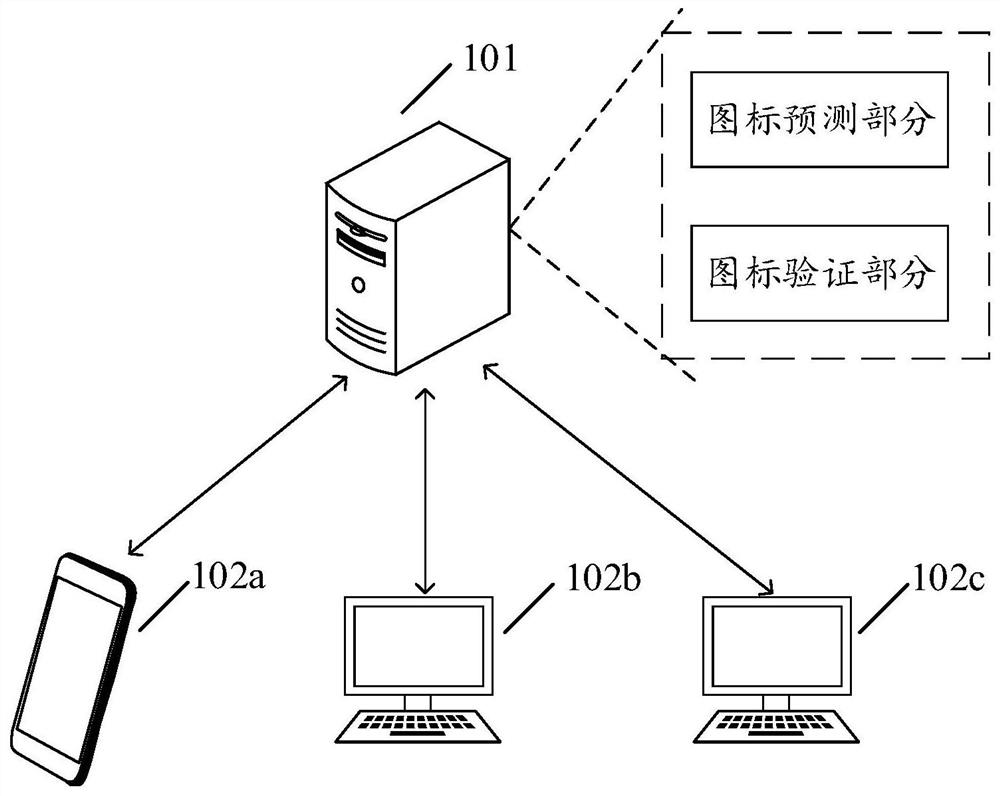
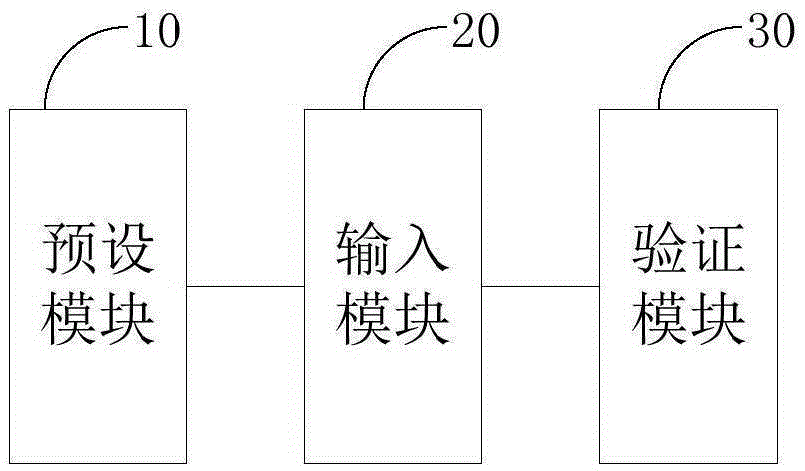
Patents
Literature
70results about How to "Implement two-factor authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
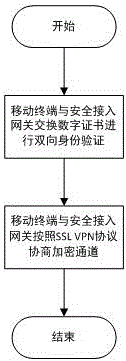
Terminal security authentication method, device and system
ActiveCN105101194AImplement two-factor authenticationUser identity/authority verificationSecurity arrangementOperational systemUser identifier
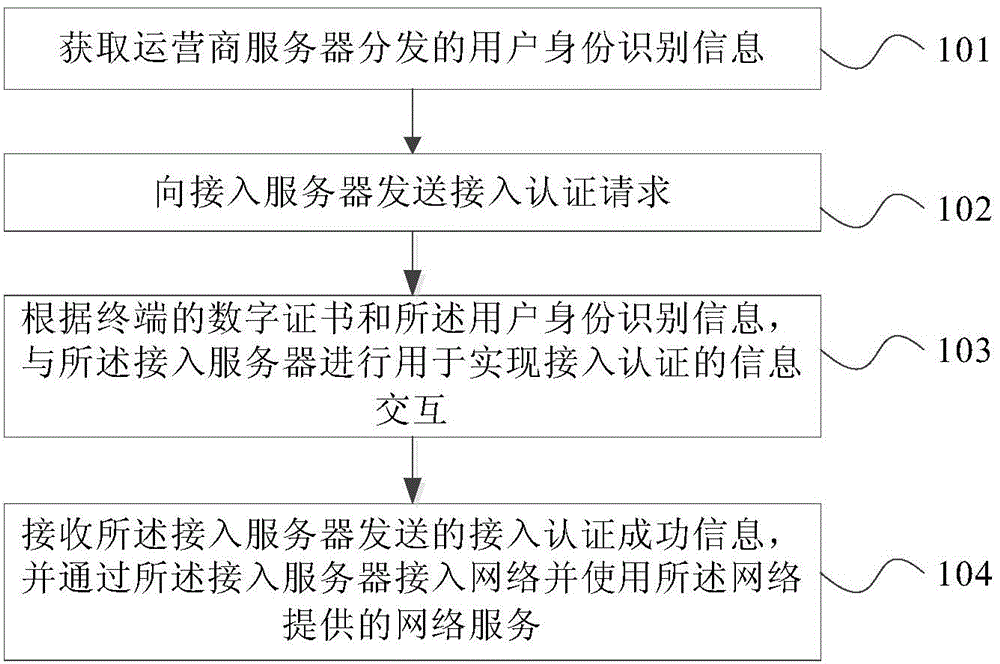
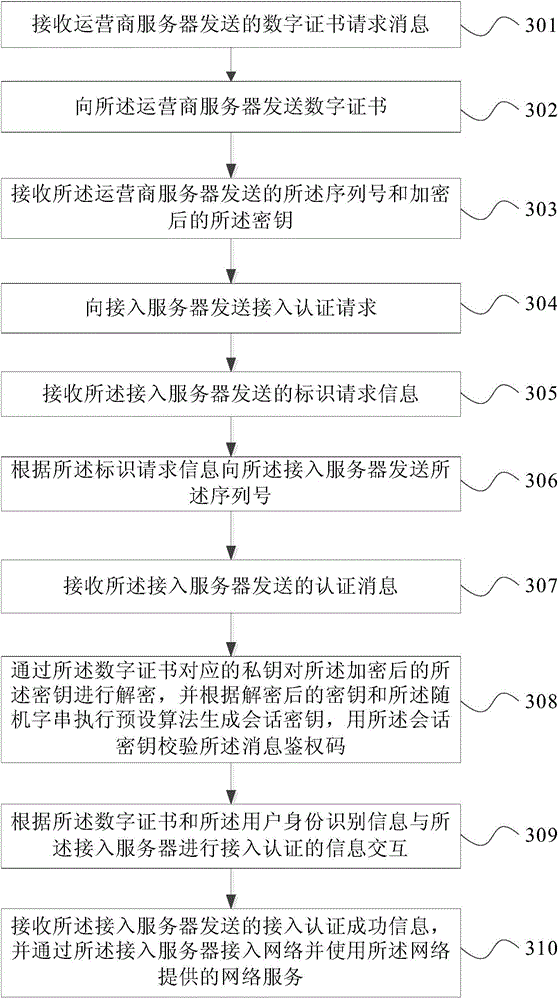
Provided in an embodiment of the present invention are a secure terminal authentication method, device and system, the method comprising: acquiring user identity information distributed by a carrier server, the user identify information comprising a serial number uniquely identifying the identity of a user and a key; transmitting an access authentication request to an access server; according to the digital certificate of the terminal and the user identify information, conducting information interaction with the access server for access authentication; and receiving the access authentication success information transmitted by the access server, accessing a network via the access server, and utilizing the network service provided by the network. The embodiment of the present invention realizes dual authentication of a terminal identifier and a user identifier, thus solving the problem that terminal access authentication using software user identity information is more dependent on the security capability of the operating system of the terminal.
Owner:HUAWEI TECH CO LTD
Authentication method, electronic equipment and authentication server
InactiveCN101764823AImprove securityImplement two-factor authenticationTransmissionUser inputPassword
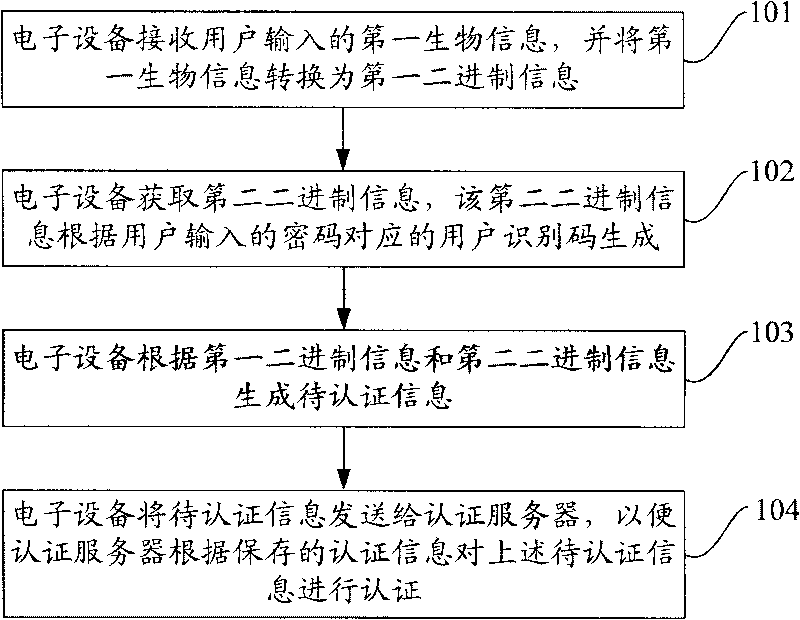
The embodiment of the invention provides an authentication method, electronic equipment and an authentication server. The authentication method includes the steps of receiving first biological information input by a user and transforming the first biological information into first binary information; obtaining second binary information which is generated according to a user identification code corresponding to a password input by the user; generating to-be-authenticated information according to the first binary information and the second binary information; sending the to-be-authenticated information to the authentication server so as to authenticate the to-be-authenticated information according to stored authentication information. The embodiment of the invention realizes double-factor authentication based on the password and the biological information, thereby improving the security of a data card.
Owner:HUAWEI DEVICE CO LTD
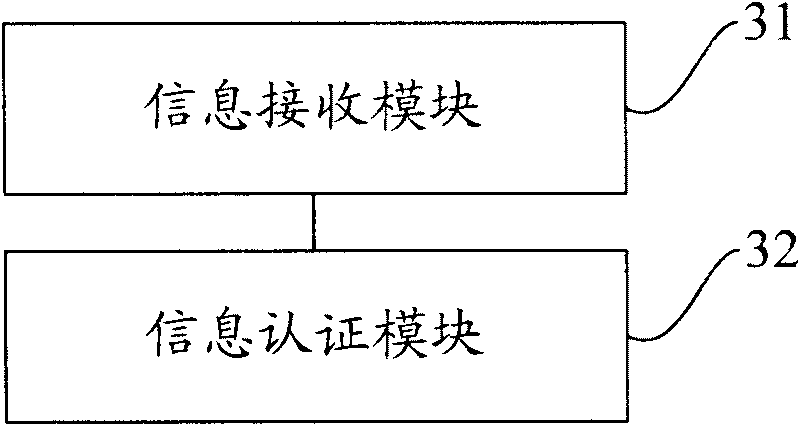
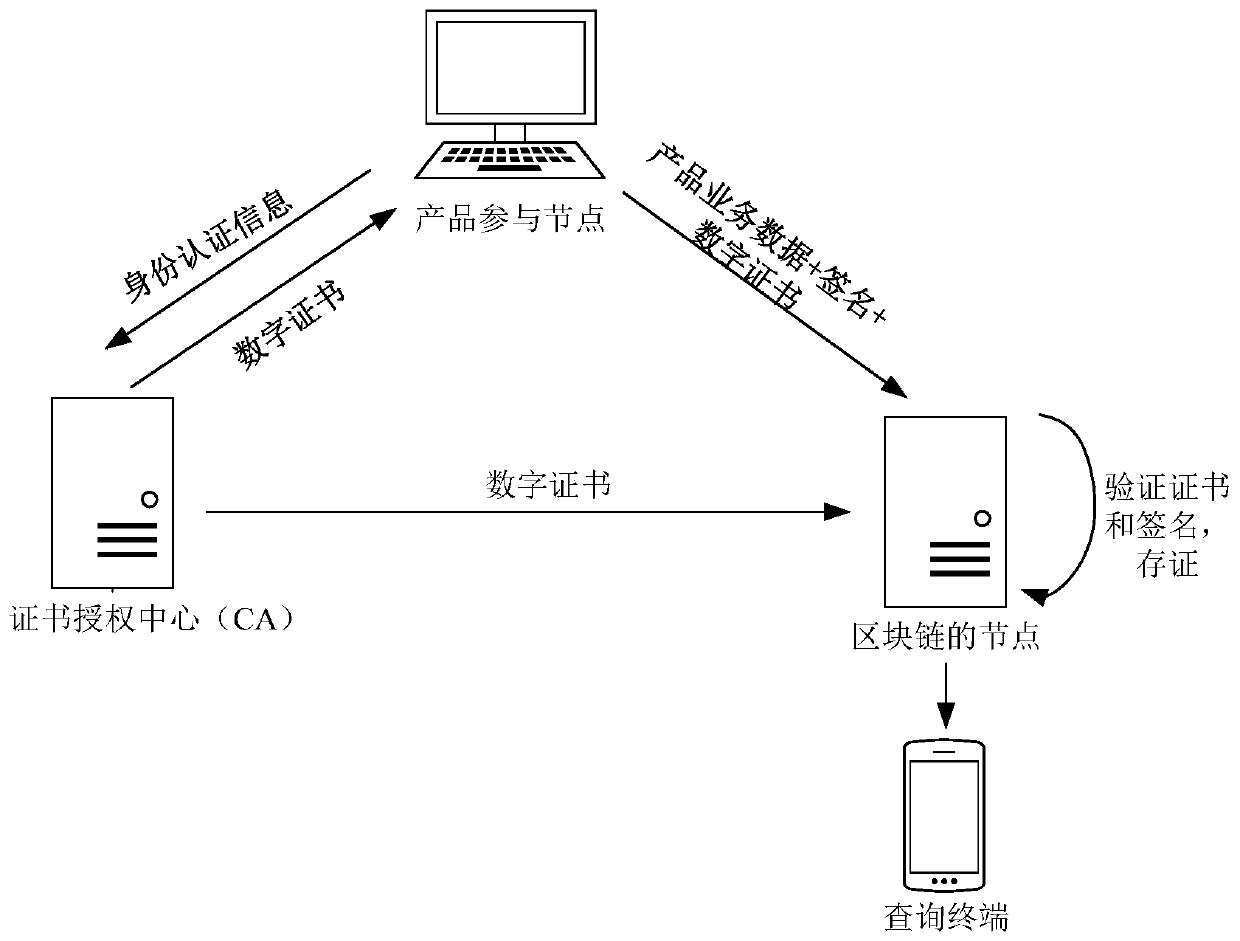
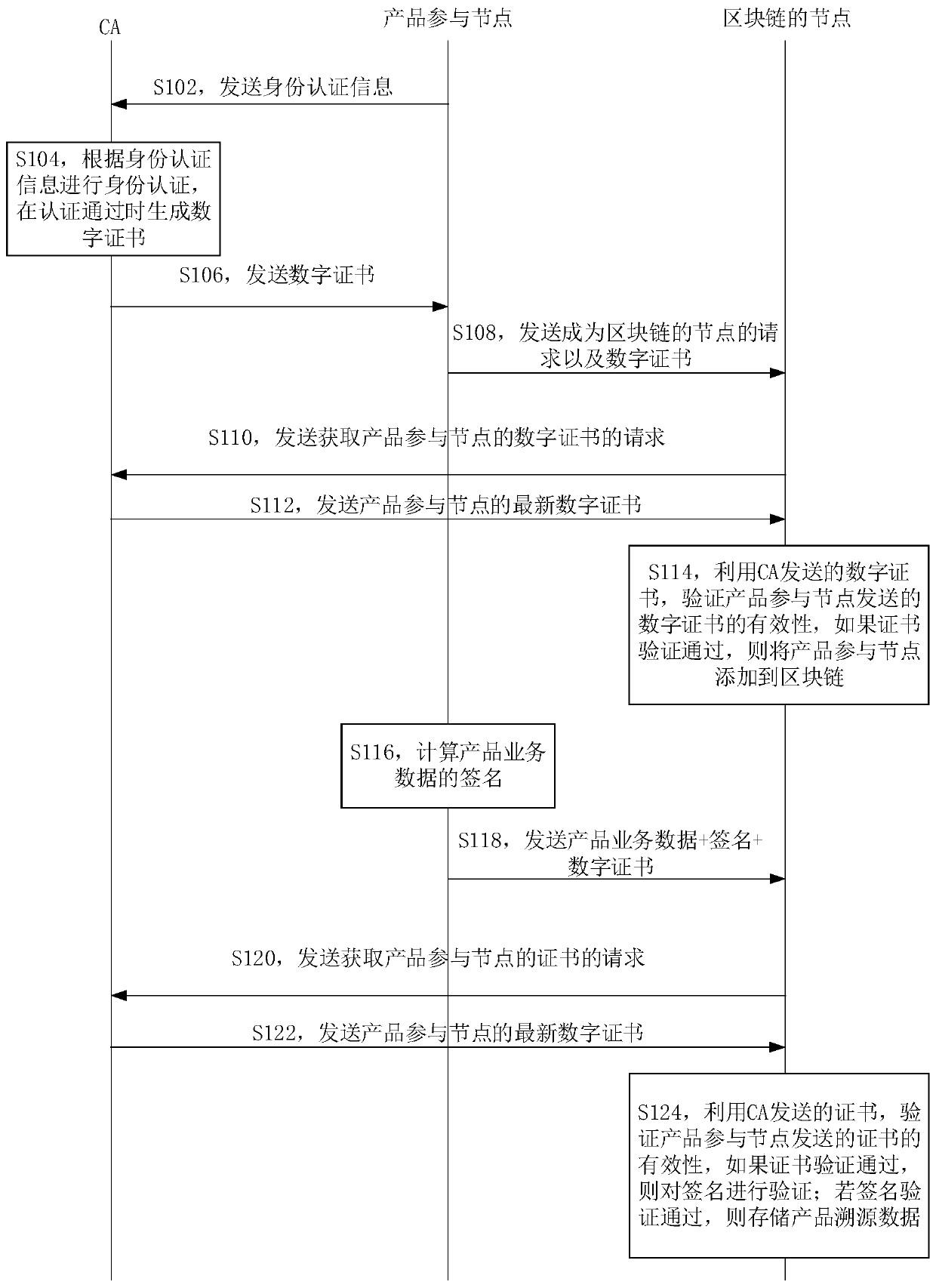
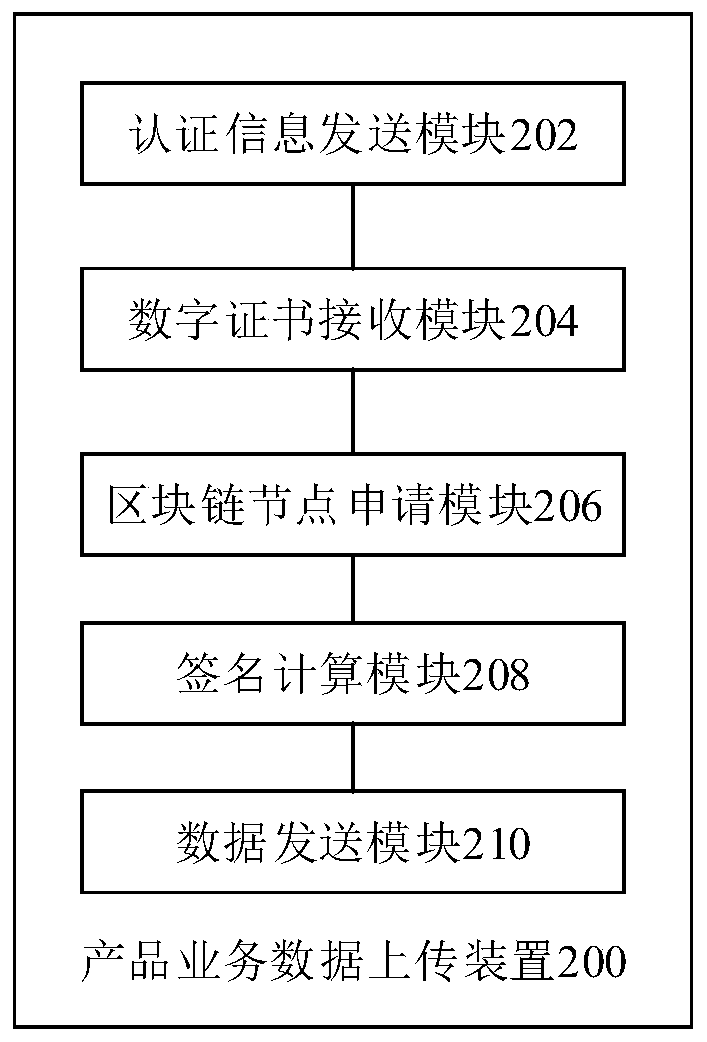
Product service data uploading method and device, product service data evidence storage method and device, equipment and medium
PendingCN110874747AThe certification result is accurateAbundant resourcesUser identity/authority verificationDatabase distribution/replicationBlockchainEngineering
One or more embodiments of the invention disclose a product service data uploading method, a product service data storage method, a product service data storage device, product service data storage equipment and a medium. The product service data uploading method comprises the following steps: sending identity authentication information of a product participation node to a certificate authority CA; receiving a digital certificate sent by the CA, wherein the digital certificate is generated by authenticating the product participation node by the CA according to the identity authentication information; according to the digital certificate, applying for the product participation node to become a node of a block chain; and after the product participation node becomes the node of the block chain, calculating the signature of the product service data for the product service data to be uploaded each time, and sending the product service data, the signature and the digital certificate to the nodes of the block chain except the product participation node.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Key generation and distribution method for wireless communication system
ActiveCN107196920AImplement two-factor authenticationTransmissionCommunications securityCommunications system
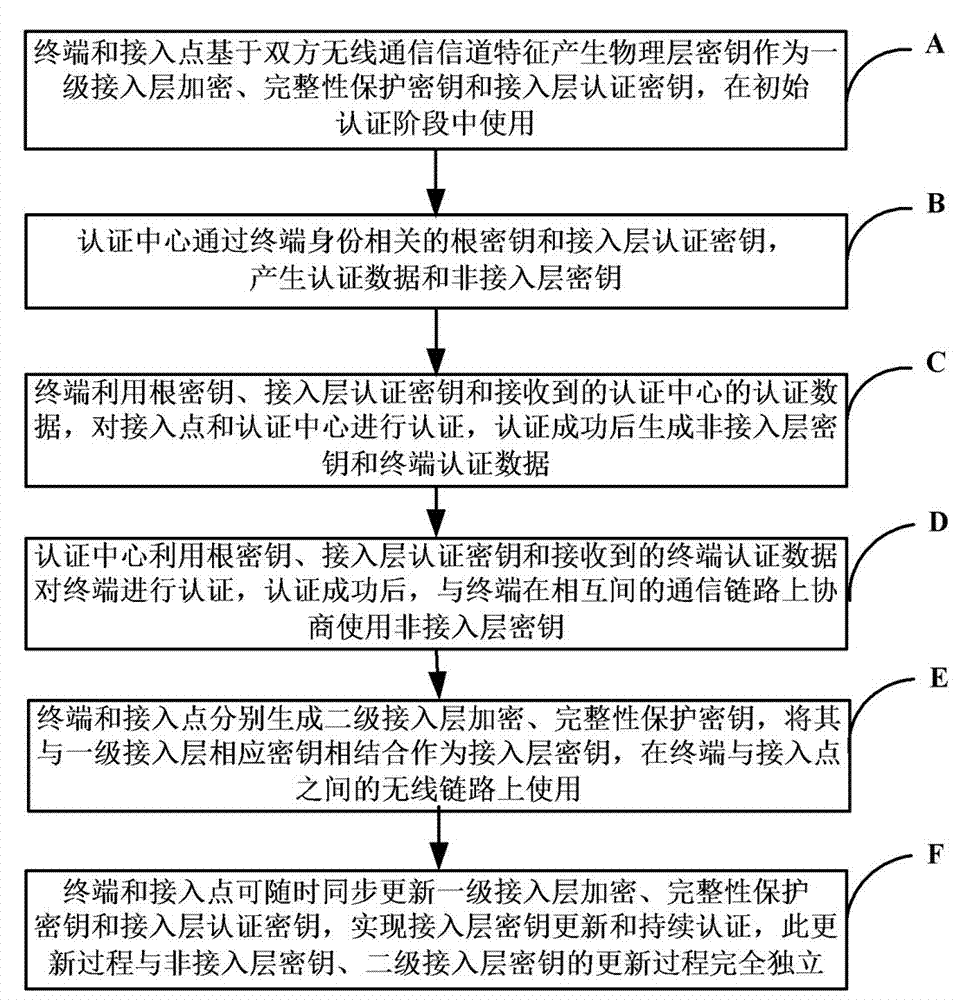
The invention relates to the technical field of communication security, and more particularly to a key generation and distribution method for a wireless communication system. The key generation and distribution method comprises the steps that: a terminal and an access point generate physical layer keys based on wireless communication channel features of the two parties; an authentication center generates authentication data and a non-access-layer key by means of a root key associated with identity of the terminal and an access-layer authentication key; the terminal authenticates the access point and the authentication center by utilizing the root key, the access-layer authentication key and the received authentication data of the authentication center; the authentication center authenticates the terminal by utilizing the root key, the access-layer authentication key and received terminal authentication data; the terminal and the access point each generates a secondary access-layer encryption and integrity protection key; and the terminal and the access point can update a primary access-layer key and the access-layer authentication key synchronously at any time, and realizes updating and continuous authentication of the access-layer keys. The key generation and distribution method utilizes the uniqueness, reciprocity and time-varying property of the wireless channel, generates the physical layer keys at the terminal and the access point separately, introduces the physical layer keys into the access-layer keys and the authentication keys, realizes dual authentication of identity and path, and can prevent the attack pattern of acquiring the access-layer keys from a non-access layer.
Owner:THE PLA INFORMATION ENG UNIV
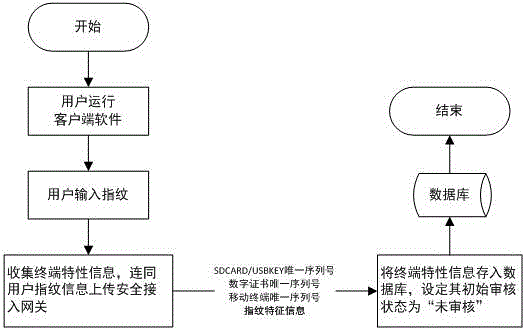
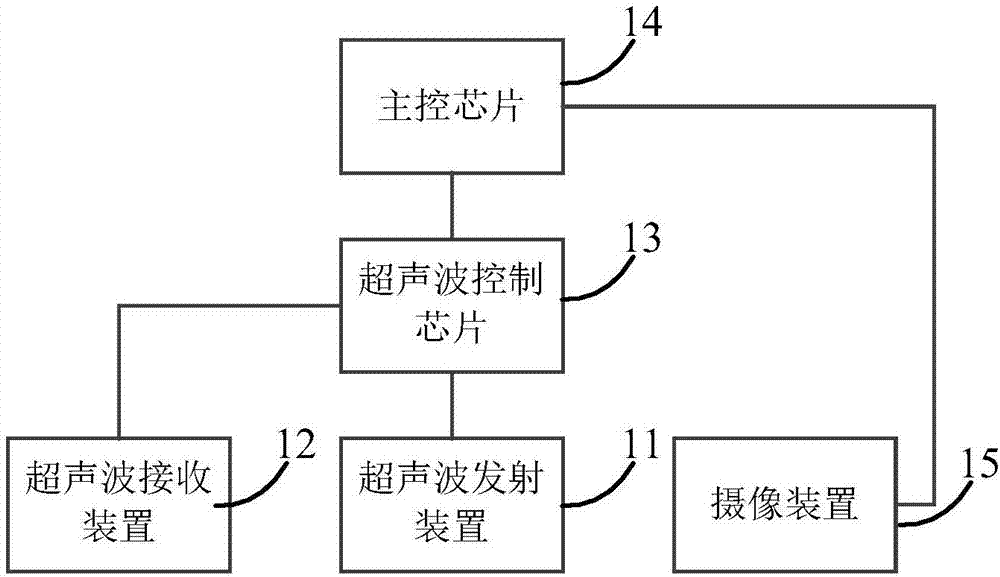
Mobile terminal safety access authentication method in combination with fingerprint
ActiveCN106488452APrevent unauthorized accessEnsure safetyDigital data authenticationSecurity arrangementIdentity recognitionInformation access
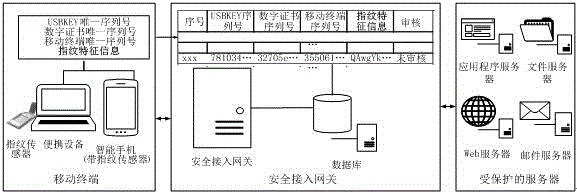
The invention provides a mobile terminal safety access authentication method in combination with fingerprint. The method comprises the four steps of establishing an encryption channel, user registering, user information checking and user business accessing. A client collects terminal feature information which comprises a USBKEY sequence number, a digital certificate sequence number, a mobile terminal sequence number and user fingerprint feature information, and the terminal feature information is uploaded to a safety access gateway through the encryption channel; the safety access gateway verifies the integrity and validity of the terminal information, and decides whether the terminal can access a protected server according to a verification result. The fingerprint recognition technology is combined with the traditional identity recognition mode, so that the medium for marking the identity is directly related to the natural person, the identity recognition and the recognized person are really corresponding to each other, the security level of the mobile terminal information access is effectively improved, and the convenient mobile technology can be facilitated to play effect in the information application.
Owner:JIANGSU ELECTRIC POWER CO +1
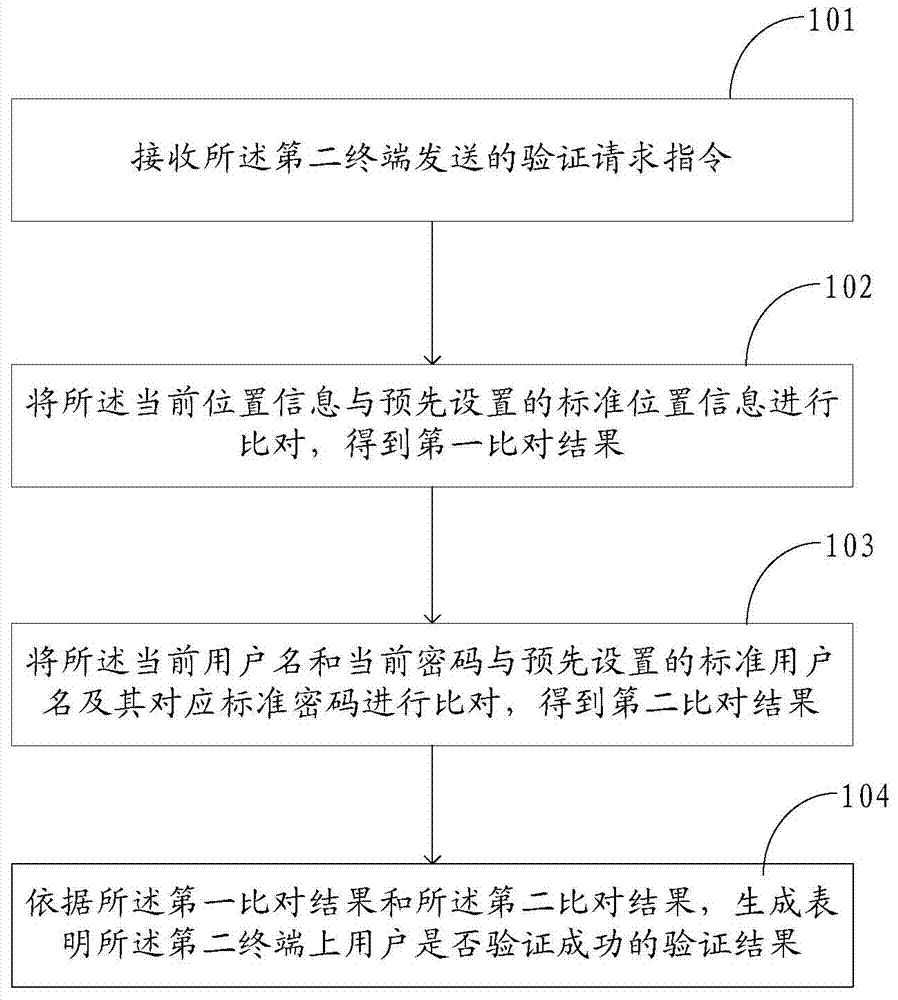
Verification method and device
ActiveCN103973711AImplement two-factor authenticationImprove securityTransmissionValidation methodsFinancial transaction
The invention discloses a verification method and device applied to a first terminal. The method comprises the following steps: receiving a verification request command transmitted by a second terminal, wherein the verification request command at least comprises current position information, current user name and current code of the second terminal; comparing the current position information with the standard position information to obtain a first comparison result; comparing the current user name and current code with the standard user name and corresponding standard code to obtain a second comparison result; and according to the first comparison result and second comparison result, generating a verification result which indicates whether the verification of the user on the second terminal is successful. The validity verification on the position information of the second terminal is performed while implementing user name code verification so as to implement dual verification on financial transactions of the user, so that the financial transactions can not be performed when one of the verifications is not successful, thereby enhancing the safety of the financial transactions of the user.
Owner:AGRICULTURAL BANK OF CHINA
Password system and encryption and decryption method
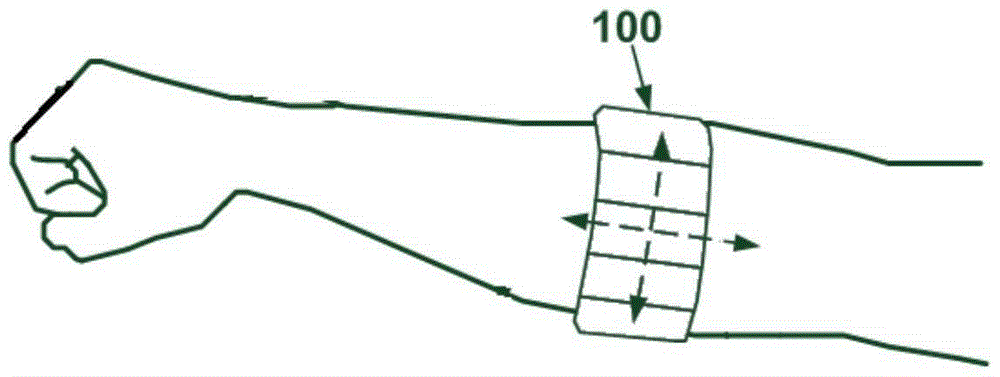
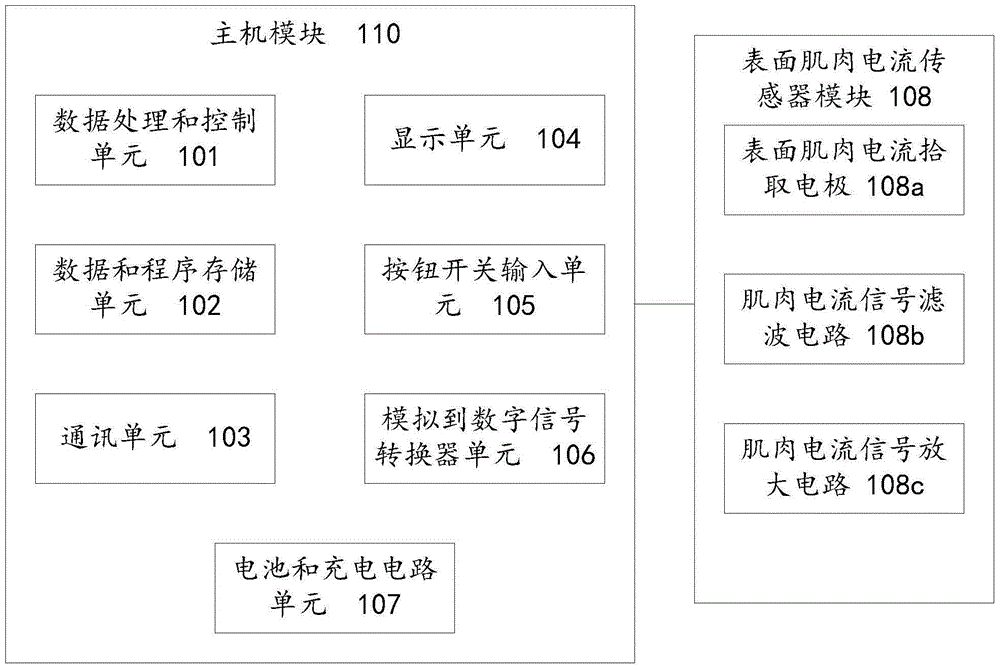
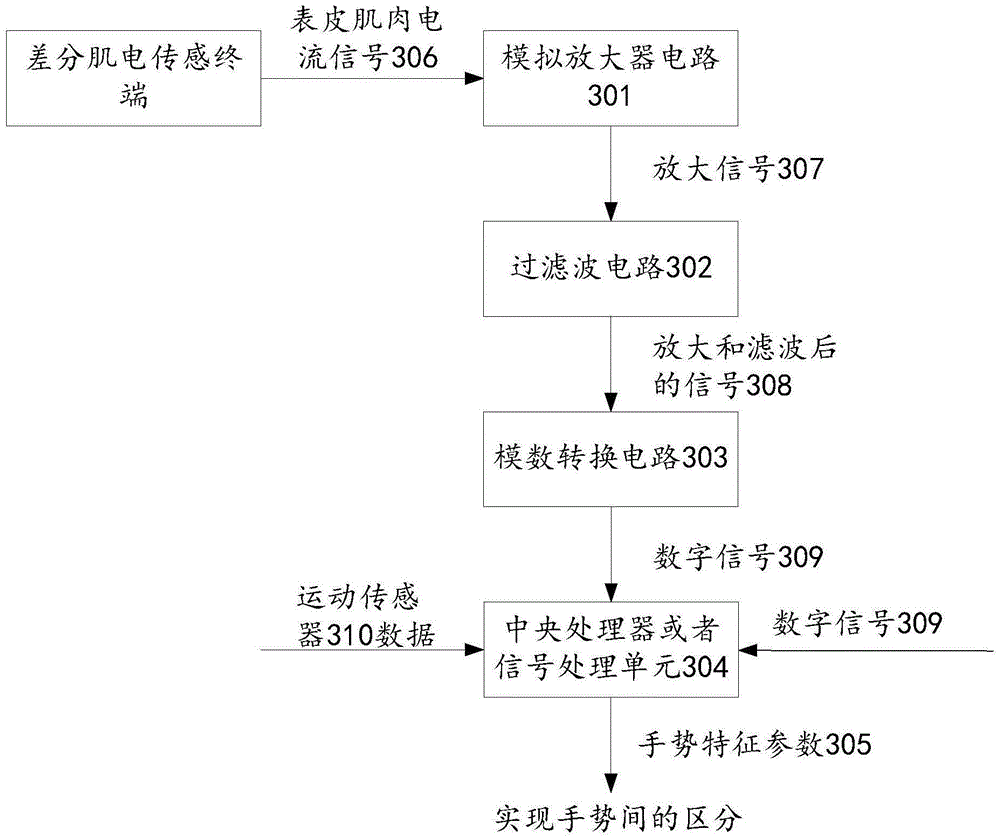
ActiveCN105243312AImprove data securityImplement two-factor authenticationDigital data authenticationHuman bodyPassword
The invention discloses a password system and an encryption and decryption method. The password system comprises a muscle current sensing terminal, a password setting module and a password identification module, wherein the muscle current sensing terminal is used for collecting muscle current on the surface of the skin of a human body and extracting a muscle current signal characteristic value; the password setting module is used for generating a password according to a muscle current signal acquired by the muscle current sensing terminal; the password identification module is used for performing comparison and matching analysis on the muscle current sensing terminal acquired by the muscle current sensing terminal and a set password so as to verify the identity of a user. According to the password system provided by the invention, the password is obtained according to the muscle current signal, and the data security can be improved.
Owner:SHANGHAI OYMOTION INFORMATION TECH
Video data processing method and device, computer and readable storage medium
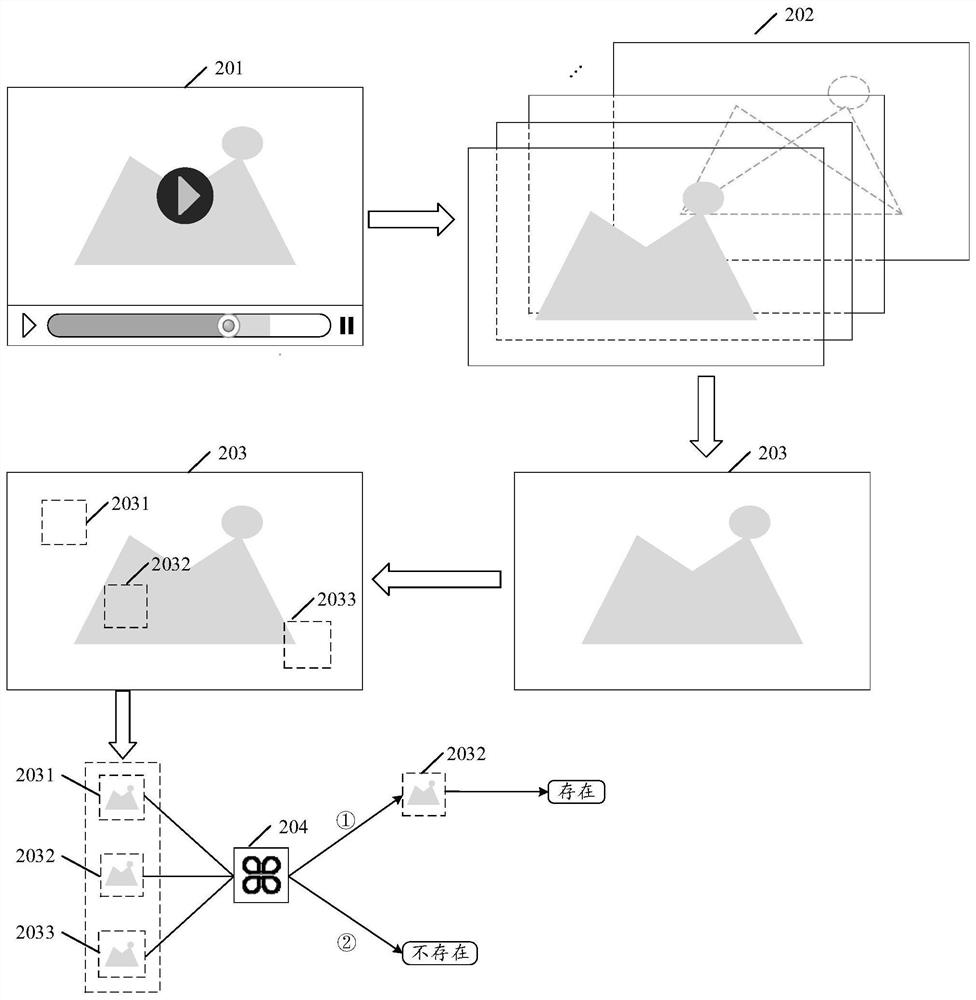
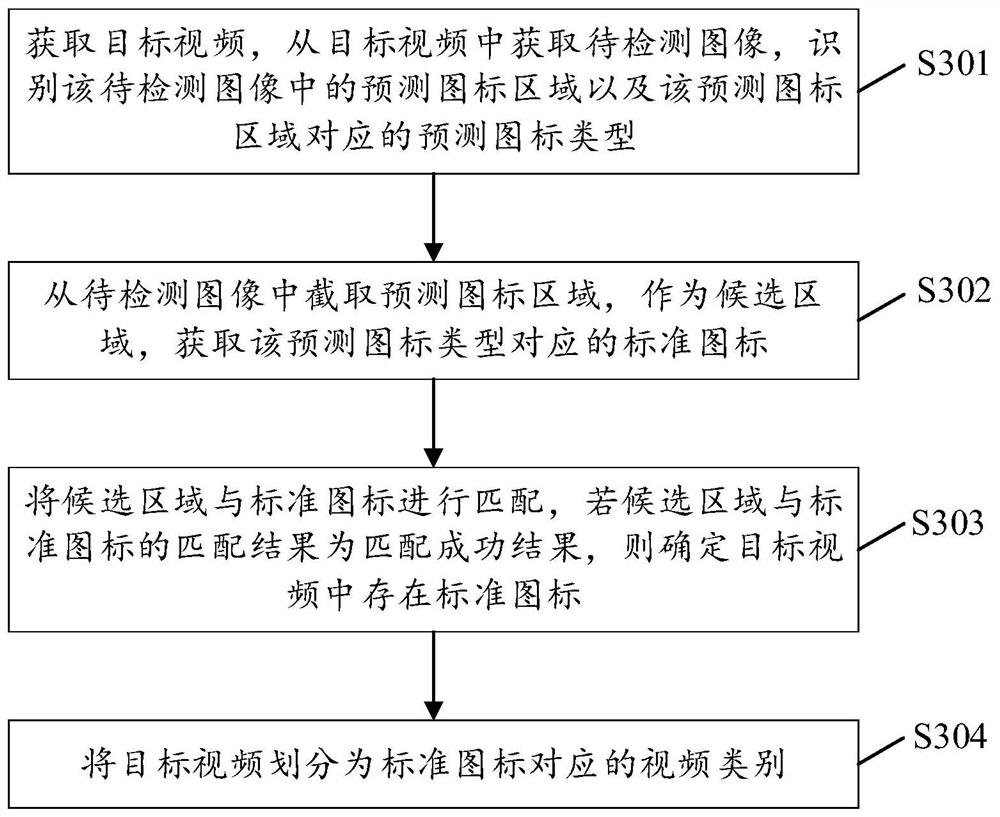
ActiveCN111950424AImplement two-factor authenticationImprove accuracyCharacter and pattern recognitionNeural architecturesComputer graphics (images)Engineering
The embodiment of the invention discloses a video data processing method and device, a computer and a readable storage medium, computer vision, deep learning and other technologies in the field of artificial intelligence can be used, and the method comprises the steps: obtaining a target video, and obtaining a to-be-detected image from the target video, identifying a prediction icon area in the to-be-detected image and a prediction icon type corresponding to the prediction icon area; intercepting a prediction icon area from the to-be-detected image to serve as a candidate area, and obtaining astandard icon corresponding to the prediction icon type; matching the candidate area with a standard icon, and if a matching result of the candidate area and the standard icon is a matching success result, determining that the standard icon exists in the target video; and dividing the target video into video categories corresponding to the standard icons. Accuracy of identifying icons in videos is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
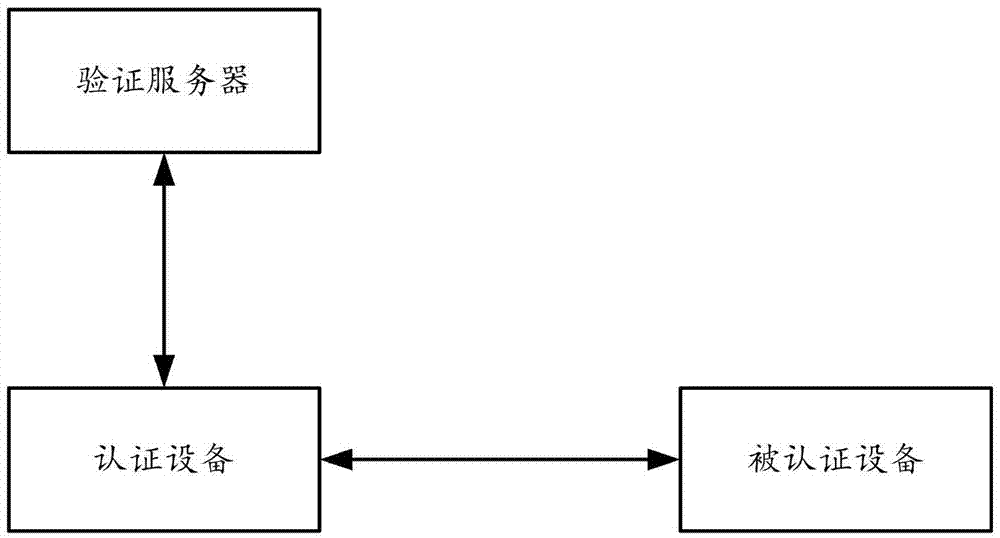
Method, device and system for realizing authentication between devices
ActiveCN106992956AImplement two-factor authenticationImprove securityTransmissionComputer scienceDevice Identifiers
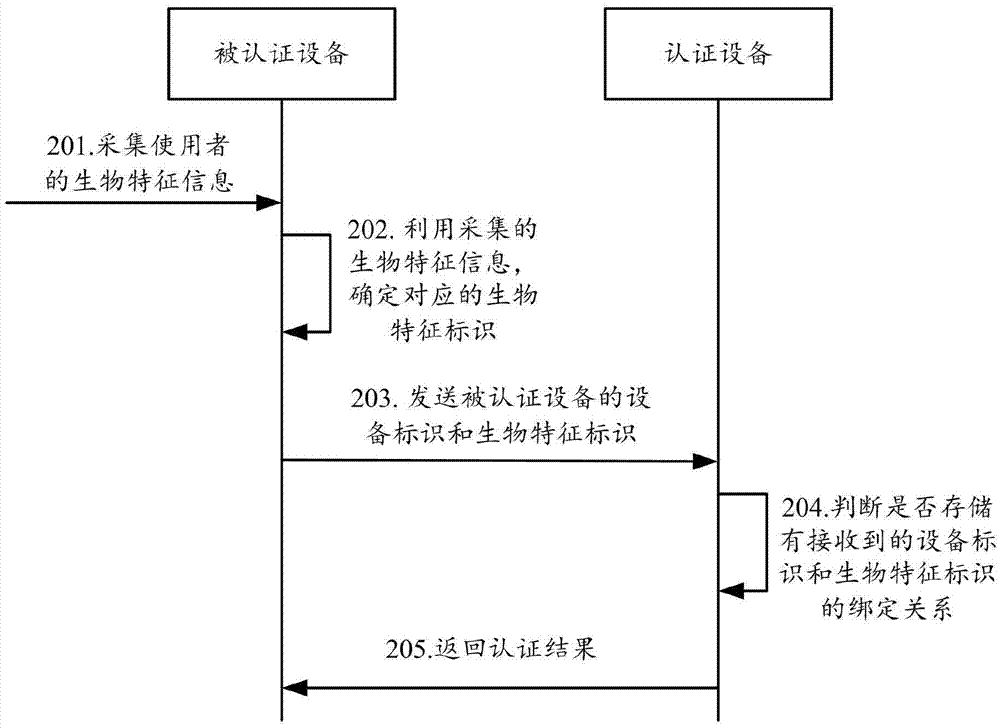
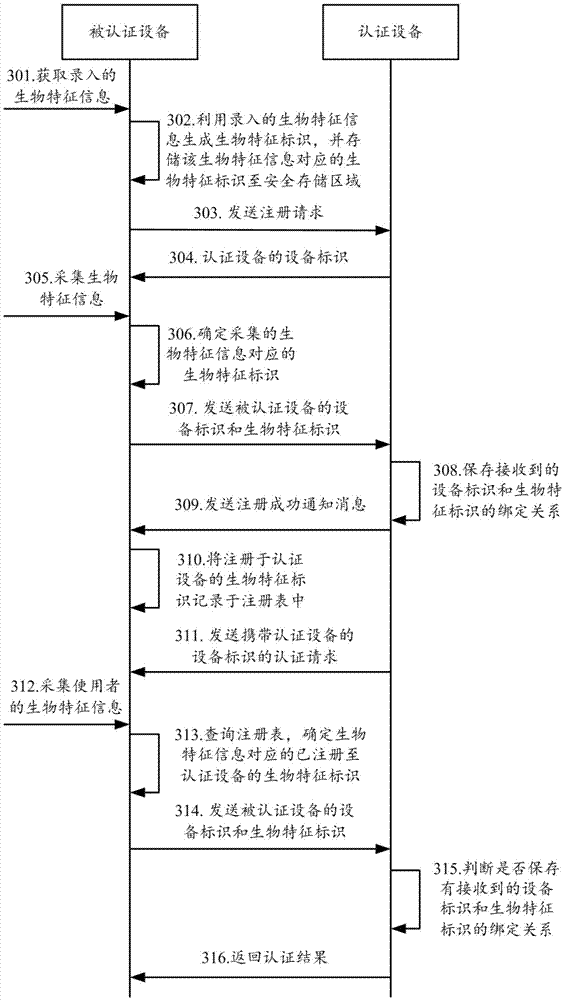
The invention provides a method, device and system for realizing authentication between devices, wherein the method comprises the steps that: an authentication device receives the device identifier of an authenticated device and the biological characteristic identifier of an authenticated device user; whether the binding relationship between the received device identifier and biological characteristic identifier is stored or not can be judged; and if not, the fact that authentication on the authenticated device is failed can be determined, wherein the authentication device pre-stores the binding relationship between the device identifier and the biological characteristic identifier provided by a registered device. By means of the method, device and system provided by the invention, dual authentication of the device and the device user identity is realized; and the security of authentication between the devices is improved.
Owner:BANMA ZHIXING NETWORK HONGKONG CO LTD
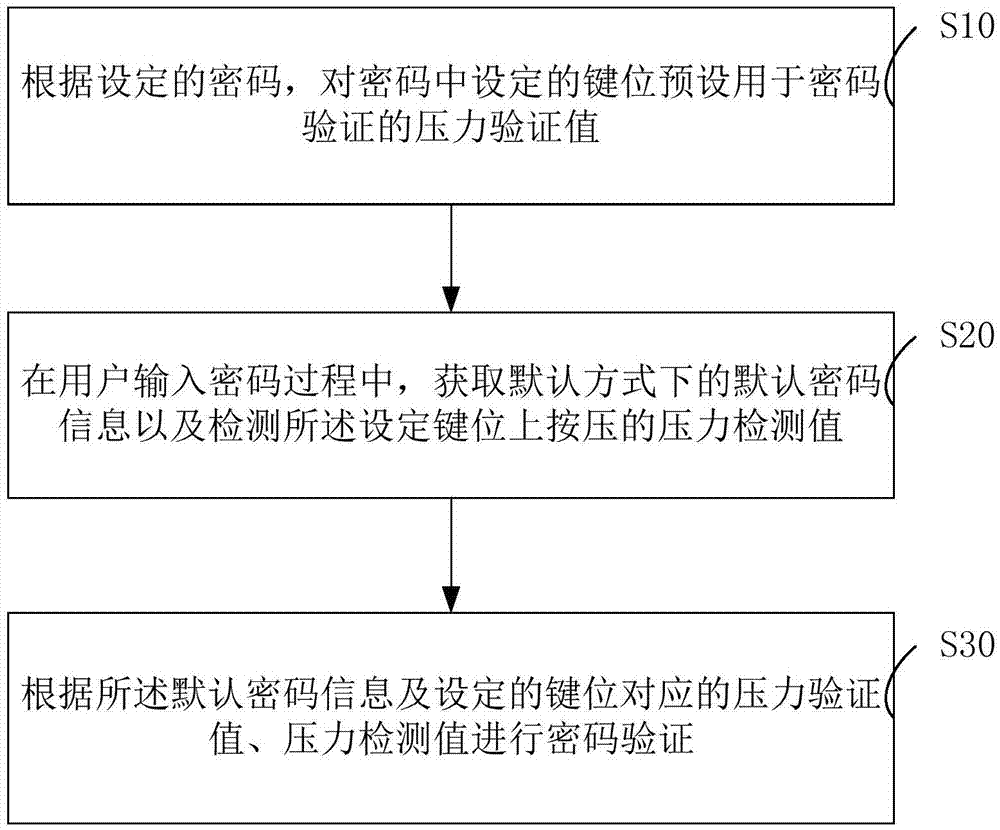
Password input verification method and system
ActiveCN105354458AImplement two-factor authenticationReduce theftDigital data authenticationValidation methodsUser input
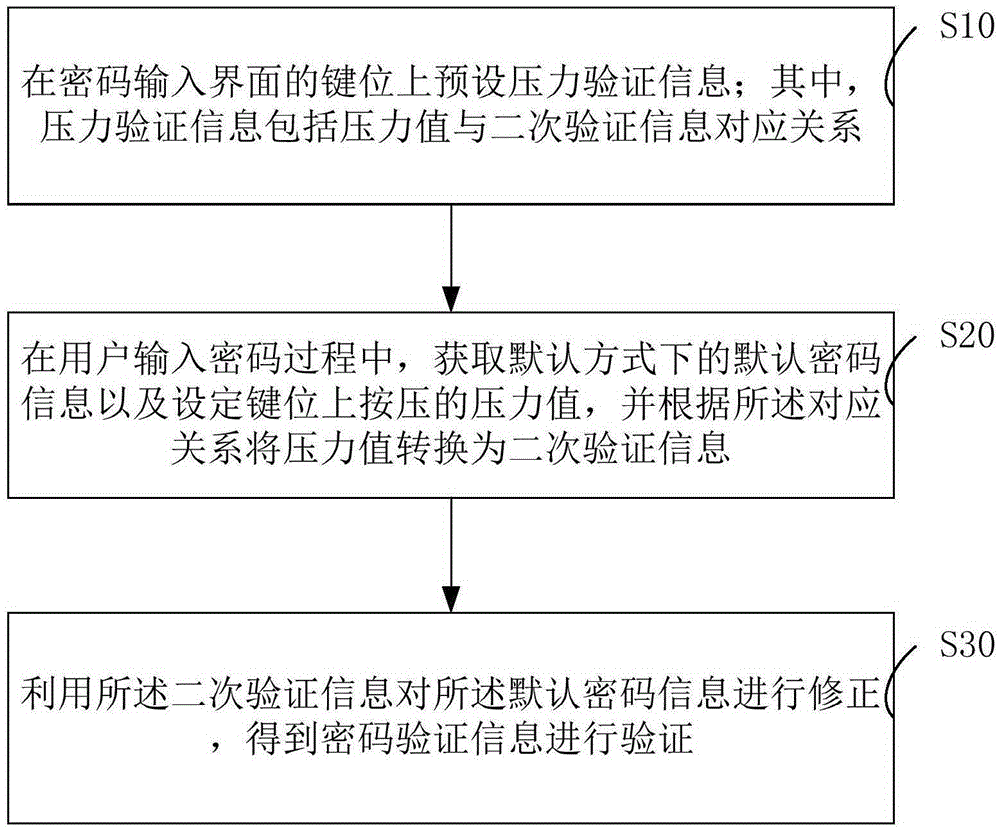
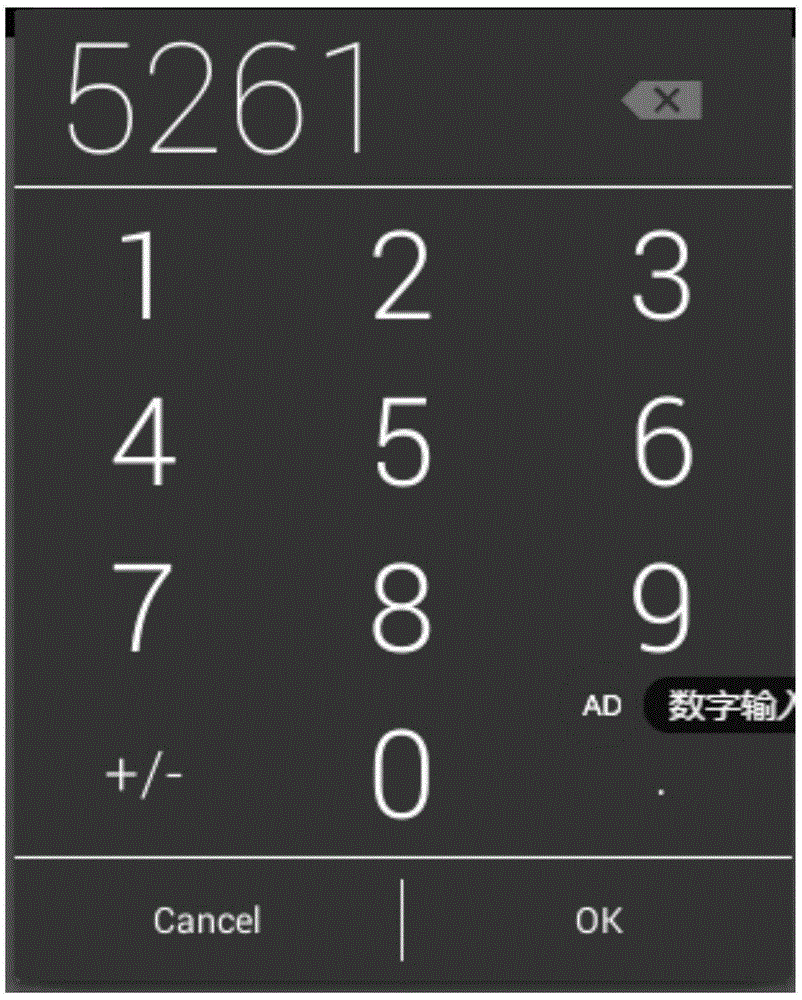
The present invention relates to a password input verification method and system.The method comprises: presetting pressure verification information on keys of a password input interface, wherein the pressure verification information comprises a correspondence between a pressure value and secondary verification information; when a user inputs a password, acquiring default password information of a default mode and a pressure value of pressing on set keys, and converting the pressure value into the secondary verification information according to the correspondence; and using the secondary verification information to correct the default password information, so as to acquire password verification information and perform verification. According to the technical scheme provided by the present invention, two-factor verification is achieved; and only a default input mode during the password input process can be watched by a bystander, so that the password of a user cannot be cracked even though the password is leaked, thereby reducing the possibility that user privacy is stolen and improving security.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Verification code authentication method and system based on biological characteristics
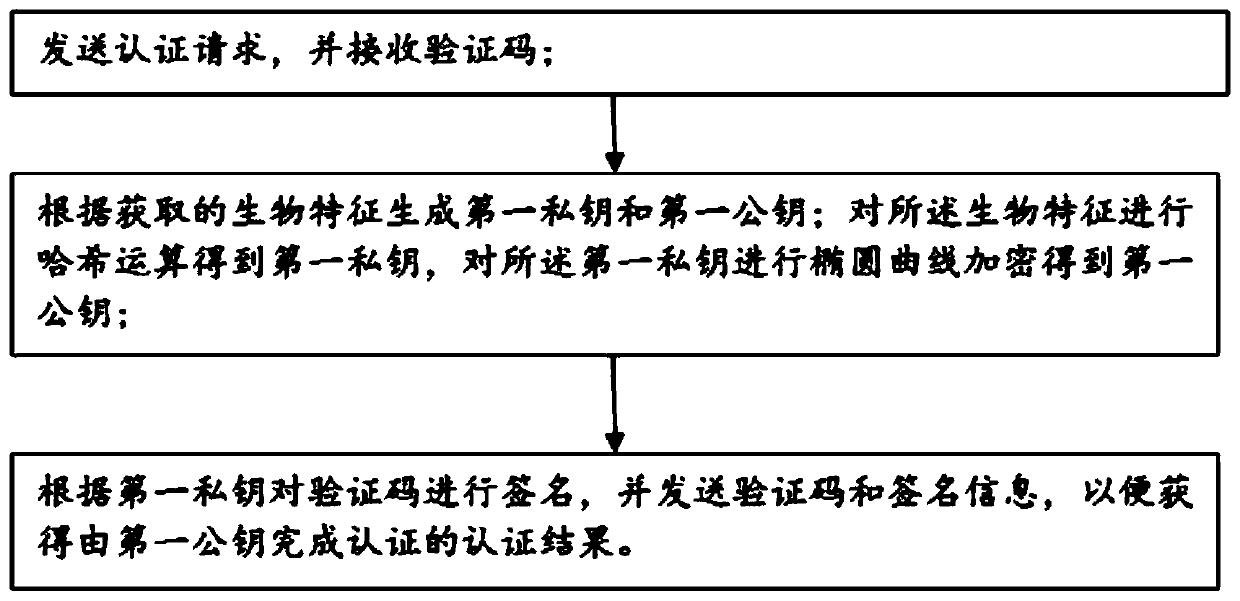
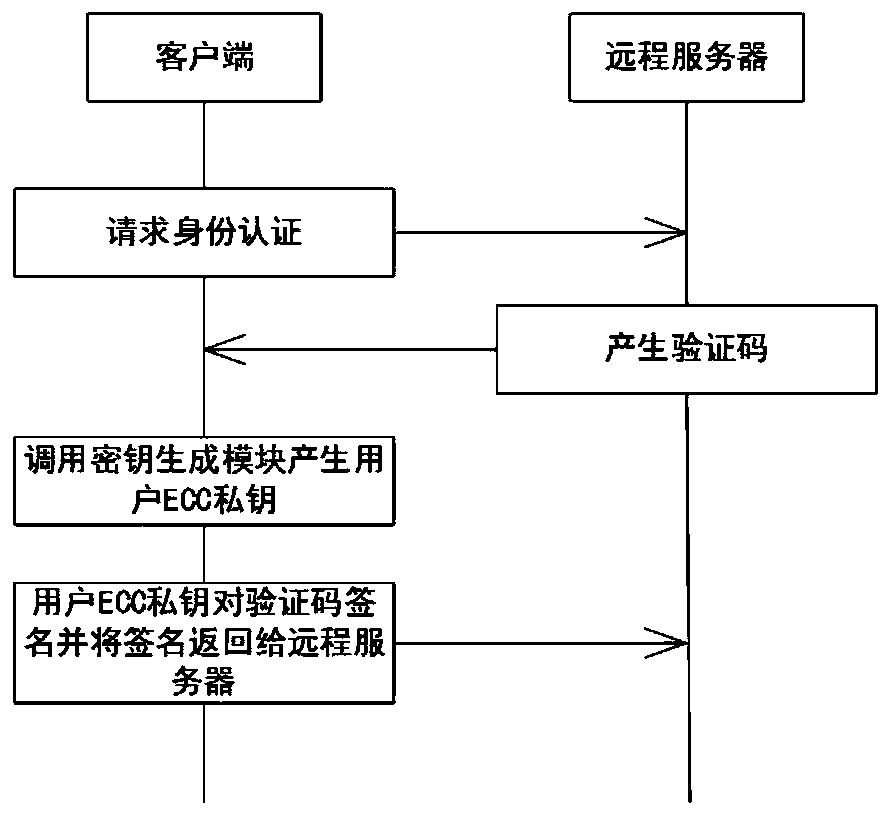
ActiveCN111600869ADid receiveAvoid safety hazardsKey distribution for secure communicationPublic key for secure communicationDigital signatureEngineering
The invention discloses a verification code authentication method and system based on biological characteristics, and the method comprises the steps: transmitting an authentication request, and receiving a verification code; generating a first private key and a first public key according to the acquired biological characteristics; performing hash operation on the biological characteristics to obtain a first private key, and performing elliptic curve encryption on the first private key to obtain a first public key; and signing the verification code according to the first private key, and sending the verification code and the signature information, so as to obtain an authentication result that authentication is completed by the first public key. The biological characteristic value of the user is taken as a private key, thedigital signature is performed on the verification code of the remote server, and the verification code is returned to the remote server; and the remote server authenticates the verification code and the signature information according to the user public key. The biometric features have uniqueness and non-reproducibility, network transmission and key management arenot needed, and the verification code is signed, so that the verification code has authentication, integrity and non-repudiation, and the security of the verification code is improved.
Owner:UNIV OF JINAN
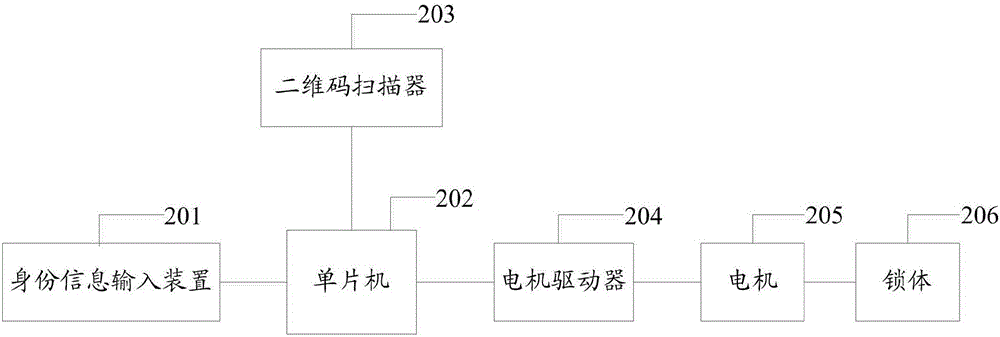
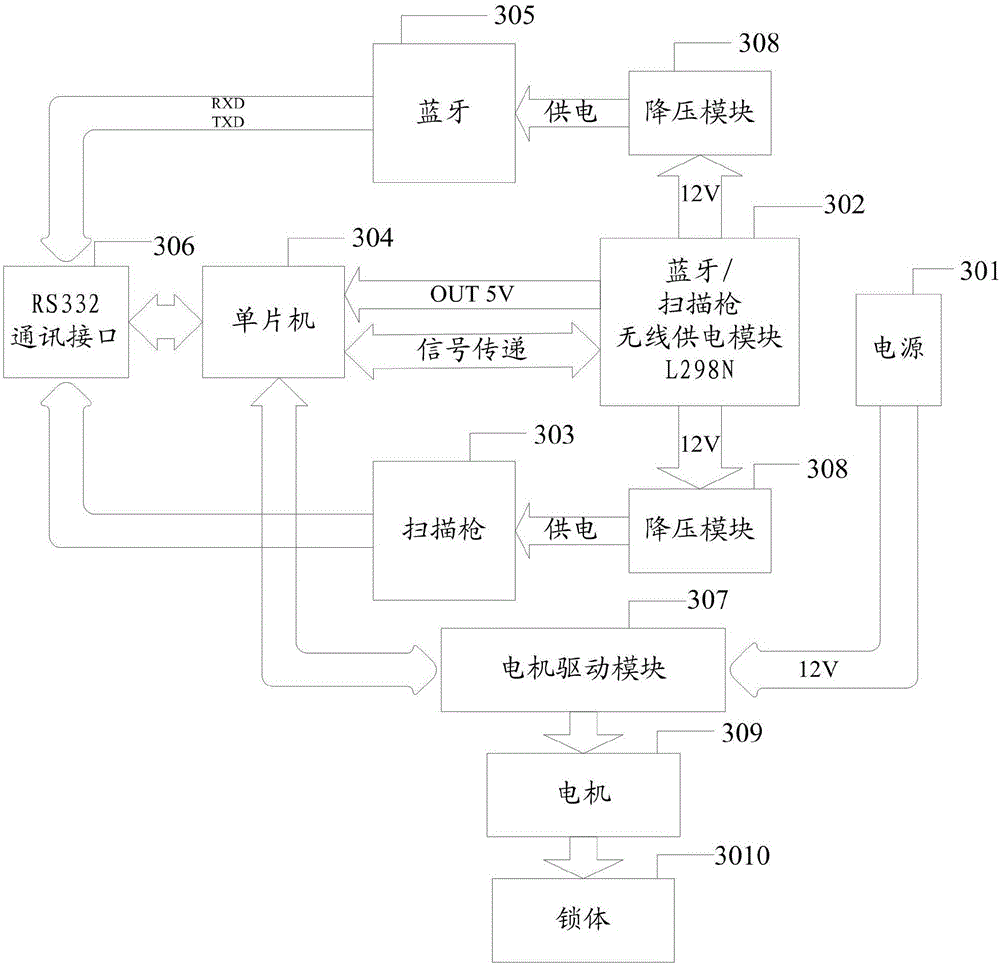
Control method and system of intelligent lock
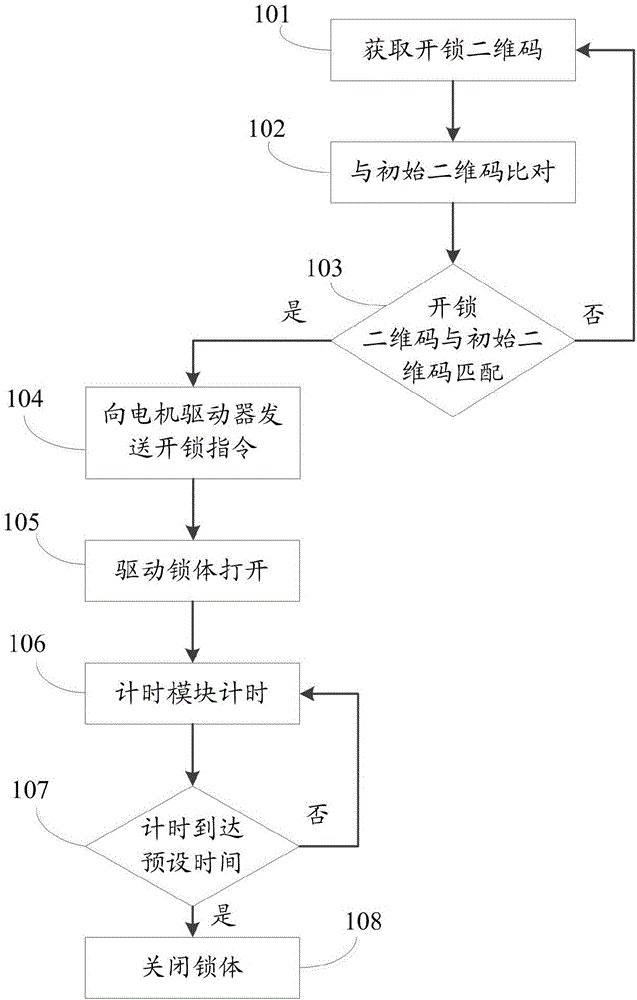
InactiveCN106408714AImprove convenienceEnsure safetyIndividual entry/exit registersComputer hardwareElectric machinery
The invention discloses a control method and system of an intelligent lock. The method includes: an initial two-dimensional code is generated according to the identity card information and fingerprint information of a user, and the initial two-dimensional code is stored; a two-dimensional code scanning device is used to scan an unlocking two-dimensional code, the unlocking two-dimensional code is compared with the pre-stored initial two-dimensional code, a motor driver controls a motor to drive the lock to unlock when the comparison succeeds, a timing module starts timing, and the lock automatically locks when preset time is reached. The control method and system has the advantages that remote unlocking can be achieved, use convenience is increased, and safety is increased by using the double-authentication identity authentication mode.
Owner:NAVAL AERONAUTICAL & ASTRONAUTICAL UNIV PLA
Method for unlocking terminal equipment, storage medium and terminal equipment
InactiveCN107358085AImplement two-factor authenticationImprove securityTelevision system detailsCharacter and pattern recognitionUser inputPassword
The invention discloses a method for unlocking terminal equipment, a storage medium and the terminal equipment. The method comprises the steps of when the terminal equipment is located at a lip language unlocking interface, collecting first lip language information of a user, wherein the lip language information comprises lip characteristics and lip language instructions; searching the first lip language information from a preset lip language information database; if the first lip language information is found, unlocking the terminal equipment. The characteristics of a user identity are verified through the recognition of lip characteristics, a password input by the user is matched through a lip language recognition technology, and therefore the double verification for unlocking the terminal is achieved, and the safety of the terminal equipment is improved.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
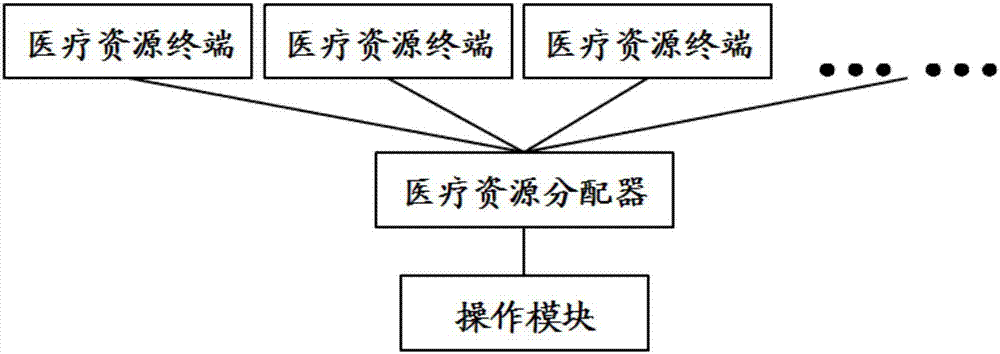
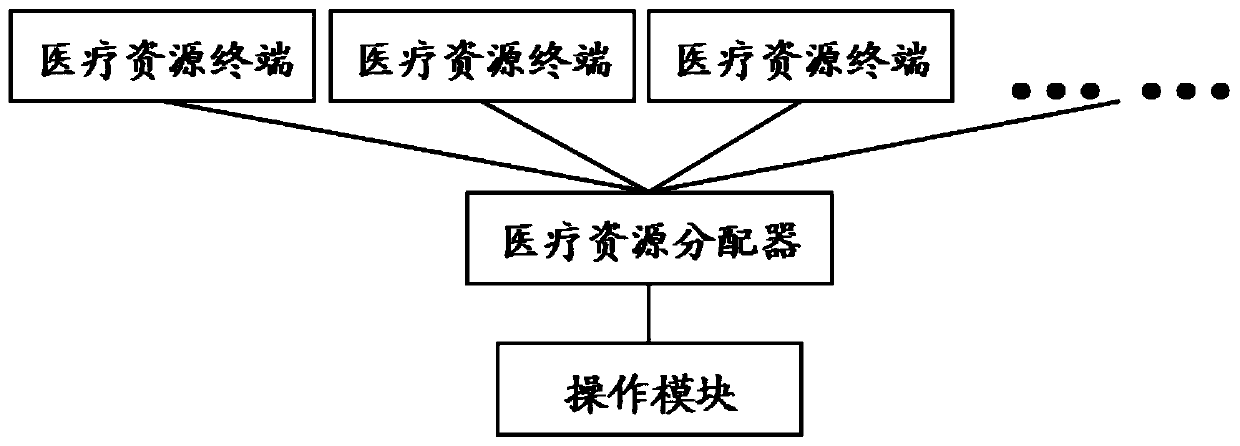
Medical resource scheduling platform
InactiveCN107506912AShorten the timeImprove authentication efficiencyResourcesHealthcare resources and facilitiesThe InternetResource allocation systems
The invention discloses a medical resource scheduling platform, which comprises a medical resource allocation system, wherein the medical resource allocation system comprises a medical resource allocator, an operation module and a plurality of medical resource terminals. The medical resource scheduling platform can schedule and match medical resources systematically in an online method by means of the internet through using the medical resource allocation system, so as to improve the matching efficiency and accuracy degree of the medical resources. In addition, the medical resource scheduling platform further comprises a doctor-end identity authentication system, which can achieve the effect of improving the authenticity and authentication efficiency of doctor identity authentication. Moreover, the medical resource scheduling platform comprises a searching and matching system, which makes a doctor searching and matching result more precise.
Owner:广州睿临网络科技有限公司
Electronic device, authentication method and storage medium
The invention relates to an electronic device, an authentication method and a storage medium. The method comprises the steps that when a user performs a service in an IVR scenario, a random code of afirst preset digit is broadcast for the user to follow, and acoustic models of a preset type are established for the broadcast random code and the voice followed by the user respectively after following; forced overall aligning is carried out on the acoustic model of the broadcast random code and the acoustic model of the voice followed by the user; a predetermined algorithm is used to calculate the same probability of two aligned acoustic models; if the probability is greater than a preset first threshold, the voiceprint feature vector of the voice followed by the user is extracted; a pre-stored standard voiceprint feature vector of the user after successful register is acquired; and the distance between the voiceprint feature vector of the voice followed by the user and the standard voiceprint feature vector is calculated to authenticate the user. According to the invention, double-effect authentication of the user is realized, and the identity of the user can be accurately confirmed.
Owner:PING AN TECH (SHENZHEN) CO LTD
Management system for safe entering/exiting of bank cash box based on Internet of Things
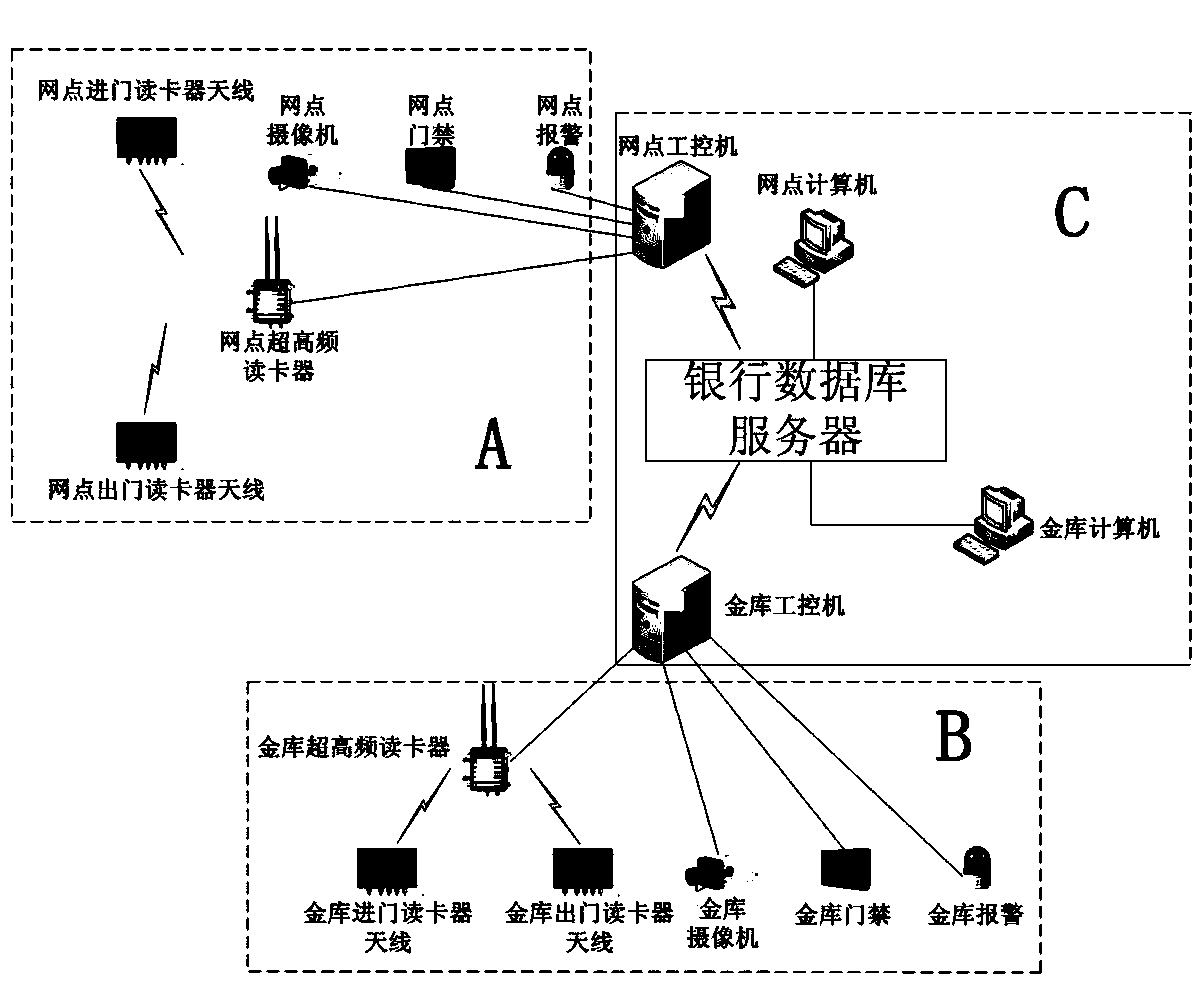
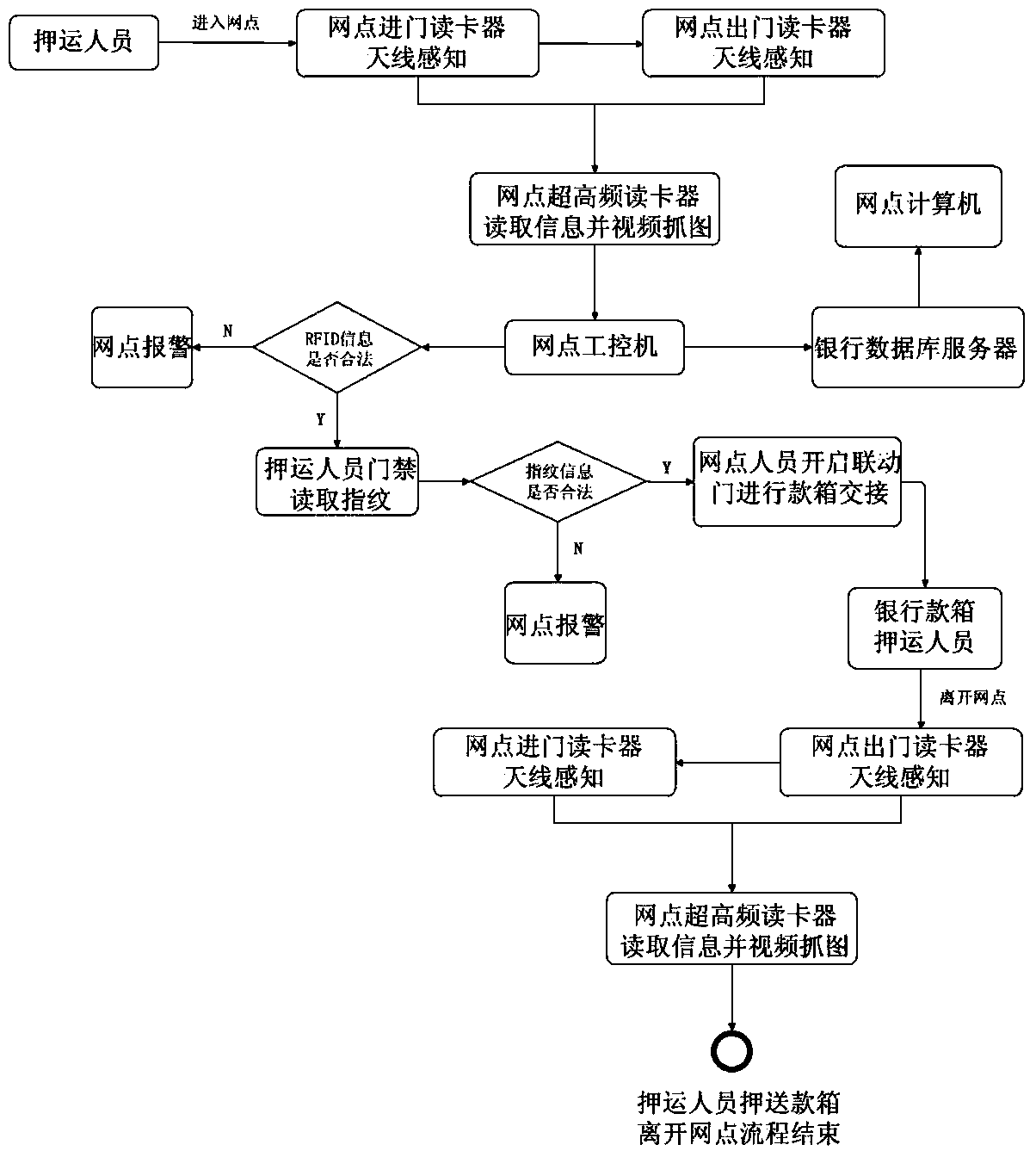
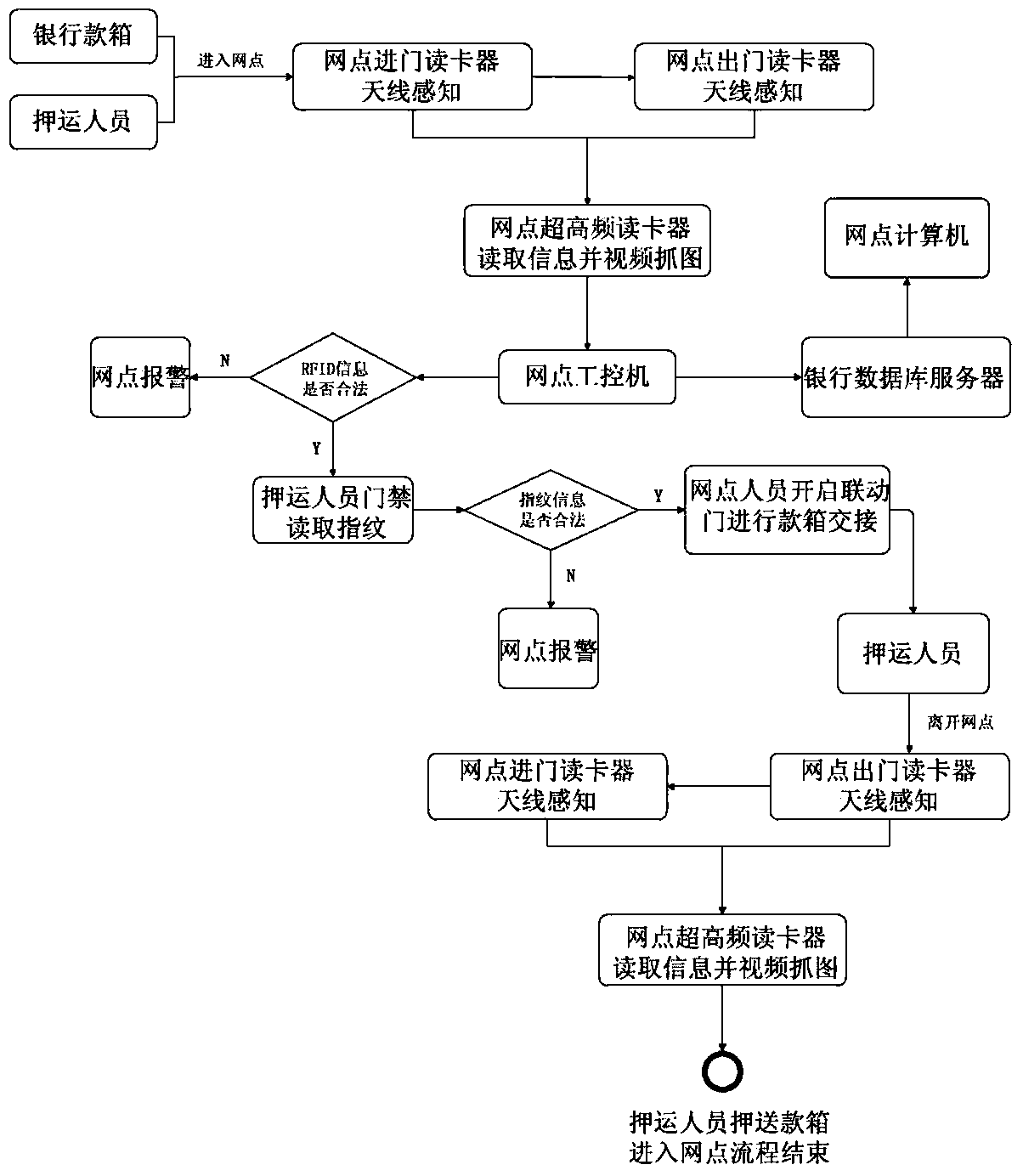
ActiveCN103530918ARealize automatic handoverSafe Handover GuaranteeIndividual entry/exit registersSensing by electromagnetic radiationData processingCard reader
The invention provides a management system for safe entering / exiting of a bank cash box based on Internet of Things. The management system comprises a website sensing unit, a vault sensing unit and a data processing and applying unit; a website industrial personal computer is in real-time connection with a bank database server by a wireless VPN (Virtual Private Network); a website computer is in real-time connection with the bank database server by a bank private network; a vault computer is in real-time connection with the bank database server by the bank private network; a website ultra-high-frequency card reader, a vault ultra-high-frequency card reader, a camera, a door guard, an alarm and corresponding industrial personal computers are in real-time connection by RJ-45 cables; an entering card reader antenna, an exiting card reader antenna and the ultra-high-frequency card reader are in wireless connection. Based on an application technology of the Internet of Things, the working efficiency of working escort personnel is improved, safe guarantees are provided for escort work of the bank cash boxes and tracing evidences are provided for treating emergency situations.
Owner:江苏腾源智能科技有限公司
Security authentication method and system, and computer readable storage medium
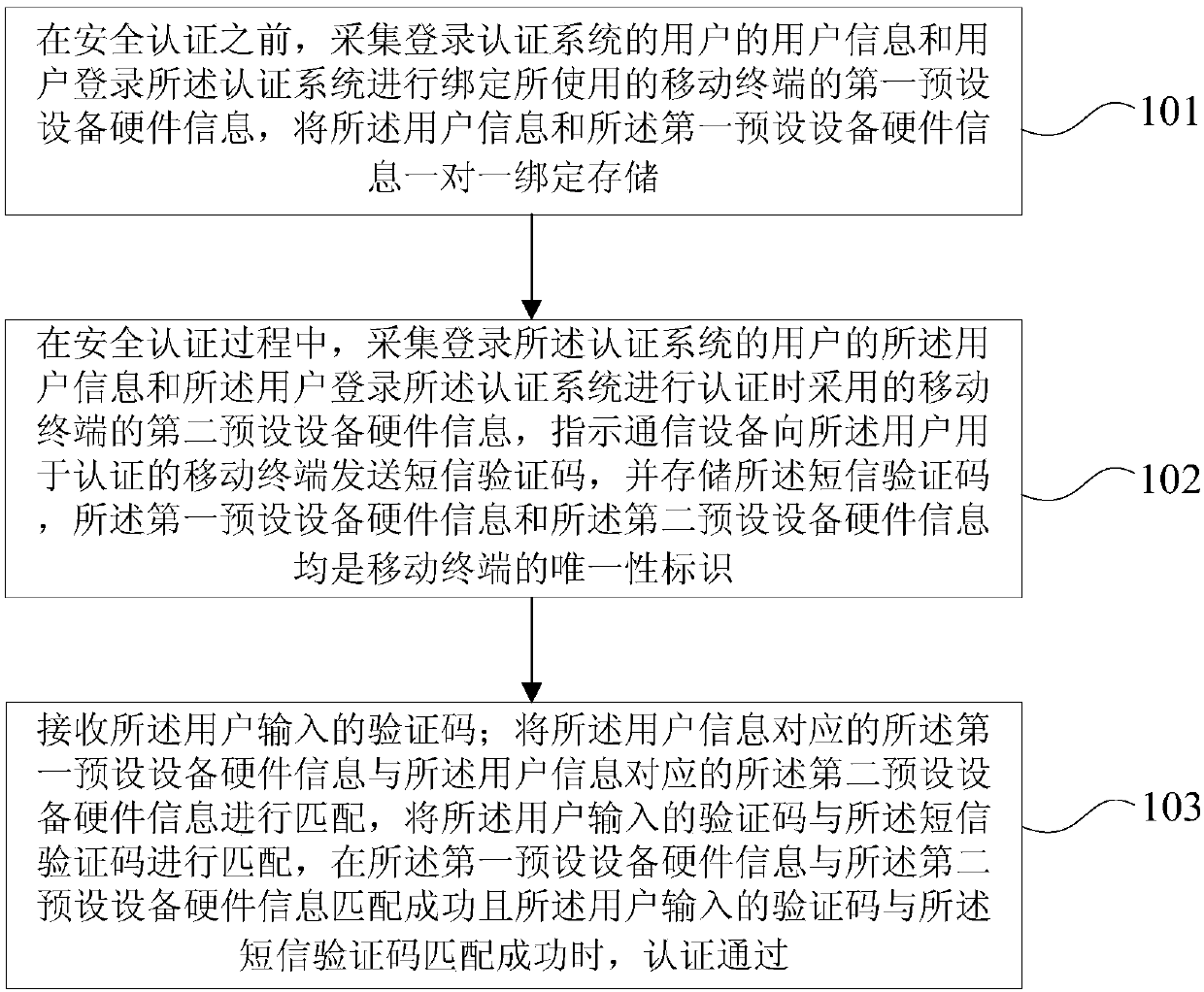
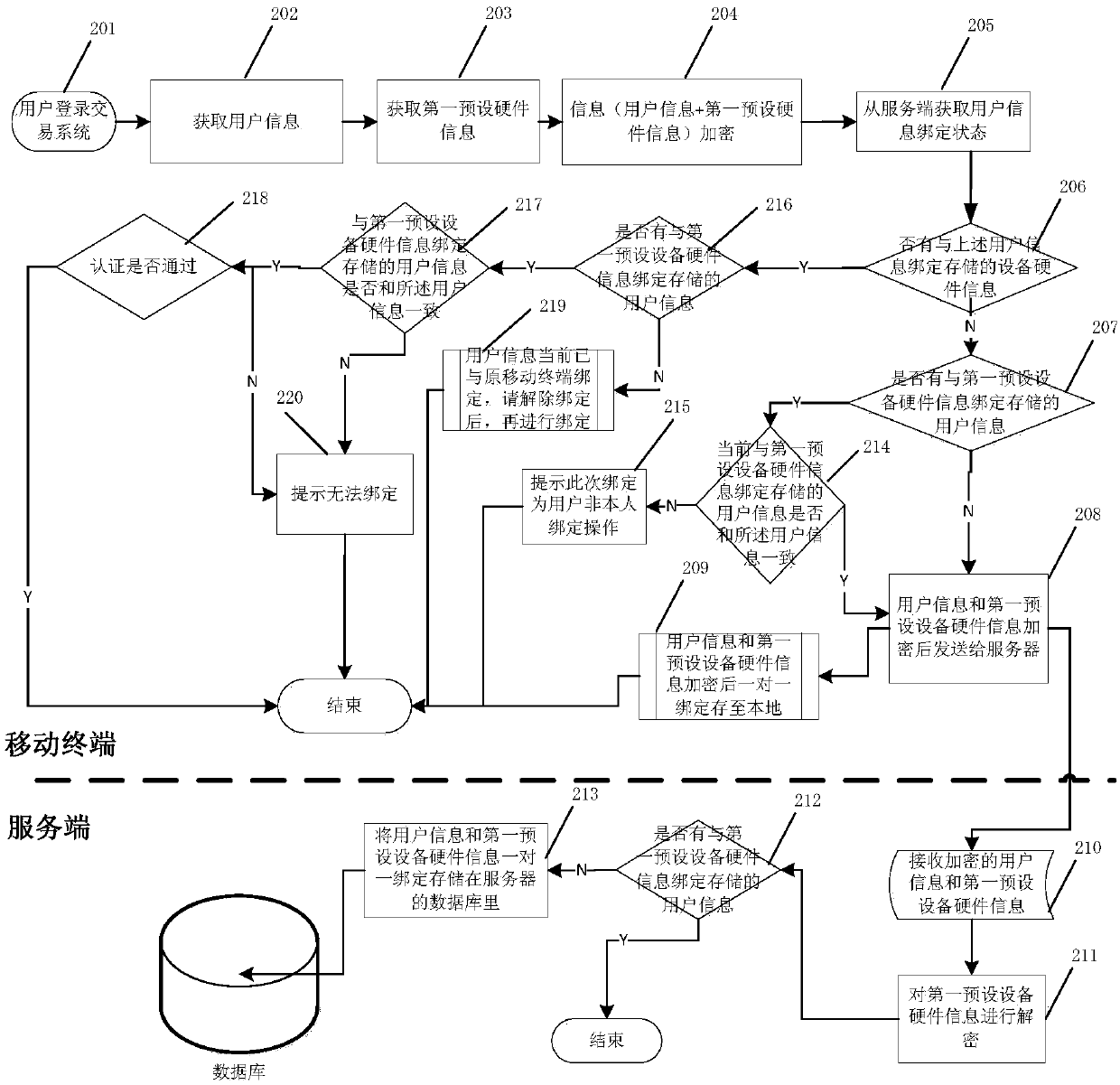
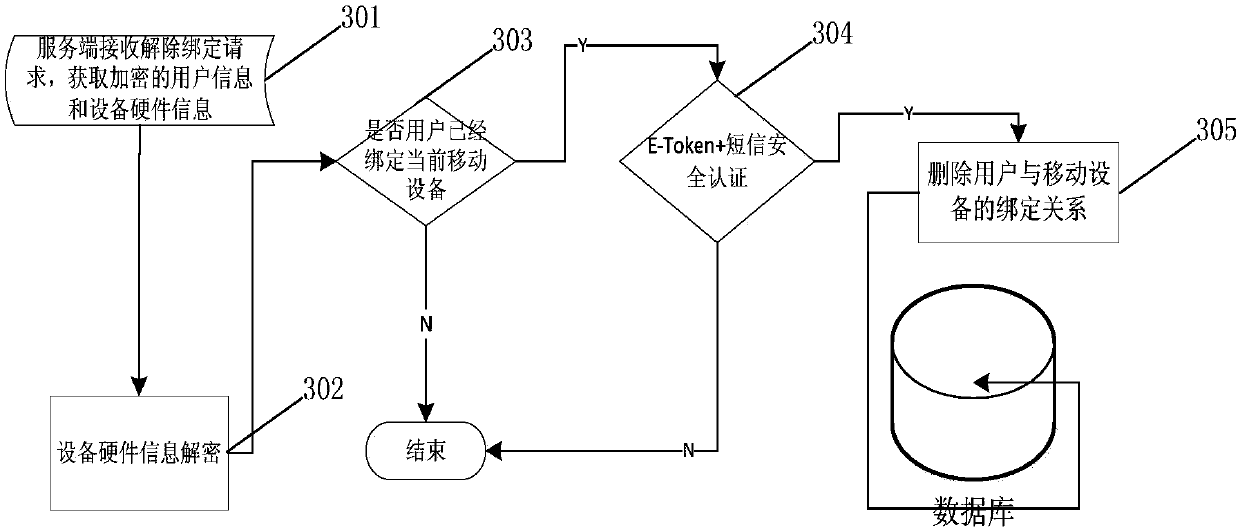
ActiveCN107819766ARealize the corresponding relationshipImplement one-to-one bindingMessaging/mailboxes/announcementsTransmissionUser inputComputer terminal
Embodiments of the invention provide a security authentication method and system, and a computer readable storage medium. The method comprises the following steps of collecting user information of a user logging in to the authentication system and first preset equipment hardware information of a mobile terminal used when the user logs in to the authentication system for binding before security authentication, and binding and storing the user information and the first preset equipment hardware information in a one-to-one manner; during a security authentication process, collecting the user information and second preset equipment hardware information of a mobile terminal used when the user logs in to the authentication system for authentication, instructing a communication device to send a short message verification code to the mobile terminal used for authentication by the user, and storing the short message verification code; receiving the verification code input by the user; and whenthe first preset equipment hardware information is successfully matched with the second preset equipment hardware information, and the verification code input by the user is successfully matched withthe short message verification code, passing the authentication.
Owner:BANK OF CHINA
Identity verification method and device
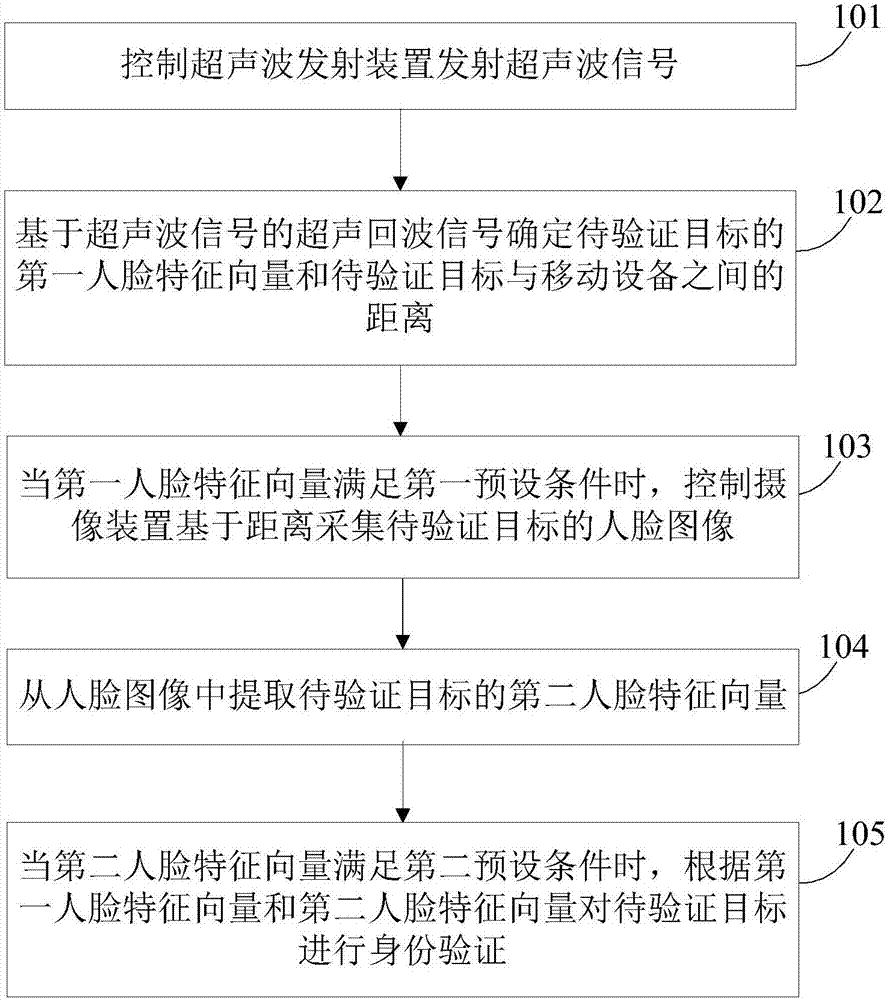
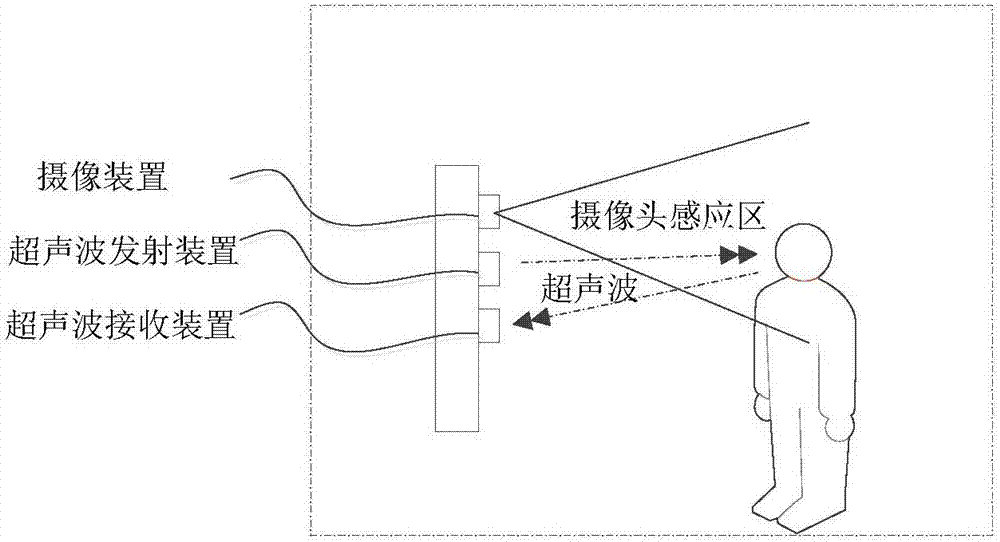
ActiveCN106980836AImprove securityReduce the risk of lossCharacter and pattern recognitionFeature vectorSonification
The invention relates to an identity verification method and device. The method comprises that a supersonic wave emitter is controlled to emit a supersonic wave signal; on the basis of supersonic echo signal of the supersonic wave signal, a first face characteristic vector of an object to be verified and a distance between the object to be verified and mobile equipment are determined; when the first face characteristic vector satisfies a first preset condition, an image pick-up device is controlled to collect a face image of the object to be verified; a second face characteristic vector of the object to be verified is extracted from the face image; and when the second face characteristic vector of the object to be verified satisfies a second preset condition, the identity of the object to be verified is verified according to the first and second face characteristic vectors. Thus, the safety of identity verification is improved via both supersonic verification and face verification manners, and the possibility of unnecessary property loss is reduced.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
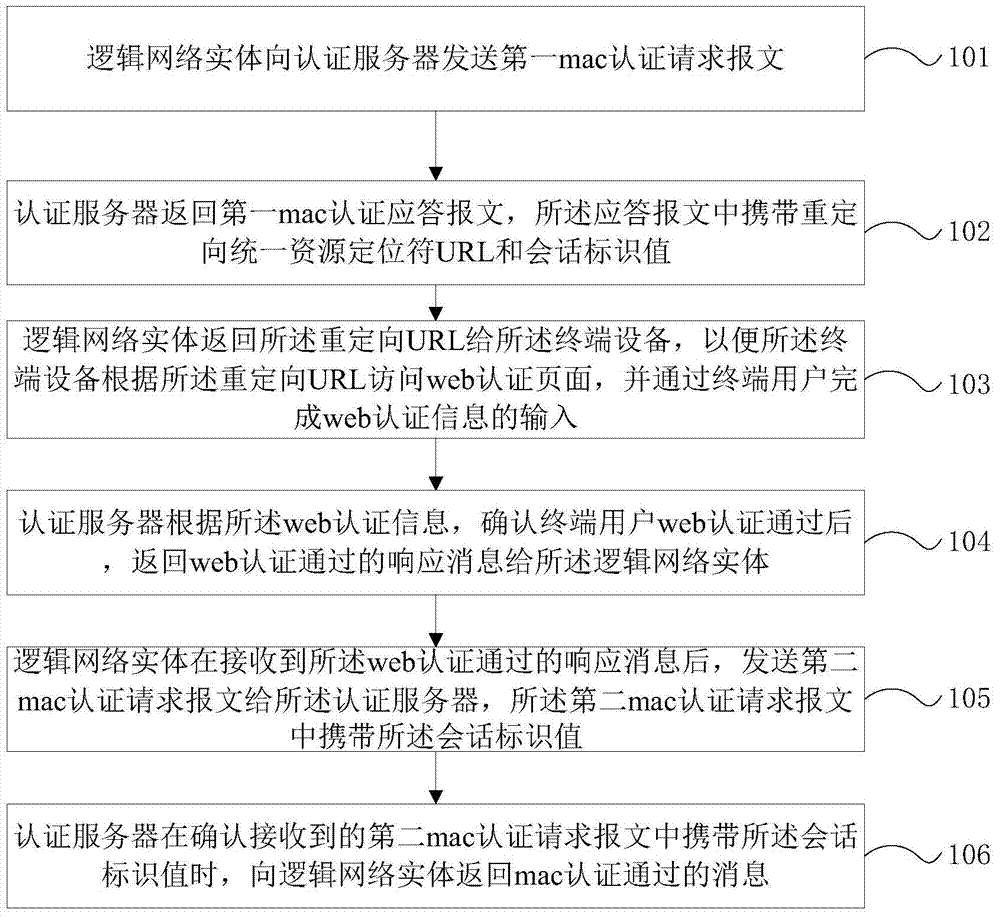
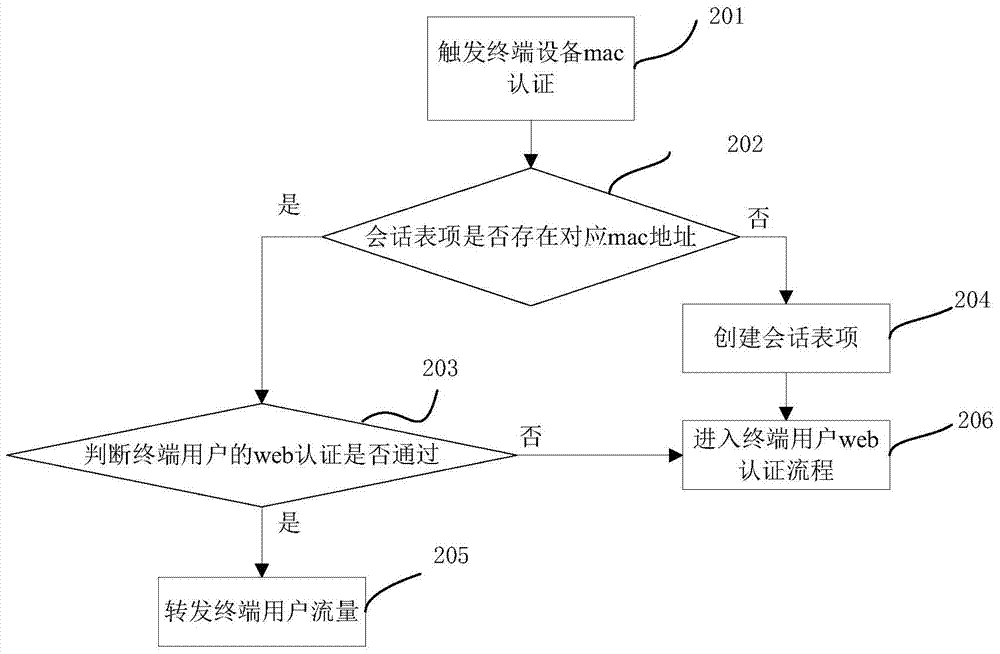
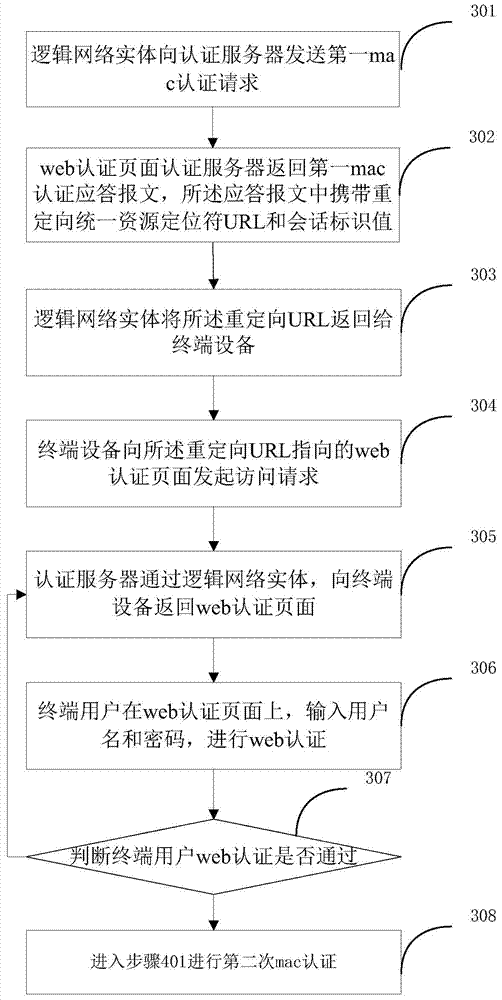
Authentication method integrating mac authentication and web authentication
ActiveCN104735050AImplement two-factor authenticationImprove securityTransmissionComputer hardwareWeb authentication
The invention is applicable to the Internet field and provides an authentication method integrating mac authentication and web authentication. The method comprises the steps that a logical net entity sends a first mac authentication request message to an authentication server; the authentication server returns a first mac authentication response message, and a re-directed URL and a session identity value are carried in the response message; the logical net entity returns the re-directed URL to terminal equipment; according to web authentication information, after confirming that a terminal user passes the web authentication, the authentication server returns a response message of passing the web authentication to the logical net entity; after receiving the response message of passing the web authentication, the logical net entity sends a second mac authentication request message to the authentication server, and the session identity value is carried in the second mac authentication request message; when confirming that the session identity value carried in the second mac authentication request message is received, the authentication server returns a message of passing the mac authentication to the logical net entity. By means of the method, the server mainly releases the re-directed url, and manual configuration on the logical net entity can be avoided, so that the configuration quantity is reduced.
Owner:FENGHUO COMM SCI & TECH CO LTD
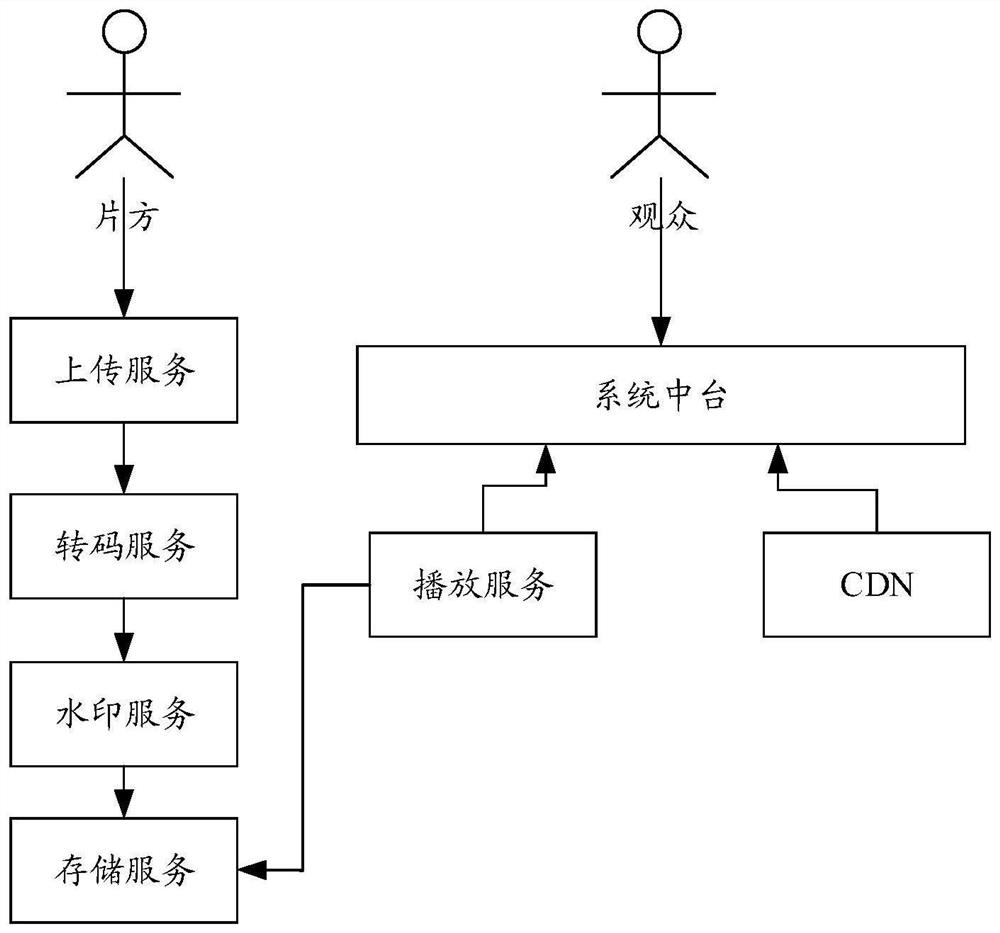
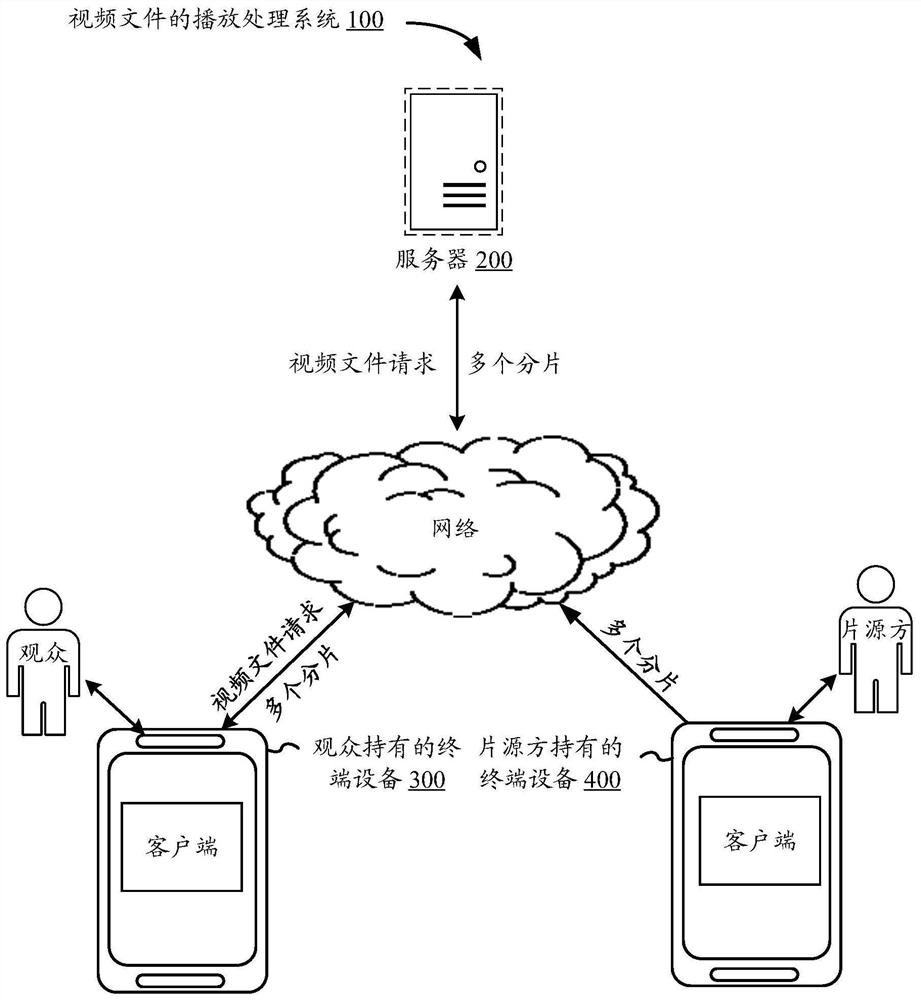
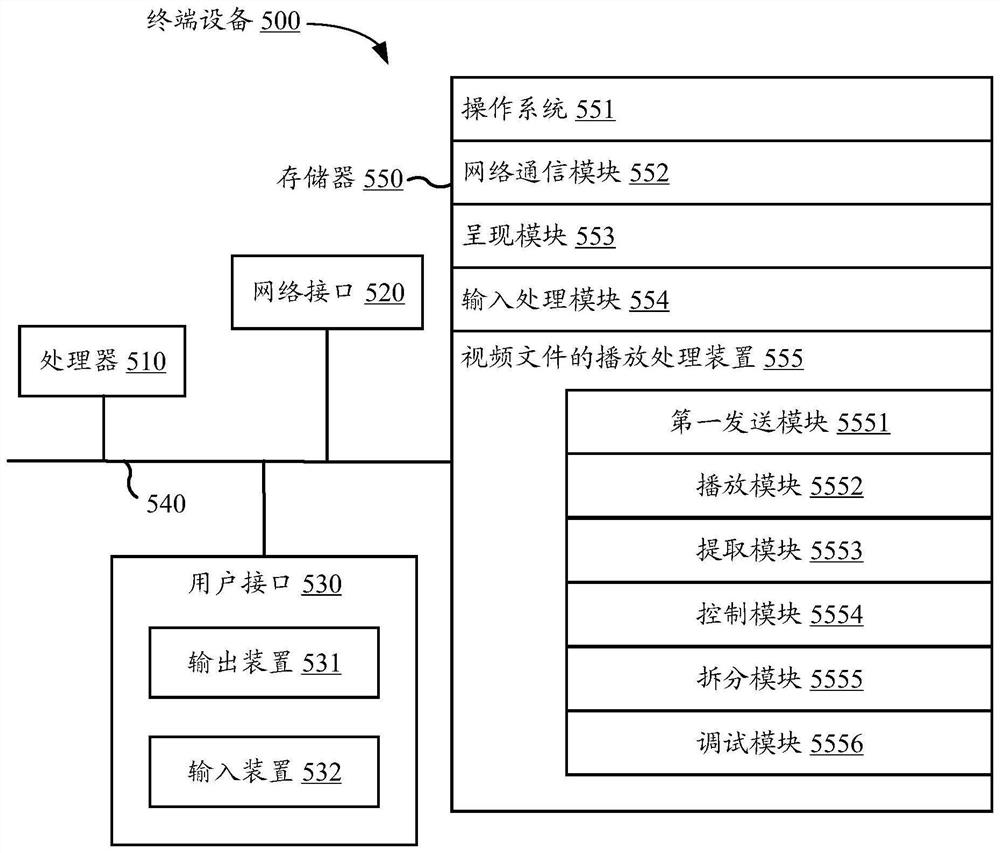
Video file playing processing method and device, electronic equipment and storage medium
PendingCN113411638ARealize decryption playbackEnsure safetySelective content distributionEngineeringWatermark
The invention provides a video file playing processing method and device, electronic equipment and a computer readable storage medium. The method comprises the following steps: sending a video file request to obtain a plurality of encryption fragments and keys corresponding to a video file; decrypting the plurality of encrypted fragments based on the secret key, and playing the fragments obtained after decryption; extracting watermark information in the fragments in a playing process, so as to obtain an authority verification result of the video file based on the watermark information; and executing a corresponding control operation on playing of the video file based on the permission verification result. According to the invention, the playing security of the video file can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
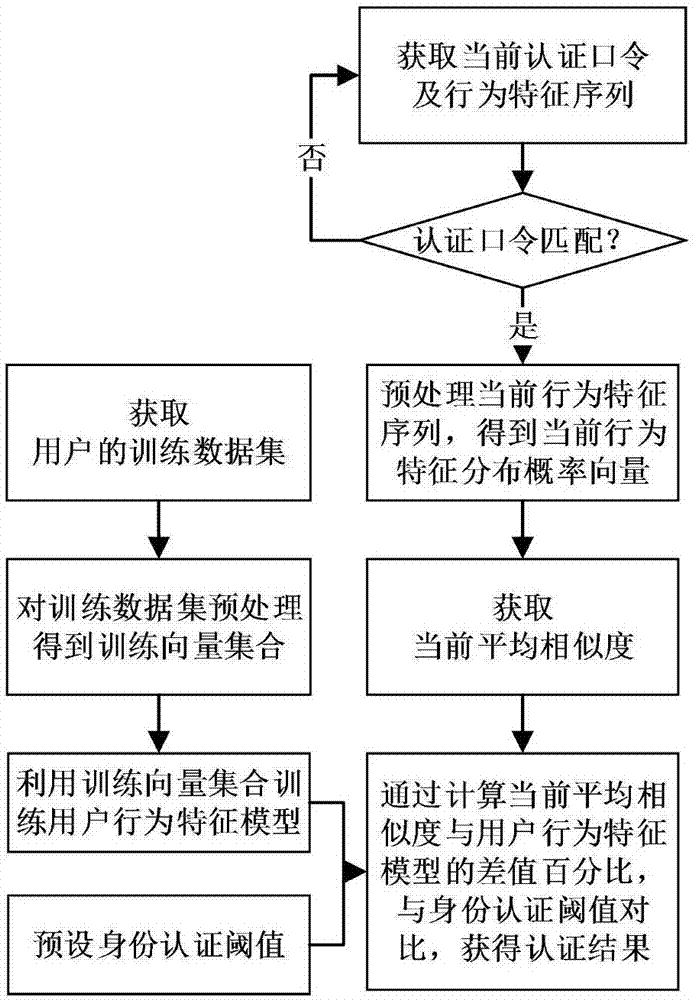
Intelligent terminal identity authentication method based on similarity
InactiveCN107194219AImprove accuracyImprove securityCharacter and pattern recognitionDigital data authenticationPattern recognitionTablet computer
The invention provides an intelligent terminal identity authentication method based on similarity. The method comprises a training period and an authentication period, used for solving the technical problem that in an existing implicit authentication method, authentication accuracy is relatively low. The method comprises implementation steps of acquiring a training data set, pre-processing a training vector set, computing similarity between behavior feature distribution probability vectors in the training vector set based on information entropy to train a user behavior feature model, and presetting an identity authentication threshold; and if an authentication password is completely matched, preprocessing a current behavior feature sequence to acquire the current behavior feature distribution probability vector, acquiring a current average similarity, judging whether a difference percentage of the current average similarity to the user behavior feature model is within a preset identity authentication threshold range, and acquiring an authentication result. The method provided by the invention is high in security and good in user experience, and can be applied to user identity authentication of smart phones and tablet computers.
Owner:XIDIAN UNIV
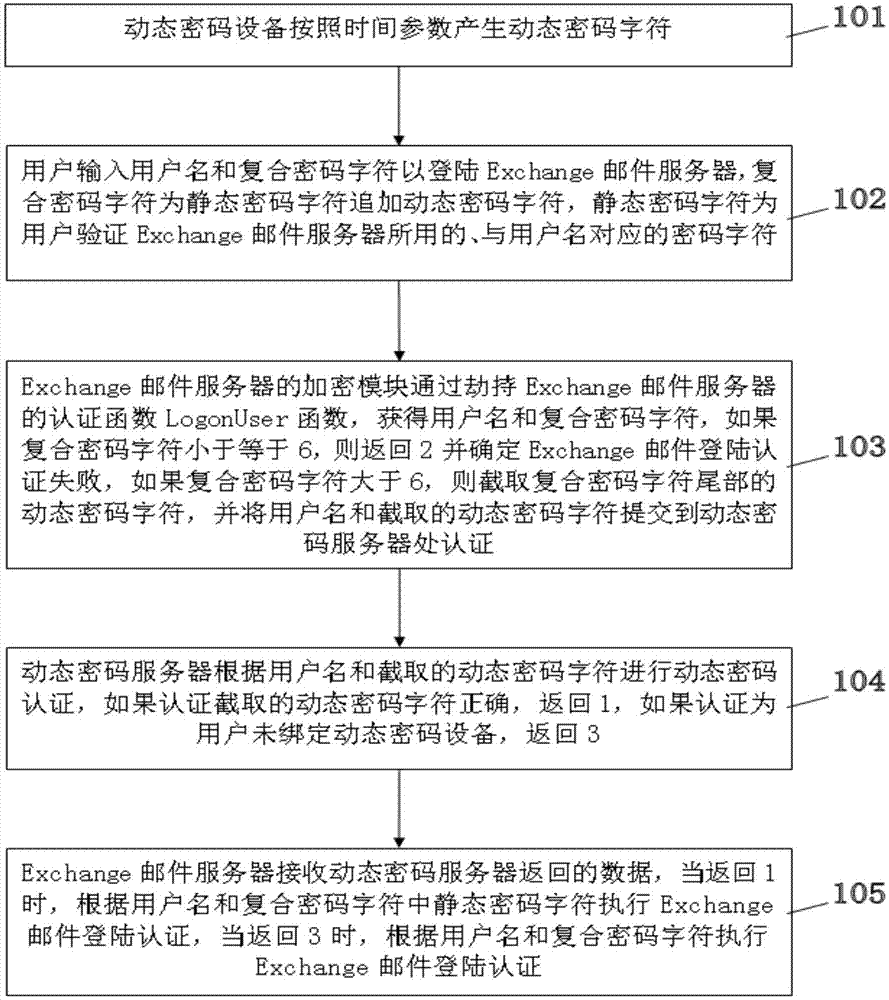
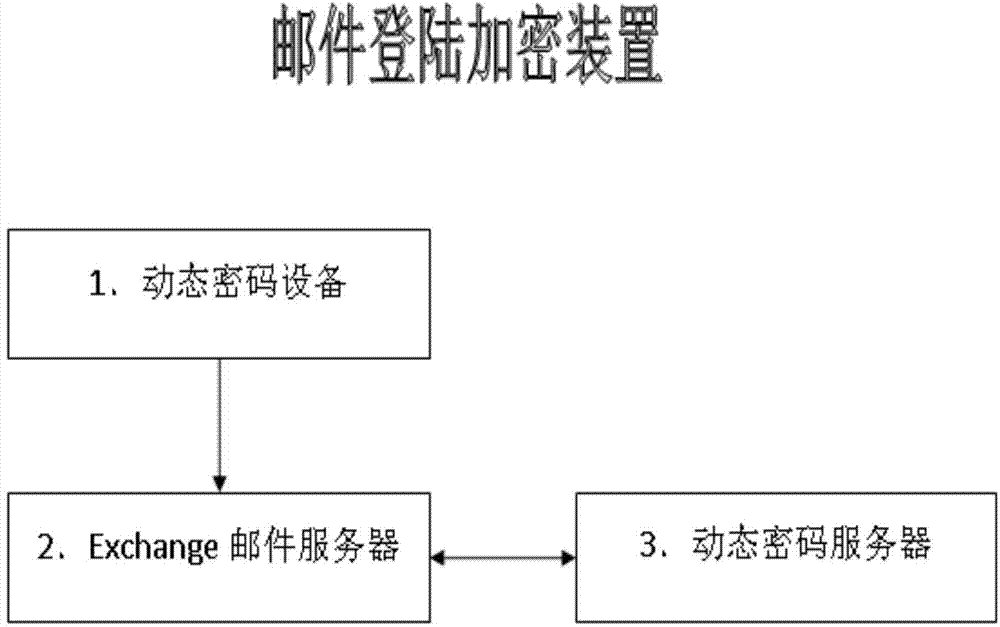
Encryption method and device for login of Exchange corporate E-mails
InactiveCN103763105AImplement two-factor authenticationImprove securityUser identity/authority verificationData switching networksPasswordElectronic mail
The invention discloses an encryption method for login of Exchange corporate E-mails. The encryption method comprises the steps that dynamic password equipment generates dynamic password characters according to time parameters, a user adds the dynamic password characters to a static password character which is preset by the user and is used for verifying an Exchange E-mail server to generate a combined password character, and a dynamic password server and the Exchange E-mail server carry out Exchange corporate E-mail login verification on the user based on a user name and the combined password characters. The invention further discloses an encryption device for login of the Exchange corporate E-mails. A dynamic password generated by the dynamic password equipment is added to an original login password, so that the safety of the Exchange E-mails is greatly improved.
Owner:SHANGHAI PEOPLENET SECURITY TECH
Network configuration method, network configuration device, electronic equipment and readable storage medium
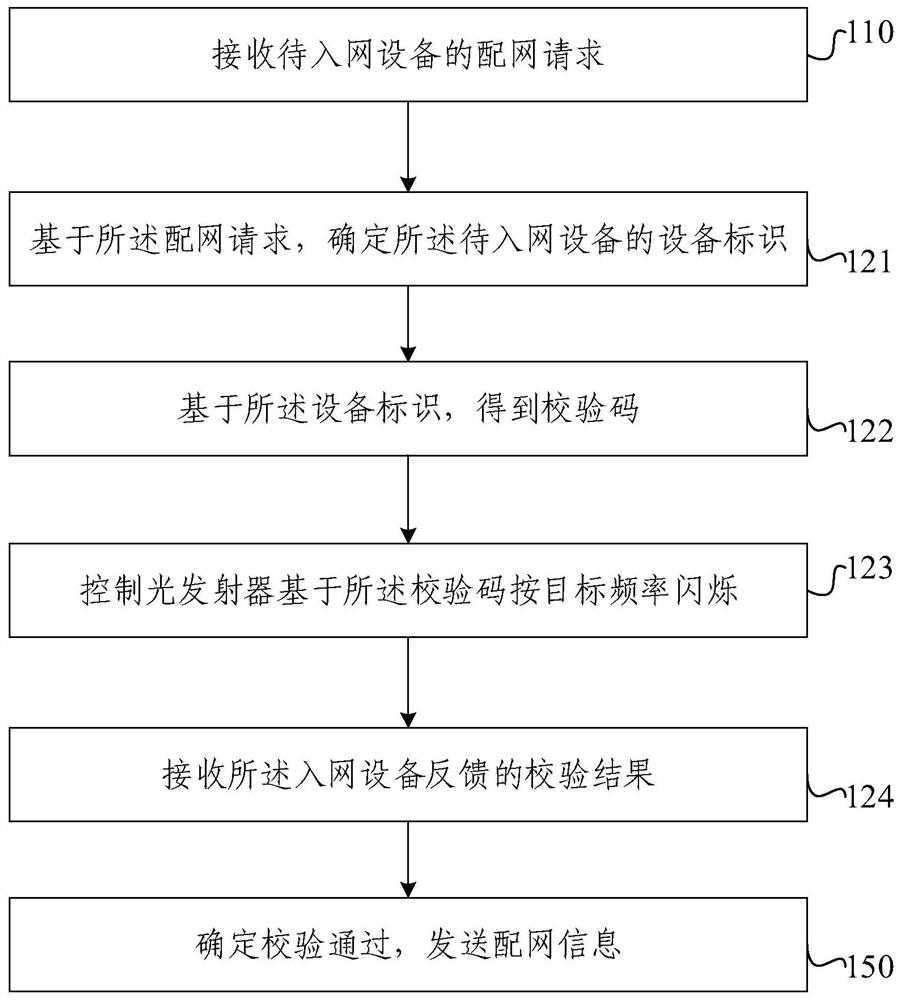
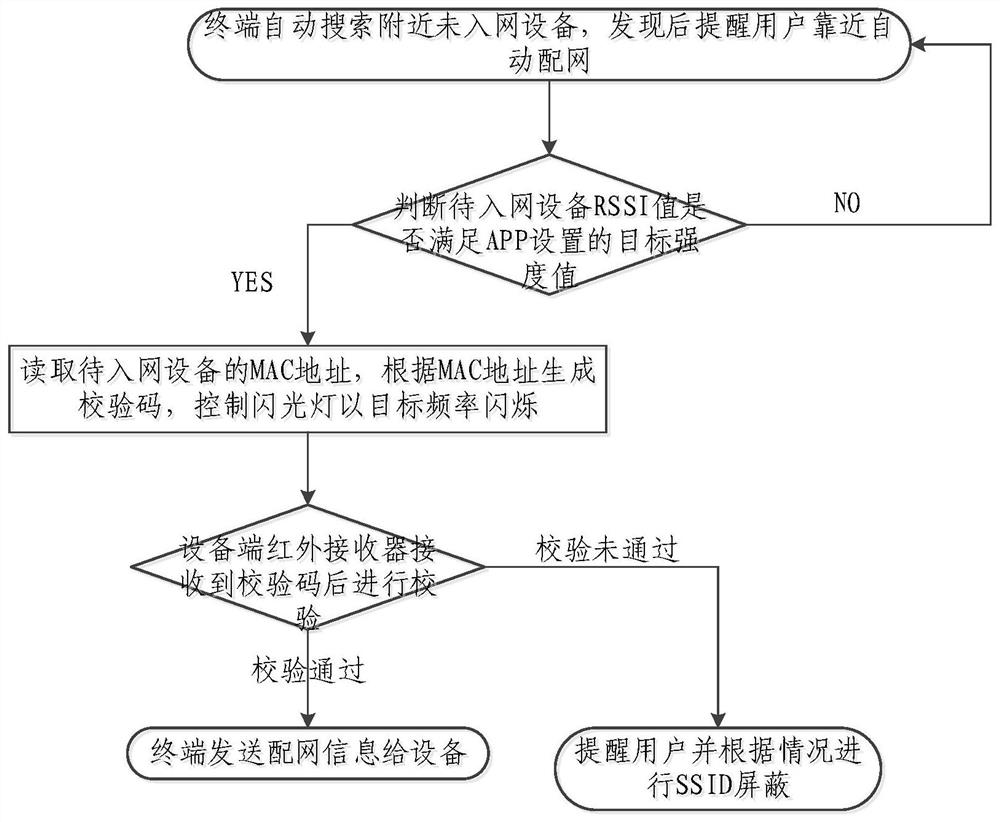
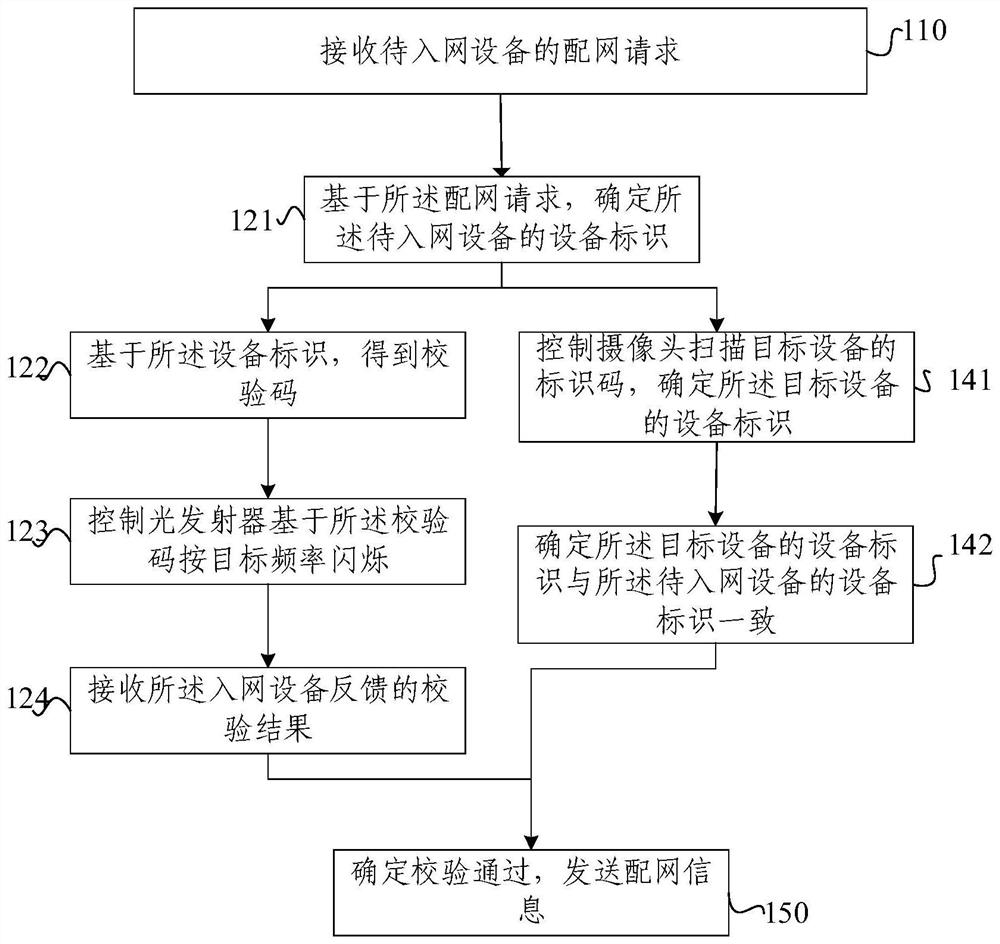
PendingCN112492611AEnsure safetyImprove securityAssess restrictionSecurity arrangementComputer hardwareLight signal
The invention relates to the technical field of communication, and provides a network configuration method, a network configuration device, electronic equipment and a readable storage medium, the network configuration method comprising: receiving a network distribution request of equipment to be accessed to a network; determining an equipment identifier of the equipment to be accessed to the network based on the network distribution request; determining a check code based on the equipment identifier; controlling an optical transmitter to flicker according to a target frequency based on the check code so as to be received by an optical receiver of the equipment to be accessed to the network; receiving a verification result fed back by the equipment to be accessed to the network; and determining that the verification is passed, and sending the distribution network information. According to the network configuration method provided by the embodiment of the invention, an optical signal isused as a verification medium when the network configuration request is received, and the light cannot penetrate through a wall, so that the safety of the network configuration can be ensured, and thepotential safety hazard and risk existing in the later period can be reduced.
Owner:MIDEA SMART TECH CO LTD +1
Dynamic token working method and dynamic token working system
ActiveCN104333555AWork process safetyProcess safetyUser identity/authority verificationWork systemsAuthentication
The invention a dynamic token working method and a dynamic token working system. The authentication requirements of users are divided into two categories in advance, namely login authentication requirements and signature authentication requirements during signature in the transaction processes (after login); after the dynamic token is activated successfully, the dynamic token generates corresponding login private keys and signature private keys for the two categories of the authentication requirements in advance. Subsequently, when a user has the transaction requirement and needs login or signature authentication, the dynamic token generates a corresponding login answer-back code or a signature answer-back code for the user according to the login private key or the signature private key in combination with a challenge code input by the user at the moment. Obviously, according to the dynamic token working method, different calculation private keys are set for different authentication requirements of the users, and therefore, the private keys of the dynamic token are not easy to break, and the working mechanism and the working flow of the dynamic token are safer; besides, dual authentication during the transactions of the users is realized, the difficulty for lawbreakers to reversely infer the working principle of the dynamic token is improved, and the security of user accounts is guaranteed.
Owner:CHINA CONSTRUCTION BANK
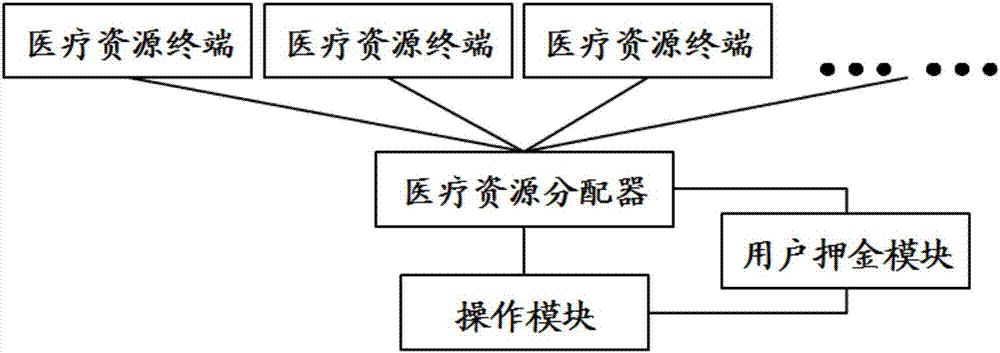
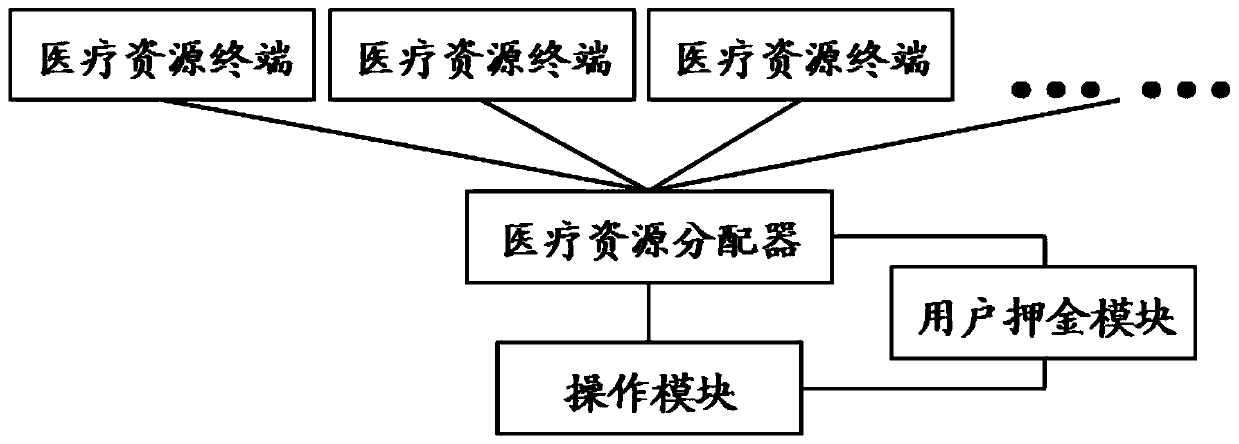
Medical resource scheduling platform
PendingCN111582699AImprove matching efficiencyImprove configuration efficiencyHealthcare resources and facilitiesResourcesResource assignmentThe Internet
The invention discloses a medical resource scheduling platform, which comprises a medical resource distribution system, and is characterized in that the medical resource distribution system comprisesa medical resource distributor, an operation module and a plurality of medical resource terminals; by means of the distribution system, medical resources can be scheduled and matched systematically through an online mode by means of the Internet, and therefore the medical resource matching efficiency and accuracy are improved; furthermore, the platform also comprises a doctor-side identity authentication system, so that the authenticity and efficiency of doctor identity authentication can be improved; furthermore, the platform comprises a search matching system, so that a doctor can search a matching result more accurately.
Owner:广州睿临网络科技有限公司
Password input authentication method and system
ActiveCN105447353AImplement two-factor authenticationReduced Chances of PrivacyDigital data authenticationValidation methodsUser input
The present invention relates to a password input authentication method and system. The method comprises: according to a set password, for a set key in the password, presetting a pressure authentication value used for password authentication; when a user inputs a password, acquiring default password information in a default way and detecting a pressure detection value pressed on the set key; and performing password authentication according to the default password information, and the pressure authentication value and the pressure detection value that are corresponding to the set key. According to the technical scheme provided by the present invention, dual authentication is achieved, so that a bystander can only directly watch the default input way in the password input process and can not break the password of the user in spite of password leakage, thereby reducing probability of user privacy stealing and improving security.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
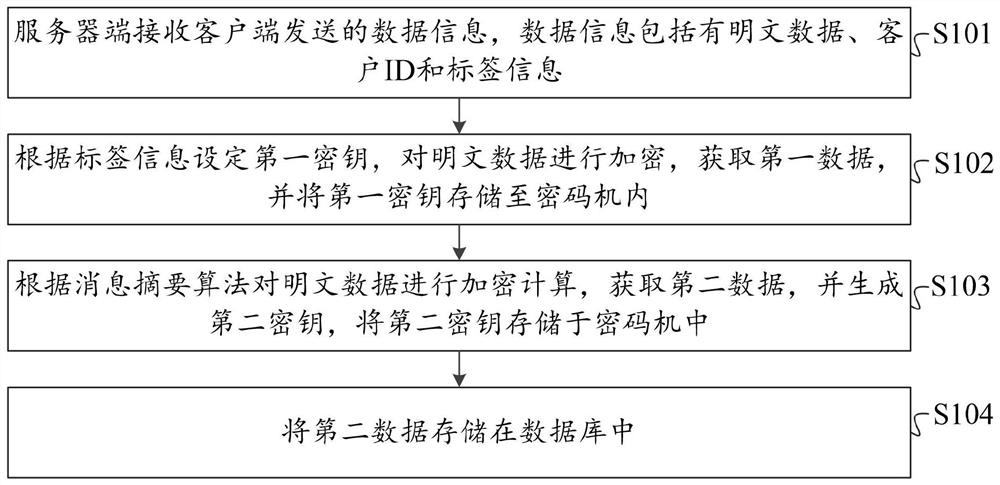
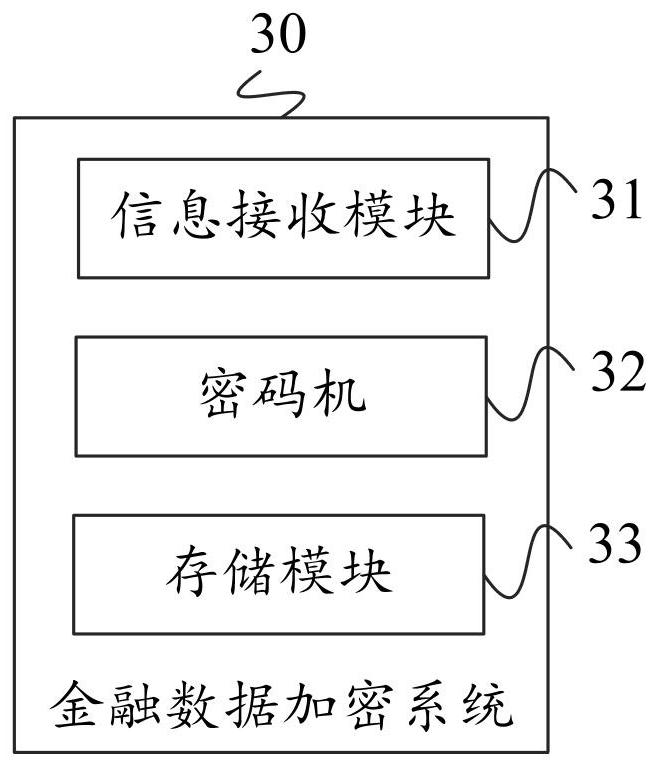
Financial data encryption method and system, financial data decryption method and system, equipment and storage medium
PendingCN112685786AImprove securityImplement separation of privilegesFinanceDigital data protectionKey storageData information
The invention provides a financial data encryption and decryption method, system and device and a storage medium, and the method comprises the following steps: a server receiving data information sent by a client, wherein the data information comprises plaintext data and label information; setting a first secret key according to the label information, encrypting the plaintext data to obtain first data, and storing the first secret key into a cipher machine; performing encryption calculation on the plaintext data according to a message digest algorithm to obtain second data, generating a second key, and storing the second key in a cipher machine; and storing the first data and the second data in a database. The authority of data information management and the authority of secret key management are separated, when the data information is obtained, double verification of the server side and the cipher machine needs to be carried out on the client side, and the safety of the data information is improved.
Owner:永辉云金科技有限公司
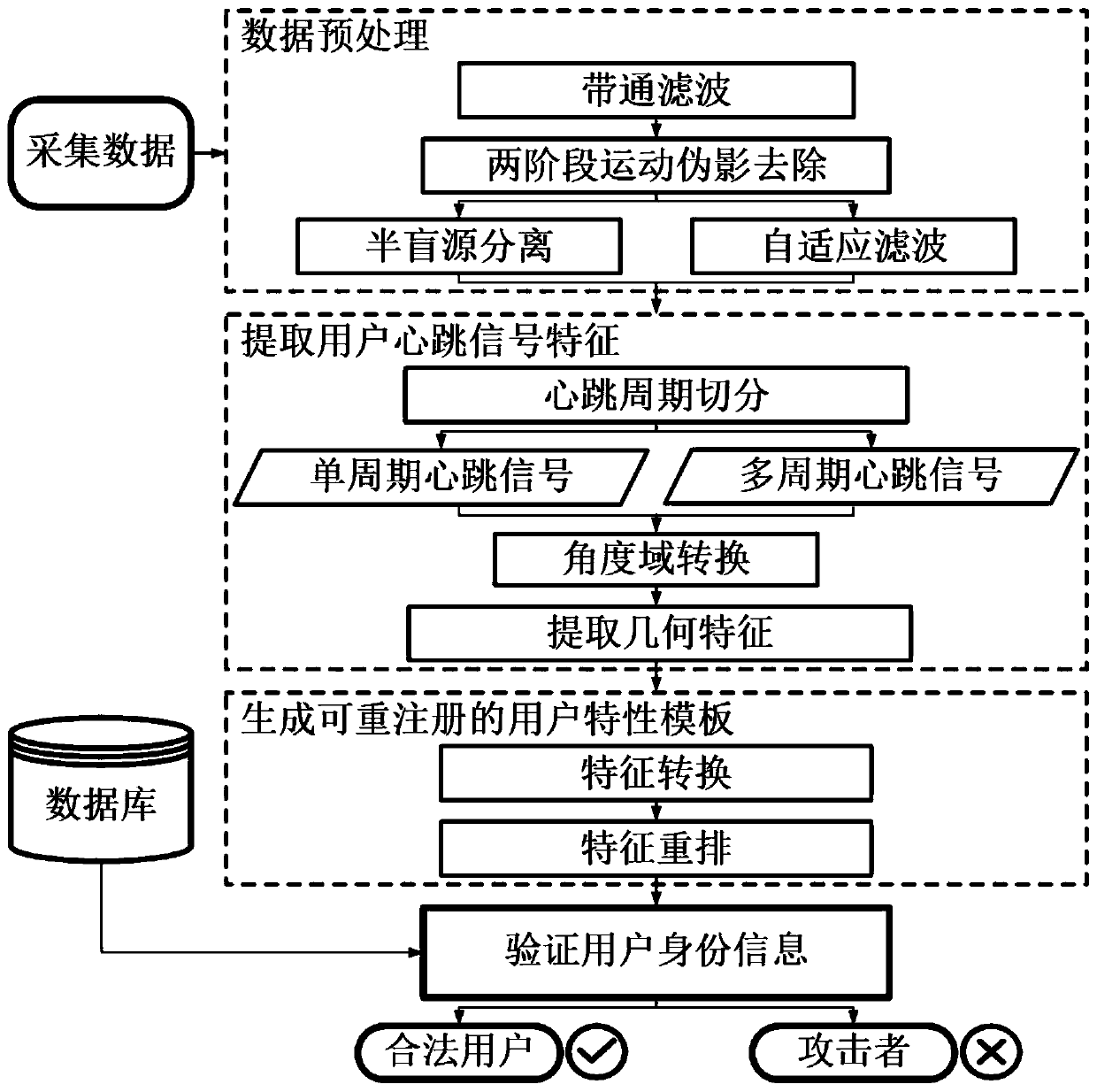
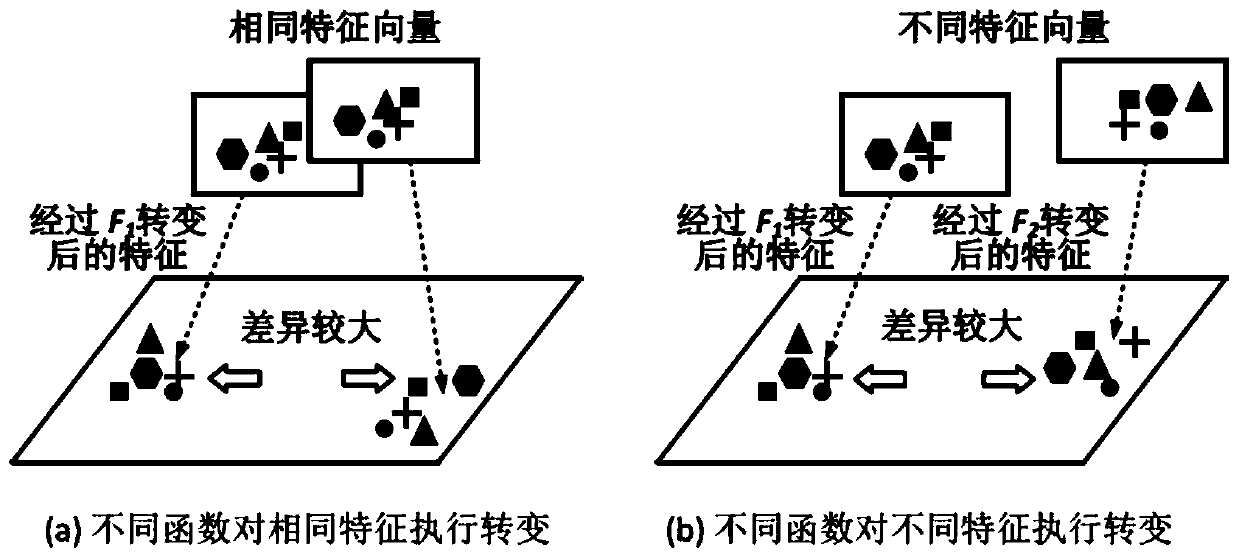
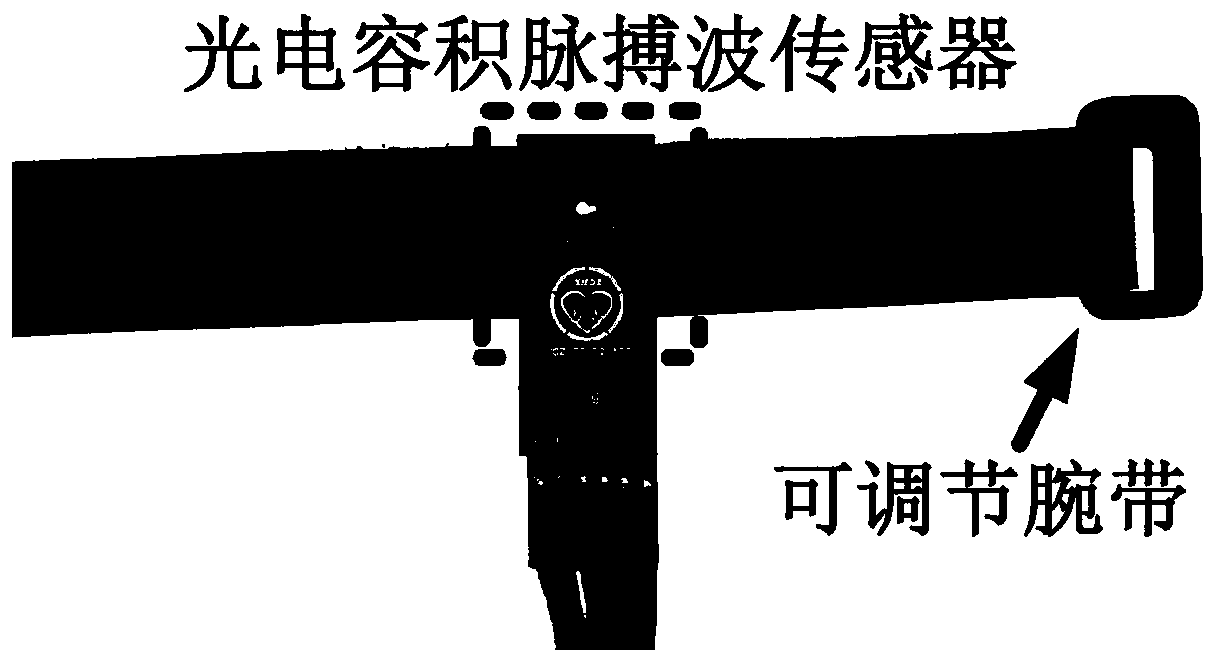
Two-factor authentication method based on photoplethysmography sensor
ActiveCN111444489APersistent mobile two-factor authenticationSecure Mobile Two-Factor AuthenticationDiagnostic signal processingDiagnostics using lightTime domainAdaptive filter
The invention relates to a two-factor authentication method based on a photoplethysmography sensor, and belongs to the technical field of mobile computing application. The photoelectric volume pulse wave sensor is used for collecting heartbeat signals of a user. A semi-blind source separation technology and an adaptive filtering technology are utilized to carry out noise removal processing on heartbeat signals interfered by motion artifacts, and pure heartbeat signals are extracted. And time domain and angle domain coordinate conversion is carried out on the extracted heartbeat signals. And the geometrical characteristics are extracted from the converted heartbeat signals, and a series of characteristics capable of uniquely identifying the user are obtained after conversion and encryptionalgorithm processing. Heartbeat signals are collected through the photoelectric volume pulse wave sensor of the intelligent wrist strap device, and double-factor authentication of a user is achieved.According to the invention, high-security identity authentication is supported, and the user is allowed to re-register the alternative credentials so as to resist replay attacks and man-in-the-middleattacks. A user does not need to keep still, and a common verification method can be used at the same time.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
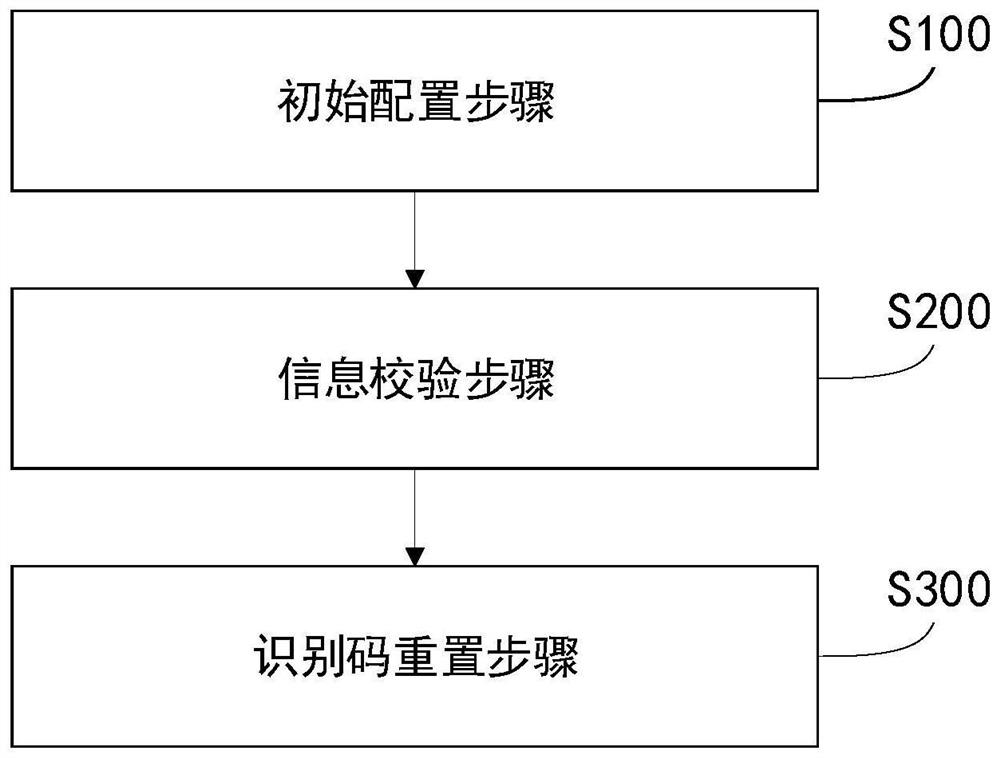
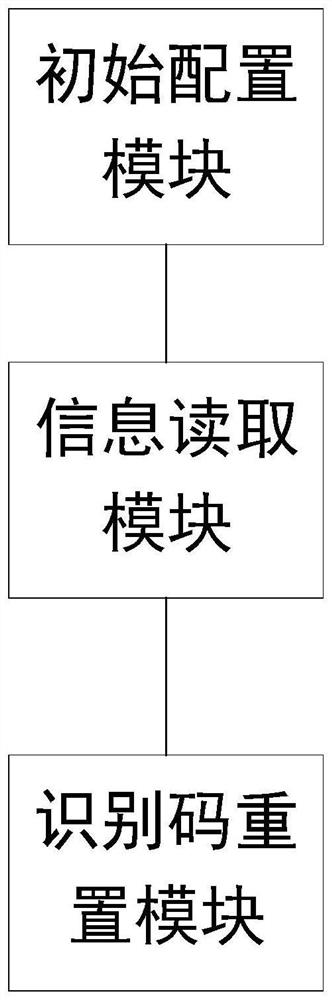
Social security card PIN resetting method and system based on standard interface and medium
PendingCN114239006AThe development logic is ingeniousUniversalDigital data protectionEmbedded systemData processing
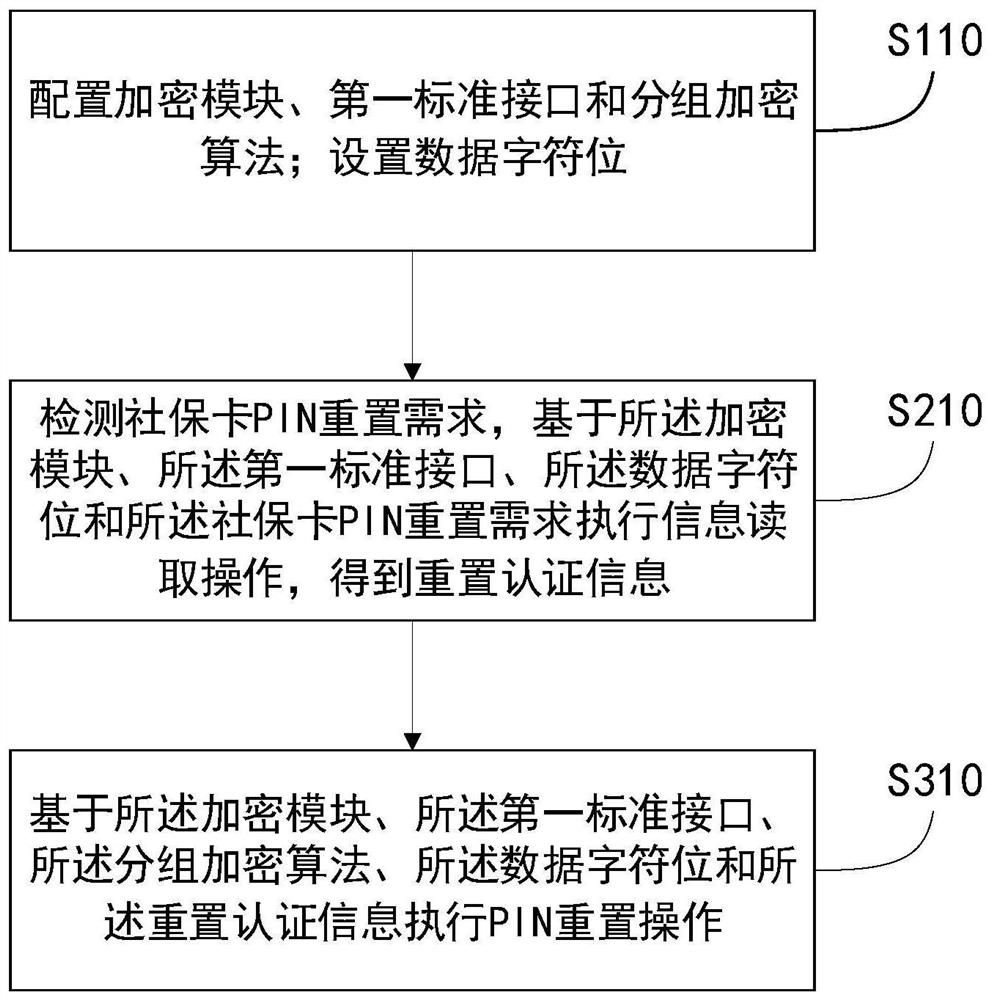
The invention discloses a social security card PIN resetting method and system based on a standard interface, and a medium. The method comprises the following steps: configuring an encryption module, a first standard interface and a block encryption algorithm; setting data character bits; detecting a social security card PIN reset demand, and executing an information reading operation based on the encryption module, the first standard interface, the data character bit and the social security card PIN reset demand to obtain reset authentication information; executing a PIN reset operation based on the encryption module, the first standard interface, the block encryption algorithm, the data character bit and the reset authentication information; according to the method, the unified standard interface of the social security card data processing module can be designed and called, information reading, information dual authentication and PIN resetting of the social security card can be realized without repeatedly developing or repeatedly designing a port by the social security card data processing module, and more comprehensive social security card data processing requirements are met.
Owner:INSPUR FINANCIAL INFORMATION TECH CO LTD
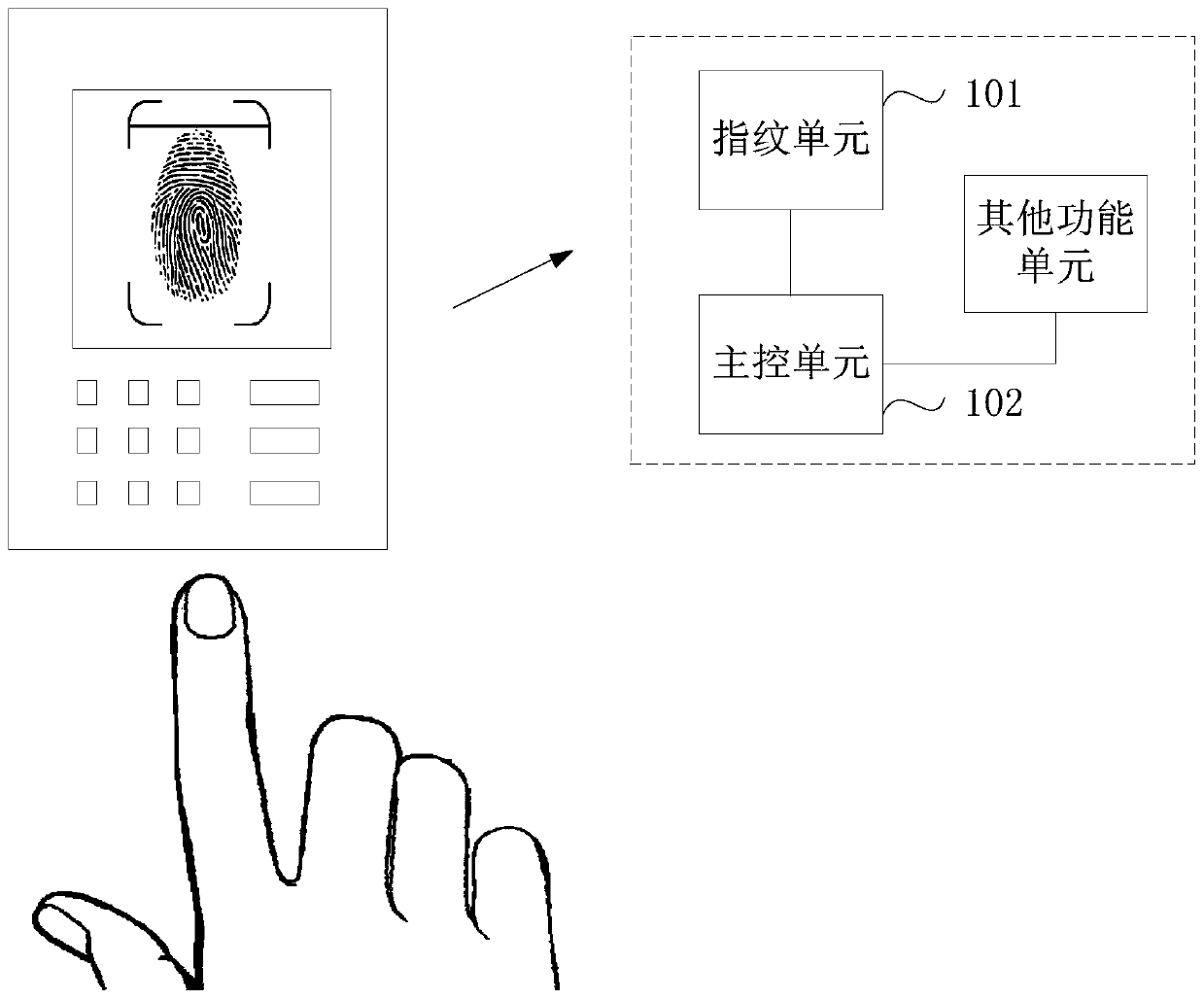
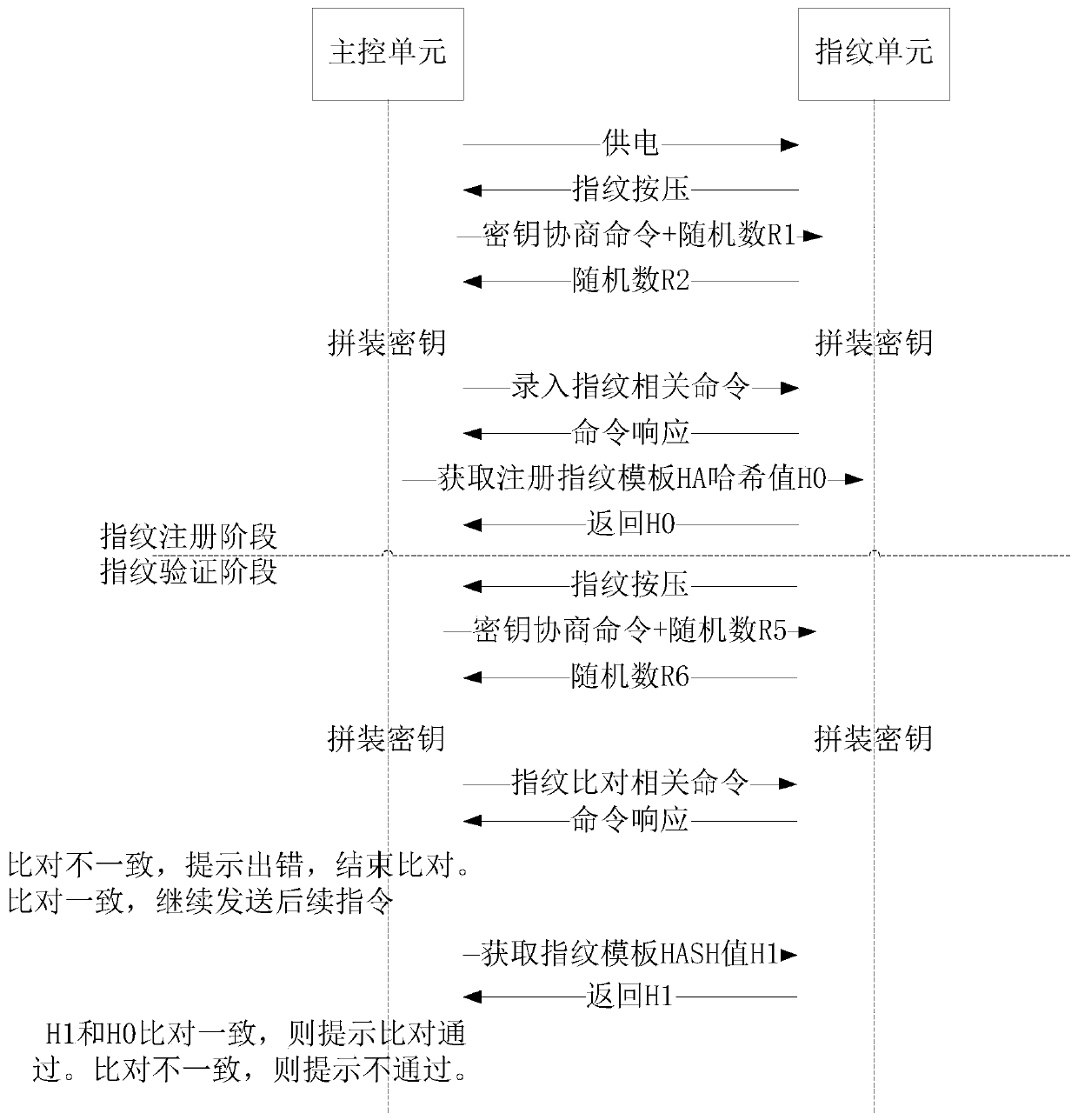
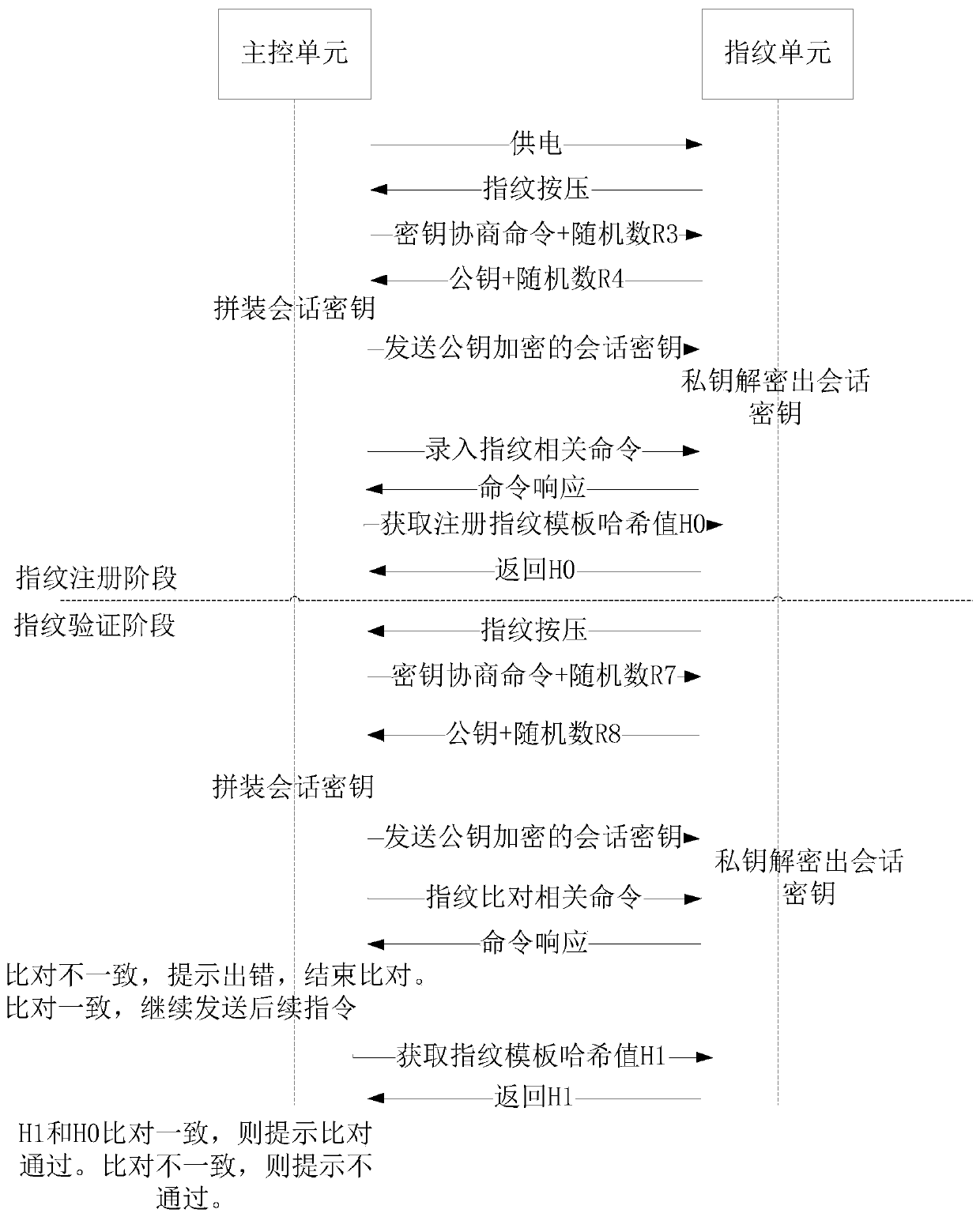
Fingerprint registration method and device and fingerprint verification method and device
PendingCN110532927AImprove securityAvoid substitutionIndividual entry/exit registersMatching and classificationFingerprintControl unit
The invention relates to a fingerprint registration method and device and a fingerprint verification method and device. The fingerprint registration method comprises the following steps: acquiring a fingerprint to be registered; generating a registration fingerprint template according to the fingerprint to be registered; performing abstract operation on the registered fingerprint template to obtain a first hash value; wherein the first hash value is used for verifying that the fingerprint template for fingerprint verification is a registered fingerprint template during fingerprint verification; storing the registered fingerprint template; and sending the first hash value to a main control unit for storage. Abstract operation can be performed on the registered fingerprint template to obtainthe first hash value.According to the invention, the first hash value is stored in the main control unit, and when fingerprint verification needs to be carried out, whether the fingerprint template of the comparison fingerprint is the registered fingerprint template or not needs to be verified in addition to the comparison fingerprint, so that dual verification is realized, the fingerprint template is prevented from being replaced, and the safety of fingerprint verification is improved.
Owner:广东华芯微特集成电路有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com