Method for driving web application penetration testing by applying SGM-SQL (sage grant management-structured query language) injection model
A technology of penetration testing and injection model, applied in software testing/debugging, instrumentation, electrical digital data processing, etc. The lack of generalization and other problems can make up for the low accuracy of penetration testing and improve the accuracy of penetration testing.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
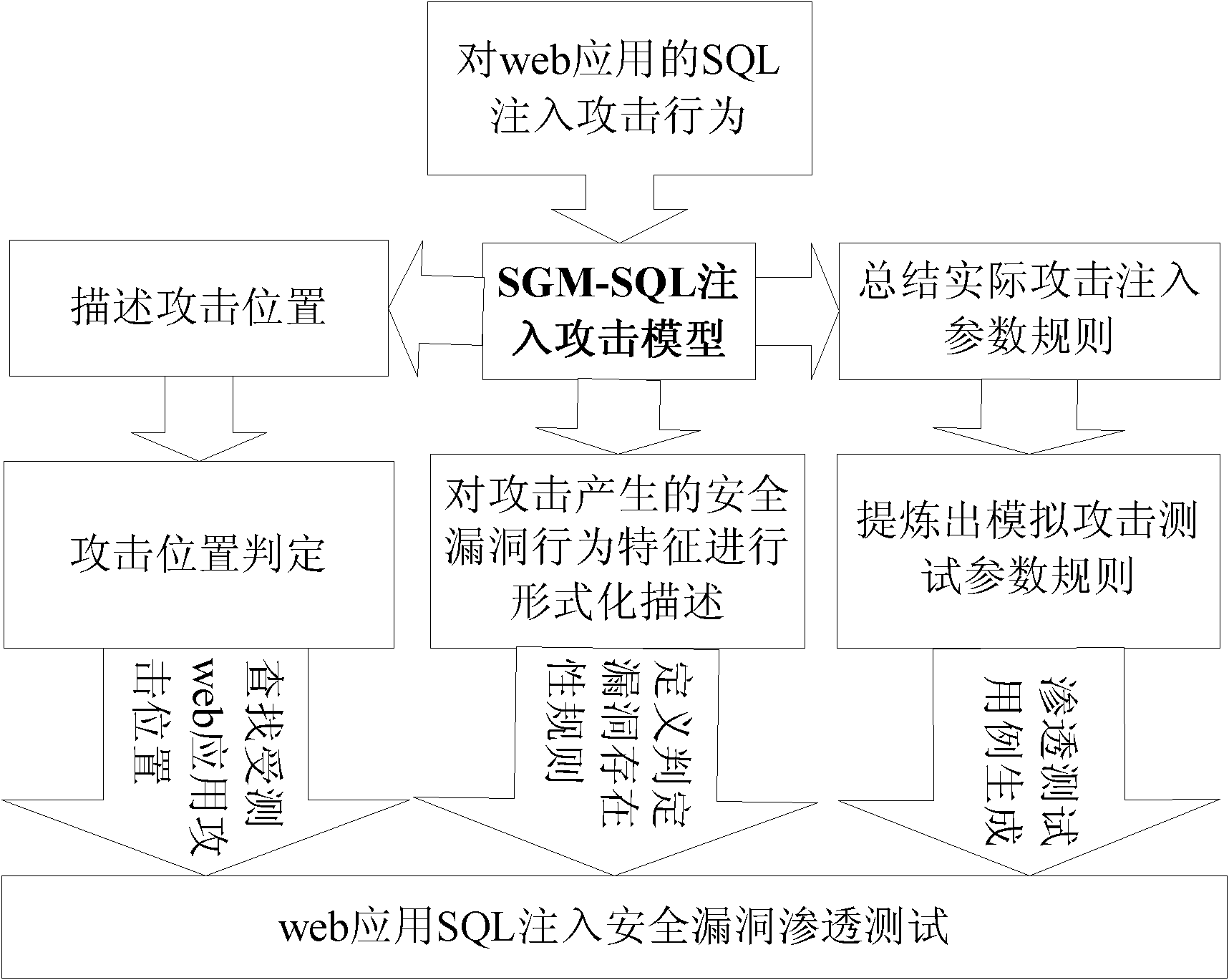
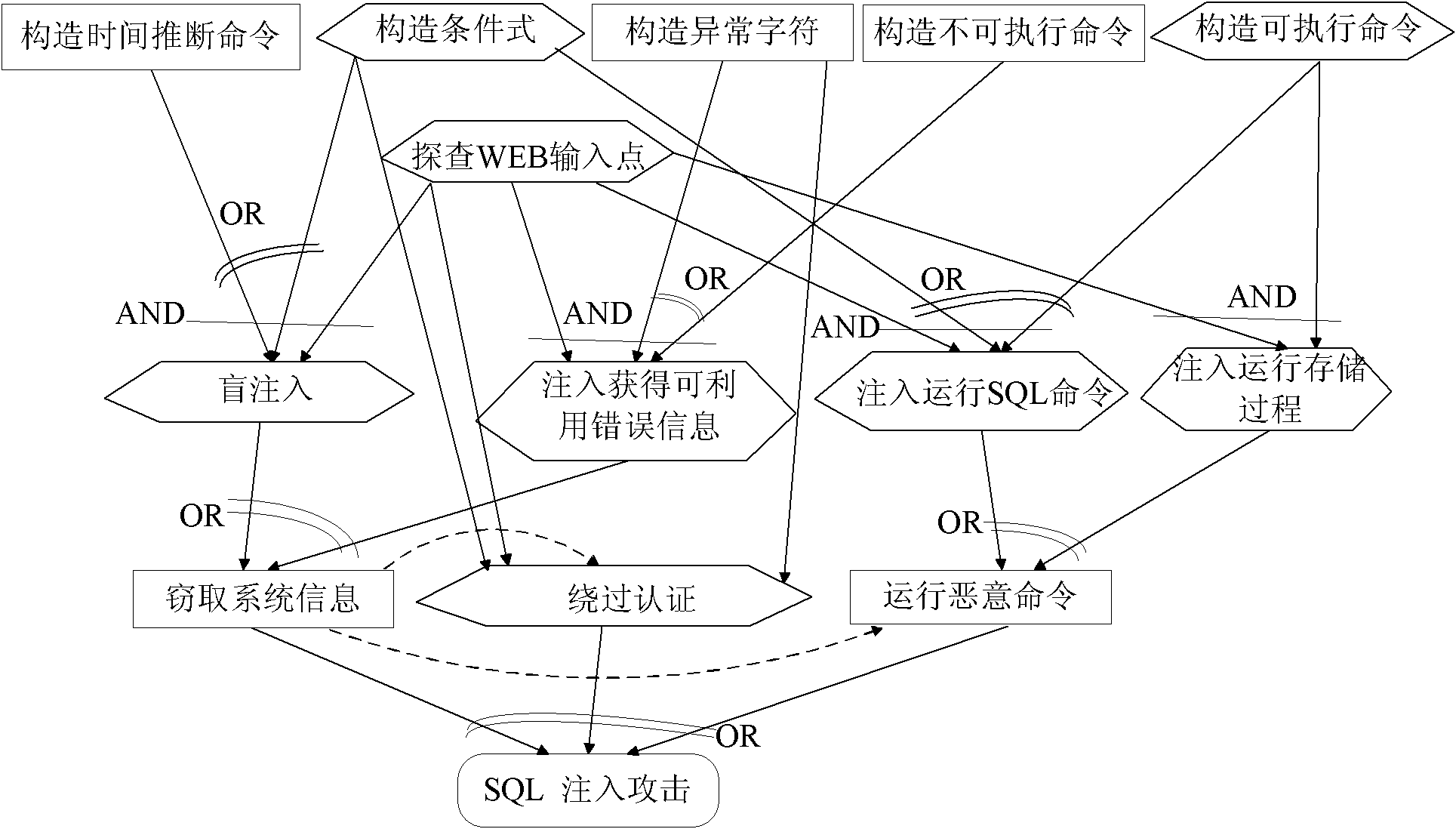
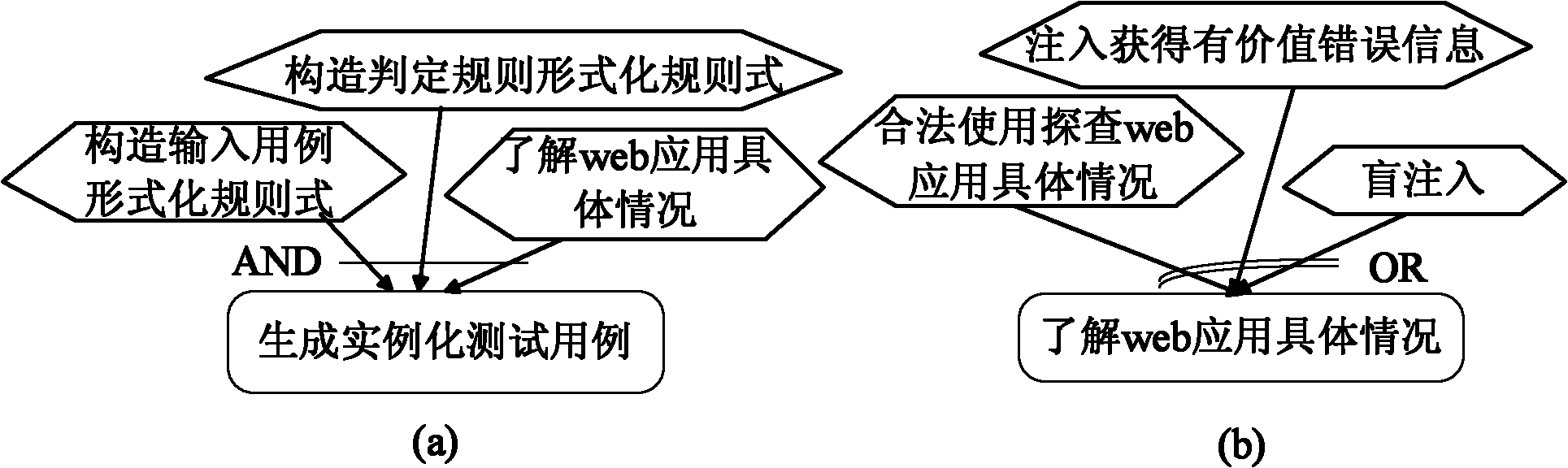
[0177] According to the method of the present invention, based on the instantiation result and test algorithm of the proposed penetration test formal expression system, the penetration test is performed on the SQL injection security loophole of the web application. Taking automatic penetration testing of web applications with SQL injection security vulnerabilities as an example, the specific implementation process is as follows.
[0178] 1. Develop an automatic web application security vulnerability penetration testing system.
[0179] In order to test the target web application, a system for security vulnerability penetration testing of the tested web application can be developed: adopt the general "crawling-injection-analysis" detection method of relevant security vulnerability penetration testing. The main structure of the automatic penetration testing system is recommended to include the following modules: crawling module, penetration testing module (including use case injec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com