Active defense method of program behavior analysis on basis of cloud platform
A behavior analysis and active defense technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of lag in anti-virus technology, troubled users, and lower threshold of malicious code manufacturing technology, and achieve the effect of improving security defense capabilities and ensuring host security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] In order to make the object, technical solution, and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
[0024] The embodiment of the present invention provides a method for program behavior analysis based on a cloud platform to solve the problem that the existing network security technology lags behind various attack technologies based on virus signature comparison technology.
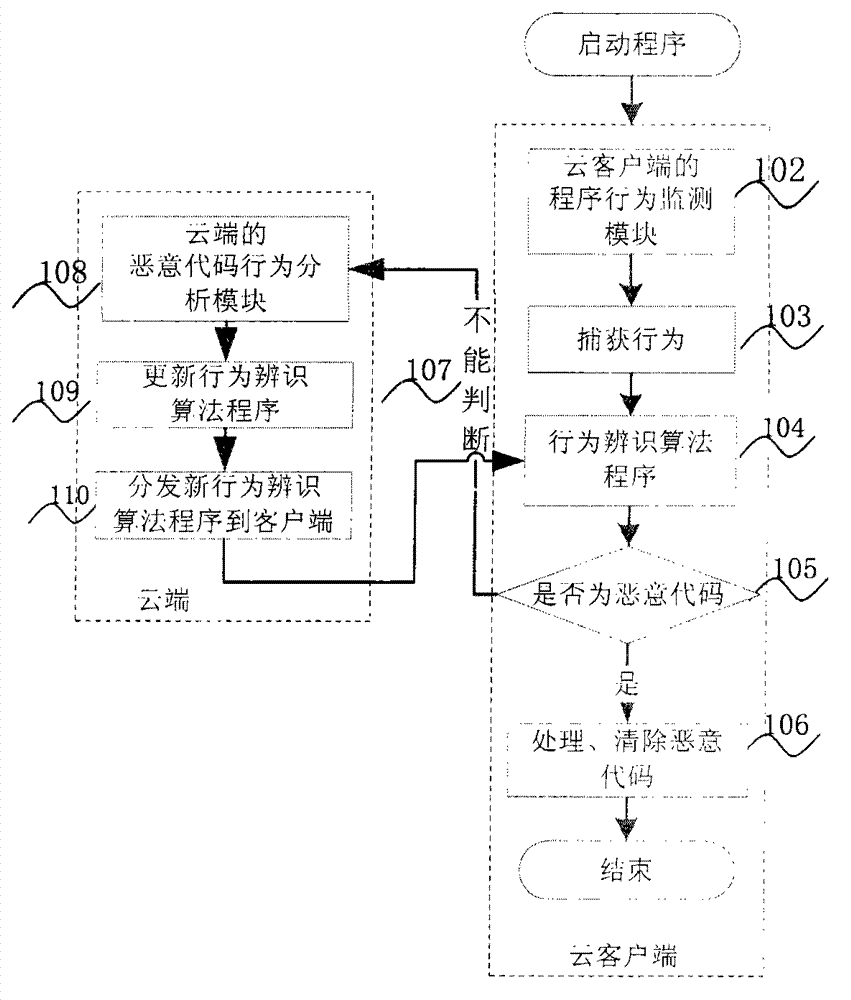
[0025] combine figure 1 The flow chart to illustrate:
[0026] Step 101: On the cloud client computer, run or start any program, such as *.exe, *.dll and other target programs; the running target programs also include operating system executable files such as: *.exe, *.com, etc.; Various script programs such as: *.vbs, *.vsh, *.js, *.bat; system kernel program and driver loading.
[0027] Step 102: under the action of the "program behavior monitoring module" of the cloud client...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com