Industrial network closed-loop control method with attack protection, and architecture of the same
A closed-loop control and industrial network technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as system robustness decline and system collapse, and achieve the effects of low cost, simplified structure, and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The technical solutions involved in the present invention will be described in detail below in conjunction with the accompanying drawings.
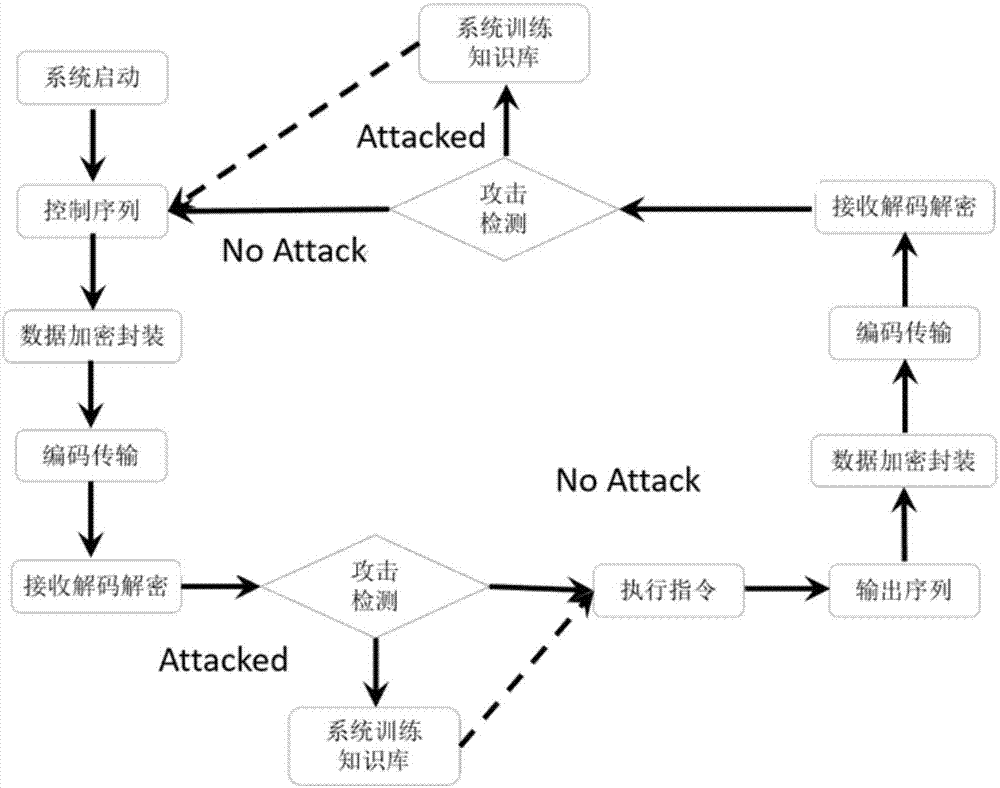
[0023] At the beginning of the system startup, at the control object side, due to the existence of good data for training and learning, in [0,t s ] During the time period, the system status is normal, which provides a basis for selecting the required credible data in the follow-up process. This is a very important design premise.
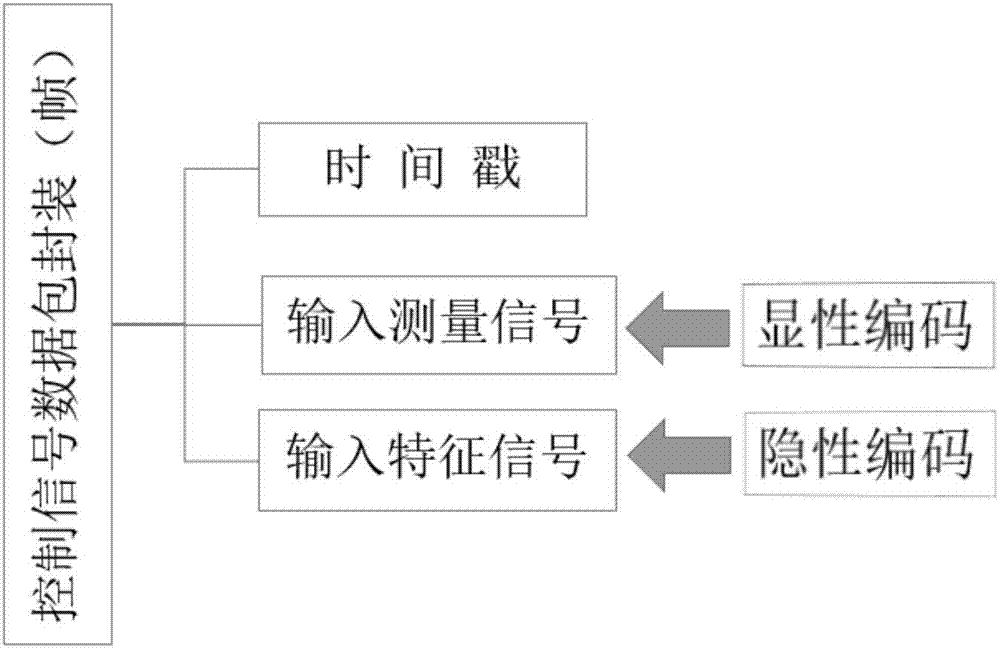
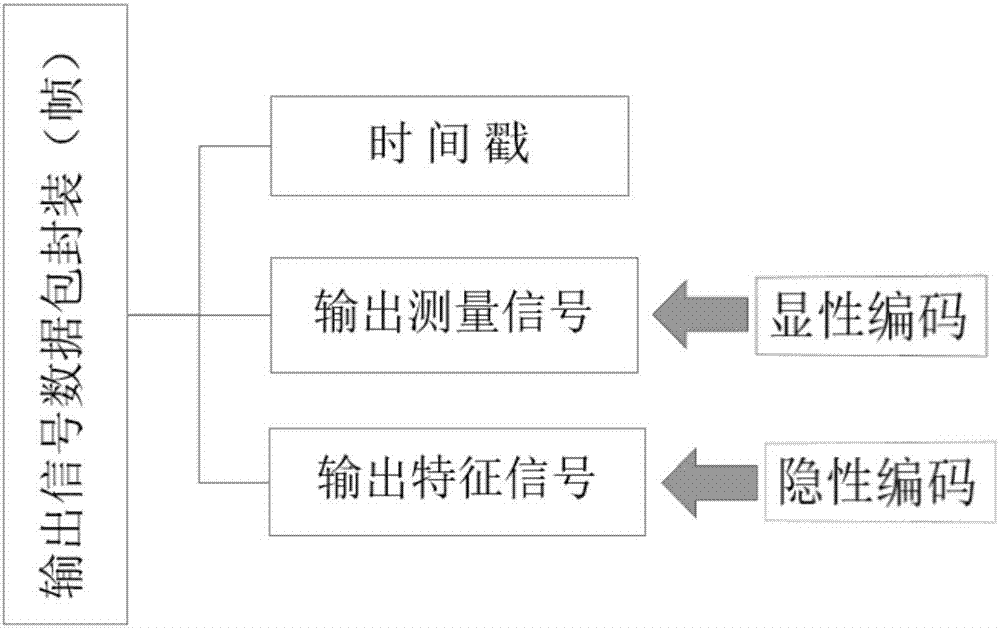
[0024] according to figure 1 , the working principle and working process of the anti-attack architecture of the closed-loop system are as follows, start the system, and control the sequence according to figure 2 The three parts shown in the figure carry out data encapsulation, and the work signal and identification signal are respectively encoded by explicit coding and implicit coding technology, and then transmitted to the remote control terminal through the network medium, the remote control terminal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com