Industrial network endogenous security boundary protection method, device and architecture
A security boundary, industrial network technology, applied in electrical components, transmission systems, etc., can solve problems such as difficult to detect in time, illegal internal network transmission, and lack of comparison of single deployment, achieve good application prospects, improve the correctness of filtering and review, The effect of mitigating the threat of uncertainty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
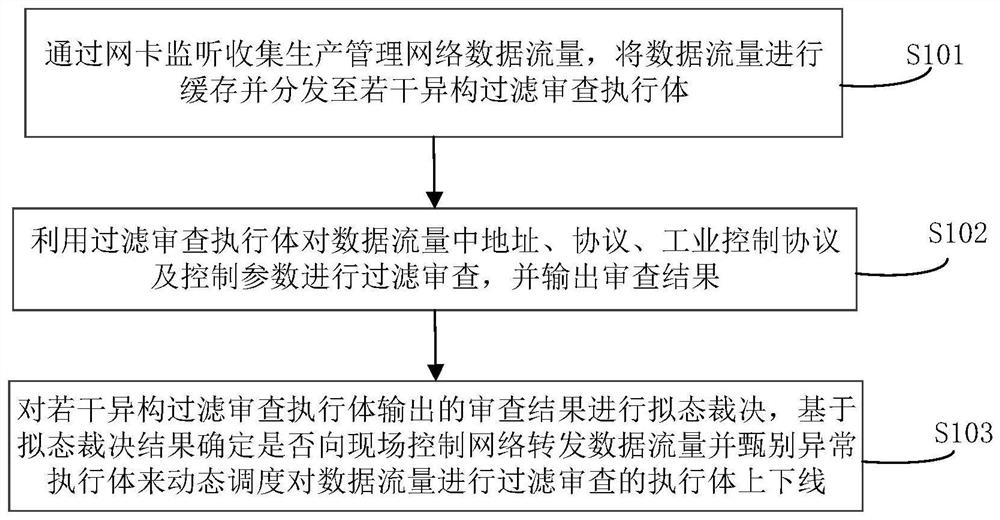
[0032] An embodiment of the present invention provides a method for protecting an endogenous security boundary of an industrial network, see figure 1 As shown, it contains the following content:
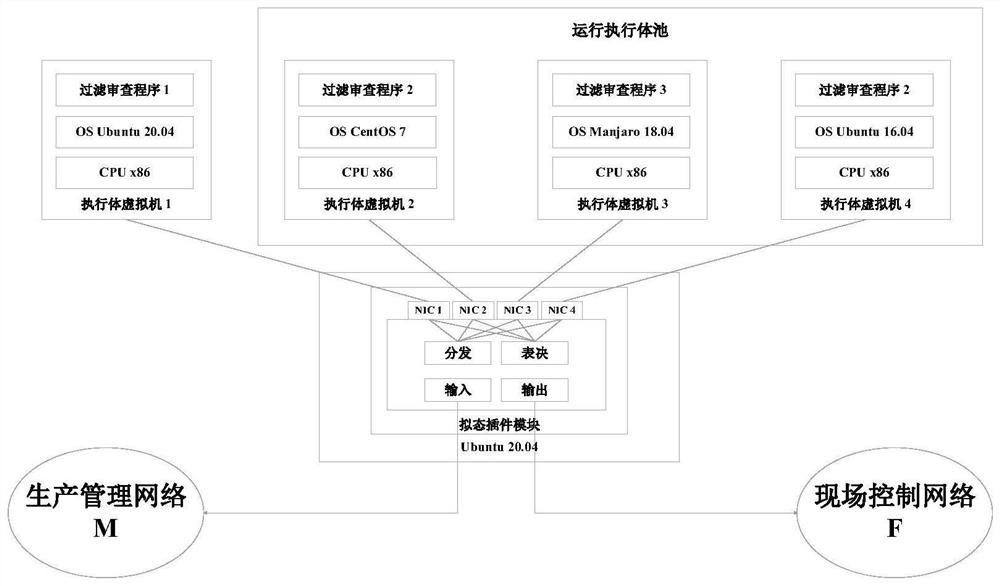
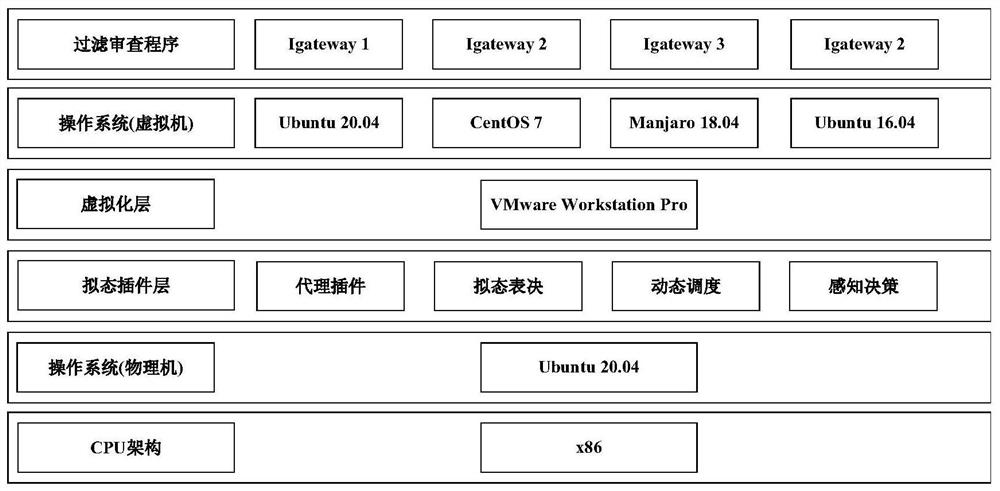
[0033] S101. Collect production management network data traffic through network card monitoring, cache and distribute the data traffic to several heterogeneous filtering and review execution bodies;
[0034] S102. Use the filtering and reviewing executive body to filter and review the address, protocol, industrial control protocol and control parameters in the data flow, and output the review result;
[0035] S103. Perform a mimicry ruling on the review results output by several heterogeneous filtering and reviewing executi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com