Real-time malicious behavior detection method and device
A real-time detection and behavior technology, applied in the field of cloud computing, can solve problems such as network traffic growth, difficult protection, inflexible network rule configuration, etc., and achieve the effect of improving the processing bottleneck
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
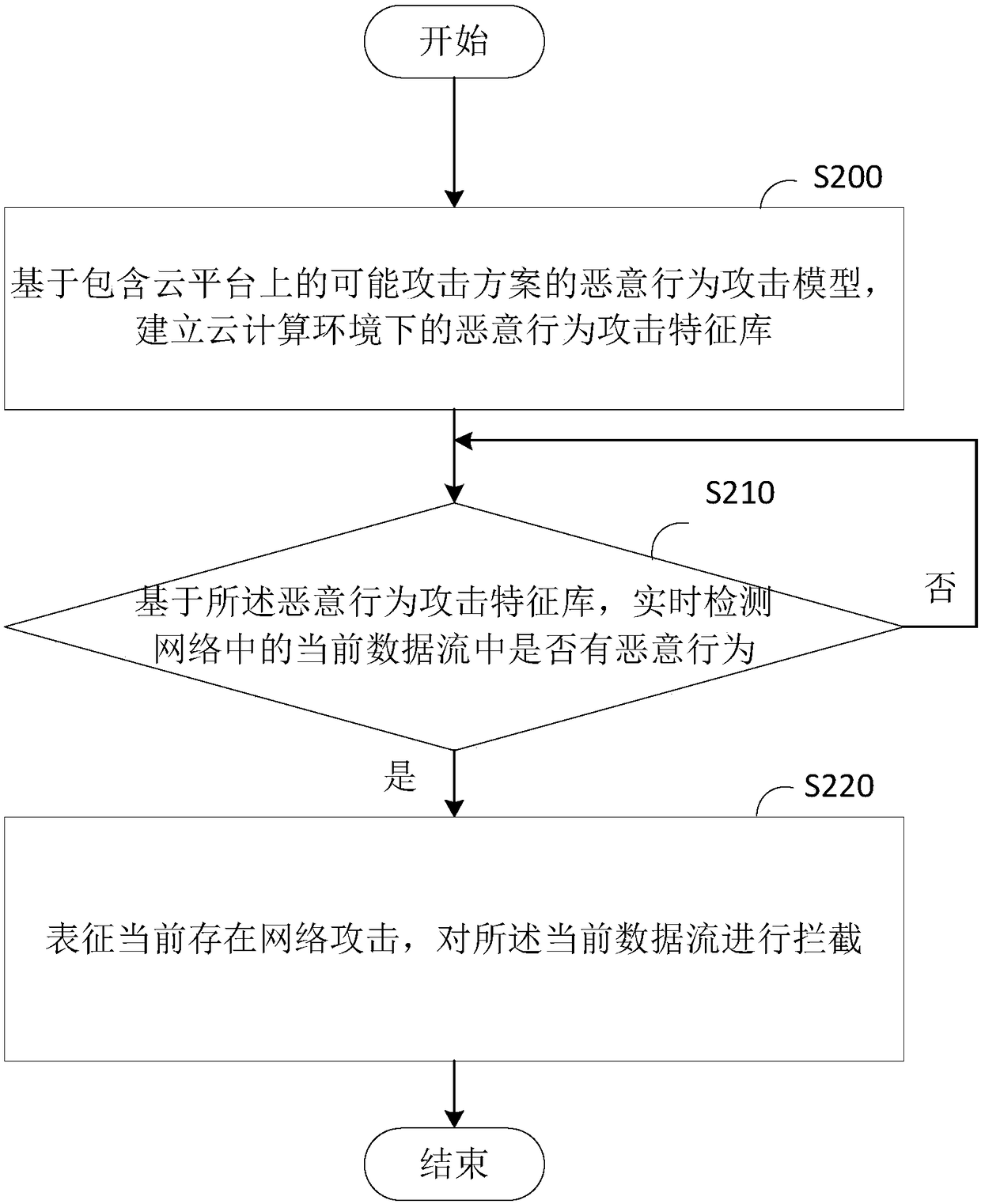
[0032] Please refer to figure 2 , this embodiment provides a method for real-time detection of malicious behavior, which is applied in an SDN network system, and the method includes:
[0033] Step S200: Based on the malicious behavior attack model including possible attack schemes on the cloud platform, establish a malicious behavior attack signature database under the cloud computing environment;
[0034] In this embodiment, by analyzing the malicious behavior supply model including possible attack schemes on the cloud platform and the remaining problems of the current attack detection model, an SDN-based malicious behavior implementation detection model, that is, the malicious behavior attack feature library, can be established. It can be understood that the content in the malicious behavior attack model may not only be limited to possible attack schemes on the cloud platform, but may also be possible attack schemes in the local system or other environments.
[0035] After...
no. 2 example
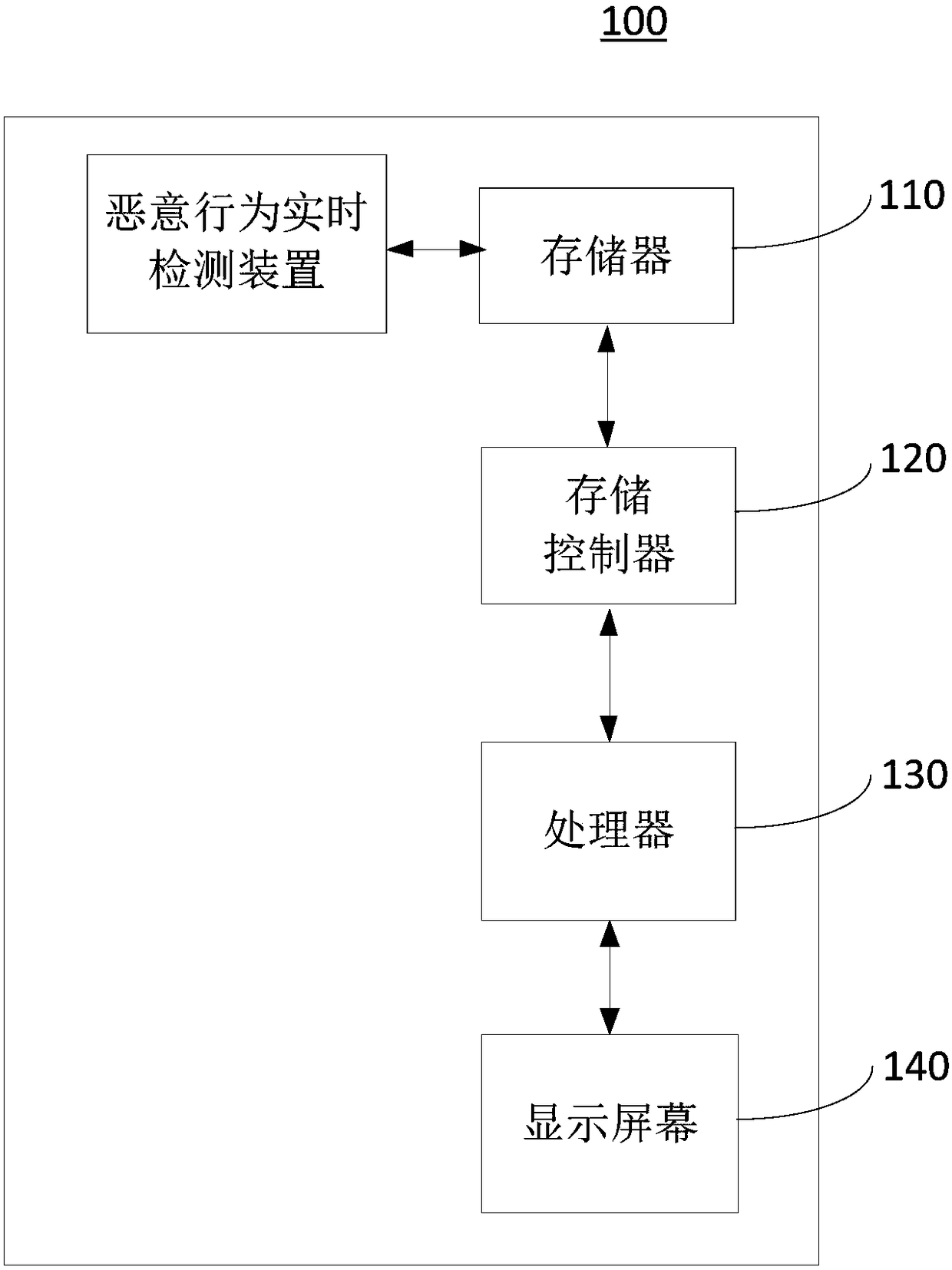
[0080] Please refer to Figure 9 , this embodiment provides a malicious behavior real-time detection device 900, which is applied to an SDN network system, and includes:
[0081] The signature database module 910 is used to establish a malicious behavior attack signature database under the cloud computing environment based on a malicious behavior attack model including possible attack schemes on the cloud platform;
[0082] A detection module 920, configured to detect in real time whether there is any malicious behavior in the current data flow in the network based on the malicious behavior attack feature library;
[0083] The interception module 930 is configured to indicate that there is a current network attack when there is malicious behavior in the current data flow, and intercept the current data flow.
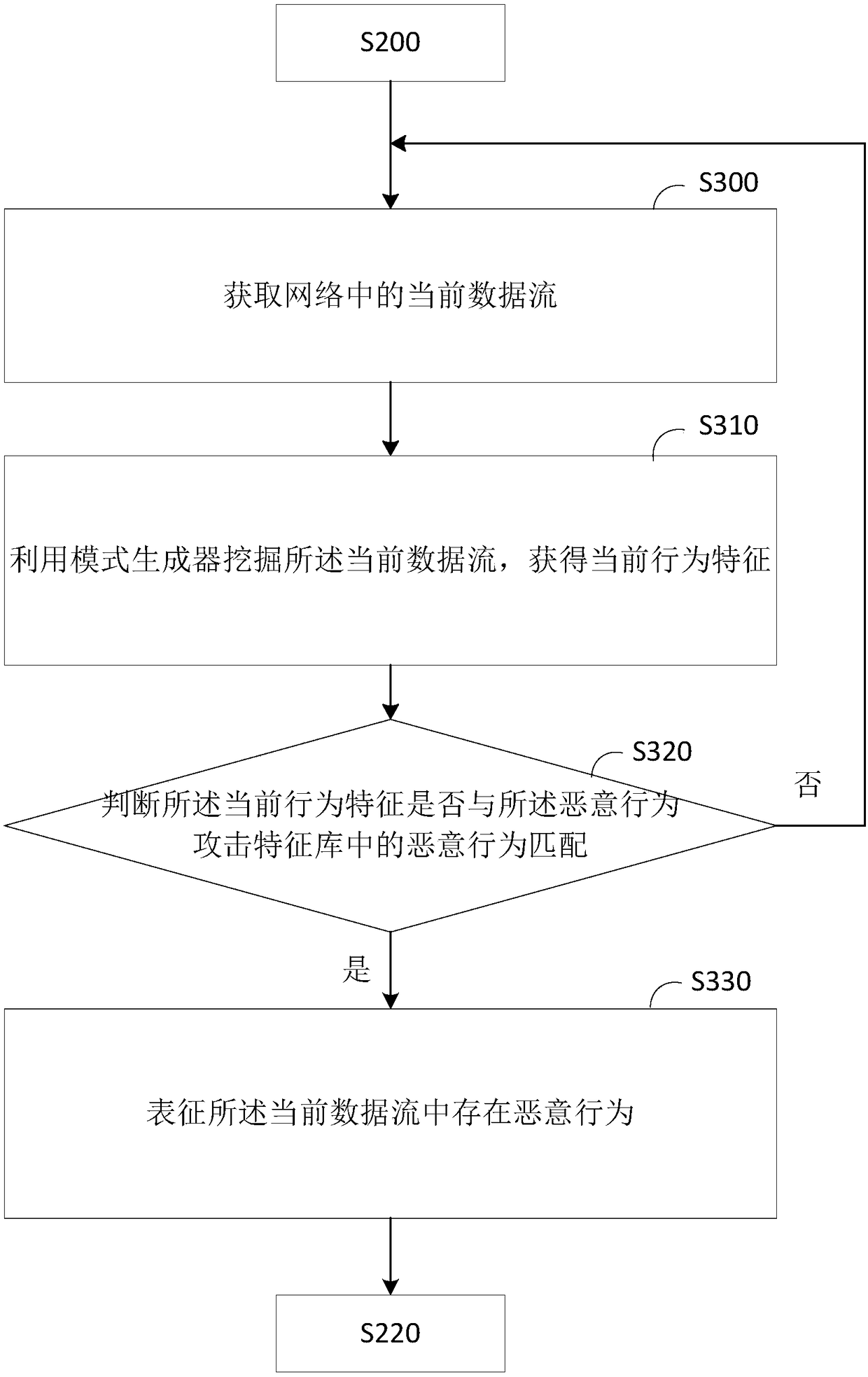
[0084] Please refer to Figure 10 , in this embodiment, further, the detection module 920 may also include the following units:
[0085] An acquisition unit 921, conf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com