Method for defending data integrity attack in direct state estimation of power system
A data integrity, power system technology, applied in transmission systems, digital data protection, information technology support systems, etc., can solve problems such as non-emergence and high cost of PMU
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention is described in further detail below in conjunction with accompanying drawing:
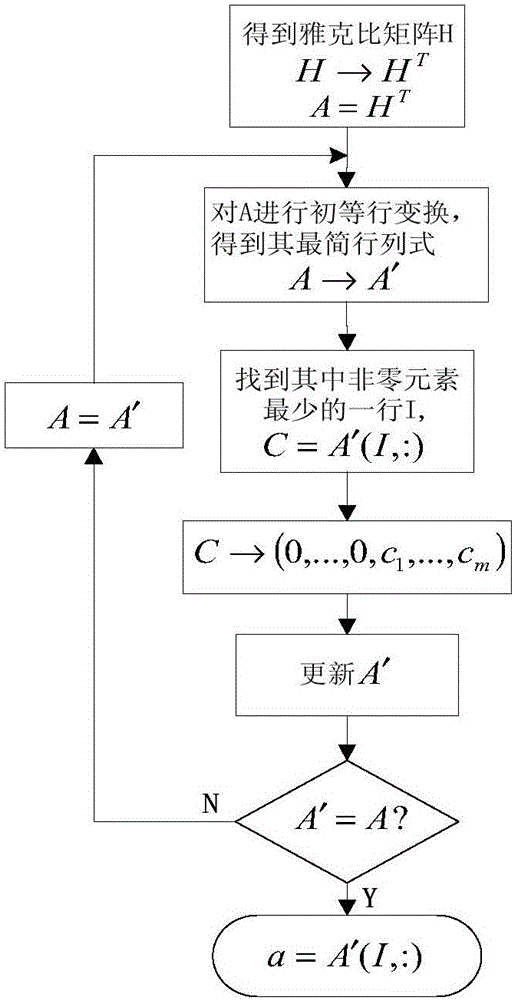
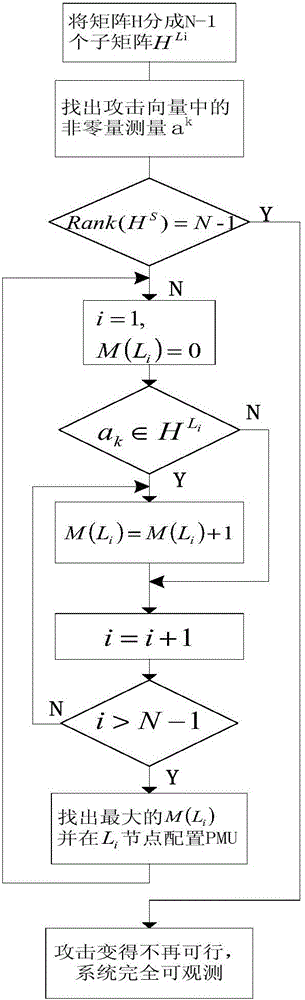
[0043] refer to figure 1 , the method for resisting the data integrity attack in the DC state estimation of the electric power system described in the present invention comprises the following steps:
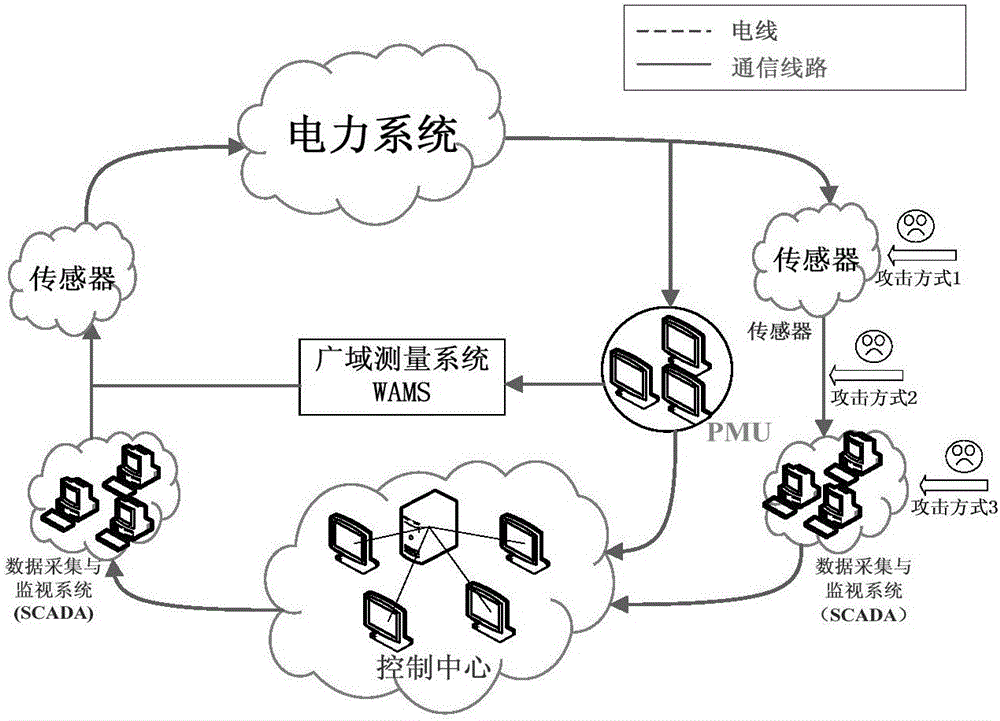
[0044]1) Obtain the network parameters of the power system from the energy management system, wherein the network parameters of the power system include the branch number of the transmission line, the first node number, the last node number, series resistance, series reactance, parallel conductance and parallel susceptance .
[0045] 2) The data acquisition and monitoring control system receives the sensor quantity measurement, and then sends the sensor quantity measurement to the state estimator of the energy management system. The state estimator of the energy management system estimates the real-time state of the power system according to the sensor quantity measurem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com