A system and method for protecting Linux operating system security base on IMA
An operating system and security technology, applied in computer security devices, platform integrity maintenance, instruments, etc., can solve problems such as the inability of security protection software to effectively protect, and pay little attention to the security of Linux operating system, so as to protect integrity and enhance safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
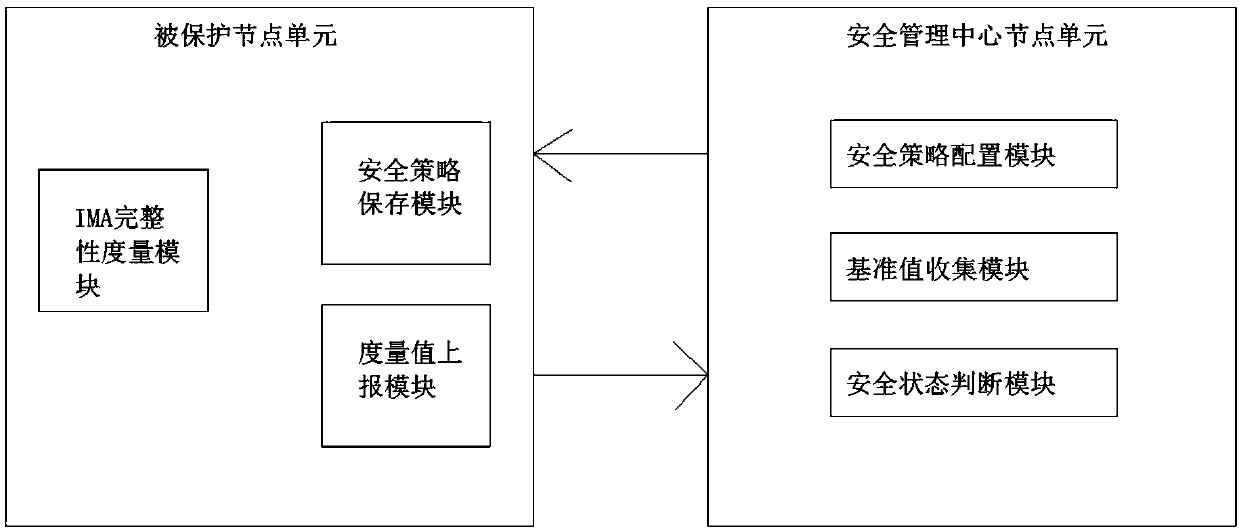
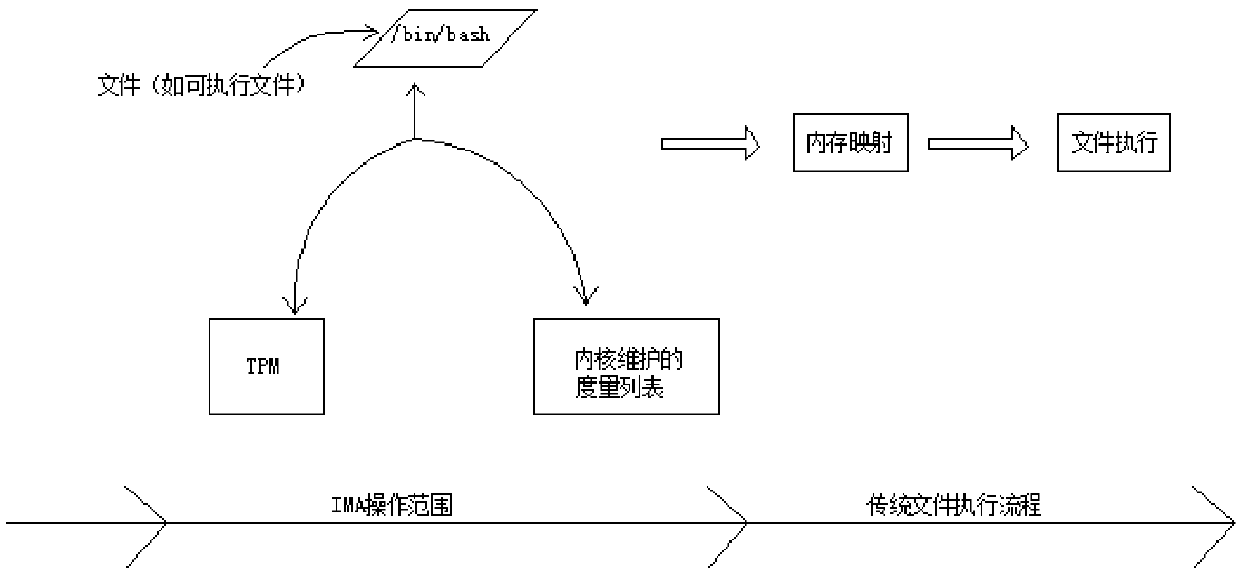
[0046]Embodiment 1 of the present invention provides a system and method for protecting the security of a Linux operating system based on IMA. Such as figure 1 Shown is a system architecture diagram for protecting the security of a Linux operating system based on IMA in Embodiment 1 of the present invention. The system includes a safety management center node unit and a protected node unit.
[0047] The security management center node unit is used for unified policy configuration and security status judgment, and mainly includes a security policy configuration module, a benchmark value collection module and a security status judgment module.
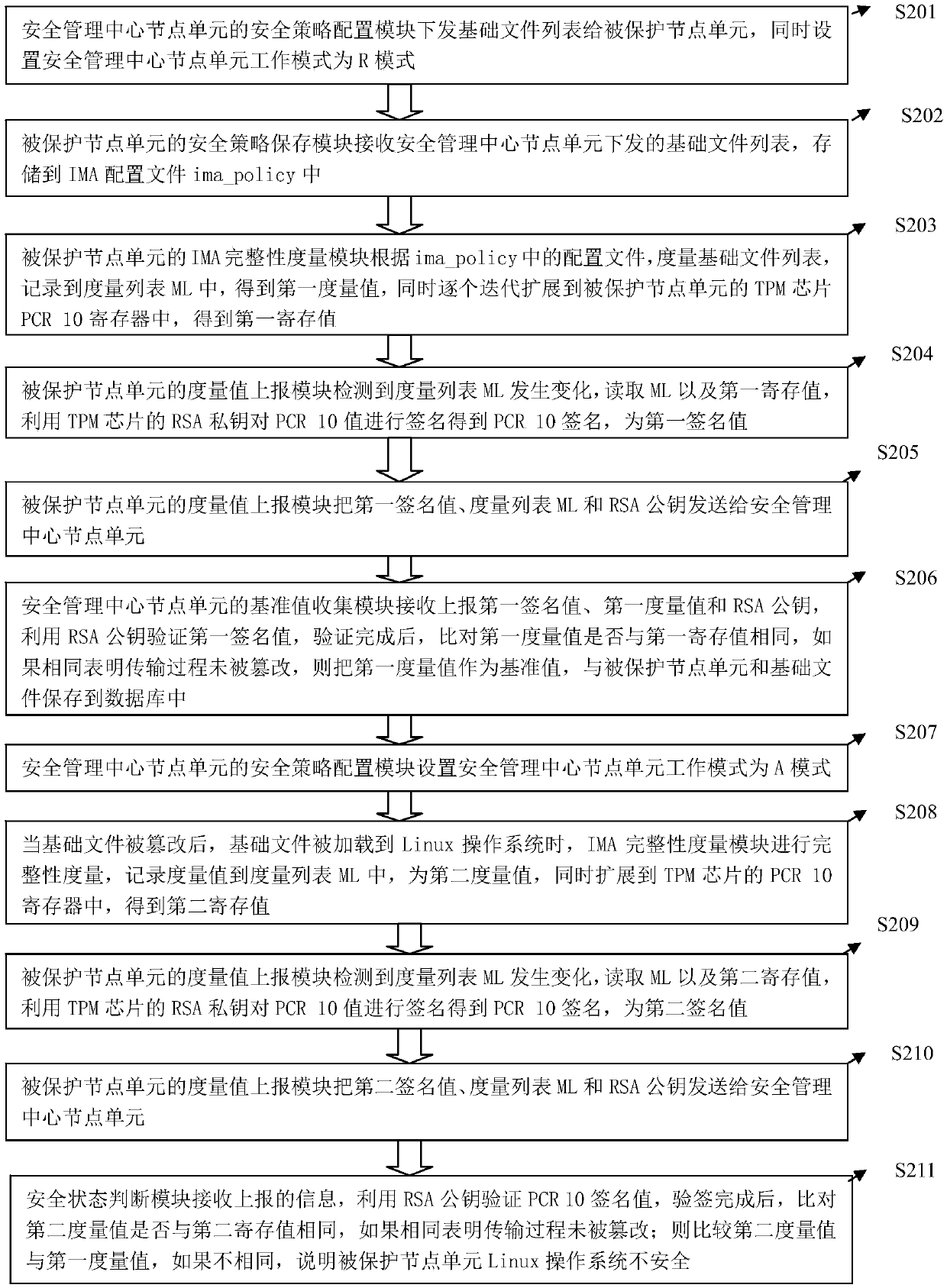
[0048] The security policy configuration module is responsible for security configuration and delivery, and is used to deliver basic files to the protected node node unit. At the same time, set the working mode of the safety management center node unit; the working mode of the safety management center node unit is divided into two type...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com