Method for remotely and accurately identifying WebShell back door
A backdoor and accurate technology, applied in the direction of using information identifiers to retrieve Web data, special data processing applications, instruments, etc., can solve the problems of deploying traffic audit systems, deformation or confusion, and inability to detect, to enrich inspection methods, improve The effect of detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be described in further detail below in conjunction with the examples, but the protection scope of the present invention is not limited thereto.
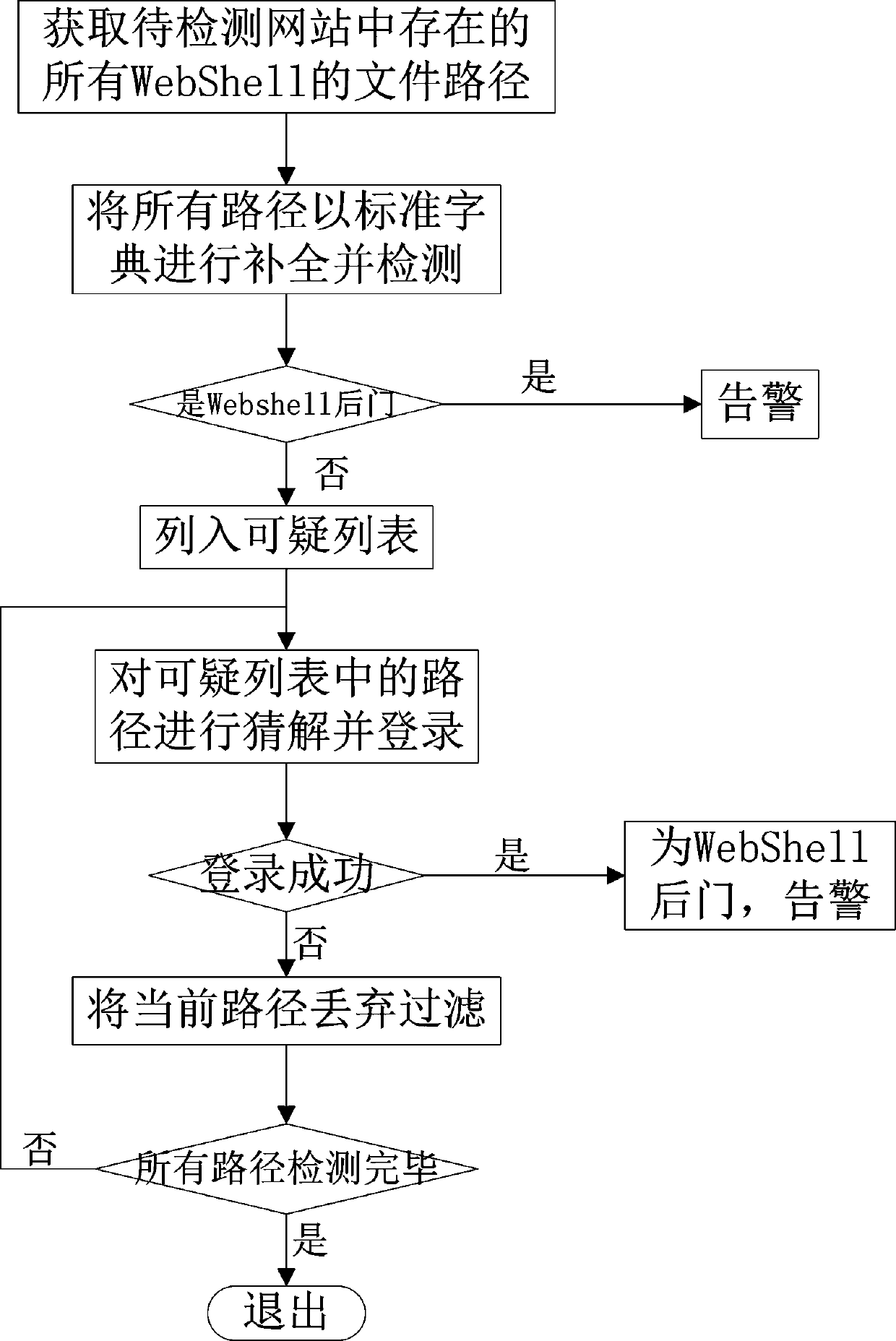
[0031] The invention relates to a method for remote and accurate identification of WebShell backdoors. All webpage resources are crawled by crawlers on the target website, and are matched with common WebShell backdoor path dictionaries throughout the site, and the WebShell backdoor rule library is used to match whether there is a backdoor, and through a remote method Accurately identify WebShell backdoors.
[0032] The method includes the following steps.
[0033] Step 1: Obtain the file paths of all WebShells existing in the website to be detected.
[0034] In step 1, the file path includes URL links of any webpage, links in attachments and / or directory listings.
[0035] In the present invention, the crawler function is used to crawl the file path of the WebShell that may exist in the website. I...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com