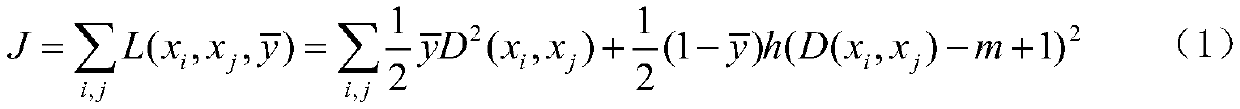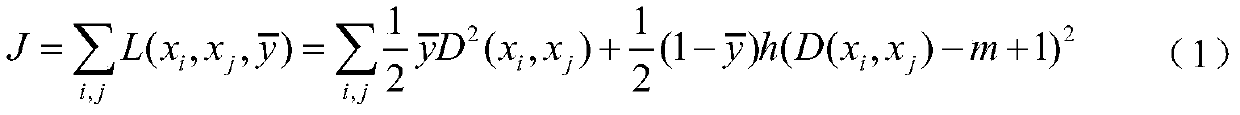Unknown malicious traffic active detection system and method based on deep embedding
A malicious traffic, active detection technology, applied in the field of network security, can solve the problems of low false alarm rate and high detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
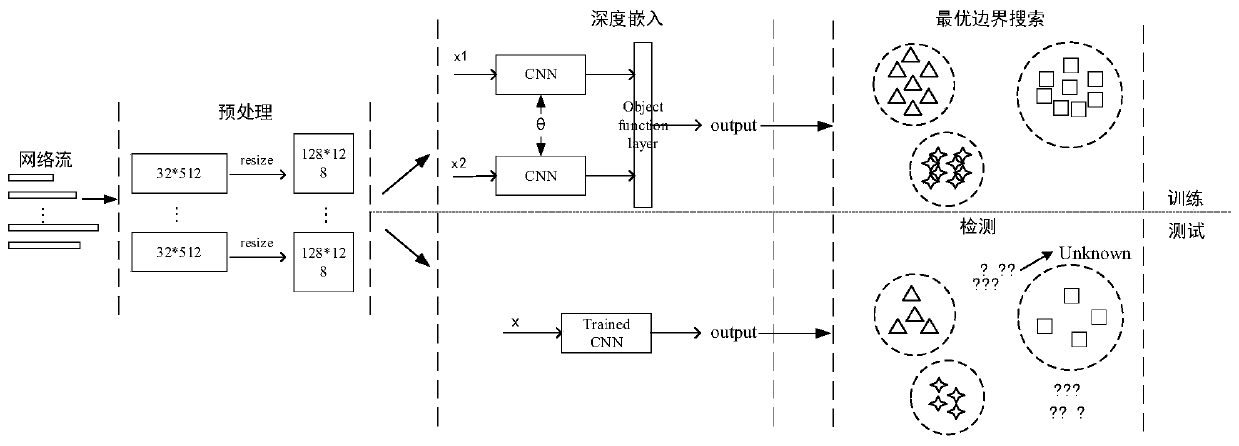
[0076] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
[0077] 1. Problem Definition
[0078] In the training phase, given the training sample set in is the training sample, y i ∈{l 1 , l 2 ,...,l k} is x i corresponding category labels. In the test phase, it is necessary to predict an open sample set D 0 ={(x i ,y i )} ∞ The class label y of i , where y i ∈{l 1 , l 2 ,...,l k ,...,l K}, K>k. In this paper, each sample x i Represents a network flow (that is, a group of consecutive data packets with the same IP quintuple ), the corresponding class label y i stands for generating x i Applications. The goal of the present invention is to use a given set of training samples to construct a classifier C: x→Y'={l 1 , l 2 ,...,l k ,unknown}, where unknown represents a category that has not appeared in the training phase. Network flows classified as unknown during the test phase are judge...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com