Key generation and distribution method for wireless communication system
A technology of a wireless communication system and a distribution method, which is applied in the field of key generation and distribution for wireless communication systems, can solve problems such as the inability to implement an attack mode wireless communication network system, and achieve the effects of realizing double authentication and preventing attack methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
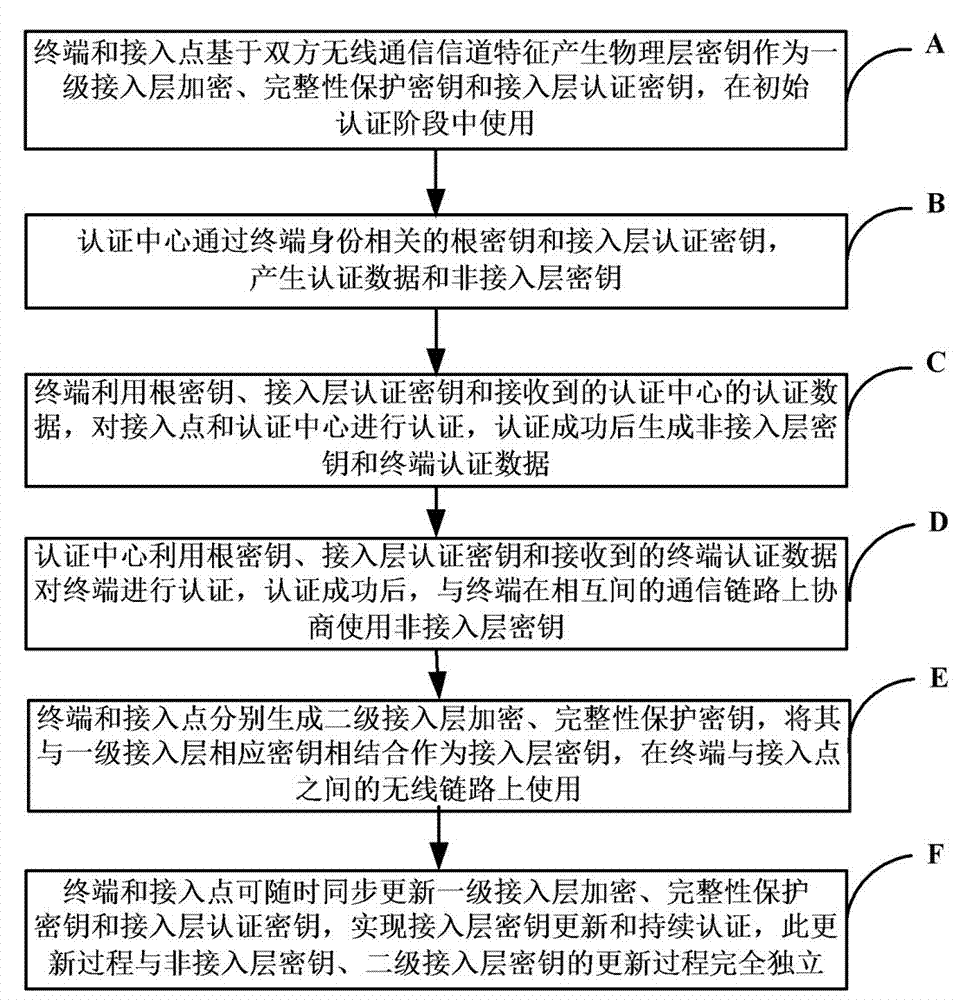
[0047] Example 1: Combining Figure 1-Figure 7 , a method for generating and distributing keys for a wireless communication system, comprising the following steps:
[0048] Step A: The terminal and the access point generate a physical layer key based on the characteristics of the wireless communication channel between the two parties as a primary access layer encryption, integrity protection key and access layer authentication key, including:
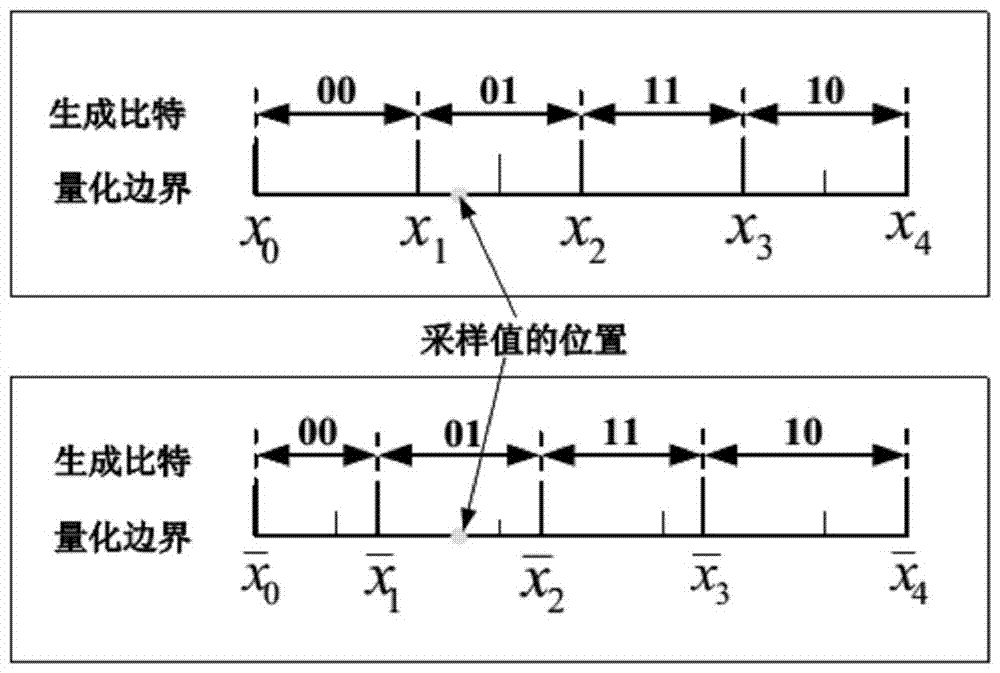
[0049] Step A1: The terminal and the access point measure the wireless channel to obtain channel characteristic parameters;
[0050] Step A2: The terminal and the access point use the channel characteristic parameters to generate a consistent physical layer key, which is used as the first-level access layer encryption and integrity protection key respectively, and is applied between the terminal and the access point before the initial authentication is successful. on the wireless channel between;
[0051] Step A3: The terminal and the...
Embodiment 2
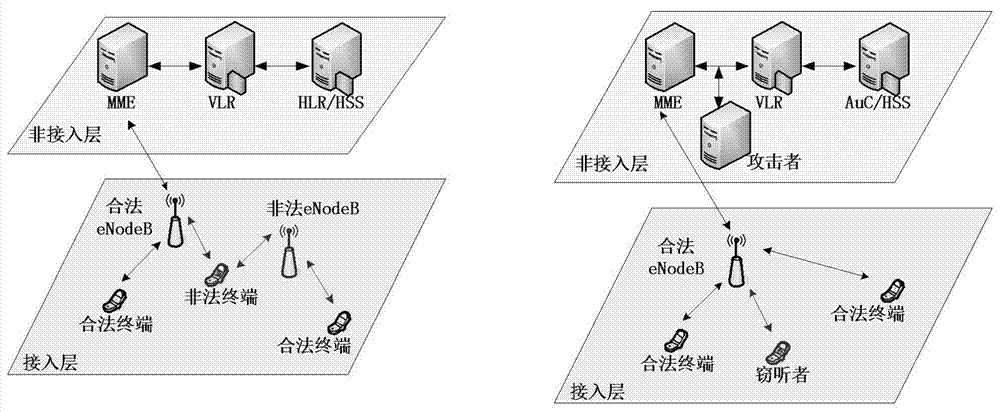
[0074] Example 2, combined with Figure 1-Figure 7 , the flow chart of the wireless communication system-oriented key generation and distribution method of the present invention, Figure 7 It is an example diagram of the wireless communication system-oriented key generation and distribution process of the present invention. The method includes the following steps:
[0075] Step A: The terminal and the access point generate a physical layer key based on the characteristics of the wireless communication channel between the two parties as a primary access layer encryption, integrity protection key and access layer authentication key, which are used in the initial authentication phase;
[0076] Step B: the authentication center generates the authentication data and the non-access layer key through the terminal identity-related root key and the access layer authentication key;
[0077] Step C: The terminal uses the root key, the access layer authentication key and the received au...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com