Cascading management system and method for secure network
A security network and management method technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as poor applicability, cumbersome deployment, and complicated management, improve security and compliance, and avoid network risks. , the effect of convenient and safe state
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
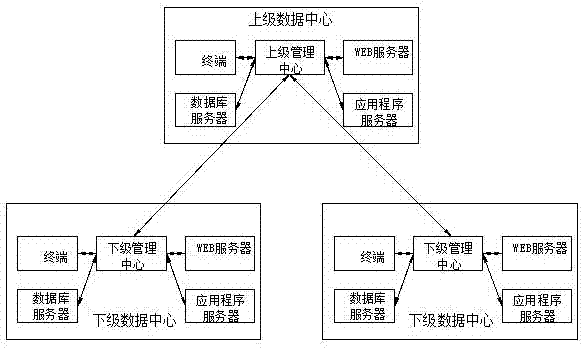
[0024] The cascading management system of the security network described in this embodiment is based on the cascading management framework, as shown in the attached figure 1 As shown, the cascaded management structure includes a superior data center and several subordinate data centers. The superior management center and terminals are set in the superior data center, and the subordinate management centers and terminals are set in the subordinate data centers. The cascaded management system can be managed centrally, showing The upper-level management center and the lower-level management center can manage the terminals in their data centers respectively; cascade management is also possible, which means that the upper-level management center can manage the lower-level data centers;
[0025] The upper-level management center can formulate mandatory policies or recommended policies to the lower-level management center according to the needs, and cascade and issue security policies;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com