Verification code authentication method and system based on biological characteristics
A biometric, authentication method technology, applied in the field of identity authentication, can solve the problems of card maintenance, limited data transmission, and no separation of man and machine.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
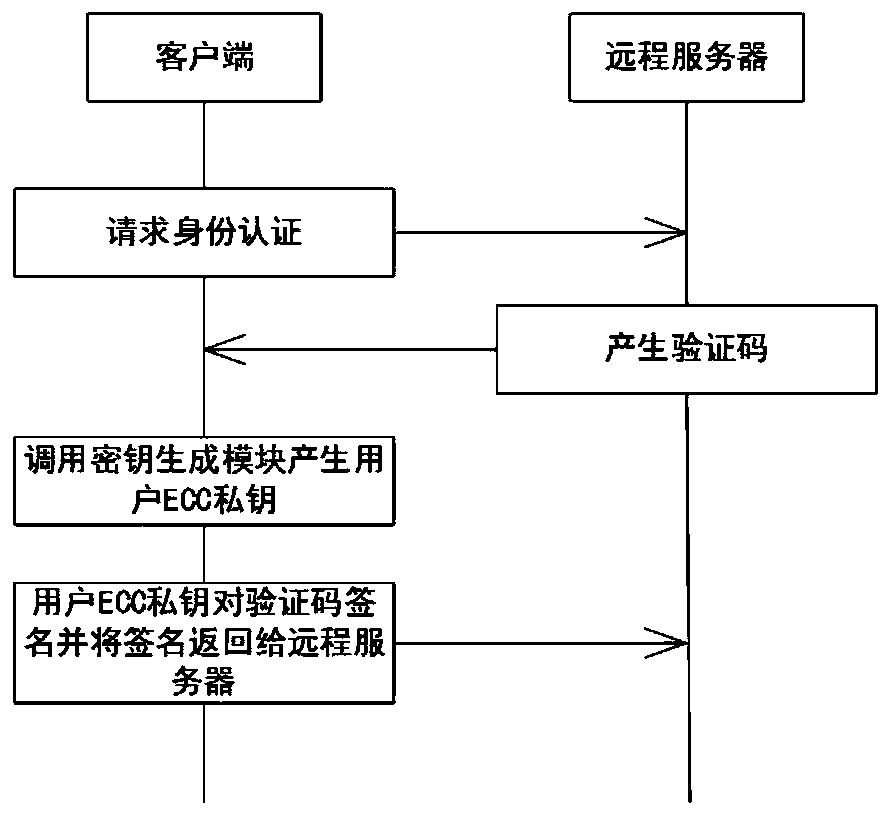
[0041] The verification code authentication method based on biometrics provided by this embodiment can be applied: when using mobile phone payment software to pay online, the third-party payment company uses the SMS verification code of the mobile phone message as the carrier to confirm the user's identity; or when the user forgets the login password , the third-party server sends a text message containing a verification code to the mobile phone number registered by the user, and the user enters the verification code into the prompt dialog box within the specified time and sends it to the remote server to verify the authenticity of the user's identity.
[0042] According to this embodiment, a biometric-based verification code authentication method is provided, such as figure 1As shown, the method is executed by the client, and it should be noted that the steps shown in the flowchart of the accompanying drawings can be executed in a computer system such as a set of computer-exec...
Embodiment 2
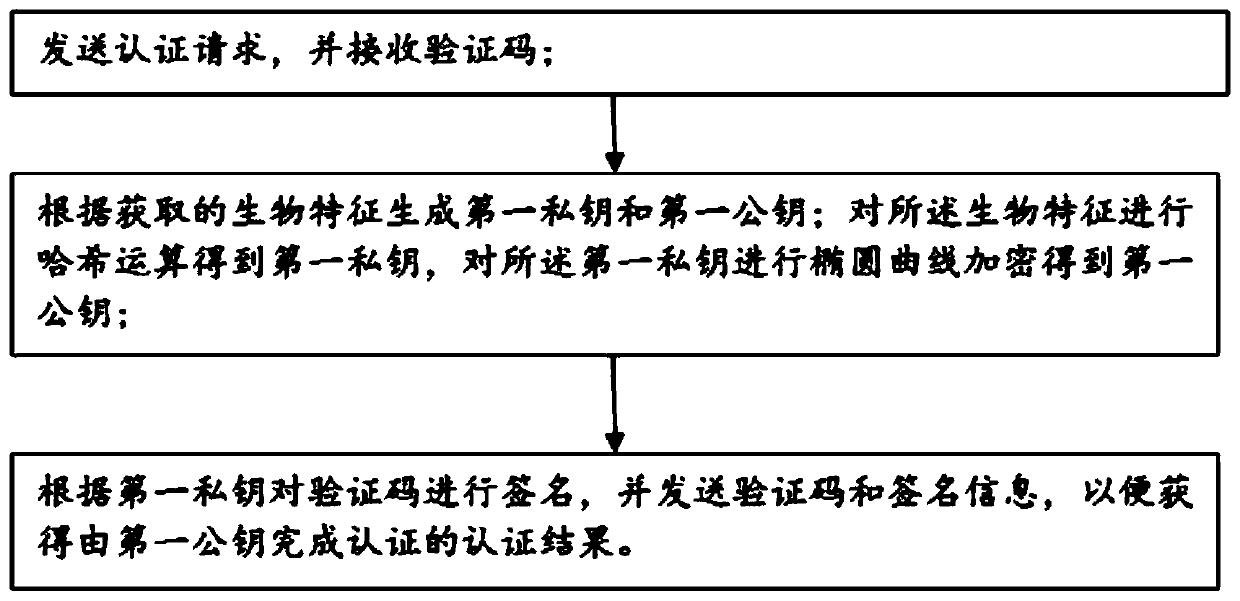
[0064] This embodiment provides a biometric-based verification code authentication method, which is executed by a client, and specifically includes:
[0065] S21: Send an authentication request and receive a verification code;
[0066] S22: Generate a first private key and a first public key according to the acquired biological characteristics; perform a hash operation on the biological characteristics to obtain a first private key, and perform elliptic curve encryption on the first private key to obtain a first public key;
[0067] S23: Transmit the generated first private key and first public key to the server using a key transmission rule;
[0068] S24: Sign the verification code according to the first private key, and send the verification code and signature information, so as to obtain a verification result verified by the first public key.
[0069] The step S21 corresponds to the step S11 of the first embodiment, and will not be repeated here.
[0070] The step S22 cor...
Embodiment 3
[0089] This embodiment provides a biometric-based verification code authentication method, which is executed by a server, and specifically includes:
[0090] S31: Receive a verification code and signature information obtained by signing the verification code with the first private key; the verification code is generated according to the received verification request, and the first private key carries biometric features;
[0091] S32: Verify the verification code and signature information according to the received first public key obtained through elliptic curve encryption with the first private key.
[0092] In the step S31, the obtaining of the first private key and the first public key and the signing process of the first private key correspond to the first embodiment, and will not be repeated here.
[0093] In the step S32, as Figure 6 As shown, the specific process of verifying the verification code and signature information according to the first public key includes:
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com