Anti-attack reliable wireless sensor network node positioning method
A wireless sensor and positioning method technology, applied in the field of network information security, can solve the problems of increasing node positioning errors, etc., achieve the effects of reducing impact, simple steps, and reducing the possibility of missed or false detections
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
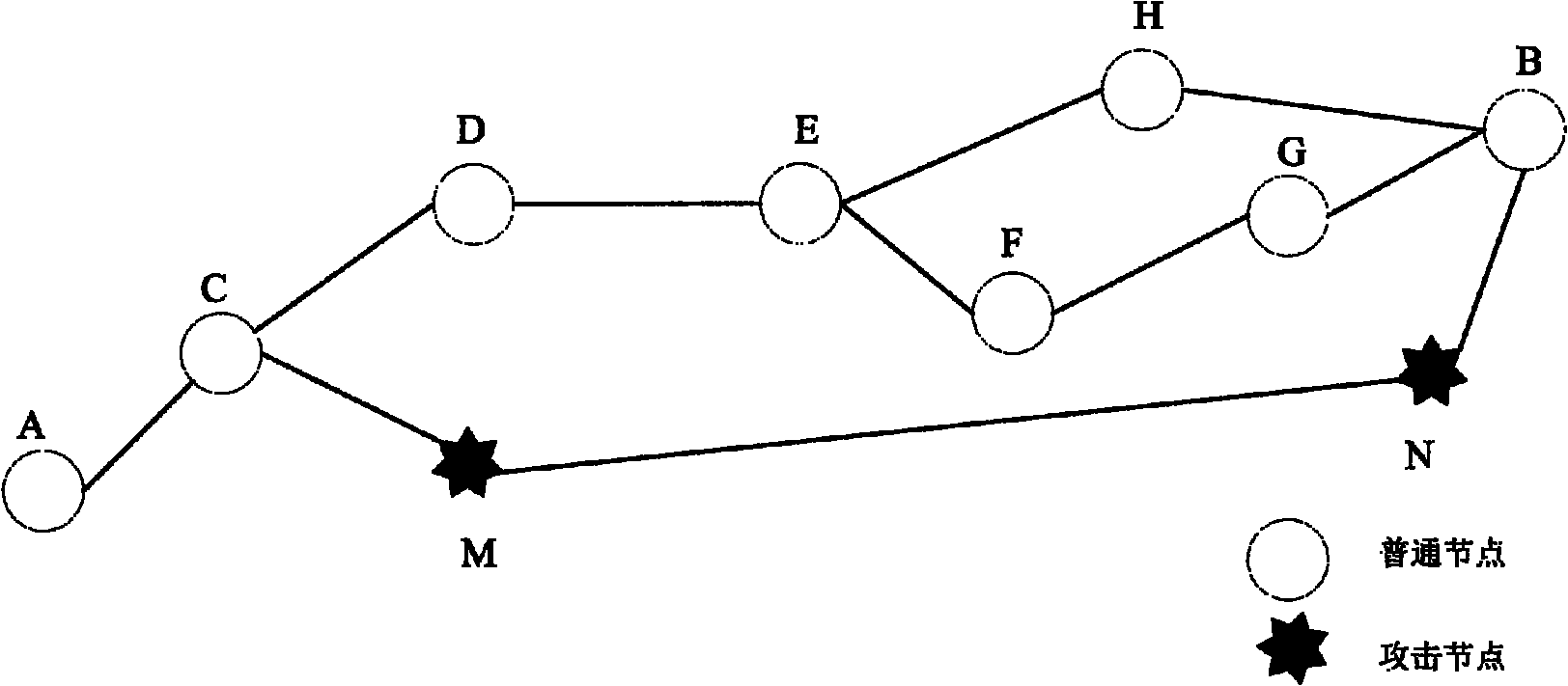
[0023] Embodiments of the present invention will be described in detail below with reference to the above description and accompanying drawings. The implementation of the present invention is based on the following prerequisites and network assumptions:
[0024] a. All legal nodes have a global symmetric key; b. Each node in the network has a unique ID number to distinguish its identity; c. The hash value H(ID) corresponding to the ID number of each beacon node All nodes are public; d. All nodes in the network have synchronous clocks, which provide conditions for calculating the propagation time of signals when detecting the distance between nodes.
[0025] 1. Implementation instructions for the minimum hop count phase between beacon nodes and other beacon nodes
[0026] At this stage, a symmetric key encryption system is introduced when calculating the minimum number of hops between beacon nodes, so that the location information sent by the beacon nodes can only be used by l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com