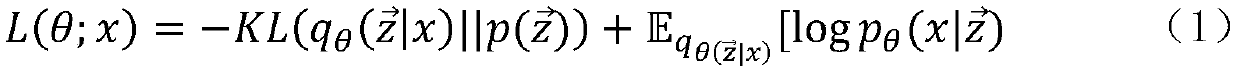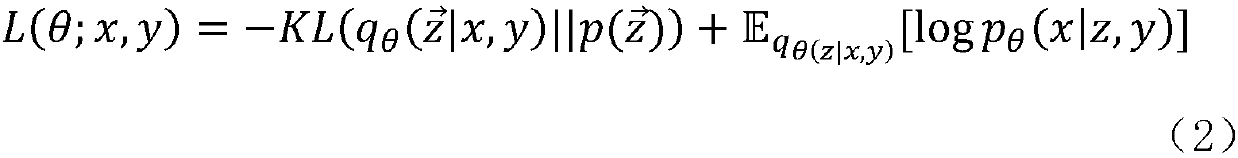A password attack evaluation method based on conditional variational self-coding
A conditional encoding and self-encoding technology is applied in the field of password attack assessment based on conditional variational self-encoding, which can solve the problems of attack, consume large computing resources and time cost, and is not suitable for real-time password strength assessment, so as to improve the strength and security. security, improve password strength and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In order to deepen the understanding of the present invention, the present invention will be further described below in conjunction with the examples, which are only used to explain the present invention, and do not constitute a limitation to the protection scope of the present invention.
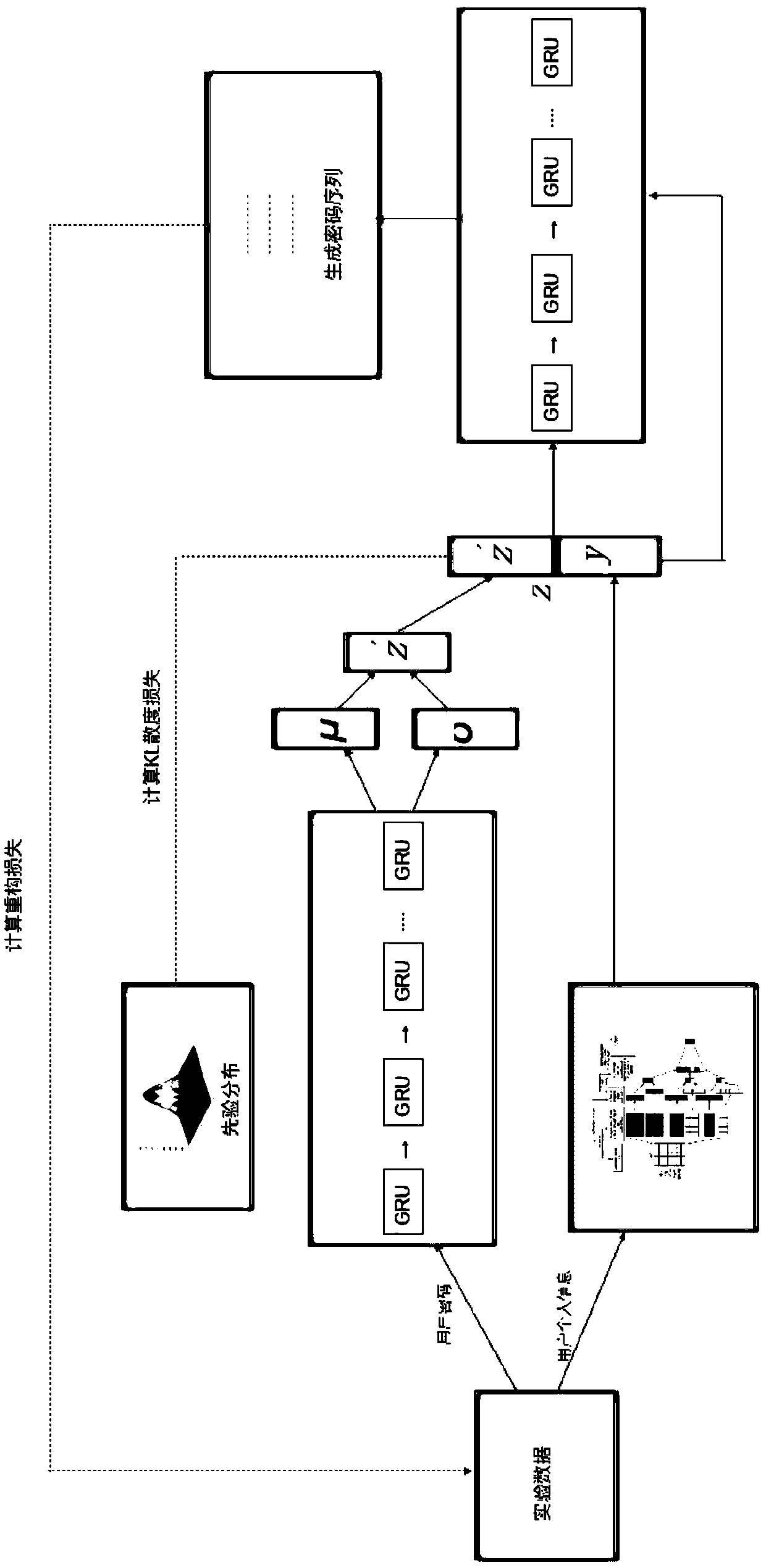
[0037] according to figure 1 As shown, this embodiment proposes a cryptographic attack evaluation method based on conditional variational self-encoding, including the following steps:
[0038] Step 1: Build a Variational Autoencoder Model
[0039] Firstly, a variational autoencoder model is generated after regularization based on the standard autoencoder model, and a prior distribution is imposed on the hidden variable by using the variational autoencoder model On the above, the encoder in the standard autoencoder is replaced by the learned posterior recognition model through the variational autoencoder model, and the neural network is used as the encoder function to parameterize t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com