Auditing access to data based on resource properties
A resource and data technology, applied in the field of audit strategy, can solve problems such as flooding system logs and reducing overall system performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
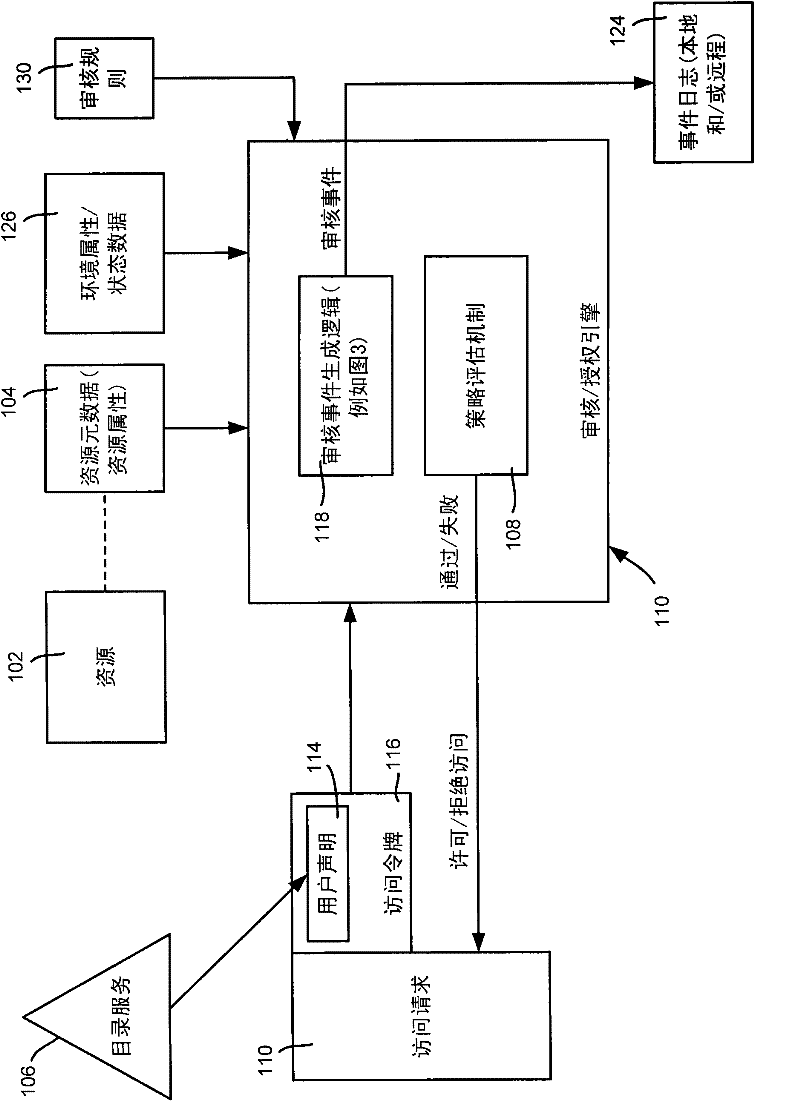
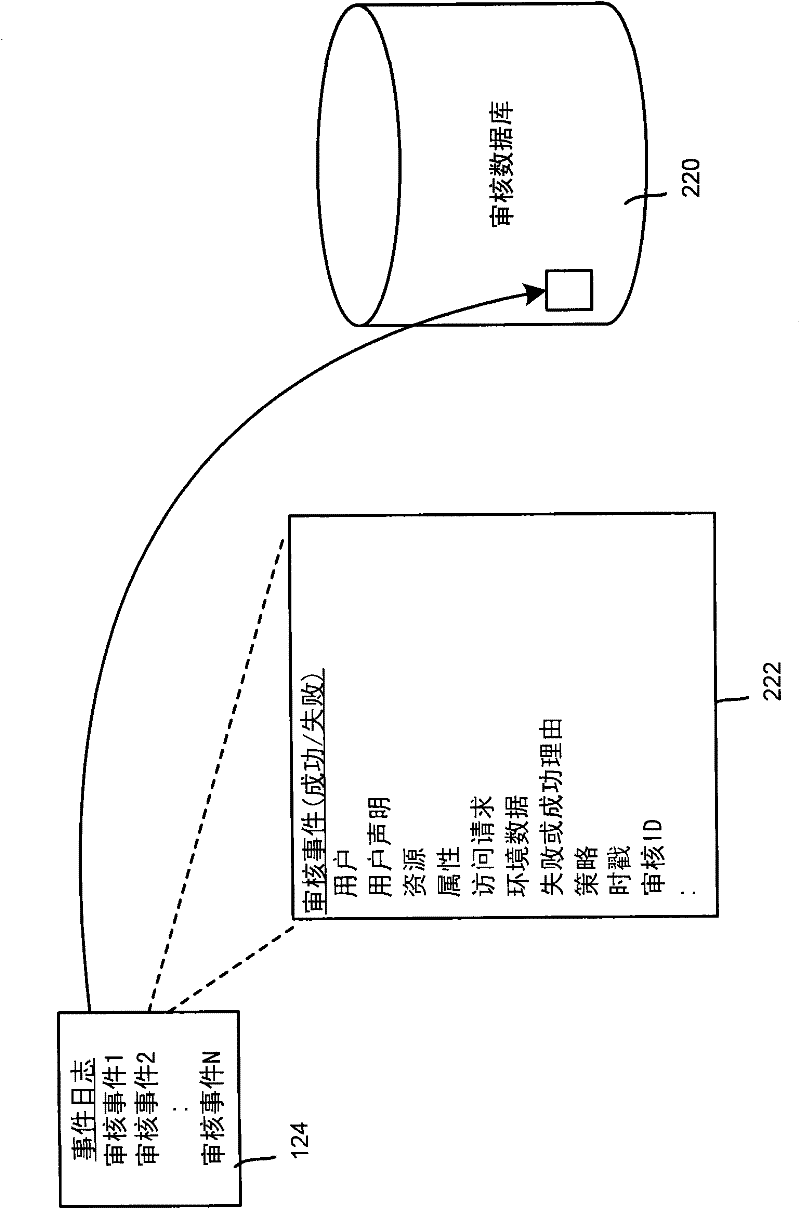
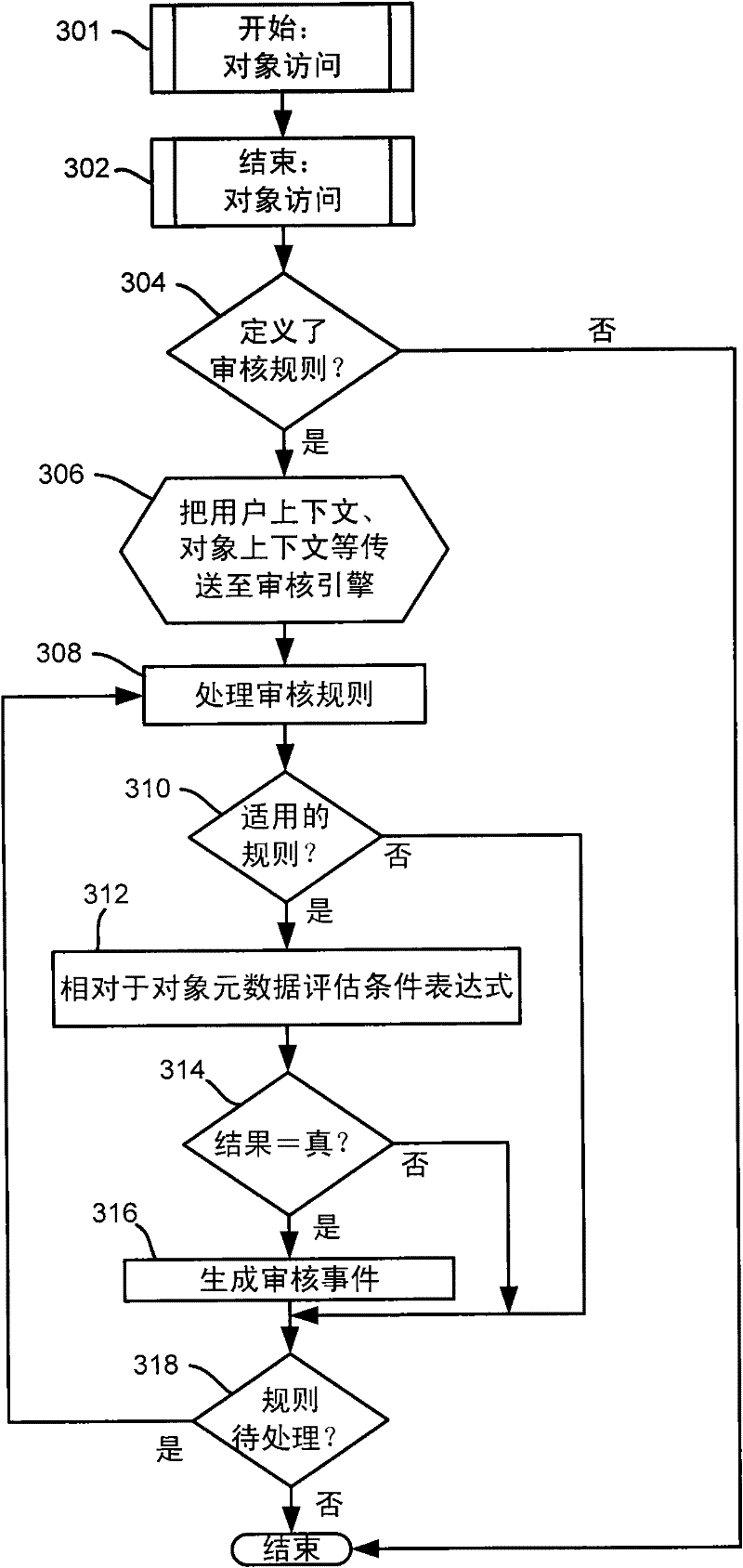
[0015] Aspects of the techniques described herein generally configure per-object audit policies for object-based metadata whereby audit triggers are affected by changes to object metadata. Also described allows the definition of audit rules using conditional expressions involving object (resource) attributes, such as sensitivity, creator, project, etc. of a file. When processing a rule, conditional expressions are evaluated against the properties of the object (and possibly based on environmental properties or other state data such as where the access request originates from). An audit event is fired if the expression evaluates to true; object access can also be granted or denied. This allows objects to be audited based on their characteristics independent of their physical location in the system.
[0016] It should be understood that any examples herein are non-limiting. In fact, for purposes of illustration, this article generally describes access to objects / resources in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com