Password strength evaluation method based on personal information
An evaluation method and password technology, applied in the field of information security, can solve the problems of increasing user information, leaking personal assets loss, inability to evaluate the results of weak passwords, etc., to achieve the effect of improving security and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
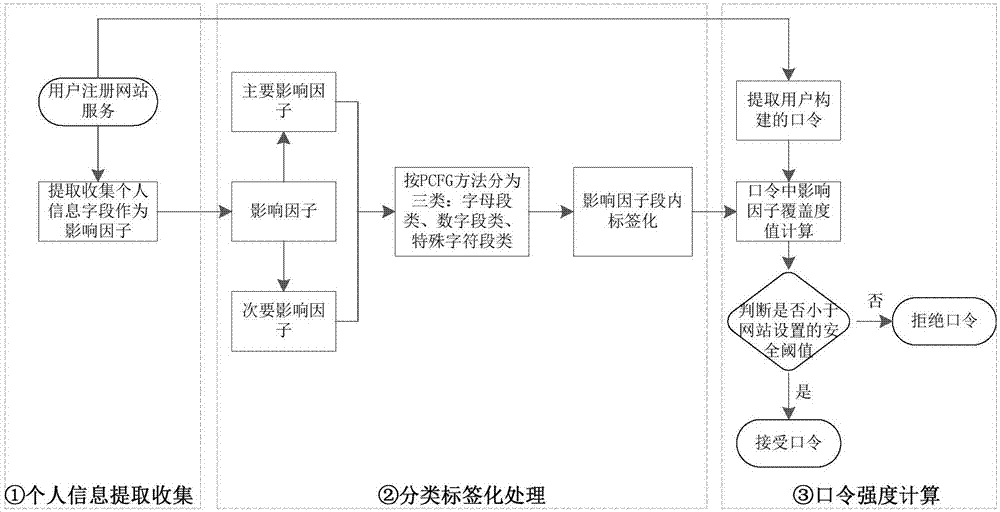
[0030] Such as figure 1 As shown, the password strength evaluation method based on personal information is divided into three stages: specifically:
[0031] Personal information collection stage: When the user registers for the website service, extract the personal information impact factor field that may be used to construct the user password.
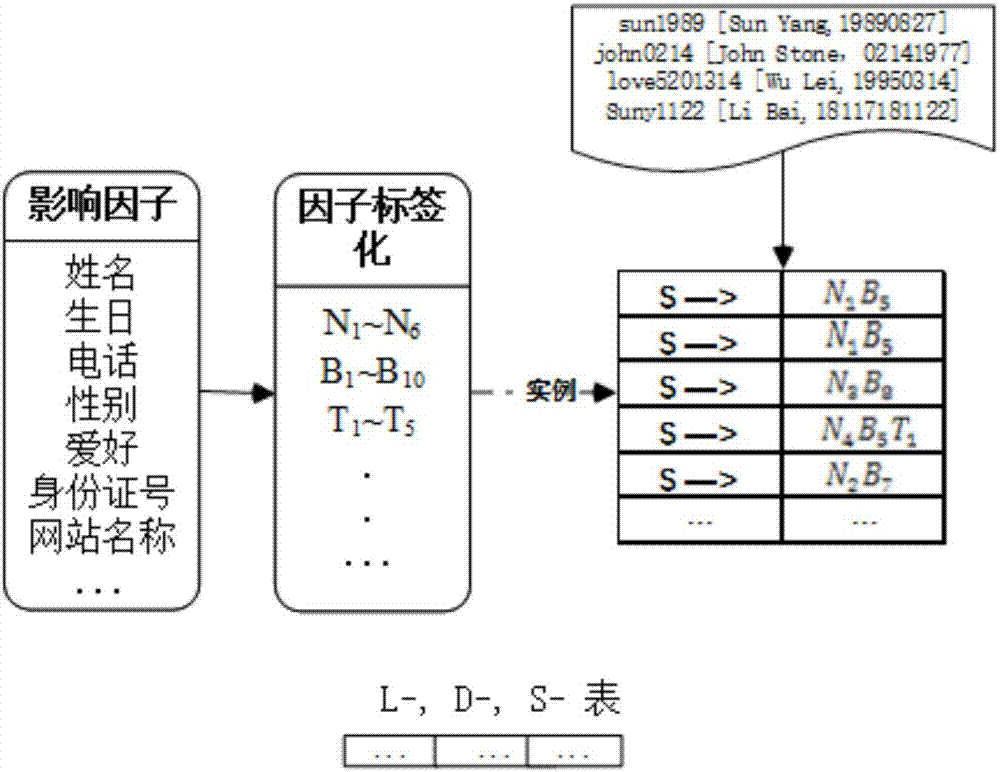
[0032] Classification and labeling processing stage: respectively classify the extracted password construction influence factor fields and label the influence factor fields according to the actual transformation form;
[0033] Password strength value calculation stage: when the user enters the password, calculate the coverage value of the influence factor in the user's constructed password according to the extracted and collected user information influence factor, and combine the coverage value with the heuristic detection method or pattern detection method to calculate Export order strength value. The target site chooses itself to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com