Malicious software image format detection model-oriented black box attack defense method and device thereof
A malicious software and detection model technology, applied in neural learning methods, computer security devices, biological neural network models, etc., can solve problems such as error-prone, time-consuming and labor-intensive, and detection technology generalization performance is not high enough to achieve good applicability and accuracy , good detection effect, and the effect of defending against black box attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be further described below in conjunction with the accompanying drawings.
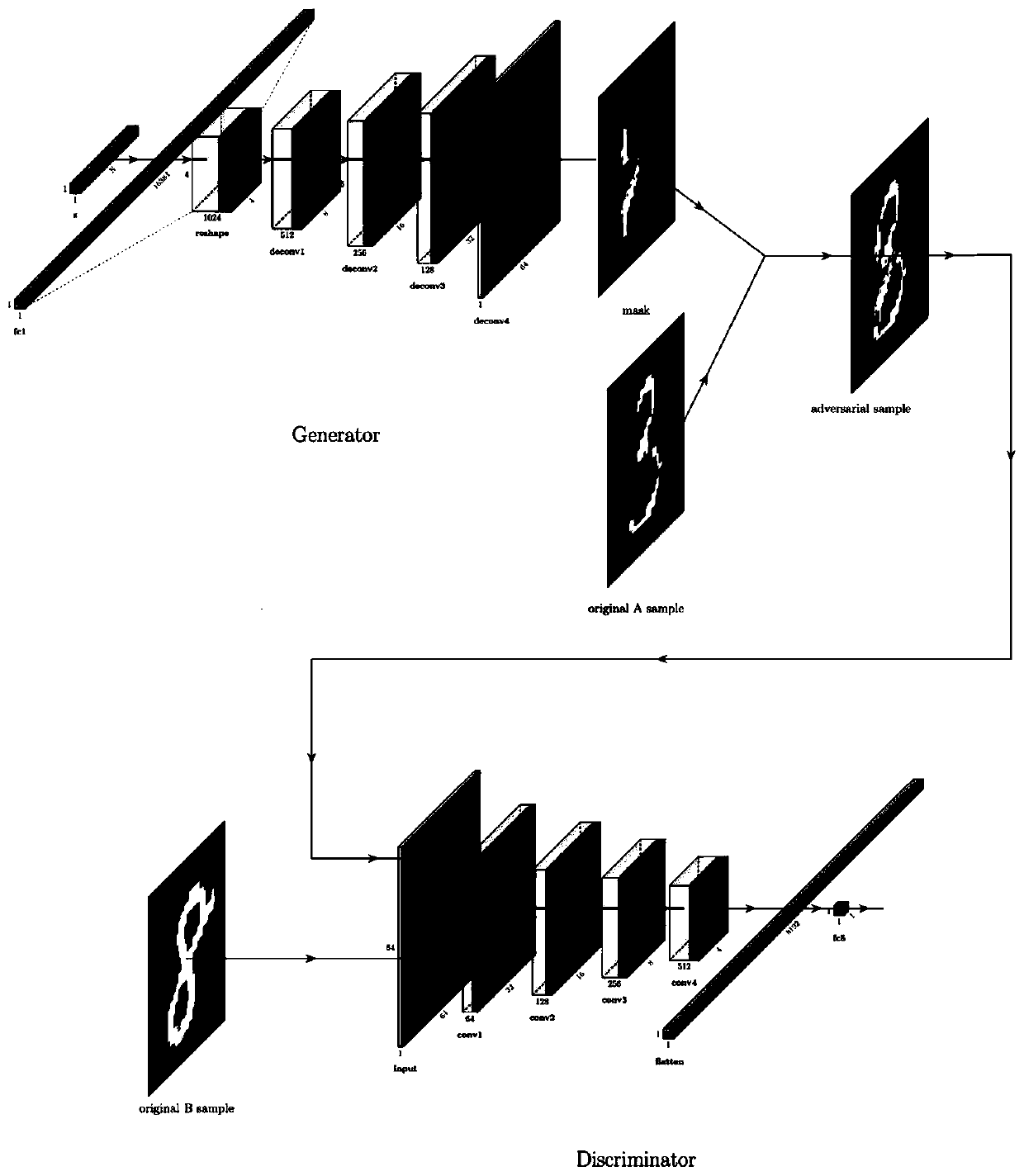
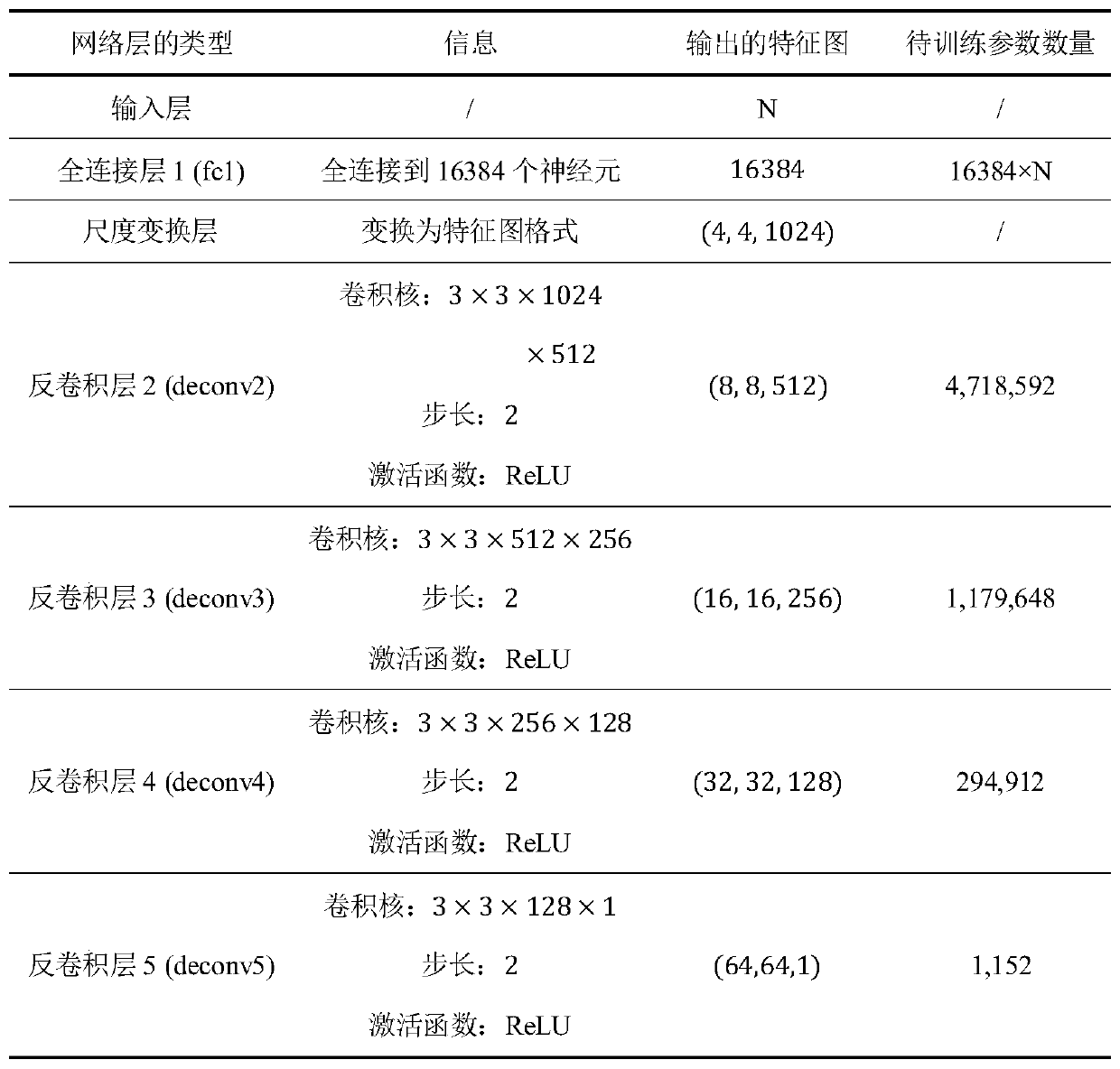
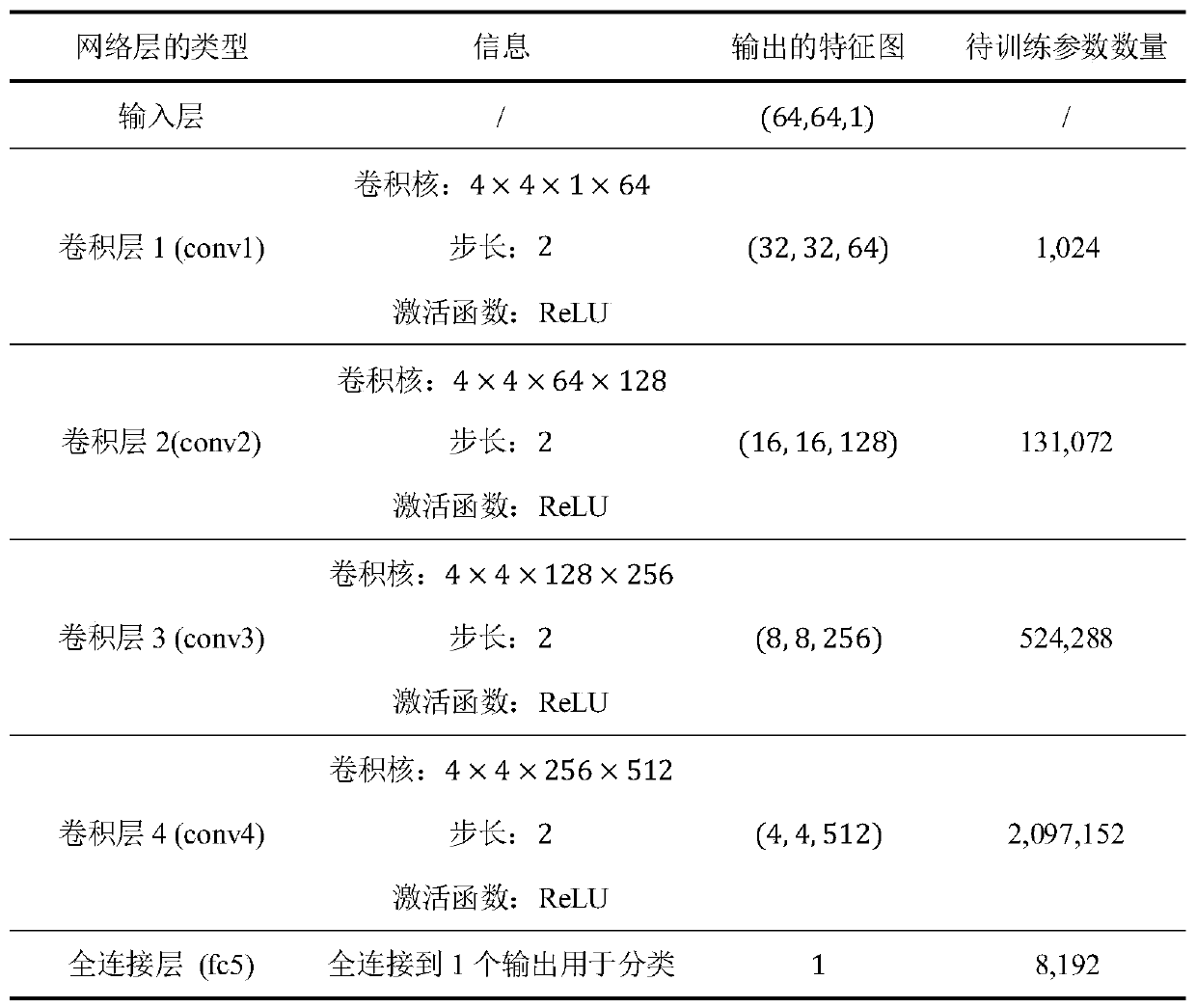
[0044] In the first aspect, the embodiment of the present invention provides a black-box attack defense method for a malware image format detection model, please refer to figure 1 , including the following steps:
[0045] 1) Get the data set and divide it into training set and test set. Specifically include:
[0046] 1.1) Collect sample data sets of various malware families, and save the data in the assembly language file type with the suffix ".asm";
[0047] 1.2) Considering the difference in the number of samples in each category and for the convenience of subsequent work, the data sets of each category are divided into a proportion of about 80% of the training set and about 20% of the test set;
[0048] 2) Convert to a malware image format, specifically including:
[0049] 2.1) For the assembly language file with the ".asm" suffix in step 1.1), each character of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com