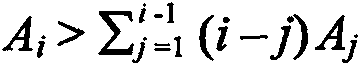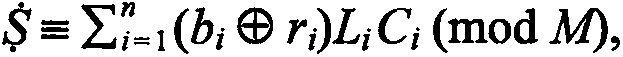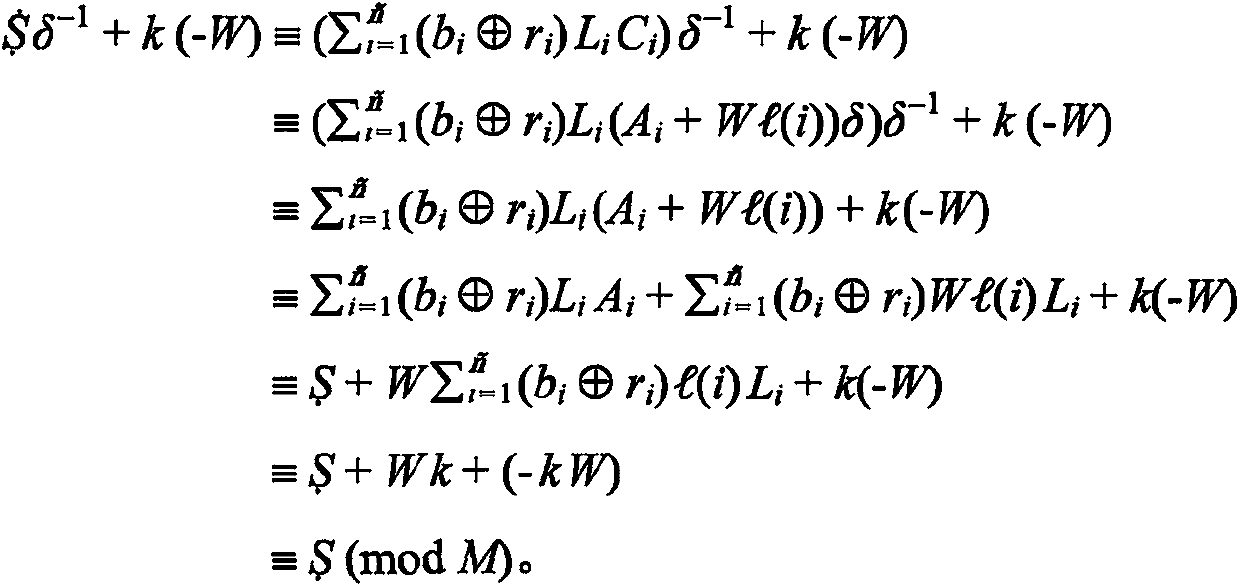Fast quantum secure asymmetrical encryption method
An asymmetric encryption and quantum technology, which is applied to public keys for secure communications, secure communications devices, and key distribution, can solve problems such as slow computing speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0101] The characteristic of the fast quantum-safe asymmetric encryption method is that it allows each user to have two keys, one key can be made public for encryption, and one key can only be kept private for decryption. In this way, there is no need to worry about the secret key being leaked during the transmission process on the Internet. When the two parties agree to transmit information on the Internet, the sender uses the receiver's public key to encrypt the file or message, and the receiver uses its own private key to decrypt the ciphertext after receiving it.
[0102] Each user can obtain two keys from the designated CA center. The CA center is an institution that registers and registers users, and generates, distributes and manages keys. It utilizes the key generation component to generate a pair of public key and private key of the user.
[0103] This encryption method can be realized with logic circuit chip or programming language, and it comprises three parts: (1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com