A prototype modeling method of network security attack based on industrial control
An industrial control network and industrial network technology, which is applied in the field of prototype modeling of network security attacks based on industrial control, can solve the problem of unclear boundaries between enterprise management network and industrial production control network, the fact that industrial control network security has not been widely used, small and medium-sized Enterprises lack awareness of industrial control safety and other issues, to achieve the effect of ensuring enterprise production management and information security, improving network operation efficiency, and ensuring safe operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the above technical solutions will be further described below in conjunction with the illustrations.
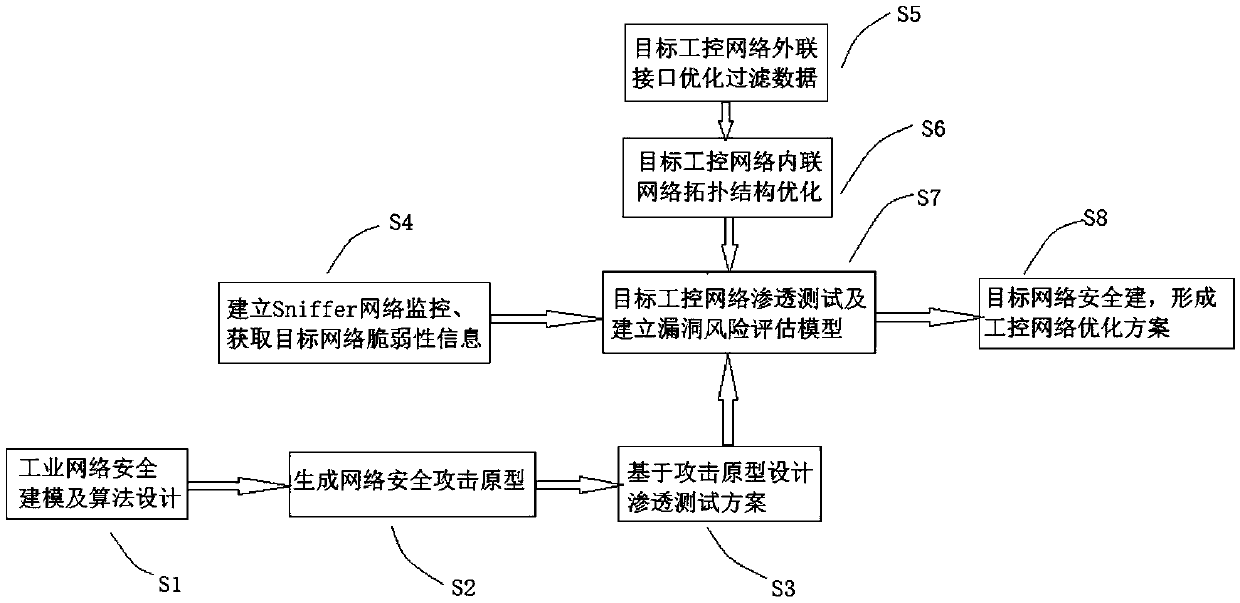
[0029] Such as figure 1 An industrial control network security approach based on prototyping modeling of industrial network attacks is shown, including
[0030] S1: Industrial network security modeling and algorithm design. Industrial network security modeling is to analyze and model network system vulnerabilities, evaluate the risk level of vulnerabilities, and realize the focus and effective defense of harmful vulnerabilities and attack paths;
[0031] S2: Generate a prototype of an industrial control network security attack. The conditions for an attacker to launch an attack are: first, the industrial control component is vulnerable; second, it has a certain connection relationship; third, it has a certain access control authority; if the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com