Webpage log attack information detection method, system and device and readable storage medium
An information detection and logging technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve the problems of not being able to obtain summary statistics of network security, missing the opportunity to capture attackers, and passing analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
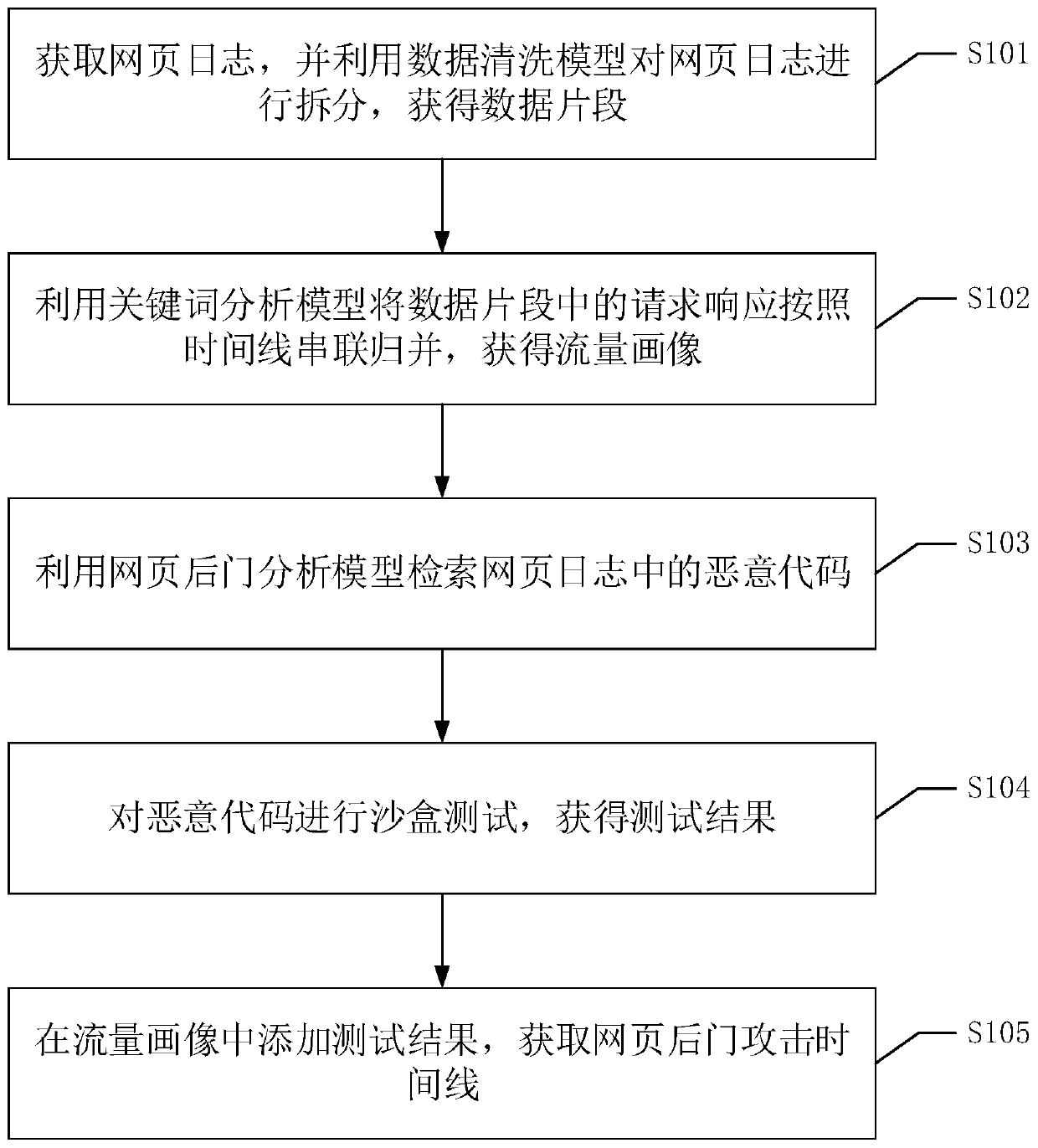
[0051] For ease of understanding, the following briefly describes the shortcomings of the prior art and the core idea of the solution proposed in this embodiment.
[0052] As far as the analysis results of existing tools for web logs (ie, web logs) are concerned, the data is simply split and not processed logically, so that web logs do not play the important role imagined in daily work.
[0053] For the existing web log analysis products, the main disadvantages are concentrated in the following aspects. Disadvantage 1: The volume of web logs is huge, many tools are difficult to analyze, and system crashes often occur. Disadvantage 2: The analysis effect of most products is not good, and it just stays in the summary of the analyzed data and does not go deep into logical concatenation of effective data fragments. Disadvantage 3: Manpower is required to draw data conclusions, and in the end it is still up to humans to judge some network operation behaviors.
[0054] In view of...
Embodiment 2
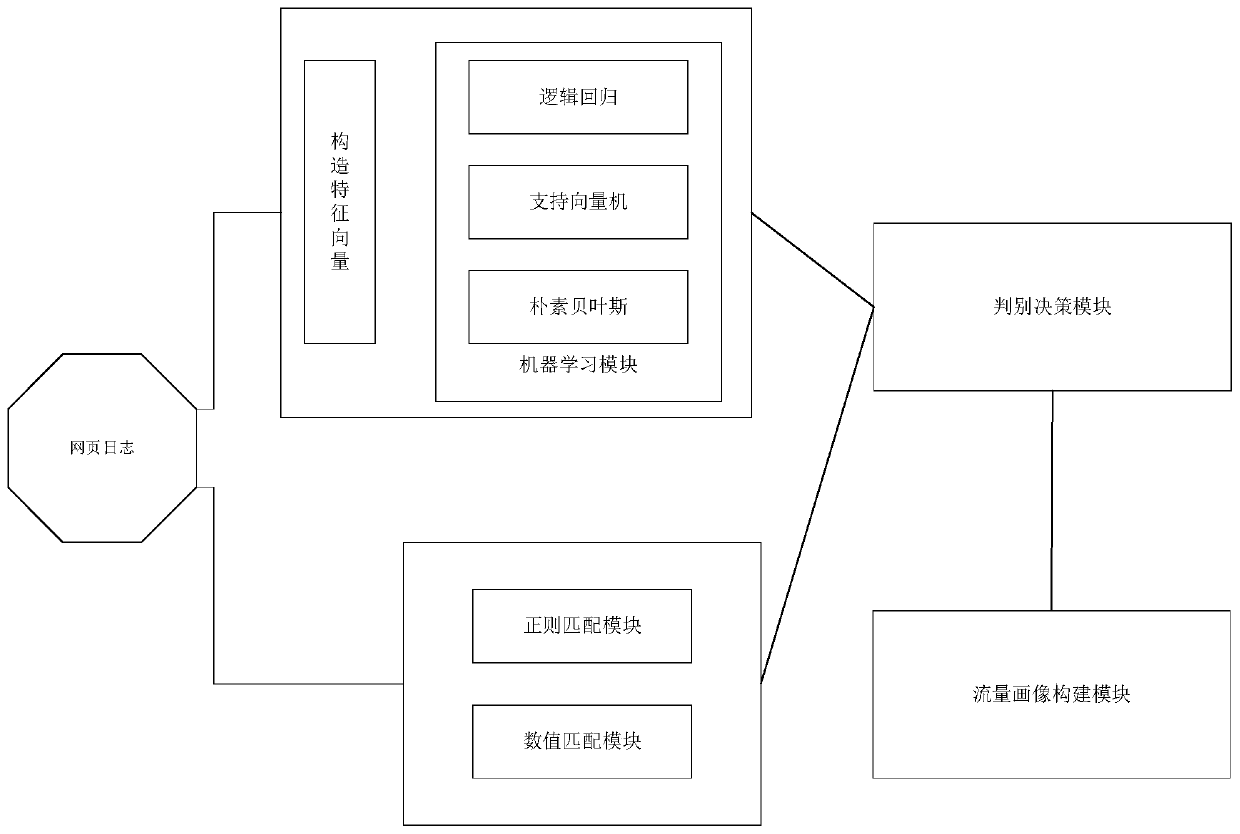
[0087] Corresponding to the above method embodiment, the embodiment of the present invention also provides a web log attack information detection system, the web log attack information detection system described below and the web log attack information detection method described above can be referred to each other.
[0088] see image 3 As shown, the system includes:
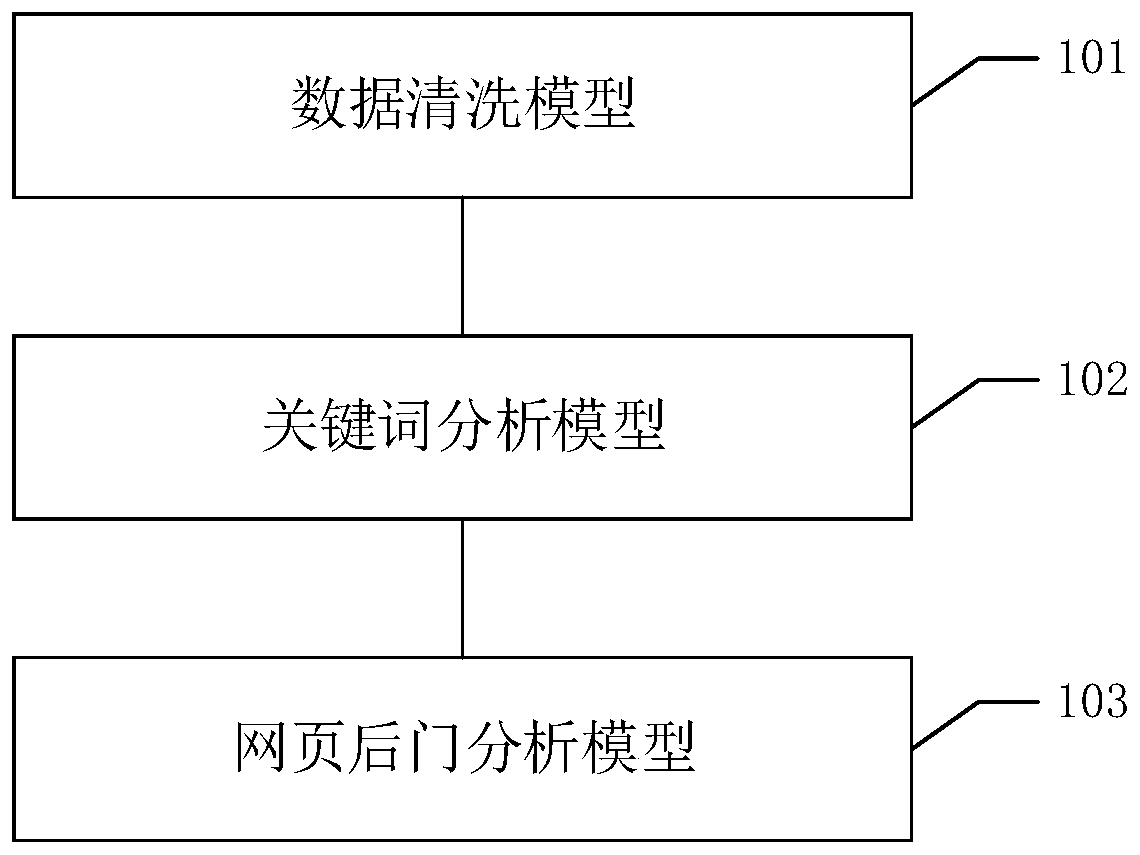
[0089] Data cleaning model 101, keyword analysis model 102 and webpage backdoor analysis model 103;
[0090] Data cleaning model, used to split web logs to obtain data fragments;
[0091] The keyword analysis model is used to serially merge the request responses in the data fragments according to the timeline to obtain traffic portraits;
[0092] The webpage backdoor analysis model is used to retrieve malicious codes in webpage logs; conduct sandbox tests on malicious codes to obtain test results; add test results to traffic portraits to obtain webpage backdoor attack timelines.
[0093] Apply the device prov...
Embodiment 3
[0107] Corresponding to the above method embodiment, the embodiment of the present invention also provides a webpage log attack information detection device, a webpage log attack information detection device described below and a webpage log attack information detection method described above can be mutually Corresponding reference.
[0108] see Figure 4 As shown, the webpage log attack information detection equipment includes:
[0109] memory D1 for storing computer programs;
[0110] The processor D2 is configured to implement the steps of the method for detecting web page log attack information in the above method embodiment when executing the computer program.
[0111] Specifically, please refer to Figure 5 , is a specific structural diagram of a webpage log attack information detection device provided in this embodiment. The webpage log attack information detection device may have relatively large differences due to different configurations or performances, and may i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com