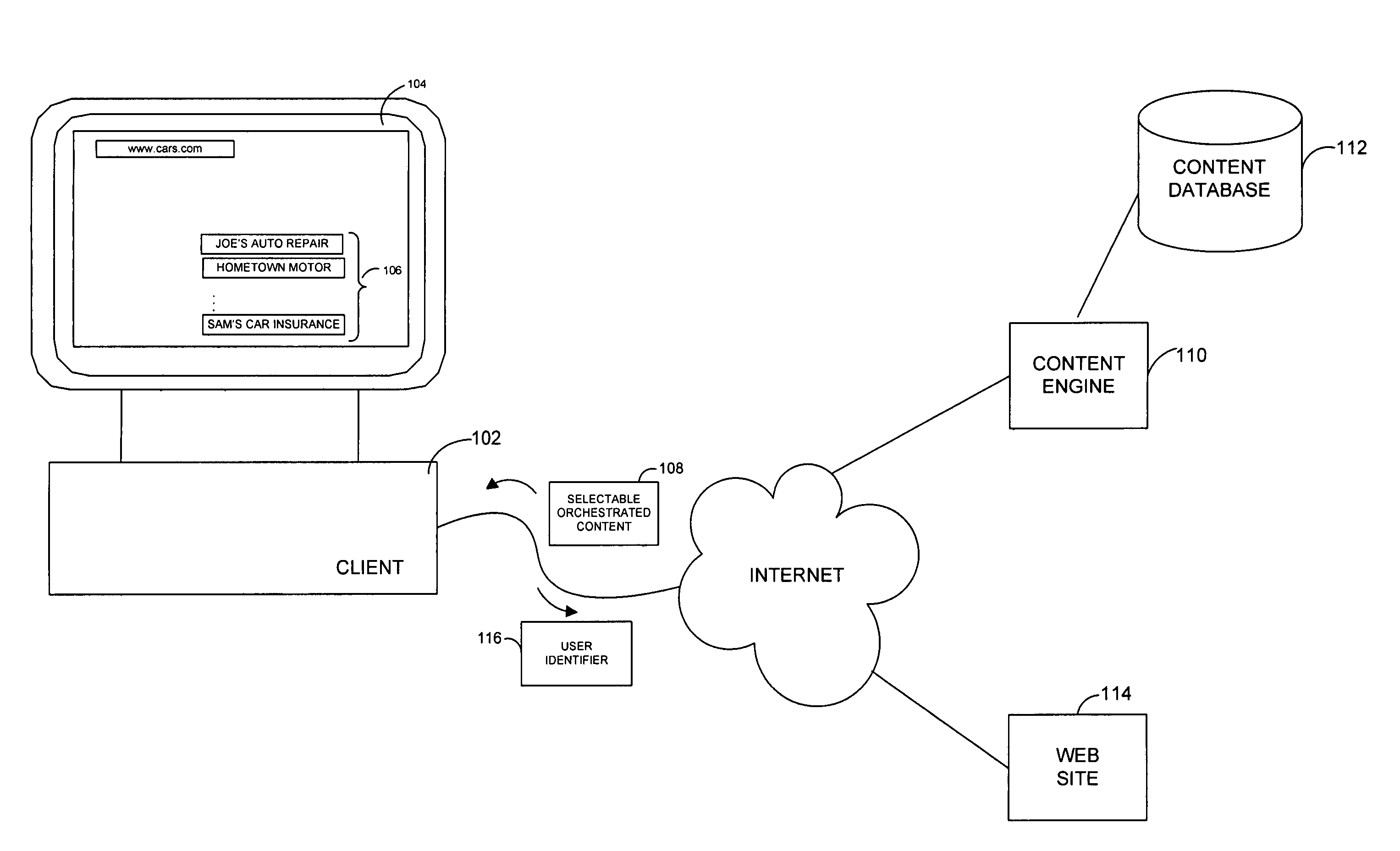
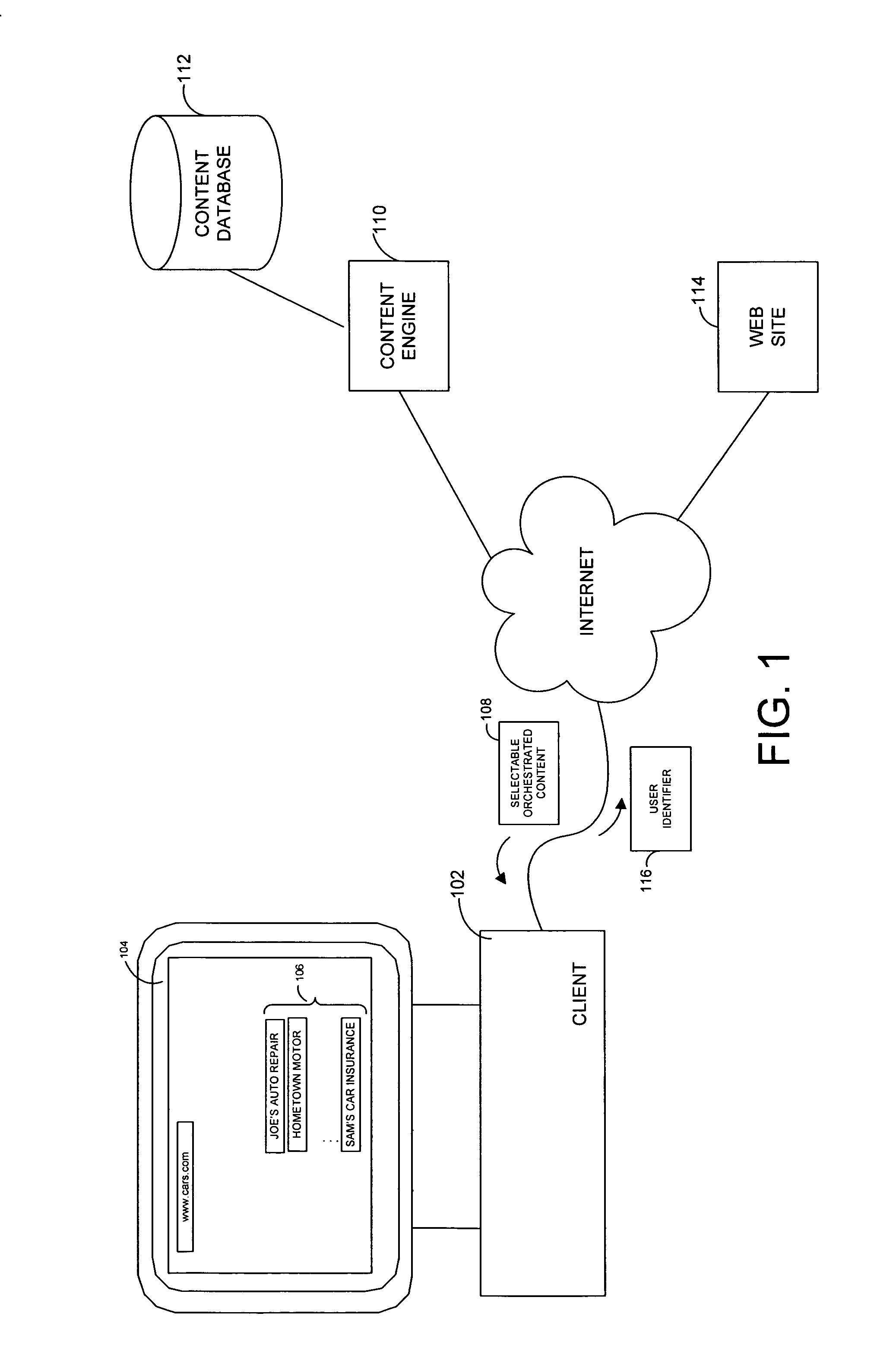
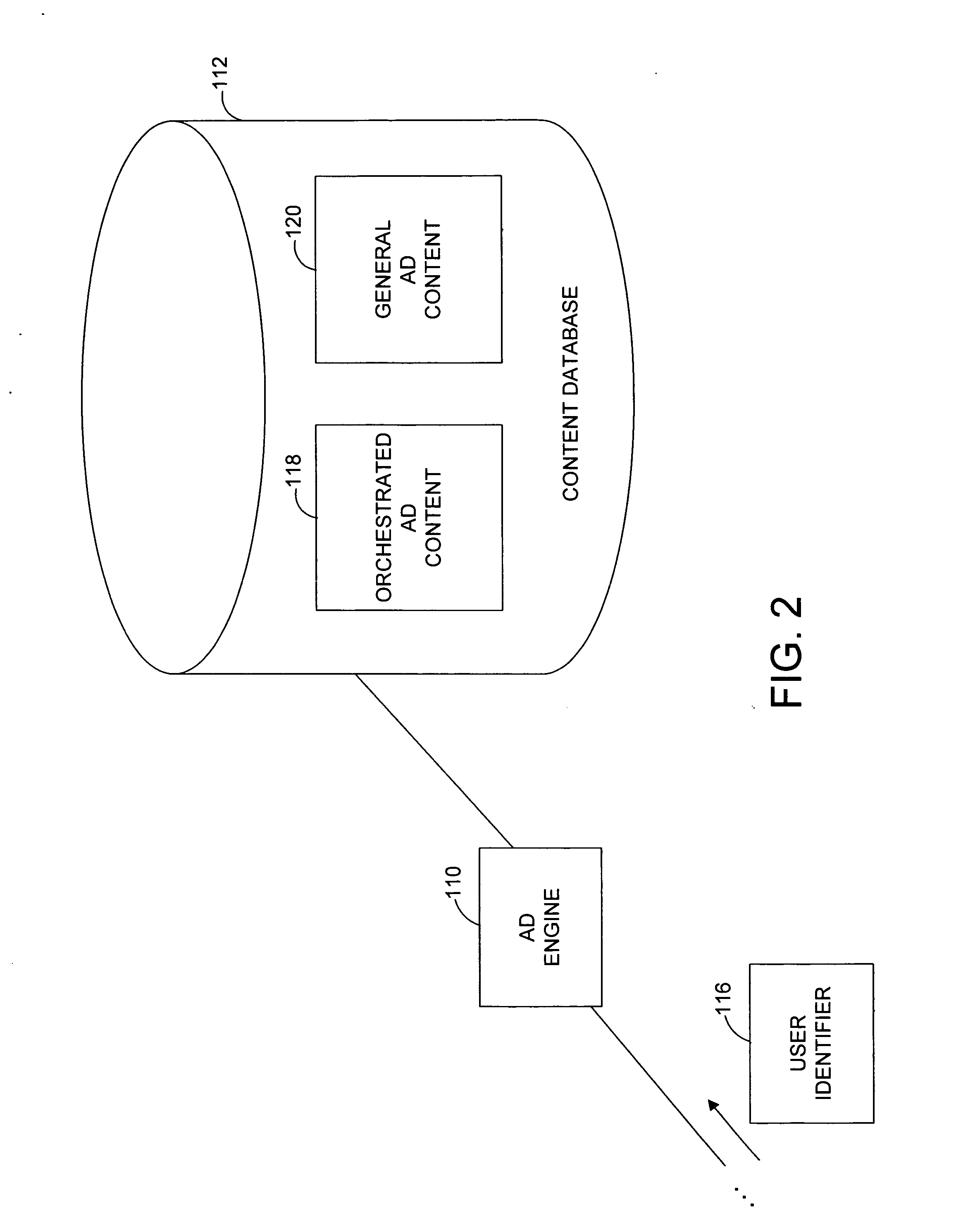
System and method for generating an orchestrated advertising campaign
InactiveUS20060069612A1Great amount of impactImprove impactMarketingUnique identifierUser identifier
A system and related techniques host and serve selective, orchestrated advertising campaigns and other content to users depending on contributing advertisers' campaign strategies as well as use interests, prior history or experiences. According to embodiments, users may navigate to a Web or other network site which contains or invokes ads or other media or content. When ad or other content is called, according to the invention in one regard a user identifier may be checked, to determine whether the user has subscribed to or had a profile established with the orchestrated ad platform of the invention. If the user does have a unique identifier associated with them, an ad engine may perform a lookup of the identifier against potential ad campaigns or delivery modes, to deliver a more coherent or orchestrated stream of ads or other media to the user. Those selected campaigns may include for instance immersive delivery modes in which a number of ads related to an area of interest, such as cars and related services or foods and restaurants, may be delivered or streamed to the user's browser or other application at a comparatively high frequency or intensity. The sequence of that content may in one regard be conditioned on the user's browsing or other history, including topics of interest as expressed for example in prior search activity, in explicit questionnaires, or in prior purchase or shopping activity, as well as other behavioral patterns such as averaged length of browsing sessions, or other parameters. Because the experience which the user receives is targeted or tailored in nature, and in addition presents a set or series of content which is selected to reflect a meaningful relationship or theme, the effectiveness of the advertising or other content delivery campaign may be enhanced compared to undifferentiated delivery techniques.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for detecting malicious behavioral patterns in a computer, using machine learning
InactiveUS20080184371A1Memory loss protectionError detection/correctionComputer wormTheoretical computer science
Method for detecting malicious behavioral patterns which are related to malicious software such as a computer worm in computerized systems that include data exchange channels with other systems over a data network. According to the proposed method, hardware and / or software parameters that can characterize known behavioral patterns in the computerized system are determined. Known malicious code samples are learned by a machine learning process, such as decision trees, Naïve Bayes, Bayesian Networks, and artificial neural networks, and the results of the machine learning process are analyzed in respect to these behavioral patterns. Then, known and unknown malicious code samples are identified according to the results of the machine learning process.
Owner:DEUTSCHE TELEKOM AG
Method and system for detecting malicious behavioral patterns in a computer, using machine learning
InactiveUS20070294768A1Memory loss protectionUnauthorized memory use protectionComputer wormComputerized system
Method for detecting malicious behavioral patterns which are related to malicious software such as a computer worm in computerized systems that include data exchange channels with other systems over a data network. Accordingly, hardware and / or software parameters are determined in the computerized system that is can characterize known behavioral patterns thereof. Known malicious code samples are learned by a machine learning process, such as decision trees and artificial neural networks, and the results of the machine learning process are analyzed in respect to the behavioral patterns of the computerized system. Then known and unknown malicious code samples are identified according to the results of the machine learning process.
Owner:DEUTSCHE TELEKOM AG
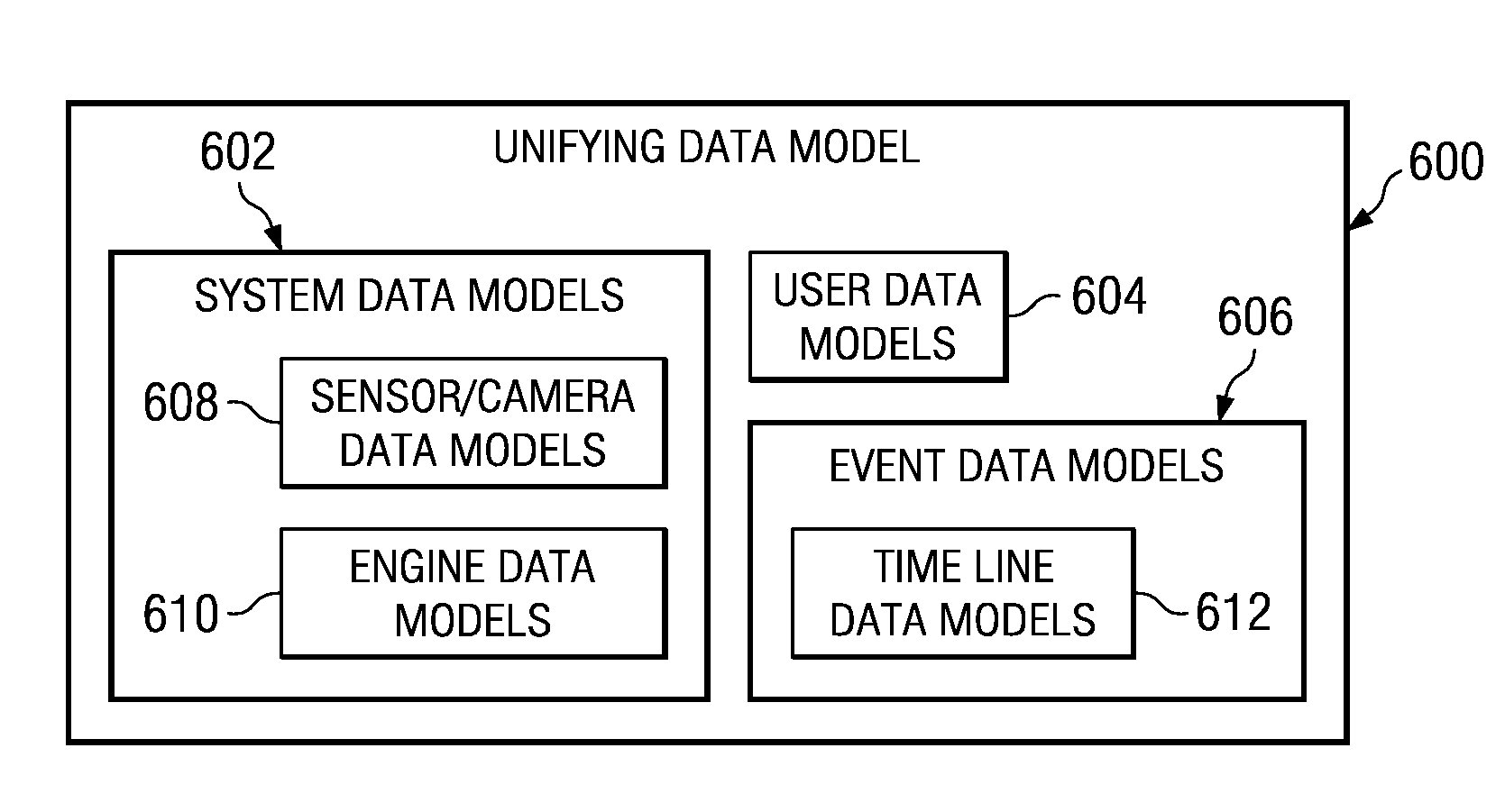
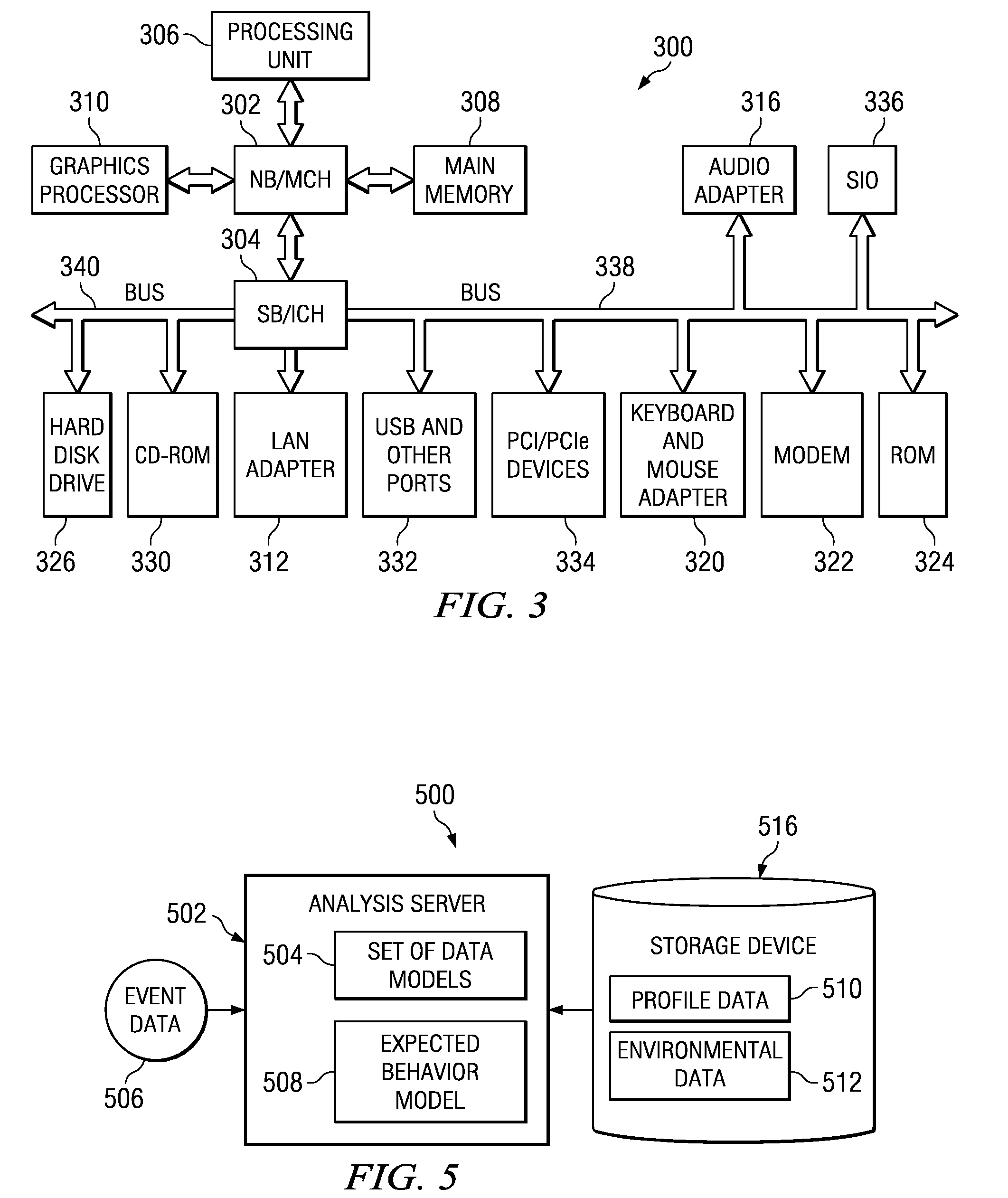
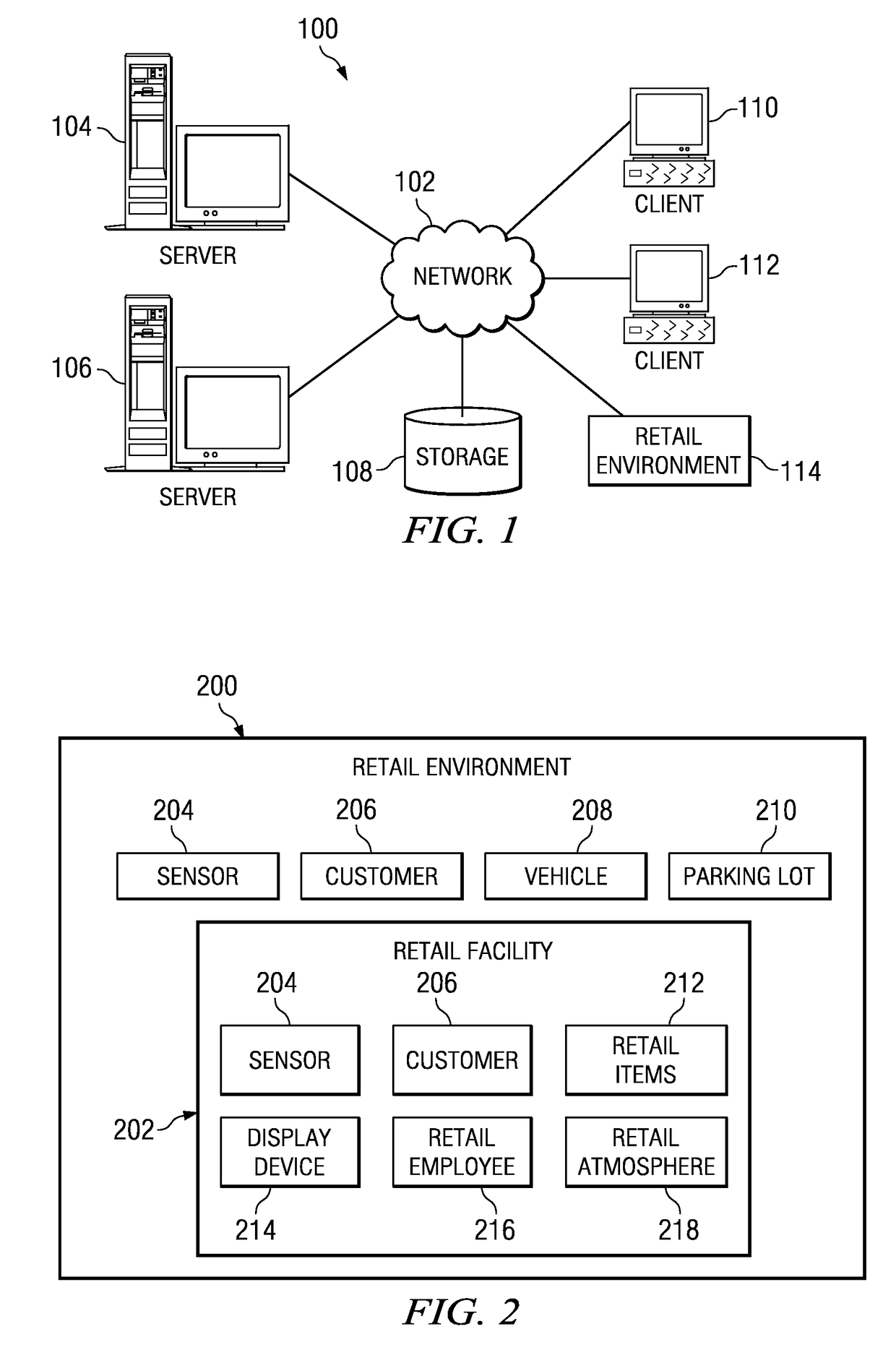
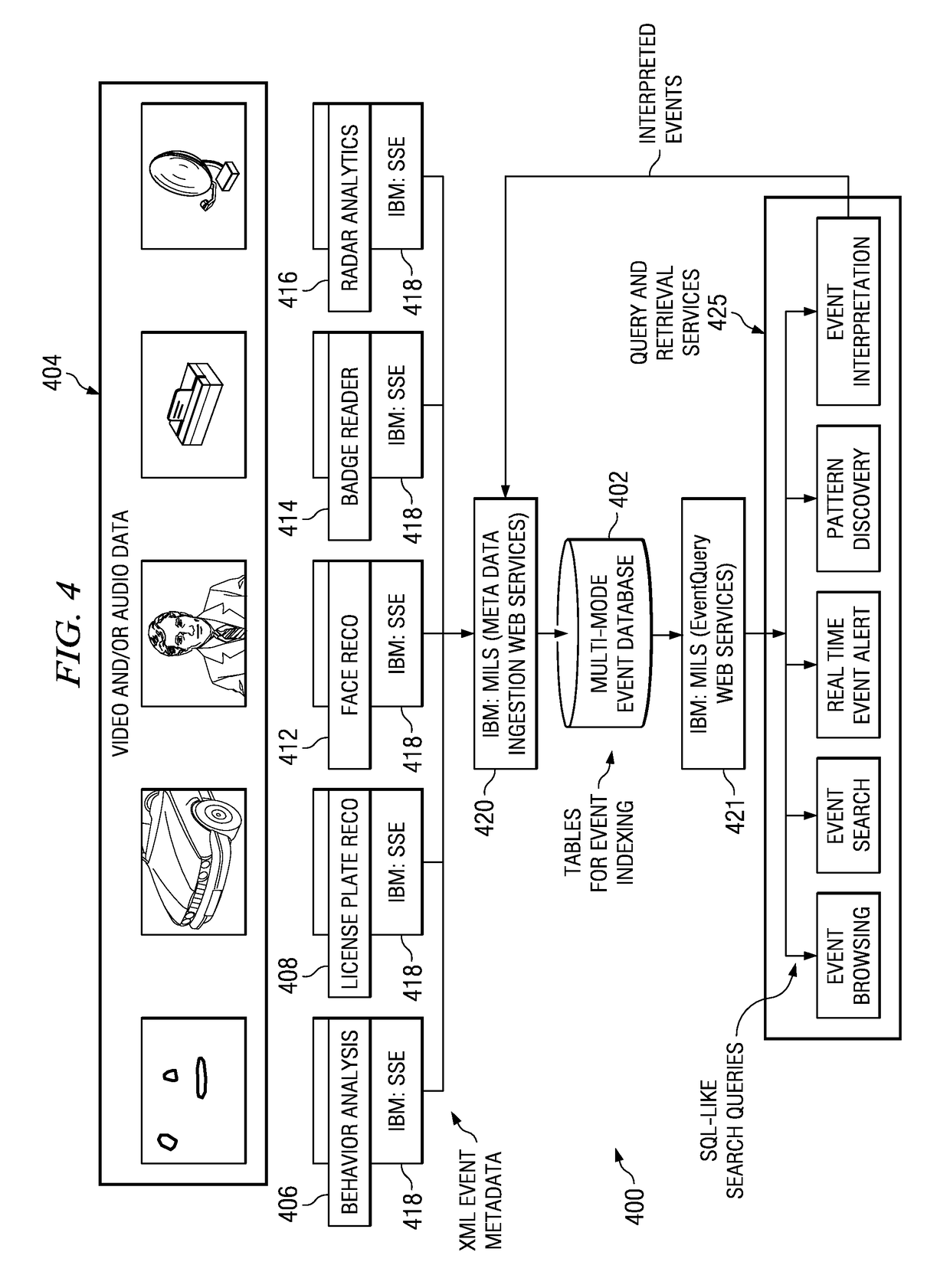
Method and apparatus for implementing digital video modeling to identify unexpected behavior
A computer implemented method, apparatus, and computer usable program product for identifying unexpected behavioral patterns. The process parses event data derived from video data to identify behavioral patterns, wherein the event data comprises metadata describing events occurring in a selected environment. The process analyzes the behavioral patterns to identify a set of expected behavioral patterns occurring in the selected environment, and generates an expected behavioral model using the expected behavioral patterns. Thereafter, the process forms a set of unexpected behavioral patterns from the behavioral patterns inconsistent with the expected behavioral model.
Owner:IBM CORP
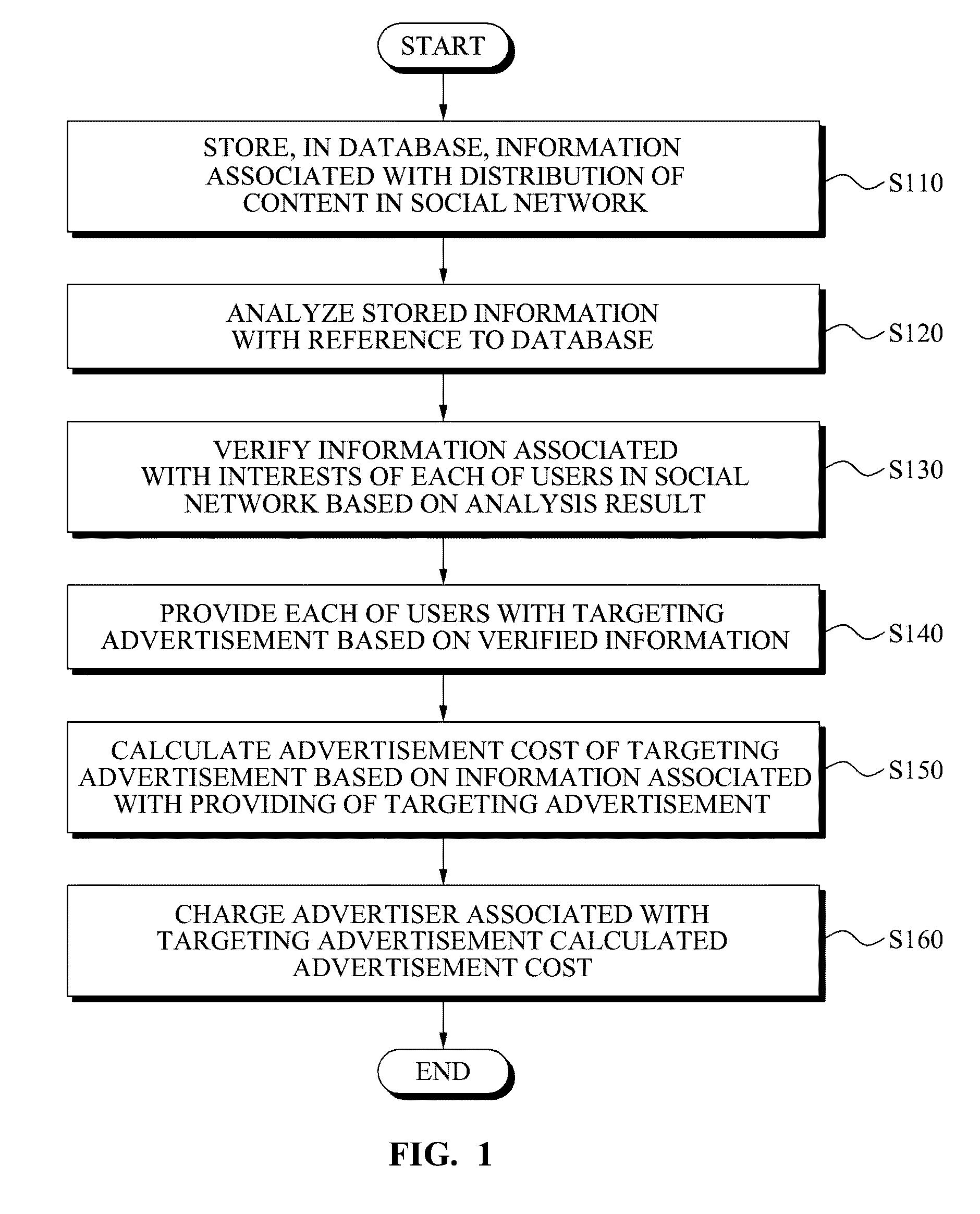
Method and system for providing targeting advertisement service in social network
InactiveUS20090216620A1Advertisement revenueMarket data gatheringReference databaseBehaviour pattern
Provided is a system for providing a targeting advertisement service in a social network, the system including: a database to store information associated with a distribution of a content in the social network; an analysis unit to analyze the stored information with reference to the database, and to verify a behavioral pattern or a matter of concern of each of users in the social network based on the analysis result; and an advertisement unit to provide each of the users with a targeting advertisement, based on the verified behavioral pattern or the matter of concern.
Owner:SAMJIN LND +1
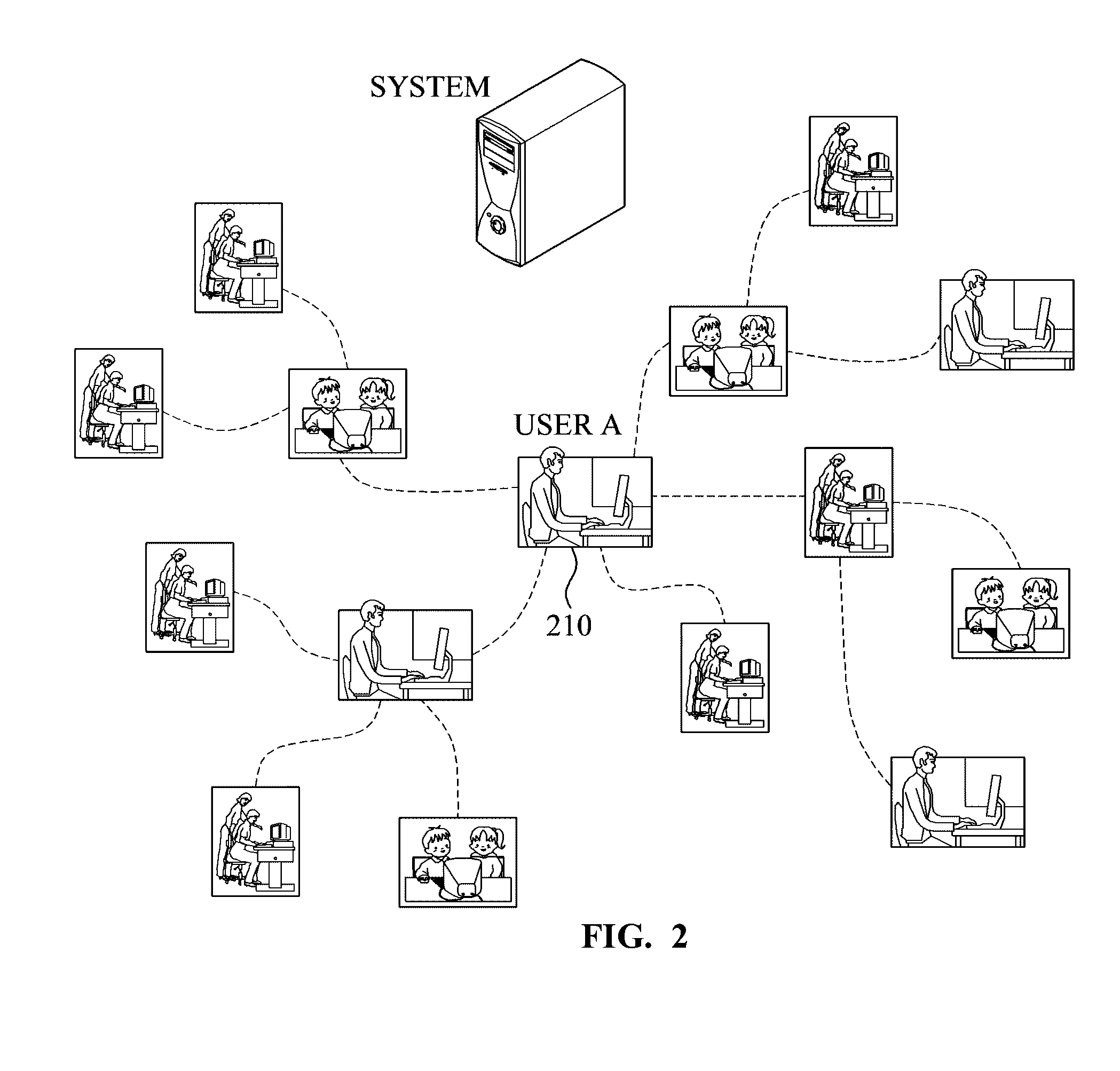
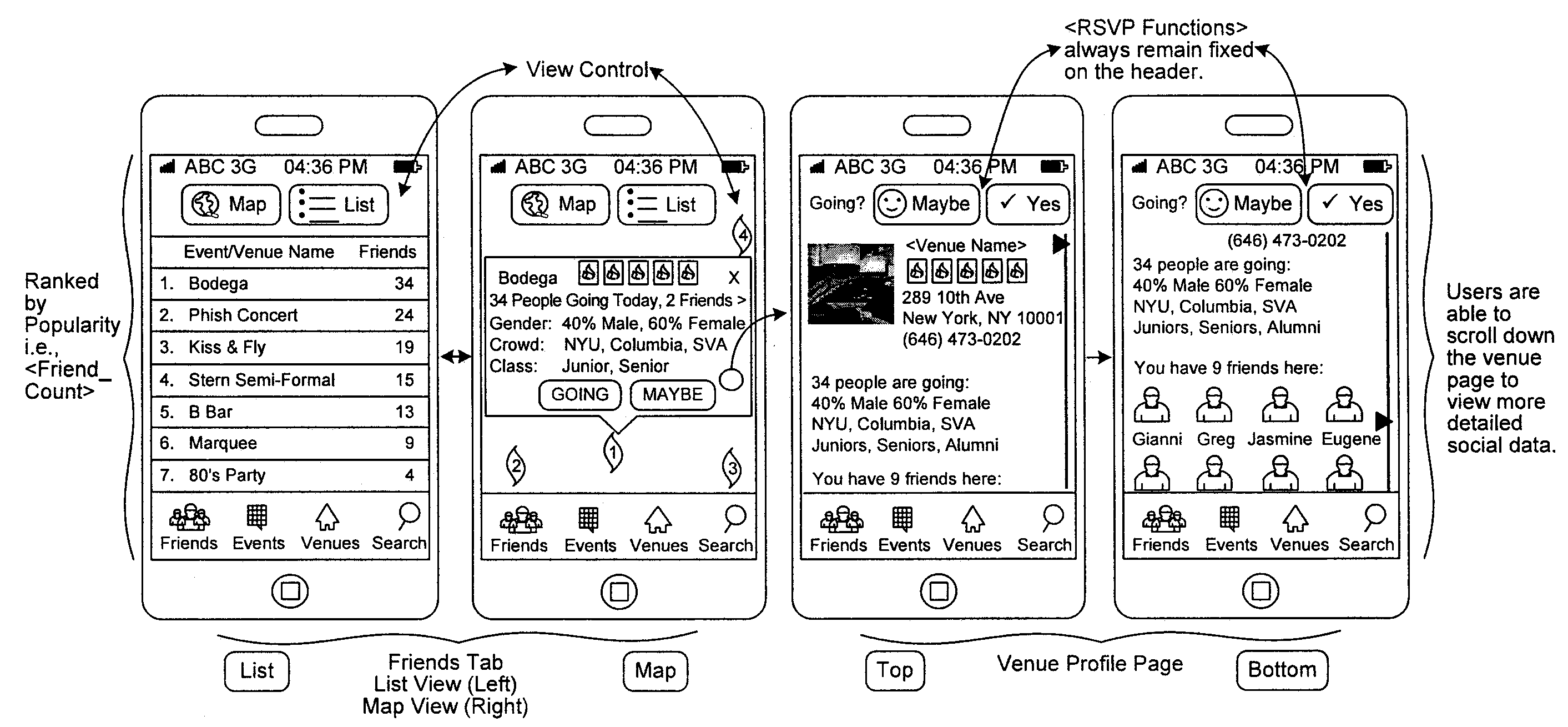
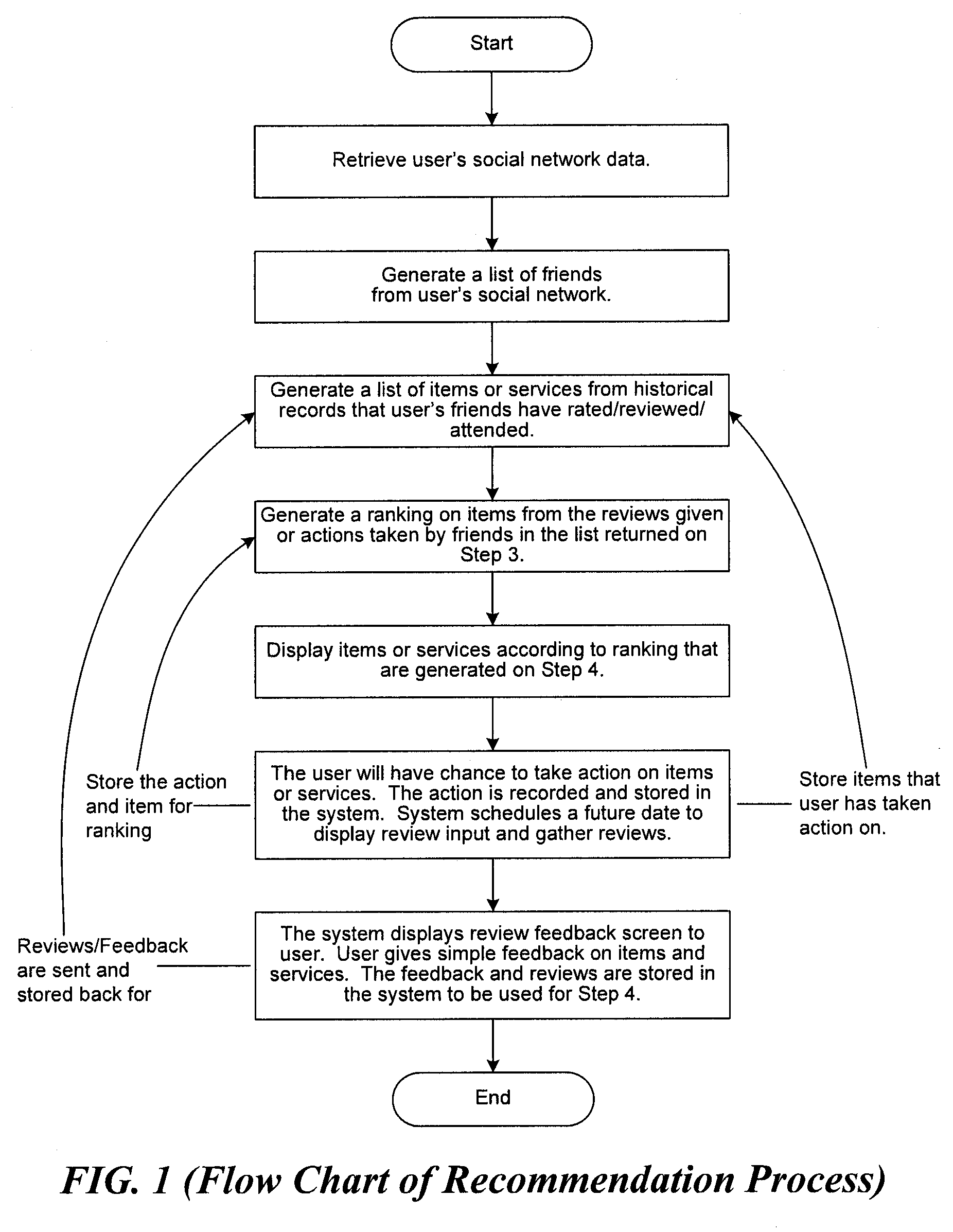
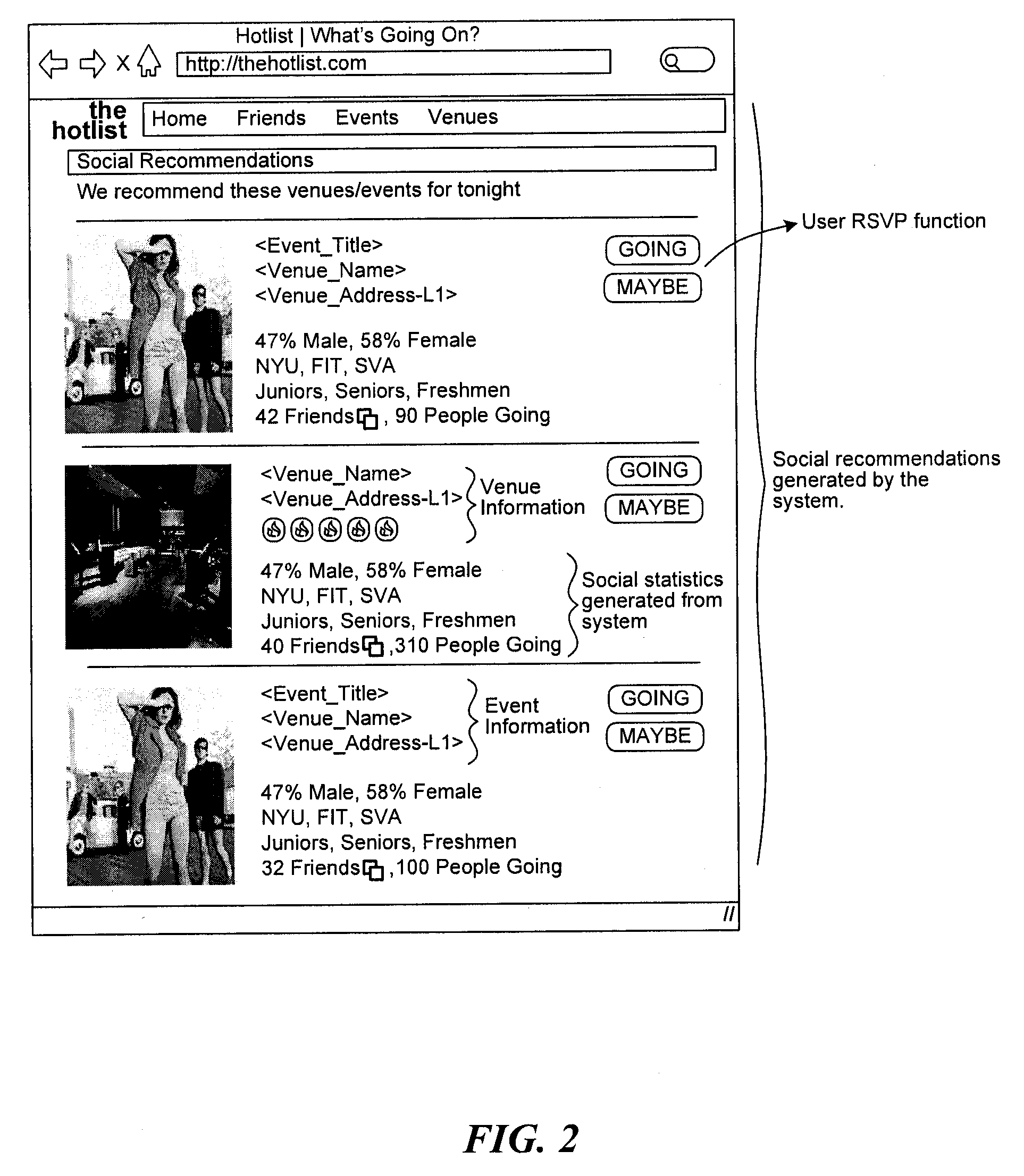
System and method for recommending venues and events of interest to a user
InactiveUS20090287687A1MarketingSpecial data processing applicationsSocial statisticsDemographic data
A system and method is disclosed for recommending venues and events to individual users using a combination of collaborative filtering and integrating social behavioral pattern data gathered and computed via an electronic device. The system and method of the present invention is configured to receive data based on users' past, present and future social activity and interests, which are submitted to the system via an electronic device. When a new data item is made available from sources such as a mobile device, social networks or GPS systems, the system and method analytically breaks down the new item data, compares it to ascertained attributes of item data that a user (i.) indicated interest to in the past, (ii.) has a friend or related network of users that indicated interest in the venue or in an event in the past, and (iii.) indicated interest in the event or venue based upon general social statistics such as male to female ratio, age, and other demographics gathered and computed by the system. The system generates the recommendations using a previously-generated table which maps items to lists of “similar” items thereby making a audience-specific, time-specific and location-specific social recommendation.
Owner:HOTLIST MEDIA
Detecting Behavioral Patterns and Anomalies Using Activity Data
ActiveUS20070156696A1Potential security breachSpecific access rightsError detection/correctionBehaviour patternComputer science
Activity data is analyzed or evaluated to detect behavioral patterns and anomalies. When a particular pattern or anomaly is detected, a system may send a notification or perform a particular task. This activity data may be collected in an information management system, which may be policy based. Notification may be by way e-mail, report, pop-up message, or system message. Some tasks to perform upon detection may include implementing a policy in the information management system, disallowing a user from connecting to the system, and restricting a user from being allowed to perform certain actions. To detect a pattern, activity data may be compared to a previously defined or generated activity profile.
Owner:NEXTLABS
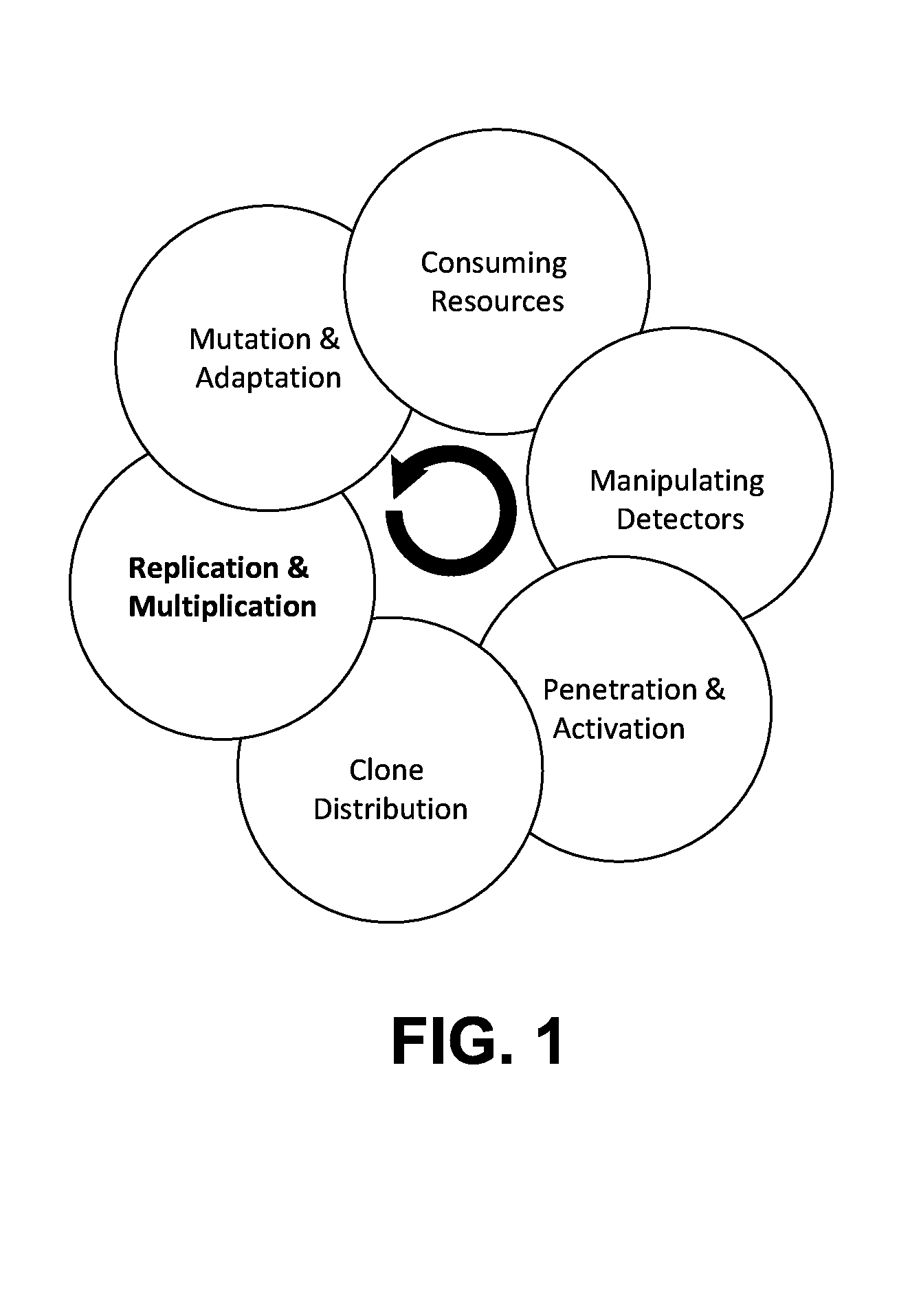
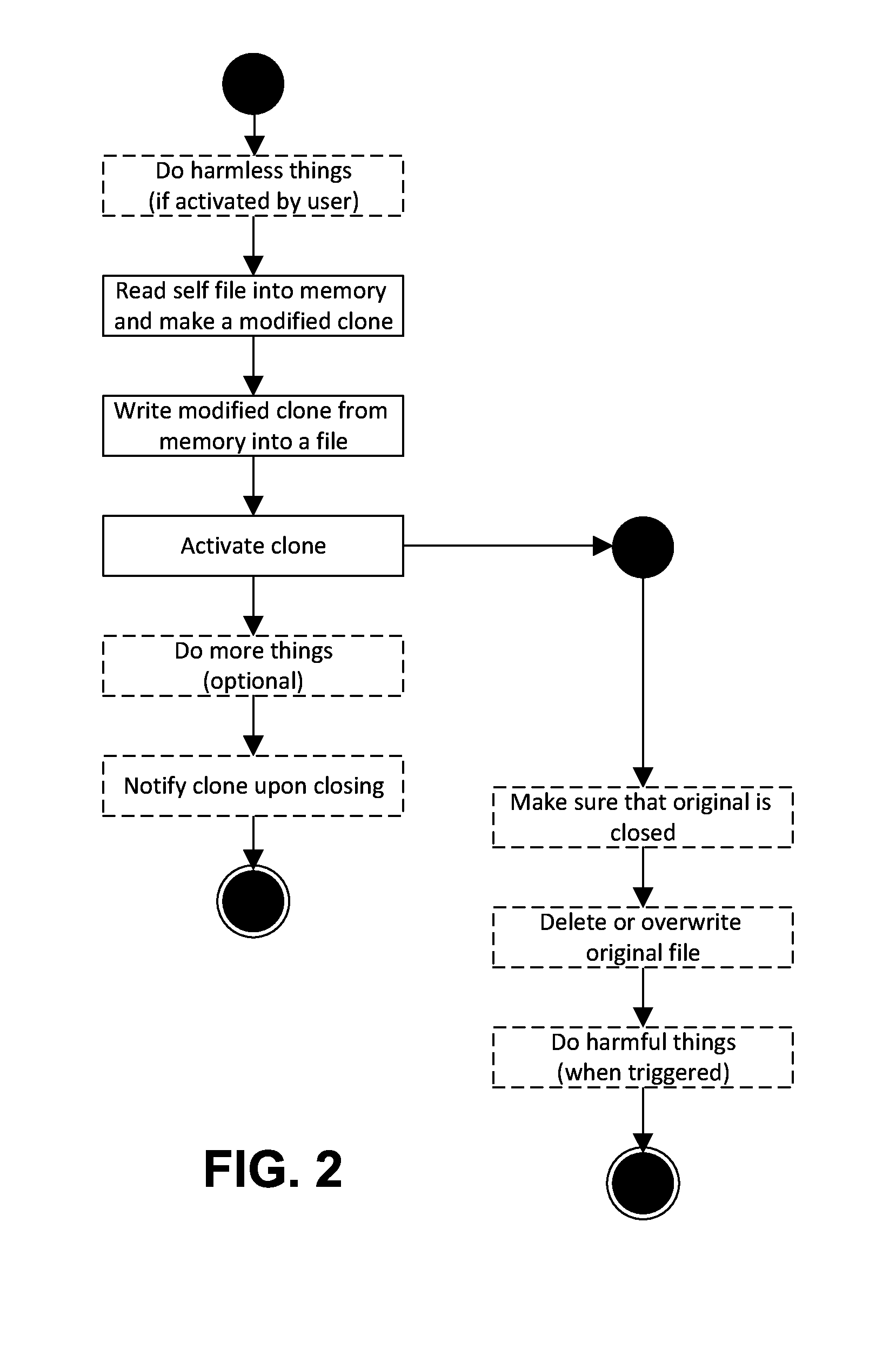
Runtime detection of self-replicating malware
ActiveUS20140123280A1Memory loss protectionUnauthorized memory use protectionTheoretical computer scienceUnique identifier
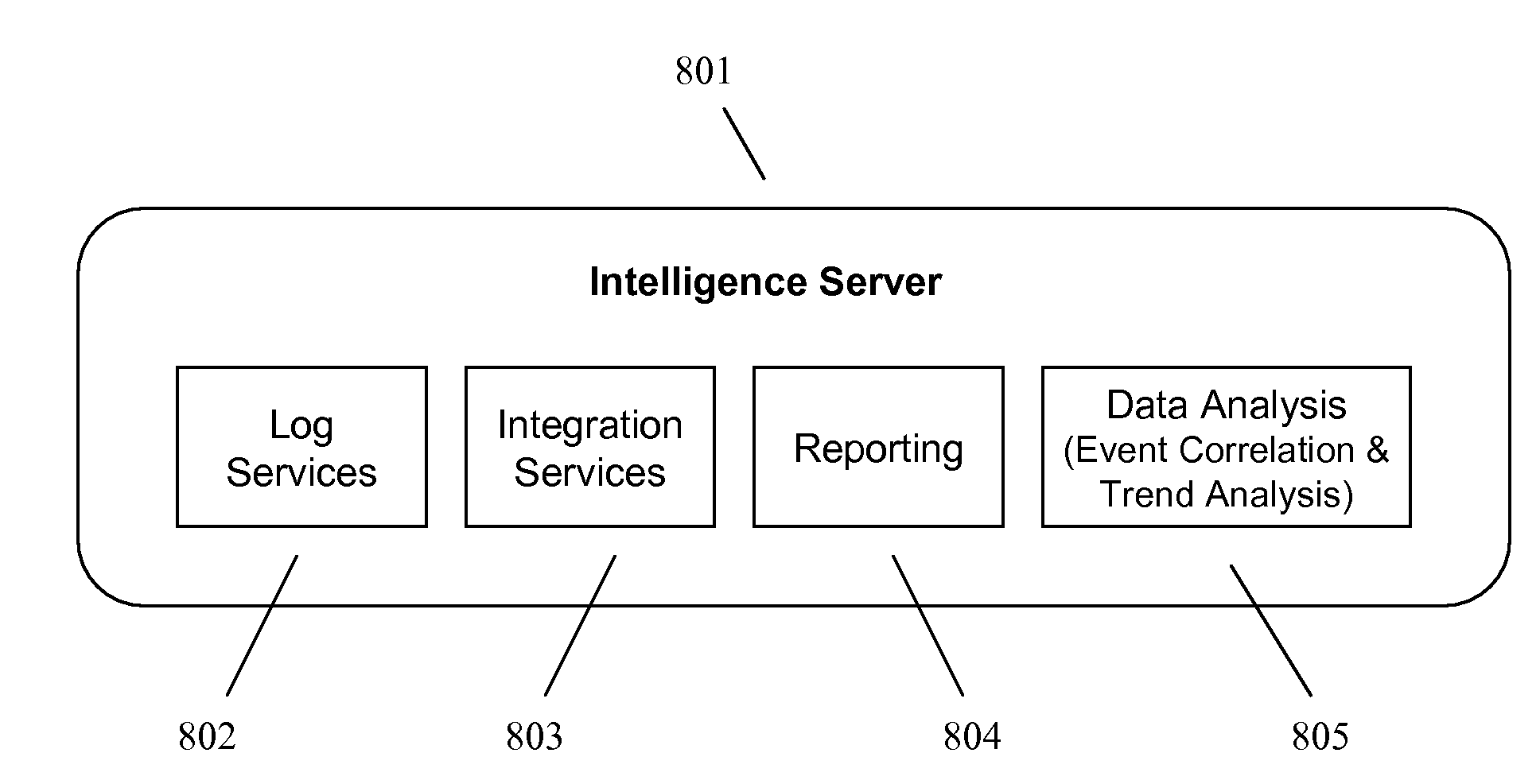
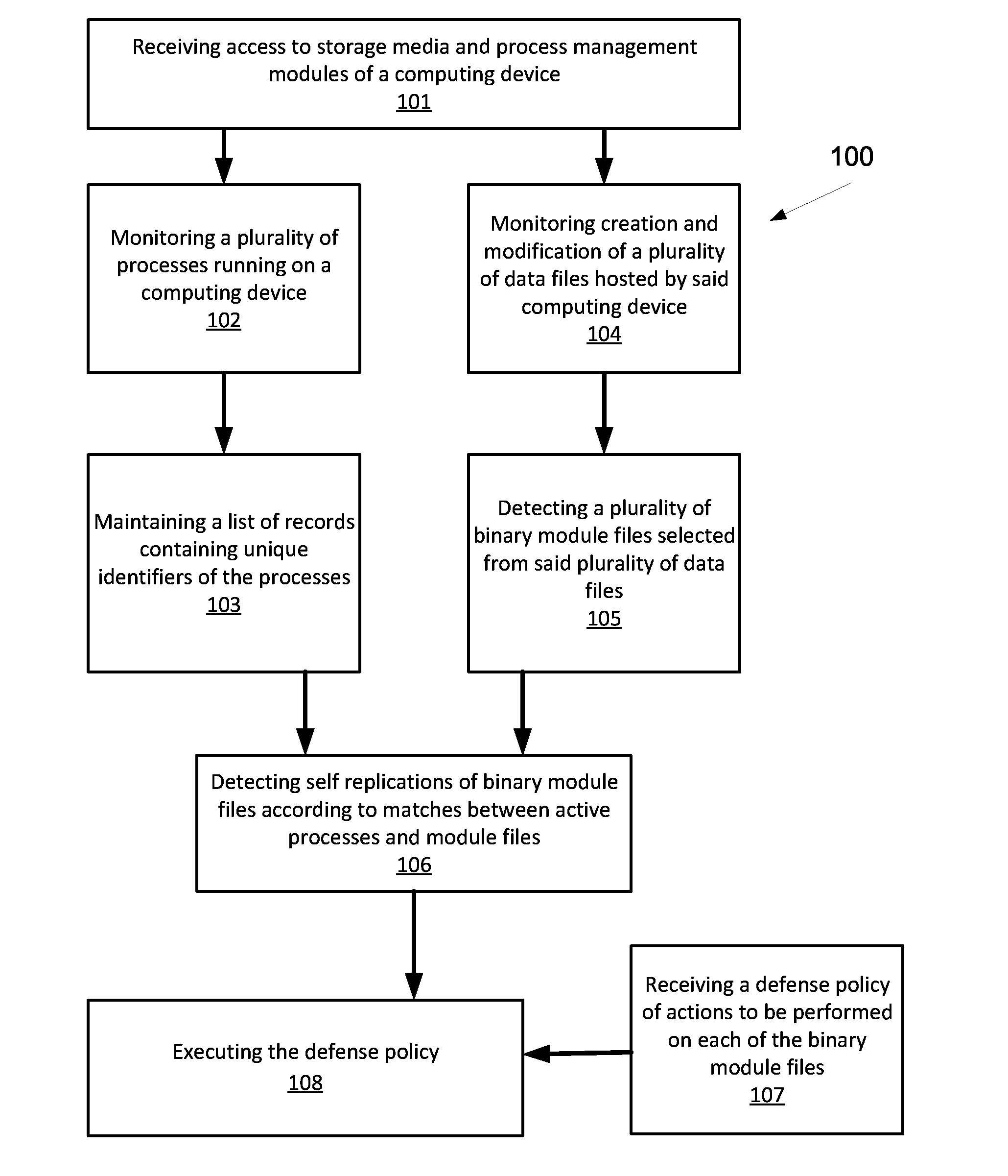
A method for detecting malicious active processes and self replicating executable binary files on a computing device. The method comprises monitoring in runtime active processes running on a computing device, extracting unique identifier(s) of each of the active processes which maps the active process to executable binary file(s) containing executable code of the active process, monitoring in runtime creation and modification of data files hosted by the computing device, identifying executable binary files among the data files, monitoring concurrent operation of logical sensors which detect malicious behavioral patterns of the active processes and maintain one or more lists of malicious behavioral pattern findings, and detecting malicious active process(es) of a malware from the active processes and self-replicating executable binary file(s) of the malicious active process(es) according to a match between the respective unique identifier(s), the malicious behavioral pattern findings and at least one the executable binary files.
Owner:KEDMA GABRIEL +1
System and method for using a data genome to identify suspicious financial transactions
A system and method for using a data genome to identify suspicious financial transactions. In one embodiment, the method comprises receiving a data set of financial activity data of multiple participants; configuring a deep neural network and thresholds, wherein the thresholds enable detection of what is within abnormal range of financial activity, patterns, and behavior over a period of time; converting the data set to a genome containing a node for each participant among the multiple participants; computing threat vectors for each node within a graphical representation of the genome that represents behavioral patterns of participants in financial activities, including determining when a key risk indicator (KRI) value computed for a particular threshold within the data set falls outside of a dynamically determined range bounded by thresholds, wherein the threat vectors automatically identify one or more of suspicious participants and suspicious activities in a provided financial activity pattern; and determining a particular edge in the network whose behavior falls outside the dynamically determined range associated with normal activity as a suspicious.
Owner:EVENTUS SYST INC
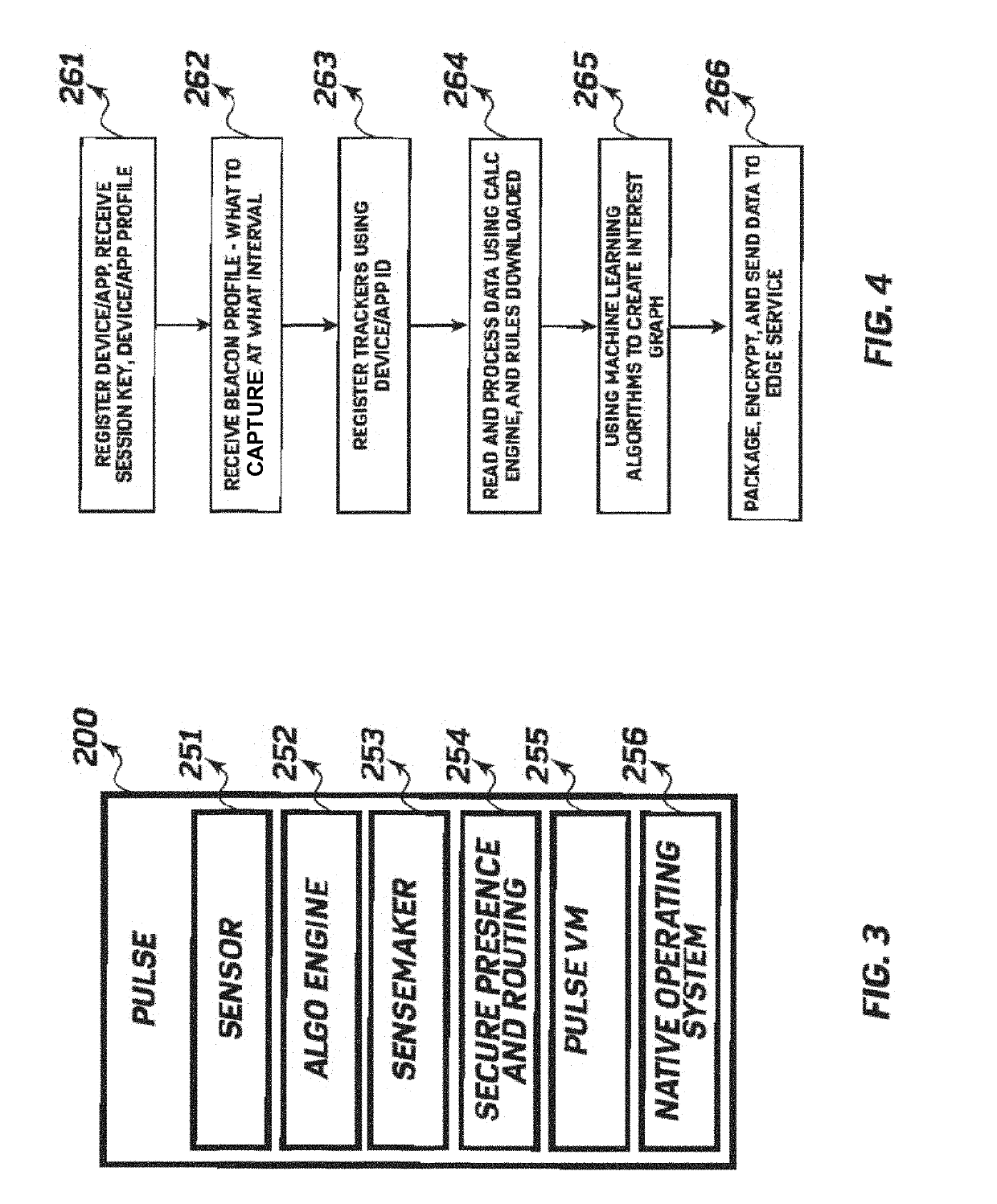
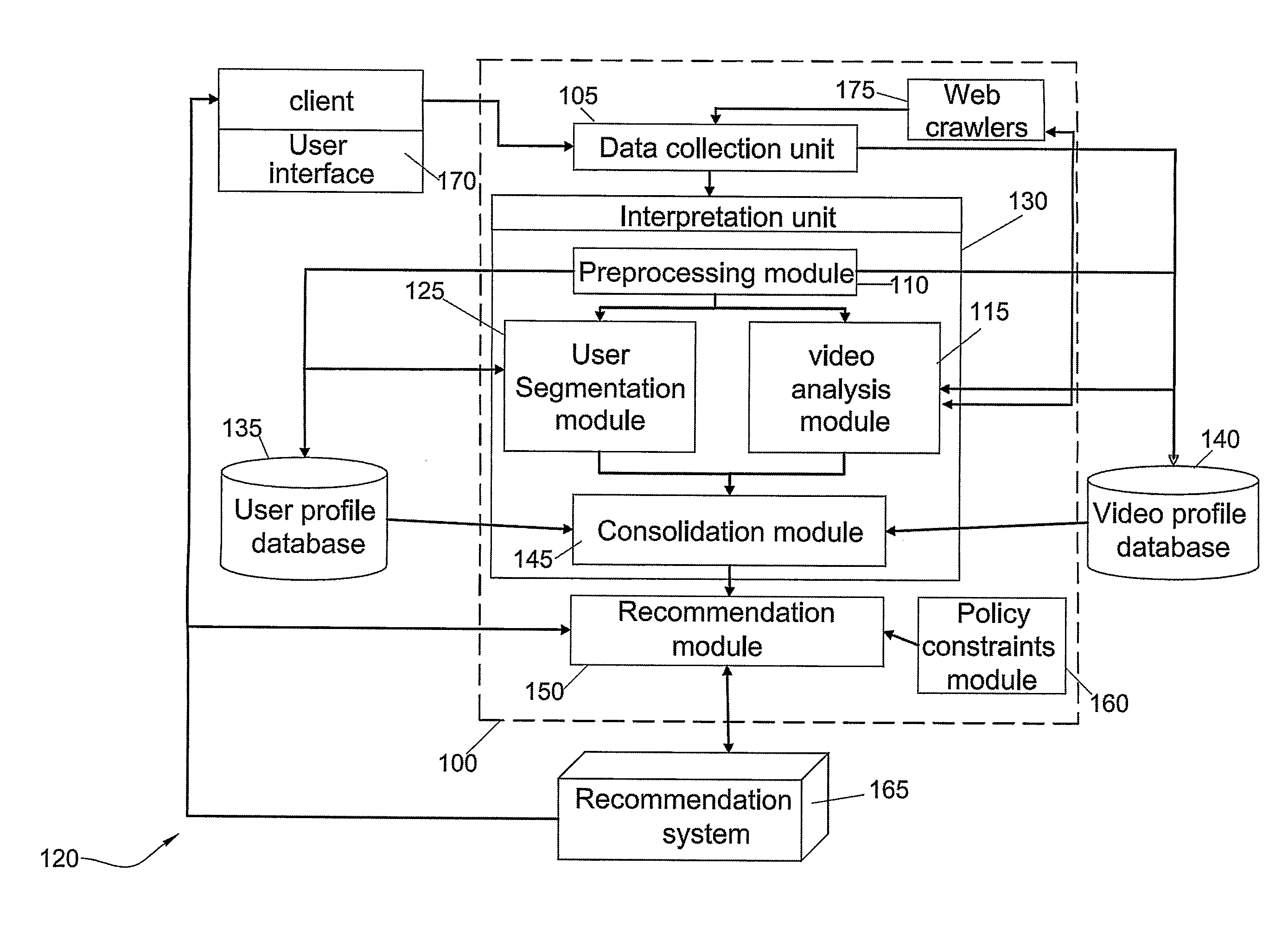
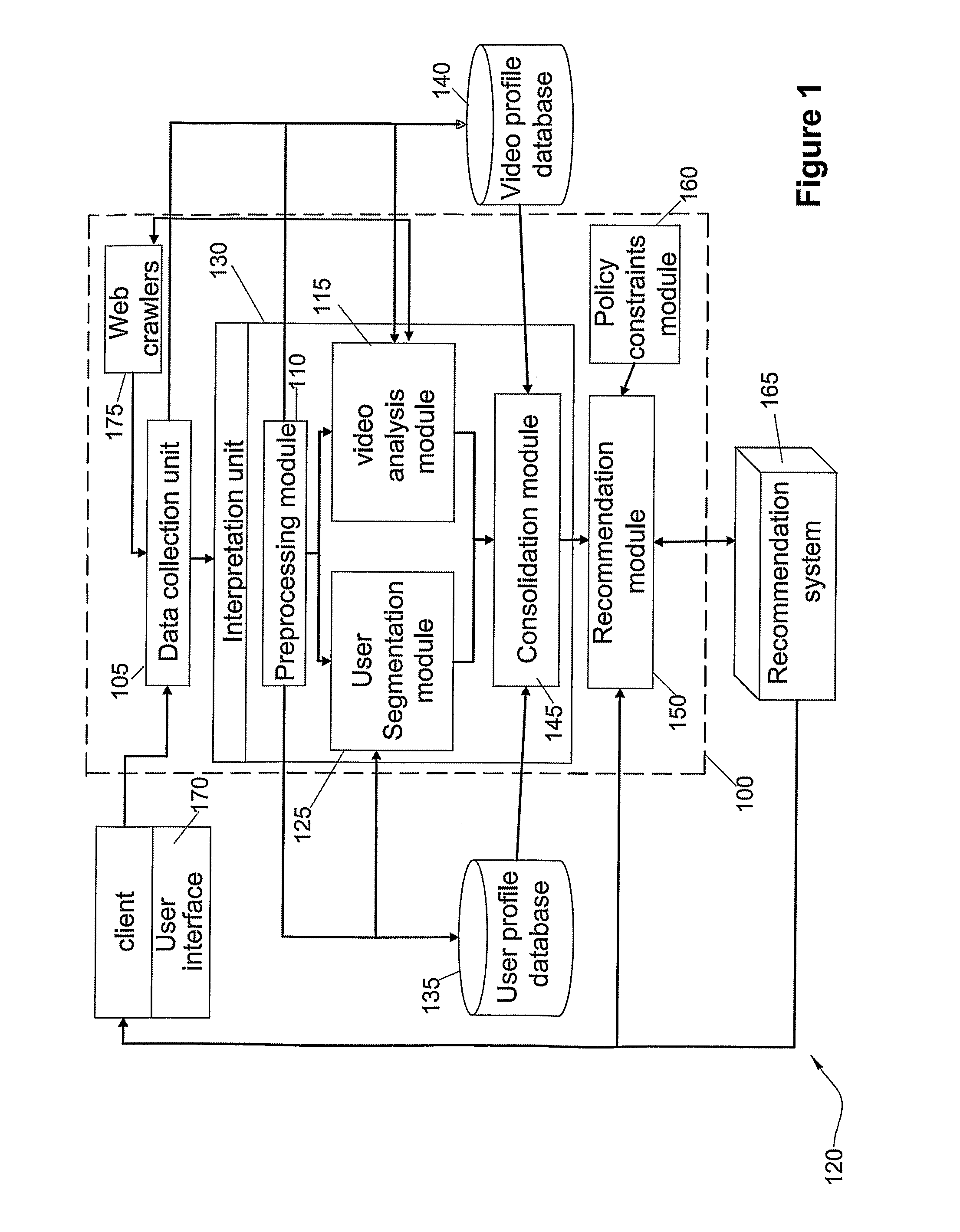
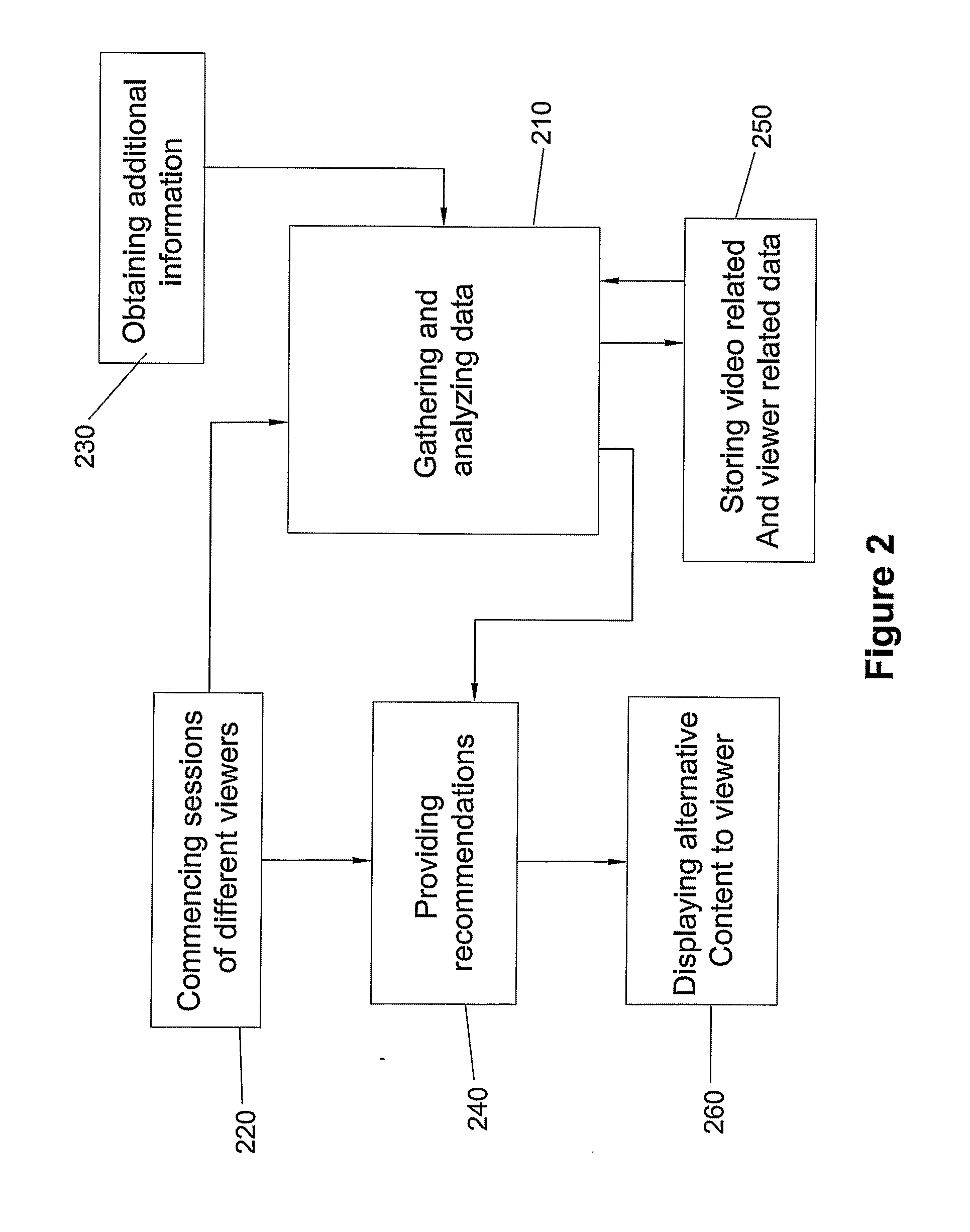
System And Method For The Presentation Of Alternative Content To Viewers Video Content
ActiveUS20110282745A1Broadcast services for monitoring/identification/recognitionBroadcast information monitoringComputer visionBehavioral pattern
Owner:TABOOLA COM
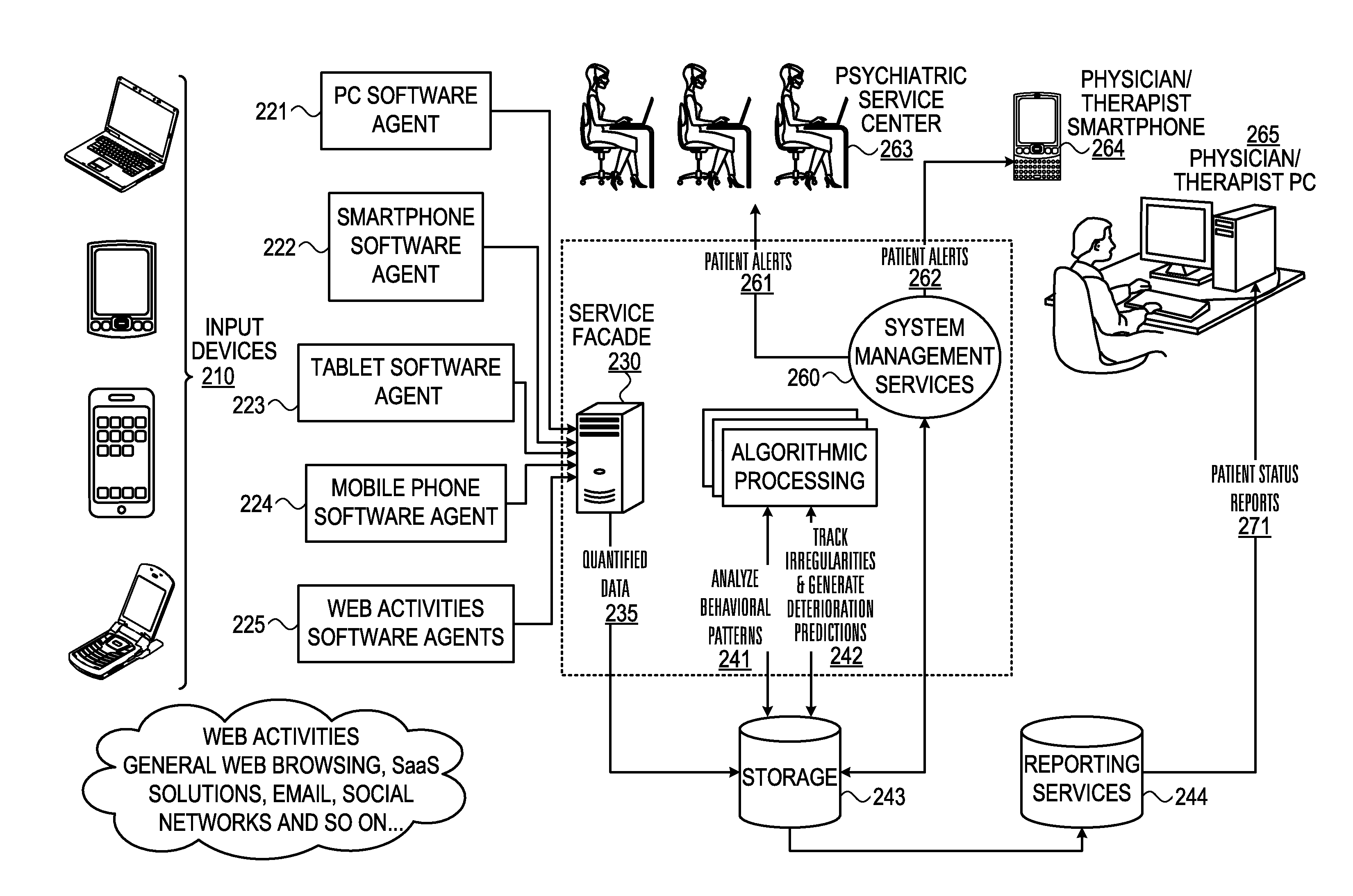
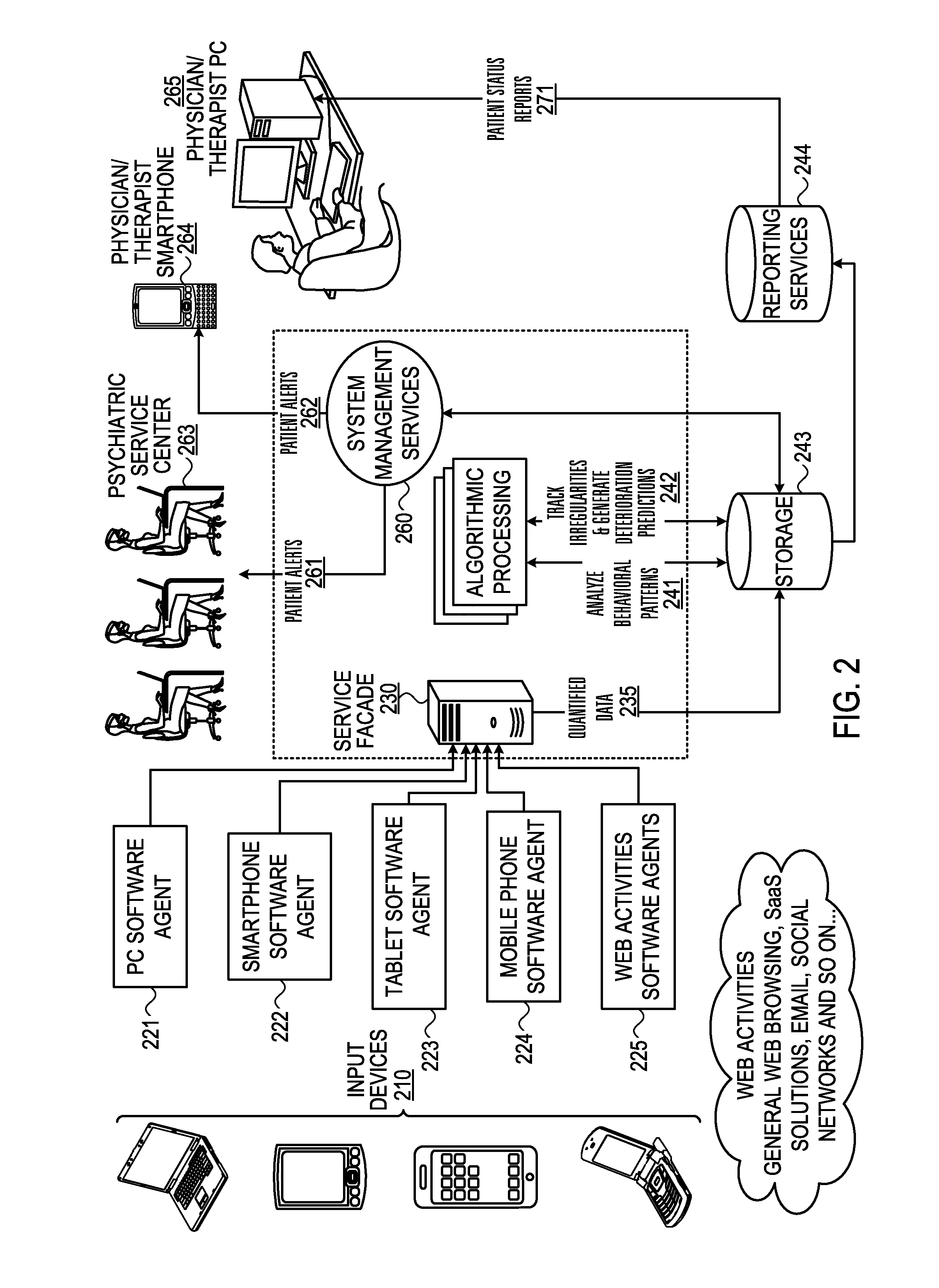
Mental health digital behavior monitoring support system and method
InactiveUS20130297536A1Digital computer detailsMedical automated diagnosisTablet computerSupporting system
A system and method for monitoring a user's mental health tor and collect data concerning. The user's use of electronic devices is tracked, such as usage of his mobile phone, tablet and his web activity. The invention “learns” each patient's unique behavioral patterns to be used as a “base line” representing the steady state (chronic phase) of the patient. The algorithmic processing unit detects any irregularities in a patient's behavioral patterns and produces a deterioration prediction. If it is determined that a threshold is exceeded, an alert is sent to a health professional.
Owner:ALMOSNI BERNIE +1
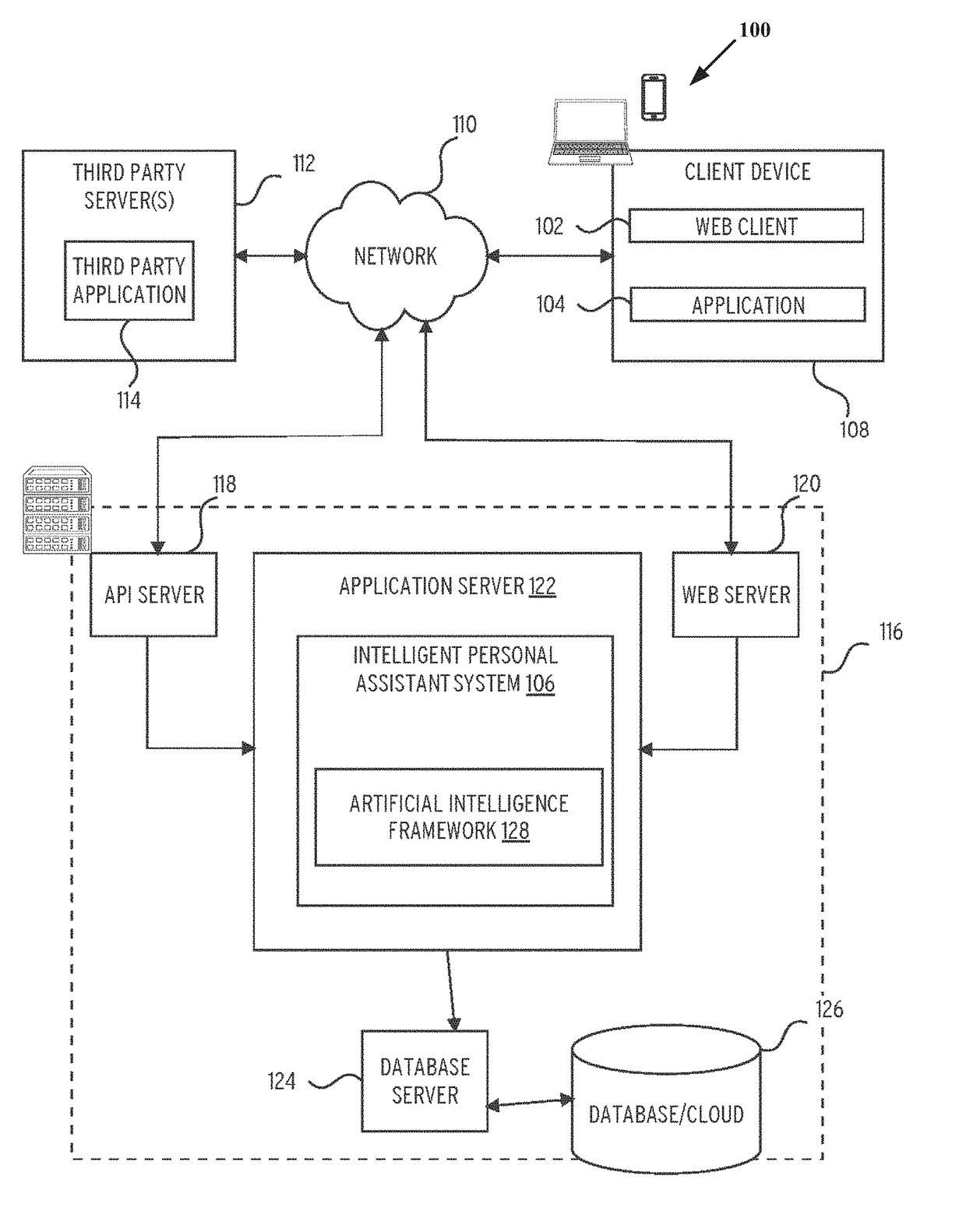
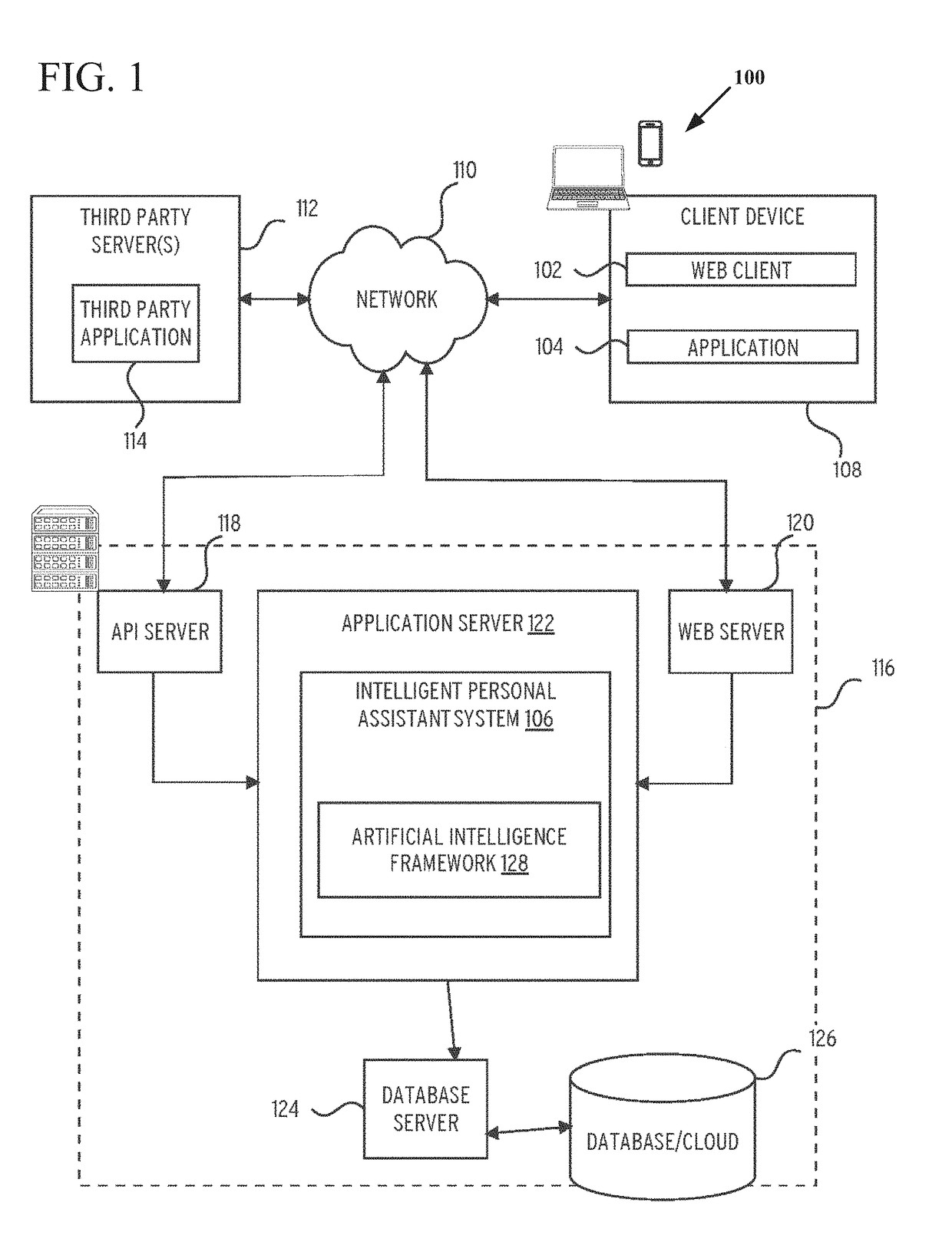
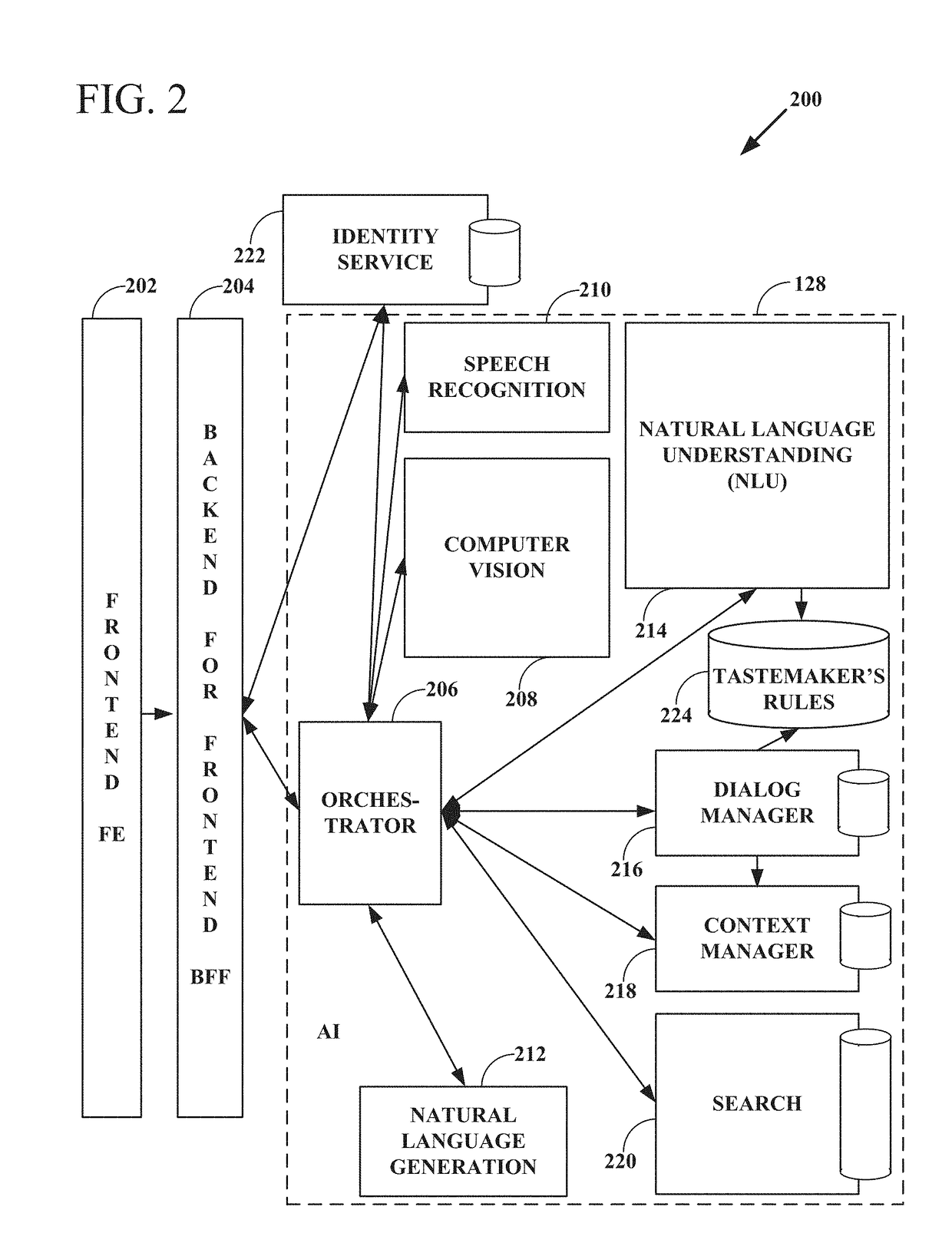
Knowledge graph construction for intelligent online personal assistant
InactiveUS20180052884A1Improve identityDigital data information retrievalNatural language analysisMarket basedMetadata
Processing natural language user inputs into a more formal, machine-readable, structured query representation used for making an item recommendation. Analyses of user inputs are coordinated via a knowledge graph constructed from categories, attributes, and attribute values describing relatively frequently occurring prior interactions of various users with an electronic marketplace. The knowledge graph has directed edges each with a score value based on: the conditional probabilities of category / attribute / attribute value interactions calculated from user behavioral patterns, associations between user queries and structured data based on historical buyer behavioral patterns in the marketplace, metadata from items made available for purchase by sellers used to better define buyers' requirements, and / or world knowledge of weather, locations / places, occasions, and item recipients that map to inventory-related data, for generating relevant prompts for further user input. The knowledge graph may be dynamically updated during a multi-turn interactive dialog.
Owner:EBAY INC
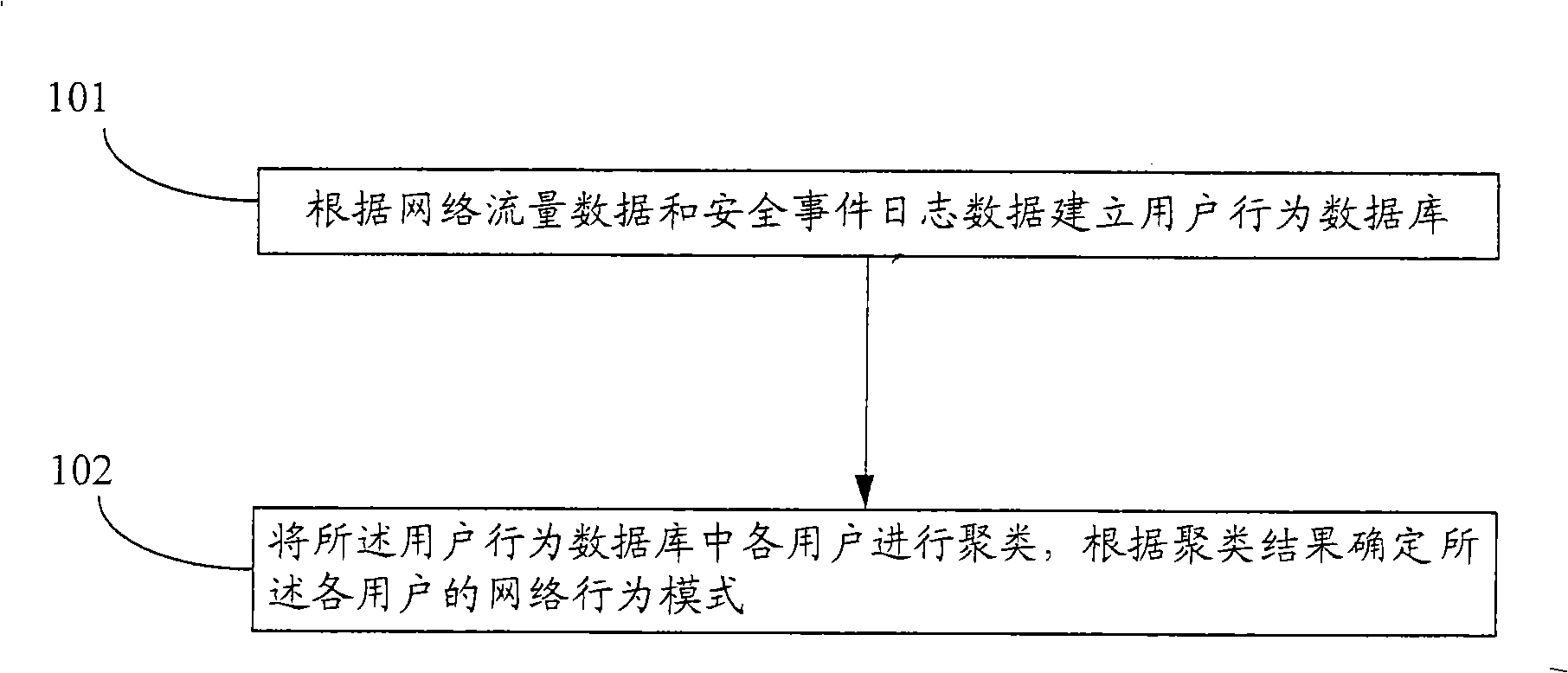
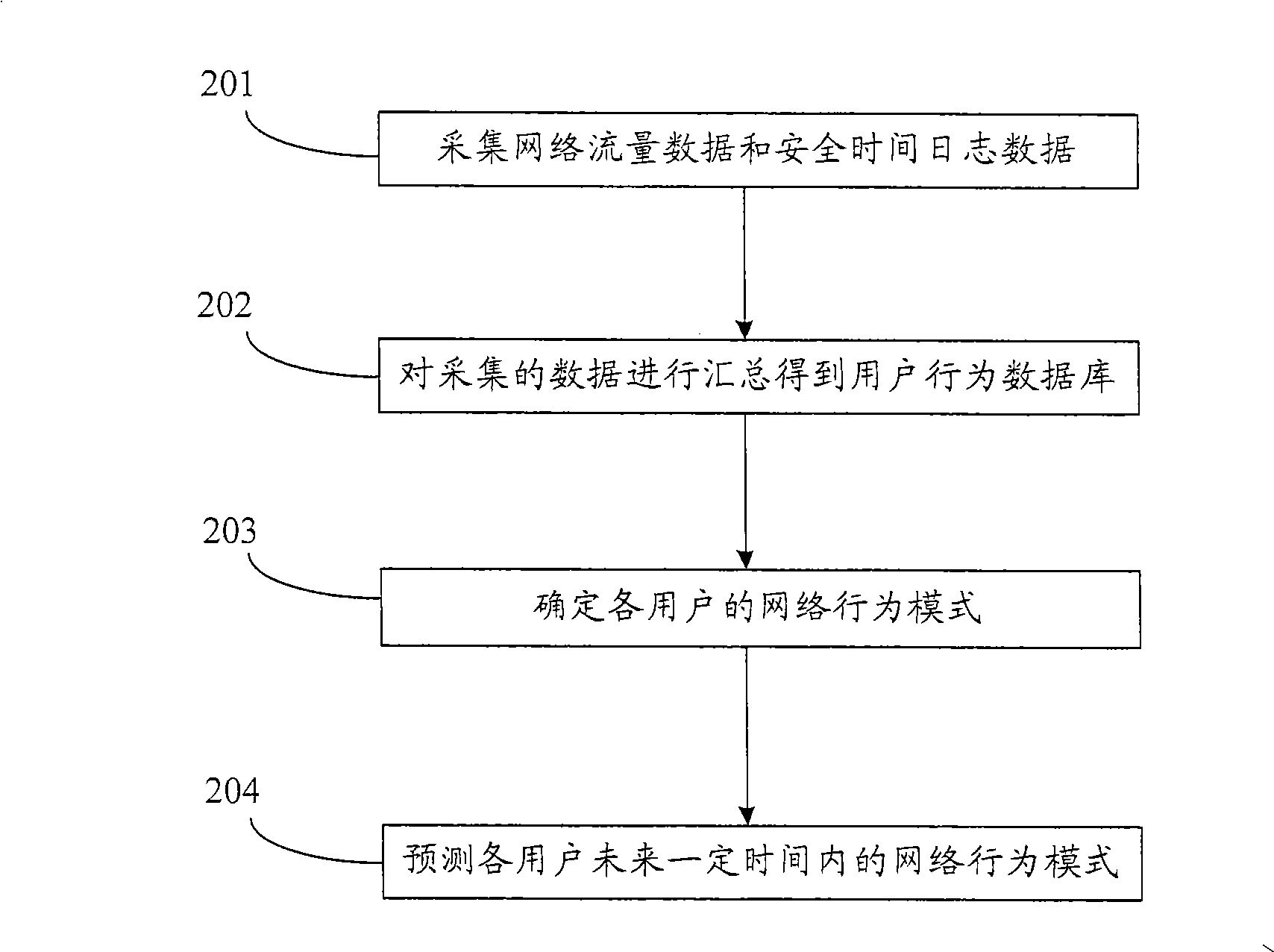
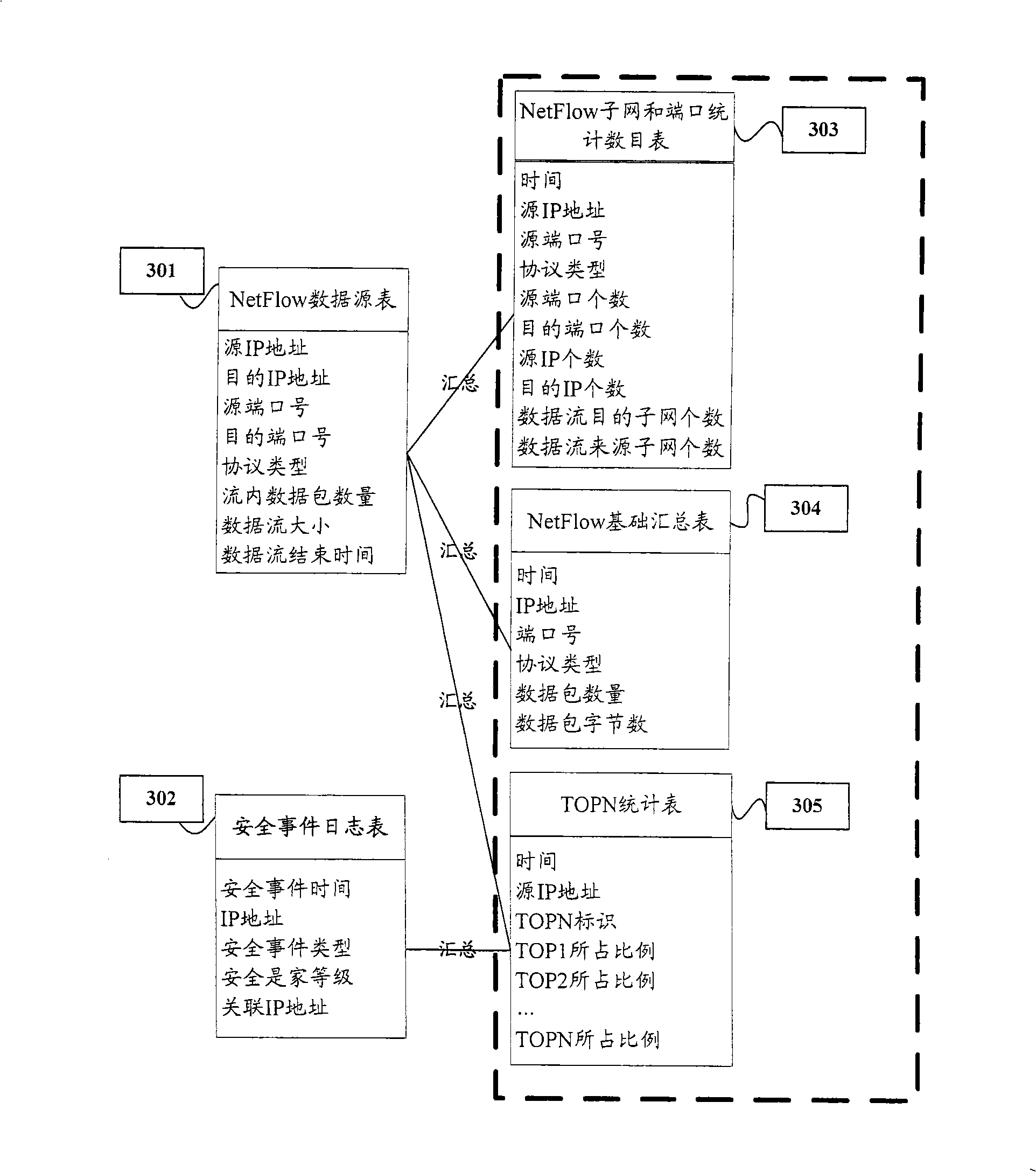
Method and apparatus for confirming user behavior
ActiveCN101355504AEffective React Network BehaviorData switching networksNetwork behaviorData mining
The embodiment of the invention discloses a method for determining user behaviors, comprising the following steps that a user behavior database is established according to the network flow data and the security event journal data; and various users in the user behavior database are clustered and the network behavioral pattern of the various users is determined according to the clustering result. In the embodiment of the invention, the various users in the user behavior database are clustered through establishment of the user behavior database; the network behavioral pattern of the various users is determined; and the network behaviors of the users are effectively reflected macroscopically.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
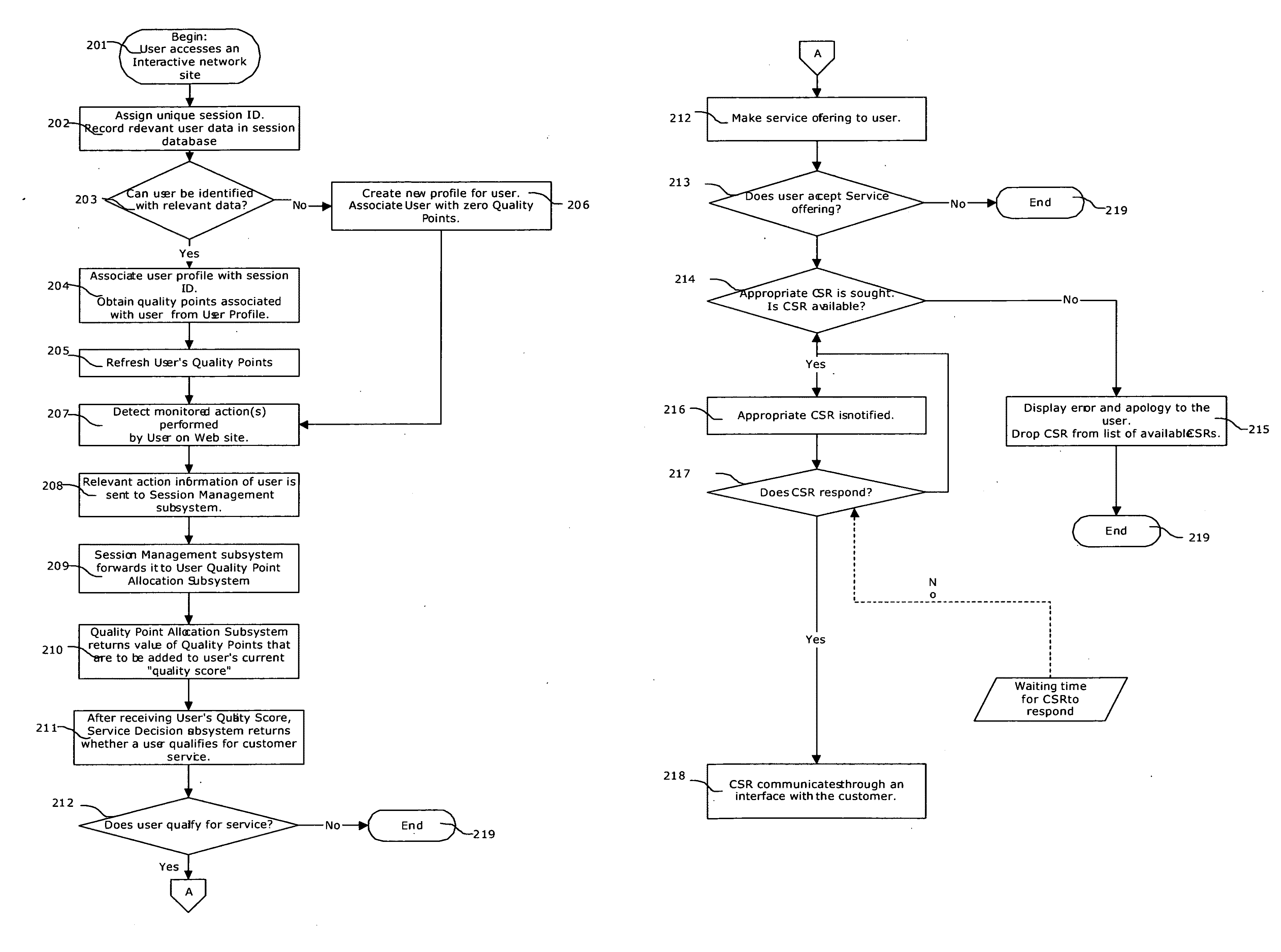
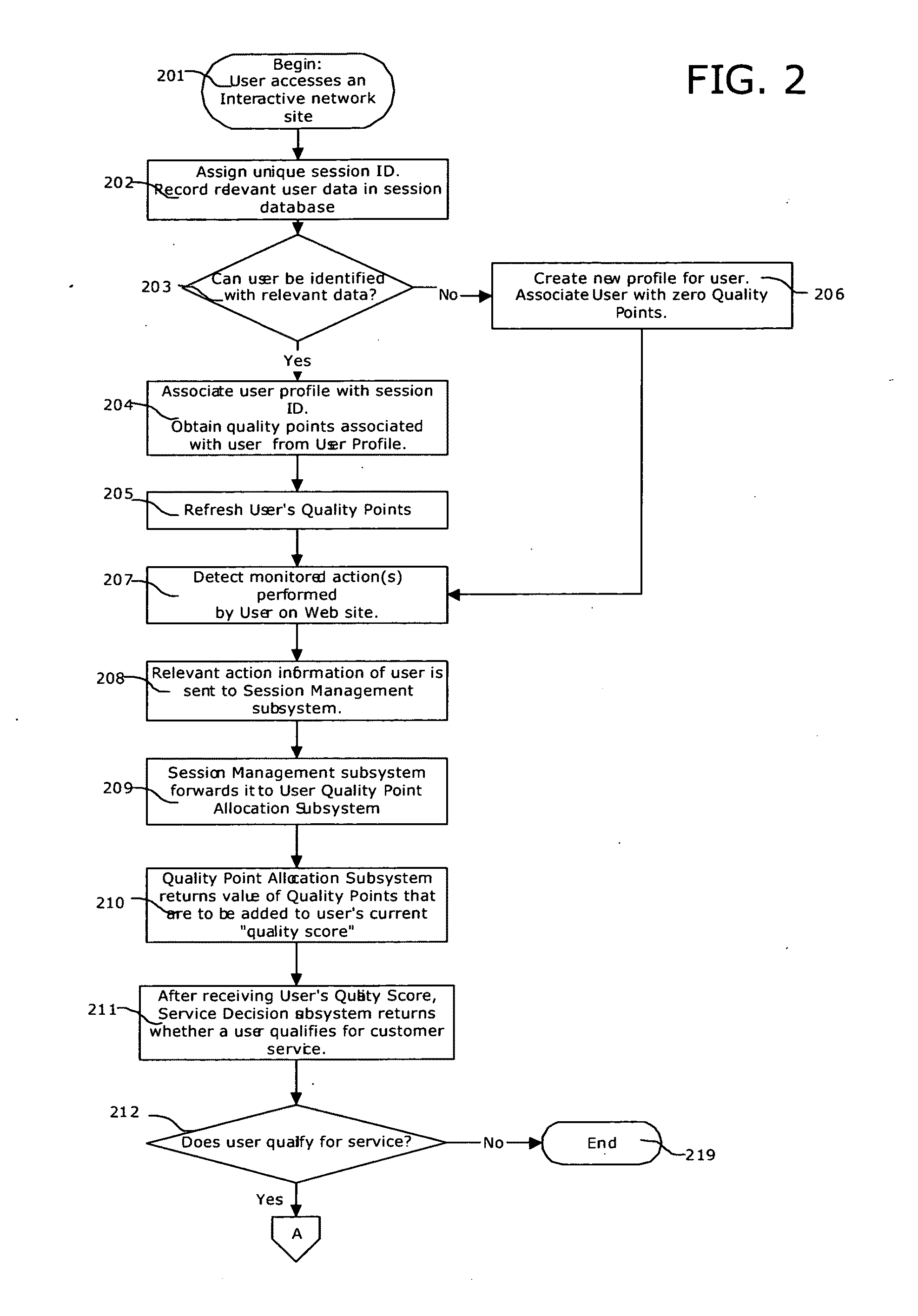
System and method for prioritization of website visitors to provide proactive and selective sales and customer service online
A system that (a) monitors and analyzes a website visitor's (or ‘user's’) behavioral patterns in real-time; (b) identifies key users by comparing the user's actions and information derived thereof to a set of pre-defined, merchant-specific business rules; (c) makes a sales and customer service offer to the user only if (1) The user satisfies the merchant's business rules and can therefore be defined as a ‘key’ customer and (2) a suitable sales assistant is online and available to deliver a sales pitch or service assistance to the customer; (d) notifies the available sales assistant only if the customer accepts of the customer service offer and (e) enables communication between the sales assistant and the user through a textual, audio or video interface, (f) improves the appropriateness of allocation of customer service representatives to users, based on user feedback, behavioral patterns and user evaluation.
Owner:FERNANDES CARLOS NICHOLAS +1
Method to perform botnet detection
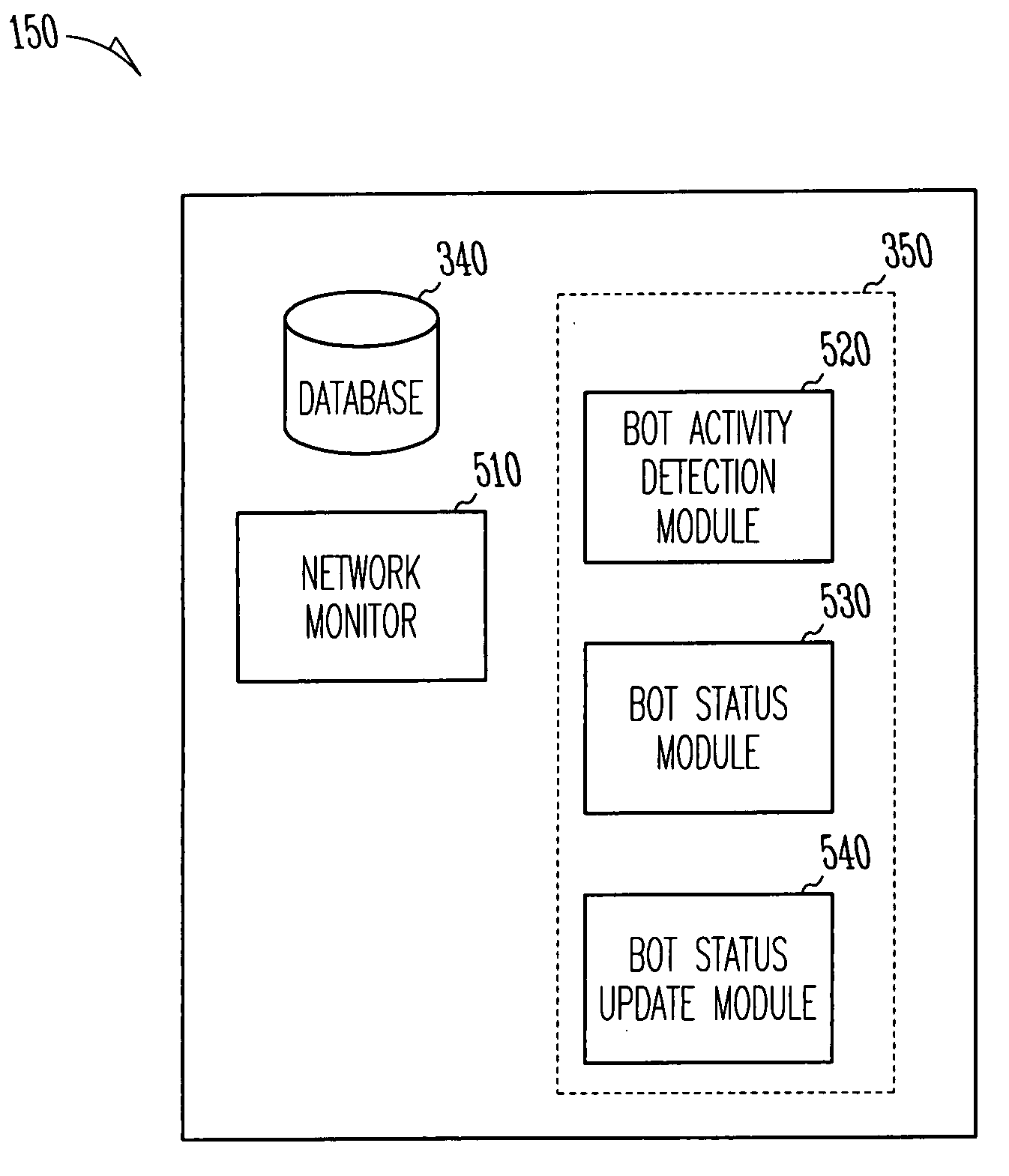
A method and a system for monitoring network activities associated with a computer connected to a network are provided. The method may include detecting a bot activity associated with the computer; attributing a bot status to the computer, based on a bot activity type associated with the bot activity, prior detections of bot activities, and considering time stamps. The method may also include updating the bot status attributed to the computer, based upon detection of subsequent bot activities associated with the computer, the bot activity types associated with the subsequent bot activities, and one or more other criteria. In one example embodiment, the network activities may include network transmissions and behavioral patterns. According to example embodiments, the system may include a network monitor, a bot activity detection module, a bot status module, and a bot status update module.
Owner:SYMANTEC CORP
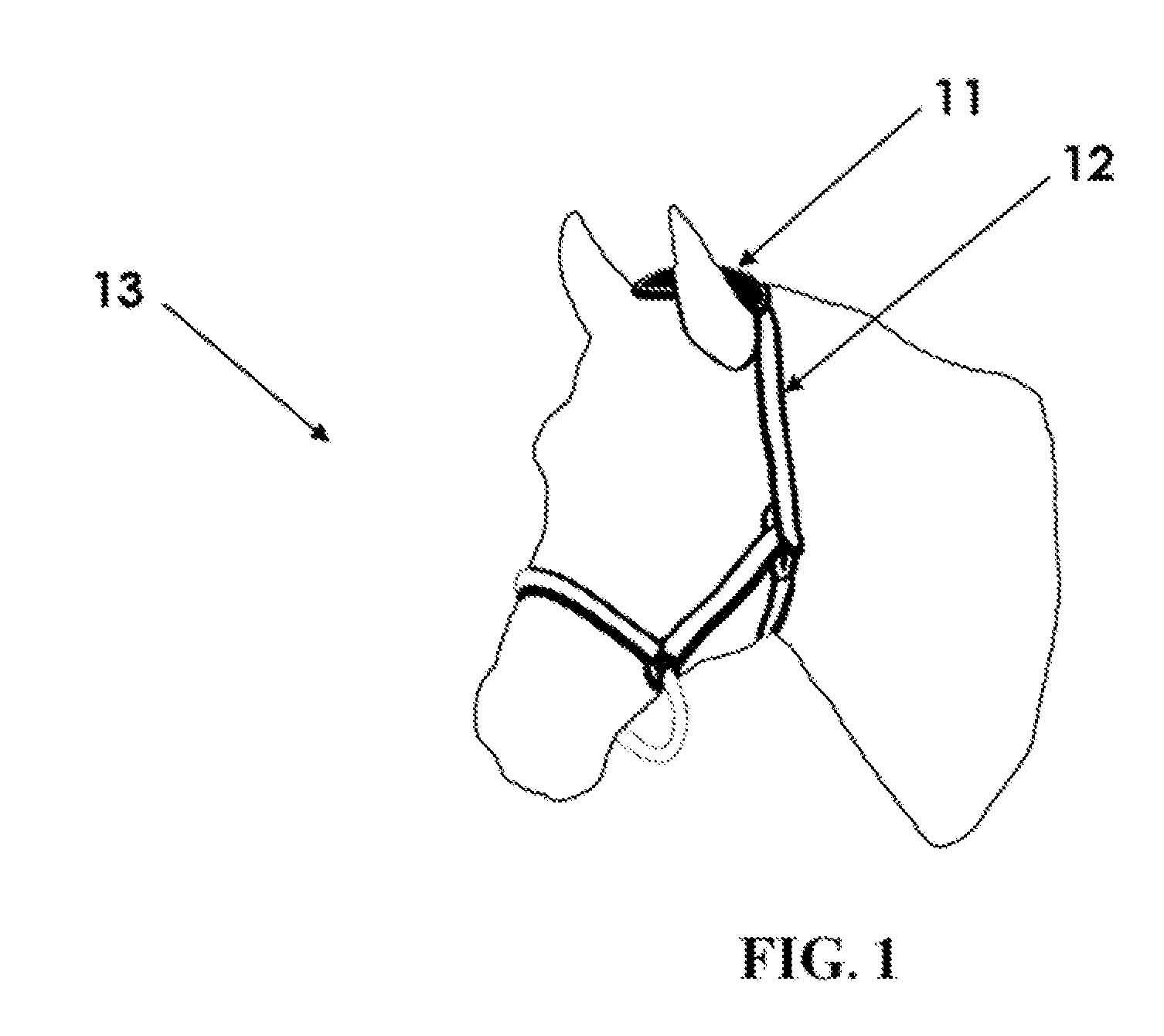
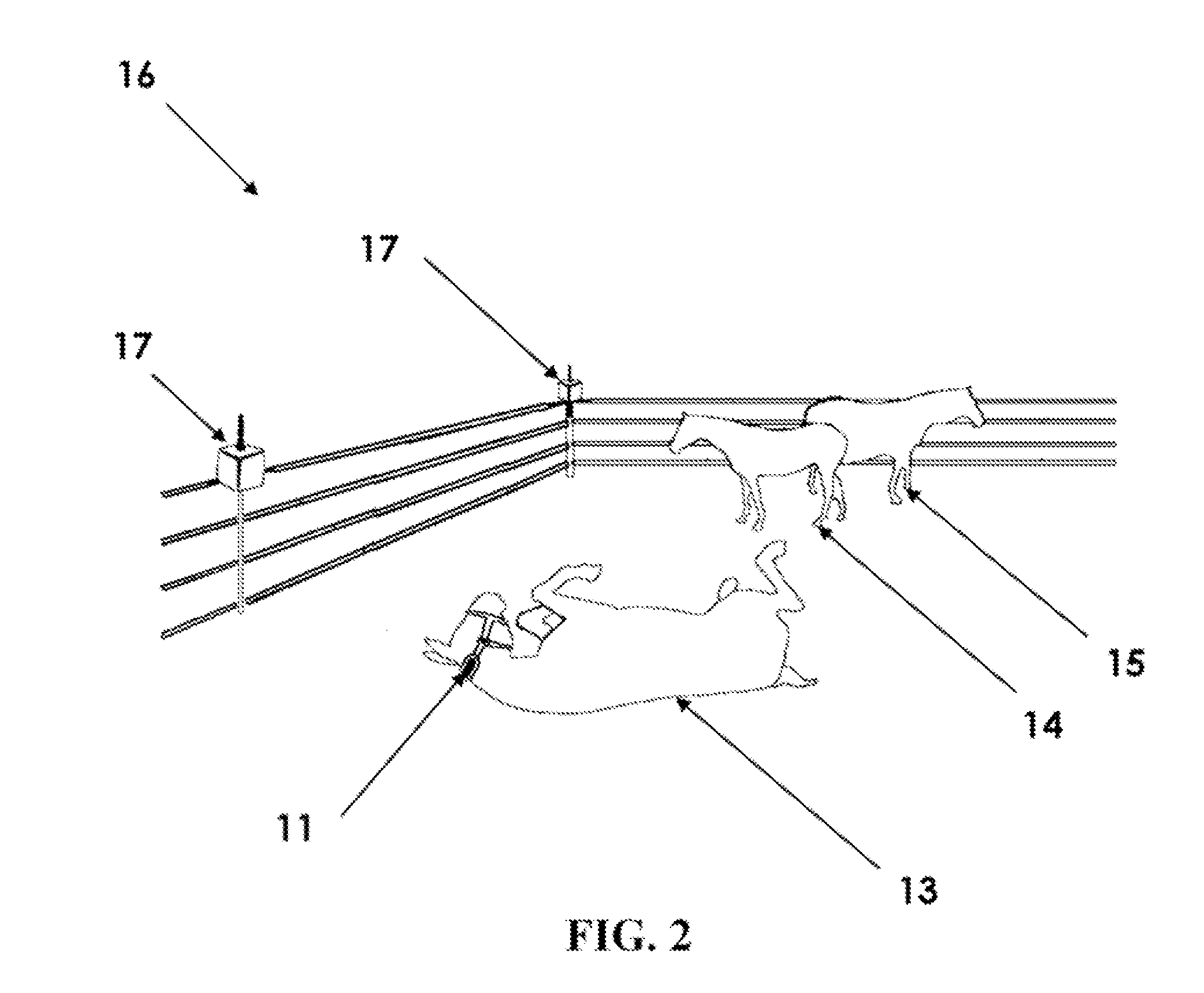
Device and Method for Remotely Monitoring Animal Behavior
InactiveUS20100302004A1Increase chances of survivalLow costSafety beltsFrequency-division multiplex detailsAnimal behaviorBehaviour pattern
The device and method for remotely monitoring animal behavior consists of a sensor unit mounted on an animal. The sensor unit utilizes motion sensors to monitor the specific behavioral patterns of the animal. Power management is controlled to turn the system on when specific types of motion are detected. Motion data is wirelessly transmitted to a base station for analysis. Data analysis functions are used to detect and identify the occurrence of characteristic motions. Network decision algorithms analyze the characteristic motions and compute weighted indicators and weighted counter-indicators which are combined into a final diagnostic score. When the final diagnostic score exceeds a threshold value, a specific behavioral pattern is confirmed which may indicate the animal is in a distress situation or experiencing another type of behavior that requires intervention. If distress is detected, the system sends a communication to notify the appropriate personnel that a distress condition exists.
Owner:UTAH STATE UNIVERSITY
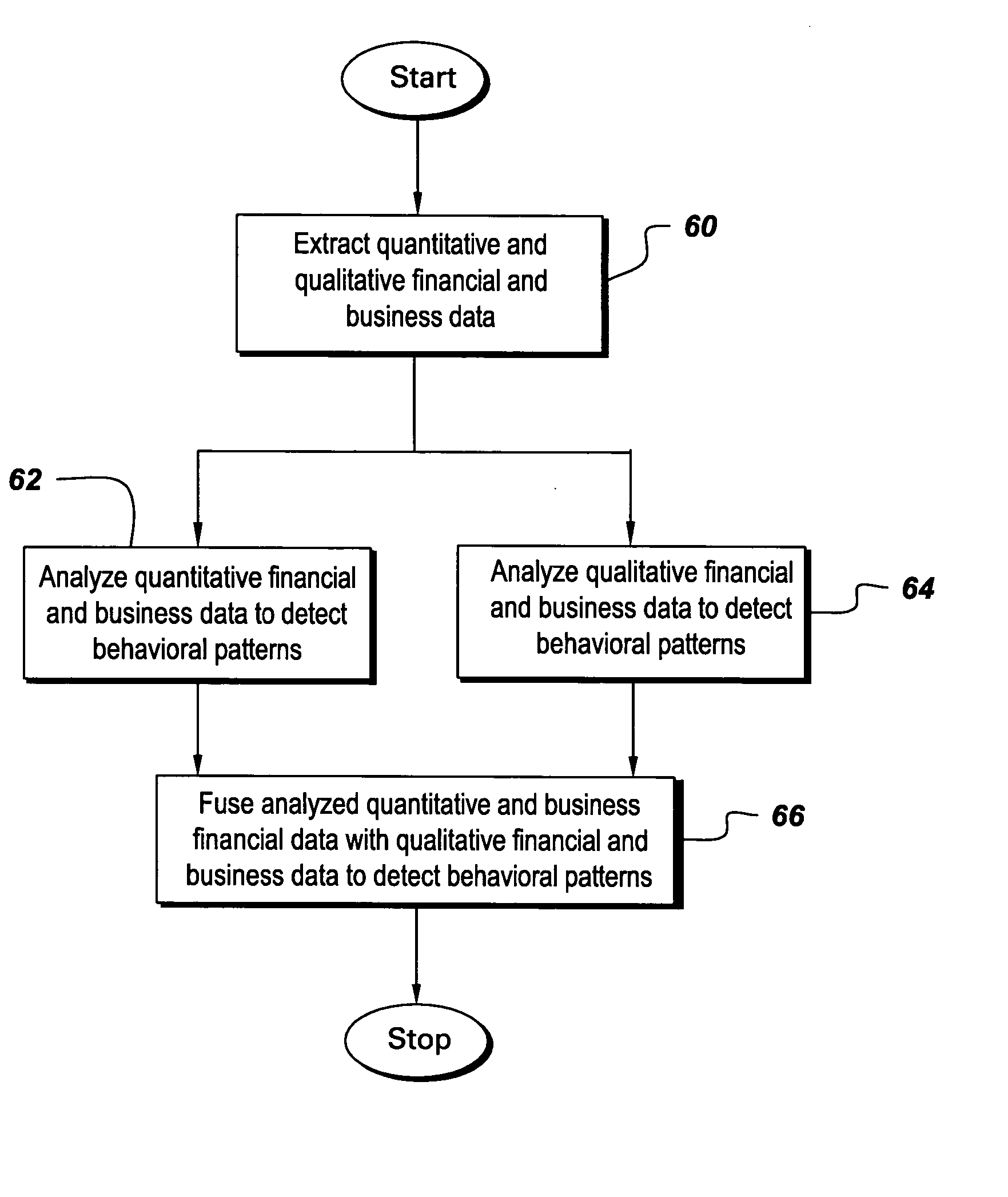
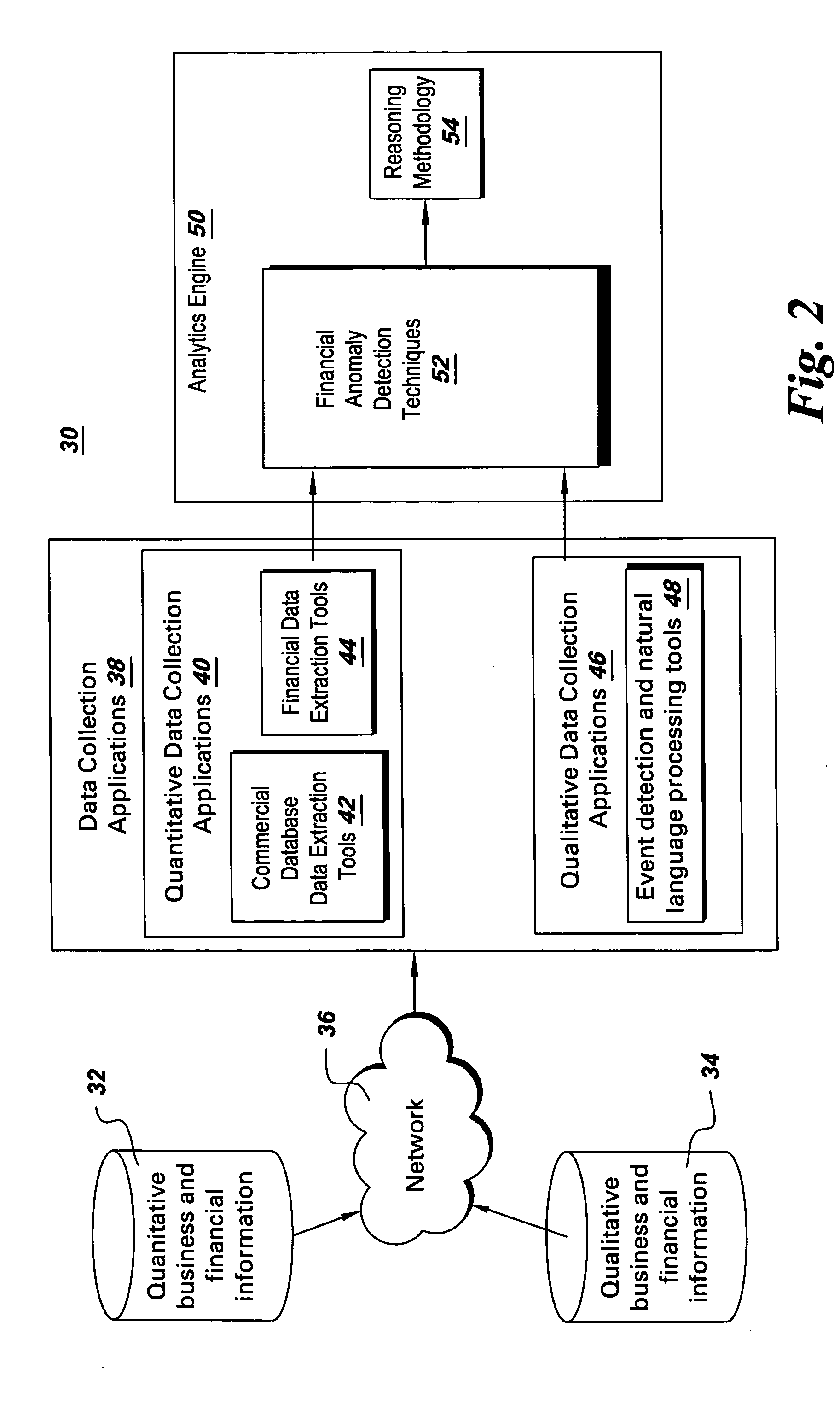
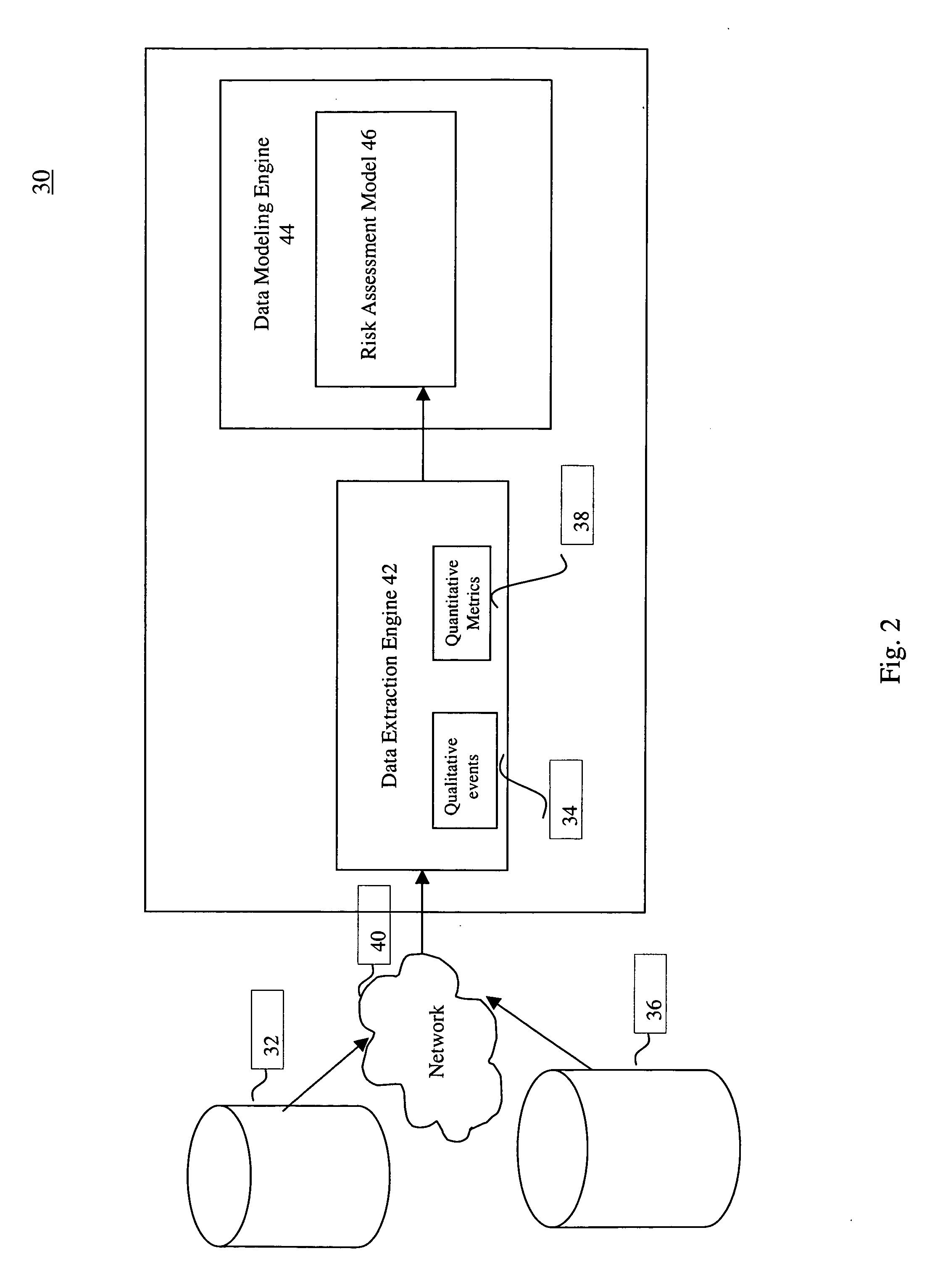
System, method and computer product to detect behavioral patterns related to the financial health of a business entity
System, method and computer product to detect behavioral patterns related to the financial health of a business entity. In this invention, financial data and business data that relate to the business entity is extracted from various data sources. The financial data comprises quantitative financial data and / or qualitative financial data. The business data comprises quantitative business data and / or qualitative business data. The quantitative financial and business data is analyzed using a financial anomaly detection technique to detect the behavioral patterns associated with the business entity.
Owner:GENERAL ELECTRIC CO
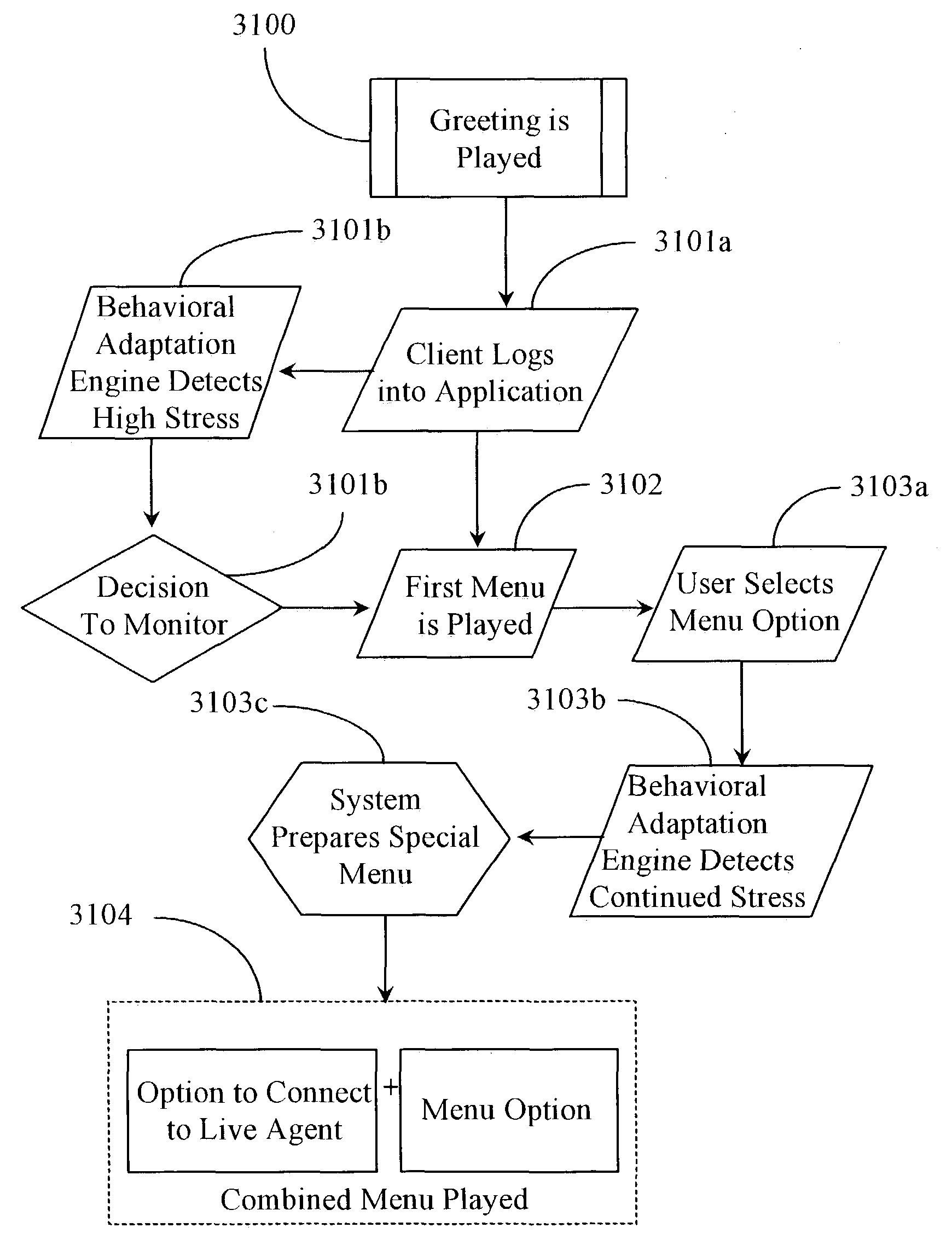
Behavioral adaptation engine for discerning behavioral characteristics of callers interacting with an VXML-compliant voice application
ActiveUS7242752B2Narrow selectionAutomatic call-answering/message-recording/conversation-recordingAutomatic exchangesClient dataData system
A behavioral adaptation engine integrated with a voice application creation and deployment system has at least one data input port for receiving XML-based client interaction data including audio files attached to the data; at least one data port for sending data to and receiving data from external data systems and modules; a logic processing component including an XML reader, voice player, and analyzer for processing received data; and a decision logic component for processing result data against one or more constraints. The engine intercepts client data including dialog from client interaction with a served voice application in real time and processes the received data for behavioral patterns and if attached, voice characteristics of the audio files whereupon the engine according to the results and one or more valid constraints identifies one or a set of possible enterprise responses for return to the client during interaction.
Owner:HTC CORP
Method and apparatus for implementing digital video modeling to generate an expected behavior model
A computer implemented method, apparatus, and computer usable program product for generating an expected behavior model. The process parses event data derived from video data to identify behavioral patterns, wherein the event data comprises metadata describing events occurring in a selected environment. The process analyzes the behavioral patterns to identify a set of expected behavioral patterns occurring in the environment, and generates the expected behavioral model using the expected behavioral patterns.
Owner:INT BUSINESS MASCH CORP
Adaptive behavioral intrusion detection systems and methods
ActiveUS8205259B2Increase opportunitiesMemory loss protectionMicrobiological testing/measurementApplication serverInternet traffic
Systems and methods for analyzing historical network traffic and determining which traffic does not belong in a network are disclosed. Intrusion detection is performed over a period of time, looking for behavioral patterns within networks or information systems and generating alerts when these patterns change. The intrusion detection system intelligently forms correlations between disparate sources to find traffic anomalies. Over time, behaviors are predictive, and the intrusion detection system attempts to predict outcomes, becoming proactive instead of just reactive. Intrusions occur throughout whole information systems, including both network infrastructure and application servers. By treating the information system as a whole and performing intrusion detection across it, the chances of detection are increased significantly.
Owner:MASERGY COMMUNICATIONS INC
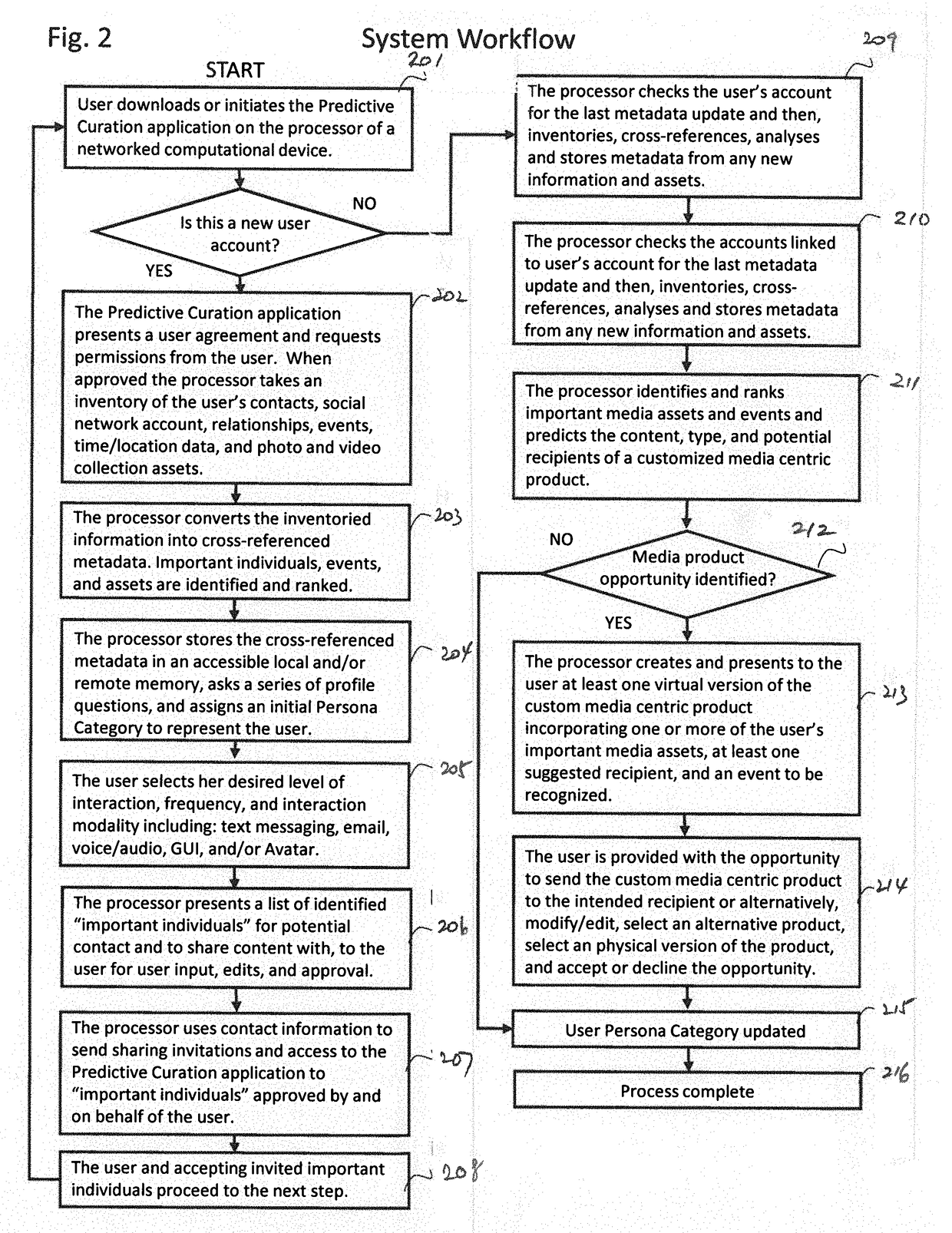
System and method for predictive curation, production infrastructure, and personal content assistant
Owner:KODAK ALARIS INC
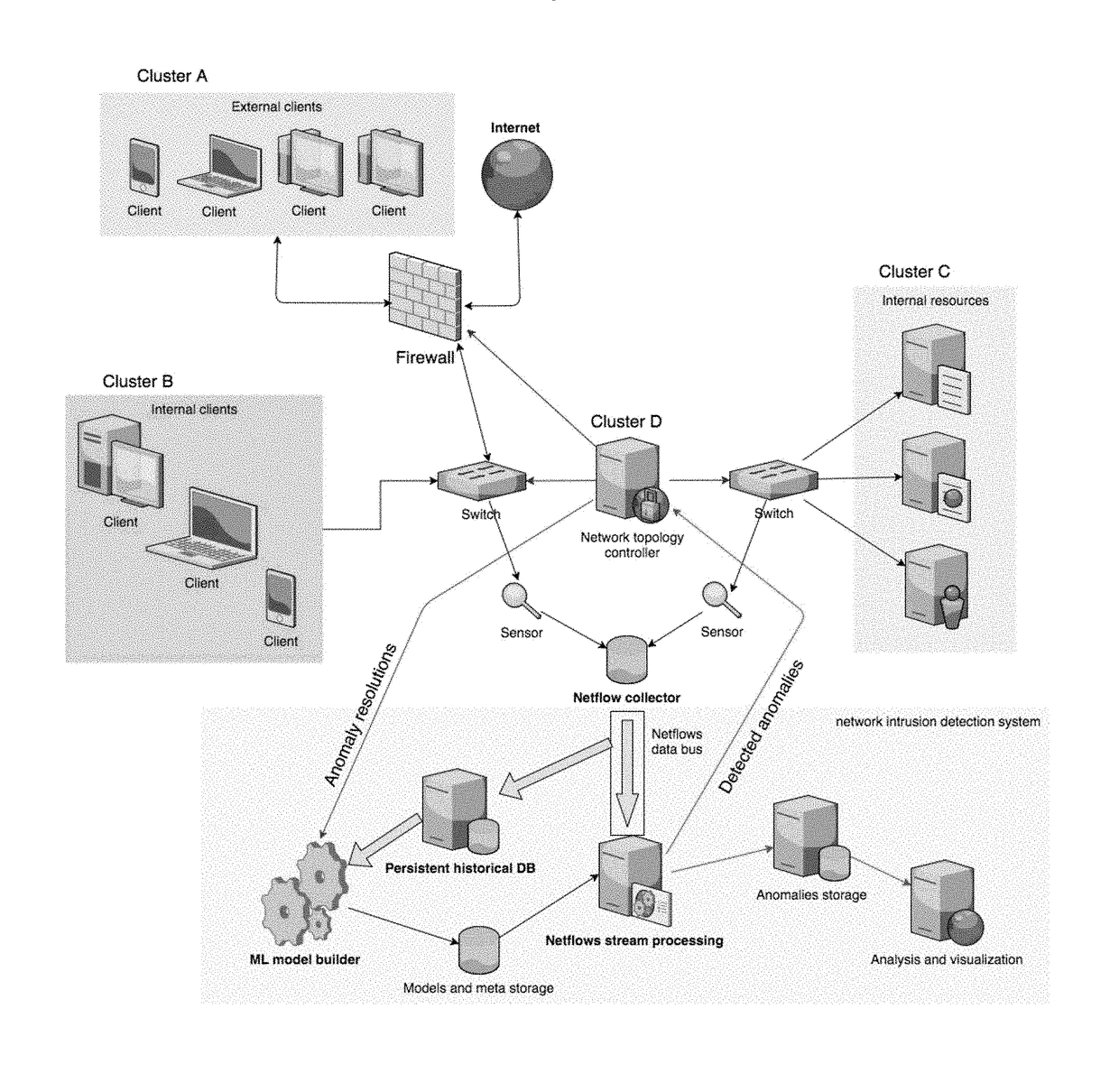
System and method for automated network monitoring and detection of network anomalies
ActiveUS20180020015A1Platform integrity maintainanceMachine learningBehavioral patternNetwork element
A system and method for unsupervised detection of system anomalies in a network, including one or more network elements, a flow collector configured to collect instances of network data from the one or more network elements, a historical dataset database configured to store the instances of network data, a historical dataset pattern extractor configured to analyze the instances of network data and produce a historical behavioral pattern for each of the instances of network data, and a flow stream processor configured to analyze instances of network data in real time, produce a current behavioral pattern for each of the instances of network data, compare the current behavioral pattern to a corresponding historical behavioral pattern, and detect an anomaly based on the comparison between the current behavioral pattern and the corresponding historical behavioral pattern.
Owner:SDN SYST LLC
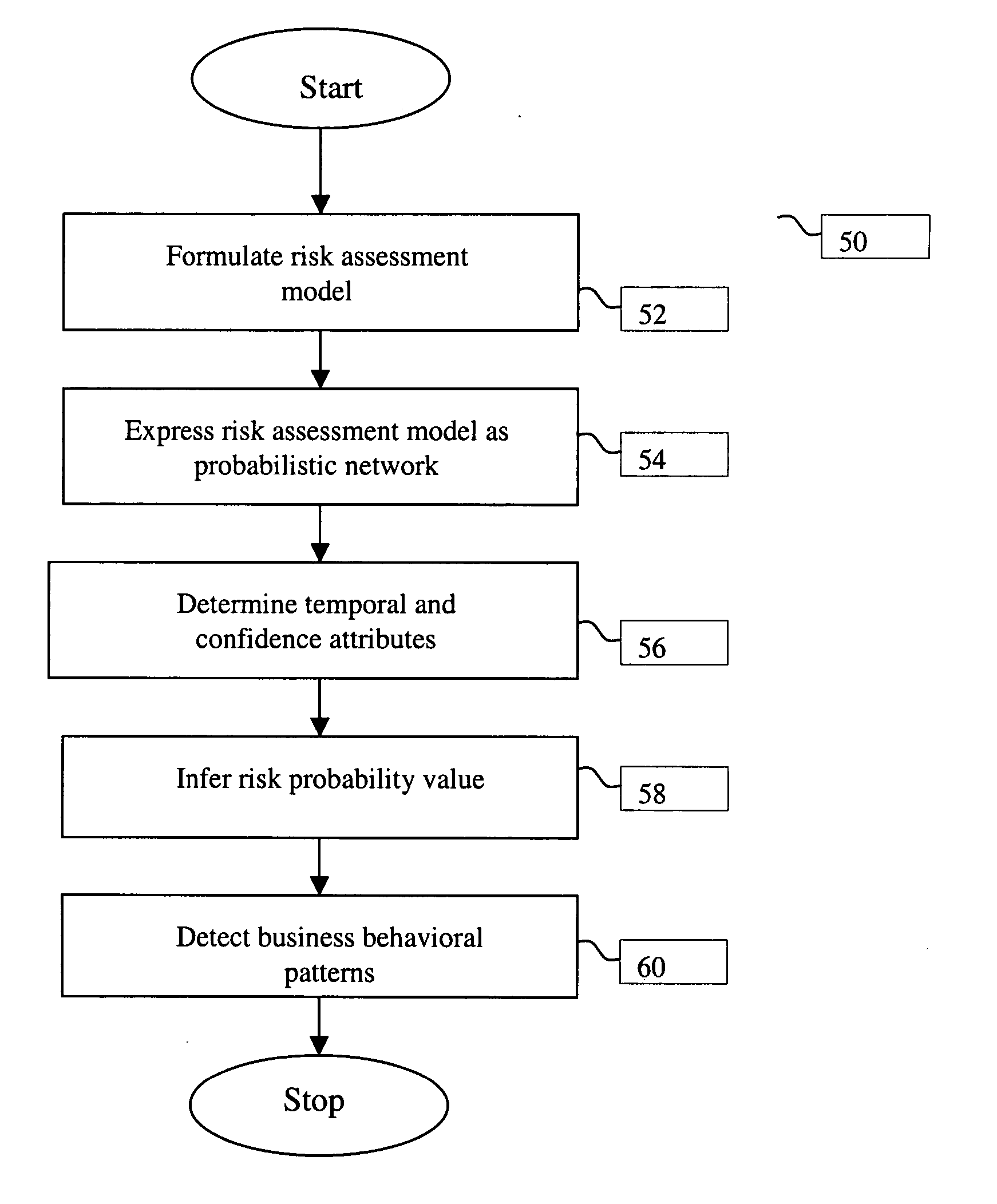
Method and system for detecting business behavioral patterns related to a business entity
A method and system for detecting business behavioral patterns related to a business entity is provided. The method comprises determining a model for business behavioral patterns in which the likelihood of a particular business behavioral pattern is associated with the occurrence of a qualitative event and a quantitative metric. The method further comprises extracting a first data set from a first data source and a second data set from a second data source. The first data set represents the occurrence of the qualitative event associated with the business entity. The second data set represents the quantitative metric associated with the business entity. Then a first confidence attribute and a first temporal attribute associated with the qualitative event is determined. Similarly, a second confidence attribute and a second temporal attribute associated with the quantitative metric are determined. Finally, the likelihood of the particular business behavior pattern is evaluated by running the model based on the first data set, the second data set, the first confidence attribute, the first temporal attribute, the second confidence attribute and the second temporal attribute.
Owner:GENERAL ELECTRIC CO
System and method for customer authentication execution based on customer behavior mode
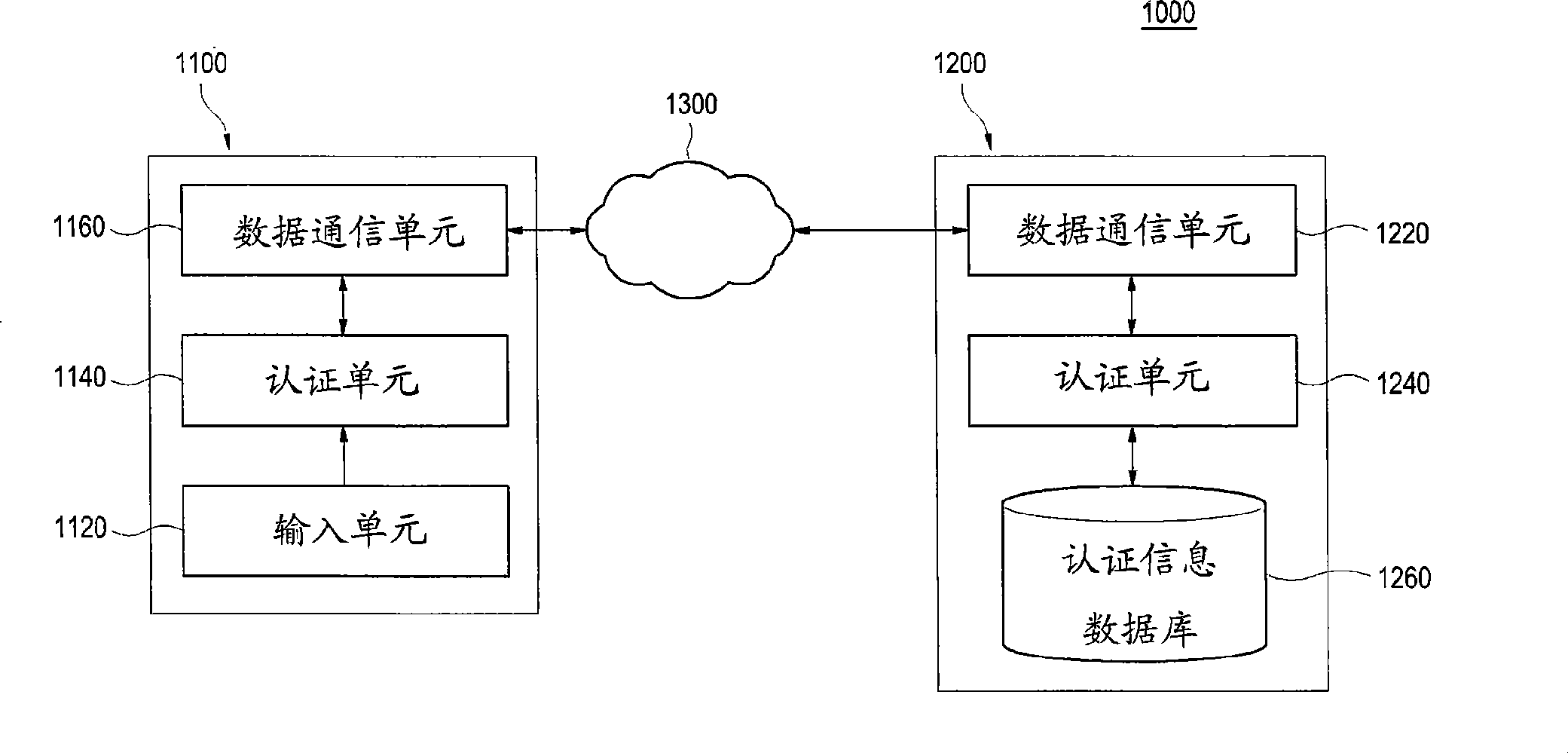
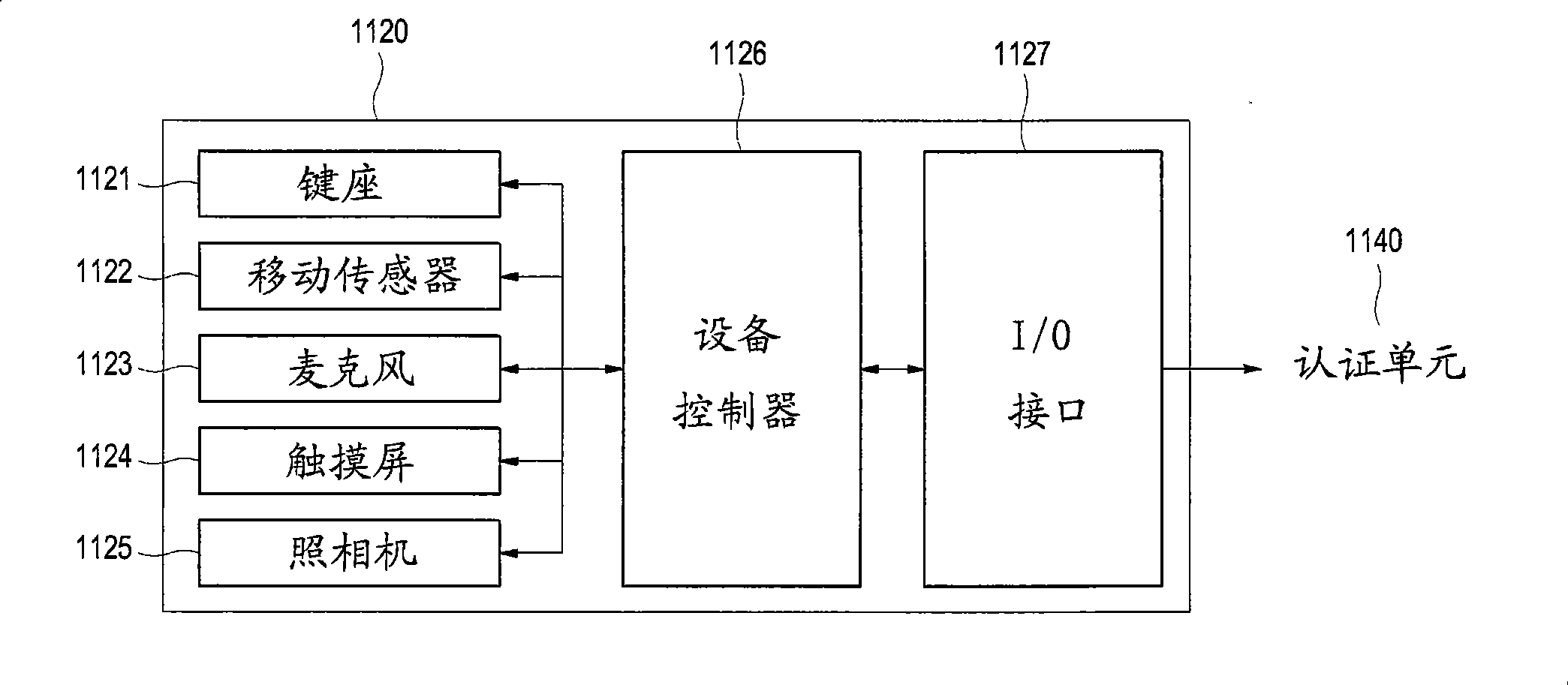
InactiveCN101365193AUser identity/authority verificationRadio/inductive link selection arrangementsCommunication unitTyping
The invention discloses a system and a method for executing the user authentication based on the behavioral pattern of a mobile terminal user. The system comprises a mobile terminal; the mobile terminal is provided with an input unit used for receiving the authentication information from the users; an authentication unit for extracting the users' behavioral pattern based on the authentication information; and a data communication unit for sending the authentication information and the behavioral pattern to an authentication server. The behavioral pattern based on the extracted authentication information includes the user characteristic behavioral patterns, such as a typing pattern, a mobile pattern, a sound pattern and a writing pattern. The system and the method for executing the user authentication based on the behavioral pattern of the mobile terminal user can improve the security and the flexibility of the user authentication system.
Owner:财团法人SEOUL大学校产学协力财团
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com