Dynamic token working method and dynamic token working system
A technology of dynamic tokens and working methods, which is applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as increasing the difficulty of deriving the working principle of dynamic tokens for criminals, and achieves the goal of being difficult to crack, The effect of increasing difficulty and ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0058] This embodiment one discloses a dynamic token working method, refer to figure 1 , the method may include the following steps:
[0059] S101: Receive a login response code generation request from a user, where the login response code generation request includes a login challenge code.
[0060] Before using the dynamic token for the first time, the user needs to activate the dynamic token, that is, each step of the present invention needs to be based on the preprocessing of activating the dynamic token.
[0061] When activating the dynamic token, the authentication server generates an activation code, and then the user manually enters the activation code generated by the server into the dynamic token. The activation code generation algorithm is as follows:
[0062] ActiveCode=ChallengeRand|Truncate_SM3(SM3(Seed|ChallengeRand))) (1)
[0063] In formula (1), ActiveCode represents a 12-digit activation code; ChallengeRand represents a 6-digit decimal random number, which n...
Embodiment 2
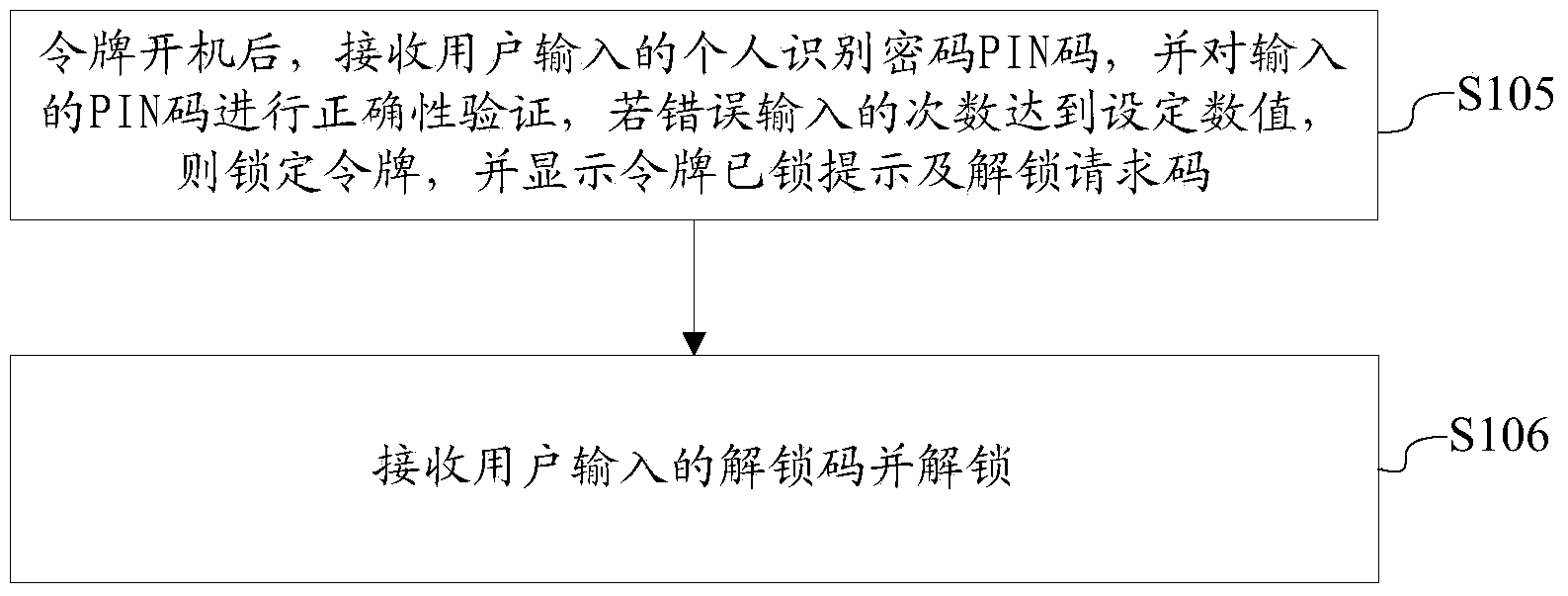
[0114] In the second embodiment, refer to figure 2 , the method may also include the following steps:
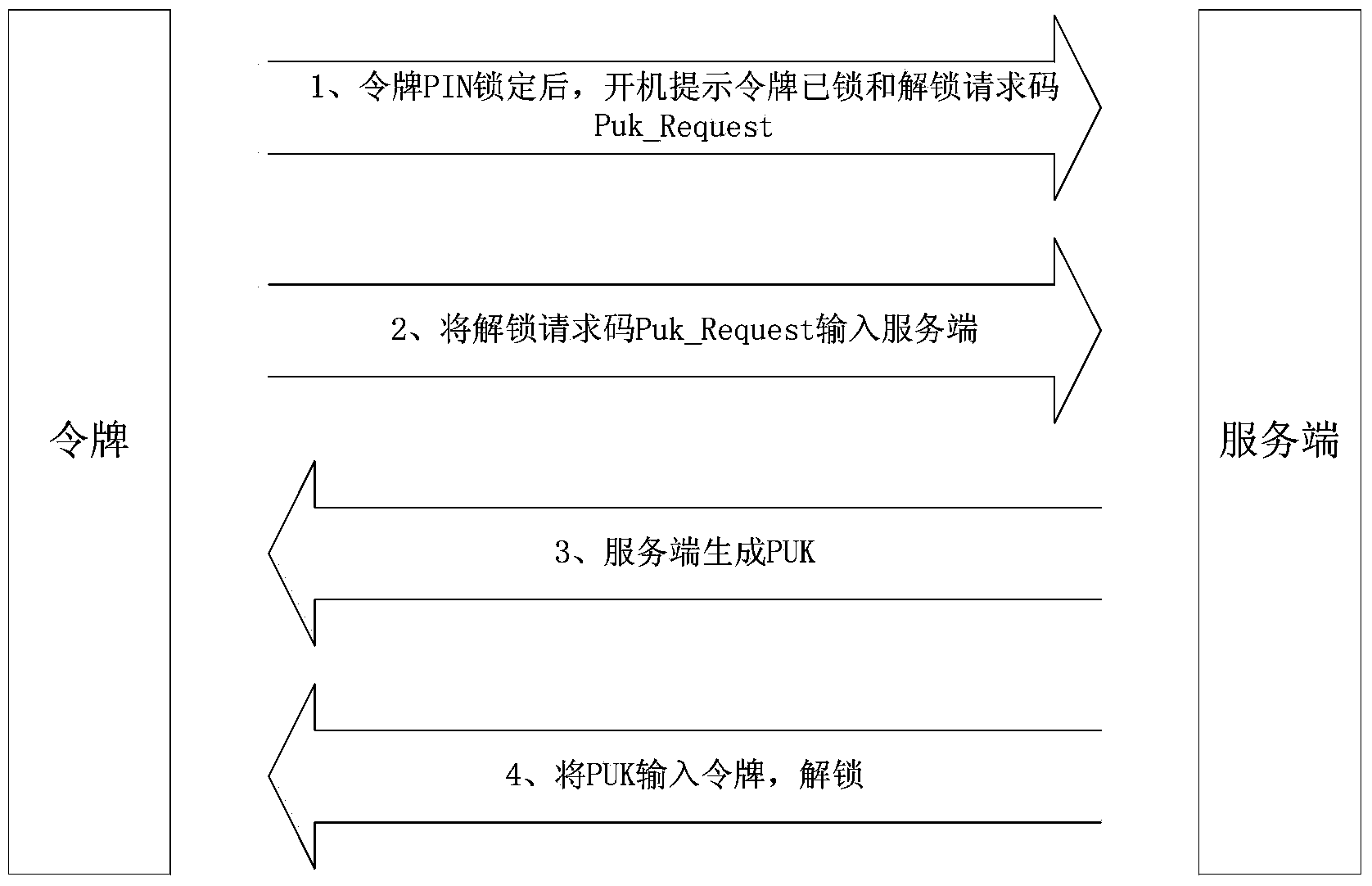
[0115] S105: After the token is turned on, receive the personal identification password PIN code input by the user, and verify the correctness of the entered PIN code. If the number of incorrectly entered PIN codes reaches the set value, the token will be locked and the token will be displayed. Lock reminder and unlock request code;
[0116] S106: Receive the unlock code input by the user and unlock it. The unlock code is generated by the authentication server according to the formula PUK=Truncate_SM3(SM3(Puk_Seed|Puk_Request)), where Truncate_SM3 represents the SM3 truncation algorithm, PUK represents the unlock code, and Puk_Request represents the unlock request code.
[0117] Specifically, this embodiment expands the calculation key to three: a login key, a signature key, and an unlock key. Therefore, while pre-defining the login key and signature key, the unlock key ...
Embodiment 3
[0132] Embodiment 3 discloses a dynamic token working system, which corresponds to the dynamic token working methods disclosed in Embodiment 1 and Embodiment 2.
[0133] First, corresponding to Embodiment 1, refer to Figure 4 , the system includes a first receiving module 100 , a first processing module 200 , a second receiving module 300 and a second processing module 400 .
[0134] The first receiving module 100 is configured to receive a user's login response code generation request, where the login response code generation request includes a login challenge code.
[0135] The first processing module 200 is configured to process the login challenge code, the pre-generated login key in the dynamic token and the current real-time time to obtain a login response code, the login key is when the dynamic token is activated , which is generated based on its built-in seed key, login purpose code, and activation code provided by the authentication server.
[0136] Wherein, the fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com