Intelligent entrance guard system for mobile terminal user verification
An intelligent access control system and user verification technology, applied in user identity/authority verification, instruments, time registers, etc., can solve the problems of high access control cost, inconvenient key carrying, low security, etc., and achieve convenient management and use costs. Low, high safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
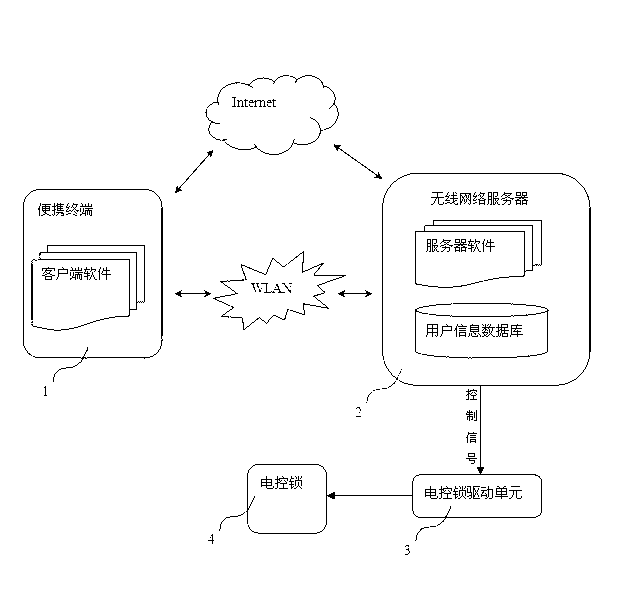
[0026] The hardware part of the present invention is composed of a mobile intelligent communication terminal (1), a wireless network server (2), an electric control lock drive unit (3) and an electric control lock (4).
[0027] Terminals are intelligent electronic devices such as smart phones, portable computers, PDAs, and tablet computers. The present invention installs client software on general intelligent terminal devices to provide client functions such as human-computer interaction interface, user information reading, and data processing and transmission.
[0028] The server is an embedded computer system with wireless routing function, which is composed of MIPS microcontroller (MCU) chip with integrated routing network communication function such as Broadcom or Atheros, peripherals equipped with memory, interface and other modules. Install and run server-side software on the server to complete functions such as user authentication and management.
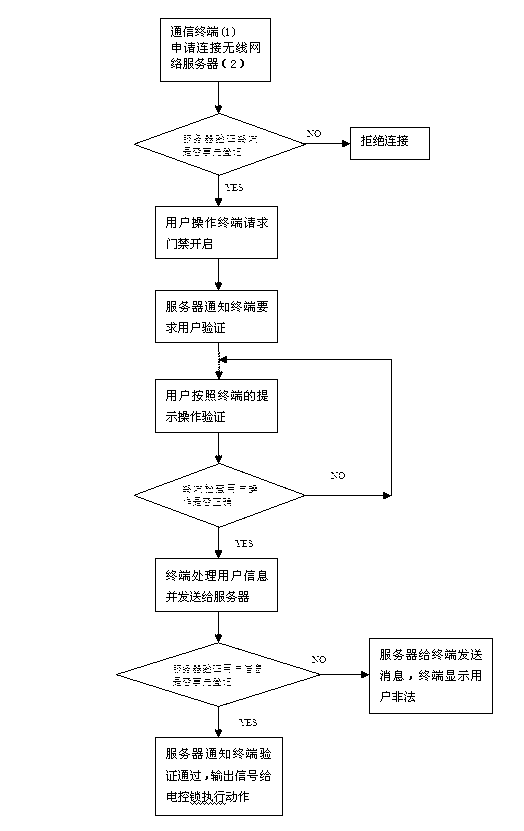
[0029] The electric c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com