Authentication method integrating mac authentication and web authentication
An authentication method and mac address technology, applied to electrical components, transmission systems, etc., can solve problems such as a single authentication method, and achieve the effects of improving security, reducing maintenance costs, and reducing the amount of configuration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
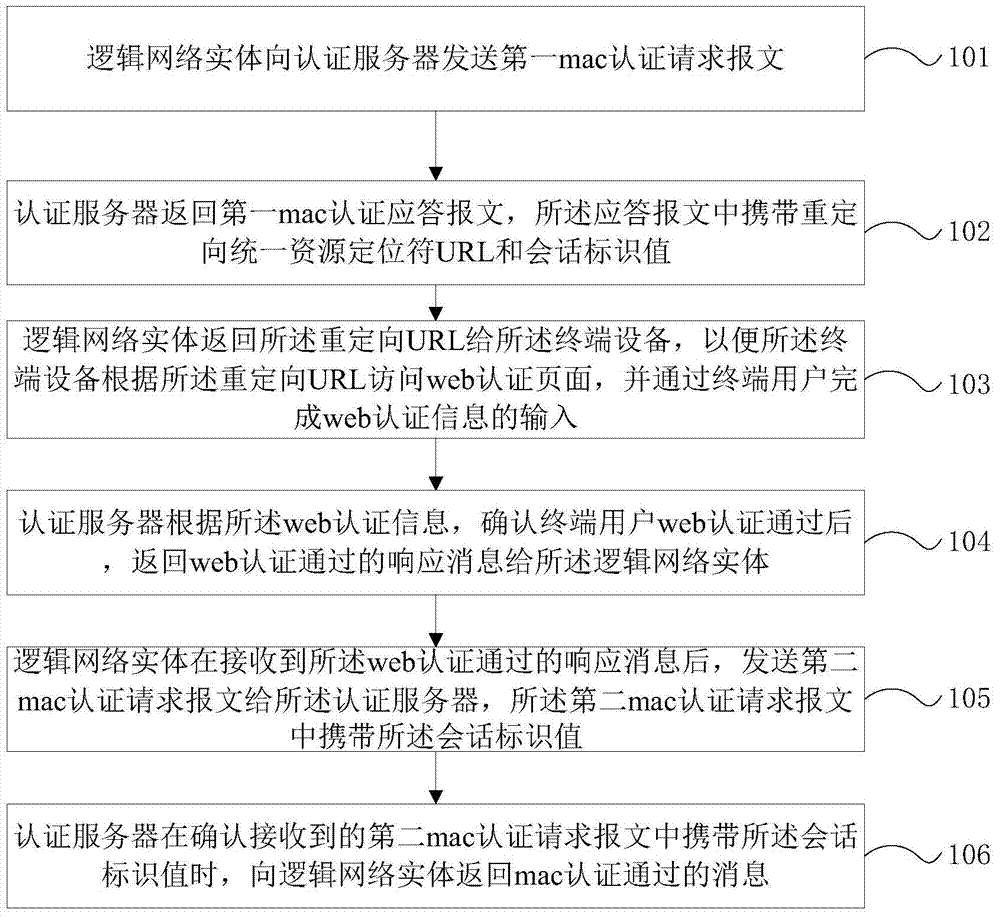
[0017] Such as figure 1 Shown is a flow chart of an authentication method that integrates mac authentication and web authentication provided by the present invention, wherein the authentication of the terminal device includes mac authentication and web authentication, and the terminal user triggers the authentication of the terminal device by the logical network entity mac authentication, the manner of triggering the first mac authentication message may specifically be: the terminal user sends a Dynamic Host Configuration Protocol (Dynamic host configuration protocol, DHCP) request, a Hyper Text Transport Protocol (Hyper Text Transport Protocol, HTTP) request or a hypertext Transport protocol security (Hyper Text Transfer Protocol, HTTPS) request. Such as figure 1 As shown, the method includes the following steps:
[0018] In step 101, the logical network entity sends a first mac authentication request message to an authentication server.
[0019] In step 102, the authentic...
Embodiment 2
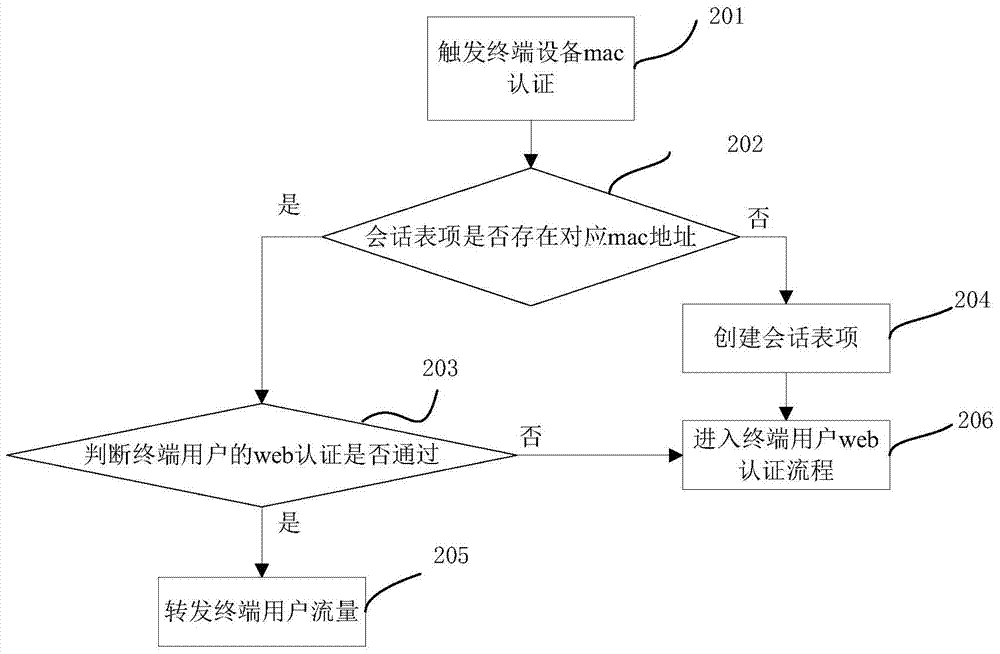
[0039] Such as figure 2 Shown is the flow of an authentication method that integrates mac authentication and web authentication provided by the embodiment of the present invention, which consists of figure 2 It can be seen that this embodiment focuses on explaining the operation content of the logical network entity before sending the first mac authentication request, specifically including:
[0040] In step 201, mac authentication of the terminal device is triggered.
[0041] The way of triggering the mac authentication of the terminal device may be when the terminal device sends a DHCP request, HTTP request or HTTPS request to the logical network entity, but the way of triggering the mac authentication of the terminal device is not limited to the above ways. After the terminal device triggers mac authentication, step 202 is executed.
[0042] In step 202, after the terminal device triggers mac authentication, the logical network entity extracts the source mac address of ...
Embodiment 3
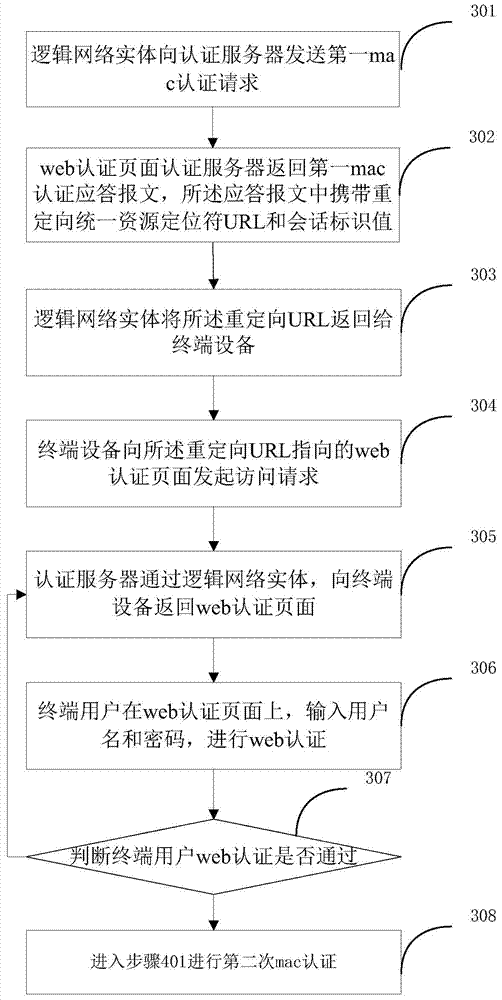
[0048] Such as image 3 As shown, this embodiment is aimed at the refinement of the web authentication content in the first embodiment, which is specifically connected after step 206 in the second embodiment, and combined with the second embodiment to form a solution. Specifically include:
[0049] In step 301, the logical network entity sends a first mac authentication request to the authentication server.
[0050] Wherein, after the logical network entity receives the HTTP request or the HTTPS request of the terminal device, it triggers the mac authentication of the terminal device, and before sending the first mac authentication request, it also specifically includes a TCP spoofing operation, the described The operation of TCP spoofing means that after the logical network entity intercepts the HTTP request or HTTPS request from the terminal device, it modifies the destination address and destination port number in the HTTP request message (or HTTPS request message) to the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com