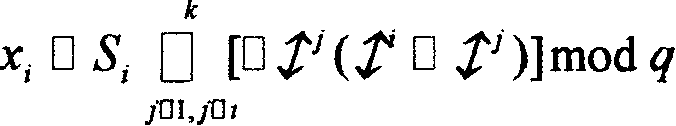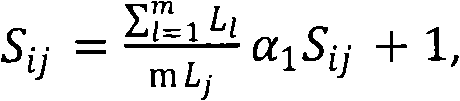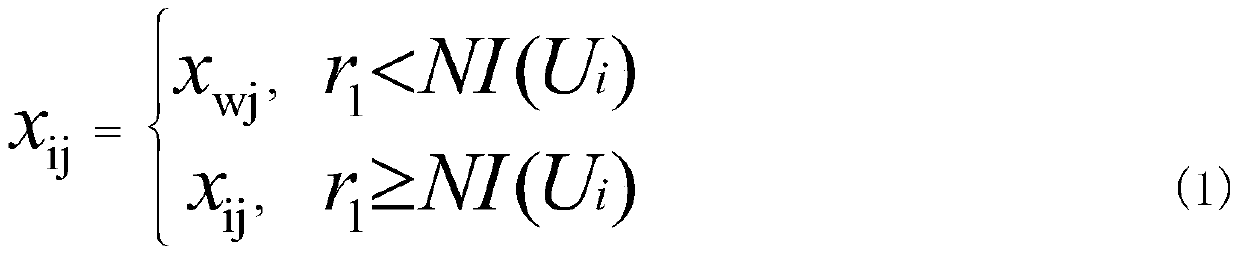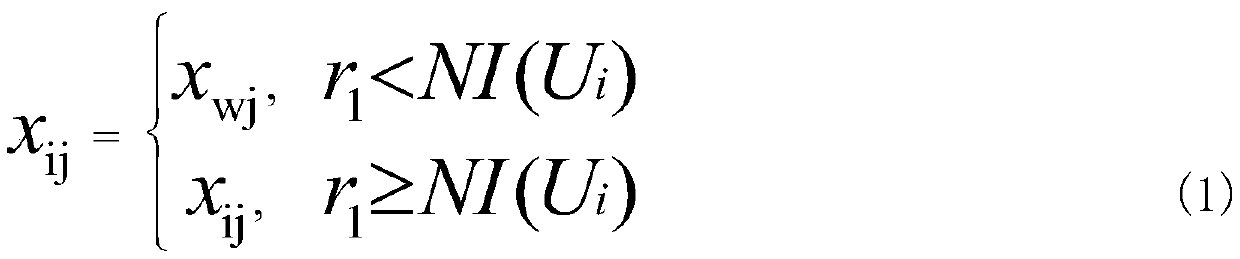Patents
Literature
120 results about "Wormhole" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A wormhole (or Einstein–Rosen bridge) is a speculative structure linking disparate points in spacetime, and is based on a special solution of the Einstein field equations solved using a Jacobian matrix and determinant. A wormhole can be visualized as a tunnel with two ends, each at separate points in spacetime (i.e., different locations and/or different points of time). More precisely it is a transcendental bijection of the spacetime continuum, an asymptotic projection of the Calabi–Yau manifold manifesting itself in Anti-de Sitter space.
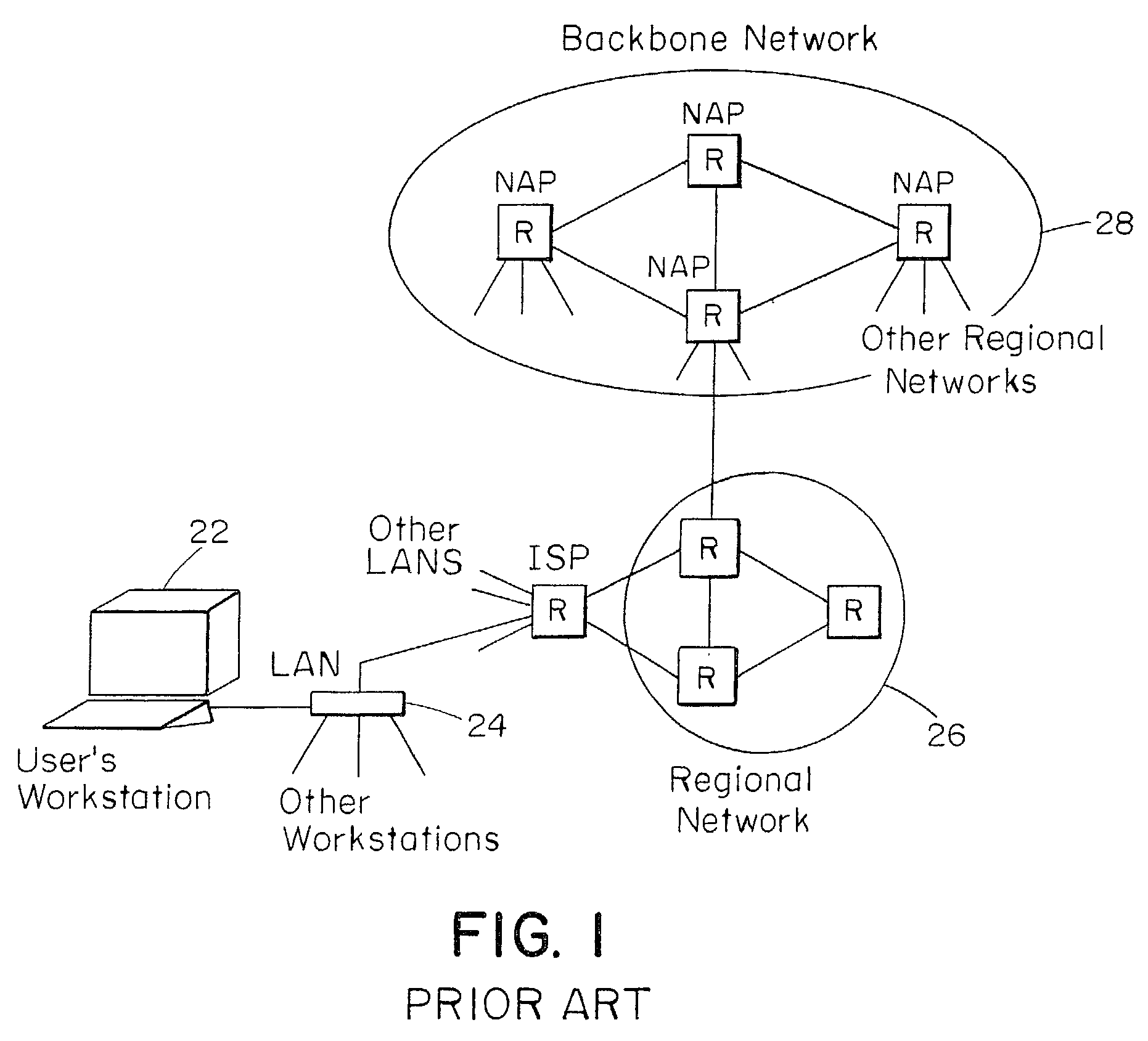
Internet switch router
InactiveUS20070140240A1High bandwidthImprove scalabilityTime-division multiplexData switching by path configurationTTEthernetNetwork structure
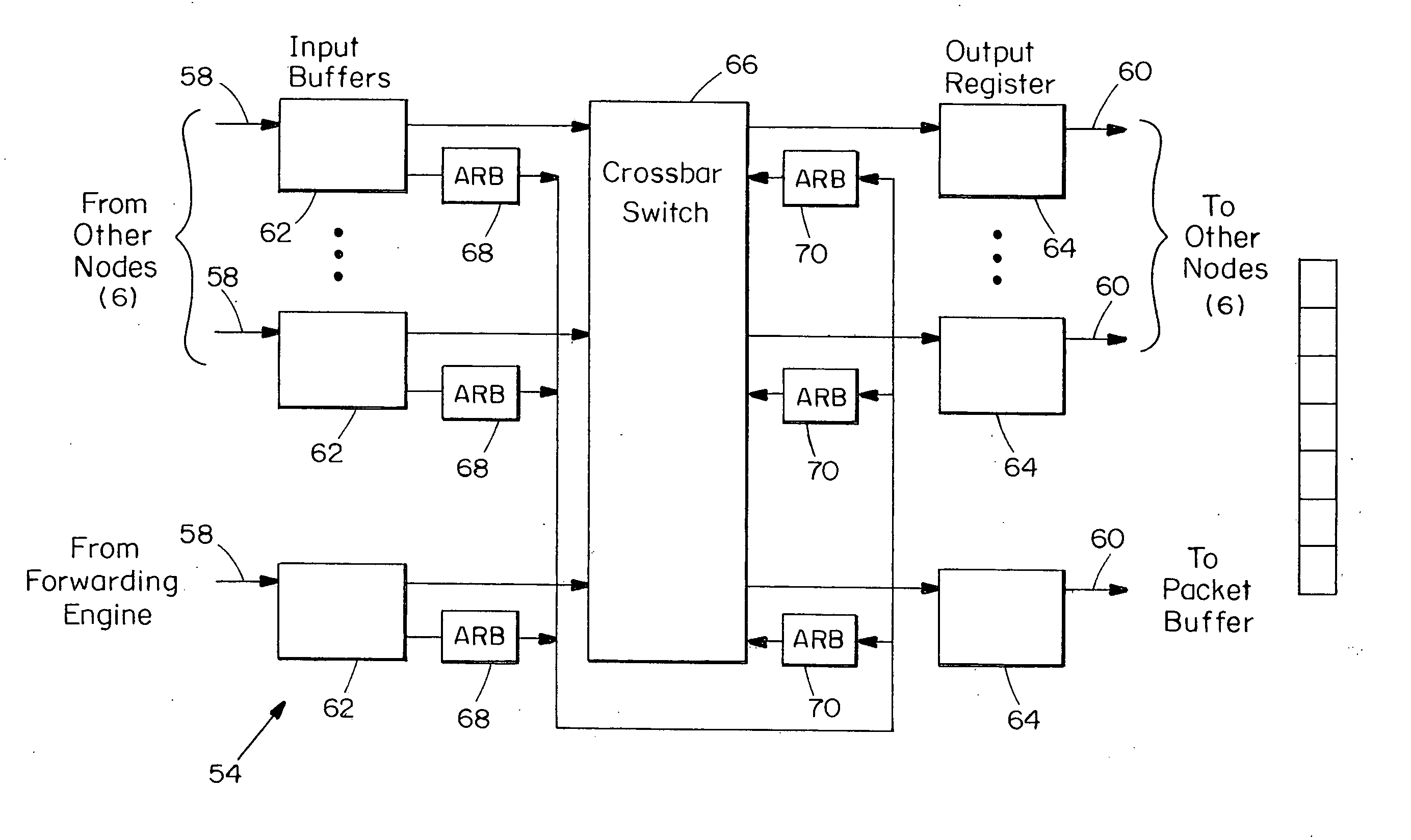
An internet router is implemented as a network fabric of fabric routers and links. The internet router receives data packets from trunk lines or other internet links and analyzes header information in the data packets to route the data packets to output internet links. The line interface also analyzes the header to define a fabric path through the router fabric. The internet packets are broken into flits which are transferred through the router according to a wormhole routing protocol. Flits are stored in fabric routers at storage locations assigned to virtual channels corresponding to destination internet links. The virtual channels and links within the fabric define virtual networks in which congestion in one virtual network is substantially nonblocking to data flow through other virtual networks. Arbitration is performed at each fabric router to assign packets to virtual channels and to assign virtual channels to output fabric links. A virtual channel is enabled for possible assignment to an output fabric link upon receipt of an indication that an input buffer is available at the next fabric router of the path.
Owner:FUTUREWEI TECH INC
Method for optimizing acid injection rate in carbonate acidizing process
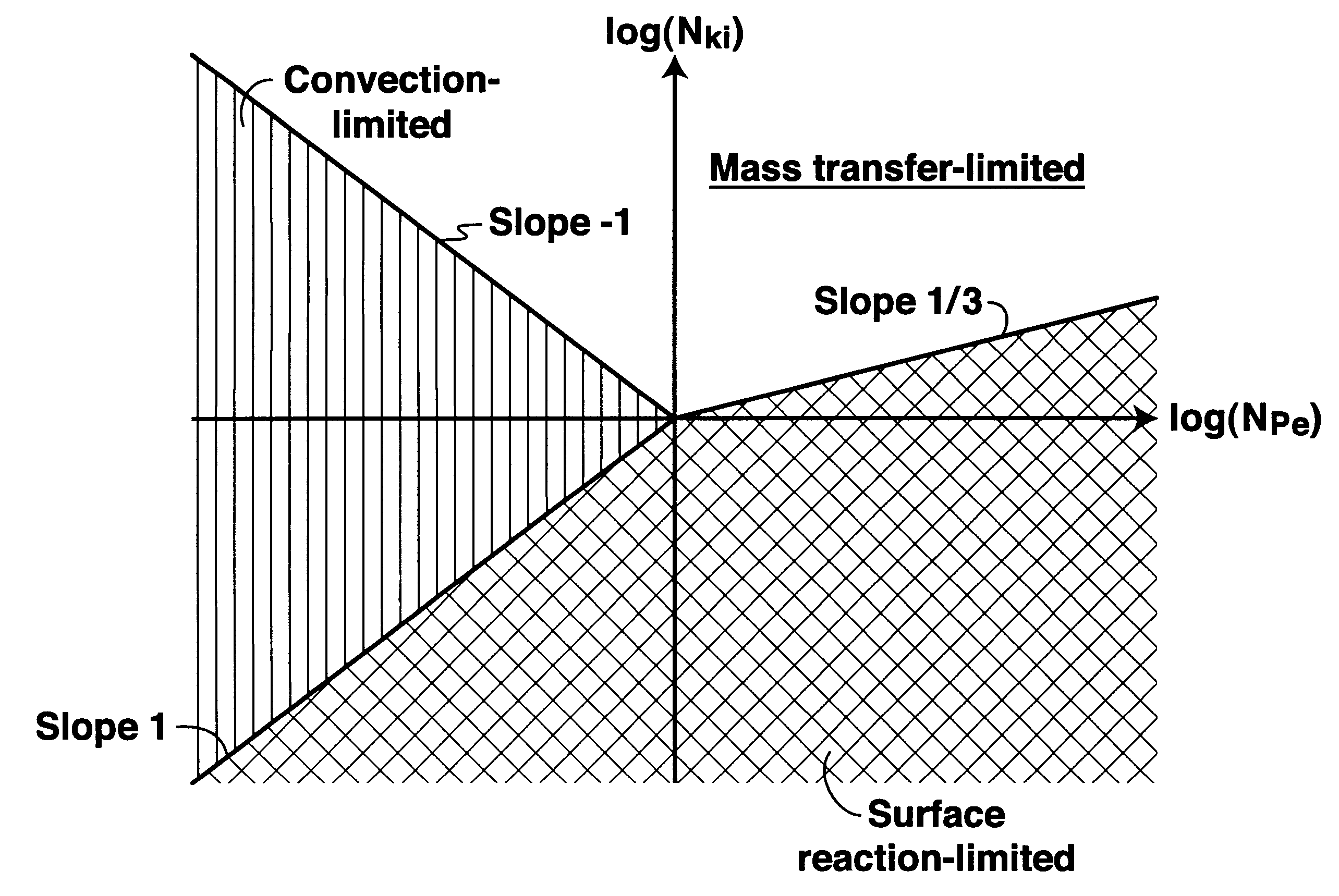
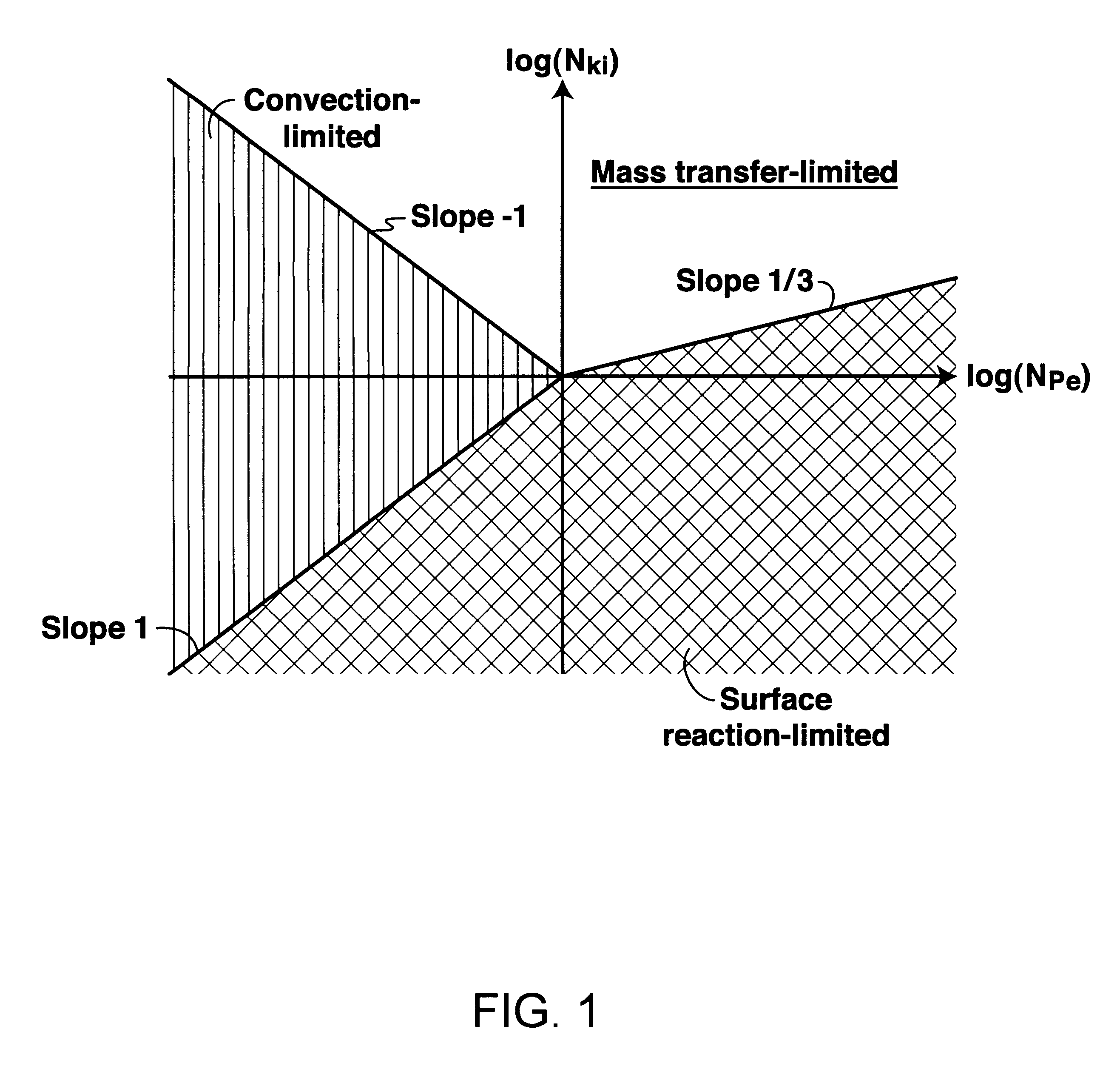
A method for optimizing the rate at which a given acid should be injected into a carbonate-containing rock formation during an acid injection process. The first step of the method calculates the Damkohler numbers for regimes in which kinematic force, diffusion rate and reaction rate control. The Damkohler numbers are then used to calculate the rate of growth of wormholes as a function of flux, taking into account compact dissolution, wormholing, and uniform dissolution. The calculated function is used to calculate an optimum flux for the formation. The optimum flux is then used to calculate an optimum injection rate at a given point in the acid injection process.
Owner:MOBIL OIL CORP
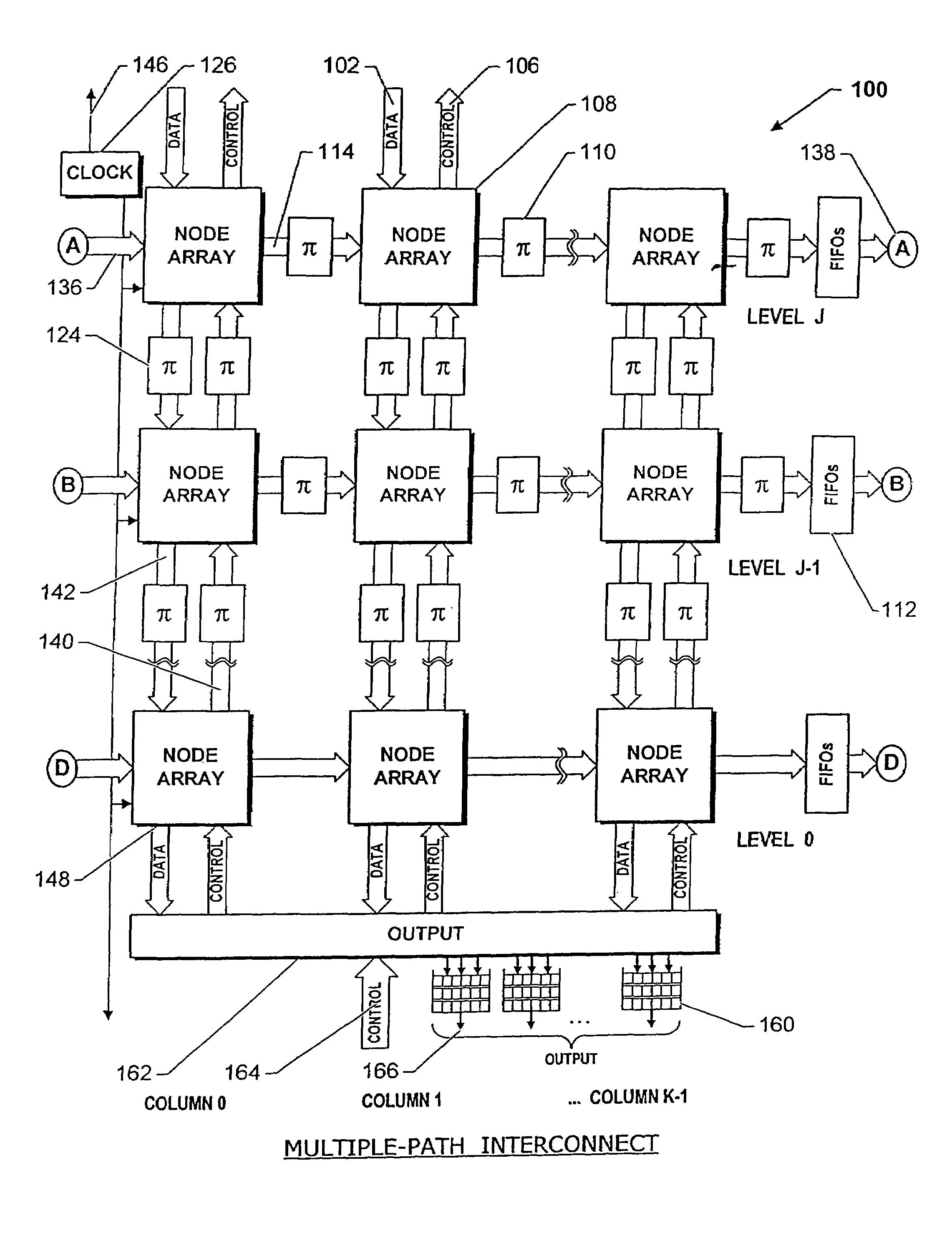
Scaleable low-latency switch for usage in an interconnect structure
InactiveUS6289021B1High bandwidthLower latencyData switching by path configurationCommunications systemLatency (engineering)
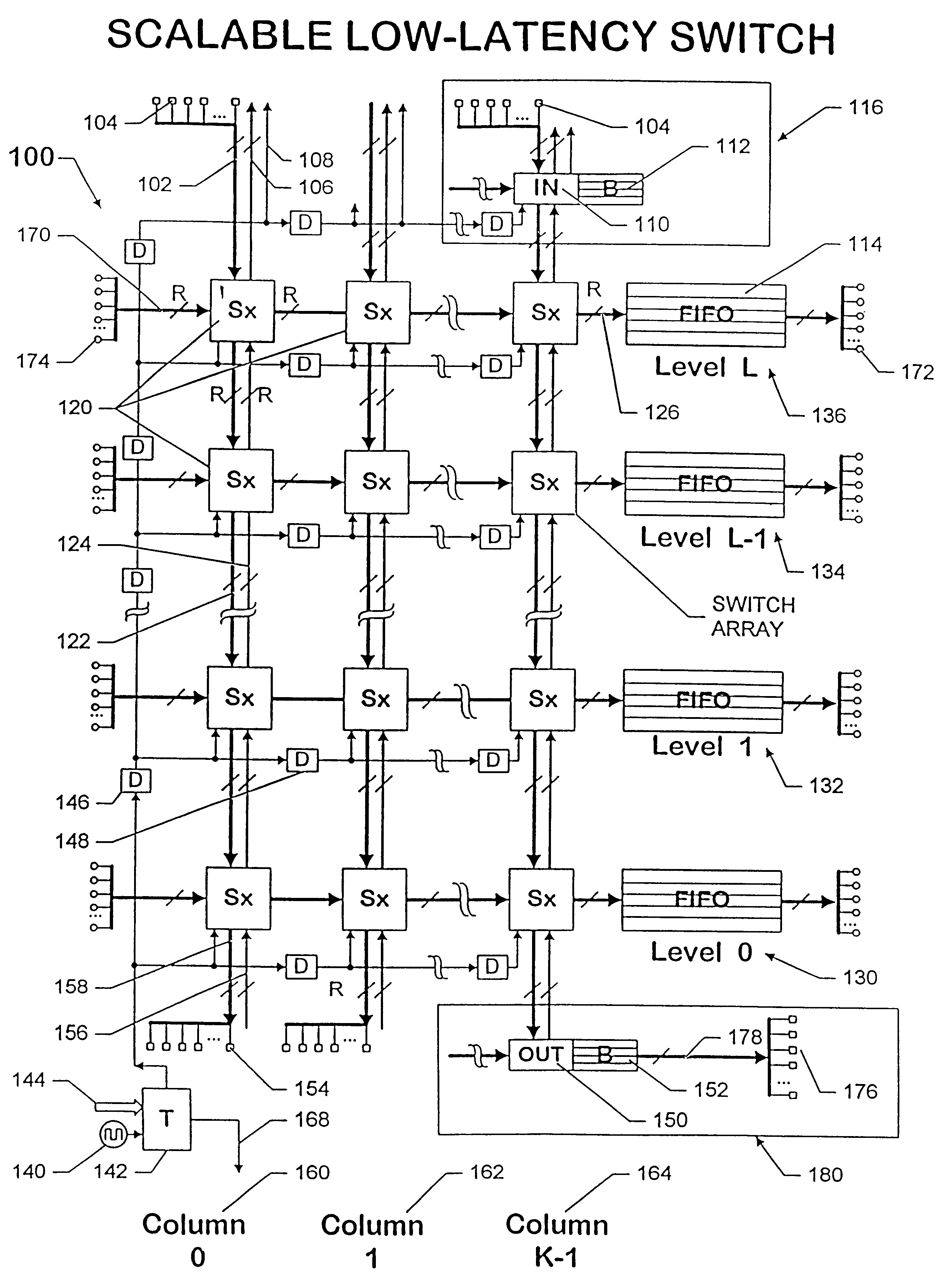
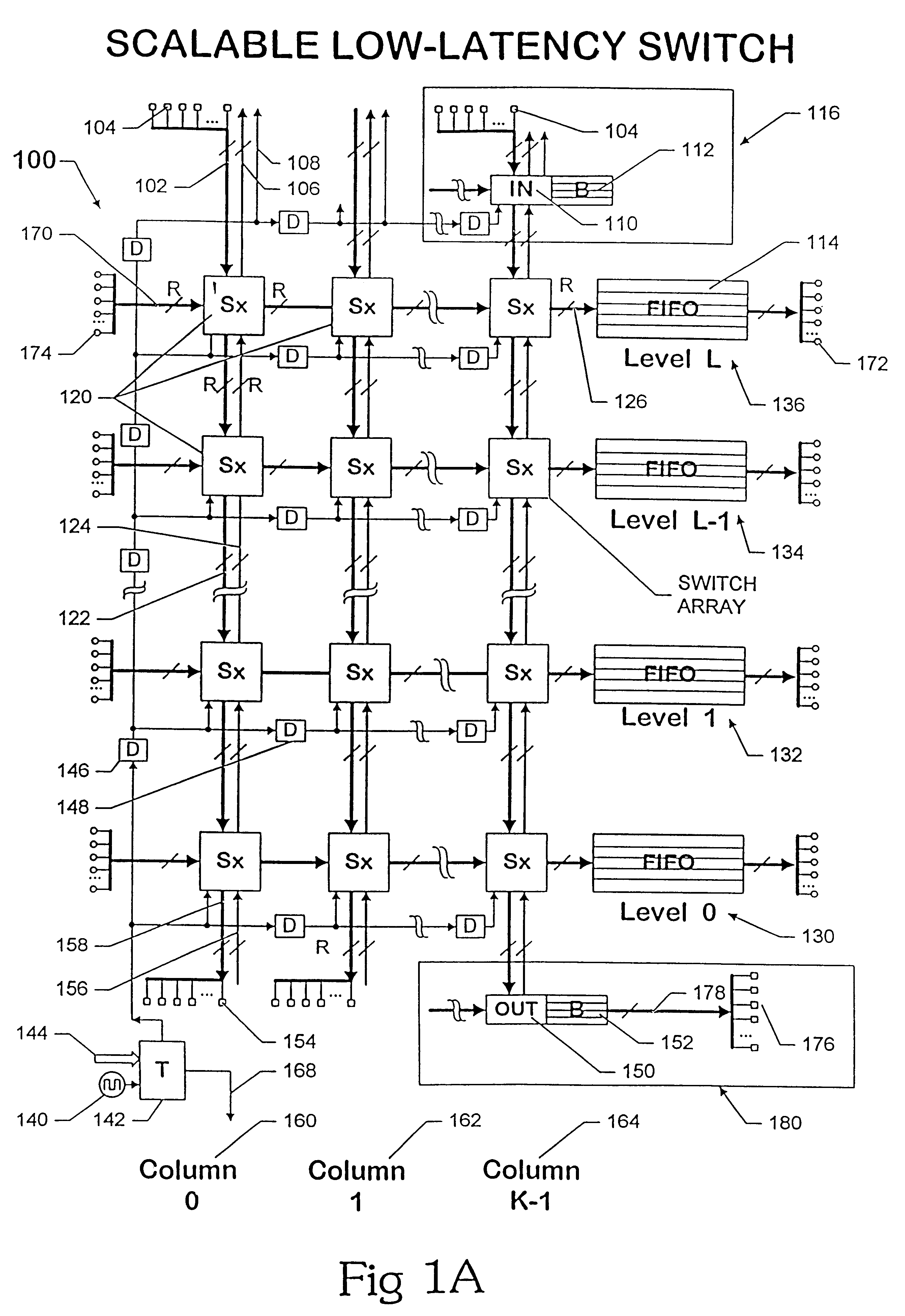
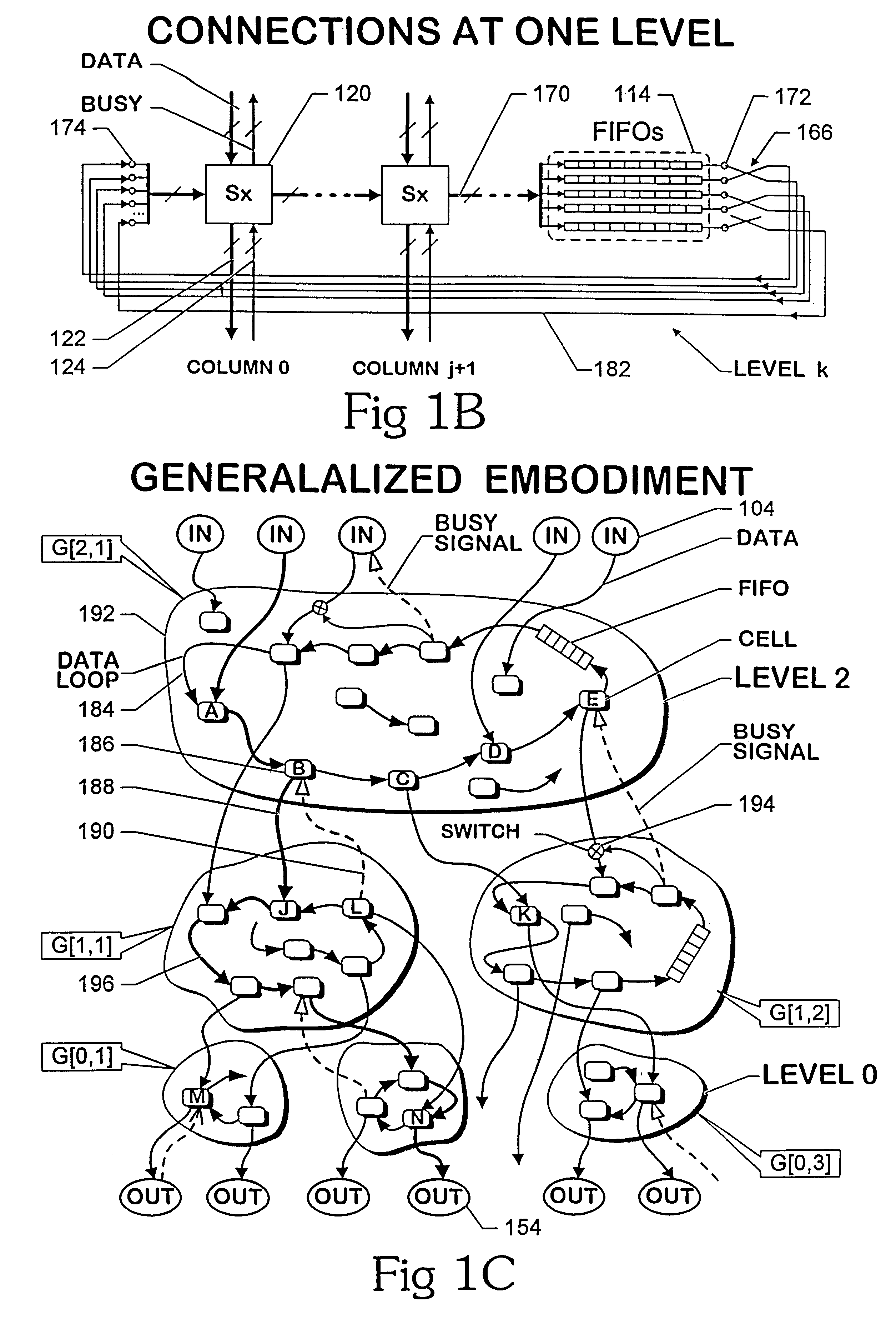
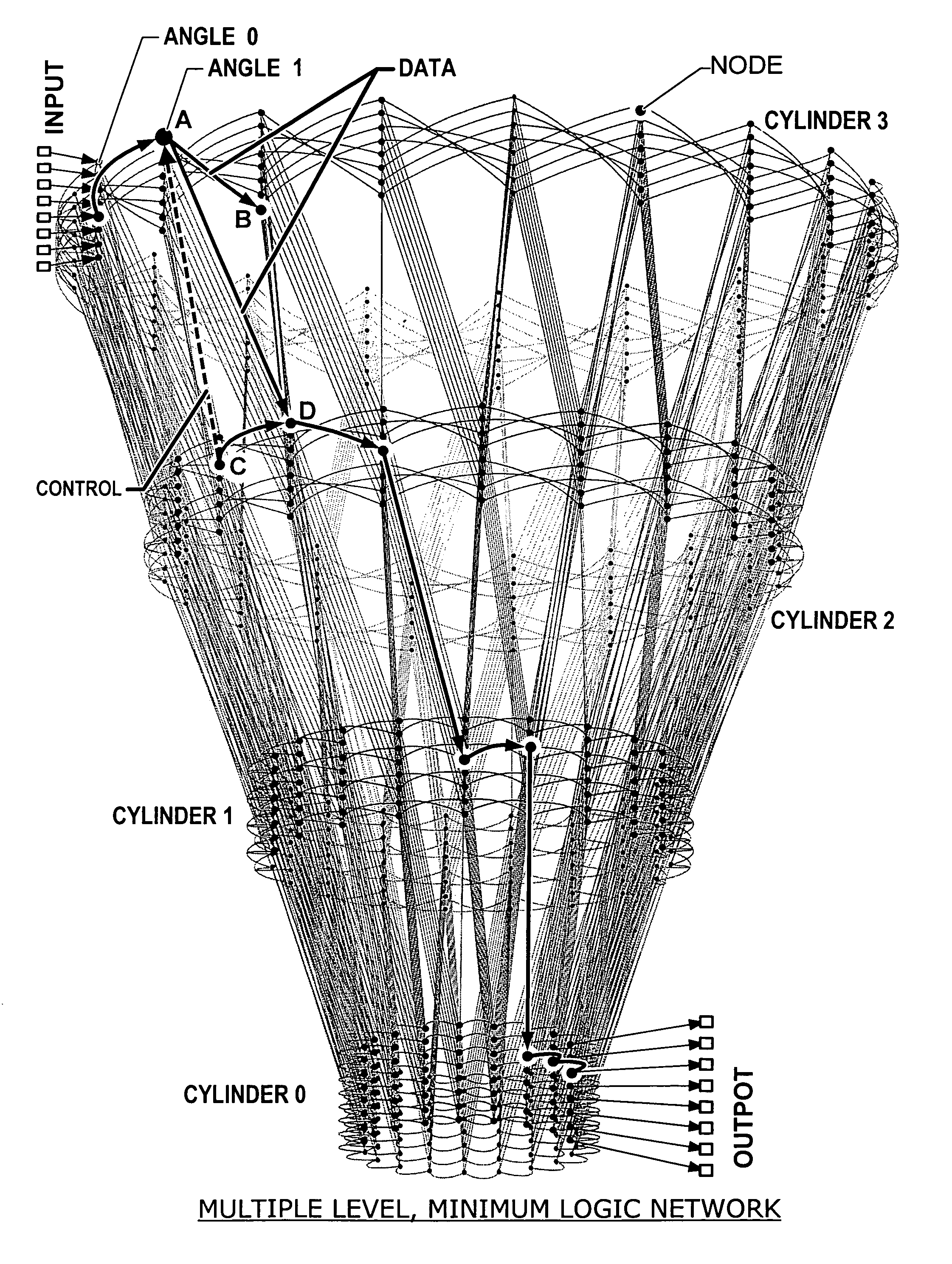
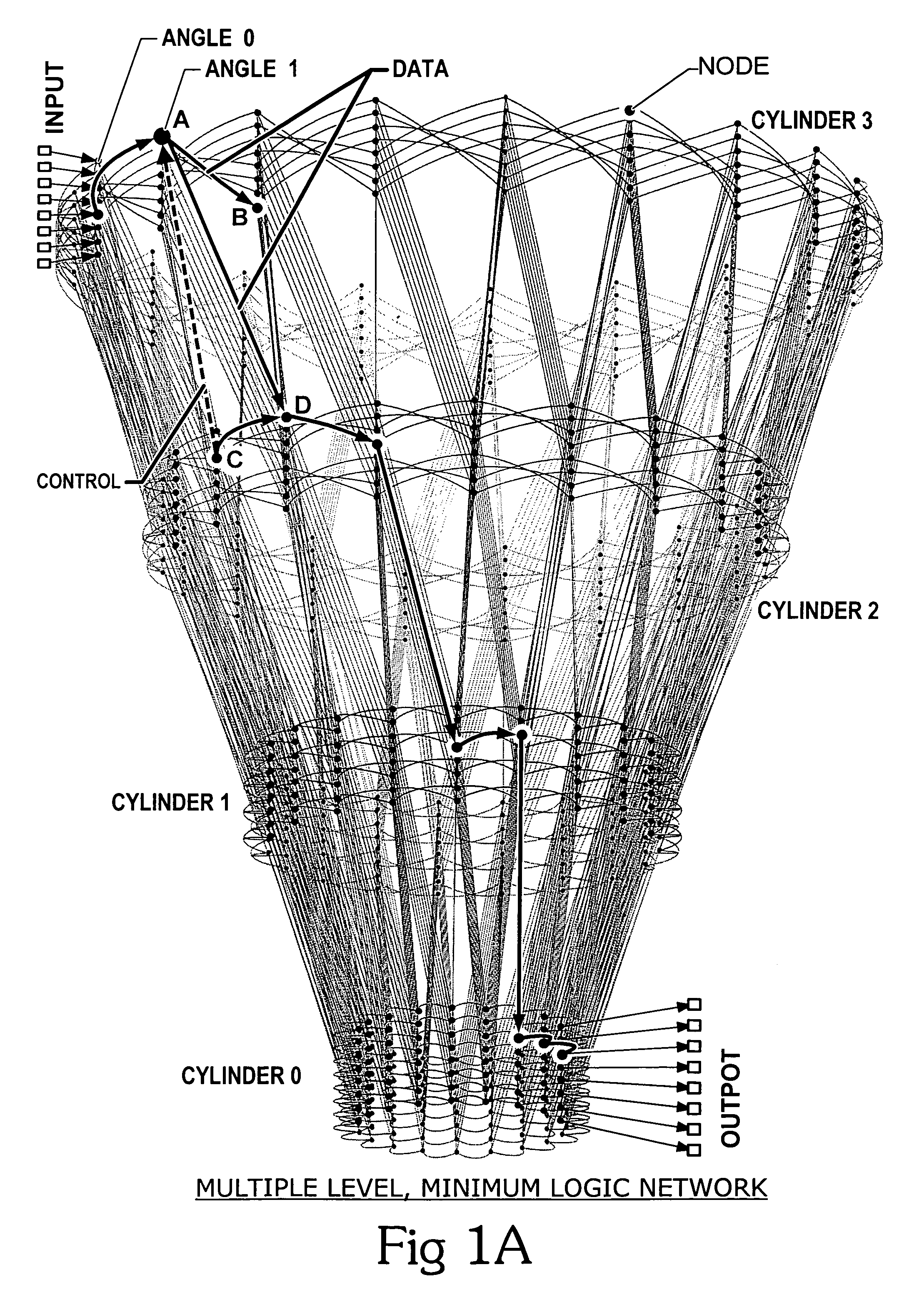
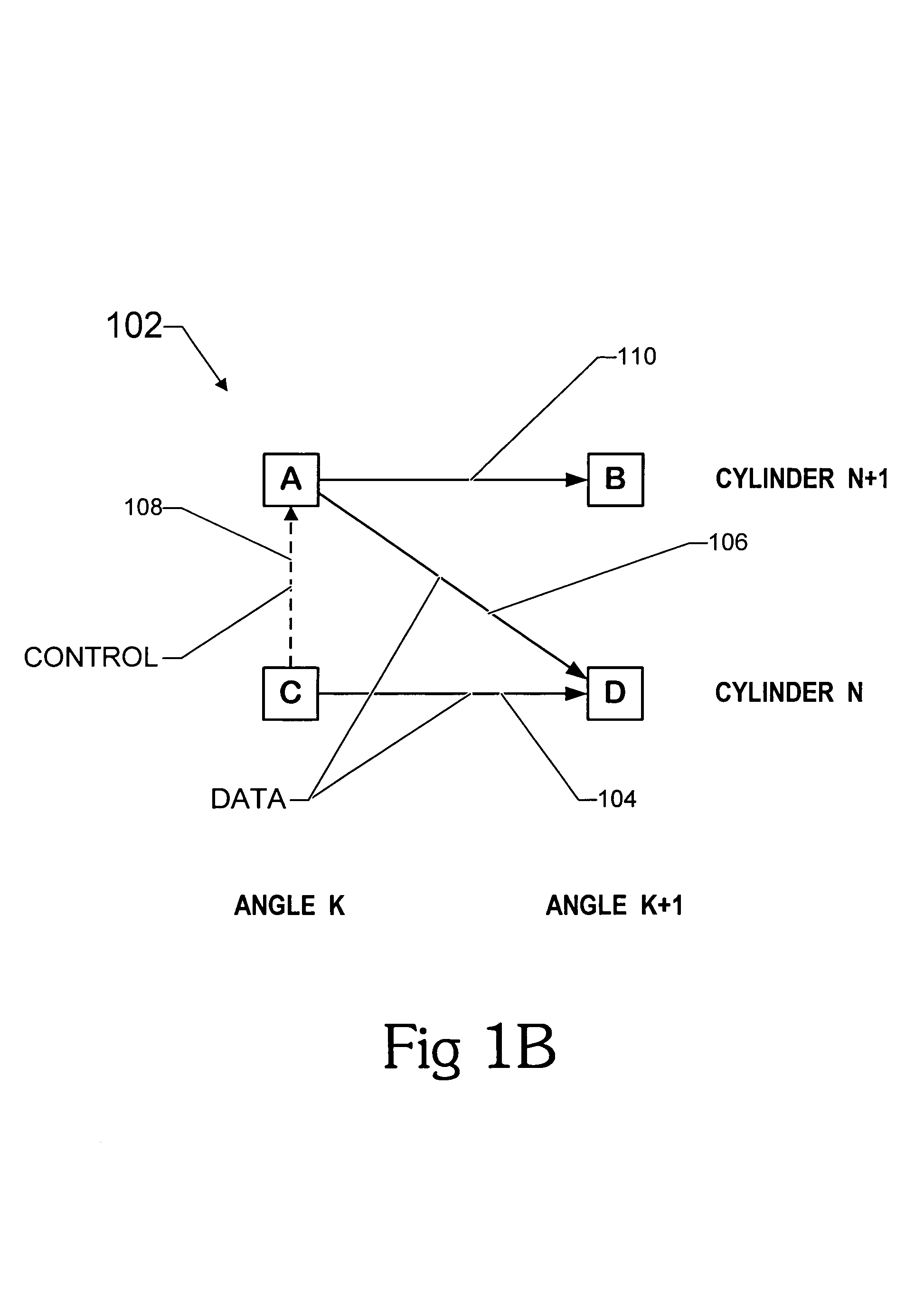
A scalable low-latency switch extends the functionality of a multiple level minimum logic interconnect structure for usage in computers of all types, networks and communication systems. The multiple level minimum logic interconnect structure employs a data flow technique based on timing and positioning of messages moving through the structure. The scalable low-latency switch is distributed throughout multiple nodes in the structure so that a supervisory controller providing a global control function and complex logic structures are avoided while the interconnect structure operates as a "deflection" or "hot potato" system in which processing and storage overhead at each node is reduced. The interconnect structure using the scalable low-latency switch employs a method of achieving wormhole routing through an integrated circuit chip by a novel procedure for inserting messages into the chip. Rather than simultaneously inserting a message into each unblocked node on the outer cylinder at every angle, messages are inserted simultaneously into two columns A and B only if an entire message fits between A and B. Messages are inserted into column 0 at time 0. Messages are inserted into column 1 at time t0+tC, where time tCis the time for a first bit of a message to move from column 0 to column 1 on the top level. Messages are inserted into column 2 at time t0+2tC, and so forth. The strategy prevents the first bit of one message from colliding with an interior bit of another message already in the switch. Contention between entire messages is addressed by resolving the contention between the first bit only so that messages wormhole through many cells.
Owner:HEWLETT PACKARD CO +1
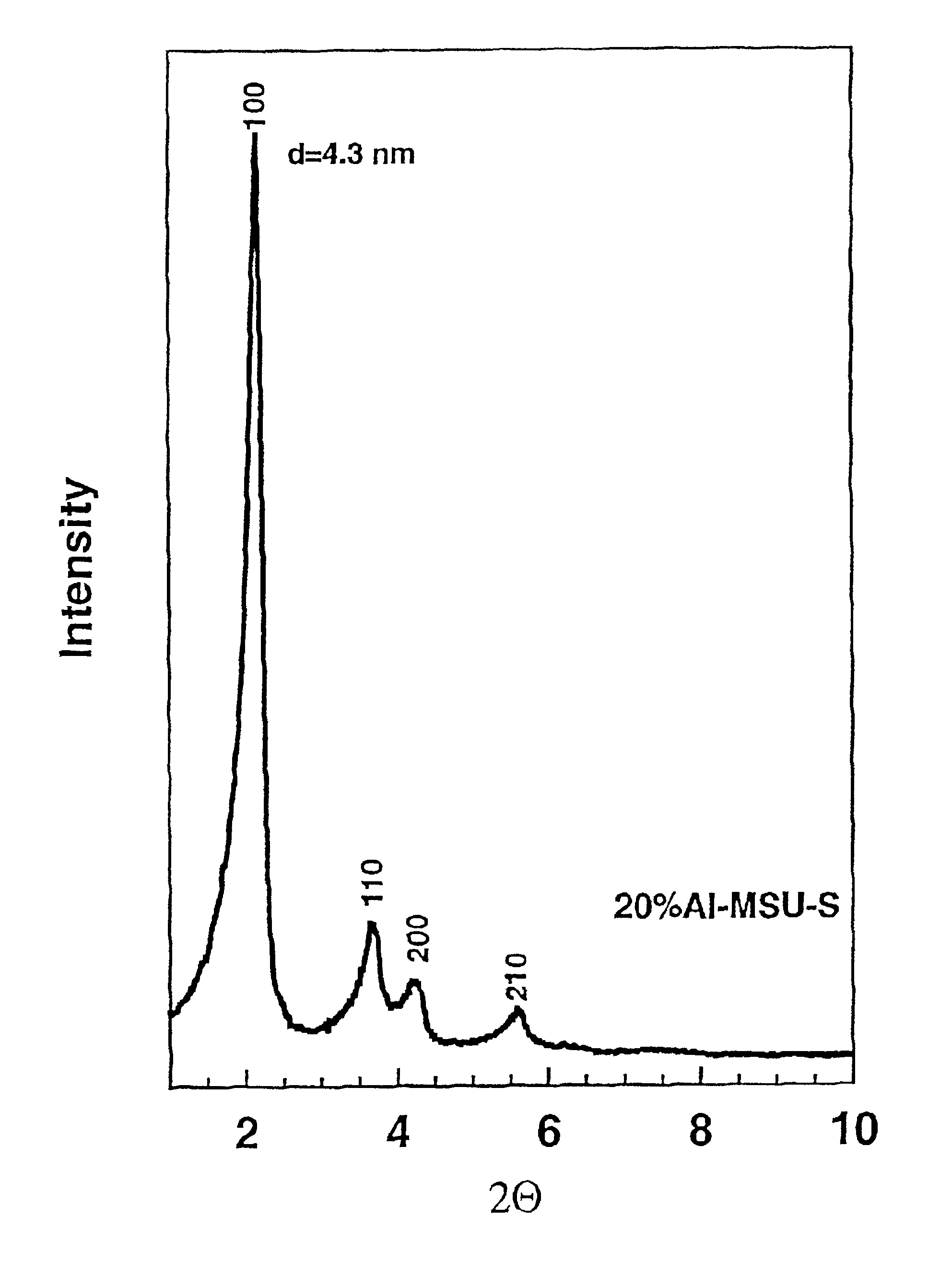
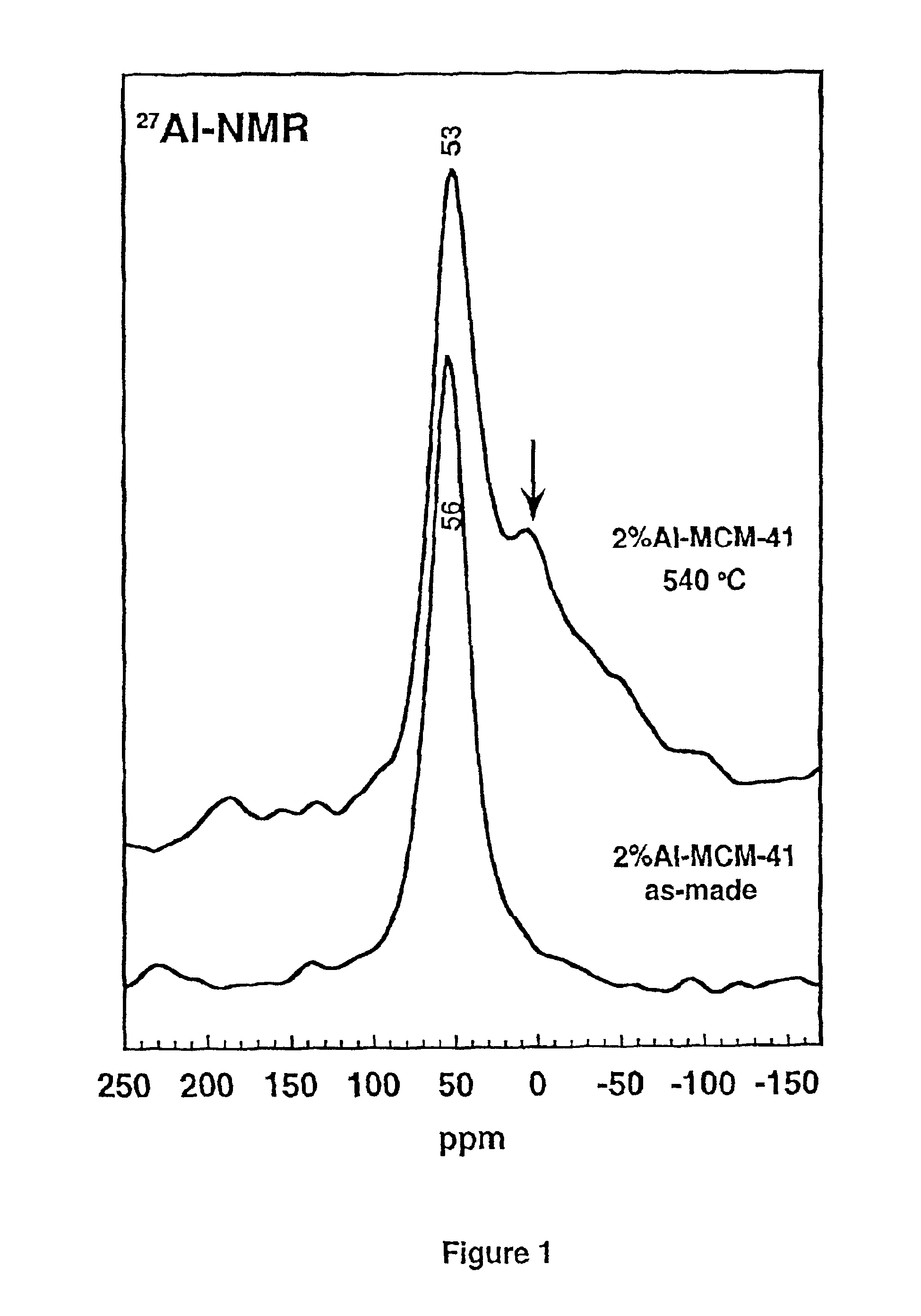
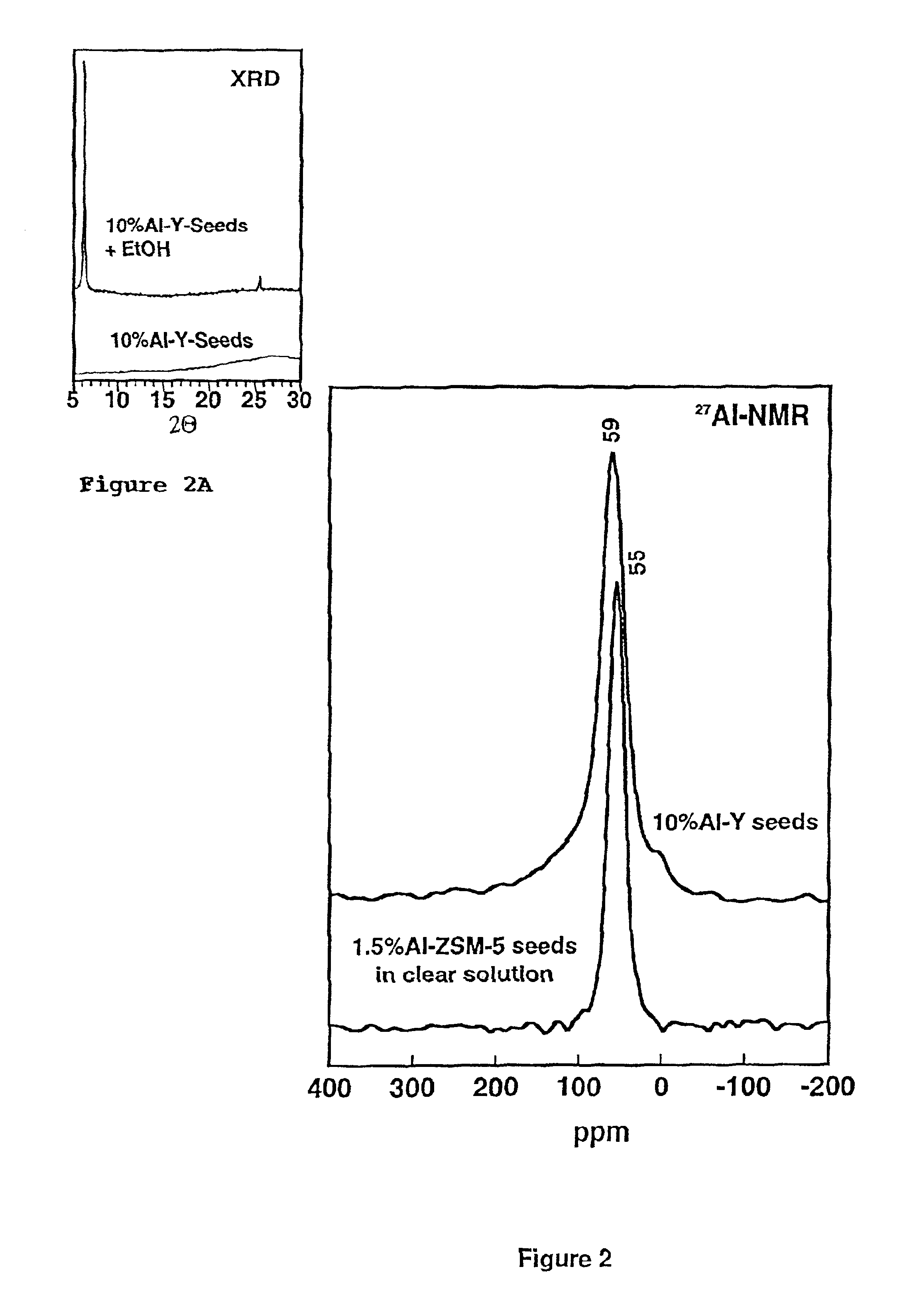
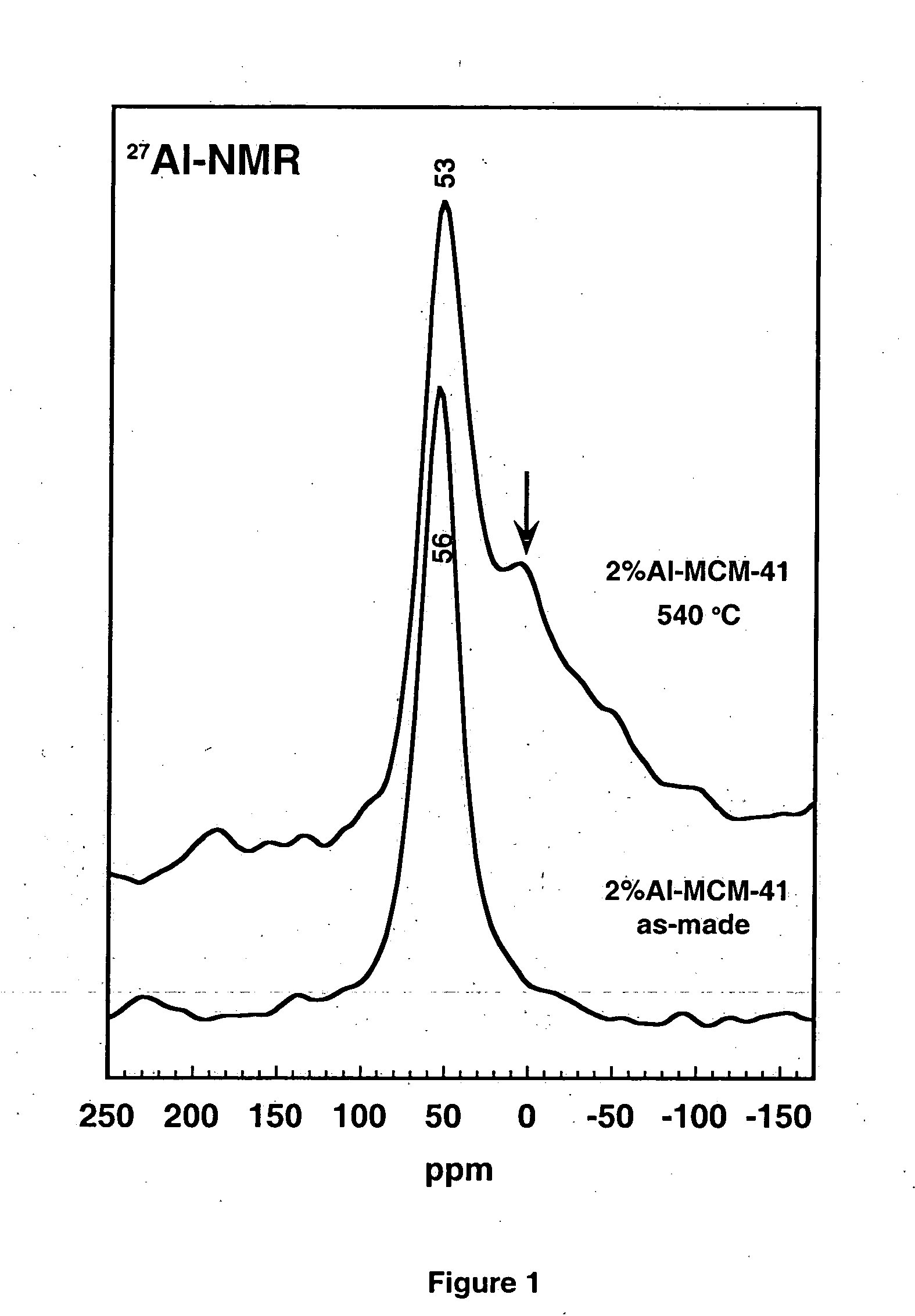
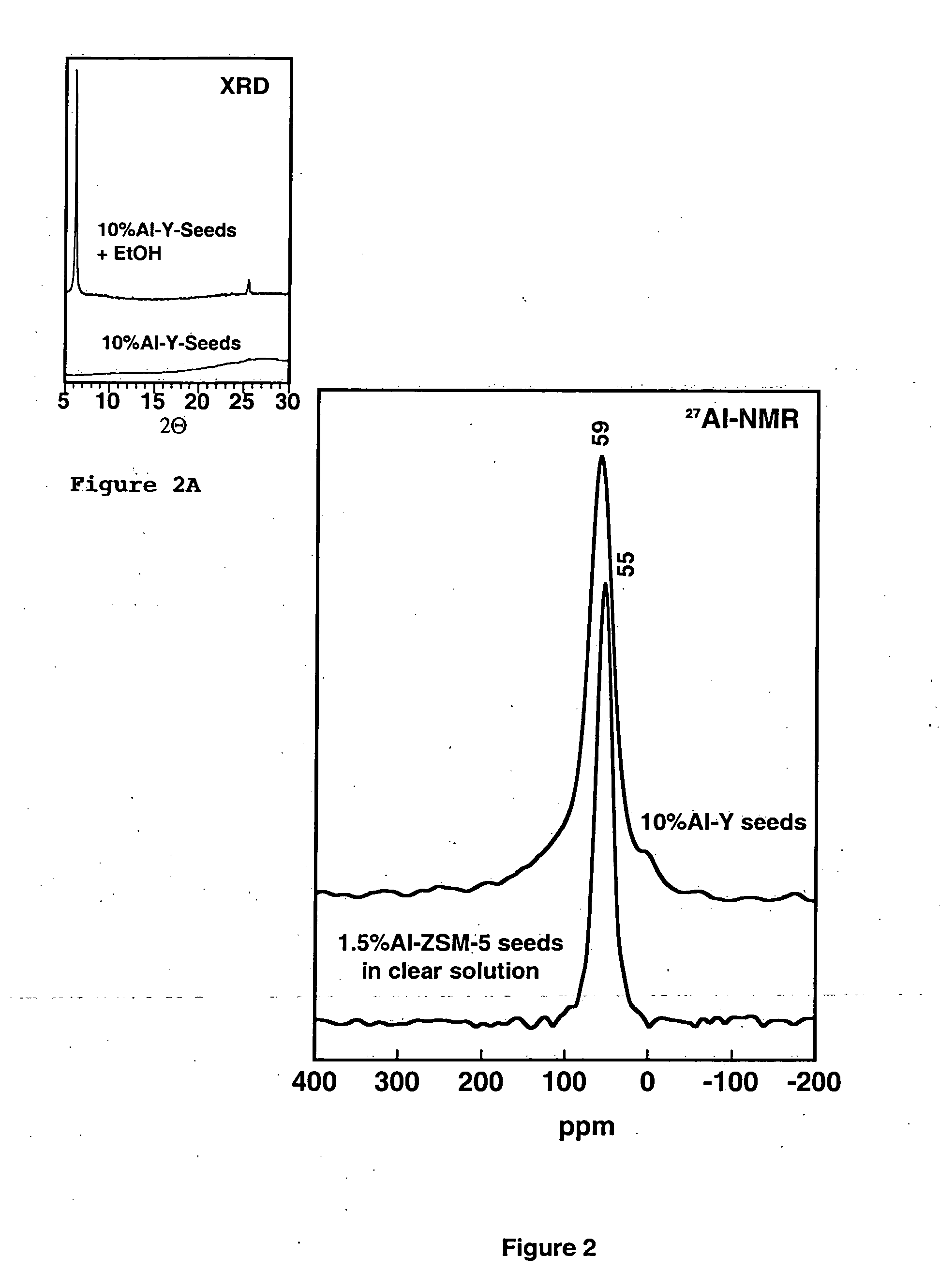
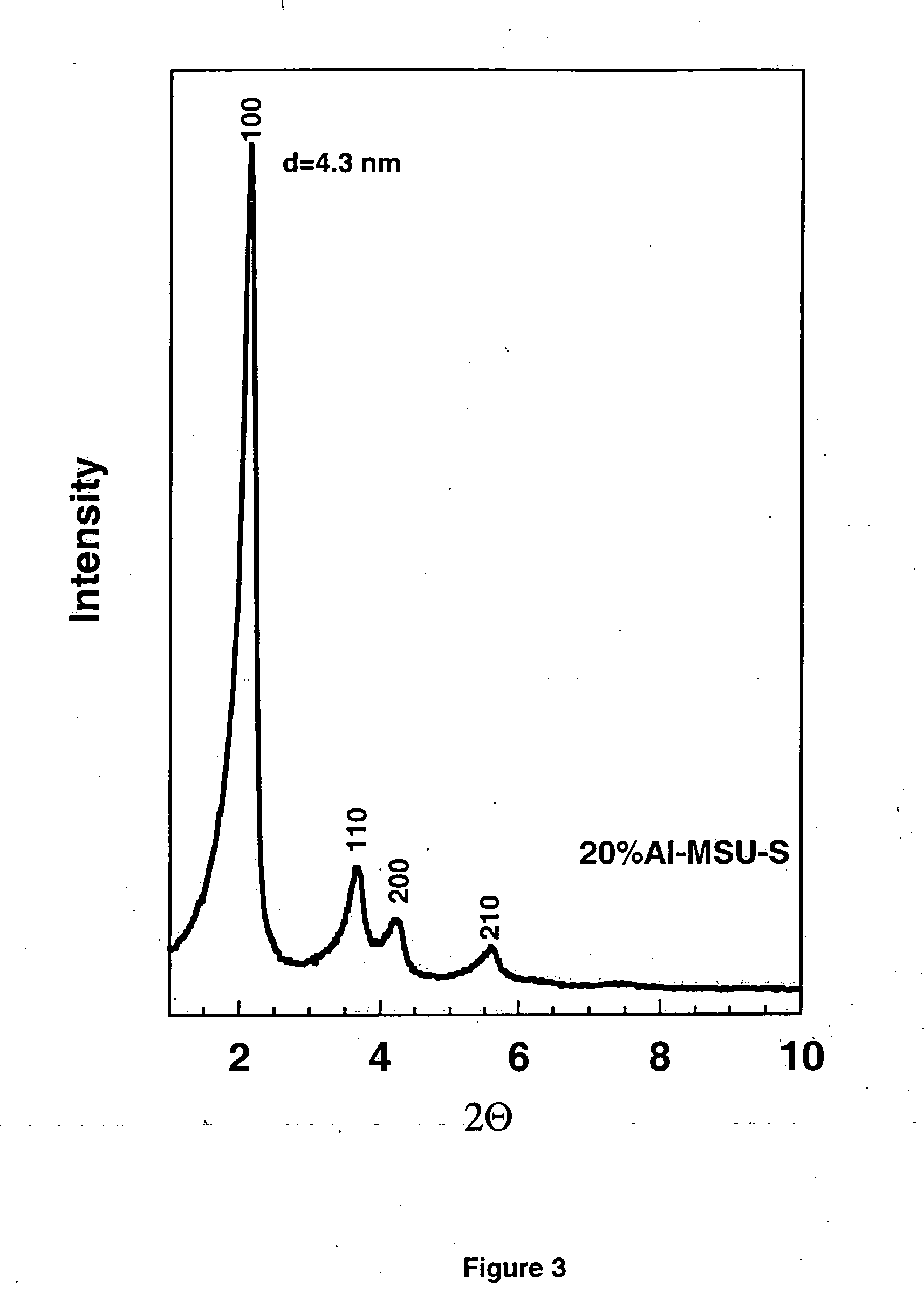
Ultrastable porous aluminosilicate structures and compositions derived therefrom
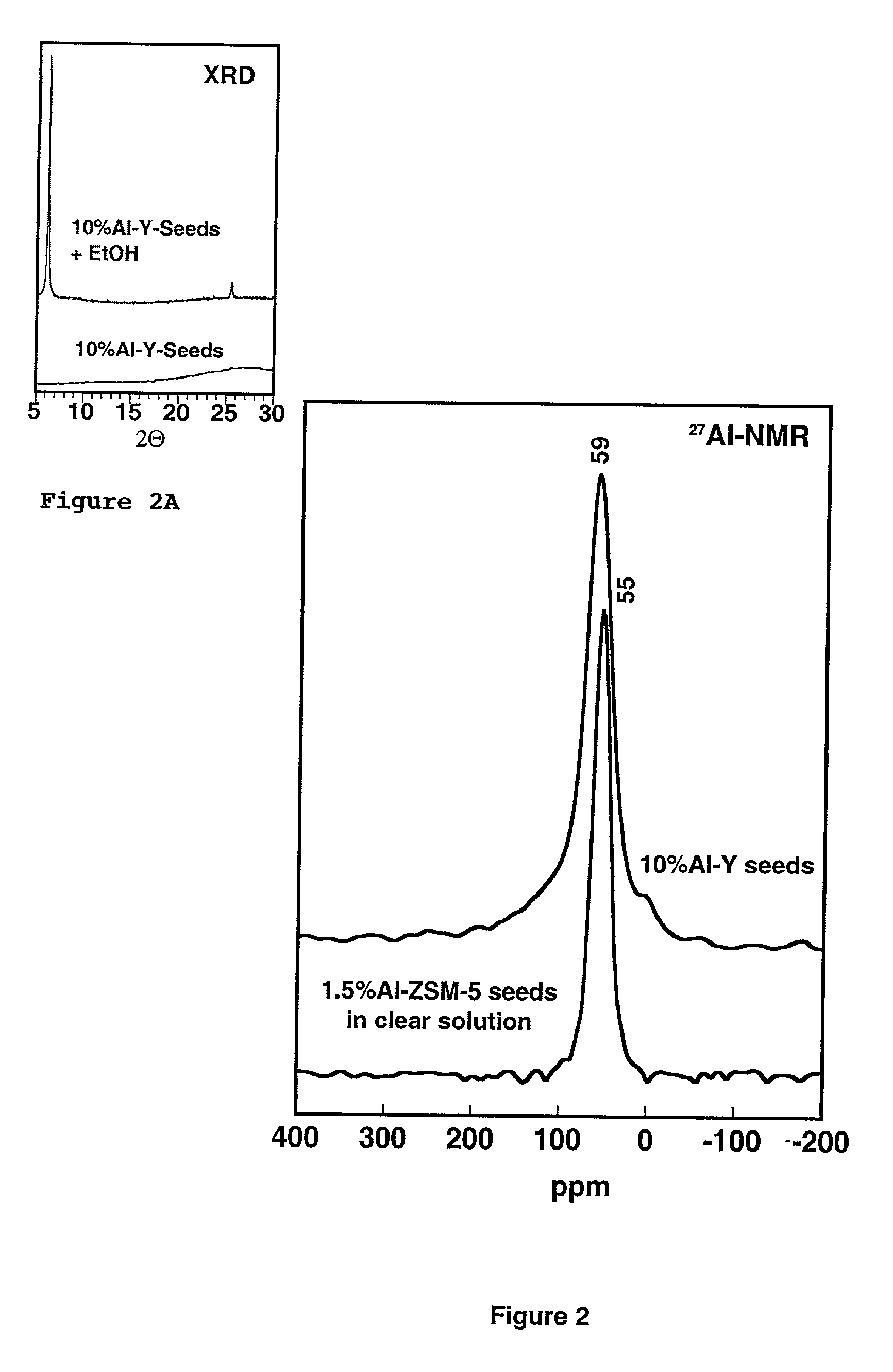
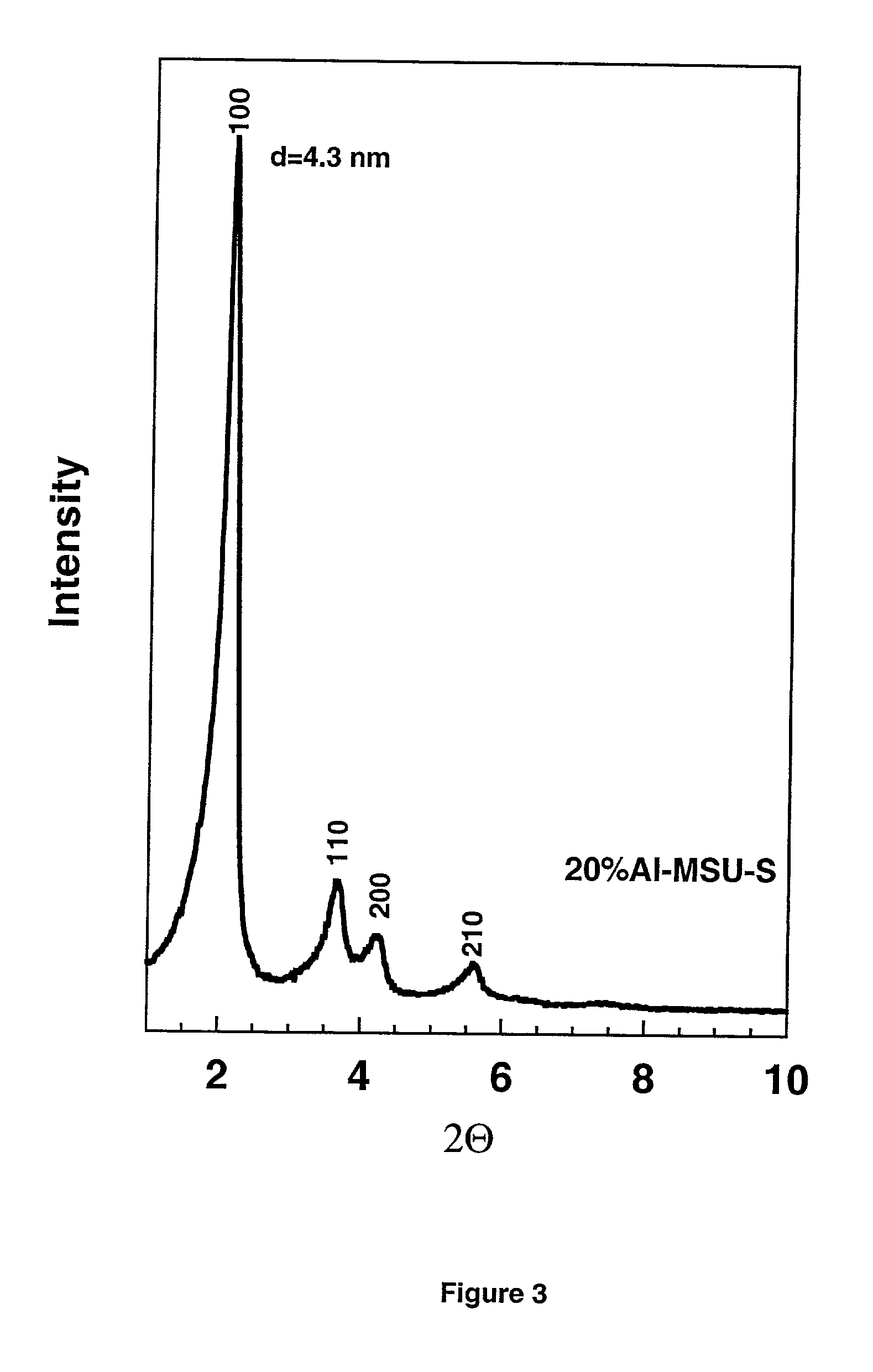
Porous hexagonal, cubic, lamellar, wormhole, or cellular foam aluminosilicates, gallosilicates and titanosilicates derived from protozeolitic seeds or zeolite fragments using an organic porogen directing agent are described. The porous aluminosilicates optionally also can contain zeolite crystals depending upon the aging of the protozeolitic seeds. The silicon and aluminum, gallium or titanium centers in the structures are stable so that the framework of the structure does not collapse when heated in the presence of water or water vapor (steam). The steam stable compositions can be used as catalysts for hydrocarbon conversions, including the fluidized bed catalytic cracking and the hydrocracking of petroleum oils, and other reactions of organic compounds.
Owner:BOARD OF TRUSTEES OPERATING MICHIGAN STATE UNIV
Propped fracture with high effective surface area
InactiveUS7114567B2Increase the effective surface areaFluid removalFlushingEffective surface areaWormhole
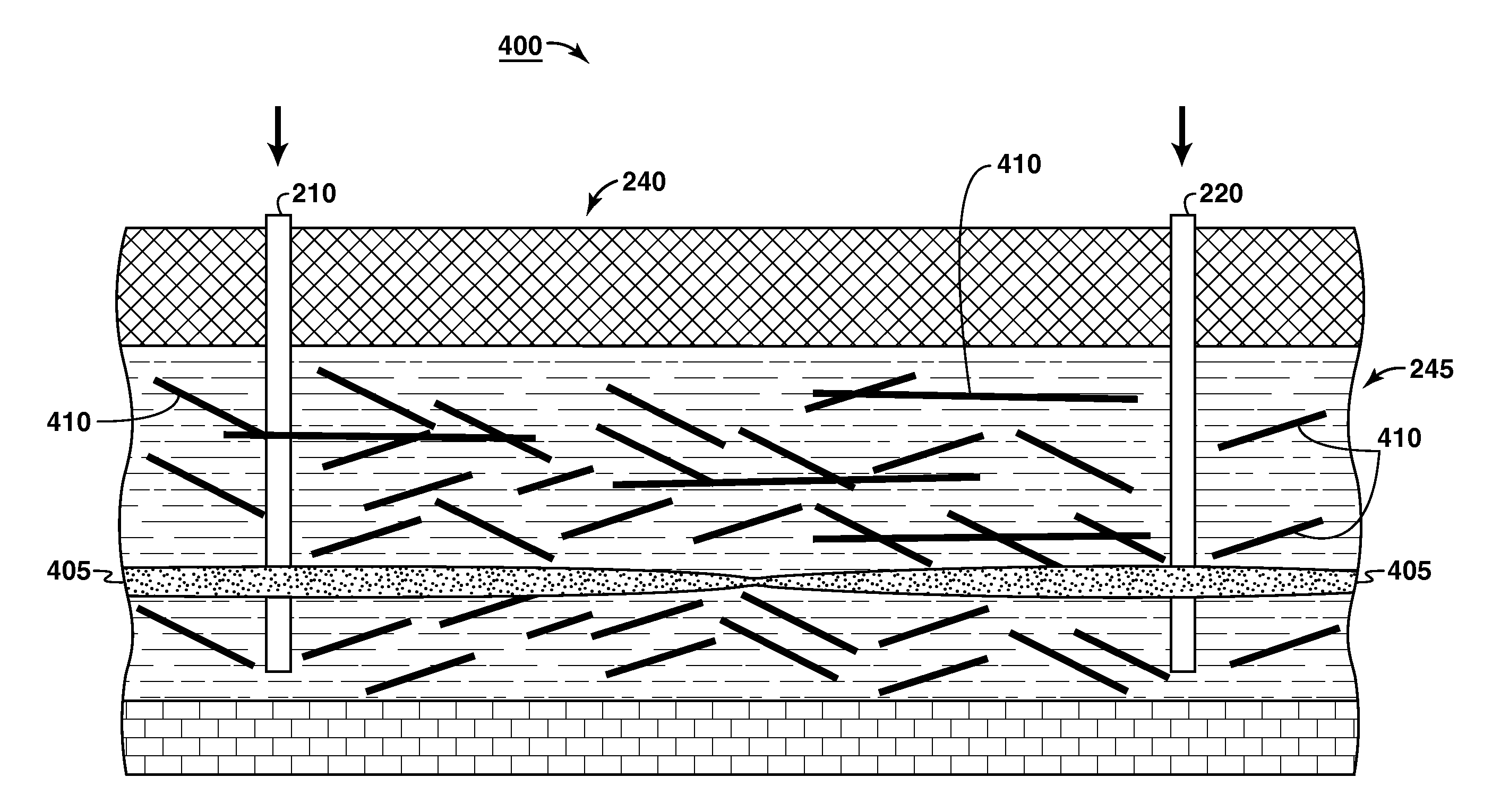
Propped fractures in formations from which fluids are produced are described that have wormholes extending out into the formations from the faces of the fractures at locations distant from boreholes. Methods are given for creating such propped fractures having wormholes in which either a closed propped fracture is formed and then the wormholes are formed, or the entire fracture and channel system is formed before the closure occurs.
Owner:SCHLUMBERGER TECH CORP
Strengthening near well bore subterranean formations
The present invention relates to improved methods for completing well bores along producing zones and, more particularly, to methods for strengthening near well bore subterranean formations. Some embodiments of the present invention provide a method of strengthening the near well bore region of a subterranean formation comprising the steps of isolating a zone of interest along a well bore; either hydrajetting a slot in the zone of interest or acidizing the zone of interest to create wormholes; filling the slot or wormholes with a consolidation material wherein the viscosity of the consolidation material is sufficient to enable the consolidation material to penetrate a distance into the formation; and, allowing the consolidation material to substantially cure.
Owner:HALLIBURTON ENERGY SERVICES INC
Internet switch router
InactiveUS7187679B2High bandwidthImprove scalabilityData switching by path configurationAnalysis dataInternet router
An internet router is implemented as a network fabric of fabric routers and links. The internet router receives data packets from trunk lines or other internet links and analyzes header information in the data packets to route the data packets to output internet links. The line interface also analyzes the header to define a fabric path through the router fabric. The internet packets are broken into flits which are transferred through the router according to a wormhole routing protocol. Flits are stored in fabric routers at storage locations assigned to virtual channels corresponding to destination internet links. The virtual channels and links within the fabric define virtual networks in which congestion in one virtual network is substantially nonblocking to data flow through other virtual networks. Arbitration is performed at each fabric router to assign packets to virtual channels and to assign virtual channels to output fabric links. A virtual channel is enabled for possible assignment to an output fabric link upon receipt of an indication that an input buffer is available at the next fabric router of the path.
Owner:FUTUREWEI TECH INC
Ultrastable porous aluminosilicate structures
Mesoporous hexagonal, cubic, lamellar, wormhole, or cellular foam aluminosilicates, gallosilicates and titanosilicates derived from protozeolitic seeds using an ionic structure directing agent are described. The silicon and aluminum, gallium or titanium centers in the structures are stable so that the framework of the structure does not collapse when heated in the presence of water or water vapor (steam). The steam stable compositions can be used as catalysts for hydrocarbon conversions, including the fluidized bed catalytic cracking and the hydrocracking of petroleum oils, and other reactions of organic compounds.
Owner:BOARD OF TRUSTEES OPERATING MICHIGAN STATE UNIV
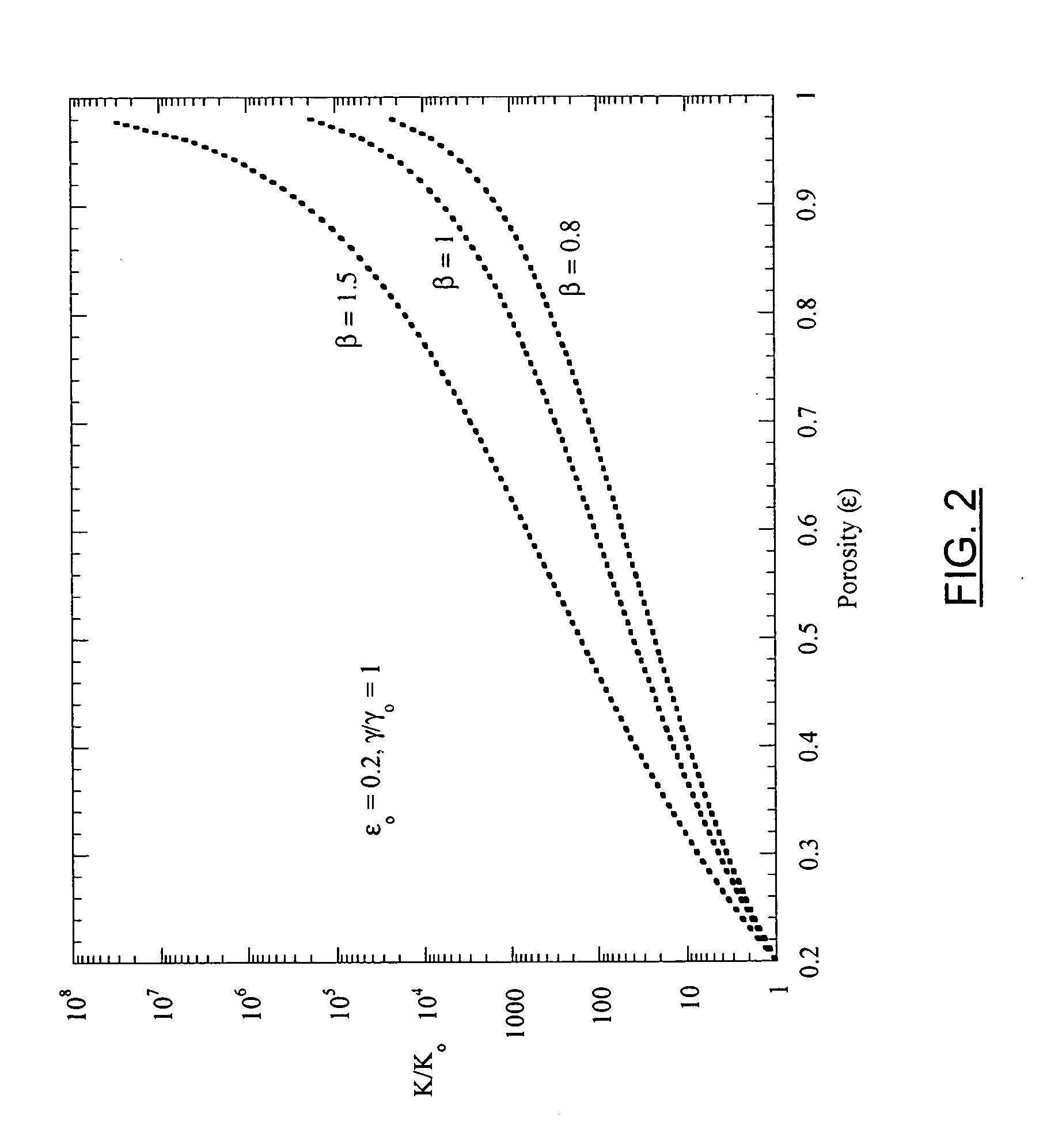
Modeling, simulation and comparison of models for wormhole formation during matrix stimulation of carbonates
InactiveUS20060184346A1Enhanced recovery of hydrocarbonPromote recoveryFluid removalSealing/packingDesign matrixModel method
Owner:SCHLUMBERGER TECH CORP
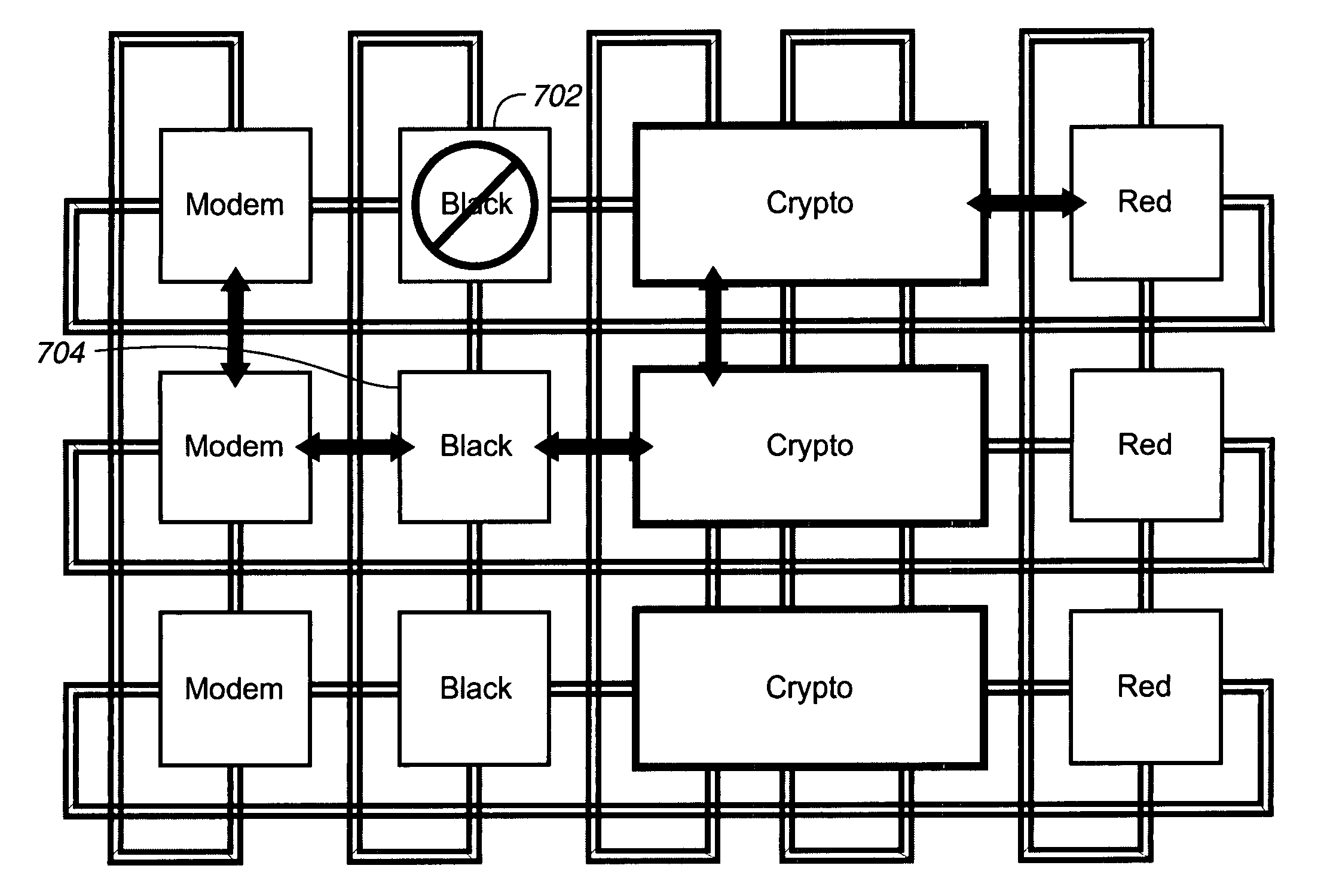
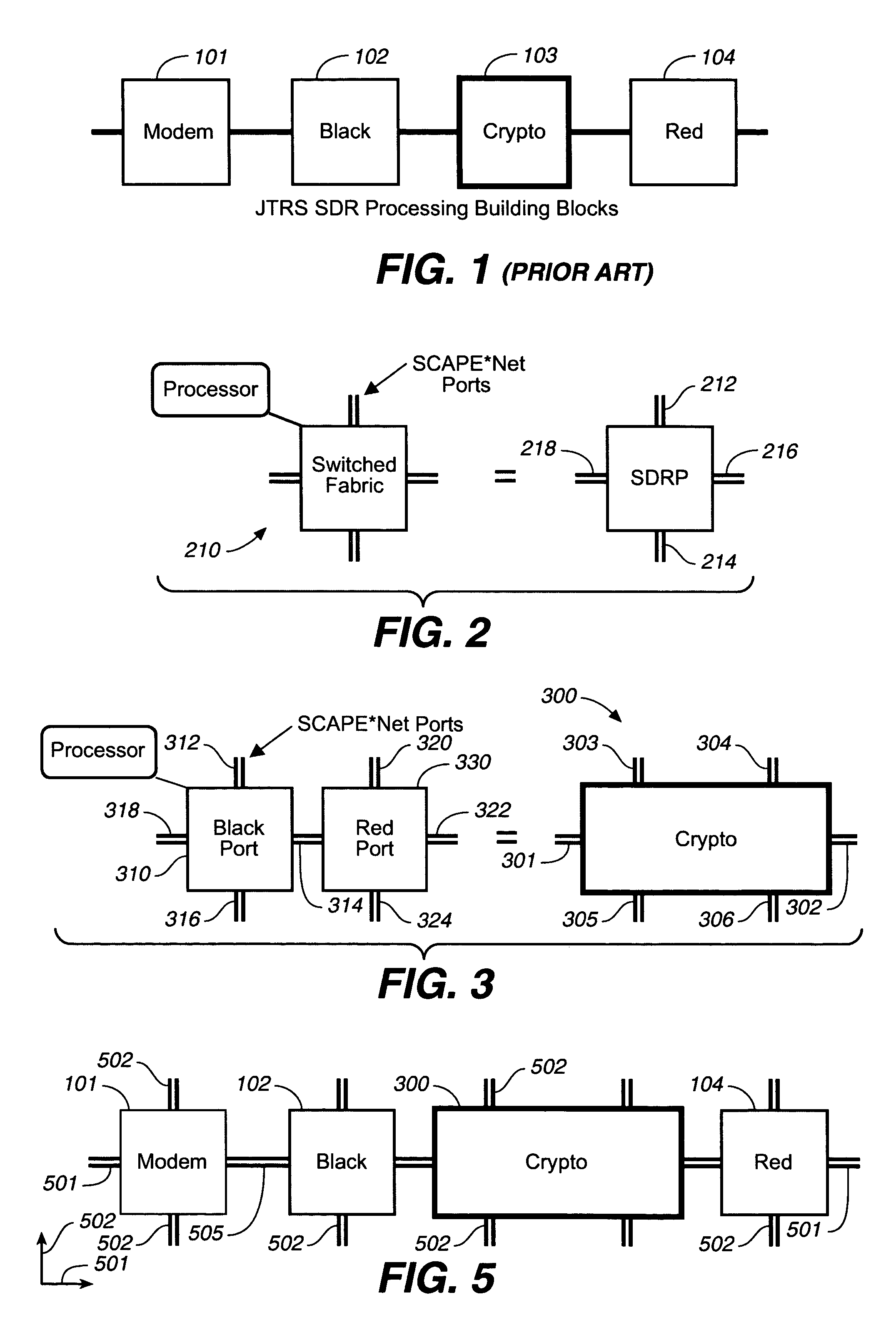
Software defined radio computing architecture
ActiveUS7509141B1Multiplex system selection arrangementsEnergy efficient ICTSoftware define radioDifferential signaling
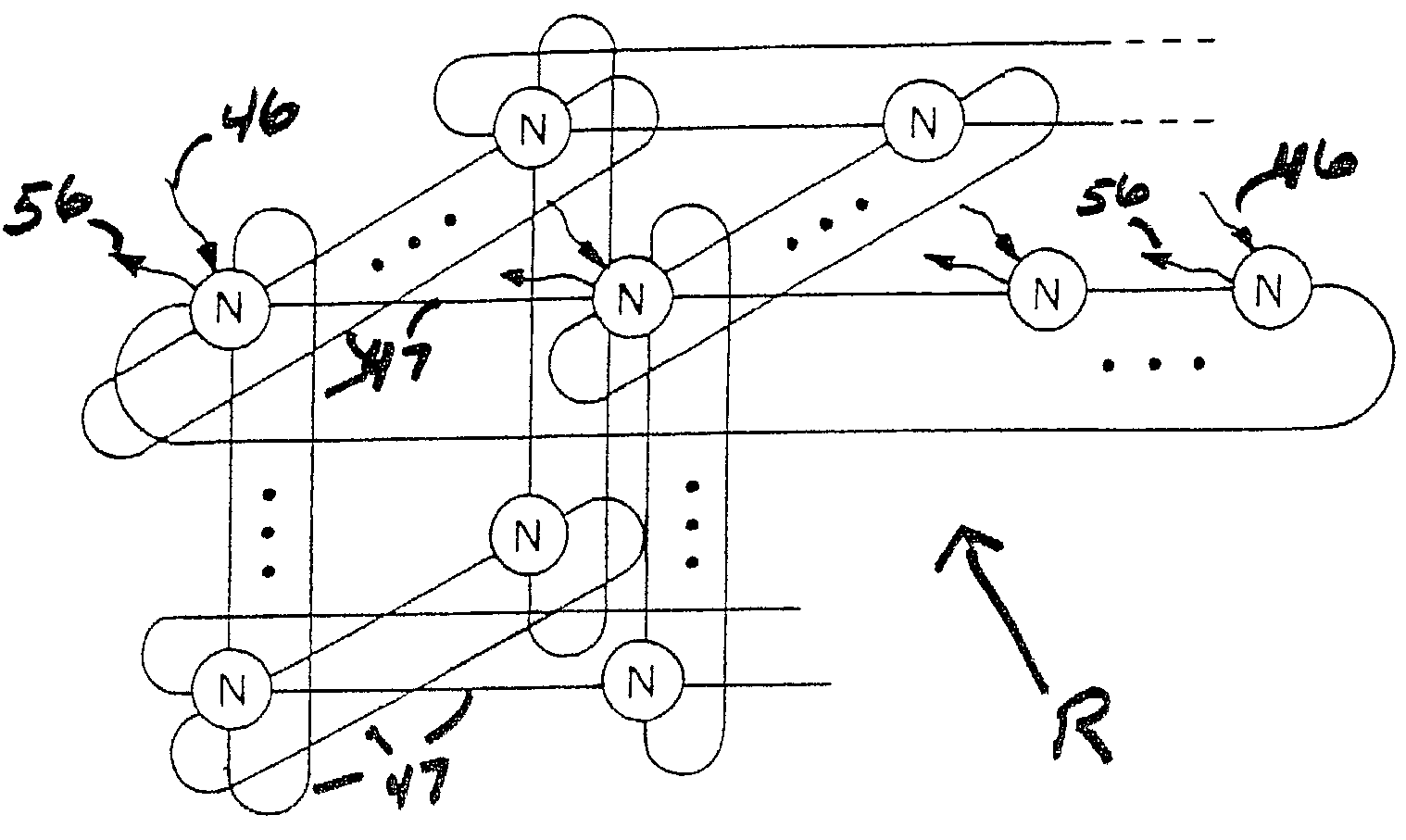
An improved architectural approach for implementation of a low power, scalable topology for a software defined radio (SDR). Low power processors and switching elements forming building blocks are employed in an embedded switched fabric architecture network having a repeating building block topology that advantageously employs wormhole routing and has self-healing, fail-safe properties. Differential signaling is used and data rates in excess of 250 Mbps are possible. In one embodiment a dual civilian and military channel SDR is disclosed; in other embodiments, a plurality of independent SDR channels, with or without encryption, are disclosed. A plurality of different topologies are disclosed including torodial topologies having a planar topology with orthogonal connections, a planar topology with orthogonal and diagonal connections, and a cube topology with both orthogonal and / or diagonal connections.
Owner:ROCKWELL COLLINS INC
Scaleable interconnect structure utilizing quality-of-service handling
InactiveUS7016363B1Quality improvementData switching by path configurationTime-division multiplexing selectionQuality of serviceLevel structure
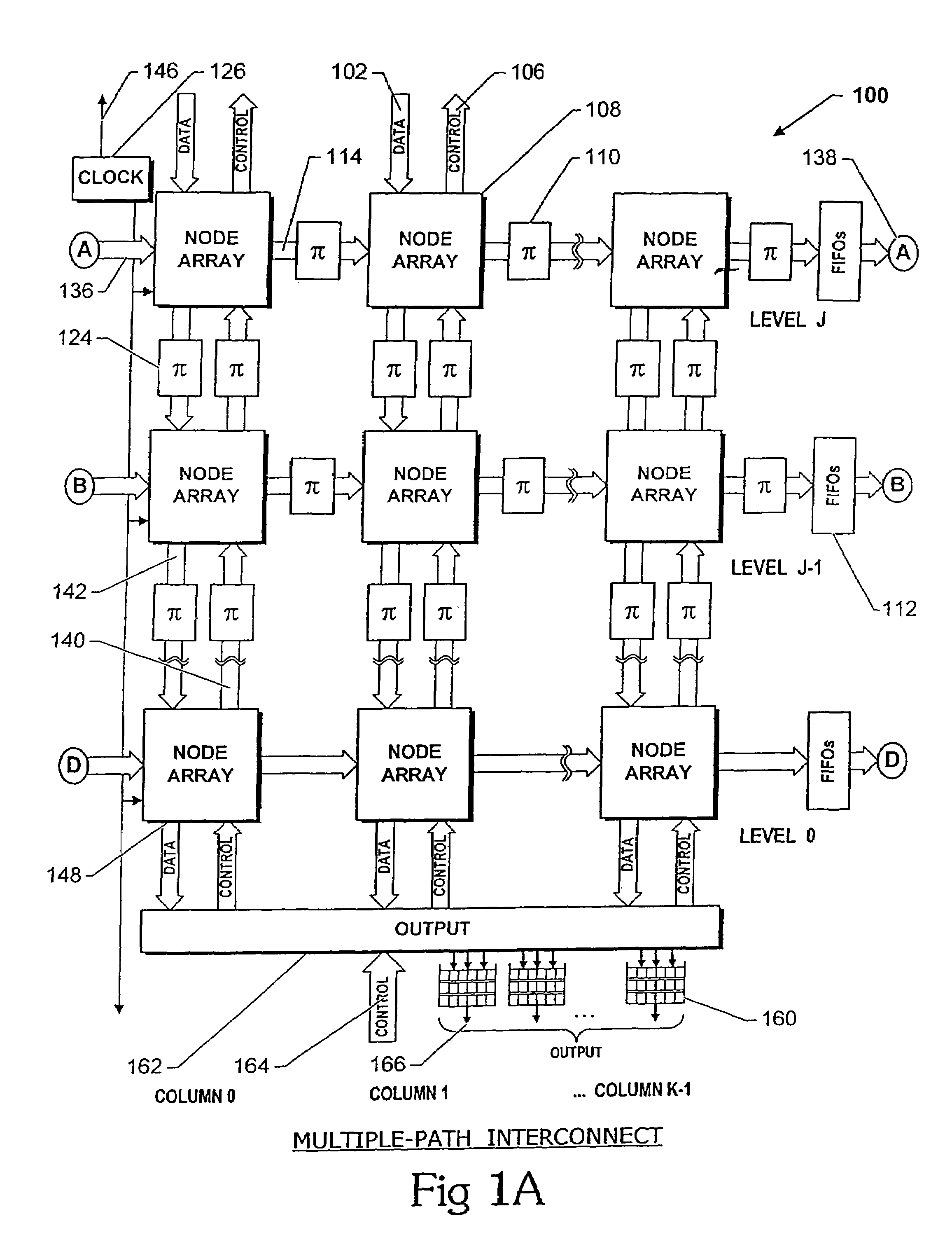
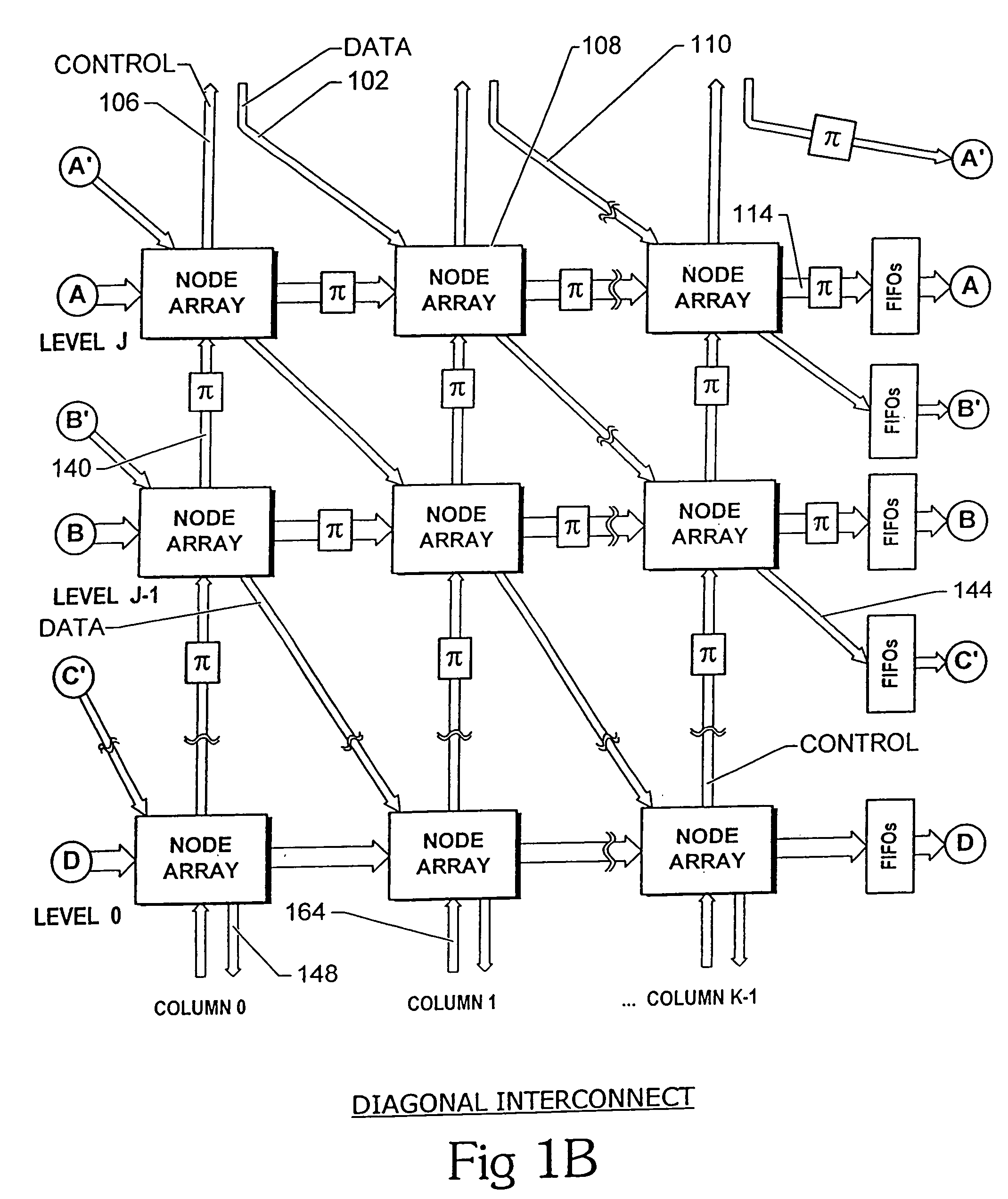
An interconnect structure and method of communicating messages on the interconnect structure assists high priority messages to travel through the interconnect structure at a faster rate than normal or low priority messages. An interconnect structure includes a plurality of nodes with a plurality of interconnect lines selectively coupling the nodes in a hierarchical multiple-level structure. Data moves from an uppermost source level to a lowermost destination level. Nodes in the structure are arranged in columns and levels. Data wormholes through the structure and, in a given time-step, data always moves from one column to an adjacent column and while remaining on the same level or moving down to a lower level. When data moves down a level, an additional bit of the target output is fixed so data exiting from the bottom of the structure arrives at the proper target output port.
Owner:INTERACTIC HLDG LLC
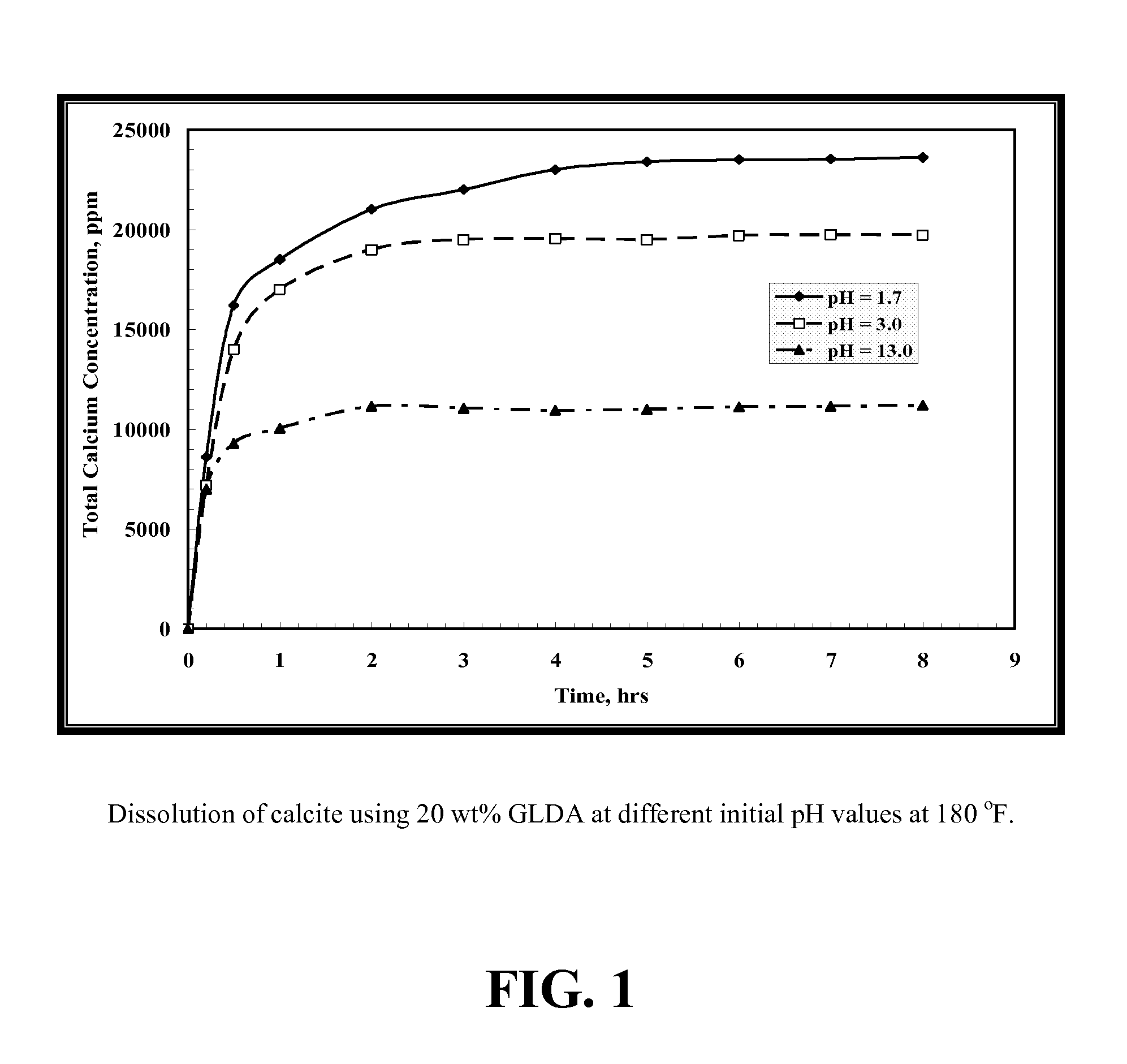
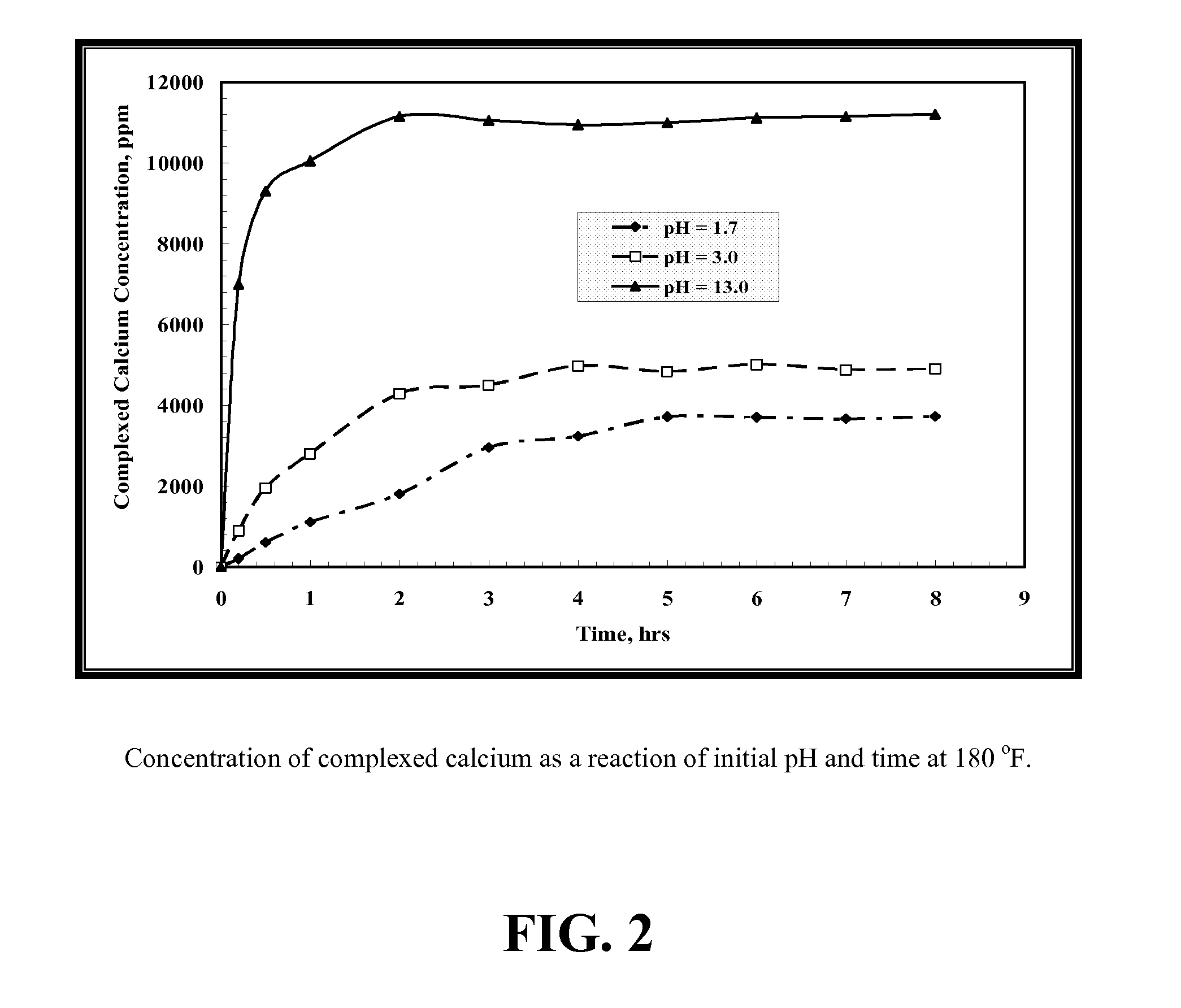
Environmentally friendly stimulation fluids, processes to create wormholes in carbonate reservoirs, and processes to remove wellbore damage in carbonate reservoirs
ActiveUS20120202720A1Reduce calcium concentrationChelating ability decreasedFlushingDrilling compositionDamage zoneWormhole
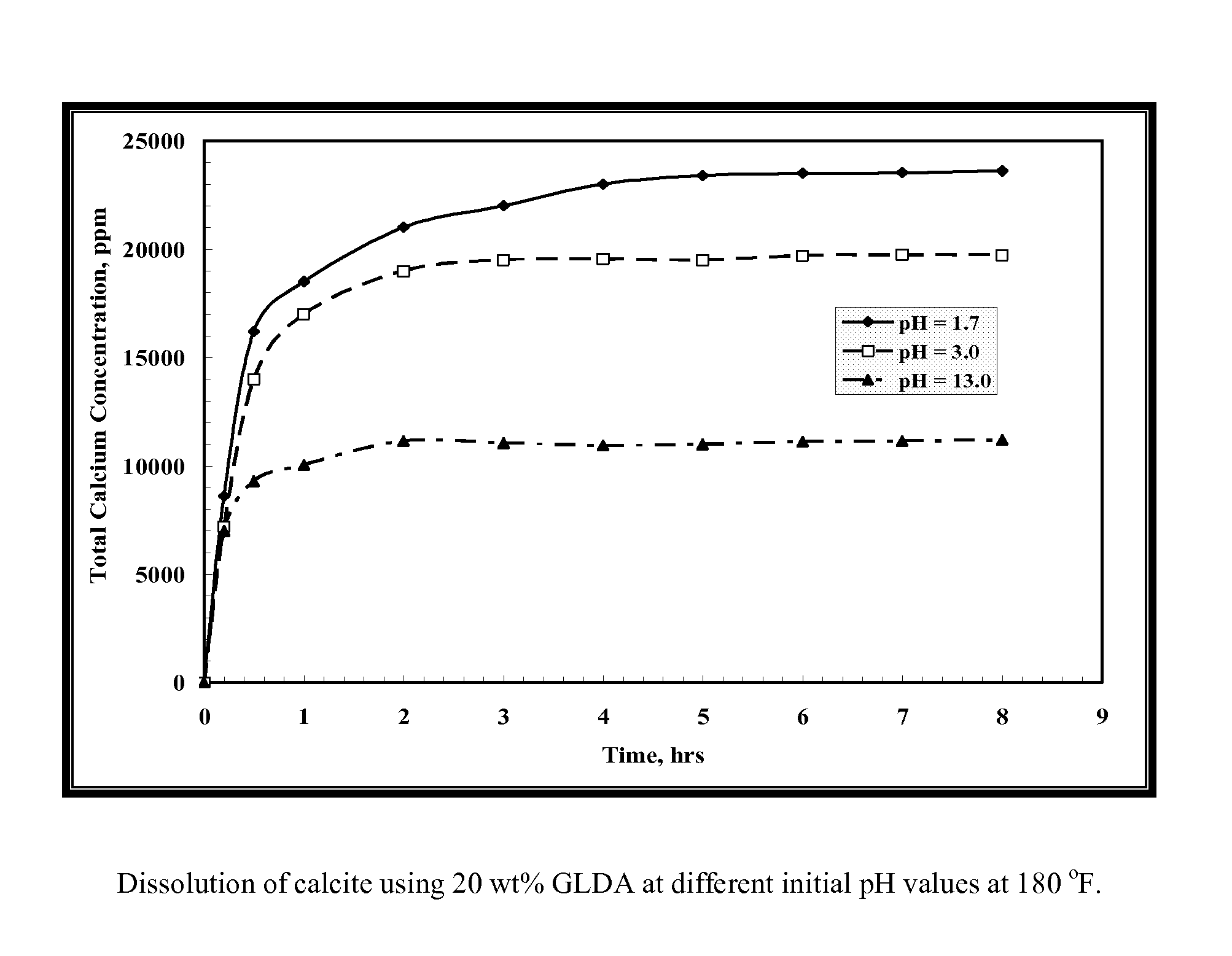
The present invention includes processes to create wormholes in carbonate reservoirs by contacting a formation with a solution comprising glutamic acid N,N-diacetic acid (GLDA) and / or a salt thereof, methylglycine-N,N-diacetic acid (MGDA) and / or a salt thereof, or a combination thereof. The present invention also includes processes to remove wellbore damage in a carbonate reservoir by contacting a damaged zone of the carbonate reservoir with a solution comprising GLDA and / or a salt thereof, methylglycine-N,N-diacetic acid (MGDA) and / or a salt thereof, or a combination thereof. The present invention further includes solutions comprising a salt and further comprising GLDA and / or a salt thereof, methylglycine-N,N-diacetic acid (MGDA) and / or a salt thereof, or a combination thereof.
Owner:AKZO NOBEL CHEM INT BV
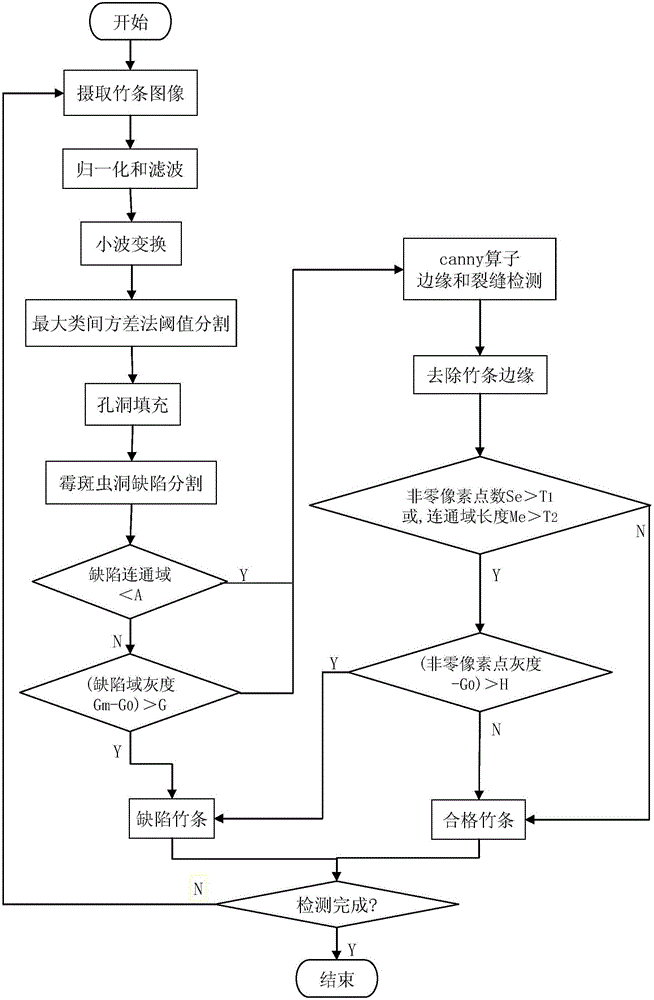
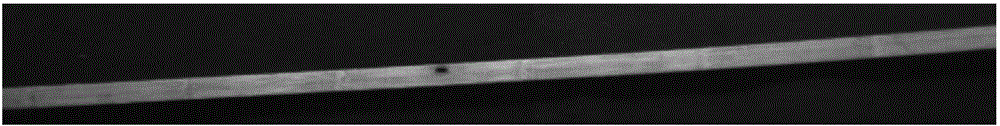
Computer vision-based bamboo strip surface defect detection method
ActiveCN105158258AGuaranteed screening efficiencyGuaranteed screening qualityImage enhancementGeometric image transformationVision basedMildew
The invention relates to a computer vision-based bamboo strip surface defect detection method. The method comprises the following steps: shooting the image of a bamboo strip, normalizing, filtering, and carrying out wavelet transformation treatment; segmenting the threshold of the image by using an OTSU technology, carrying out closed operation to fill holes of the bamboo strip image, carrying out corrosion operation to remove negative influences of the closed operation, segmenting the wormhole and / or mildew spot defect in the bamboo strip image through a difference image technology, and considering no mildew spot or wormhole defect exists and entering crack detection if the connected domain area of the defect is smaller than the defect domain area threshold A; calculating the defect connected domain image gray average Gm if the connected domain area of the defect is not smaller than the defect domain area threshold A, and considering mildew spot or wormhole exists and judging the bamboo strip as a defected bamboo strip if a difference between the Gm and a bamboo strip image scale average G0 is greater than a threshold G; and detecting edges and cracks if the difference is not greater than the threshold G, removing the bamboo strip edges of the image, determining crack defects exist if the total number of nonzero pixel points or a maximum connected domain length is greater than a corresponding threshold and the crack scale average is greater than G0, and determining the bamboo strip is qualified if not. The method has the advantages of high detection efficiency, strong noise resistance and high stability, and allows the correct recognition rate to reach 95% or above.
Owner:GUANGXI NORMAL UNIV
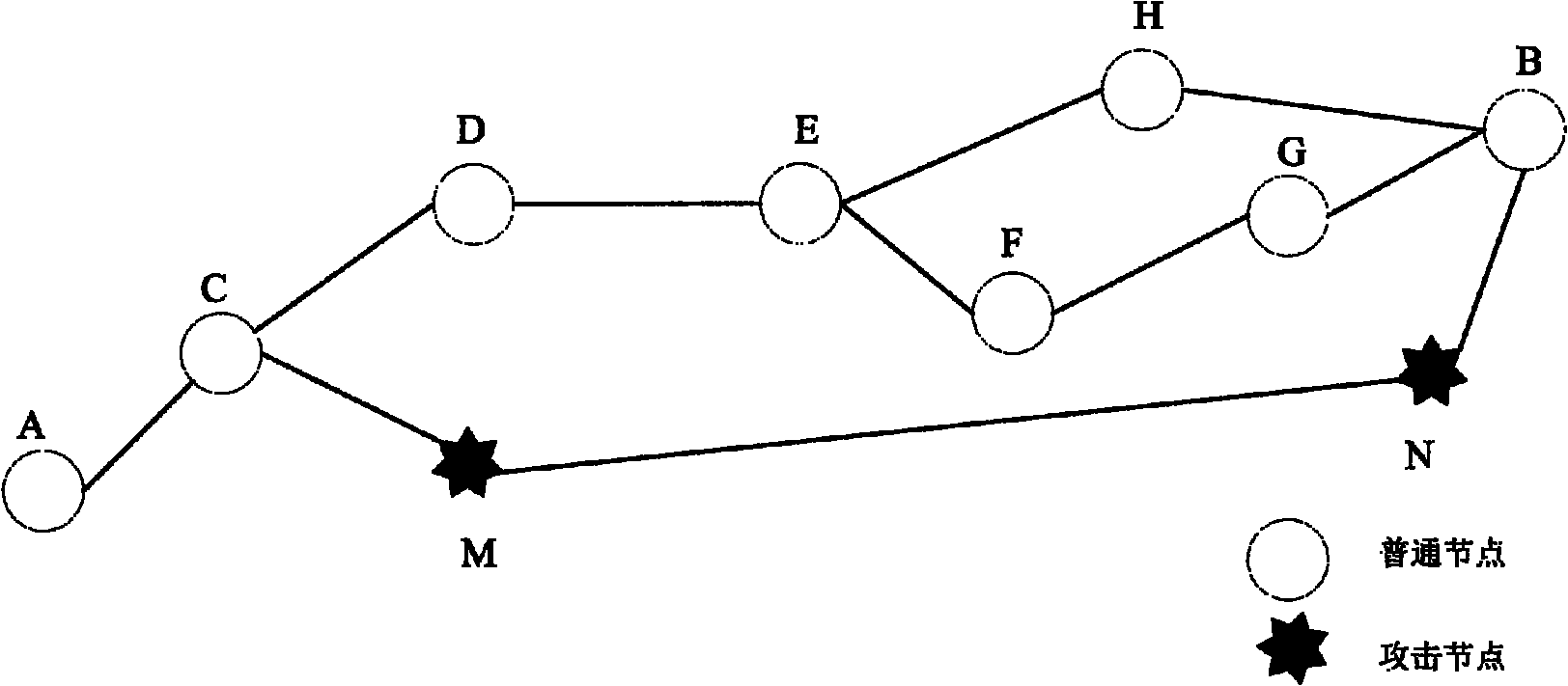
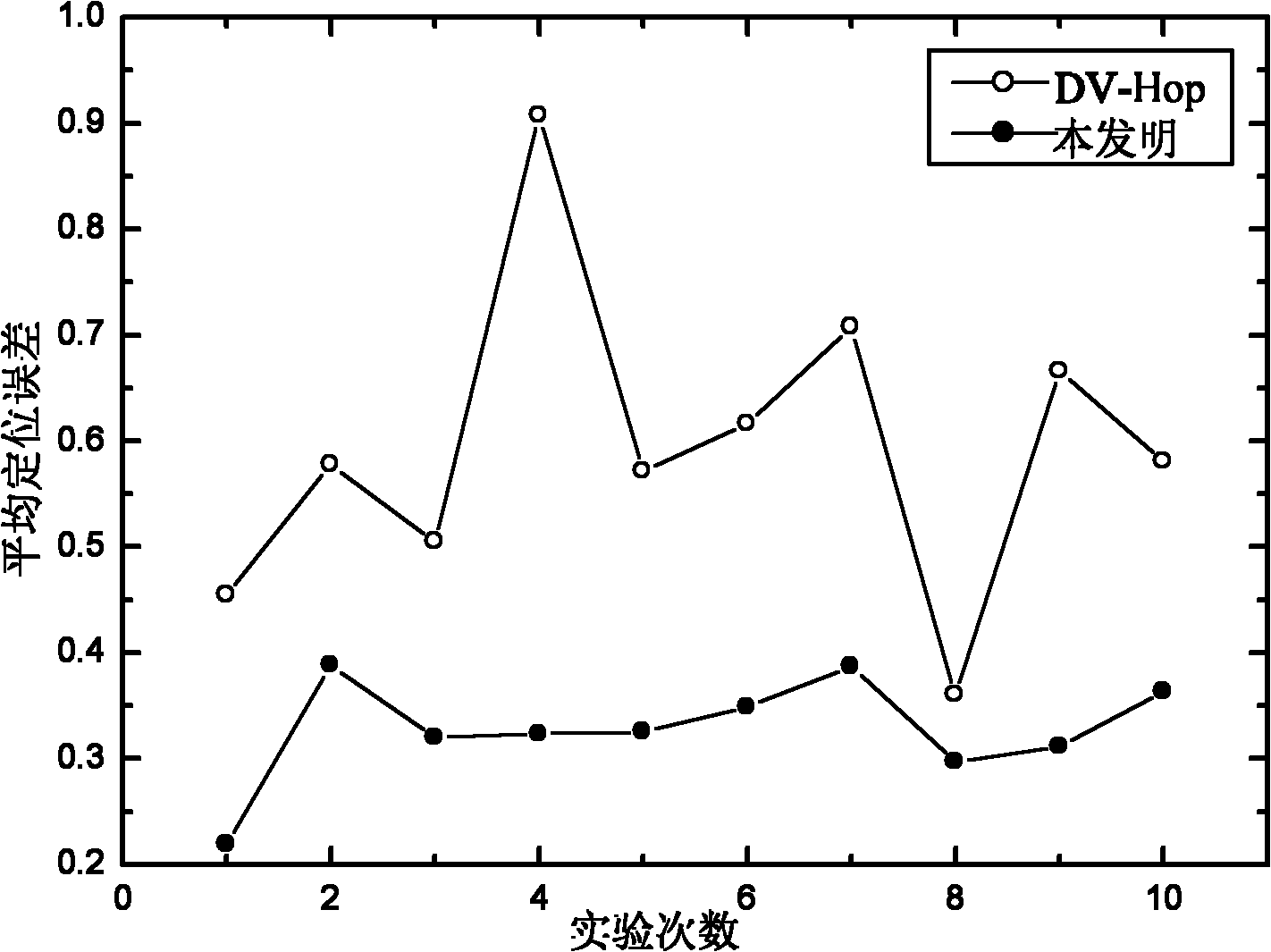
Anti-attack reliable wireless sensor network node positioning method
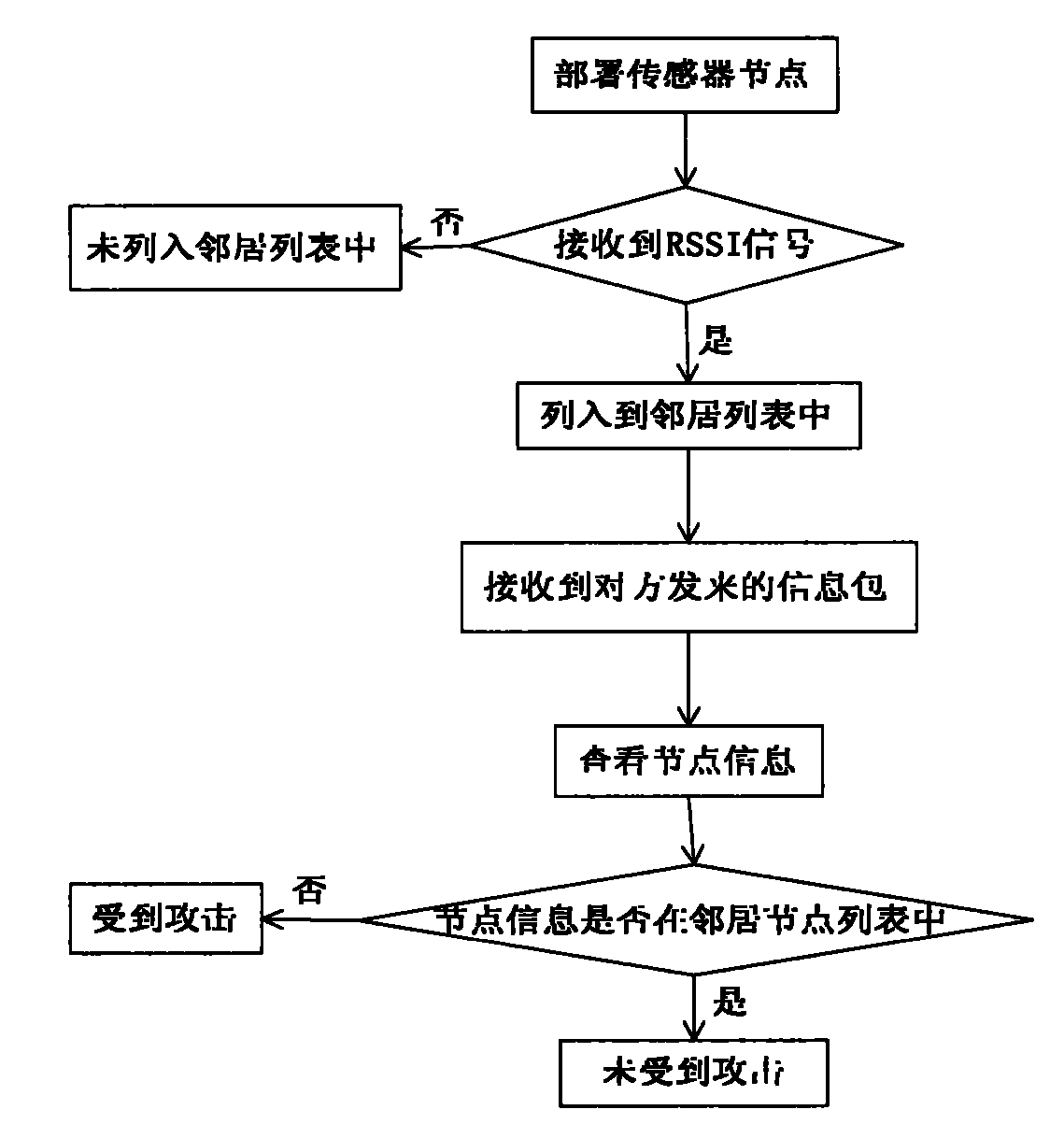
ActiveCN102186171AReduce computational costSave spaceSecurity arrangementHigh level techniquesWireless sensor networkingWormhole
The invention belongs to the technical field of computer network security, and relates to an anti-attack reliable wireless sensor network node positioning method. In ordinary positioning methods, nodes to be positioned are easy to attack by malicious nodes, so the positioning effects of the nodes are influenced. By the reliable positioning method provided by the invention, Sybil attacks and wormhole attacks can be resisted at the same time. The method comprises that: a beacon node estimates the smallest hop number between the beacon node and other beacon nodes; the beacon node estimates an average hop distance among the nodes; the nodes cooperate with one another to detect attack nodes in a network; and unknown nodes estimate own coordinates. Compared with the prior art, the invention improves the attack resistance of the wireless sensor nodes in a positioning process, reduces positioning errors in an environment with the malicious nodes, and reduces the communication cost and calculation cost of the nodes as much as possible in the positioning method by fully combining the characteristic that the energy of the wireless sensor nodes is finite.
Owner:北京涵鑫盛科技有限公司
Highly reliable network server system on chip and design method thereof
ActiveCN101335606AReduce areaReduce power overheadError preventionData switching networksFault toleranceTime delays
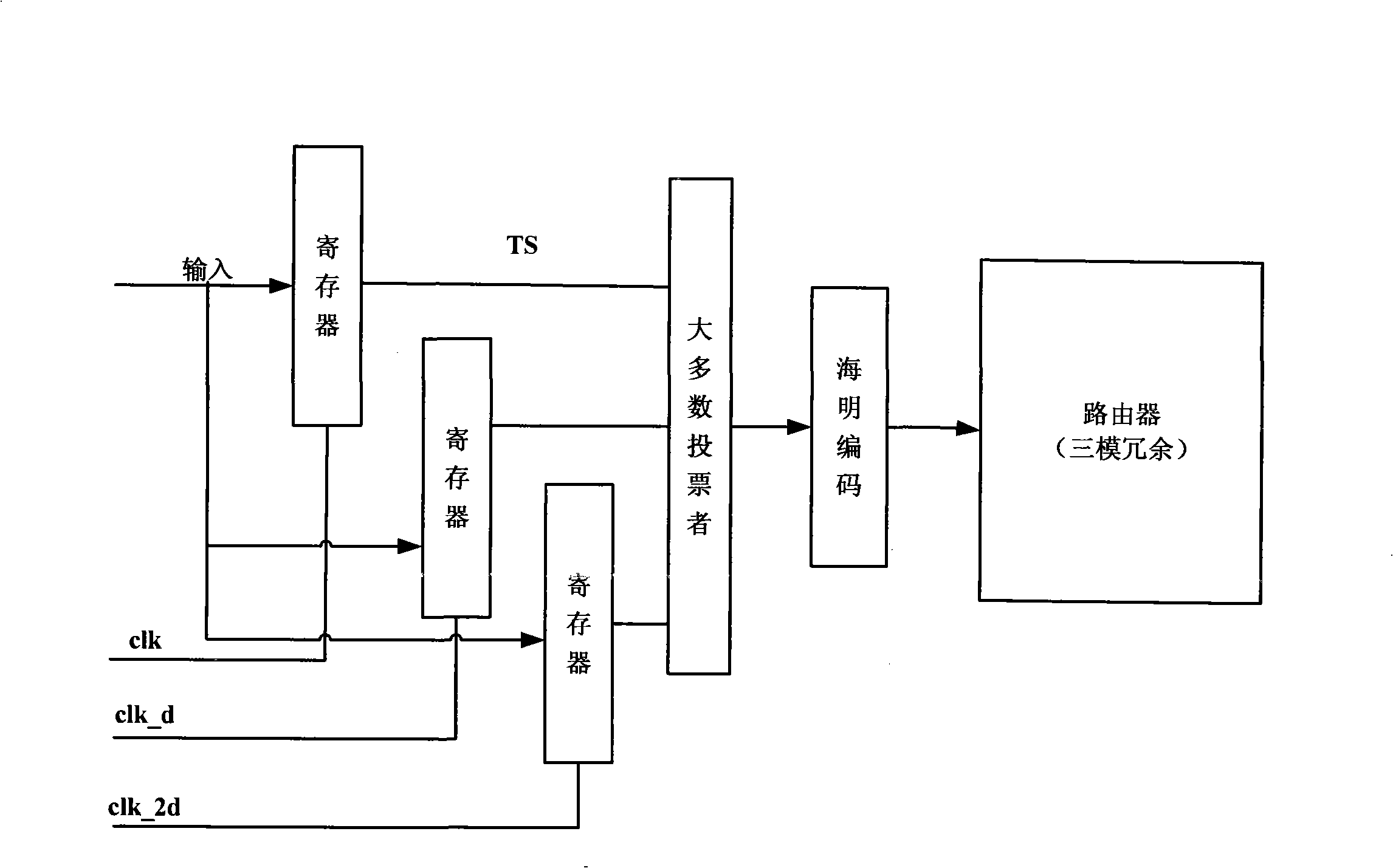
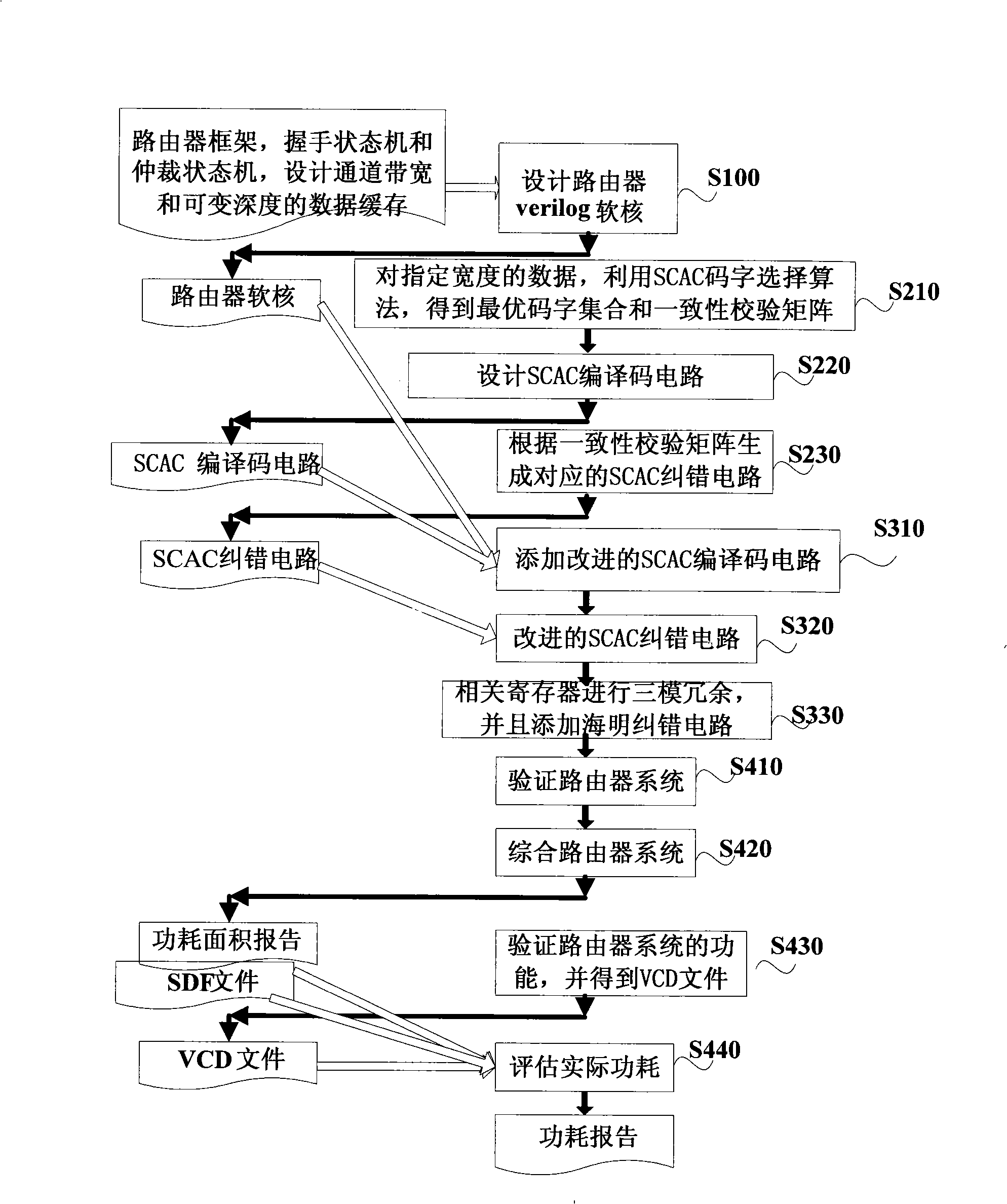
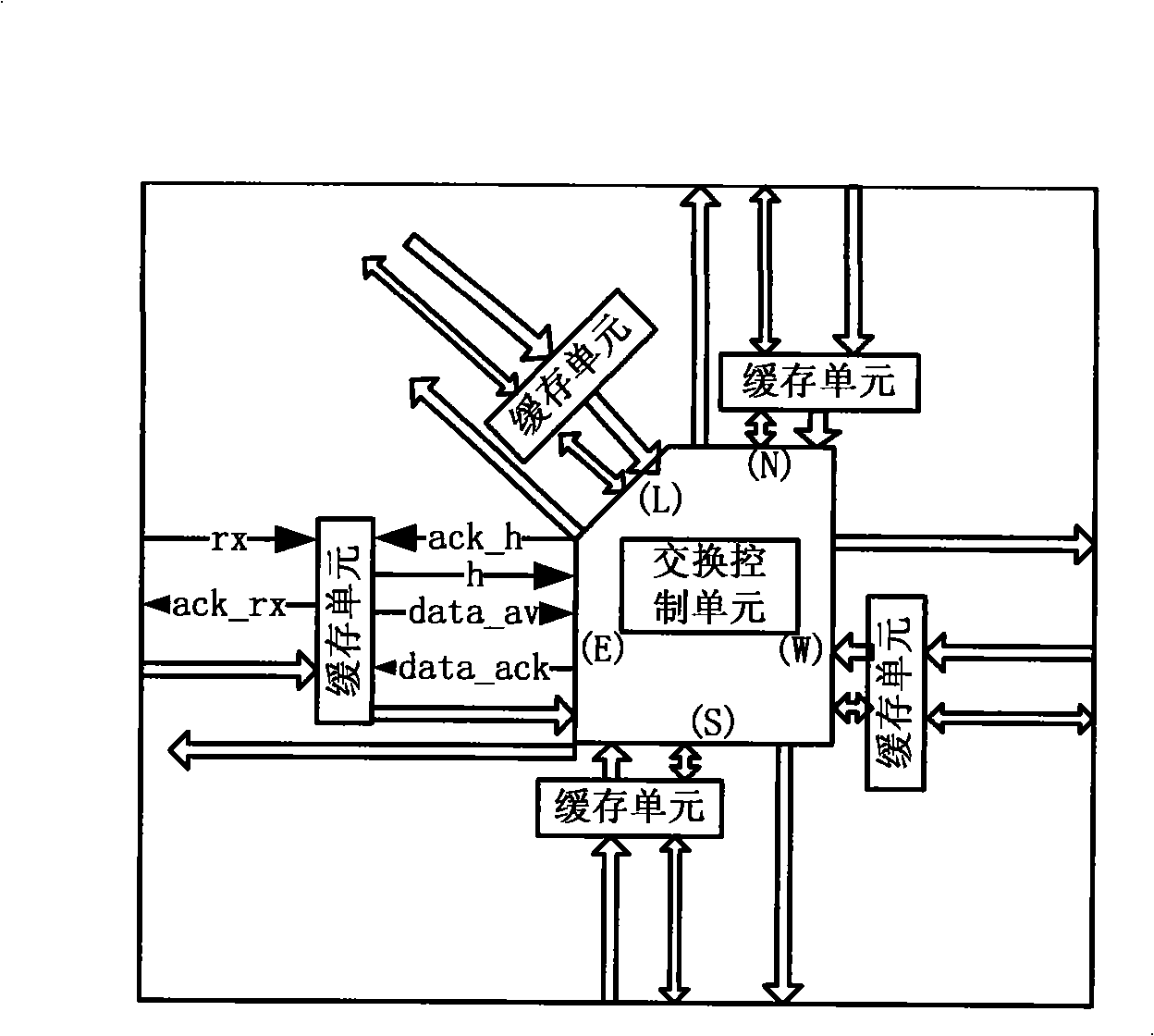
The invention discloses an on-chip network router system with high reliability and a design method thereof, wherein, the design method of the on-chip network router system with high reliability comprises the steps that: a router soft core based on a wormhole routing swap mode and a rotation routing selection mode is designed; a corresponding SCAC coding circuit, an SCAC decoding circuit and an SCAC error correction circuit are designed for data with a specified width; and the SCAC error correction circuit is added into the router; the SCAC coding circuit and the SCAC decoding circuit are connected with the router so as to from a framework of the router system; an SCAC-TMR fault tolerance proposal is designed for the framework of the router system and the on-chip network router system with high reliability is realized; the functions of the on-chip network router system with high reliability are tested and verified and the performance of the on-chip network router system with high reliability is evaluated. The on-chip network router system with high reliability of the invention can reduce the area, the energy consumption and the expenses of the on-chip network, ensure the reliable data transmission of the on-chip network and prevent a signal jumping with a relatively long time delay from appearing on the channel, thus being more applicable to the design of fault-tolerant and multi-core processors in the future.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
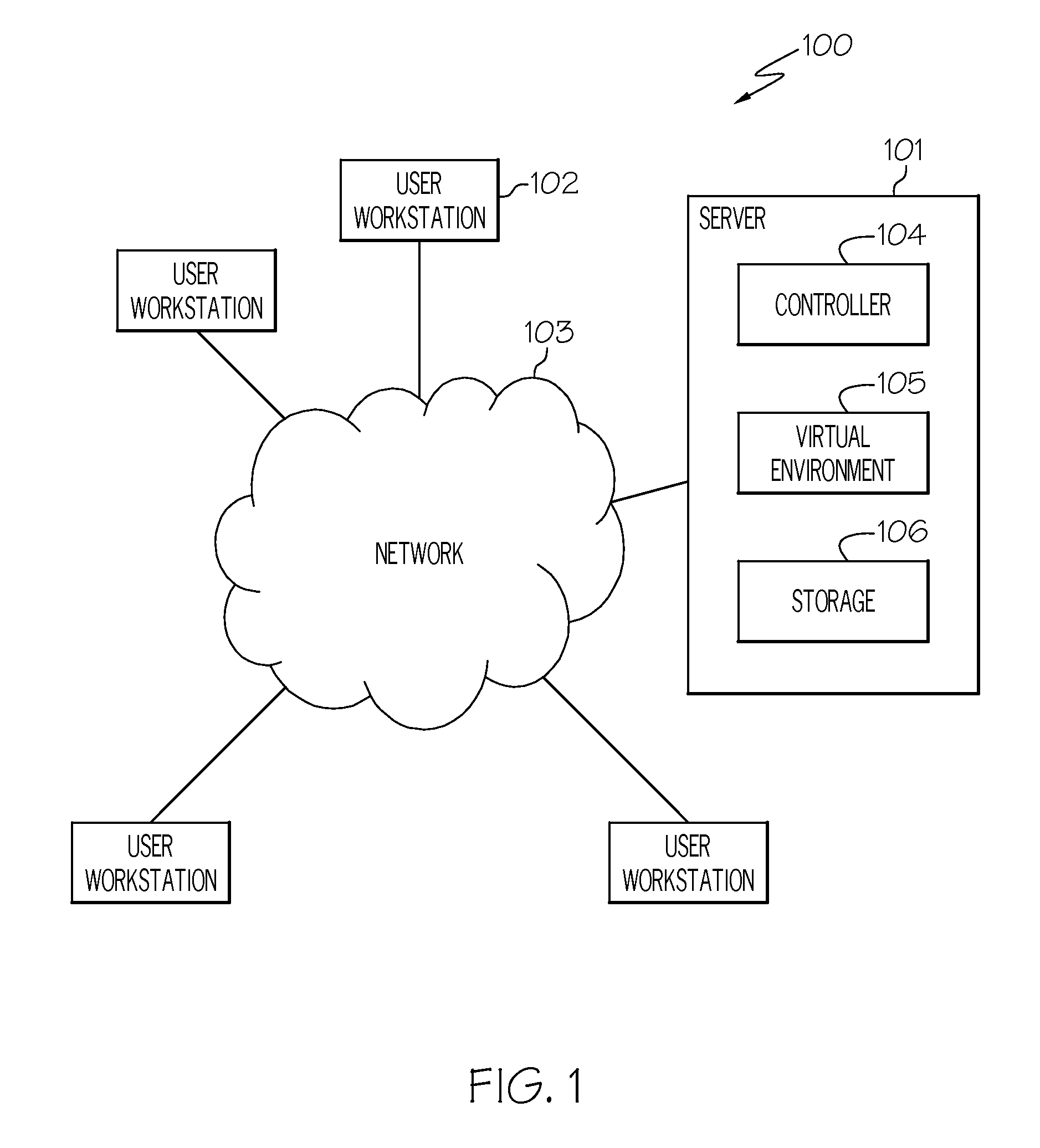
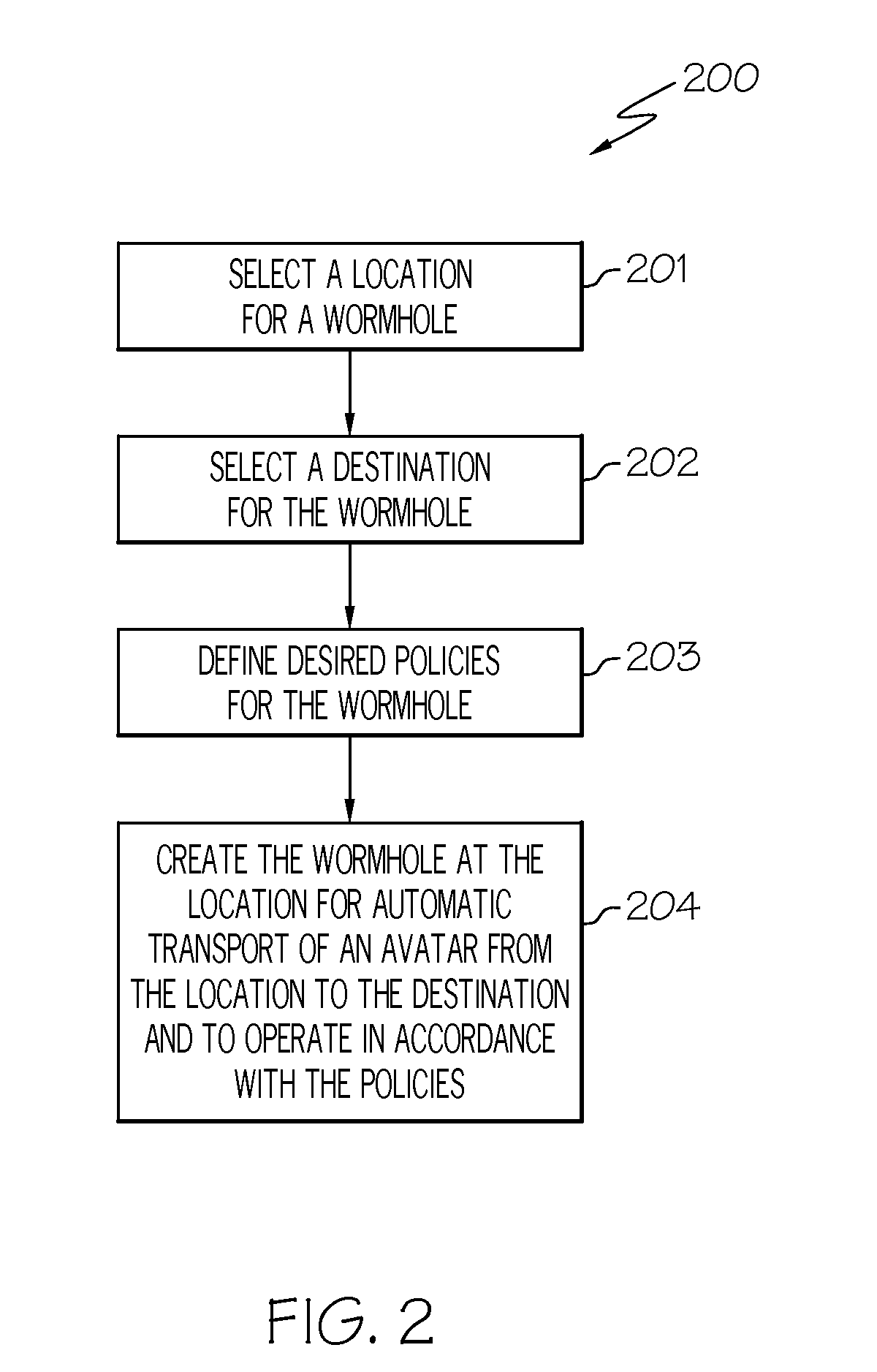
Three-dimensional (3D) virtual world wormholes
A three dimensional (3D) virtual world wormhole includes hosting a 3D virtual world, and creating a wormhole at a selected location in the 3D virtual world for automatic transport of an avatar from the selected location to a selected destination in the 3D virtual world. Policies may be defined for the wormhole where the wormhole operates in accordance with the defined policies. An avatar may be automatically transported from the location to any one of a plurality of destinations based on a current capacity of each of the plurality of destinations.
Owner:IBM CORP
Ultrastable porous aluminosilicate structures
Mesoporous hexagonal, cubic, lamellar, wormhole, or cellular foam aluminosilicates, gallosilicates and titanosilicates derived from protozeolitic seeds using an ionic structure directing agent are described. The silicon and aluminum, gallium or titanium centers in the structures are stable so that the framework of the structure does not collapse when heated in the presence of water or water vapor (steam). The steam stable compositions can be used as catalysts for hydrocarbon conversions, including the fluidized bed catalytic cracking and the hydrocracking of petroleum oils, and other reactions of organic compounds.
Owner:BOARD OF TRUSTEES OPERATING MICHIGAN STATE UNIV
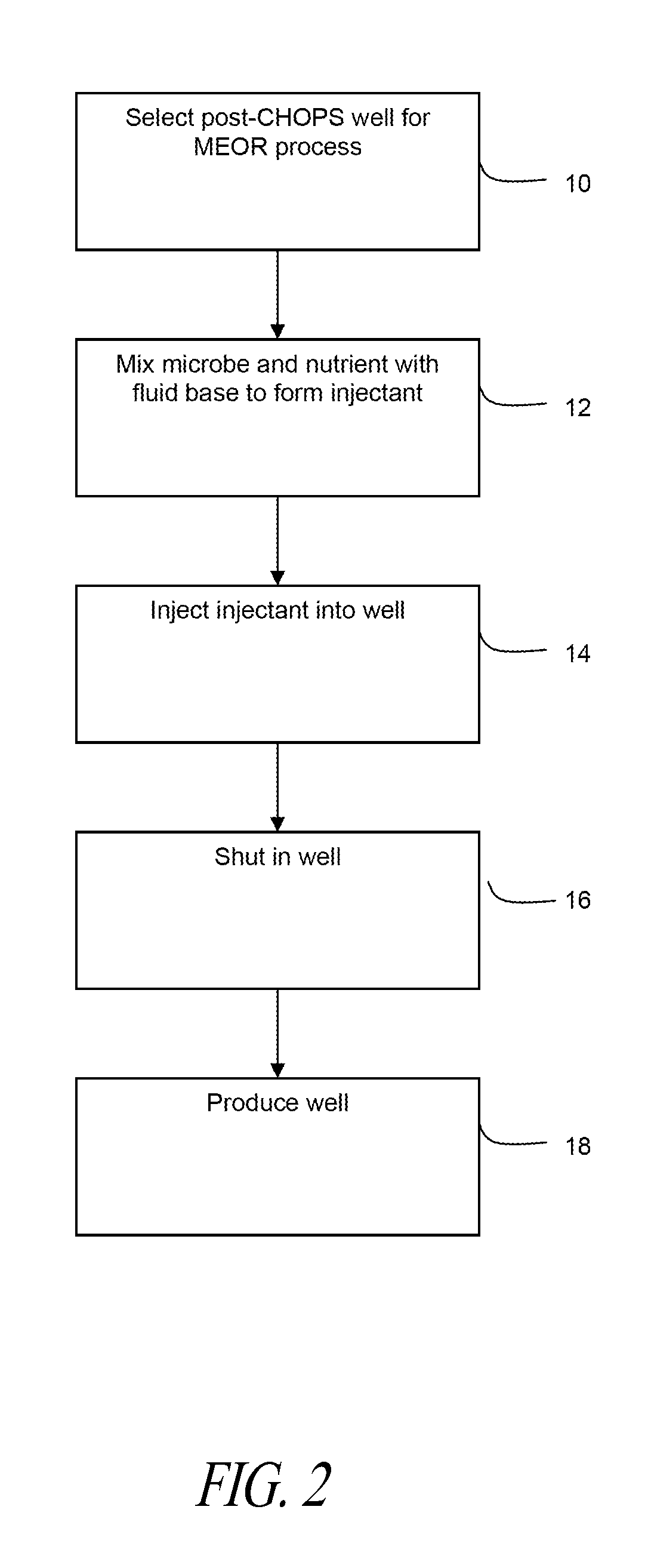
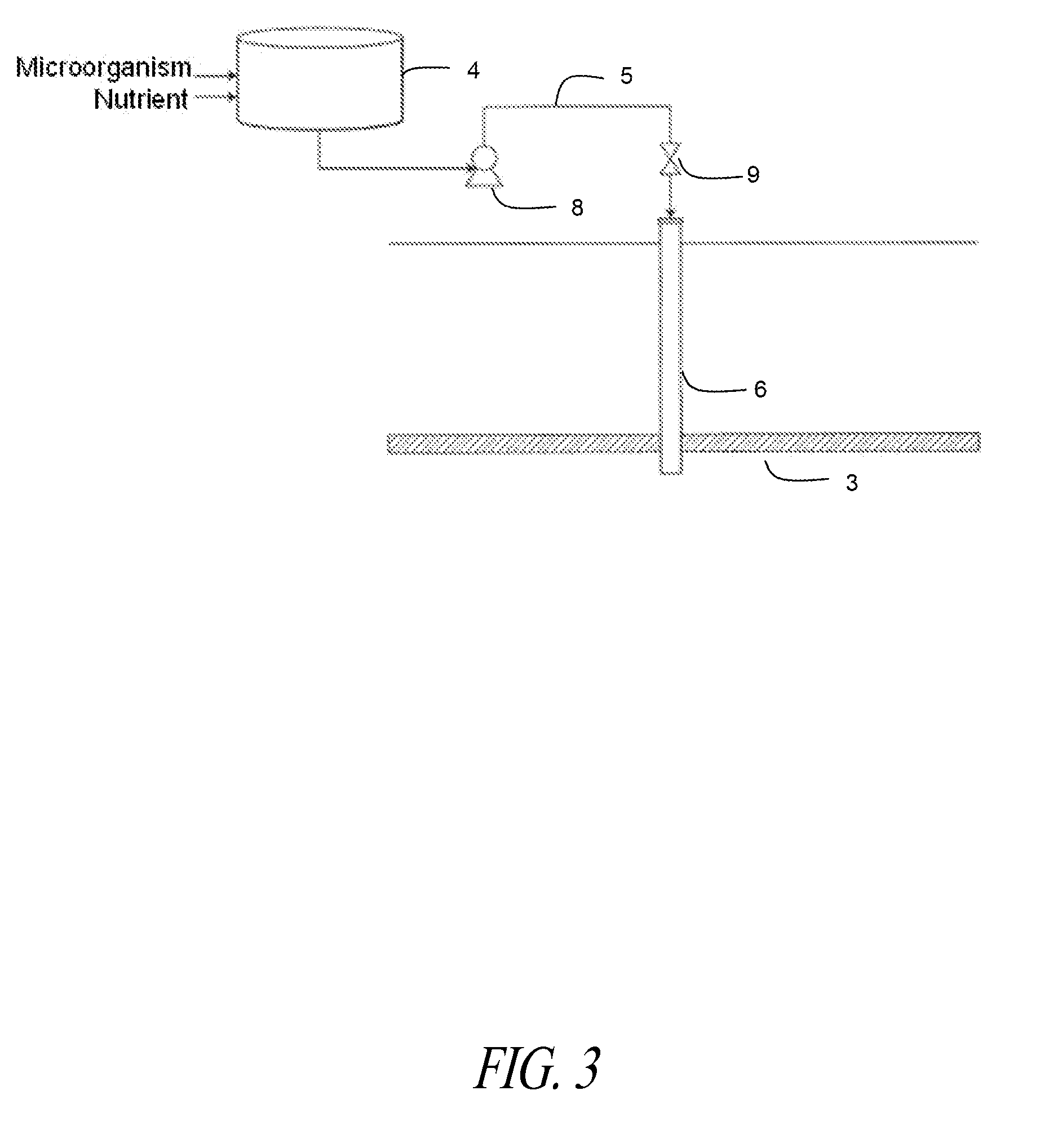
Microbial enhanced oil recovery process for heavy oil accumulations
ActiveUS8746334B2Fluid removalDrilling compositionRecovery methodCold heavy oil production with sand
A post cold heavy oil production with sand (“CHOPS”) microbial enhanced oil recovery method comprises selecting a well having at least one wormhole and that has completed primary CHOPS production. When the reservoir does not contain enough of a gas producing indigenous microbe, an injectant is prepared comprising a gas-producing microbe, a nutrient suitable for the microbe, and a fluid base. The injectant is injected through the well and into the at least one wormhole in the reservoir; the well is shut in until pressure in the well reaches the target pressure; and then the well is produced.
Owner:HUSKY OIL OPERATIONS
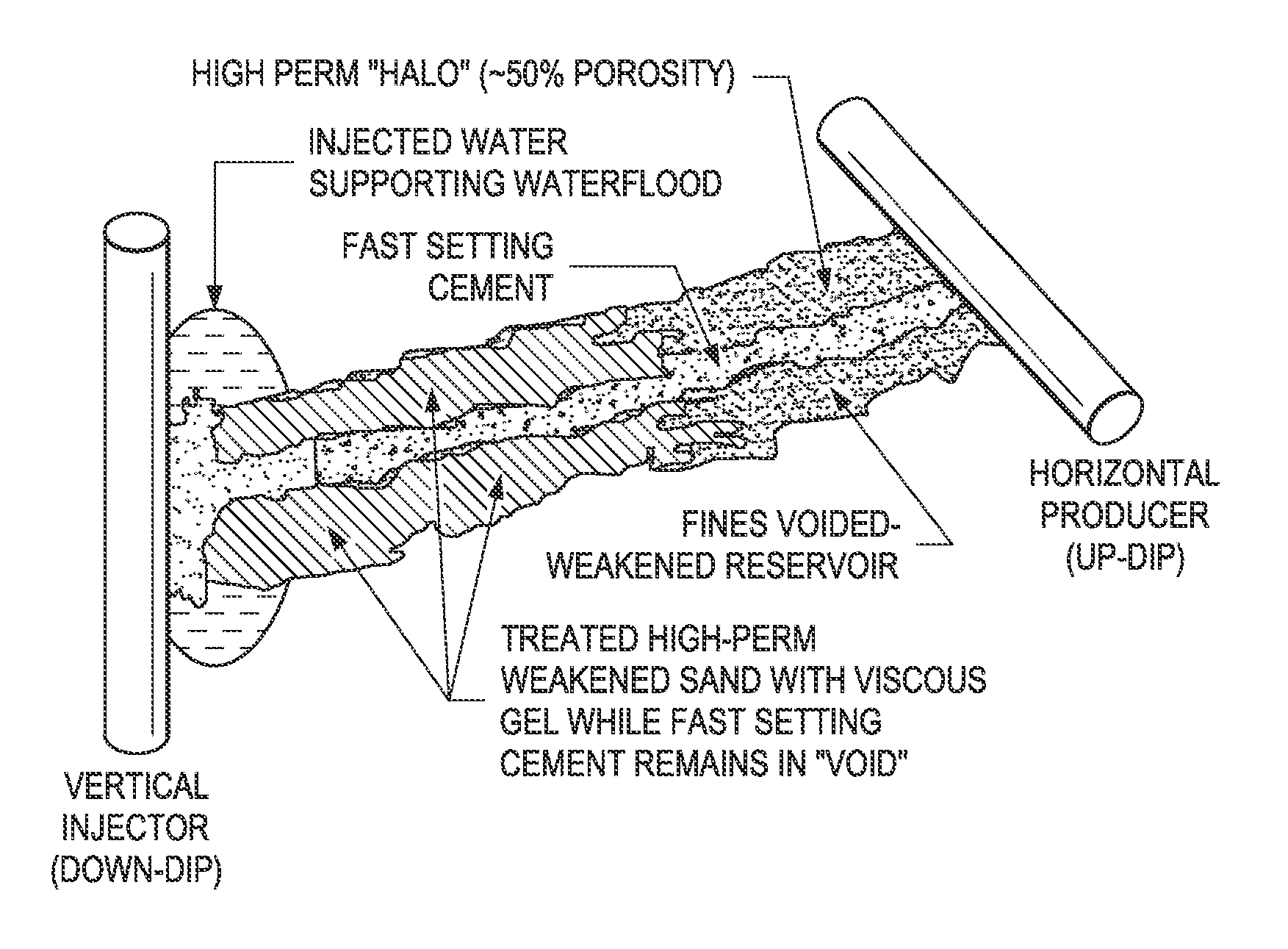
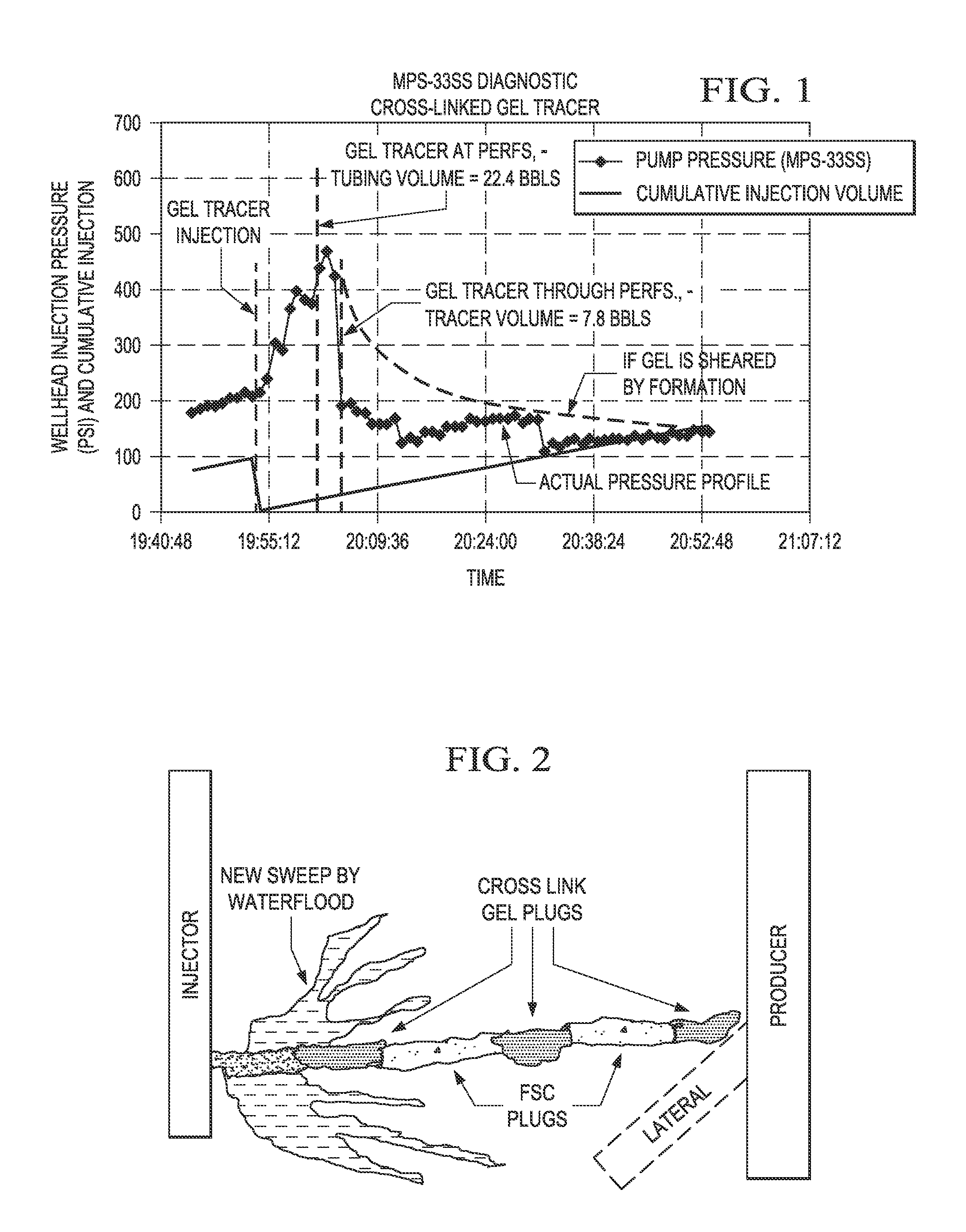
Method to Control Driving Fluid Breakthrough During Production of Hydrocarbons from a Subterranean Reservoir
InactiveUS20110024115A1Reduce flow communicationReduce communicationFluid removalDrilling compositionSlurryEngineering
The invention is directed to a method for controlling driving fluid breakthrough caused by zones of pressure communication, i.e., a matrix bypass event (“MBE”) or a wormhole, having a void space and possibly areas of enhanced permeability (a halo region) associated with the void space, within a subterranean formation arising from use of a driving fluid in reservoirs where heavy / viscous oil is being produced. In particular, the method is directed to remediation of pressure communication between injection and production wells used to produce heavy / viscous oil by way of a waterflood operation combined with a cold production method. Direct or rapid communication of water between the injector and producer wells makes the waterflood recovery process virtually ineffective and limits the production of oil from the reservoir. The invention comprises in embodiments a method wherein a slurry of a cementitious material is injected into the zone, which upon setting, provides a cement plug in the void space that reduces the pressure communication and flow of driving fluid within the zone. Another step is used to inject a gel precursor within the zone, which upon setting, produces a gel plug that also reduces pressure communication and driving fluid flow through the halo region of the zone.
Owner:BP CORP NORTH AMERICA INC
Multiple-path wormhole interconnect
InactiveUS7382775B2Multiplex system selection arrangementsDigital computer detailsSupercomputerWorkstation
Owner:INTERACTIC HLDG LLC
Safety guide model for distributed identity authentication in mobile self-organizing network
InactiveCN1953374AReduce loadGuaranteed freshnessUser identity/authority verificationData switching by path configurationNetwork packetDigital signature
The invention relates to a safety guide module for distributed identification check in mobile self-organism network. Wherein, it comprises two processes that guiding the safety mode (with public variable and calculate algorism) based on threshold digit sign to all nodes; using said safety mode to process distributed safety identification check. The invention has the advantages that the resource route will not be changed in route request process, to avoid false sign; and since it has mark of route request message, the bugged data pack can not be rearranged, to prevent attach; and it has jump identification check, to avoid DoS attach of malice node.
Owner:NO 709 RES INST OF CHINA SHIPBUILDING IND CORP
System and method for automatic merging of real and virtual environments
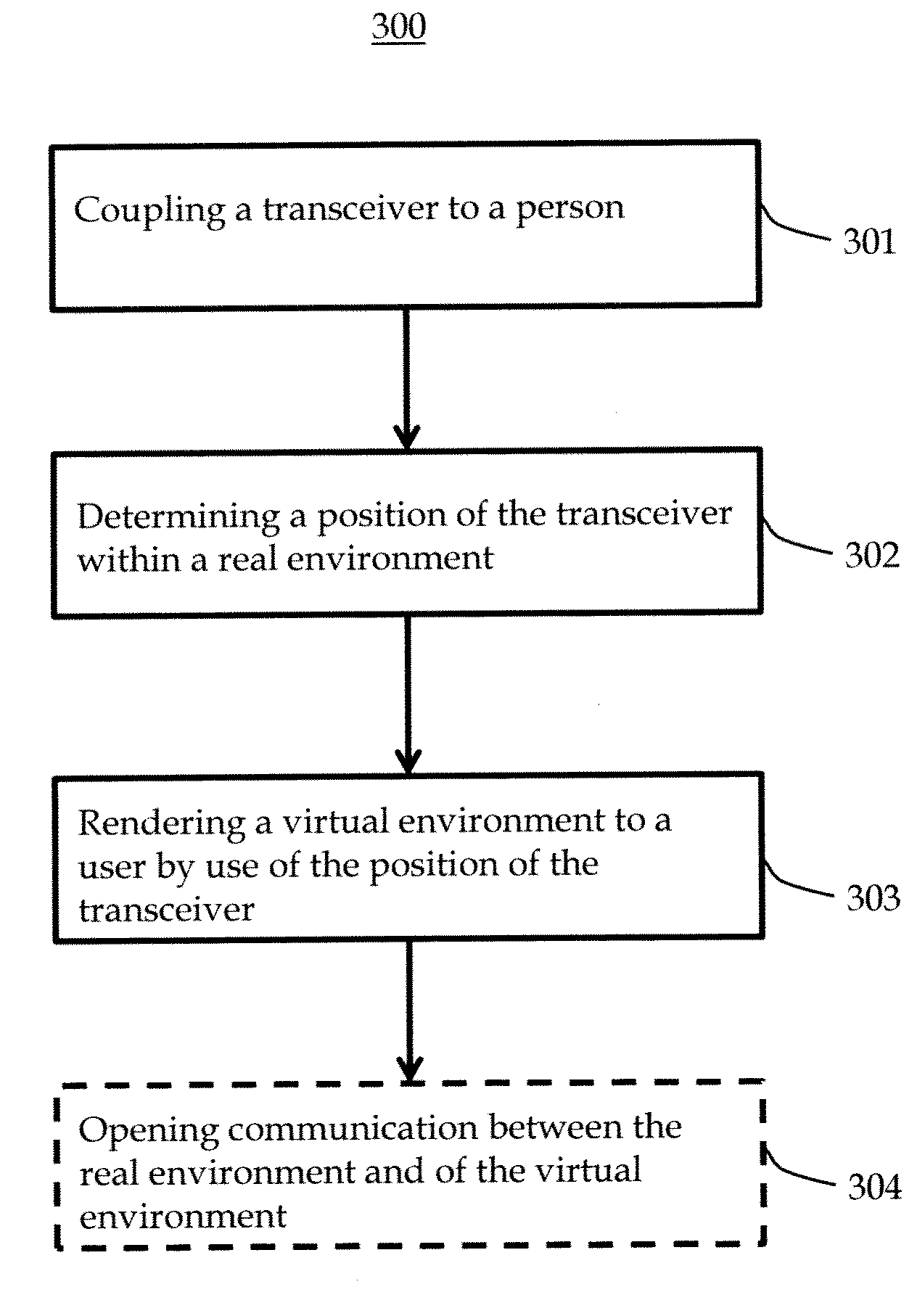
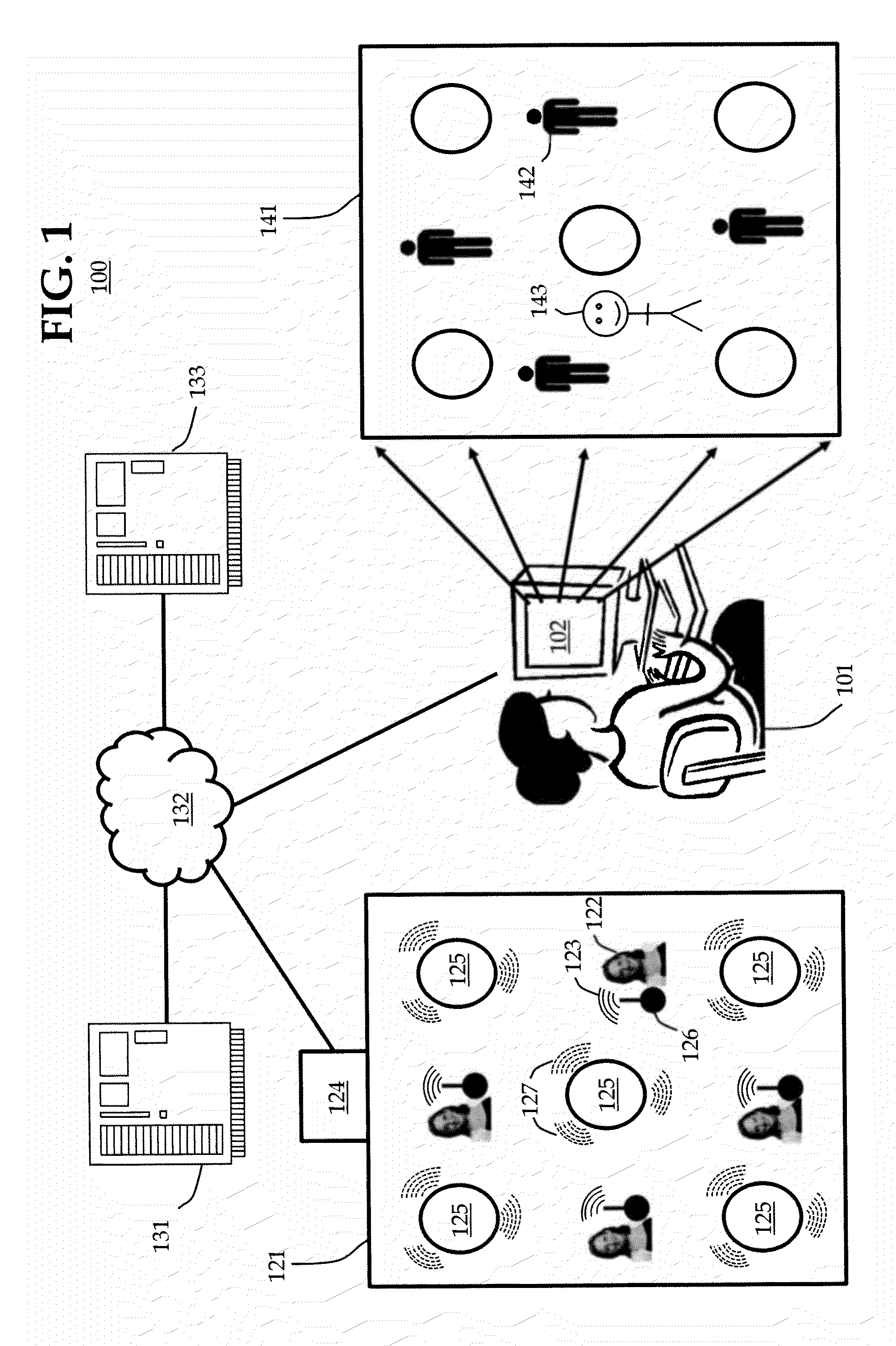
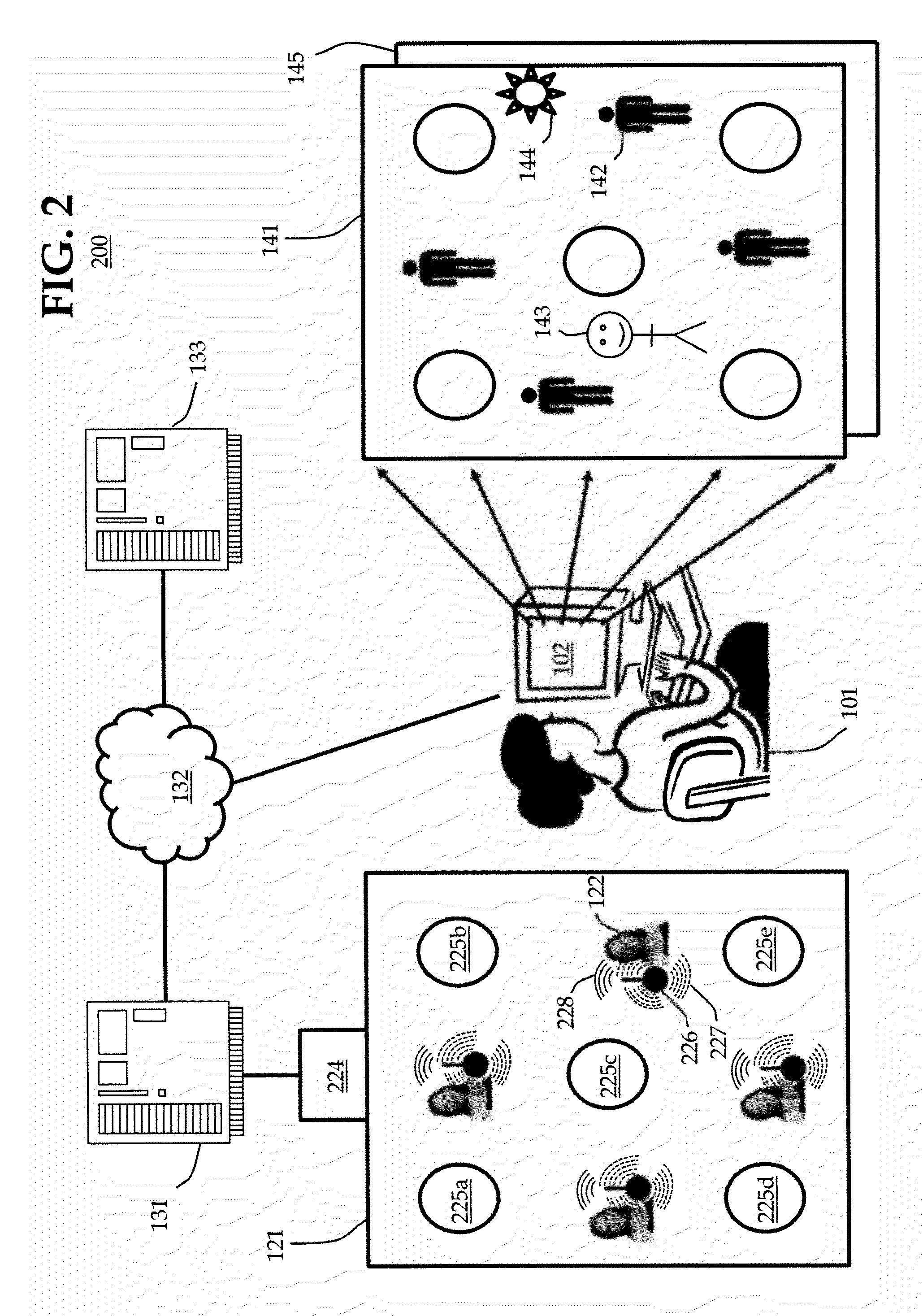
Method and system to coordinate a virtual environment with a real environment, including: coupling a transceiver to a person; determining a position of the transceiver within the real environment by use of a position-determination module; and rendering the virtual environment to a user by use of a virtual environment server that is configured to determine a position of the transceiver. The method and system may further comprises a wormhole server configured to provide communication services between the user and the person.
Owner:AVAYA INC
Application of Reservoir Conditioning In Petroleum Reservoirs
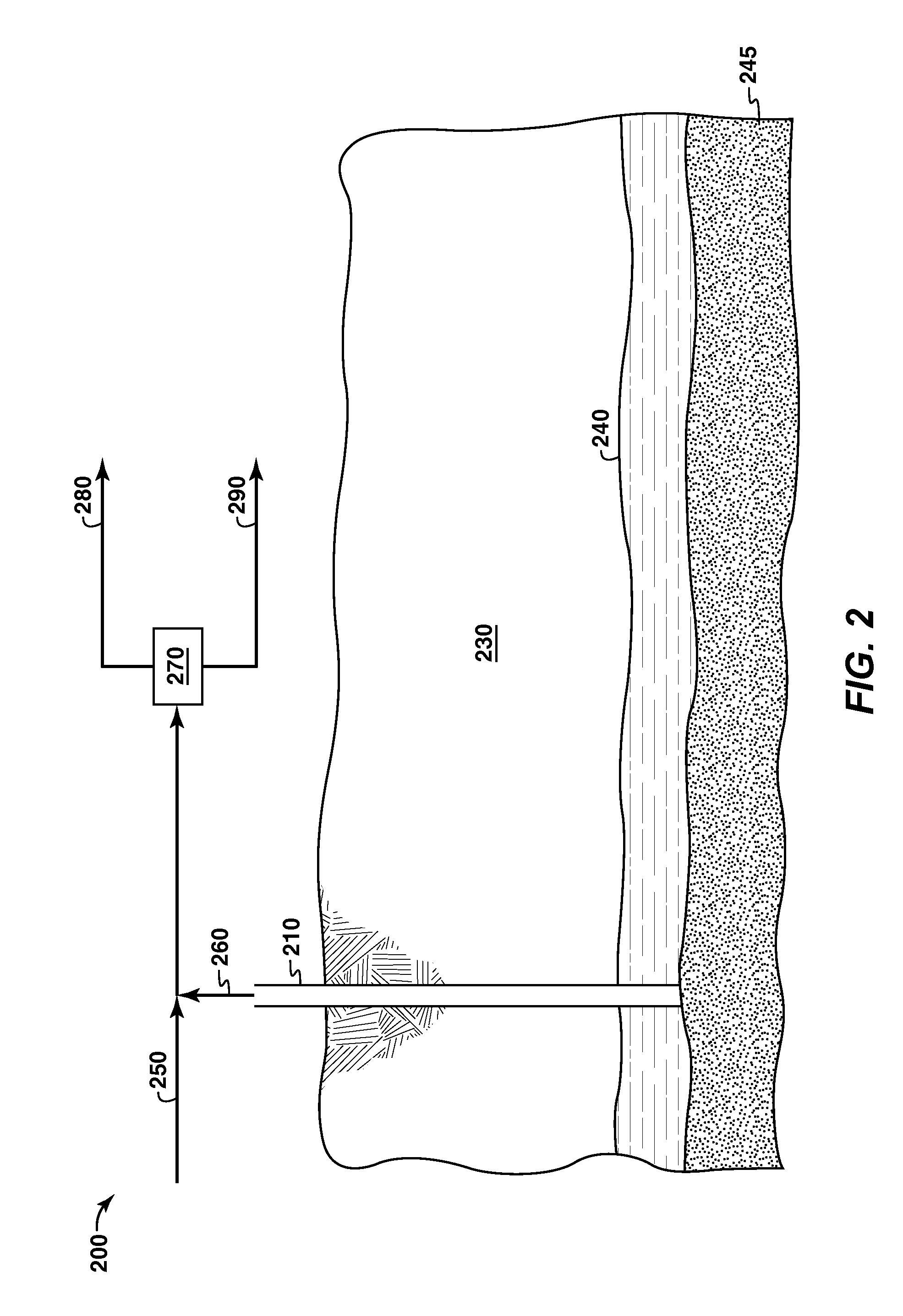
Methods for recovering heavy oil are provided. In at least one embodiment, the process includes conditioning a reservoir of interest, then initially producing fluids and particulate solids such as sand to increase reservoir access (“slurry production”). The initial production may generate high permeability channels or wormholes in the formation, which may be used for heavy oil production processes (“hydrocarbon production”) such as cold flow (CHOPS) or enhanced production processes such as SAGD, or VAPEX.
Owner:EXXONMOBIL UPSTREAM RES CO
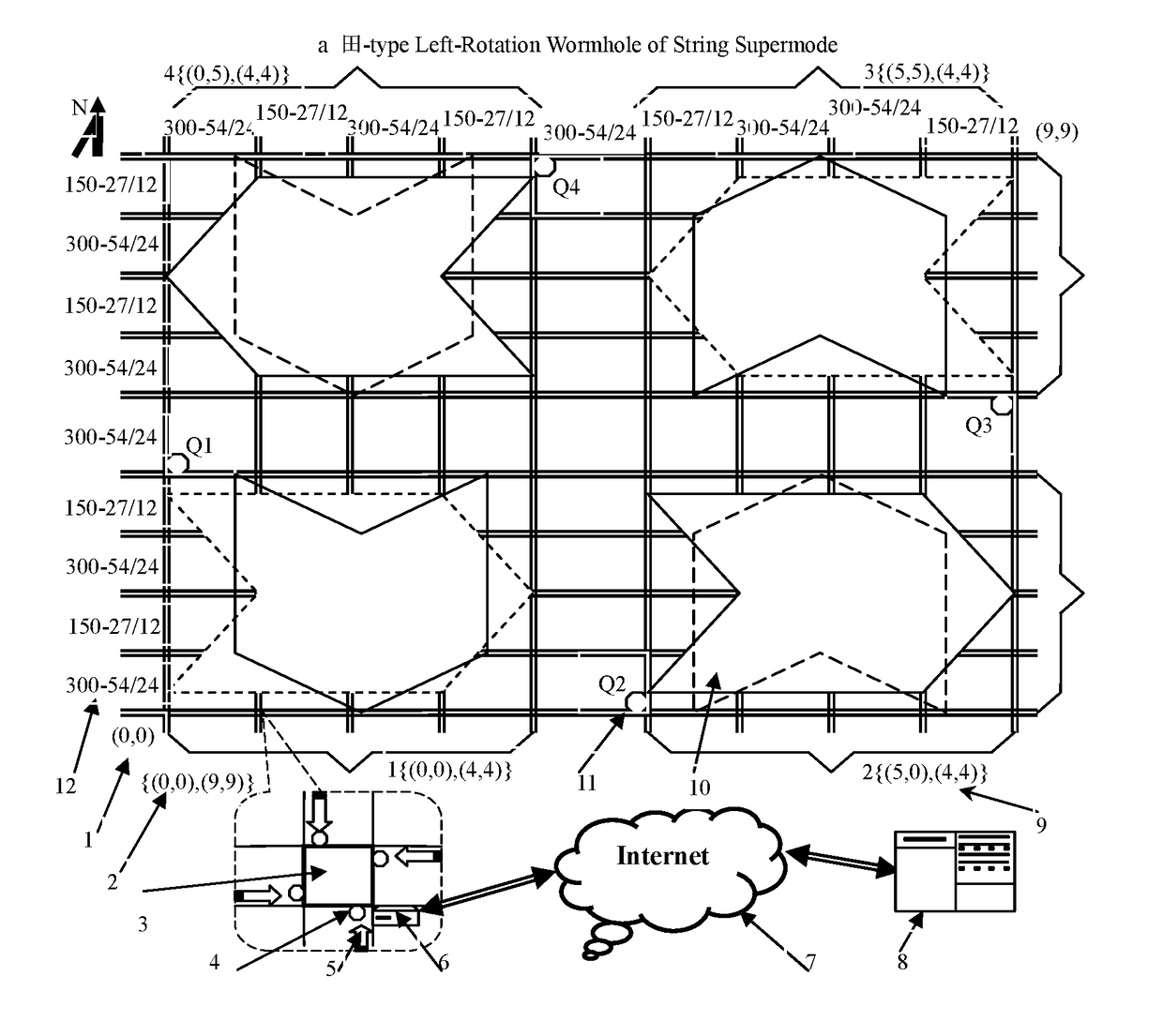
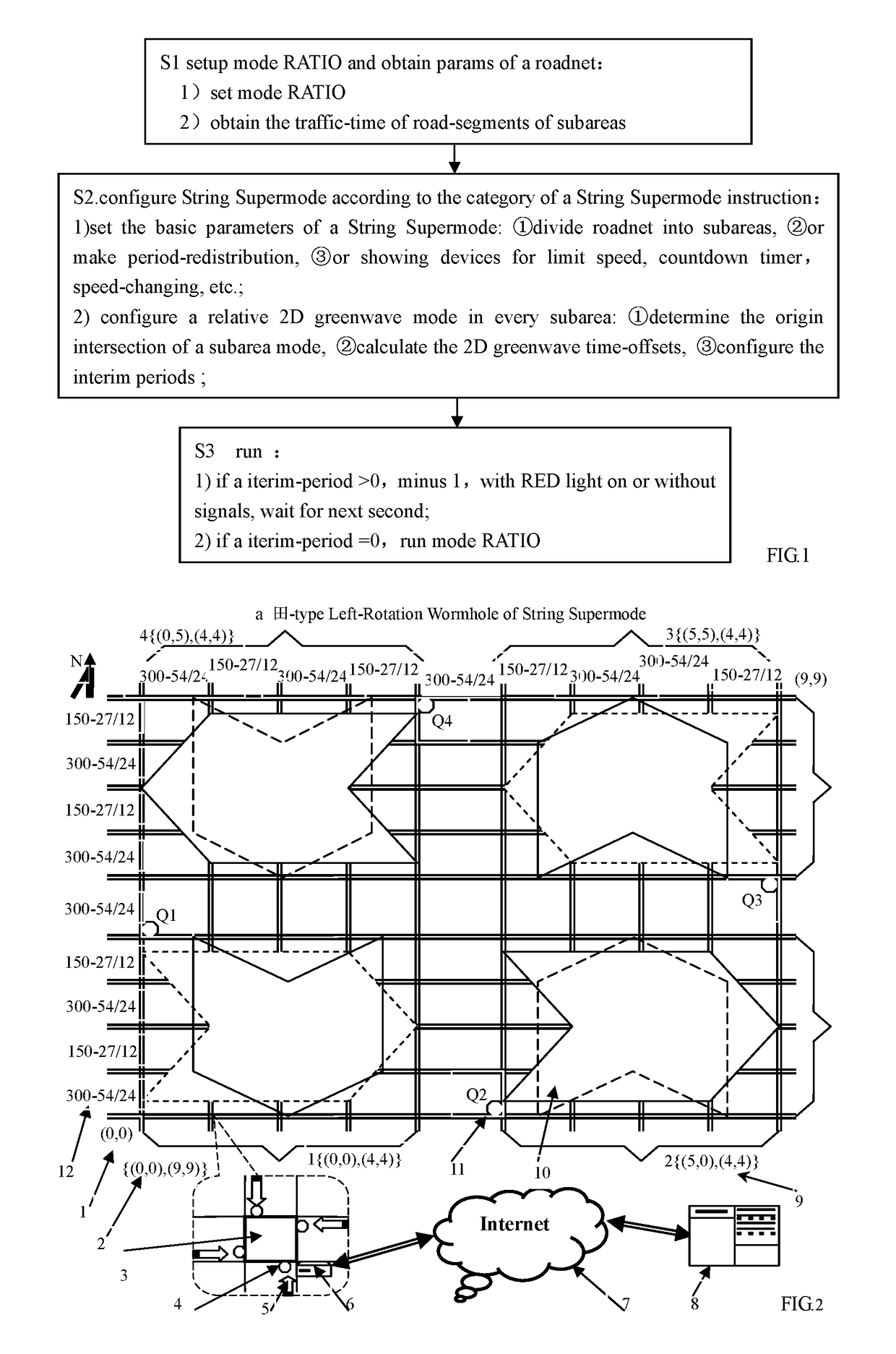
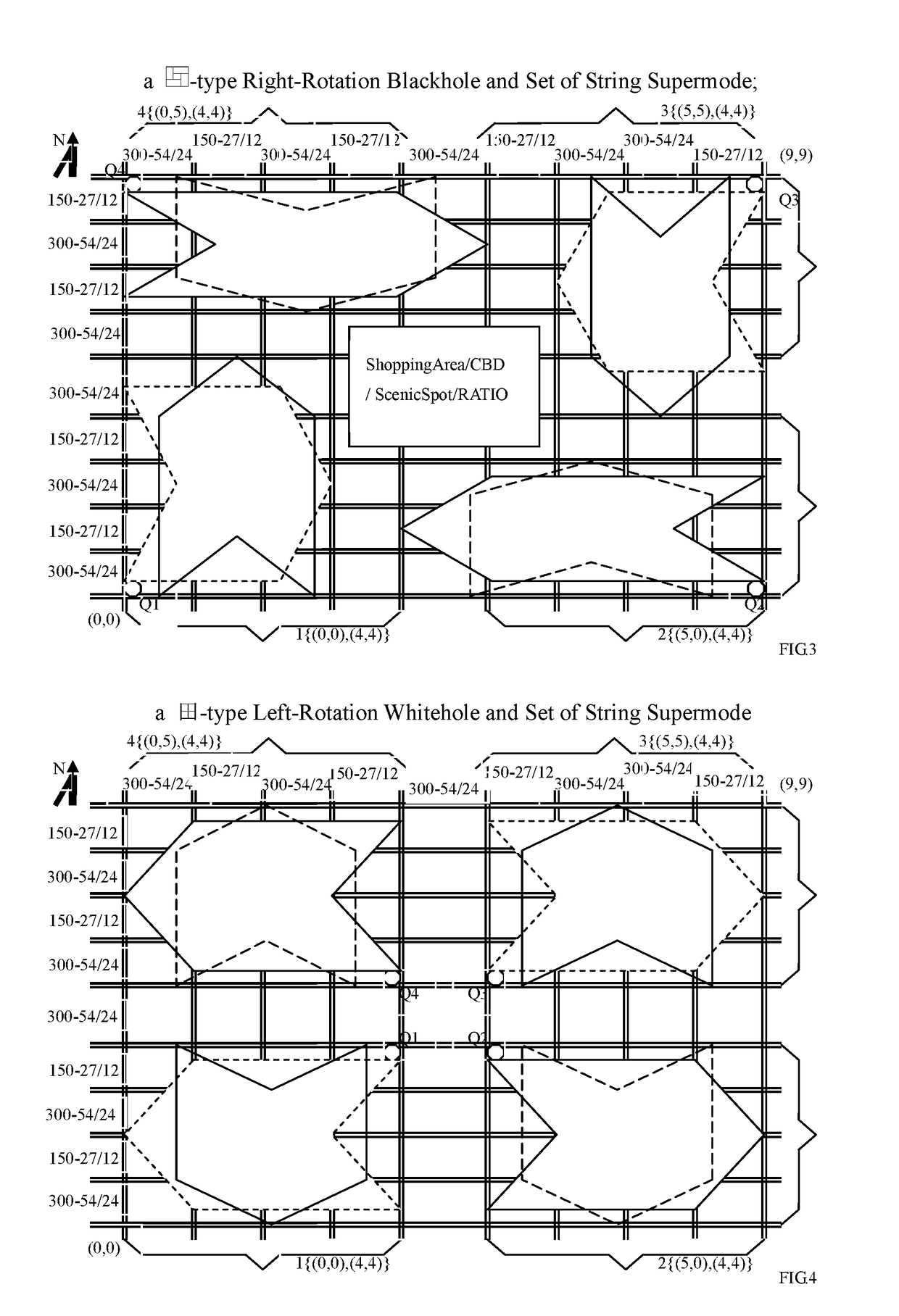
Traffic Signal String SuperMode Control Method
The invention relates to a traffic signal mode field, discloses a method for a supermode of traffic signal control: String Supermode, its main steps includes: 1)get String Supermode instruction; 2)set the basic parameters of String Supermode: subareas of a roadnet, period-redistribution; 3)set 2D greenwave mode in the relative subareas according to a String Supermode structure; 4)calculate the 2D greenwave time-offsets and their interim-period in each subarea; 5)run new mode after the above interim-period run out. The present invention realizes the effectiveness of signals equilibrium, high effieciency, multi-purpose, universe, easy to use: vehicles entering Wormhole-area from any direction and going to any position of the diagonal far-corner area, need 4.5 times of red lights on average, no matter how large a Wormhole-class controlled area and how big the number of intersections in the area are, multiple-class-change based on Wormhole-class presents the functions of the fast inhalation of vehicle flow from omni-direction, :the fast spitting out of vehicle flow to omni-direction, the relieving jammed vehicle flow during spitting out to omni-direction, the relieving jammed vehicle flow during inhalation from omni-direction, the coordinating artery roads to quickly shunting vehicle flow, and also, the vehicles' going through an area by only 1 red light of Pulsar-class; this String Supermodes are determined by only about 20 of parameters, can switch rapidly with no redundance, provide an area-type traffic control, analysis, operation basic mode.
Owner:MENG WEIPING
Method for fixing plant leaves on base material or handiwork and formed decorative material
The invention provides a method for fixing plant leaves on a base material or a handiwork and a formed decorative material. The method comprises the steps of carrying out hot pressing, drying and molding on plant leaves which are immersed and rinsed; coating an adhesive on the surface of the base plate; coating the adhesive on sticking surfaces of the treated plant leaves and sequentially sticking on the surface of a sheet material; and carrying out hot pressing and compounding to form a whole body, de-coloring the leaves and coating one layer of protective paint on the surface. According to the method disclosed by the invention, a product is peculiar; colors, veins, defects and wormholes of the blades and flowers sufficiently represent natural and original ecology styles, so as to bring about fresh, elegant, green and environment-friendly feelings to people; and the method disclosed by the invention provides the decorative material and the handiwork which are novel and wide in application.
Owner:张玉清
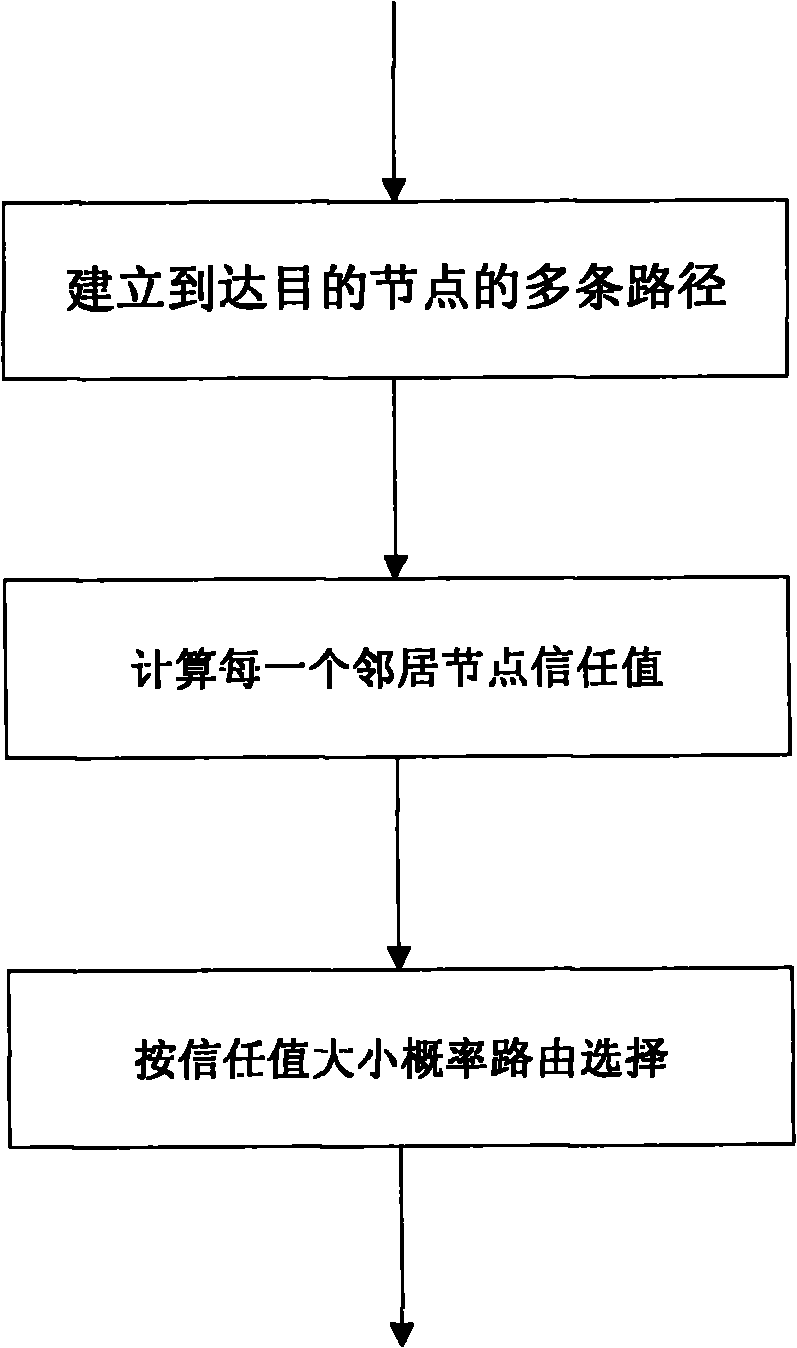
Wormhole attack defense method based on multipath routing and trust mechanism in Ad hoc network
ActiveCN102035726AResist attackVersatileNetwork topologiesData switching networksNODALTime information
The invention relates to a wormhole attack defense method based on multipath routing and a trust mechanism in an Ad hoc network, belonging to the technical field of information safety. The wormhole attack defense method comprises three steps: step 1, establishing multiple paths to destination nodes; step 2, calculating the trust value of each neighbor node of the nodes; and step 3, selecting routing according to the probability of the magnitude of the trust values. The safety problem is the key factor influencing the application and popularization of the Ad hoc network, and because the wormhole attack defense method does not need additional equipment such as a directional antenna, a global positioning system (GPS), special radio-frequency, an ultrasonic device and the like, does not need precise time information and nodal position information, and does not need overstrict assumption such as that a special guard node and an attack node have to lose packets and the like, the wormhole attack defense method has superior universality; and because a punishment mechanism is adopted for packet loss, the method also can resist black hole attack and grey hole attack. The wormhole attack defense method has better practical value and wide application prospects in the technical field of information safety.
Owner:BEIHANG UNIV
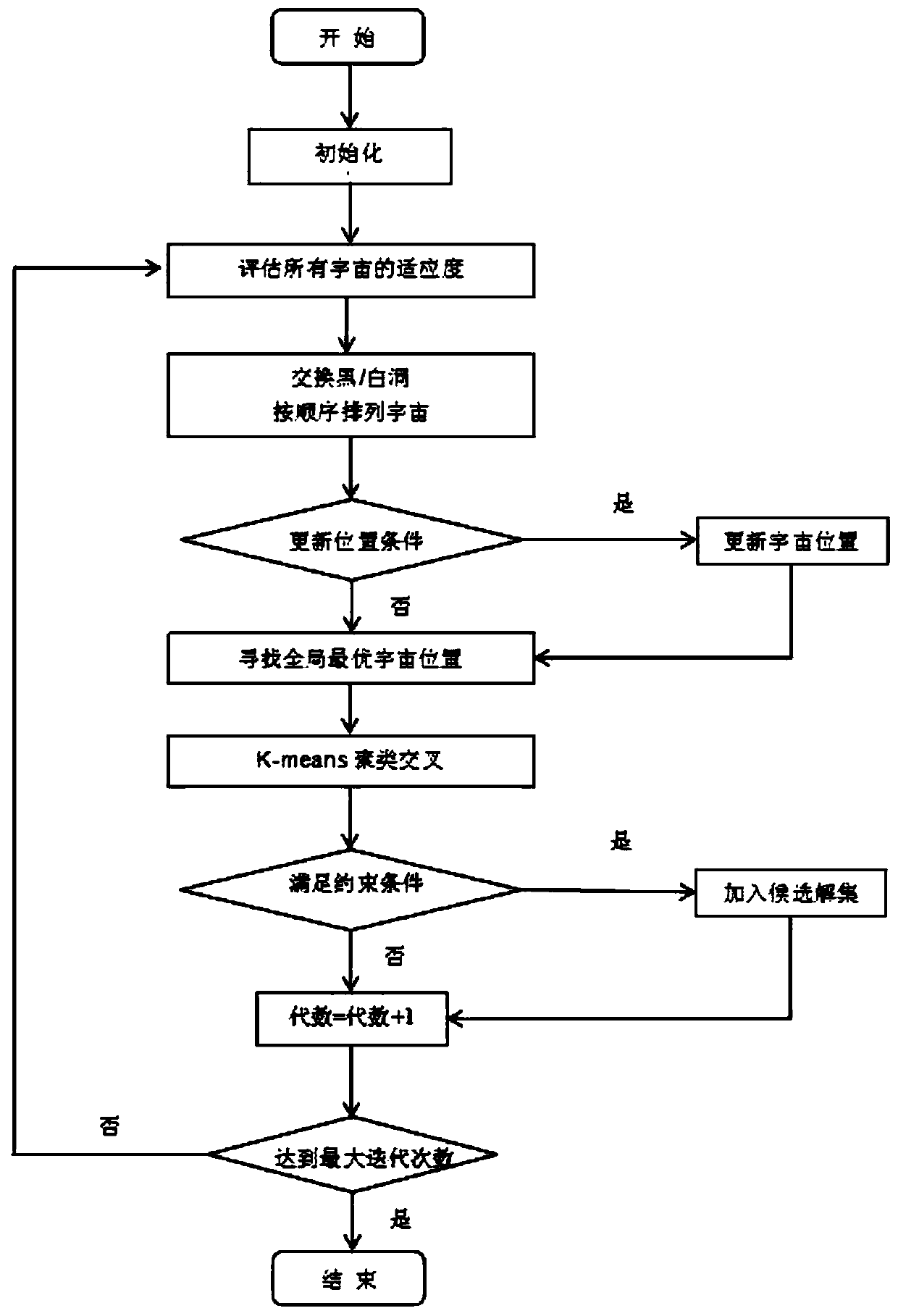
DNA storage coding optimization method based on K-means clustering multivariate universe algorithm
ActiveCN110533096AImprove average fitnessFast iterationCharacter and pattern recognitionDNA computersCluster algorithmDna encoding
The invention discloses a DNA storage coding optimization method based on a K-means clustering multivariate universe algorithm, and the method specifically comprises the steps: constructing an optimalDNA coding sequence meeting a combination constraint condition, firstly constructing a certain number of DNA sequences as an initial population, and carrying out the evaluation and sorting of the fitness of the population; secondly, optimizing the obtained DNA coding sequence by using a k-means clustering algorithm and wormhole intersection to obtain a DNA coding sequence with higher fitness; then, judging whether to add an alternative solution set or not according to constraints through constraint comparison; and finally, outputting an optimal DNA coding sequence. According to the method, DNA coding sequences with relatively good quantity can be searched.
Owner:DALIAN UNIV
Wireless sensor network safety positioning method
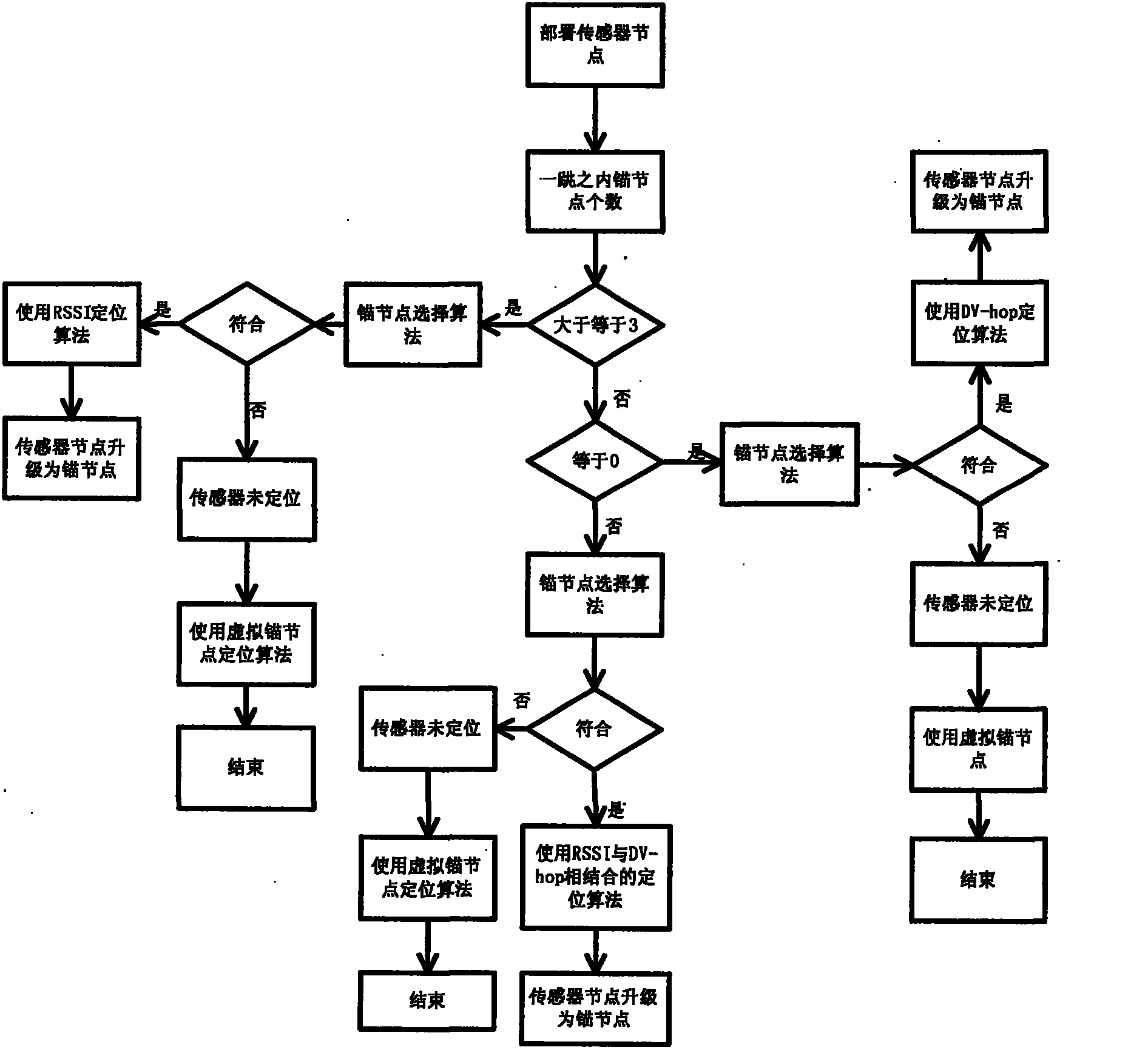
InactiveCN103297955AAvoid attackEffective positioningNetwork topologiesSecurity arrangementWireless sensor networkingSensor node
The invention provides a wireless sensor network safety positioning method based on multiple strategies, and belongs to the field of wireless communication. The method includes the steps that (1) under the condition that a malicious node attack does not exist, self-adaptation hybrid positioning of a sensor node and an anchor node is carried out, so position coordinate information of the sensor node is obtained, (2) under the condition that a malicious node launches a wormhole attack, whether the sensor node is under the wormhole attack is detected, if the result is positive, a step (3) is carried out, and if the result is negative, a step (4) is carried out, (3) the sensor node under the wormhole attack is eliminated, wherein the sensor node under the attack of the malicious node is obtained and then eliminated, (4) the self-adaptation hybrid positioning of the sensor node and the anchor node is carried out, so the position coordinate information of the sensor node is obtained. By means of the method, efficient self-adaptation positioning of the sensor node is achieved, and wormhole attacks are effectively avoided.
Owner:TIANJIN POLYTECHNIC UNIV
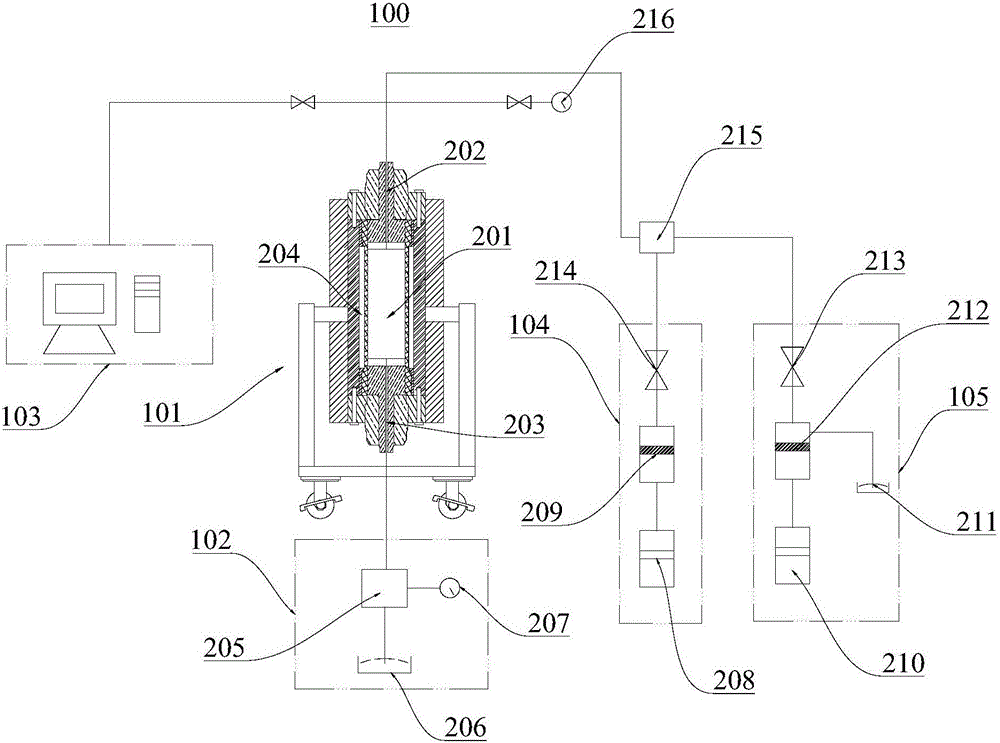
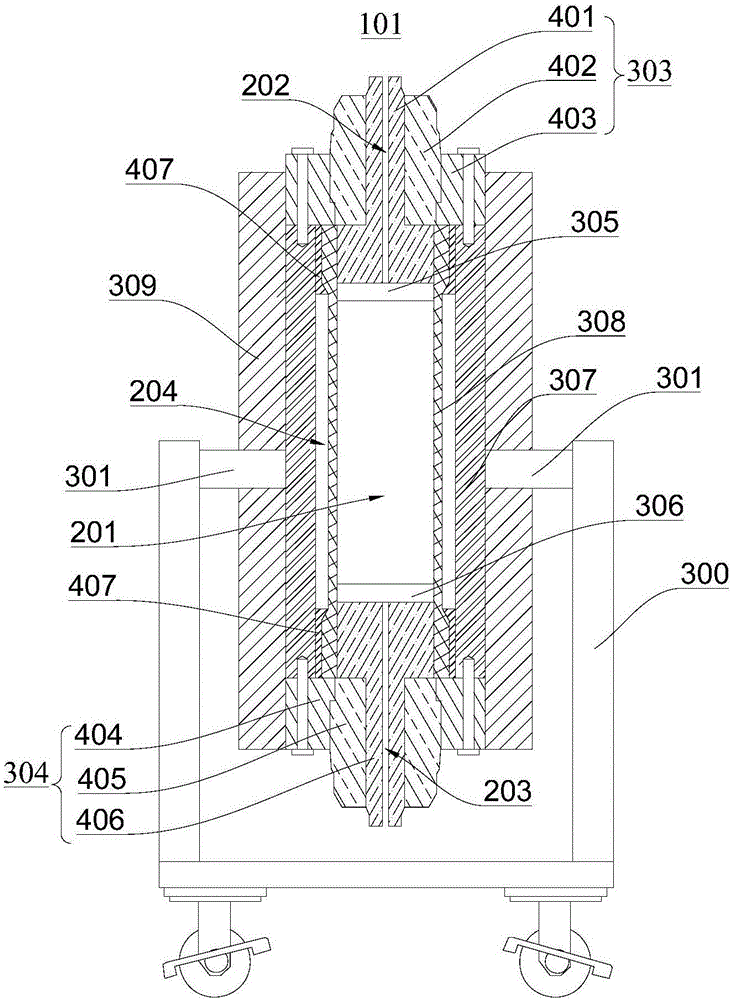
Simulating device for expanding full-diameter core acid wormhole and experimental method
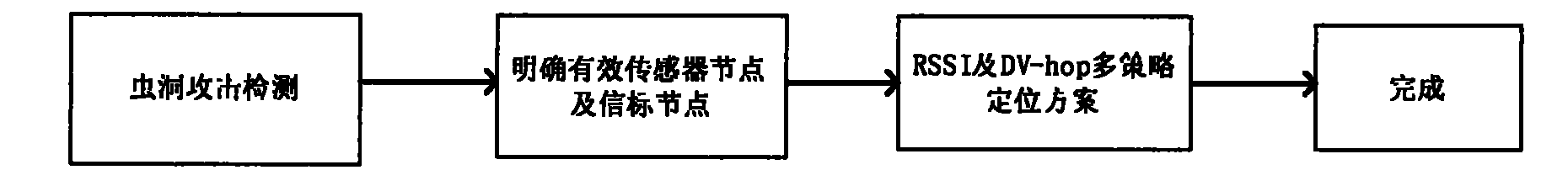
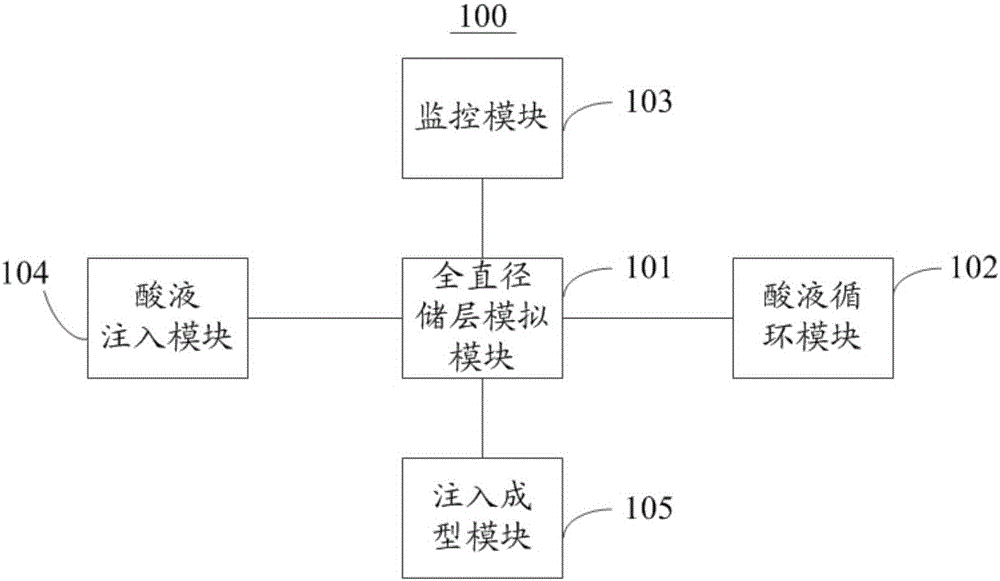
InactiveCN106198928AHigh simulationEffective simulationEarth material testingExperimental methodsWormhole
The invention discloses a simulating device for expanding a full-diameter core acid wormhole and an experimental method, and belongs to the fields of oil and gas reservoir capacity increasing revamp and oilfield chemistry. The simulating device for expanding the full-diameter core acid wormhole comprises an acid liquor injecting module, an acid liquor circulating module, an injection molding module, a monitoring module and a full-diameter reservoir simulating module. The expansion of the acid wormhole in a full-diameter oil and gas reservoir can be simulated efficiently, simply and conveniently by using the simulating device for expanding the full-diameter core acid wormhole, so that the true environment of a simulated rock stratum can be effectively simulated, and a positive guiding function is provided for mining of oil and gas.
Owner:SOUTHWEST PETROLEUM UNIV
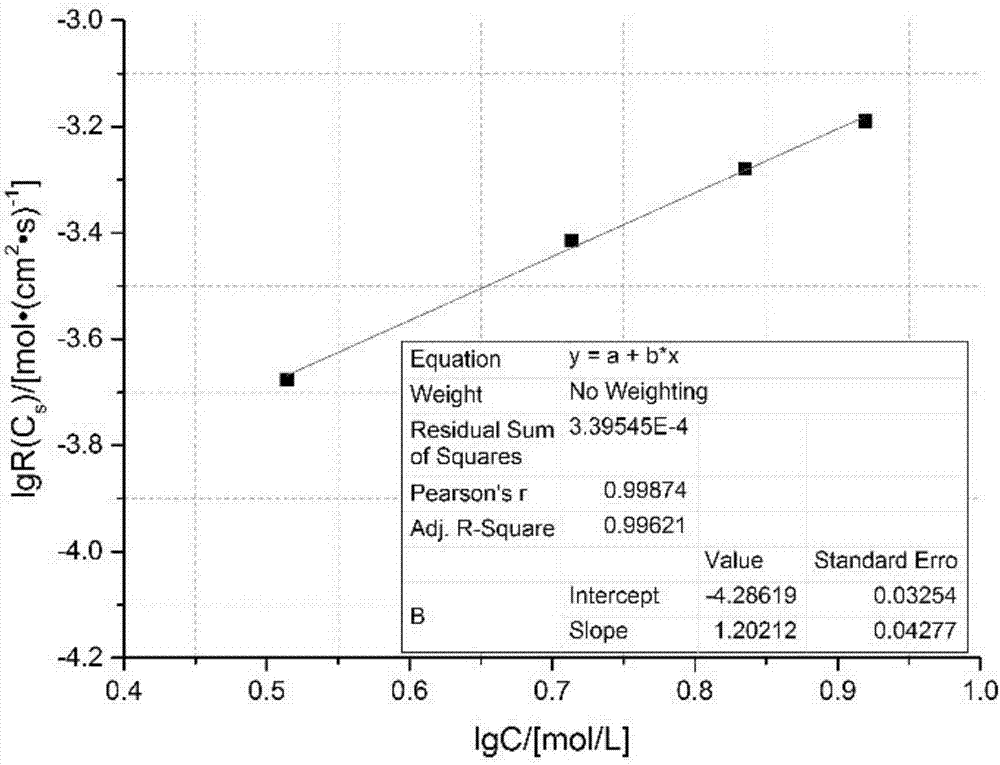
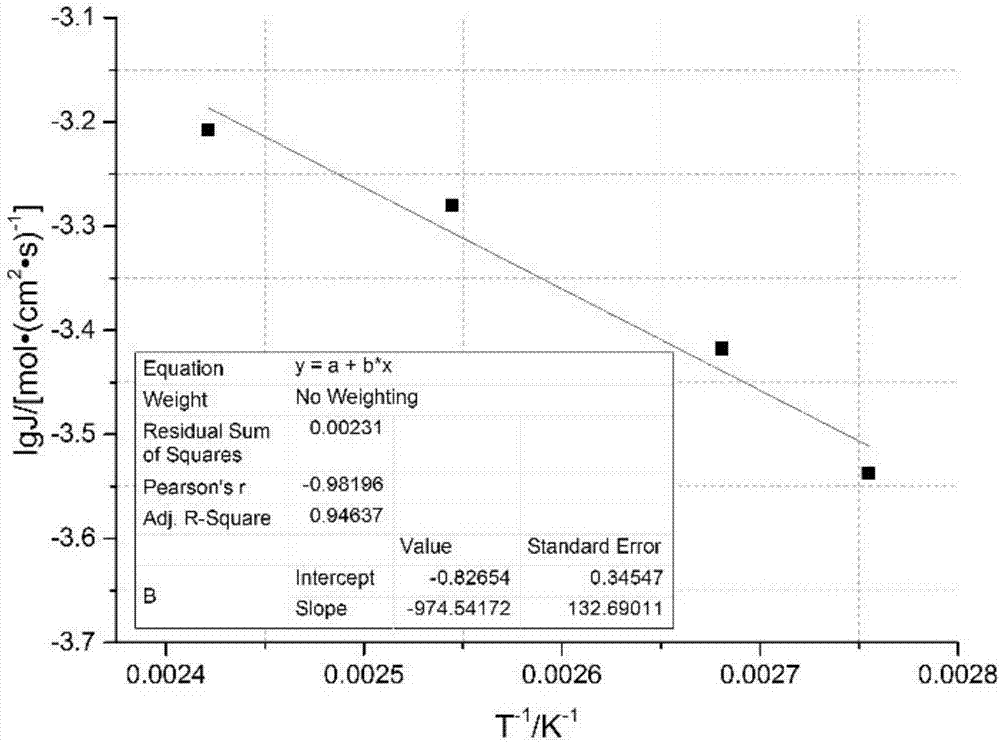
Full three-dimensional simulation method for acidification flow experiment
ActiveCN107577895ANon-destructiveGood compatibilitySpecial data processing applications3D modellingThree dimensional simulationThroat
The invention discloses a full three-dimensional simulation method for an acidification flow experiment. According to the method, a differential method is utilized to discrete a fluid seepage continuity equation and an acid-liquid mass diffusion reaction equation, and an H+ local equilibrium equation, a porosity change equation, a permeability change equation and a pore throat radius change equation are established at the same time; initial conditions and boundary conditions are substituted into the simulation equations; a simulation program is compiled by utilizing the equations, the initialconditions and the boundary conditions; 6, reservoir cores are scanned to obtain three-dimensional spatial distribution parameters of porosity; a three-dimensional spatial distribution model of the porosity is established, and the compiled program is utilized to achieve full three-dimensional numerical simulation of the acidification flow experiment on the basis of the established three-dimensional spatial distribution model of the porosity. According to the method, full three-dimensional numerical calculation is adopted, the calculation precision is effectively improved, and meanwhile the influence laws of each parameter on the development of wormholes are conveniently, quickly and accurately studied.
Owner:CHENGDU NORTH OIL EXPLORATION DEV TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com