Computer operating system safety protecting method
An operating system and security protection technology, applied in computing, instrumentation, electrical and digital data processing, etc., can solve problems such as no secure operating system and no foundation for network security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
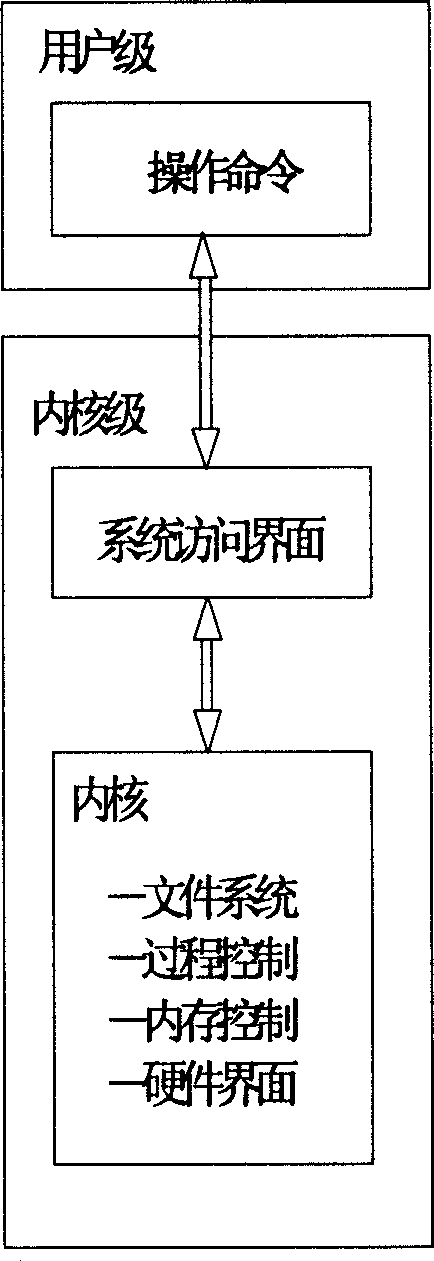
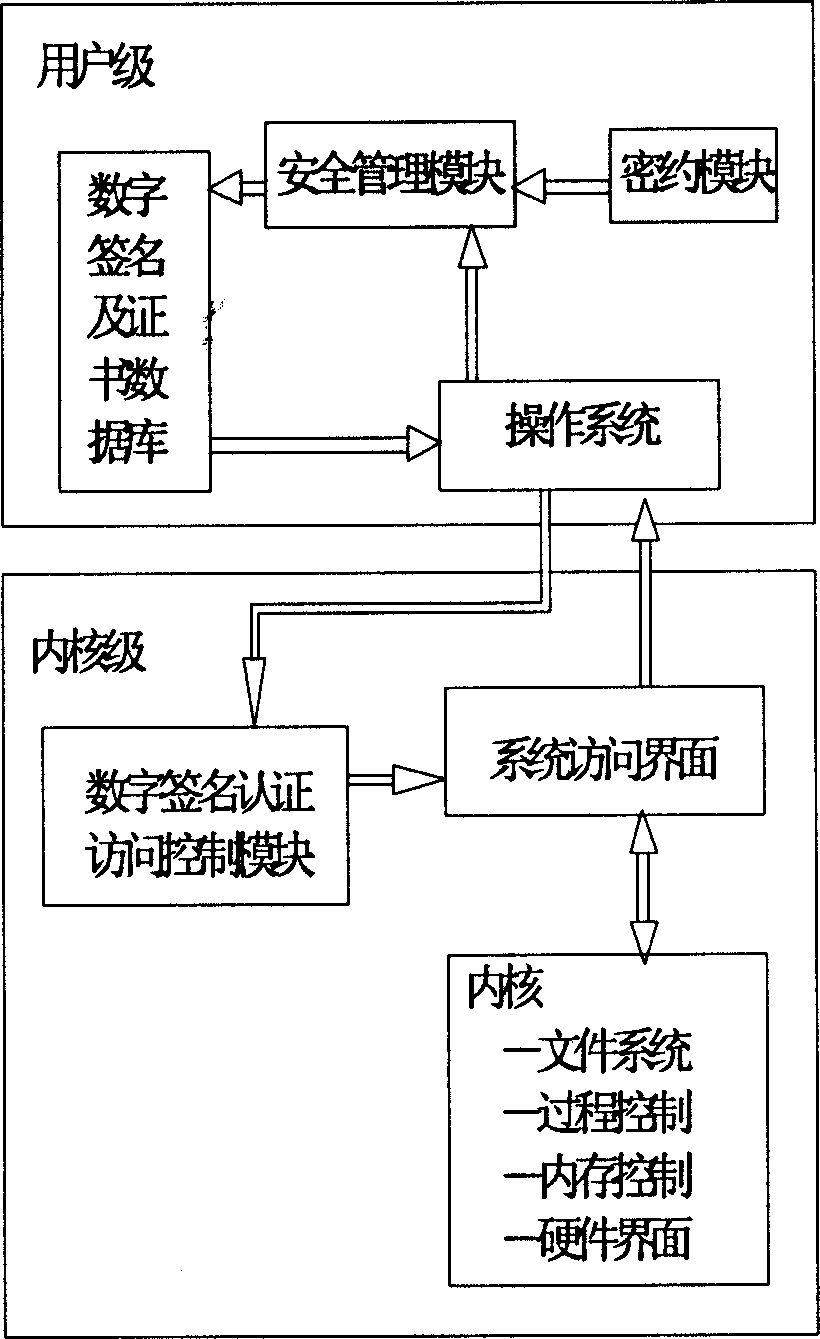
[0013] as attached figure 2 As shown, the operating system security protection method is implemented in the following ways:
[0014] The operating system security protection steps are as follows:
[0015] (1) Set up a digital signature and certificate database, a security management module and a confidential contract module in the user level of the Unix operating system. When the user requests access, the security management module and the confidential contract module are firstly authenticated, and the application program enters after passing the certification. Operating system kernel, access to resources, use of hardware devices, and communication between processes;
[0016] (2) A digital signature authentication access module is set at the kernel level of the Unix operating system to save relevant system call instructions in the system call interface, and the digital signature authentication access module directs the security-related system call instructions to the operati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com