Solution for cloud Web application to cope with virtual host layer attacks
A virtual host and solution technology, applied in software simulation/interpretation/simulation, program control design, instruments, etc., can solve problems such as defense methods that cannot meet the security requirements of web servers on the cloud, business interruption, and servers that cannot be repaired immediately. Achieve the effect of increasing attack difficulty and cost and realizing business
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be described in further detail below with reference to the accompanying drawings and examples.
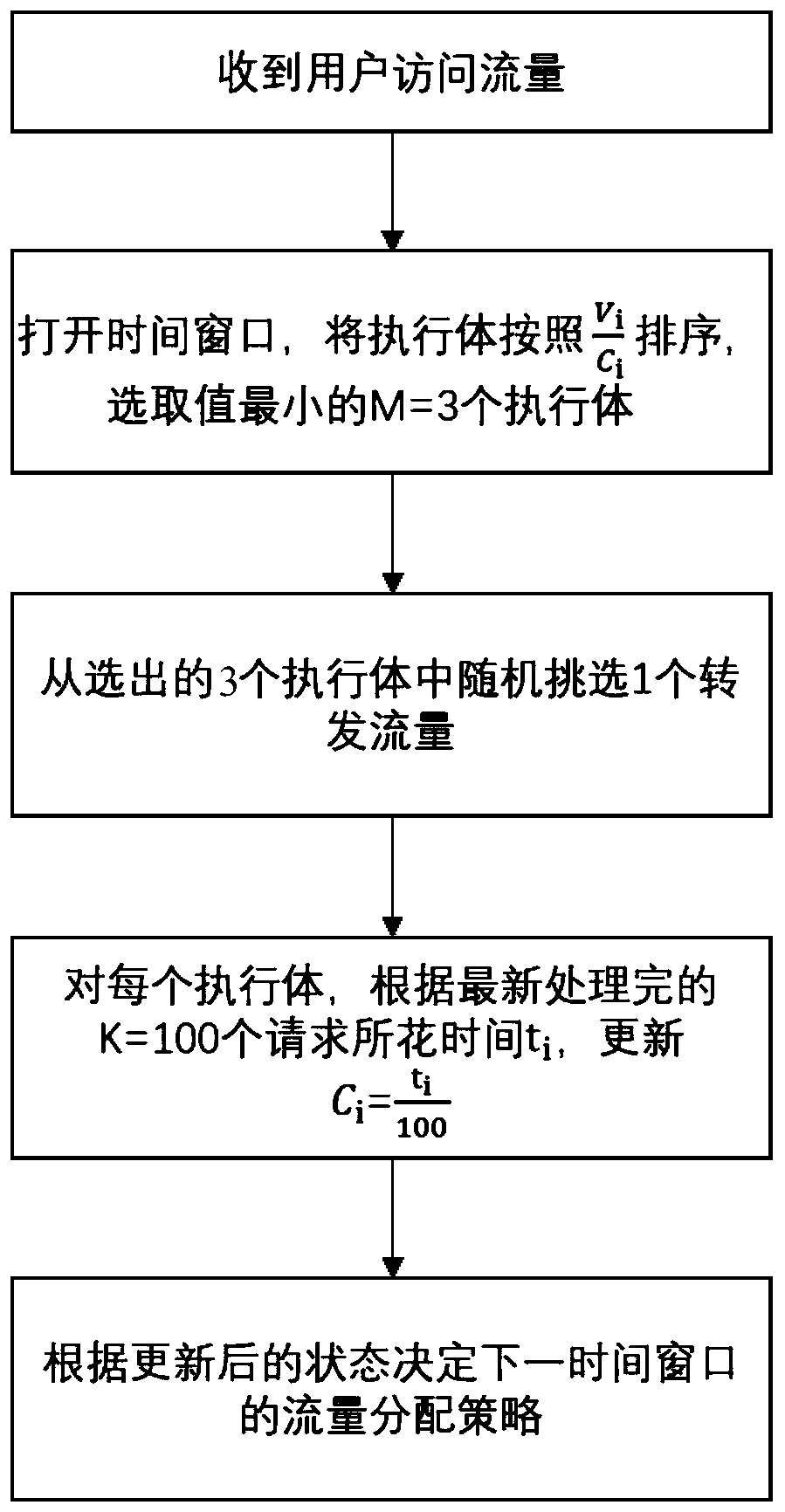
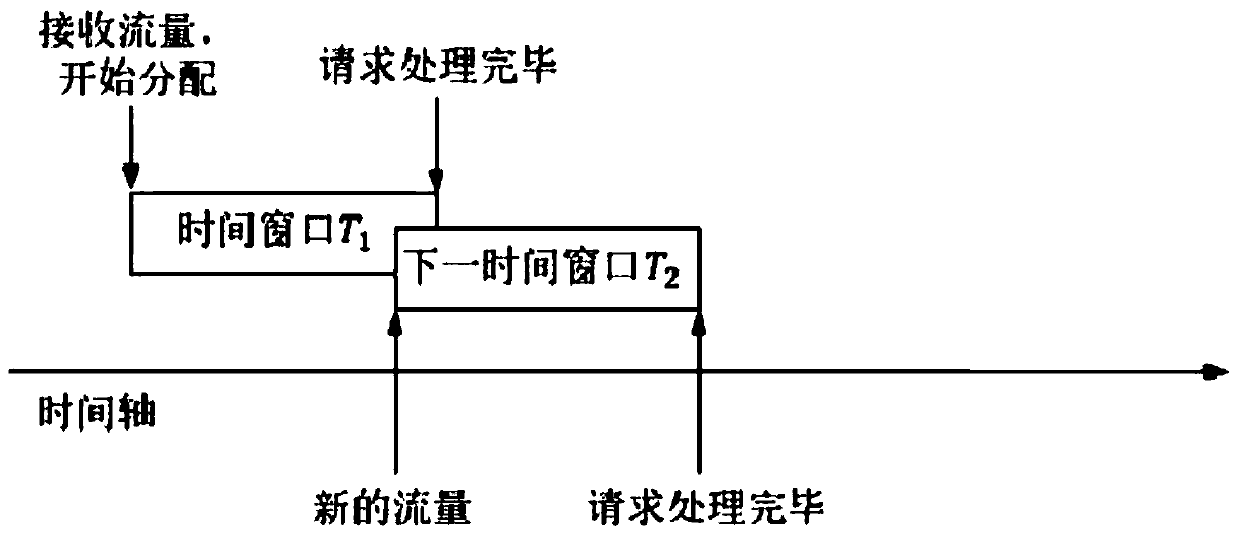
[0023] The present invention is realized through the following steps:
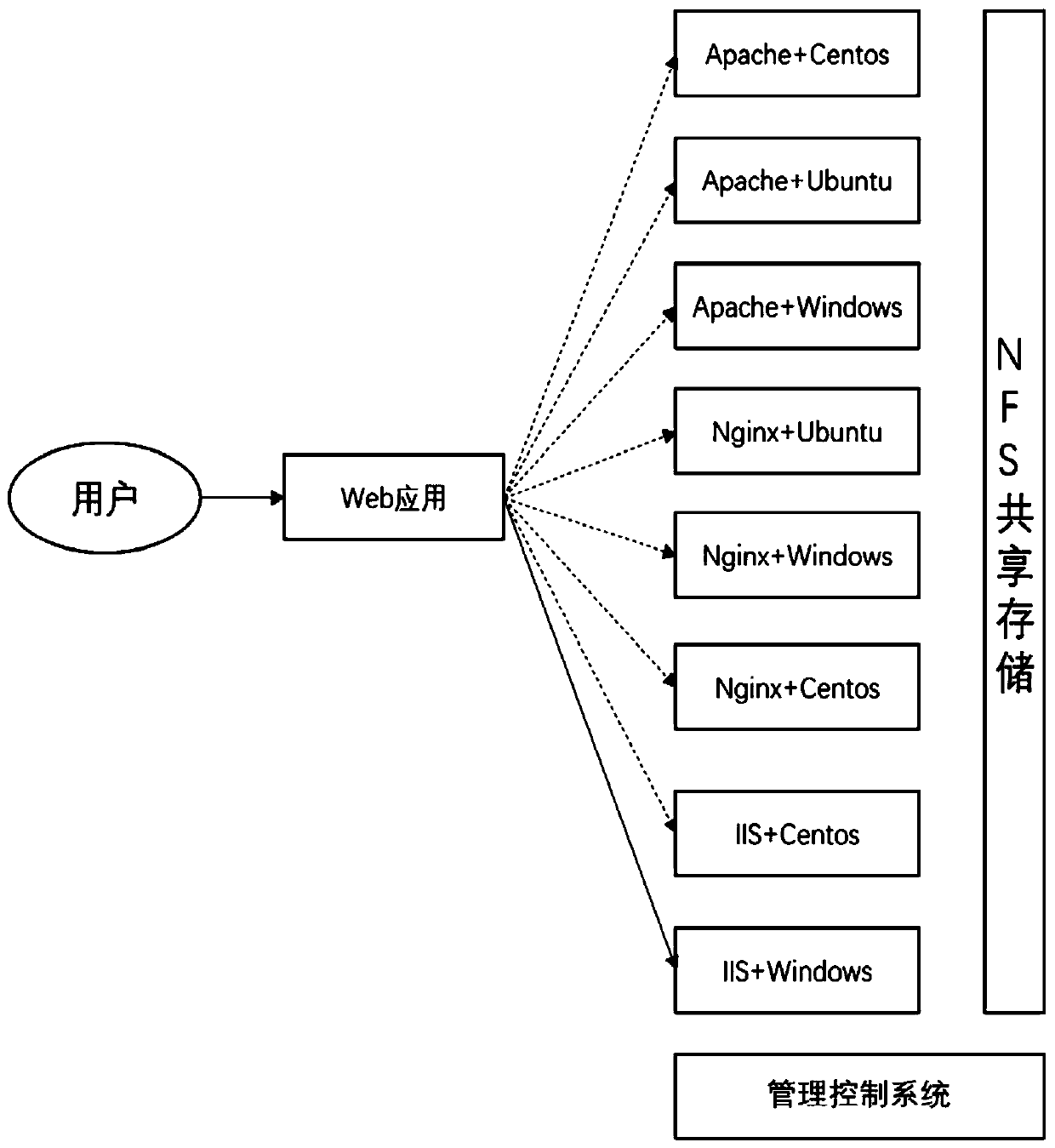
[0024] Step 1. Realize the heterogeneity of the operating system of the Web server and the virtual machine.
[0025] Build multiple virtual machines, and install a web server and operating system on each virtual machine, and the combination of web server and operating system is not exactly the same, and each heterogeneous virtual machine is an execution body. The web server can choose Apache, Nginx and IIS; the operating system can choose Ubuntu, Windows and Centos operating system. like figure 1 As shown, a total of 8 executives A have been created 1 ~A 8 (Apache+Centos, Apache+Ubuntu, Apache+Windows, Nginx+Ubuntu, Nginx+Windows, Nginx+Centos, IIS+Centos, IIS+Windows).
[0026] Step 2, ensuring redundancy among executive bodies.
[0027] The web application data on all e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com