Creditable calculation password platform and realization method thereof
A technology of trusted computing and cryptographic algorithms, applied in computing, computer security devices, instruments, etc., can solve the problems of undefined trusted computing platform operating system, undefined measurement of application program integrity, etc., to increase the degree of attack resistance, Increase the scope of application and apply flexible effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention is further described as follows in conjunction with accompanying drawings and embodiments.
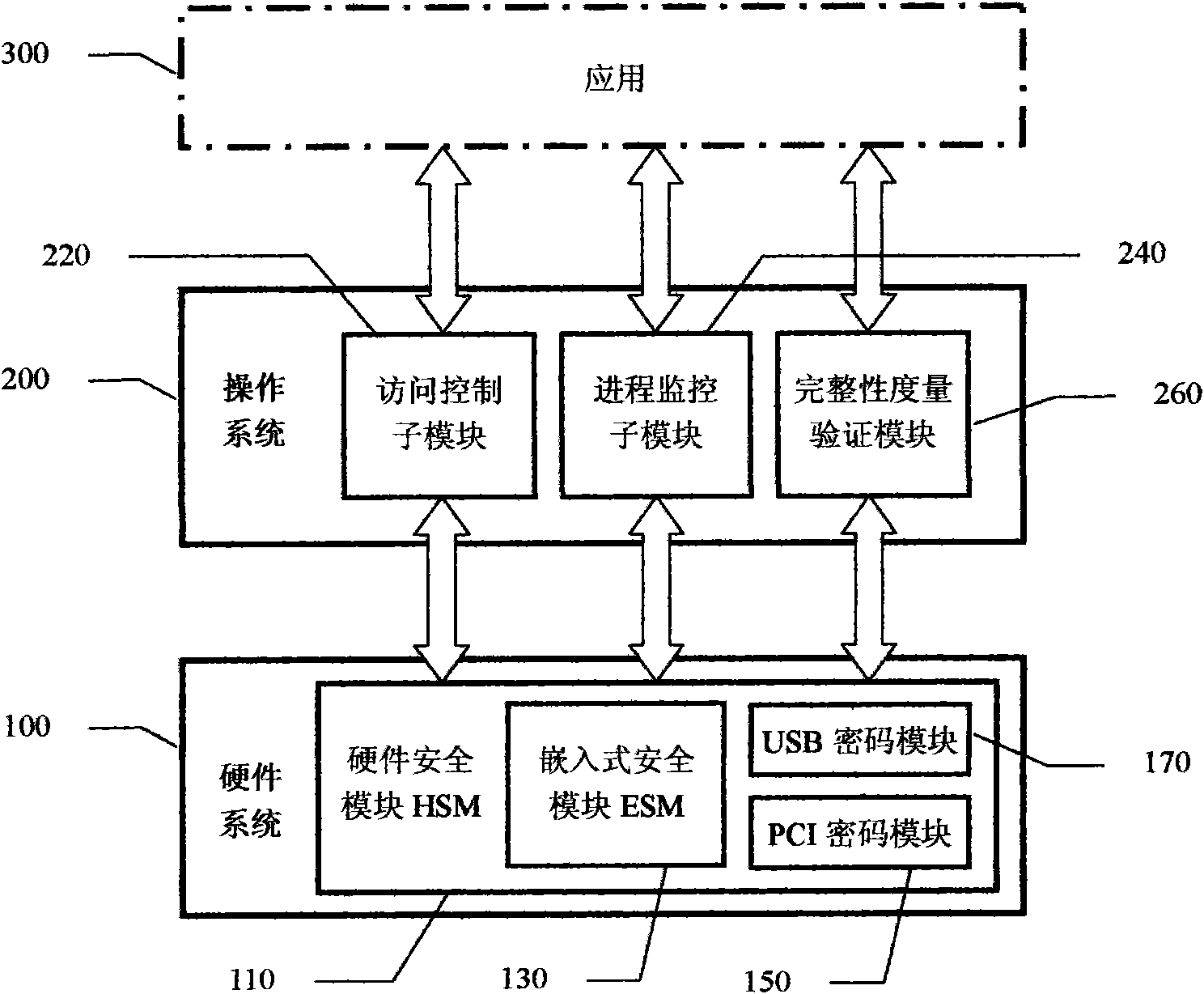
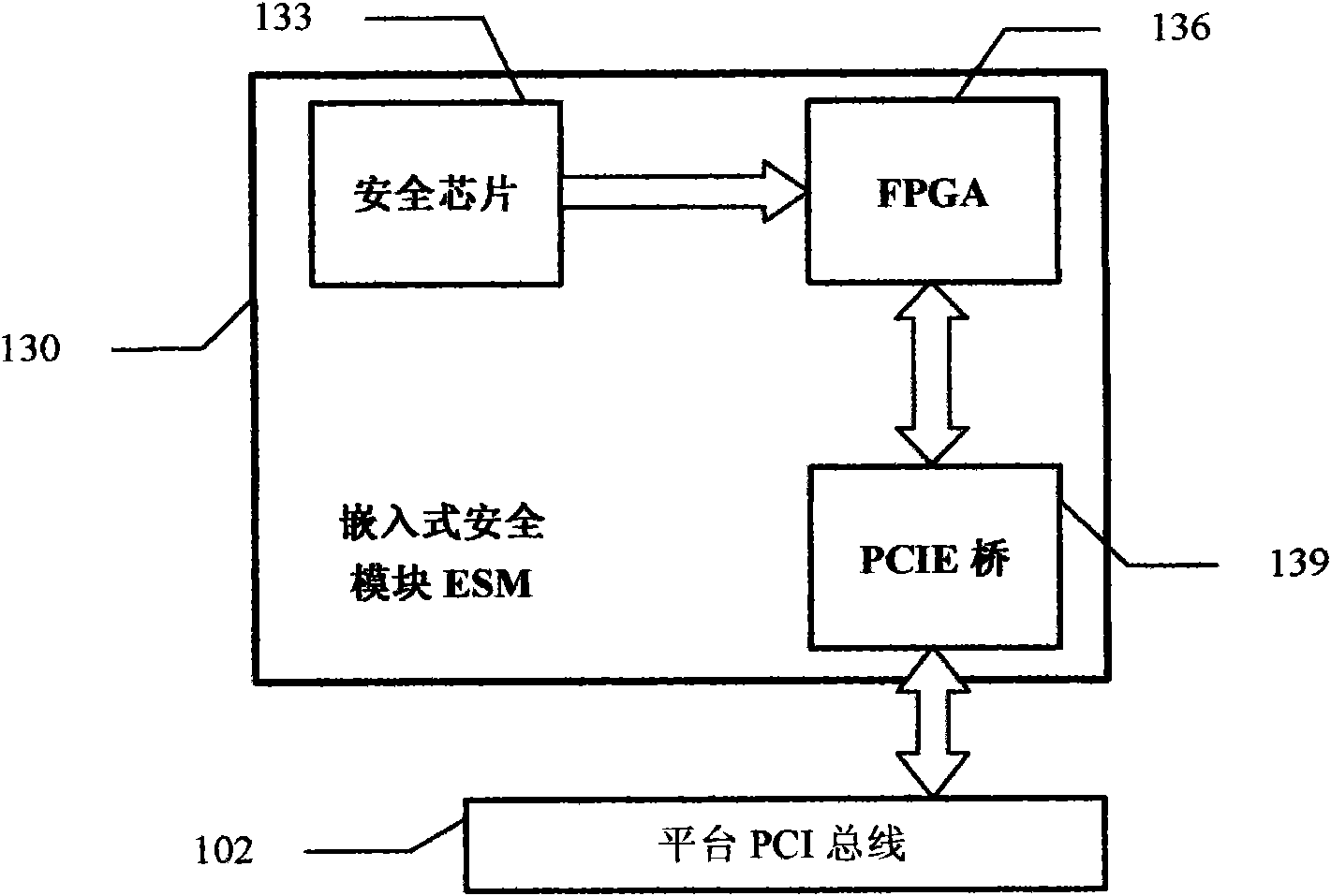
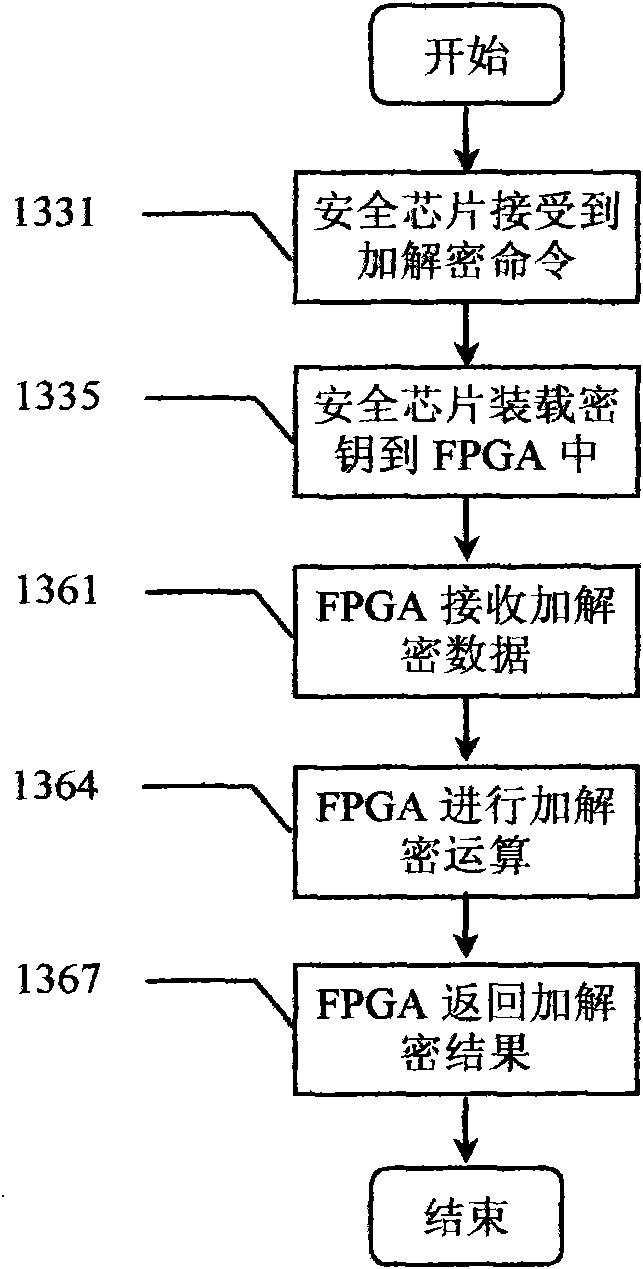
[0040] As shown in the figure, a trusted computing cryptographic platform adopts a multi-level structure, and has a hardware system 100 and an operating system 200; the hardware system 100 is connected to the operating system 200; the hardware system 100 has a hardware security module HSM 110 (Hardware Security Module); the hardware security module HSM 110 is bound to the platform, and is an embedded security module ESM 130 (Embedded Security Module) connected to the motherboard, or a pluggable USB / PCI password module 170 / 150, when it is the pluggable USB password module 170, or the PCI password module 150, or when the three all have, then it is a different embodiment; the operating system 200 has an operating system security module, which is accessed by mandatory It consists of a control submodule 220, a process monitoring submodule 240, and an applicatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com