An authentication method for network signaling between quantum secure network devices
A technology of secure network and network equipment, which is applied in the field of authentication of communication signaling between network communication terminal equipment, can solve the problem that encrypted data cannot be effectively constructed by itself, and achieve the effect of preventing replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
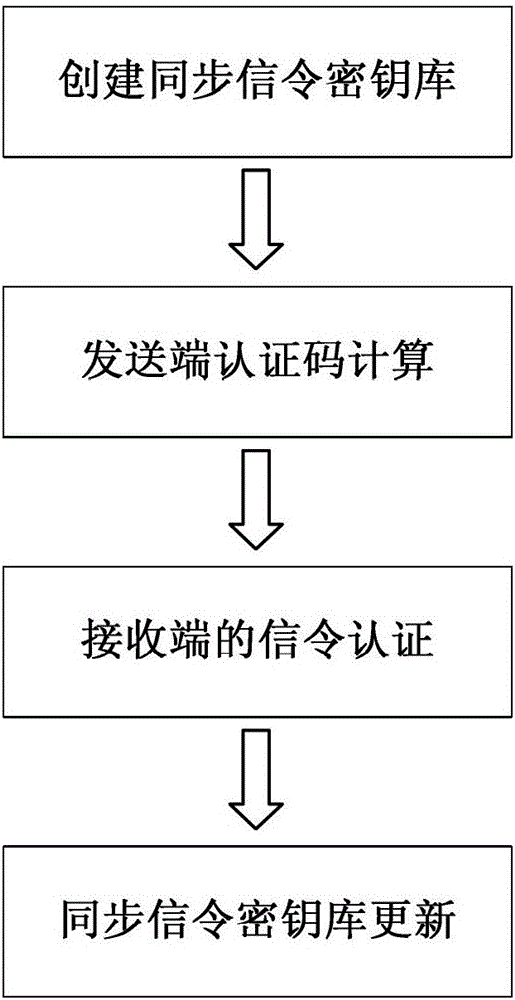
[0032] figure 2 Shown is the signaling authentication flow chart of the present invention, assuming that the communicating network devices are A and B respectively, it is agreed that the length of the key used for signaling authentication each time is L bits, and the value of L is much smaller than the signaling key storehouse The length of the data; the calculation algorithm of the key-related hash operation message authentication code is agreed to be T.
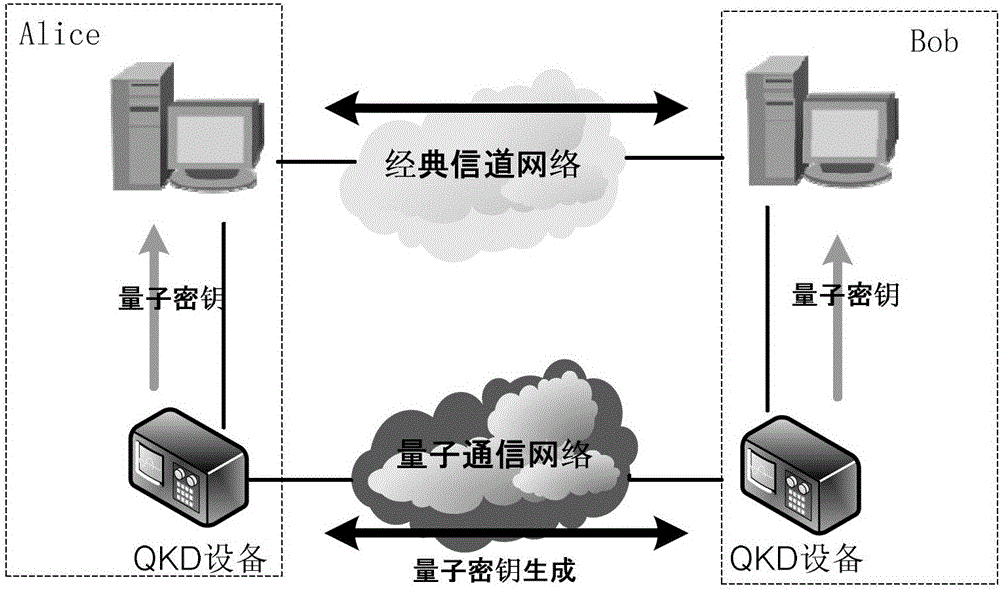
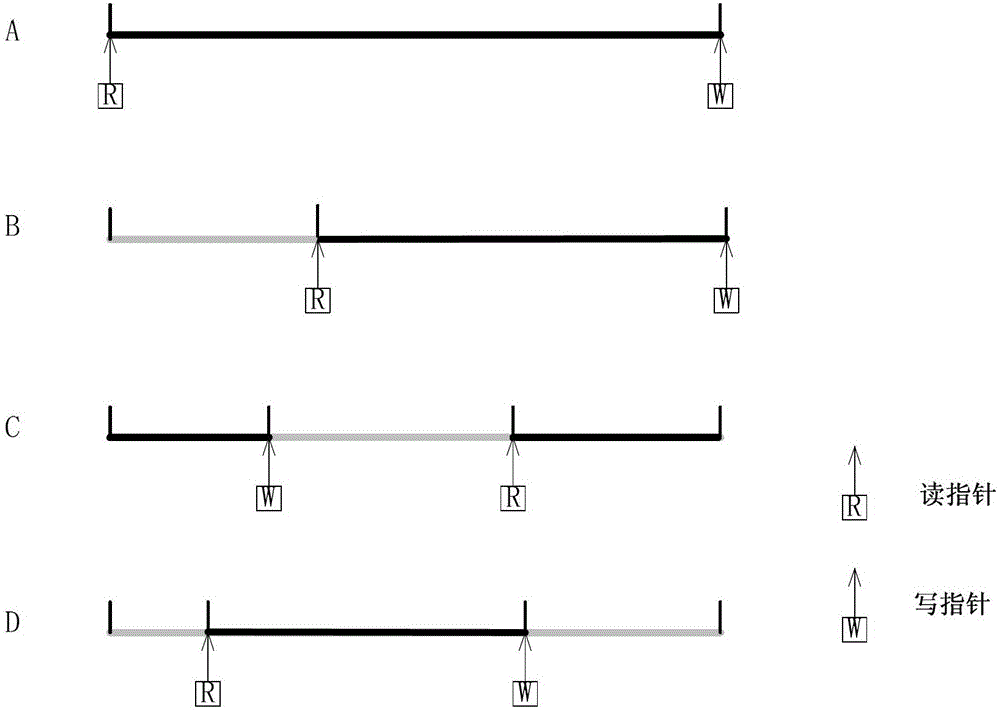
[0033]In the first step, a synchronized quantum key storehouse for signaling authentication of both parties is preset between network device 1 and network device 2, that is, a synchronous signaling key storehouse. The synchronous signaling keystore is divided into two parts, the encrypted signaling keystore and the decrypted signaling keystore; the encrypted signaling keystore is used for encryption of signaling authentication, and the decrypted signaling keystore is used for signaling authentication decryption. The encr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com