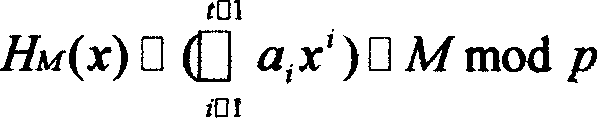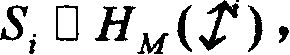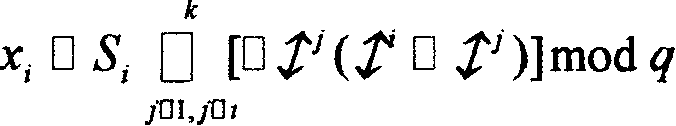Safety guide model for distributed identity authentication in mobile self-organizing network
A technology of mobile self-organization and security guidance, applied in user identity/authority verification, data exchange through path configuration, etc., can solve the problems of high computational cost, difficulty in practical use, and no security guidance model found, etc., to resist insects Hole attack or other replay attack, freshness guarantee, load reduction effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0008] 1. Establishment of Threshold Digital Signature Key and Import of Signature Mechanism
[0009] Before introducing the security boot model proposed by the present invention in detail, the relevant parameters are described in advance as follows:
[0010] p, p': 10 200 A large prime number that satisfies p□1(mod8) and p′□1(mod8);
[0011] q: a large prime factor of p′□1;
[0012] h:
[0013] g: g h (p′□1) / q mod p′, where
[0014] y: y g m mod p, where m is the secret key and y is the public key:
[0015] Primitive elements of the finite field GF(p′);
[0016] H(m): a one-way hash function on the finite field GF(p′);
[0017] where the parameters y, p′, q, h, g, and is public.
[0018] 1.1 The establishment process of the threshold digital signature key
[0019] A polynomial H of degree t-1 is secretly selected by the secure boot server over the finite field GF(p′) M (x) and satisfy H M (0)□M, as follows:
[0020]
[0021] where a i (i□1,...,t□1) i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com