Patents
Literature
3919results about "Microprogram loading" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
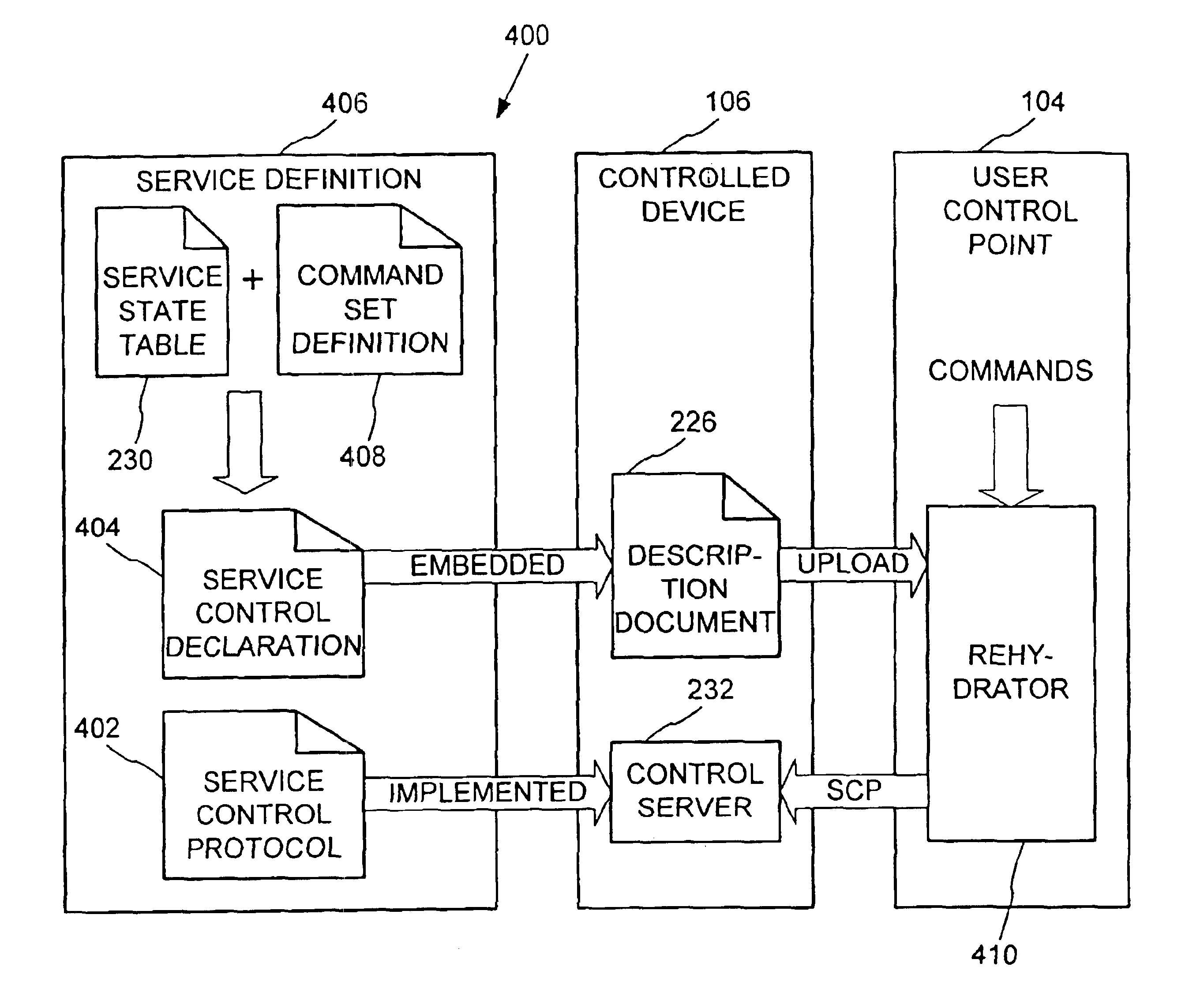
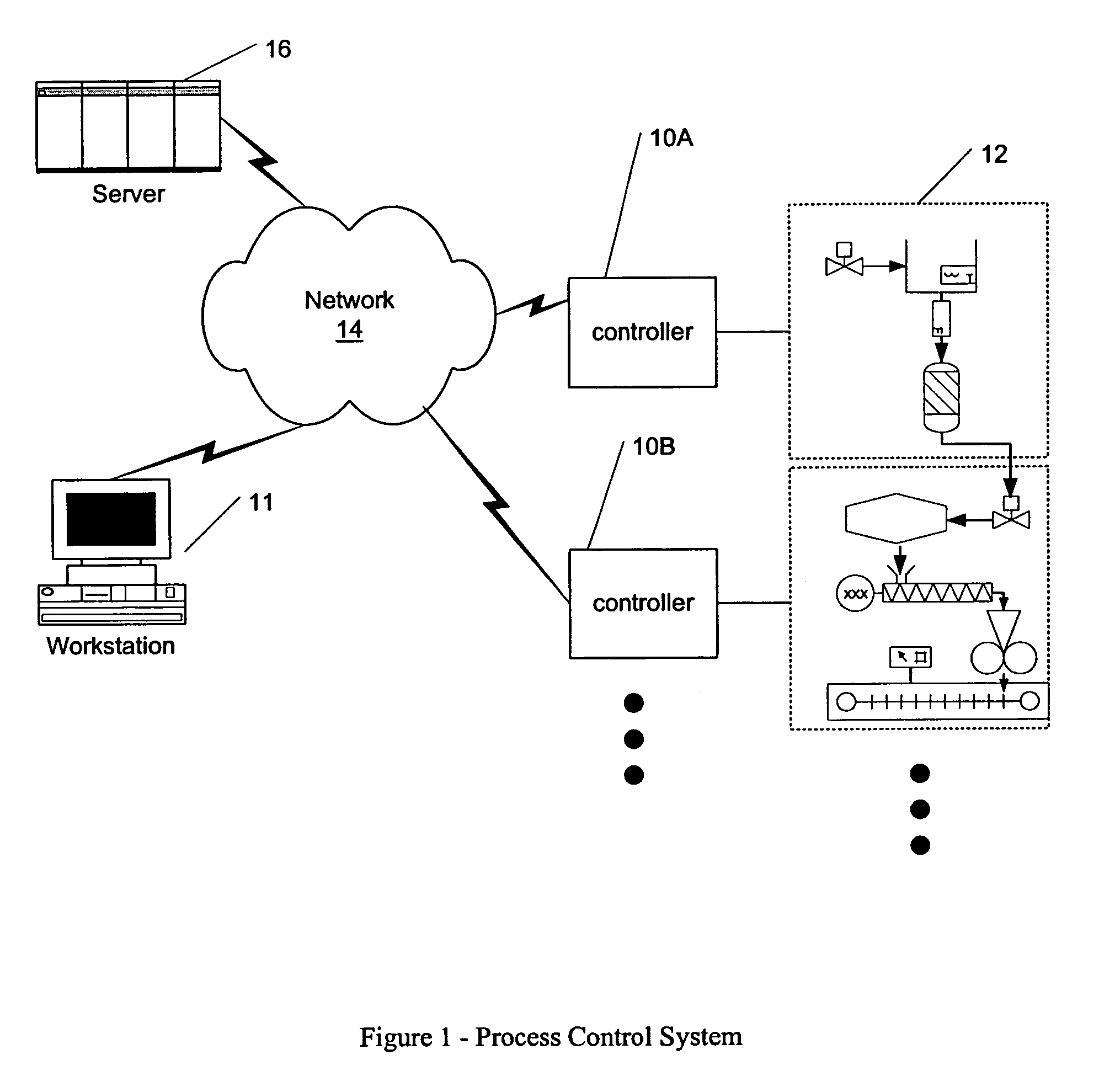
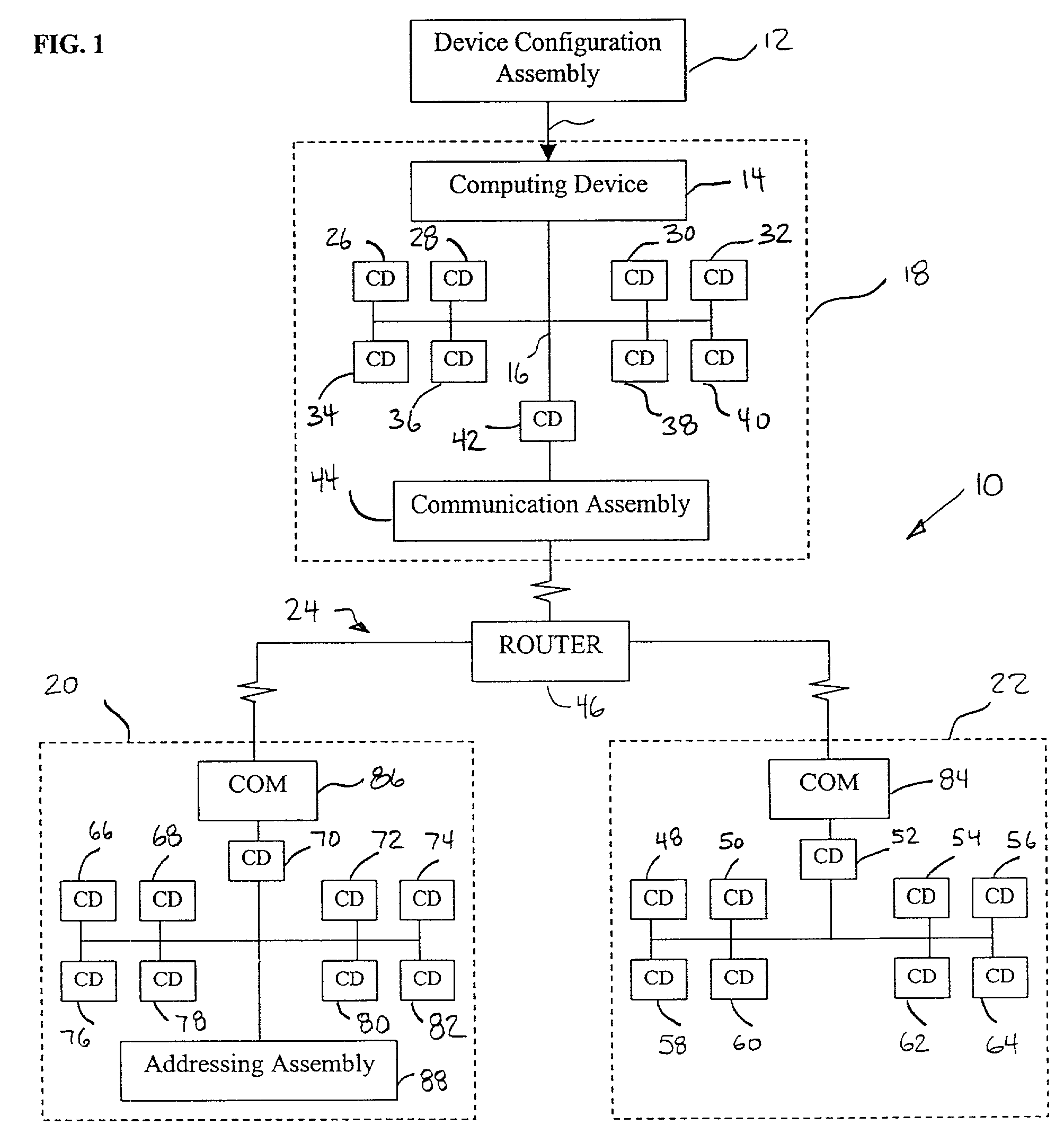
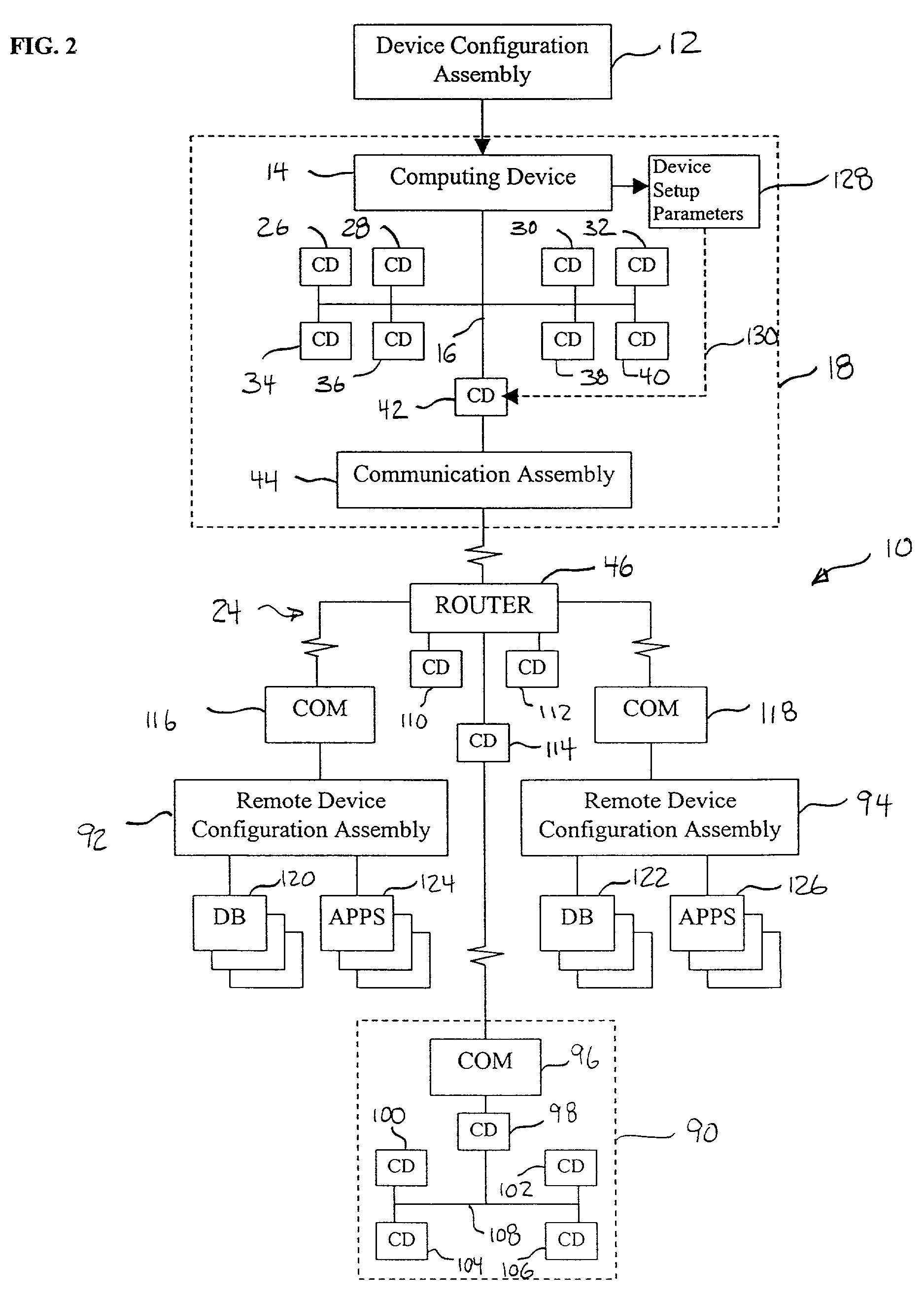
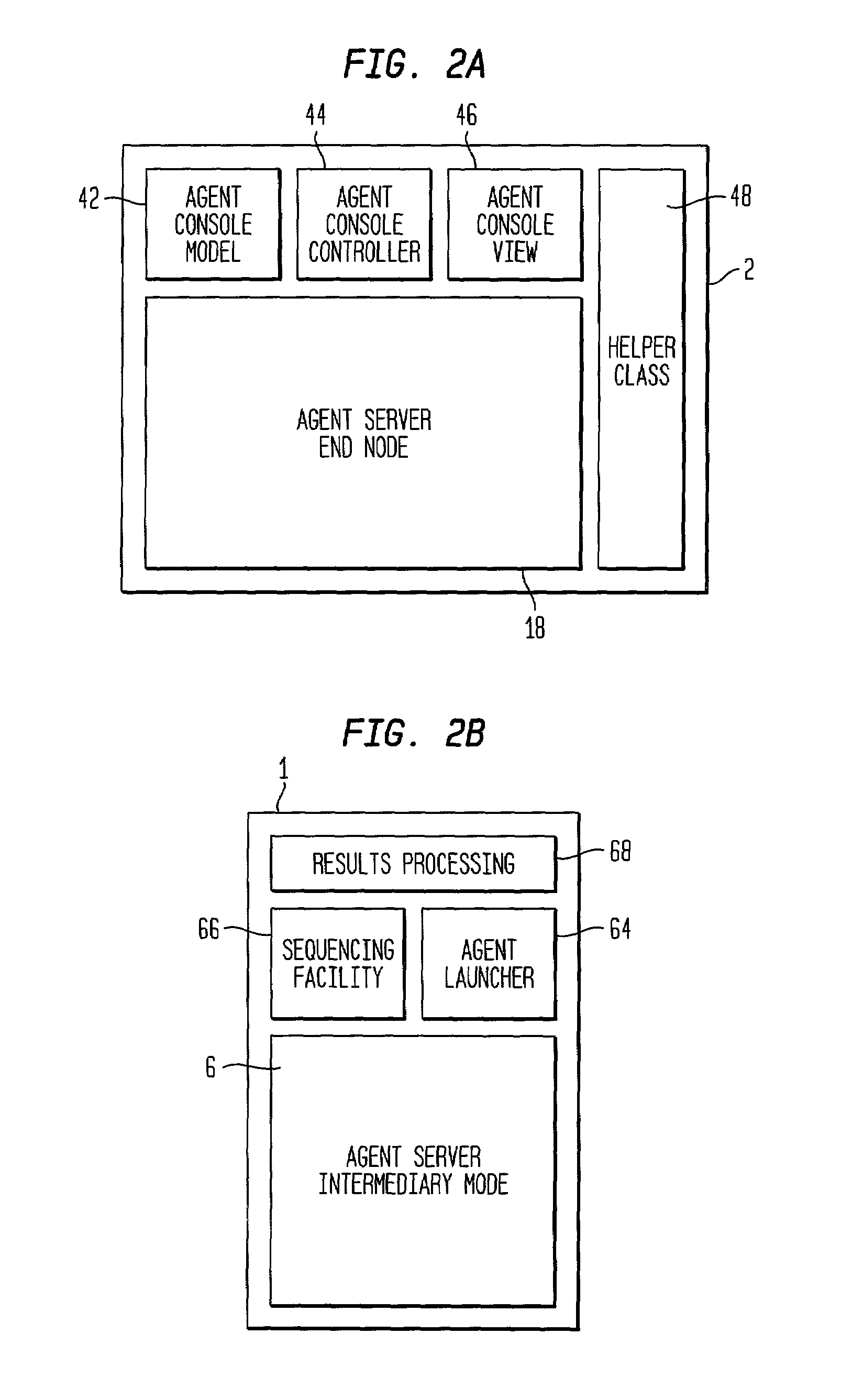
Dynamic self-configuration for ad hoc peer networking using mark-up language formated description messages
InactiveUS6892230B1CostConnectivity solutionDigital computer detailsNetworks interconnectionAuto-configurationHuman language
A device control model provides an integrated set of addressing, naming, discovery and description processes that enables automatic, dynamic and ad-hoc self-setup by devices to interoperate with other devices on a network. This permits a computing device when introduced into a network to automatically configure so as to connect and interact with other computing devices available on the network, without a user installation experience and without downloading driver software or persisting a configuration setup for connecting and interacting with such other computing devices. Upon completing interaction with such other devices, the computing device automatically releases the setup for such other devices so as to avoid persistent device configurations that might create a configuration maintenance and management burden.
Owner:ROVI TECH CORP
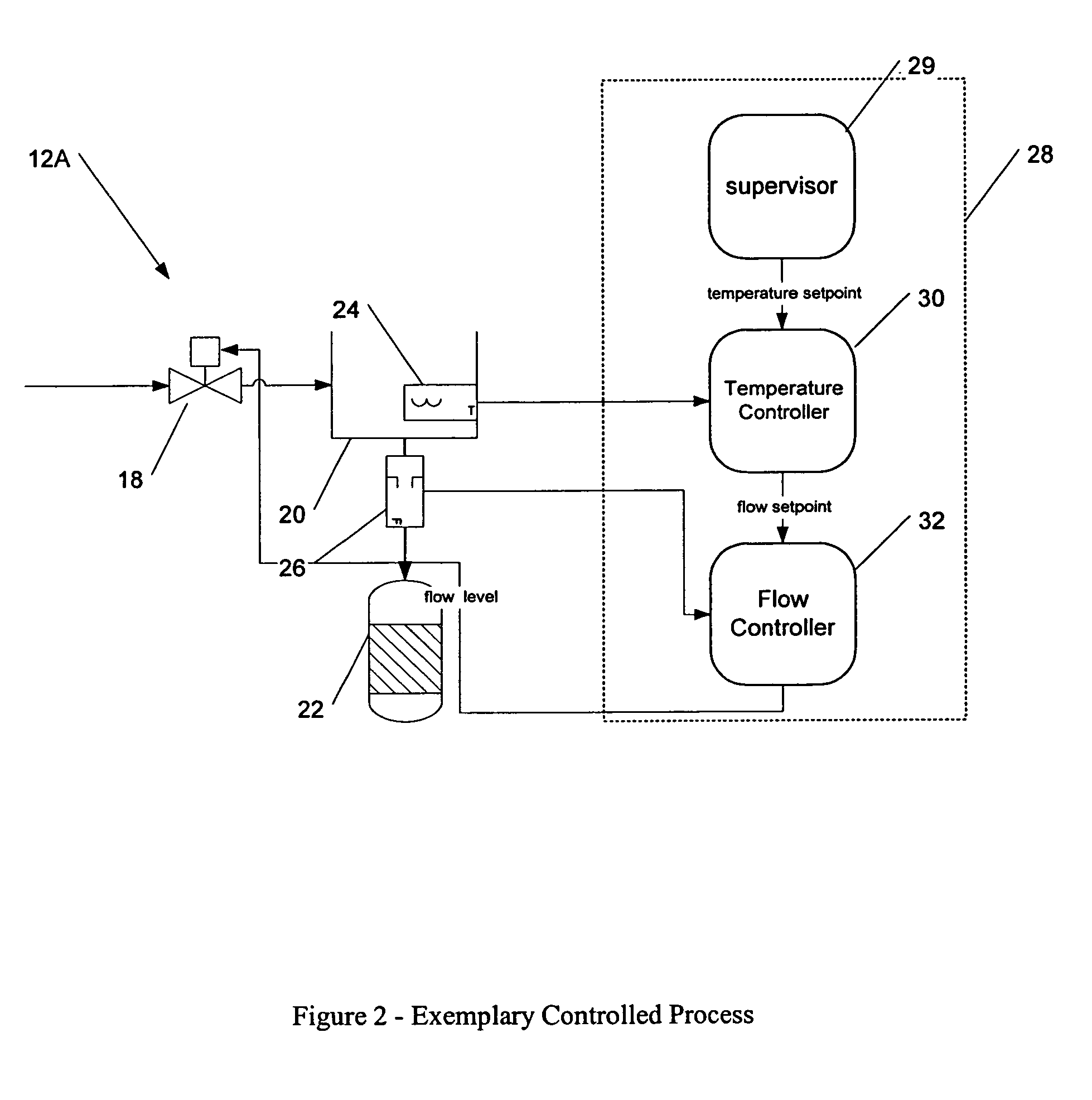
Methods and apparatus for control configuration with versioning, security, composite blocks, edit selection, object swapping, formulaic values and other aspects
InactiveUS7272815B1OptimizationOptimize system configurationData processing applicationsDigital data processing detailsGraphical user interfaceComposite object
Methods and apparatus for configuring process, environmental, industrial and other control systems generate and / or utilize models representing configurations of control systems and / or the systems controlled by them. Records of changes to the models or the configurations represented by them are maintained, thereby, for example, providing bases for determining current states, prior states and histories of changes. Objects in the model have characteristics, such as an object type characteristic and an area characteristic. Users can have corresponding permissions. A security mechanism apparatus controls access by users to the objects. Composite objects are defined by definition objects and are displayed in encapsulated or expanded formats. Objects can include an edit control type identifier that determines how they are presented for editing. Functionality responds to user commands by transferring characteristics of a first object depicted by the graphical user interface to a second object. Configuration-time formulas contained objects are evaluated to constants prior to downloading to the control system.
Owner:SCHNEIDER ELECTRIC SYST USA INC
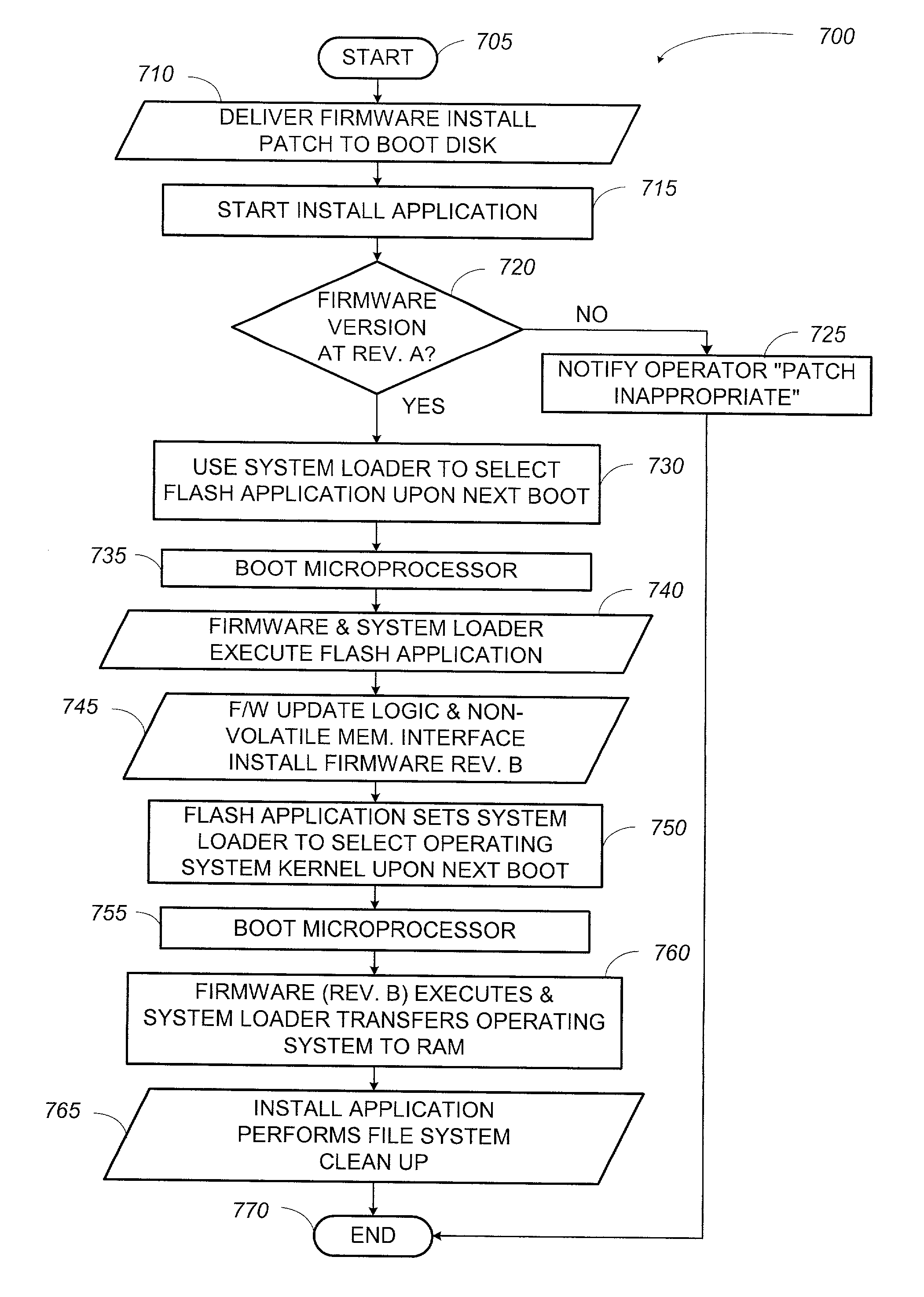
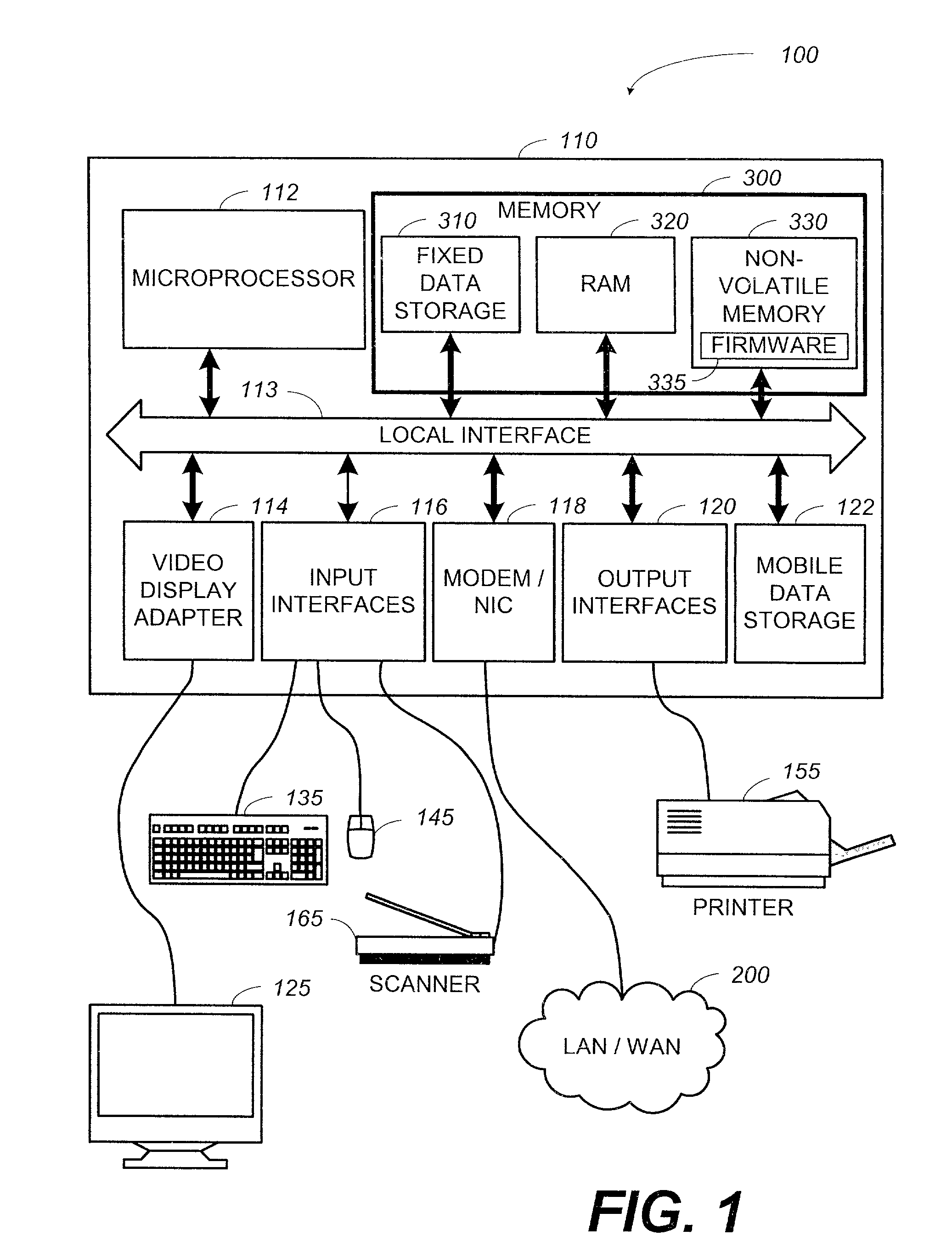
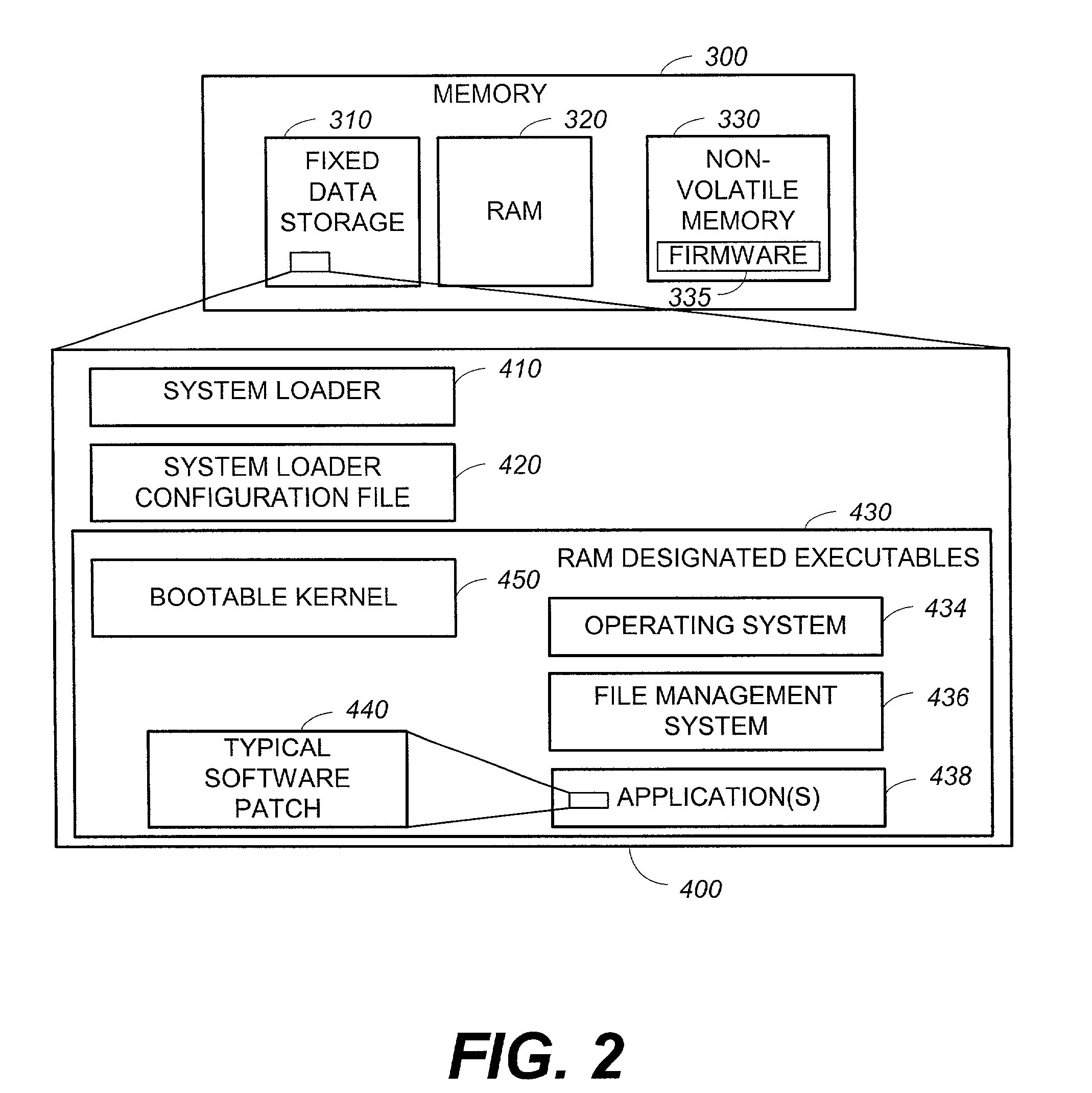
System and method for updating firmware
InactiveUS7055148B2Avoid manual interventionDigital computer detailsProgram loading/initiatingOperational systemFirmware version
A system and a method that uses a software application operable under a current firmware / operating system configuration to install a new firmware version without “compromising” the operating system are presented. The software application may configure a computer system to install a plurality of software fixes configured to enhance functionality under a new firmware / operating system environment after the firmware has been successfully upgraded. Such functionality enhancements may be associated with external peripherals, as well as, input / output circuit cards, processors, and the like. In addition, the software application may configure the computing device to “boot” under the new firmware / operating system environment upon subsequent system initializations. Furthermore, the software application permits the distribution of firmware upgrades via a network. The capability to install firmware remotely permits a system administrator to “push” the new firmware to a plurality of network coupled computing devices, thus avoiding manual intervention at each device.
Owner:HEWLETT PACKARD DEV CO LP
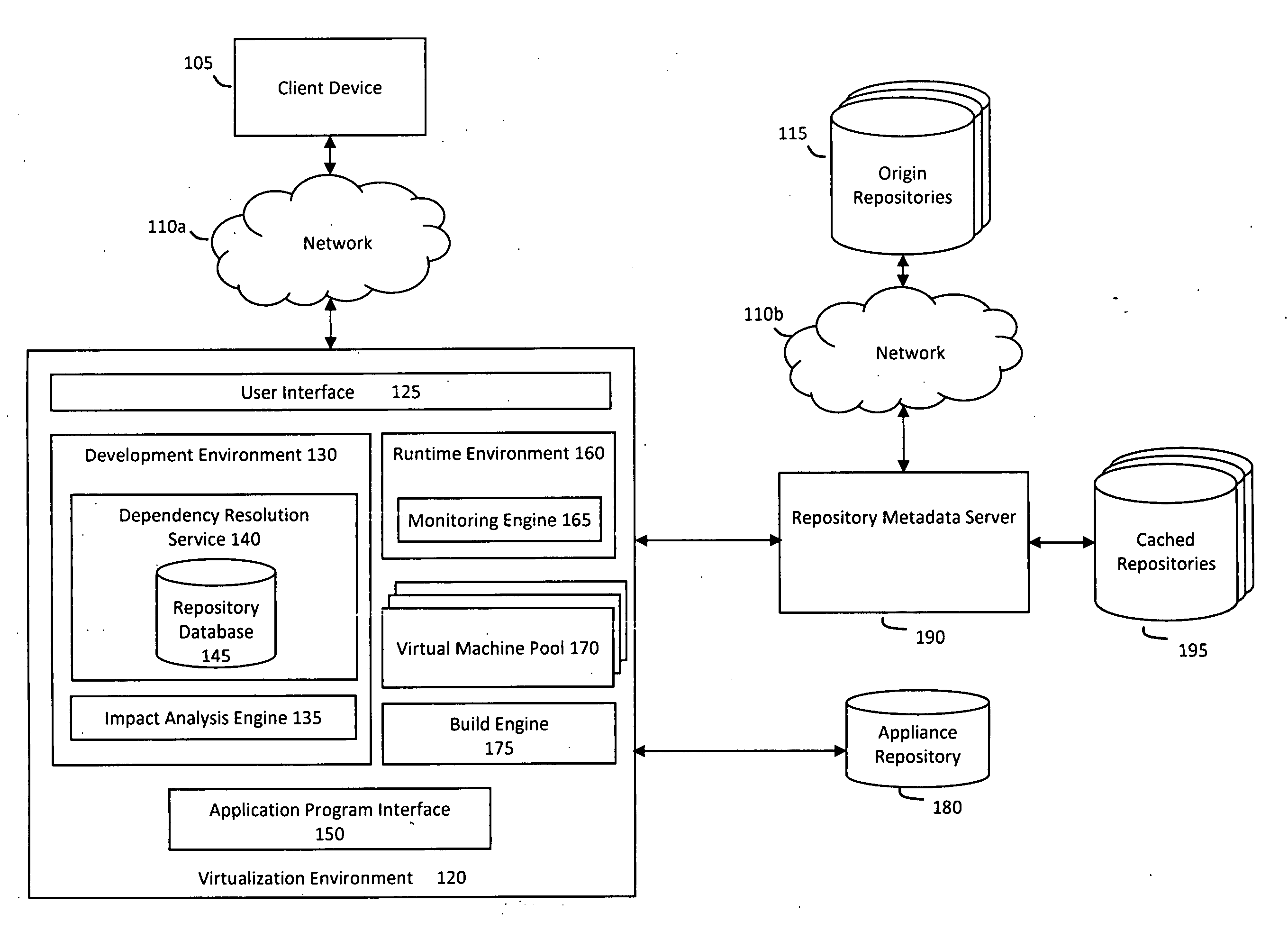
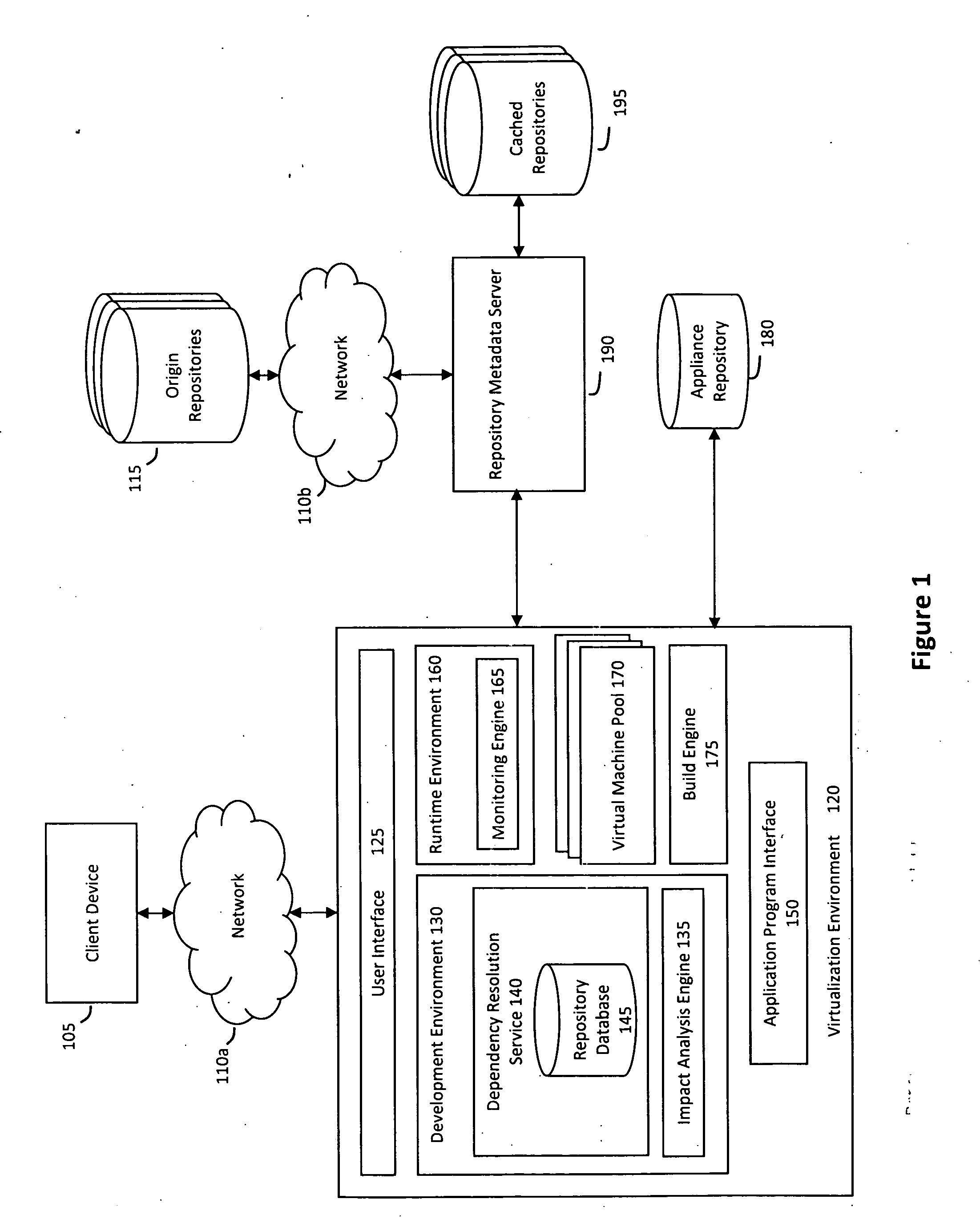
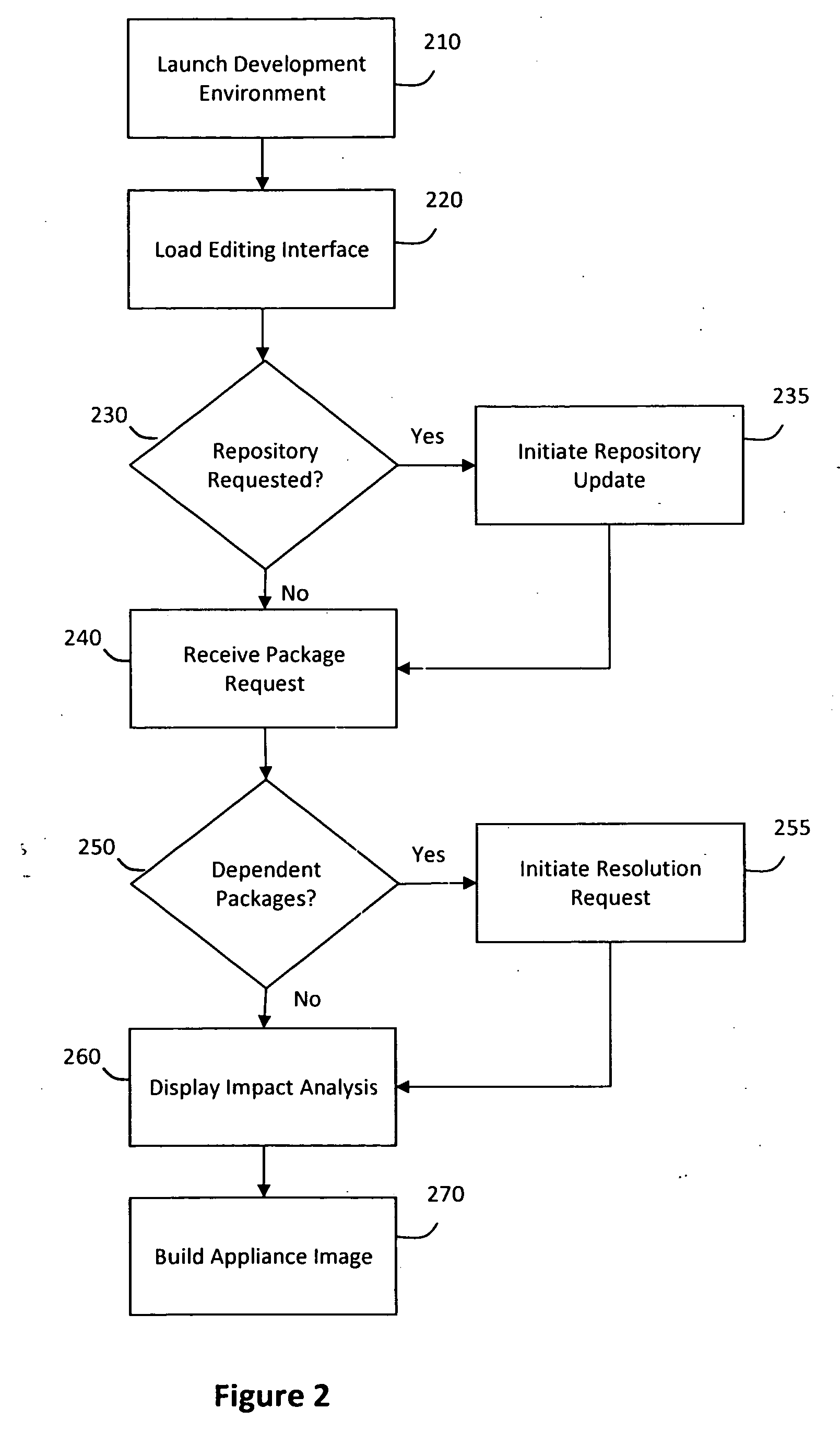
System and method for managing a virtual appliance lifecycle
InactiveUS20090300151A1Drawback can be addressedReduce the amount requiredError detection/correctionDigital computer detailsPersonalizationReal time analysis
A system and method for managing a virtual appliance lifecycle is provided. In particular, a hosted web service may provide a collaborative environment for and unified environment for developing, configuring, personalizing, building, testing, deploying, and otherwise managing a lifecycle for one or more virtual appliances, wherein the collaborative and unified environment may provide various features for-creating virtual appliances, monitoring upstream changes and modifications to the virtual appliances, and providing real-time analysis and feedback during various phases of the virtual appliance lifecycle, among other things.
Owner:SUSE LLC
Voltage negotiation in a single host multiple cards system
InactiveUS6279114B1Avoid writingMemory architecture accessing/allocationVolume/mass flow measurementComputer hardwareCommunications system
A low cost data storage and communication system. The low cost data storage and communication system has a host and at least one card connected to the host. A voltage negotiator located in the system for determining a common operating voltage range that is a common demonminator of all independent operating voltage ranges of all of the cards connected to the system. In addition, there is a novel feature of partitioning the memory storages of the card. This feature provides the host the ability to simultaneously erase any combination of sectors in a single erase group, or any combination of the entire erase groups. Another feature feature provided by this novel method of partitioning the memory storages is the ability to write protect any combination of memory groups in the card.
Owner:SANDISK TECH LLC
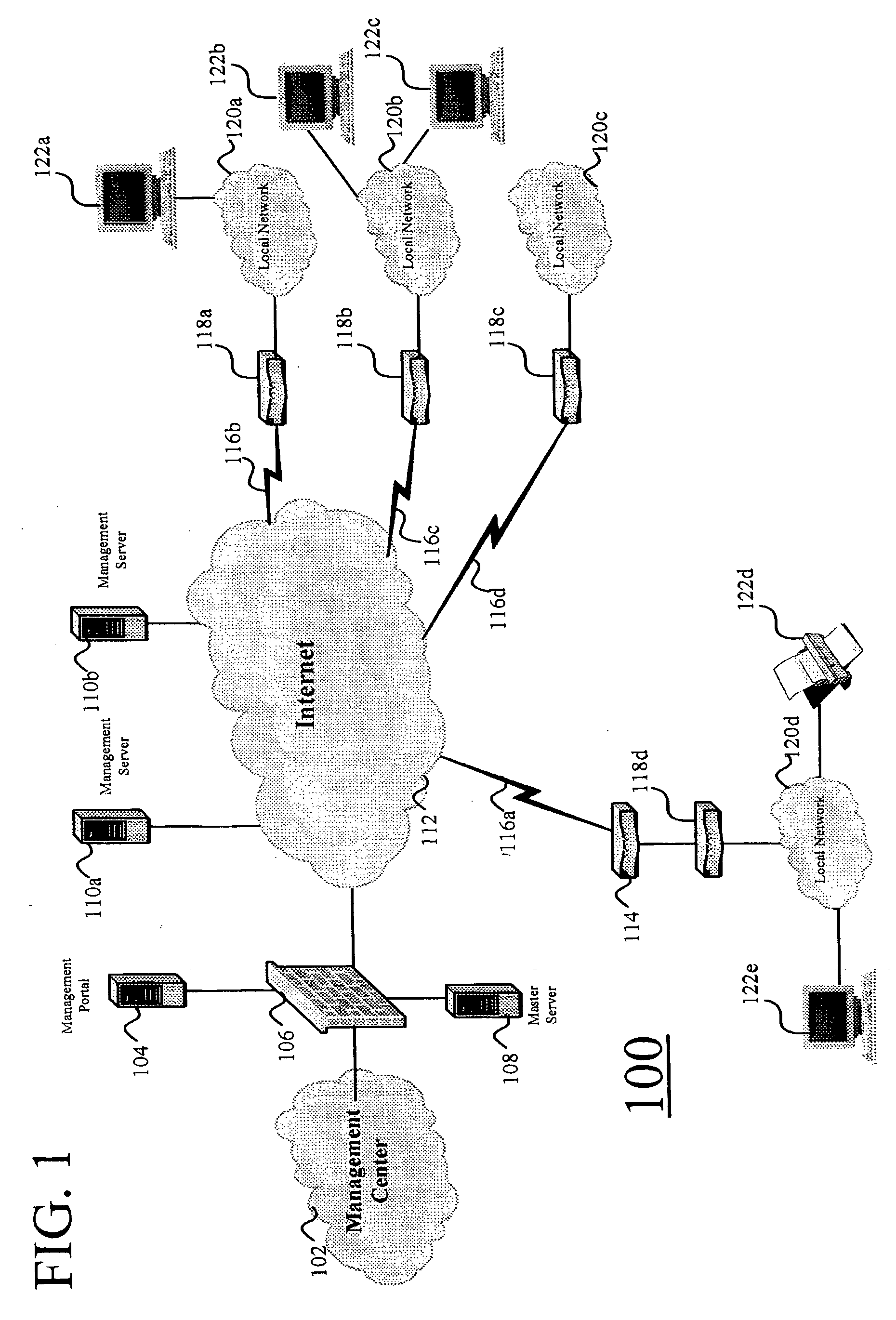
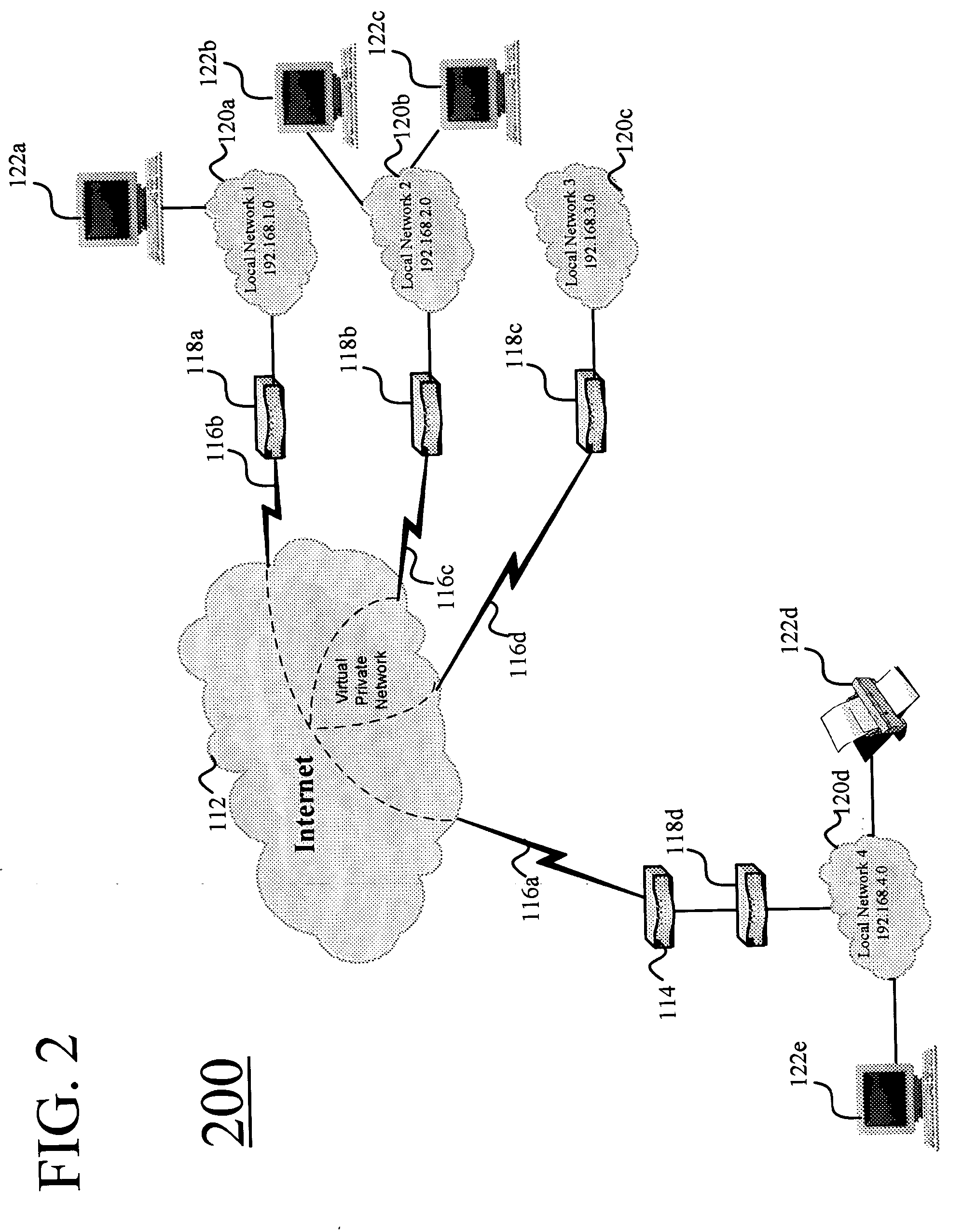
Systems and methods for automatically configuring and managing network devices and virtual private networks
ActiveUS20060236095A1Multiple digital computer combinationsSpecial data processing applicationsComputer hardwareGraphics
Systems and methods are disclosed for automatically configuring, managing, and maintaining a network device or VPN using a public network such as the Internet. Initial configuration of a network device or VPN occurs upon a user entering minimal information via a simple HTML page. After receipt of this minimal information, the present invention automatically configures the network device or VPN without user intervention. Thereafter, a user may modify the network device or VPN configuration via an easy-to-use and easy-to-understand graphical user interface. Parameters are presented such that a user simply checks and unchecks boxes, or clicks on radio buttons, to configure network device parameters. Upon completion of the selection, the user clicks on save, and the configuration is automatically modified. In addition, upon a significant change to any network device, the changed network device automatically initiates reconfiguration of the network device or VPN with zero input from a user.
Owner:ANXEBUSINESS
System and Method for Management and Installation of Operating System Images for Computers
InactiveUS20080046708A1Digital computer detailsProgram loading/initiatingOperational systemOperating system
Shown is a method and system for provisioning a target computer with an operating system, which calls for booting the target computer in a pre-operating system environment, collecting configuration information for the target computer, and transmitting the configuration information to a predetermined server. The approach shown also provides for searching a database in the server for a pre-existing operating system image corresponding to the configuration information from the target computer. If a corresponding operating system image is found, then the present approach involves transferring the pre-existing operating system image to the target computer and installing the pre-existing operating system image on the target computer.
Owner:MICRO FOCUS LLC
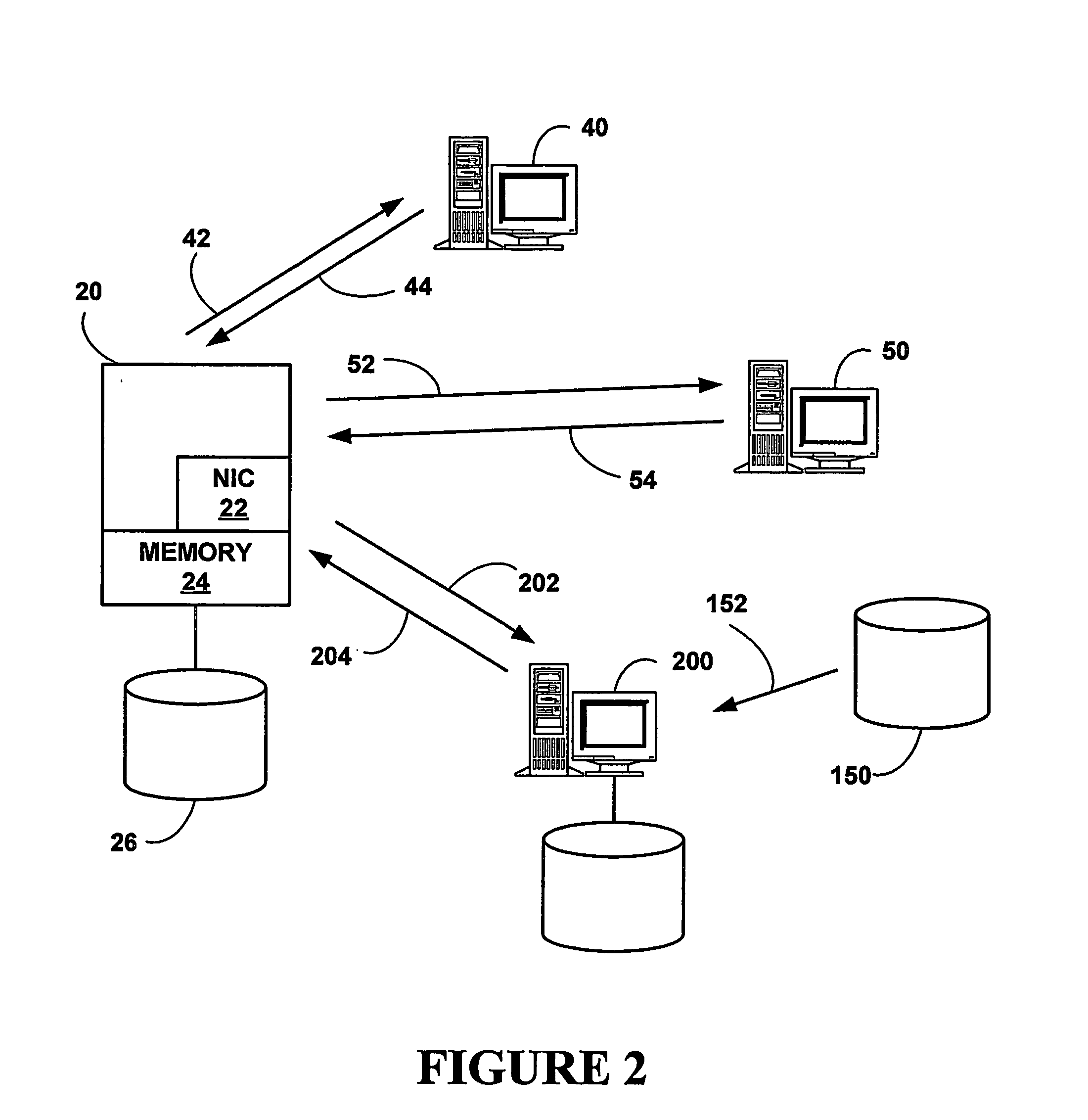
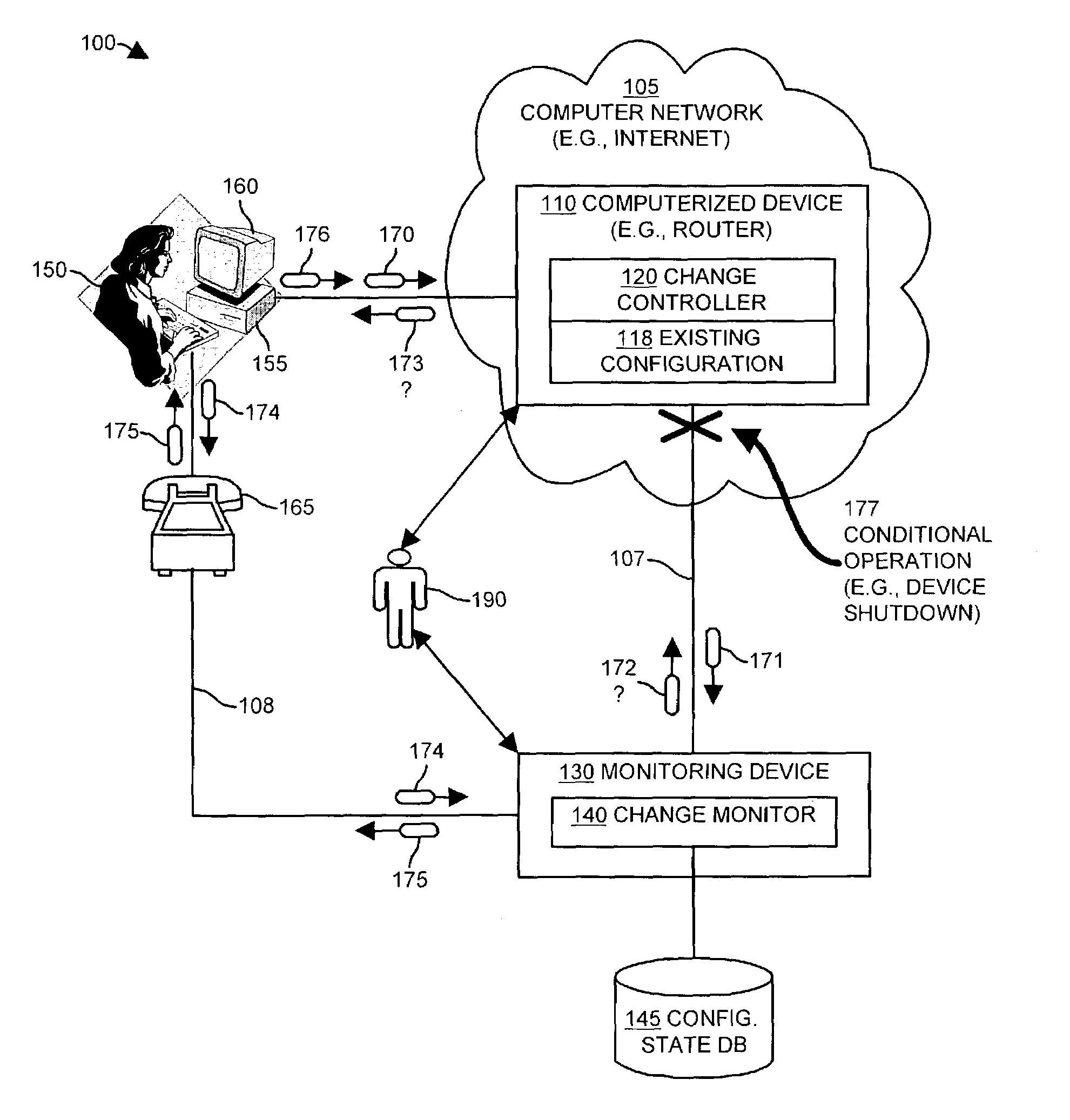
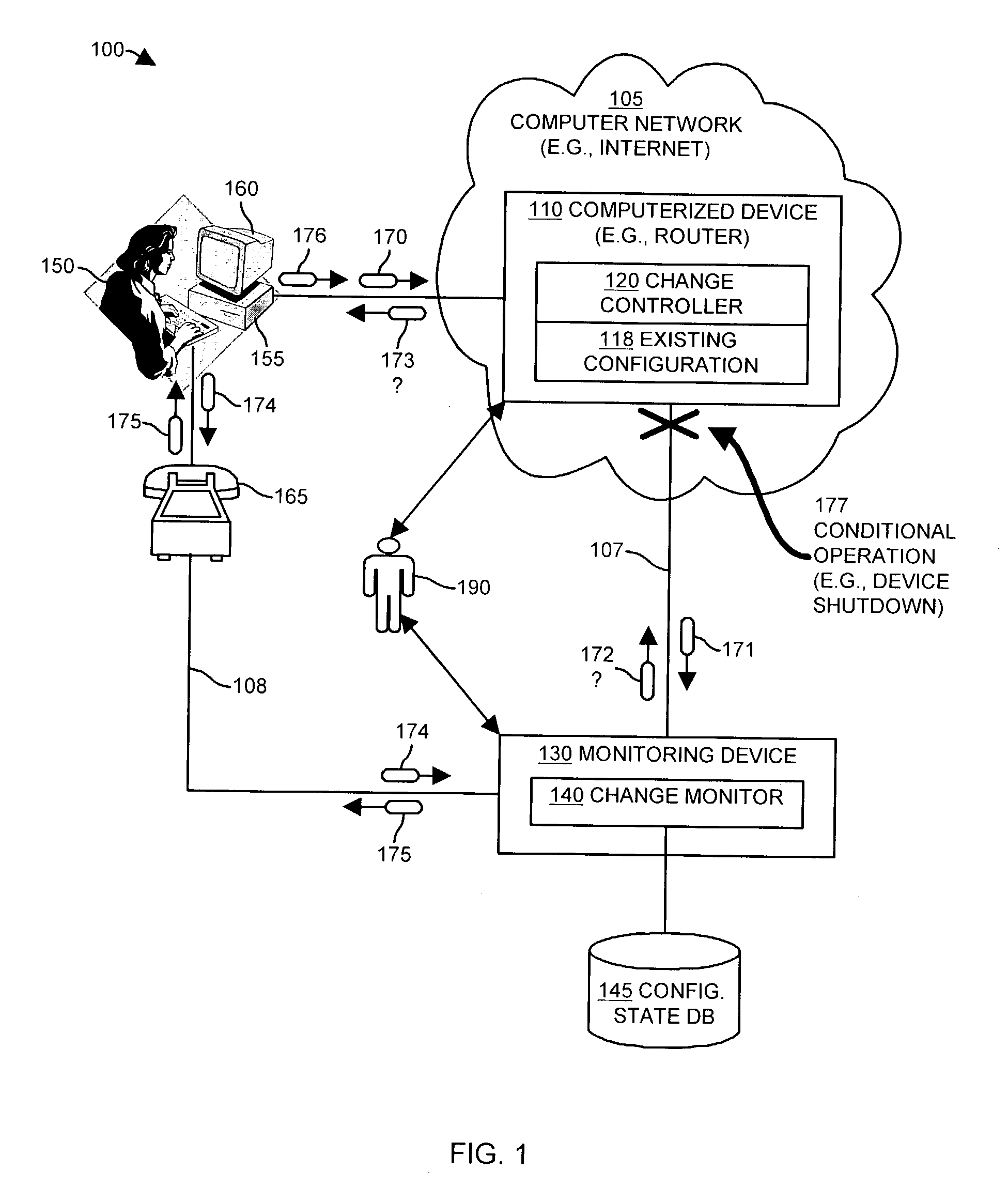
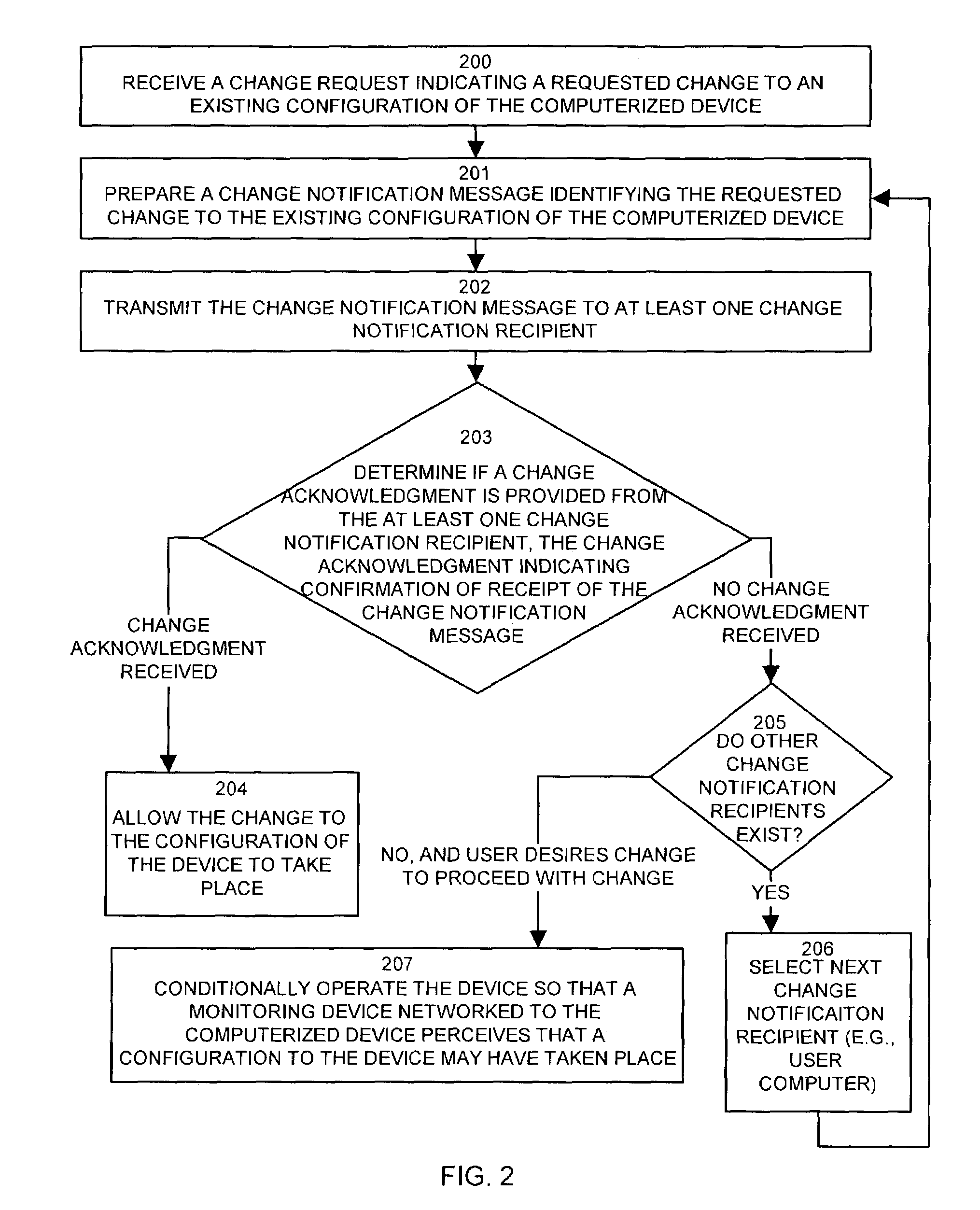
Methods and apparatus for auditing and tracking changes to an existing configuration of a computerized device
InactiveUS7024548B1Maliciously compromisedOvercome deficienciesMemory loss protectionError detection/correctionNotification ReceiverChange control
A change controller application, process and system tracks modification to a configuration of a computerized device by receiving a change request indicating a requested change to an existing configuration of the computerized device and preparing a change notification message identifying the requested change to the existing configuration of the computerized device. The change controller transmits the change notification message to at least one change notification recipient and determines if a change acknowledgement is provided in response. If a change acknowledgement is provided from a change notification recipient that indicates confirmation of receipt of the change notification message, the system allows the requested change to the configuration of the computerized device to take place. If the change acknowledgement is not provided from a change notification recipient, the system conditionally operates the computerized device so that a monitoring device networked to the computerized device perceives that a configuration change to the computerized device may have taken place.
Owner:CISCO TECH INC
Operating system boot from network location
InactiveUS20060242395A1Easy to manageEasy to storeDigital computer detailsMemory systemsOperational systemInit
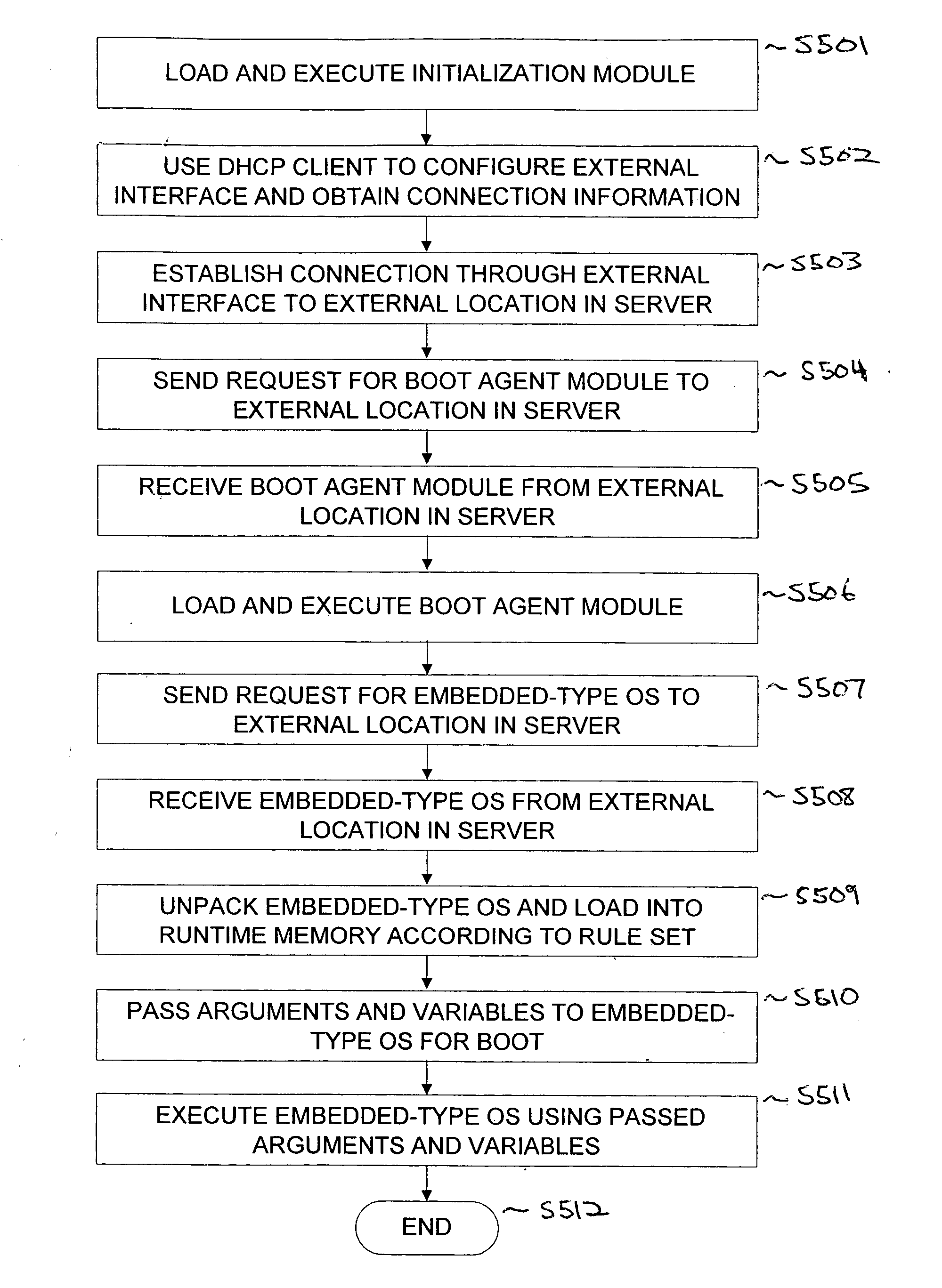
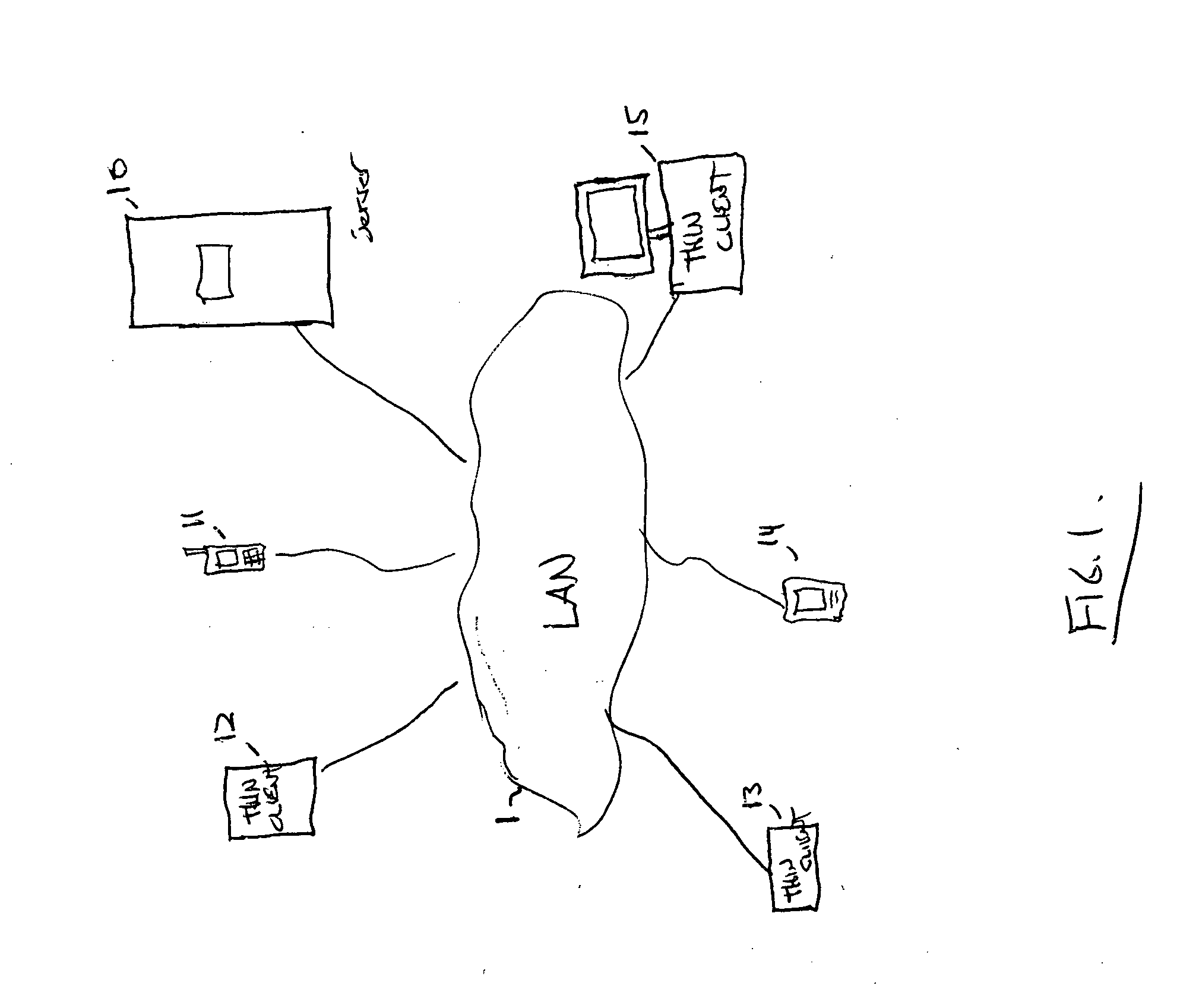
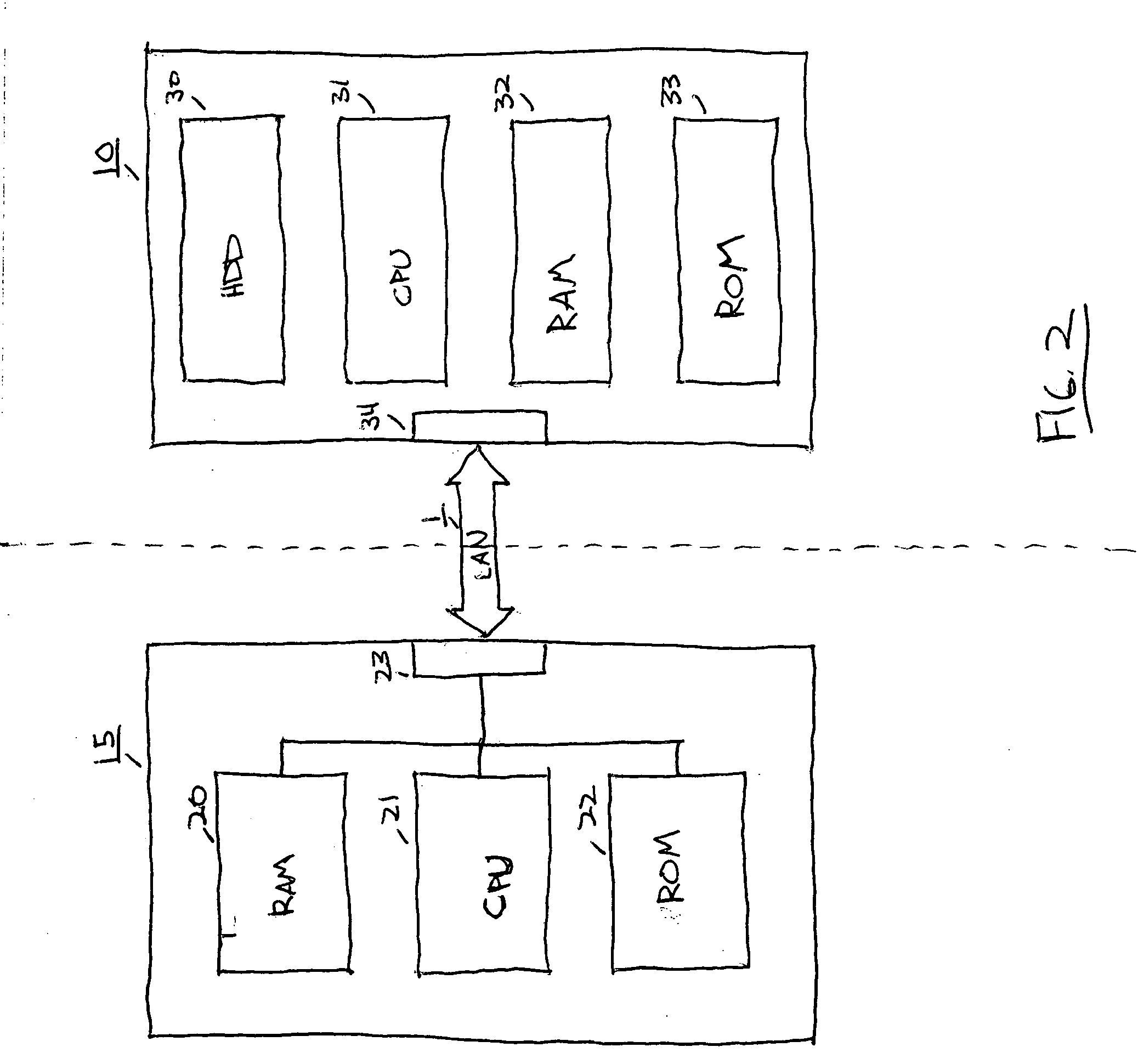
The present invention provides a system for booting an intelligent device with an embedded-type operating system obtained through an external interface disposed in the intelligent device, wherein the system includes an initialization module stored in a read-only memory provided in the intelligent device, the initialization module being executed in a processor disposed in the intelligent device and connecting to an external location through the external interface, and a server having a memory media which stores a boot agent module and an embedded-type operating system at the external location, the server sending the boot agent module to the intelligent device through the connection in response to a request from the initialization module, wherein the boot agent module is loaded into a runtime memory in the intelligent device and executed by the processor, the boot agent module then retrieving an embedded-type operating system image from the external location in the sever, whereupon the embedded-type operating system image is loaded into the runtime memory and executed by the processor.
Owner:WYSE TECH LLC
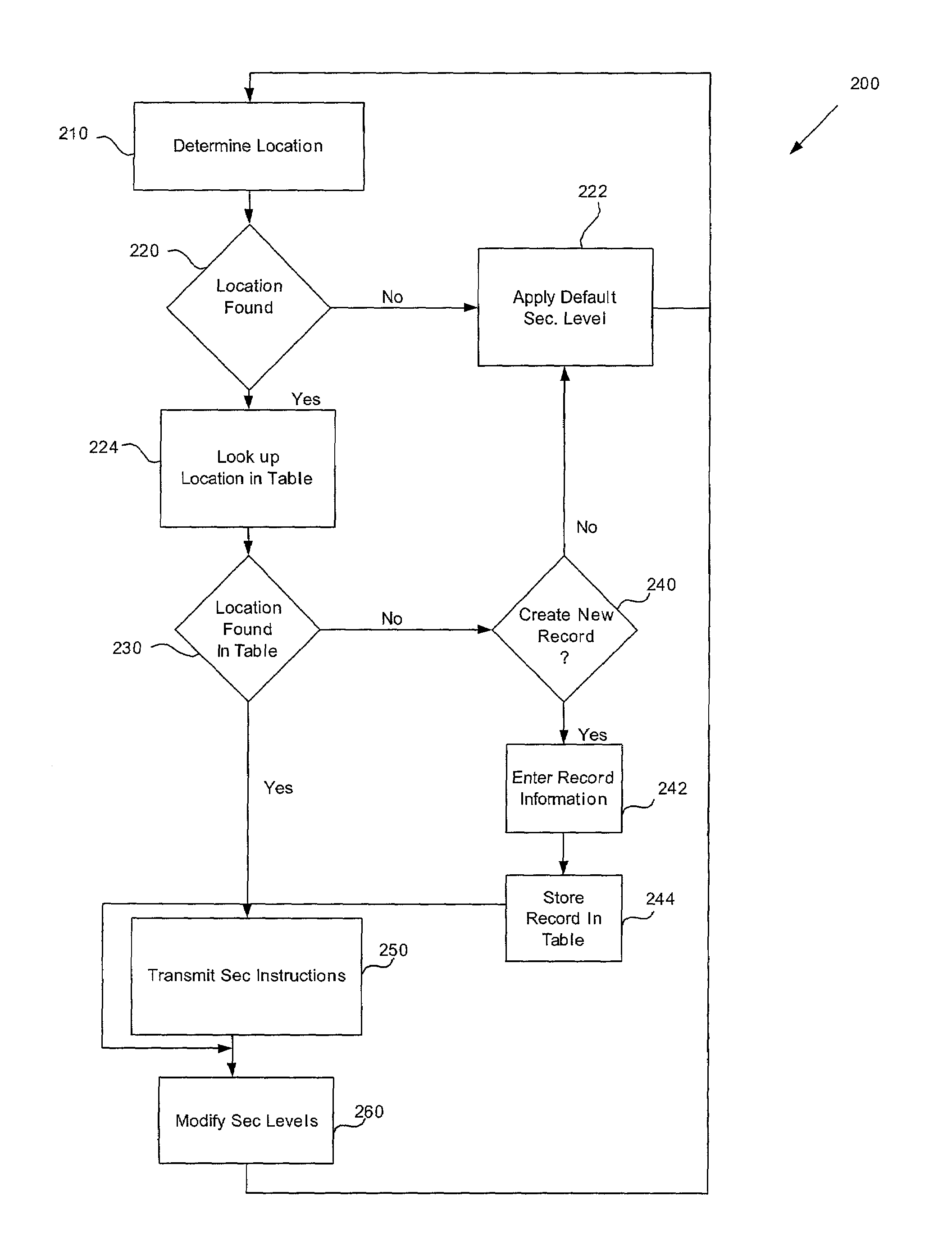
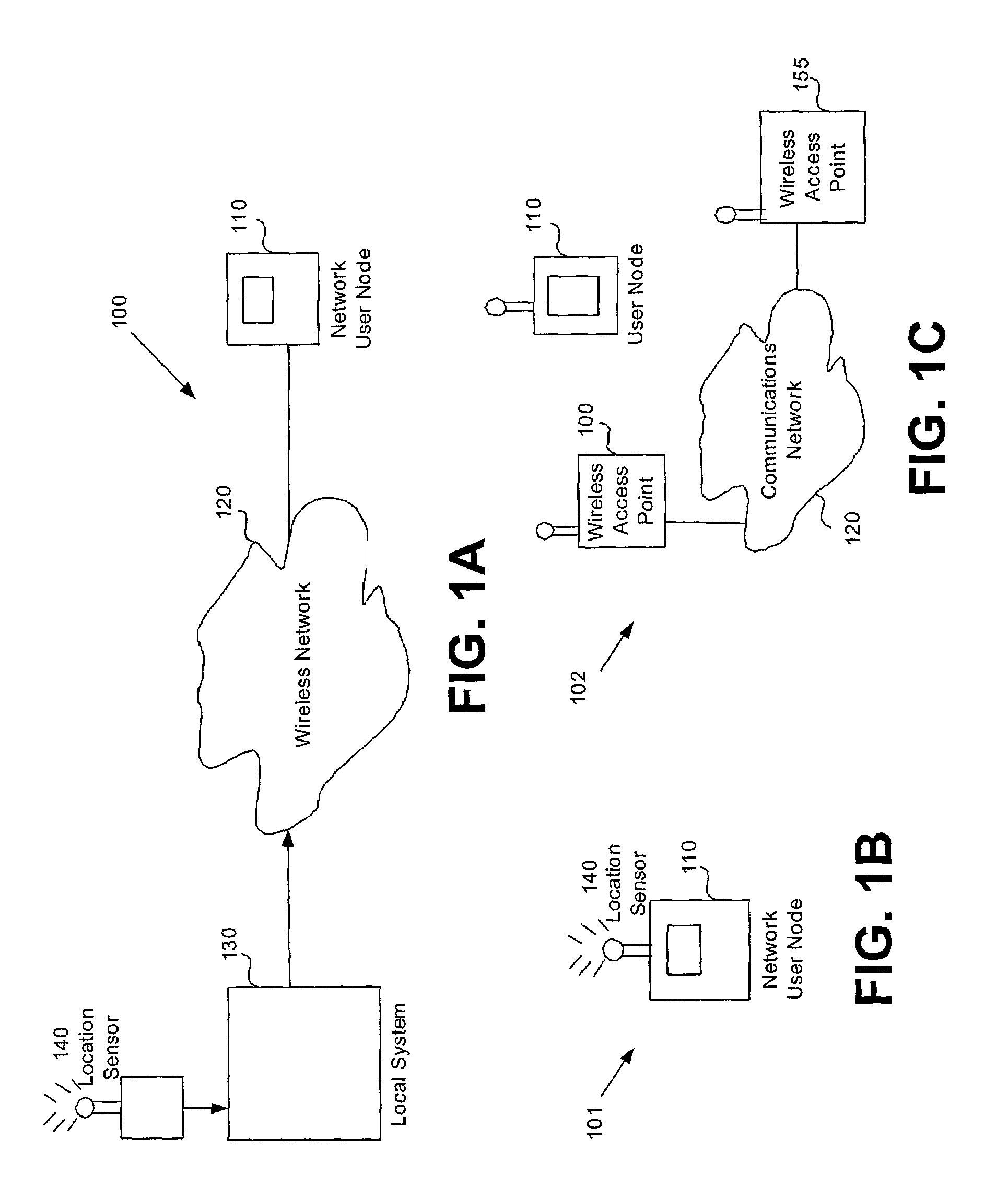
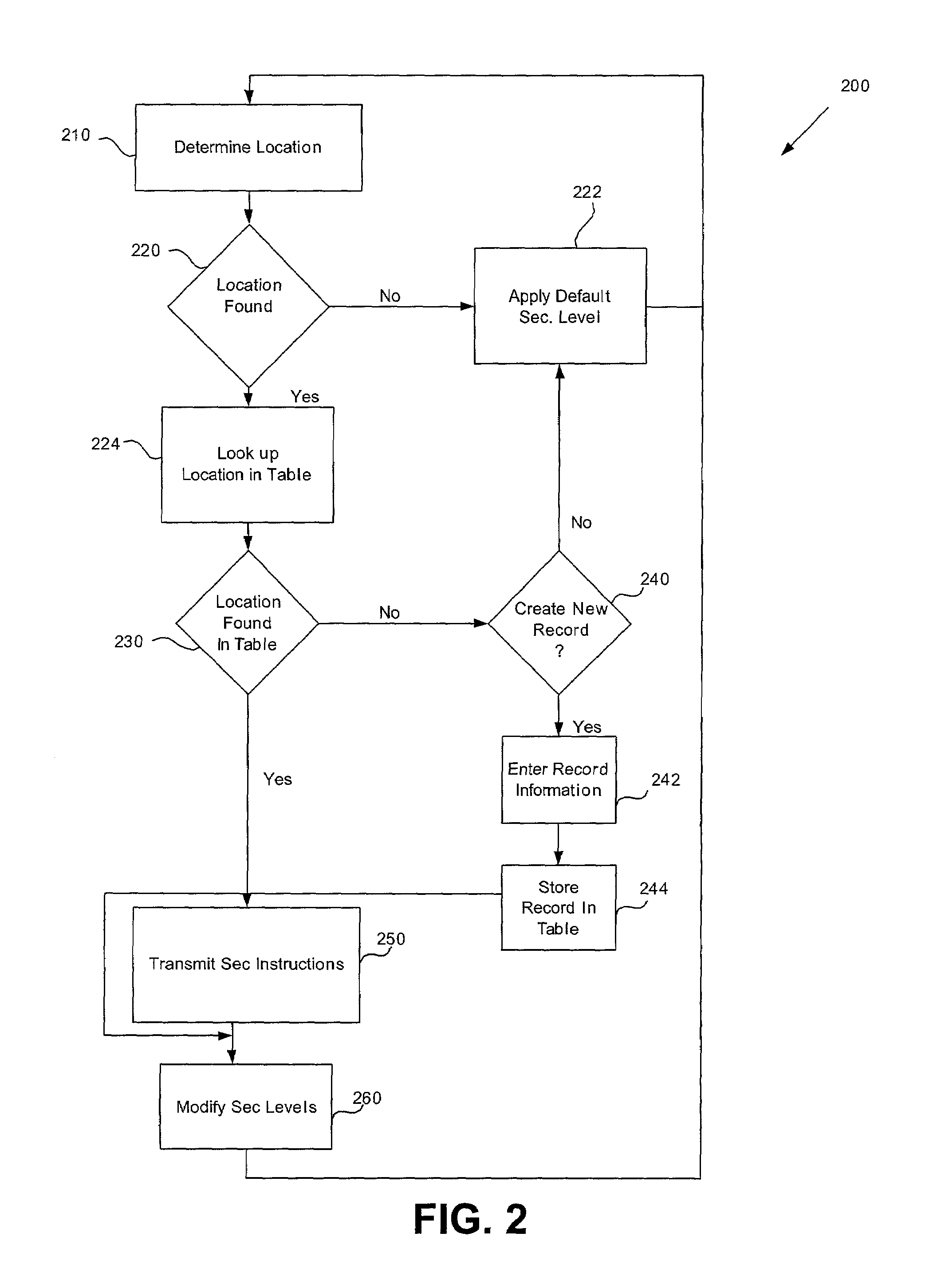
Location based security modification system and method
ActiveUS7591020B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSingle levelSecurity level
A method or system for providing a level of data security dependent on the location of the user of a wireless device is disclosed. One exemplary embodiment relates to a method of adjusting security for a network user node in communication with a network based upon the location of the node. The method is performed by determining the location of a network user node, selecting a single level of security from a group of more than two security levels based on the determined location, and modifying the security protection for the network user node based upon the selected level of security.
Owner:QUALCOMM INC
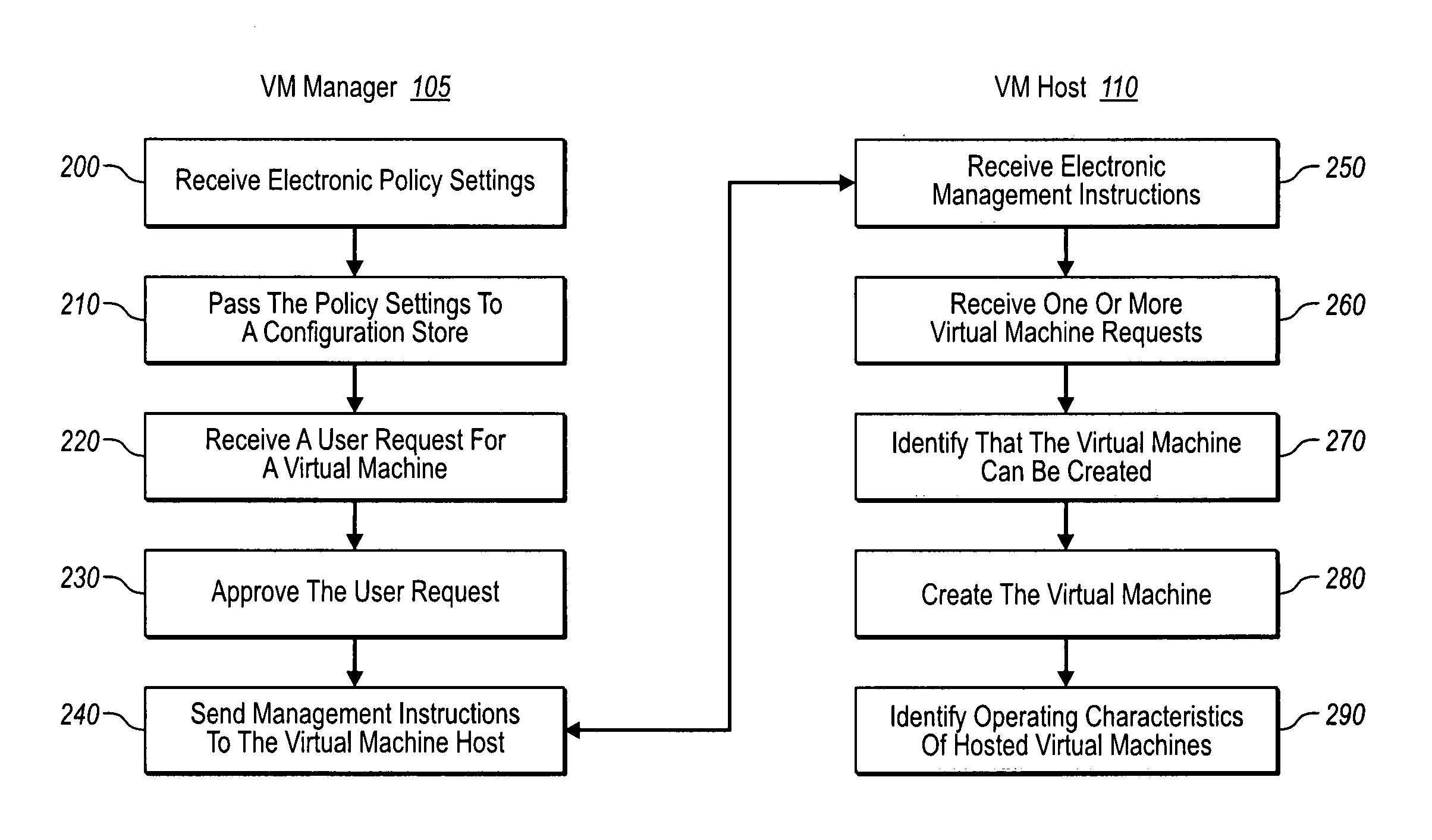
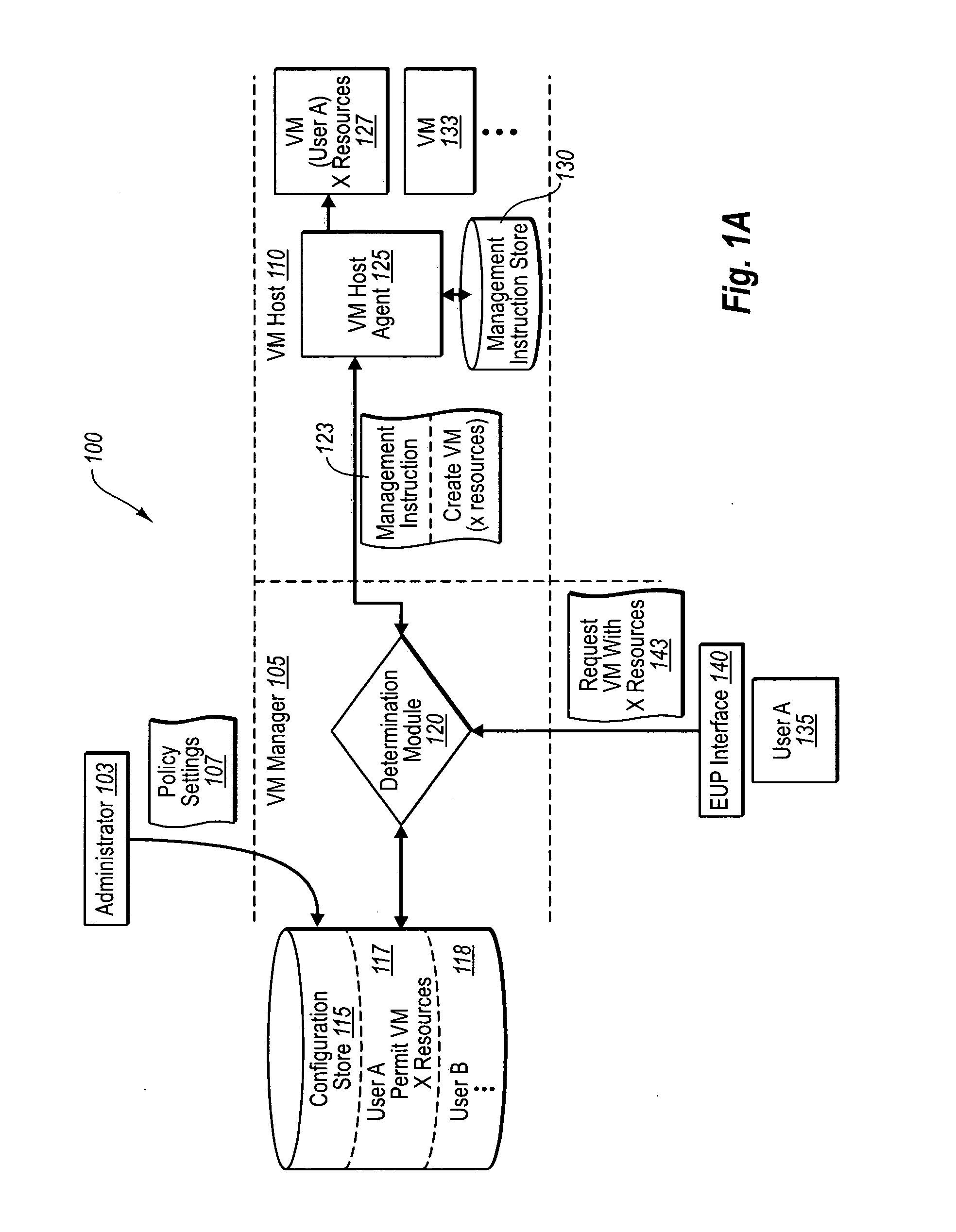
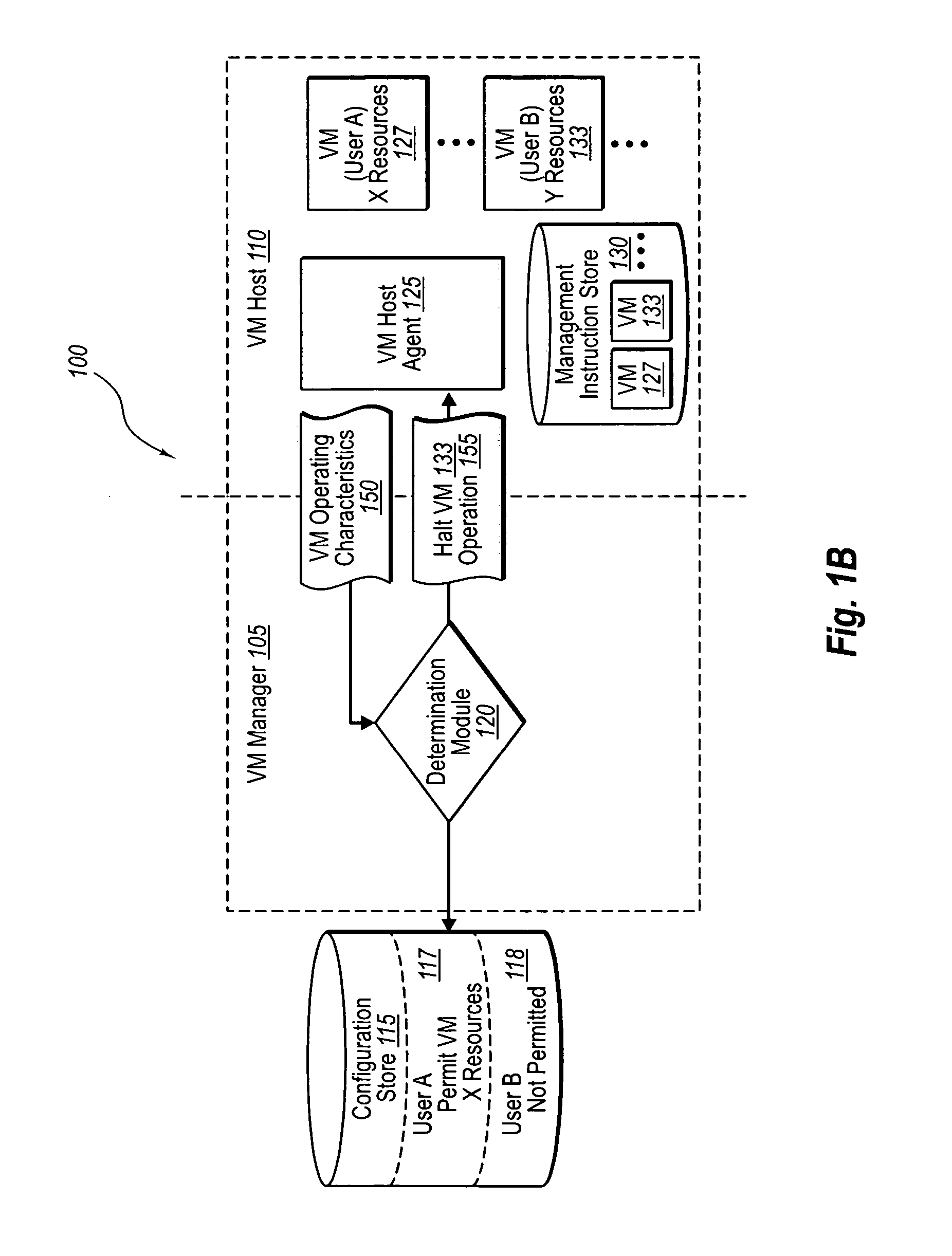
Managing virtual machines with system-wide policies
ActiveUS20070250833A1Digital computer detailsComputer security arrangementsVirtual machineHost machine
An administrative authority for virtual machines can send one or more delegated policy settings to a virtual machine manager. The virtual machine manager can in turn send management instructions that include the one or more policy settings to one or more virtual machine hosts. As such, a user's request for a virtual machine at a virtual machine host can be granted or denied based on the delegated policy settings. The policy settings can be updated periodically, and can include additional information about starting, stopping, expiring, saving, or even deleting virtual machines by particular users, as well as users accessing from particular locations. In addition, an agent operating at the virtual machine host can monitor and report virtual machine activity, to ensure unauthorized virtual machines are quickly stopped and reviewed until authorized.
Owner:SERVICENOW INC
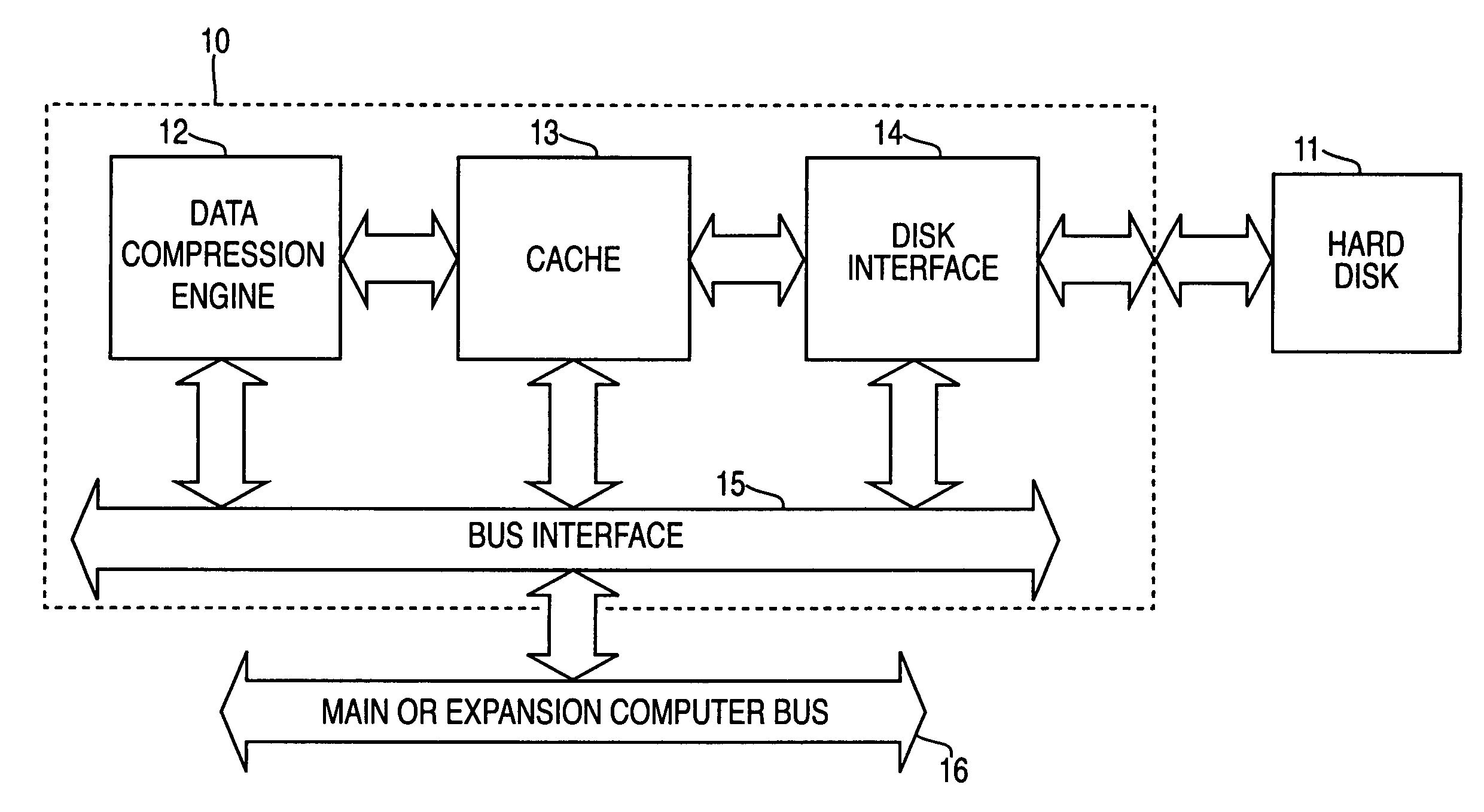
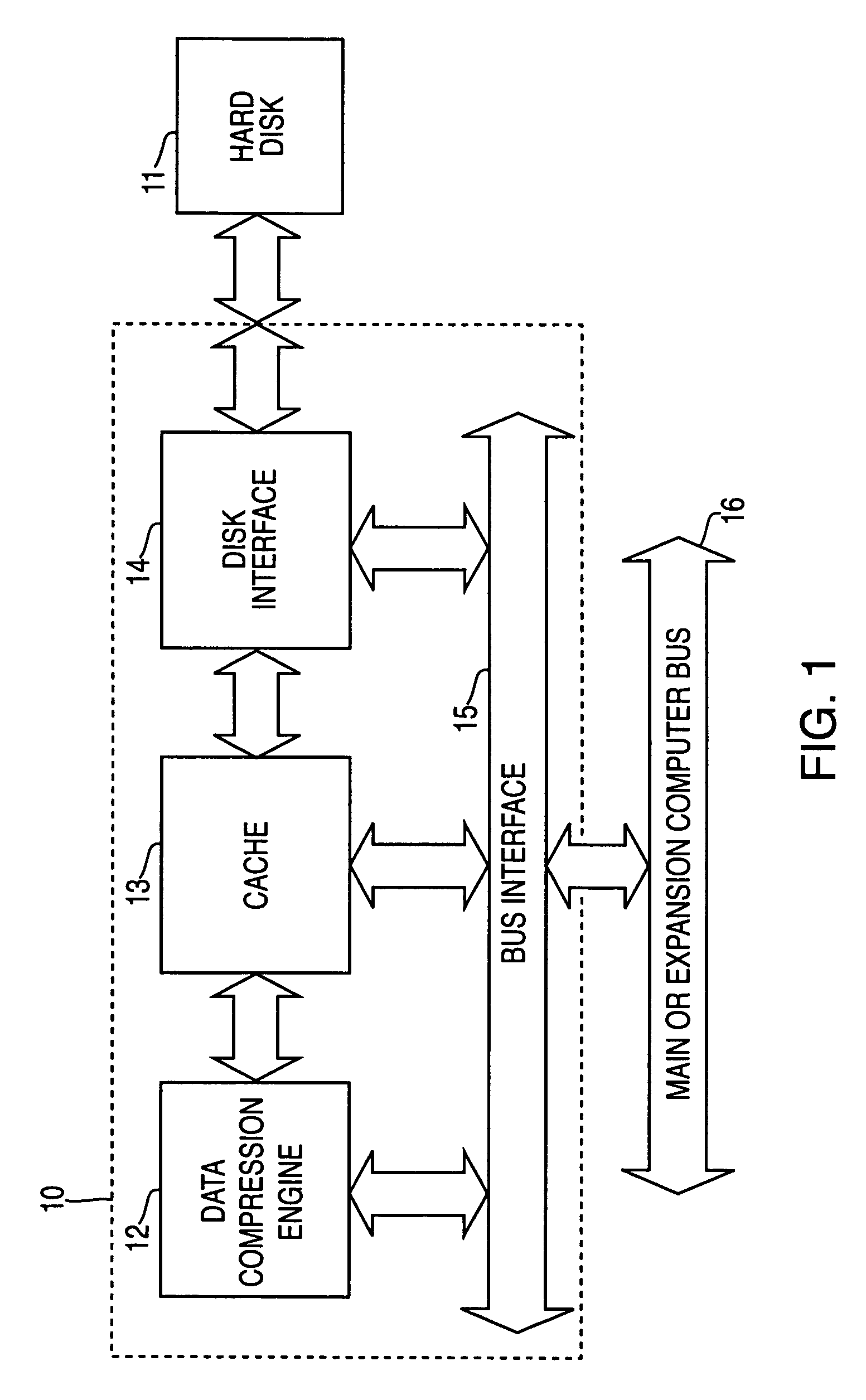
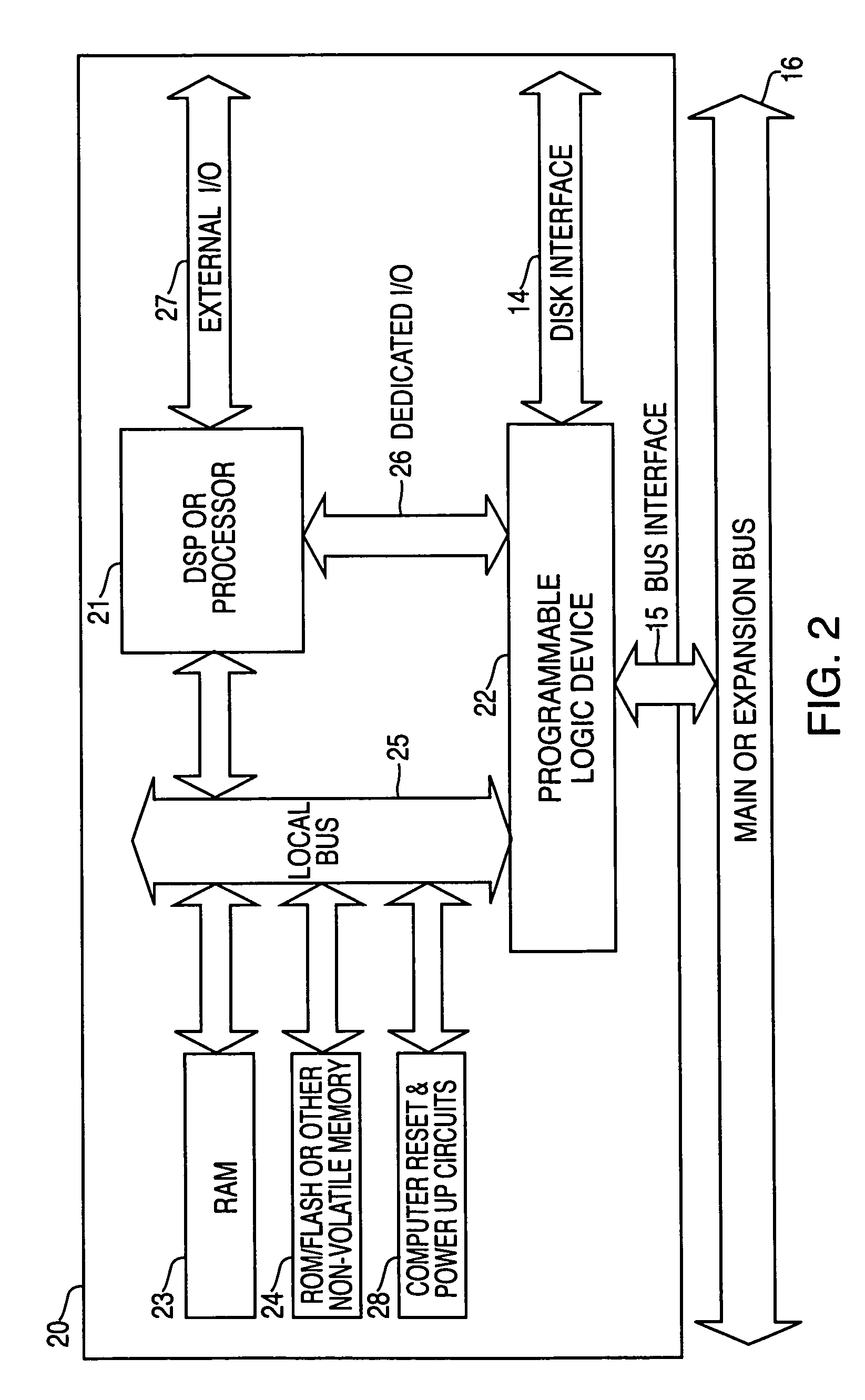
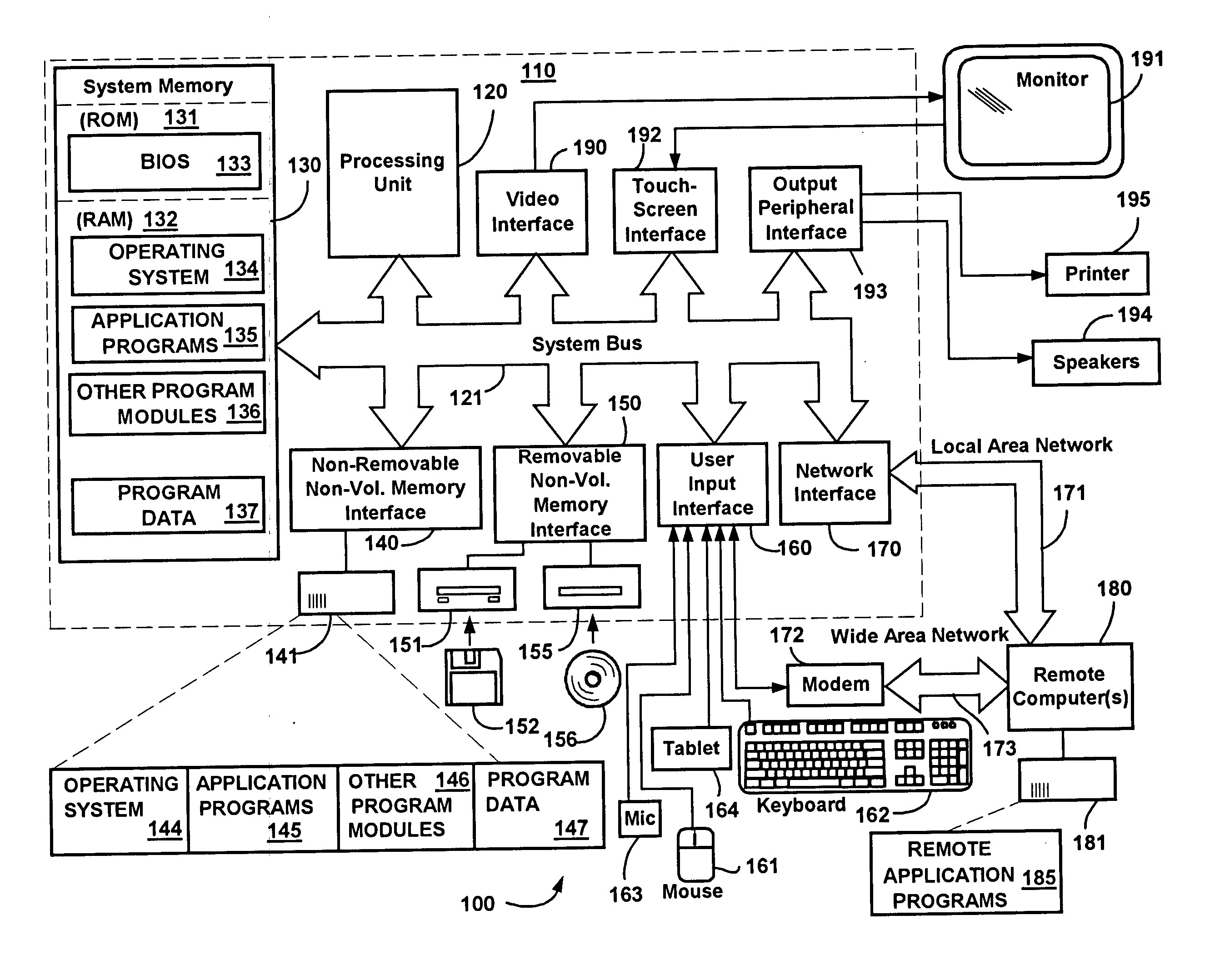
Systems and methods for accelerated loading of operating systems and application programs
InactiveUS7181608B2Easy loadingBroaden applicationInput/output to record carriersCode conversionOperational systemComputerized system
Systems and methods are provided for accelerated loading of operating system and application programs upon system boot or application launch. In one aspect, a method for providing accelerated loading of an operating system includes maintaining a list of boot data used for booting a computer system, preloading the boot data upon initialization of the computer system, and servicing requests for boot data from the computer system using the preloaded boot data. The boot data may comprise program code associated with an operating system of the computer system, an application program, and a combination thereof. The boot data is retrieved from a boot device and stored in a cache memory device. The boot data is stored in a compressed format on the boot device and the preloaded boot data is decompressed prior to transmitting the preloaded boot data to the requesting system.
Owner:REALTIME DATA
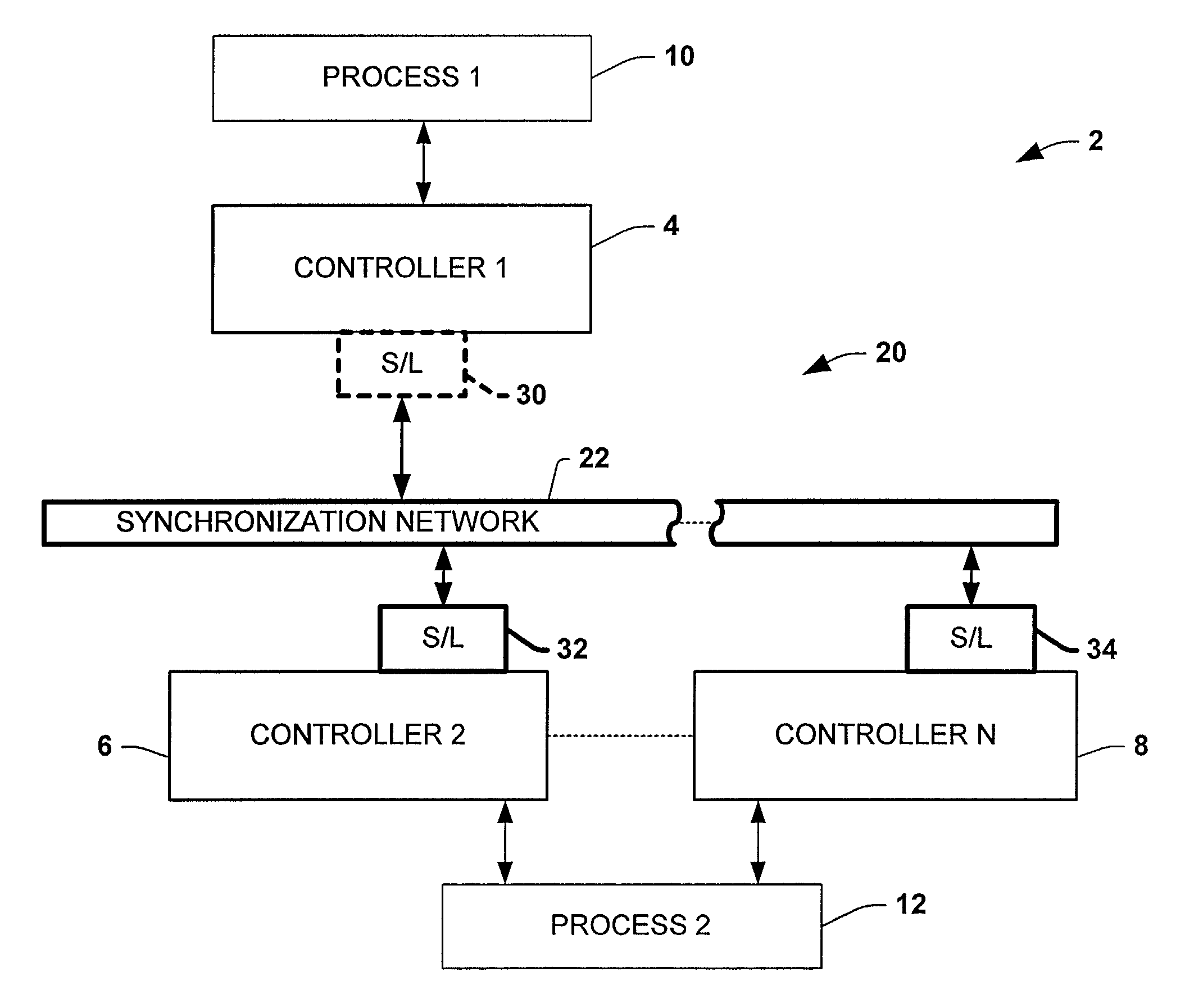
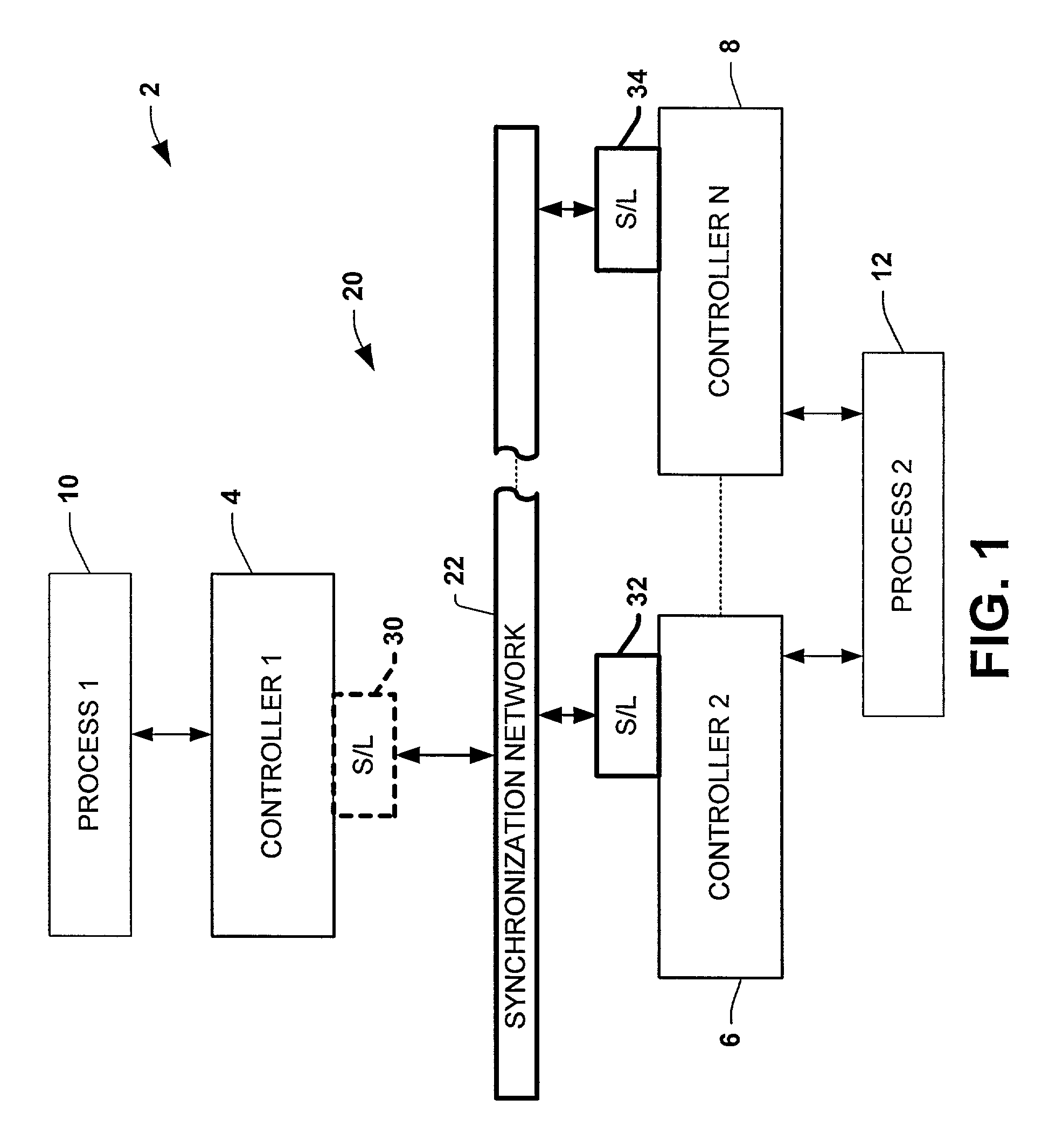
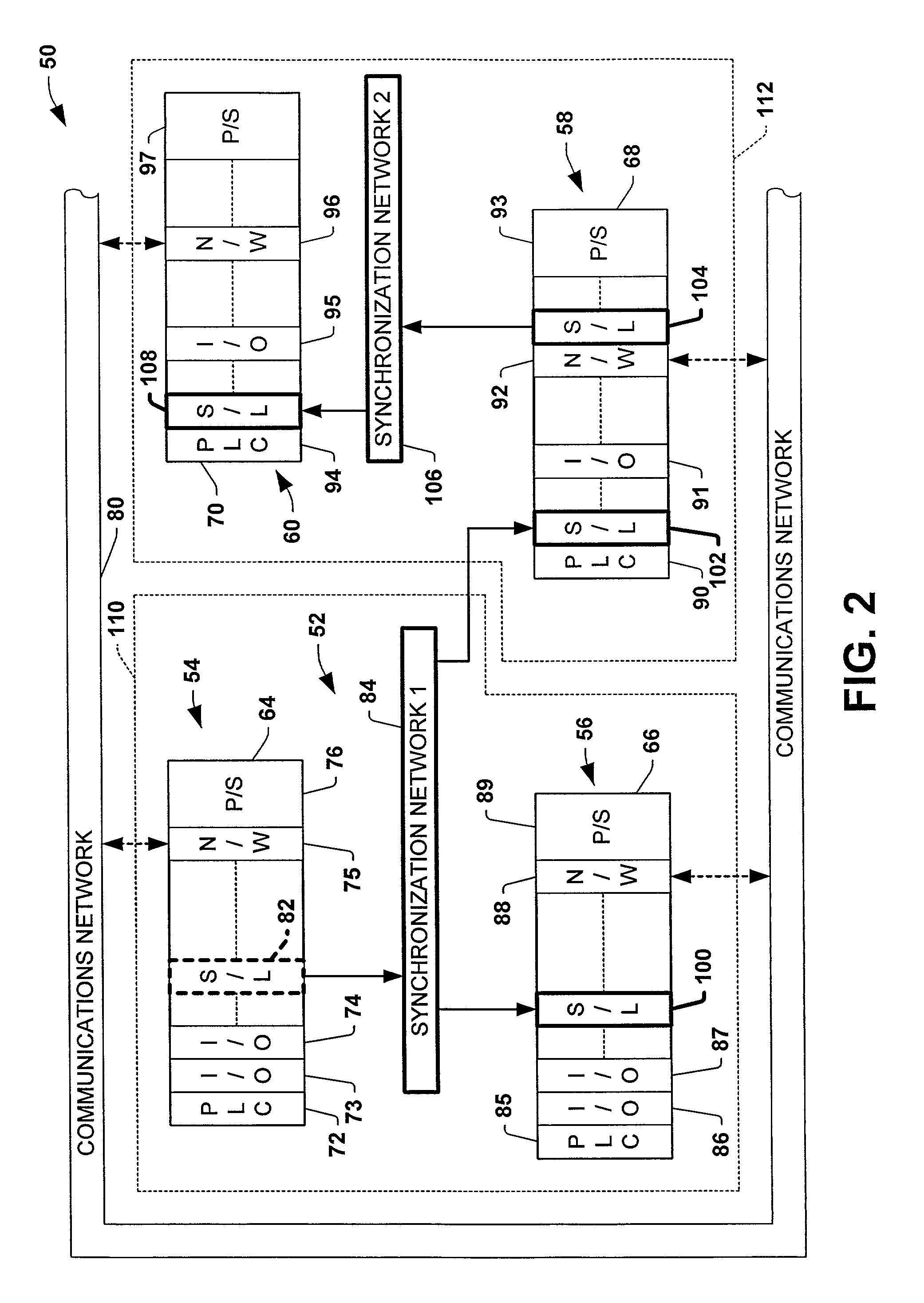
Protocol and method for multi-chassis configurable time synchronization
ActiveUS7007106B1Data representation error detection/correctionCode conversionSynchronous controlControl system
Systems and methods are disclosed for time synchronization of operations in a control system. Synchronization networks and devices are provided for transferring synchronization information between controllers in a distributed or localized control system, which is employed in order to allow operation of such controllers to be synchronized with respect to time. Also disclosed are synchronization protocols and hardware apparatus employed in synchronizing control operations in a control system.
Owner:ROCKWELL TECH
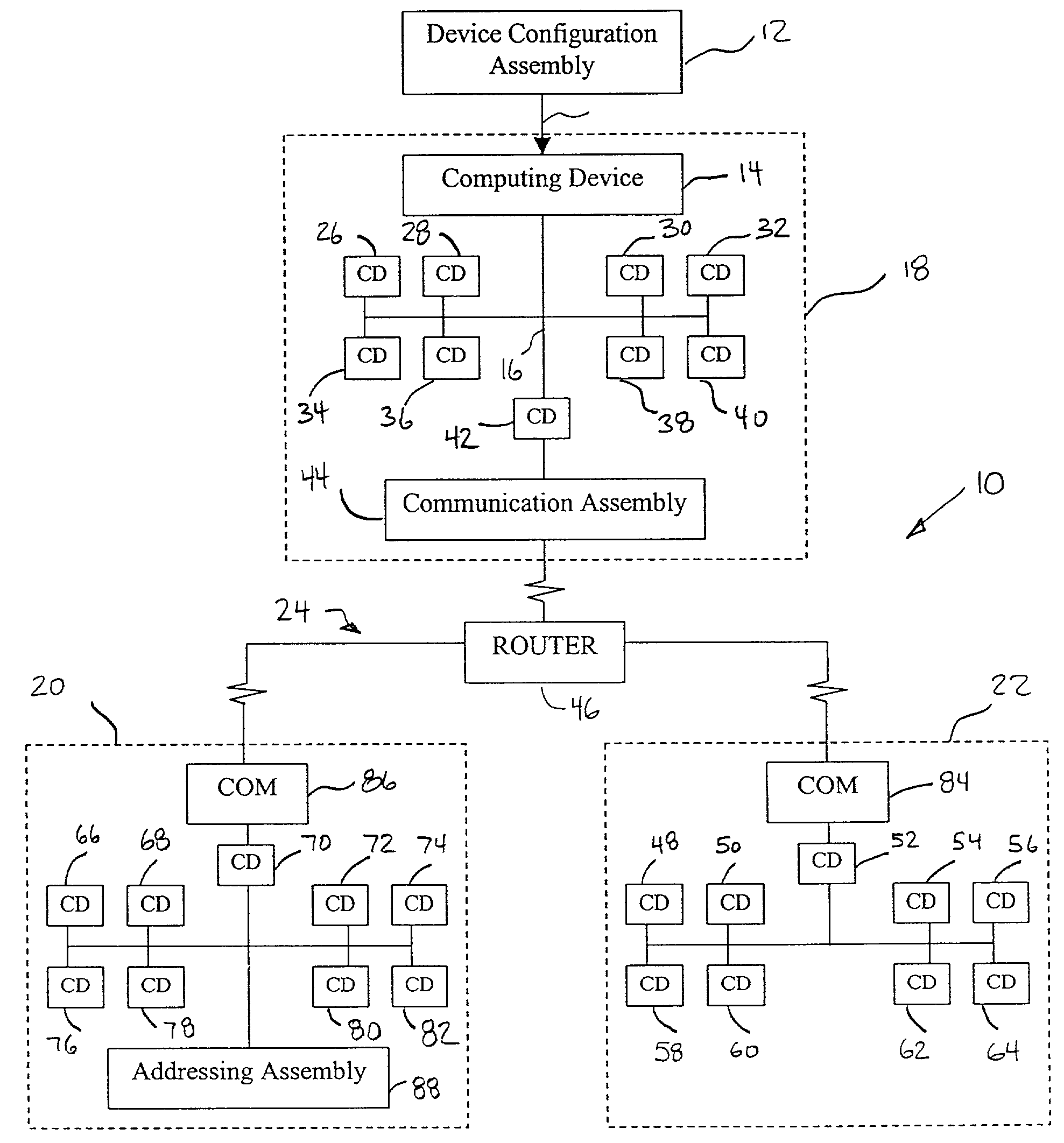
System and method for remote discovery and configuration of a network device
A technique for remotely configuring a computing device via a network. A device configuration system is provided to determine a network address of the computing device, to identify the computing device, and to facilitate network configuration of the computing device. The device configuration system also may include a remote interface and a remote device information system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
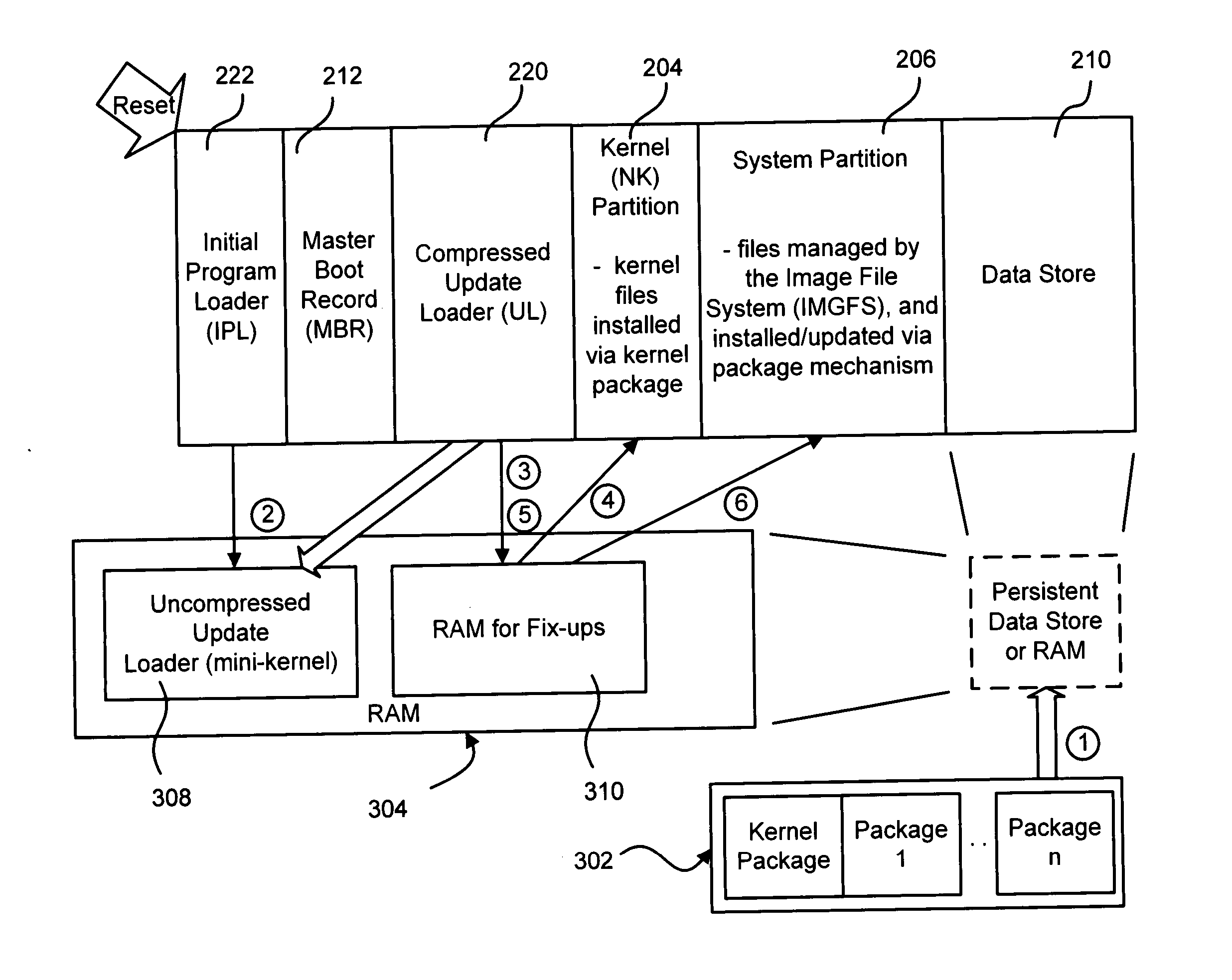
Applying custom software image updates to non-volatile storage in a failsafe manner
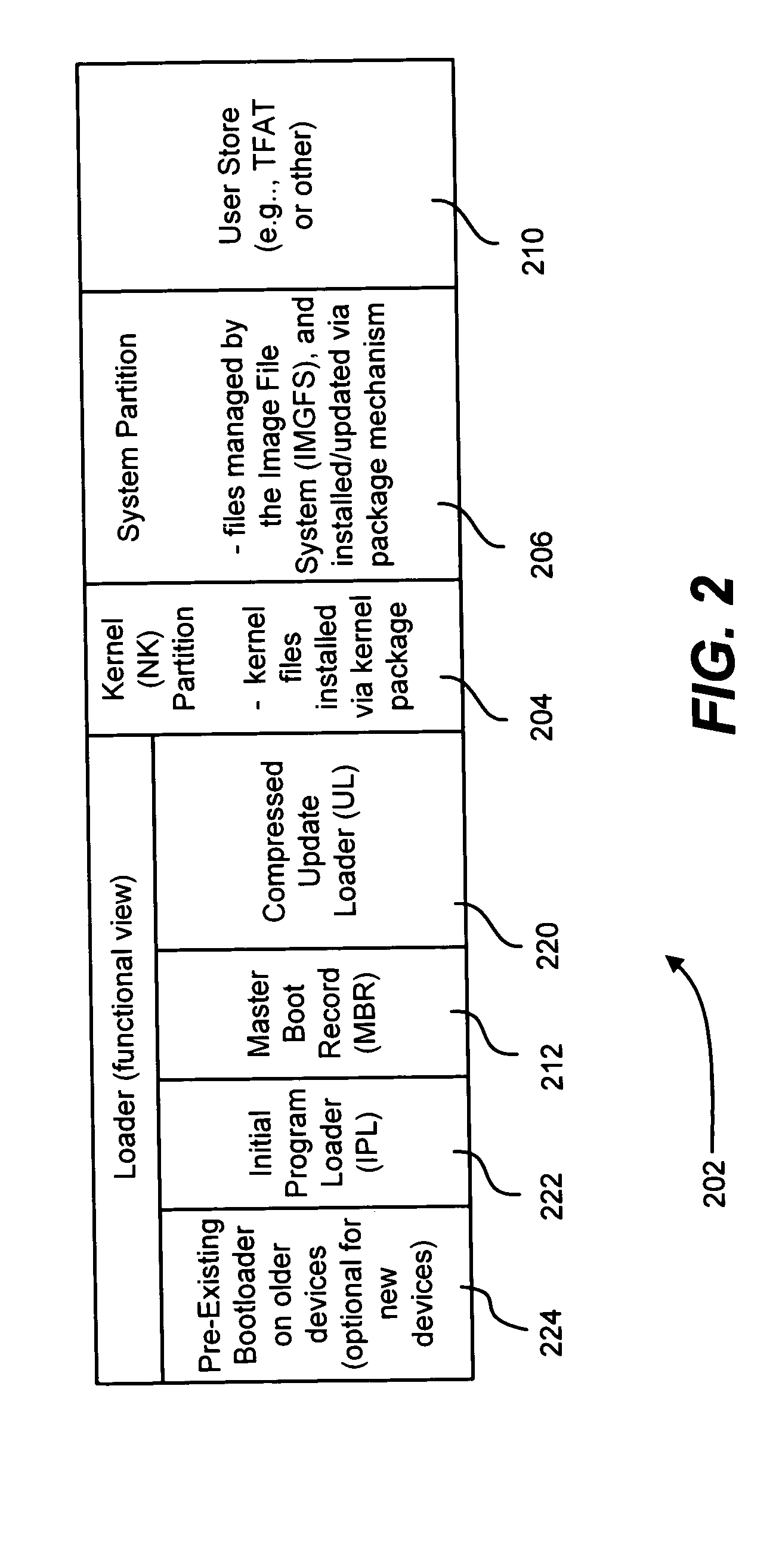
Described is a system and method in which software updates in the form of self-contained, secure entities are applied to an embedded device's non-volatile storage in a failsafe manner. Various types of software updates may be applied, and updates may contain executable code and / or data. Following a reboot, an initial program loader determines an update mode, and if updating, boots to a special update loader. The update loader processes update packages to apply the updates. Kernel partition, system partition and reserve section updates may be updated with entire files or binary difference files, with failure handling mechanisms are provided for each type of update. Updates may be simulated before committing them. Updates may be relocated in memory as appropriate for a device.
Owner:MICROSOFT TECH LICENSING LLC
Methods, systems and computer program products for secure firmware updates
ActiveUS7069452B1Avoid accessReduce stepsDigital computer detailsUnauthorized memory use protectionData storeControl equipment
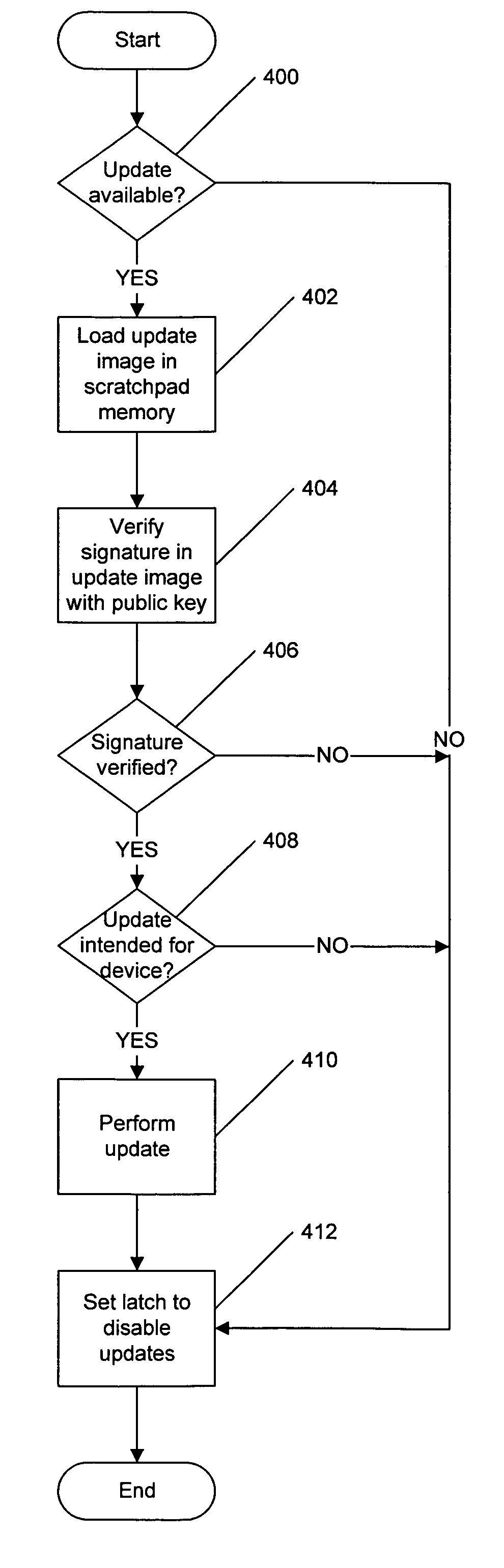
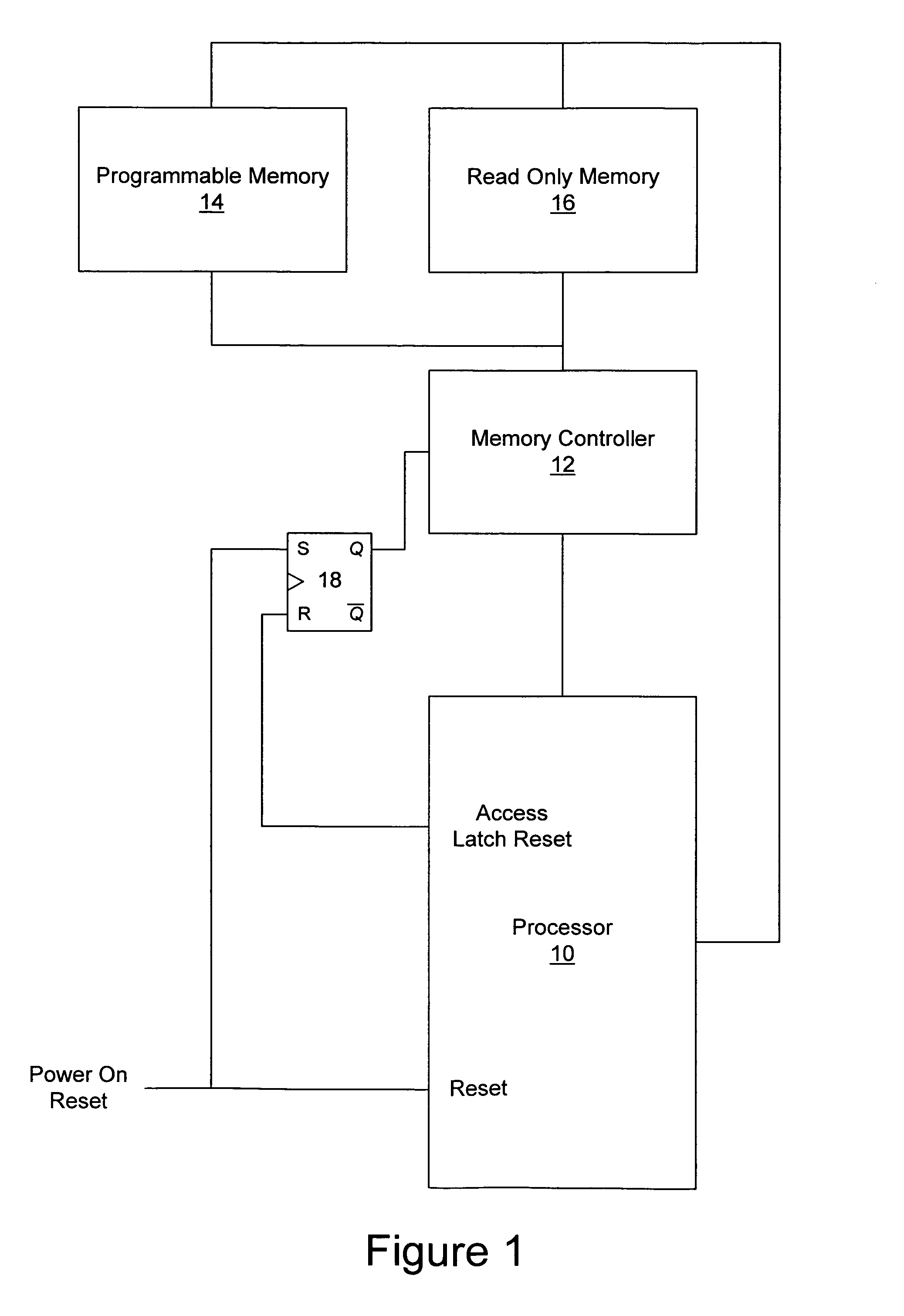
Methods, systems and computer program products which provide secure updates of firmware (i.e. data stored in a programmable memory device of a processing system) are disclosed. Updates of a programmable memory of a device may be controlled by providing an update window of finite duration during which the programmable memory may be updated. Access to the programmable memory may be based on the state of an access latch. The access latch may be set to allow access after a hardware reset of the device. An update control program may be executed to control access to the programmable memory and the latch reset to prevent access upon completion of the update control program. Verification of the update may be provided through encryption techniques and rules incorporated in certificates for application of updates to provide for selectively updating devices. Also disclosed are methods of securely providing differing functionality to generic devices.
Owner:IBM CORP
Computer System and Method for Performing Integrity Detection on the Same
InactiveUS20090300415A1Ensure consistencyEnsures strictnessFault responseDigital data processing detailsOperational systemComputerized system
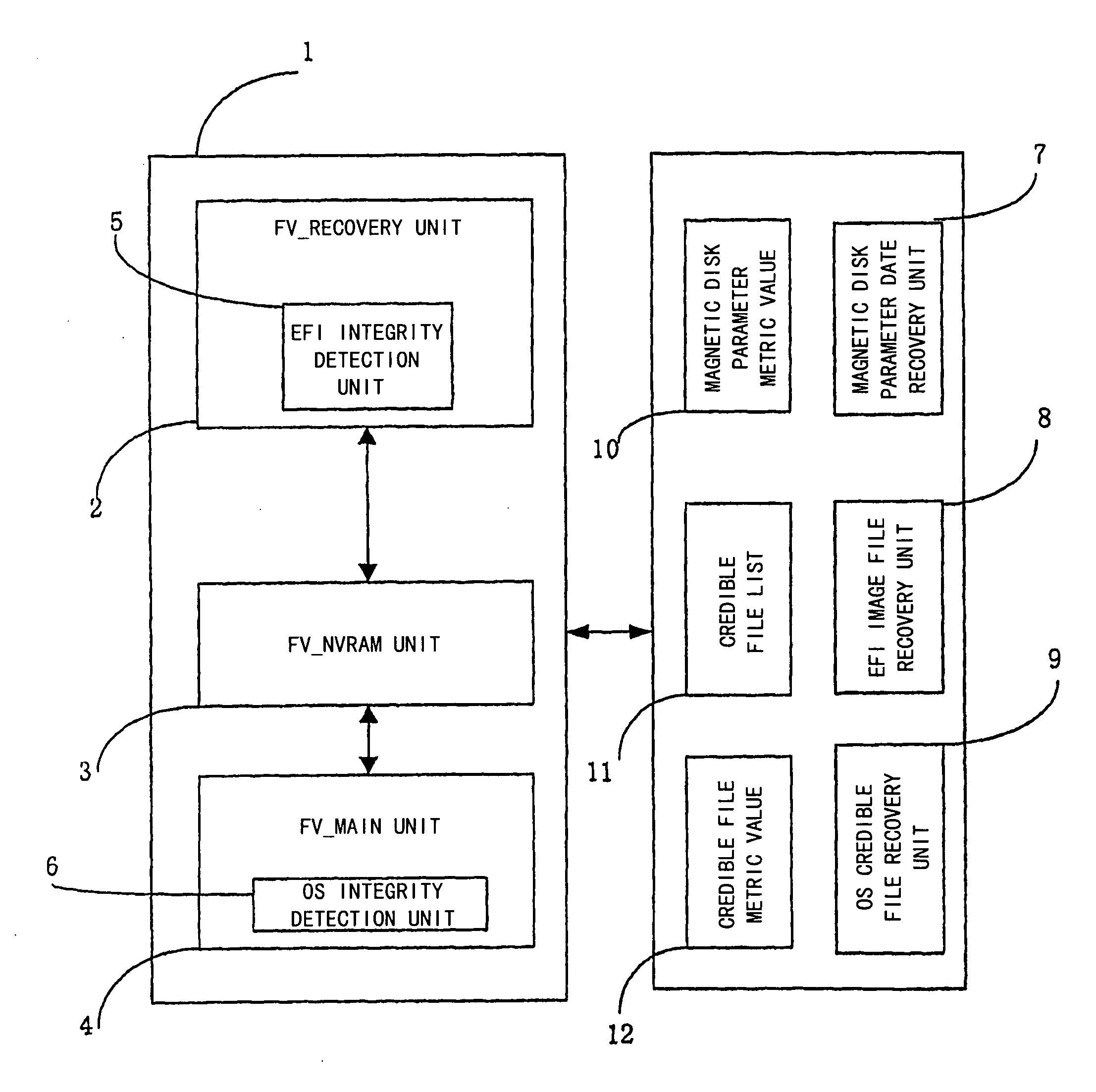
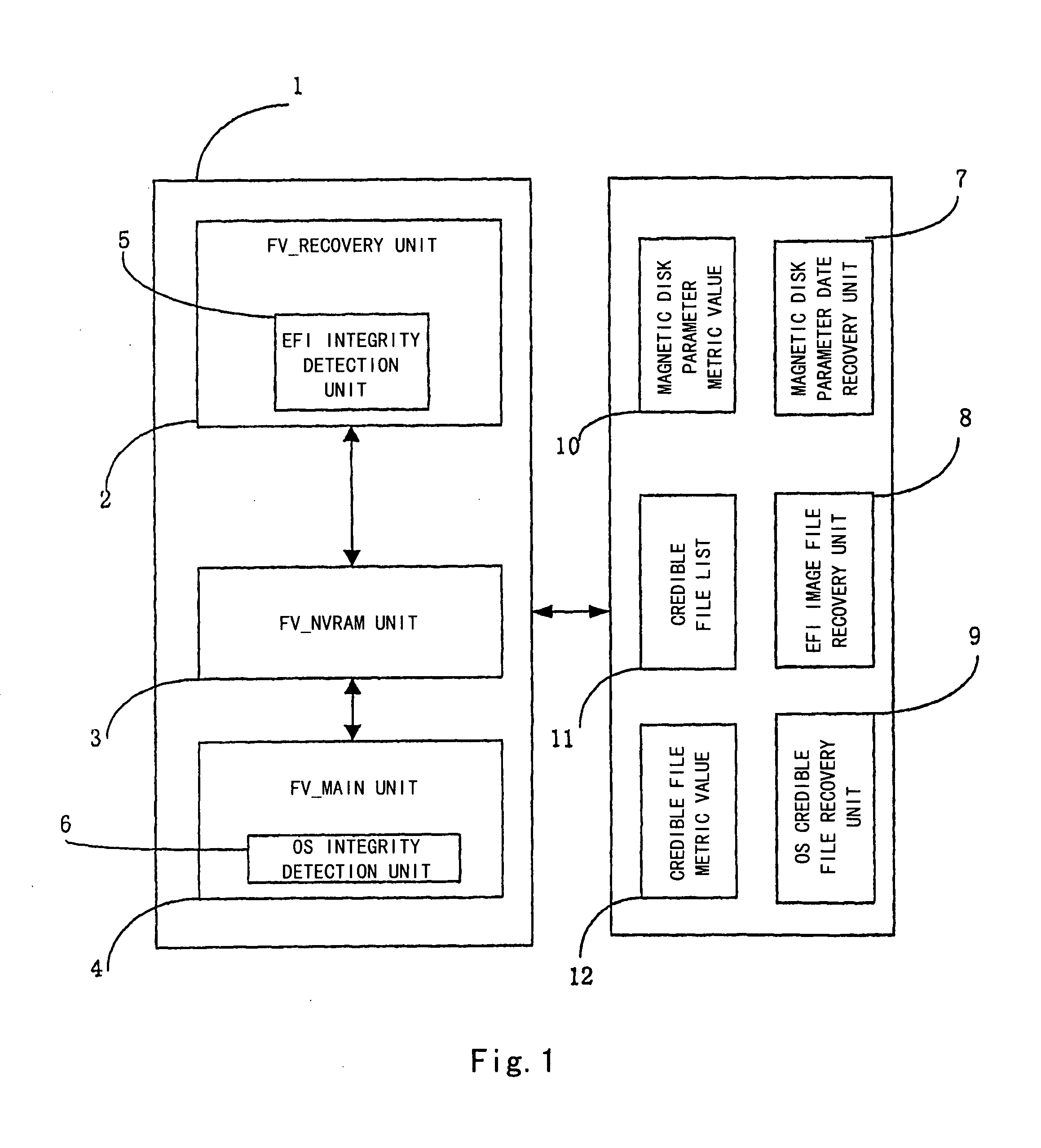
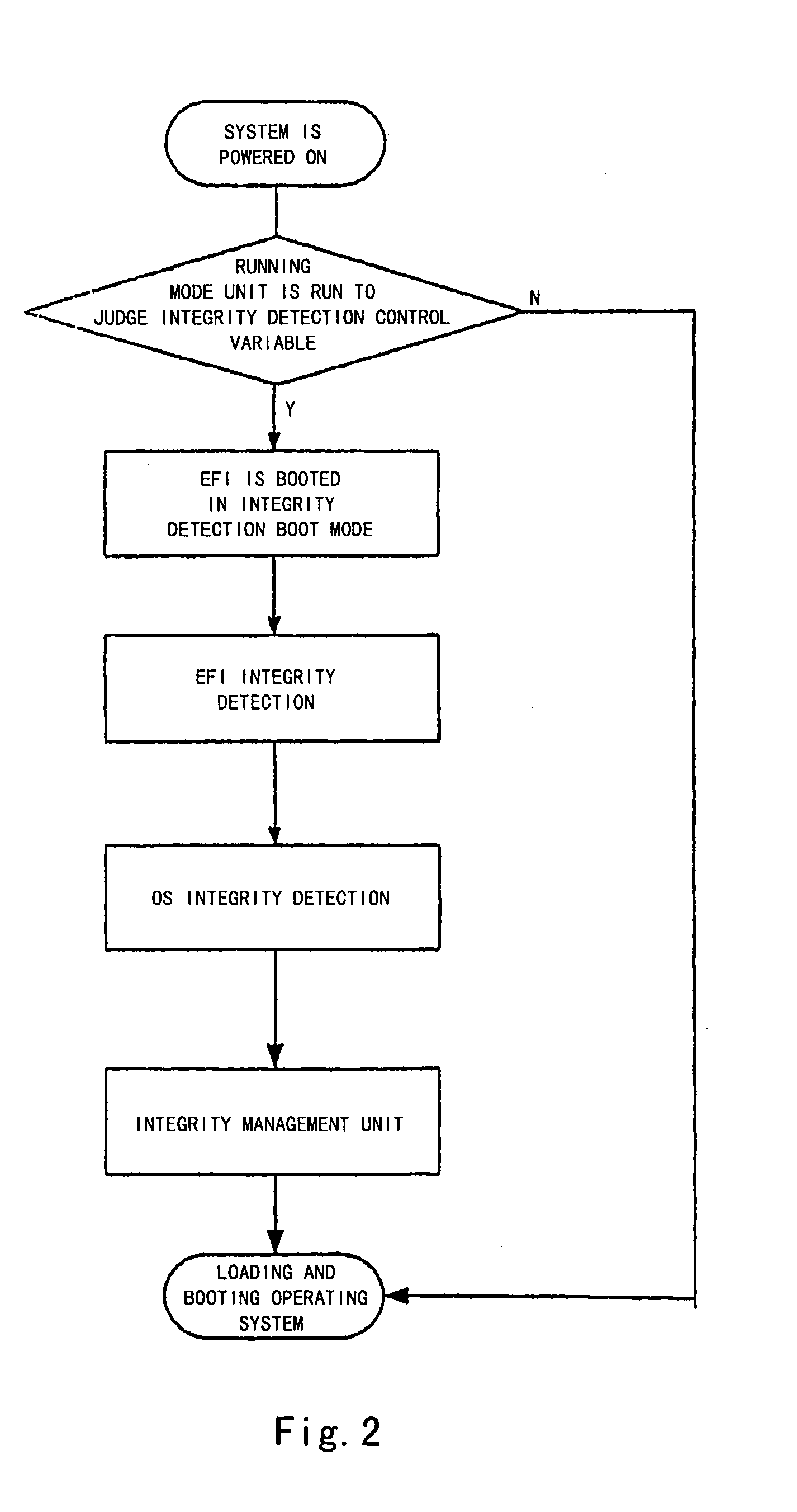
The present invention proposes a computer system and a method capable of performing integrity detection, comprising: a running mode unit which comprises an integrity detection boot variable to determine whether or not to initiate an integrity detection boot mode by judging said running mode unit; an EFI integrity detection unit (5), which is used for performing an integrity detection on EFI image codes in the integrity detection boot mode, and comprises an integrity metric value for being compared with an EFI integrity calculated value generated after the EFI integrity detection unit performs the integrity detection on the EFI image codes, to determine the integrity of the EFI image codes; an operating system integrity detection unit (6); and an integrity management unit. The present invention is based on the EFI BIOS to perform the integrity detection on the operating system during the pre-boot stage, having better reliability and security.
Owner:LENOVO (BEIJING) CO LTD
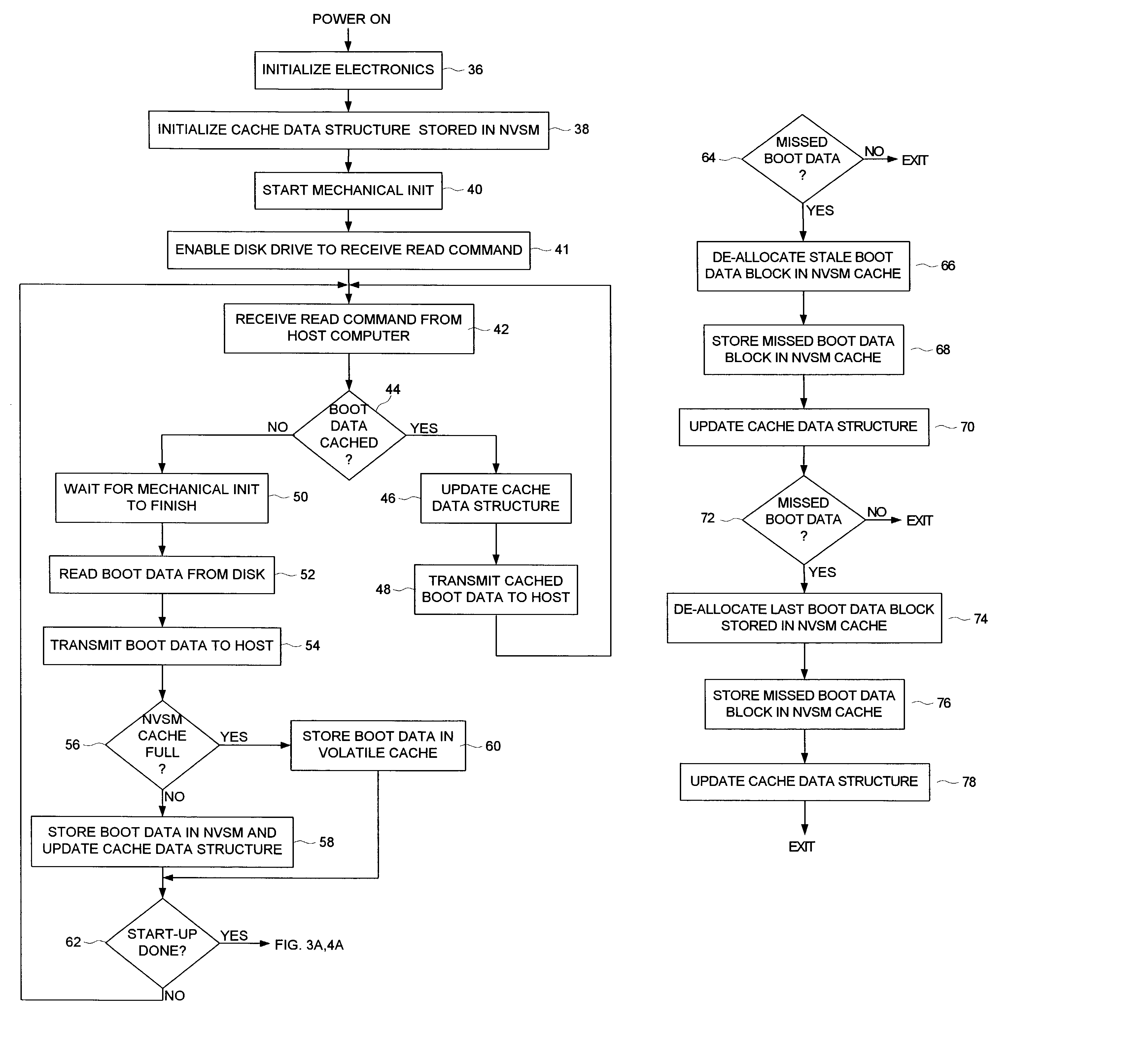
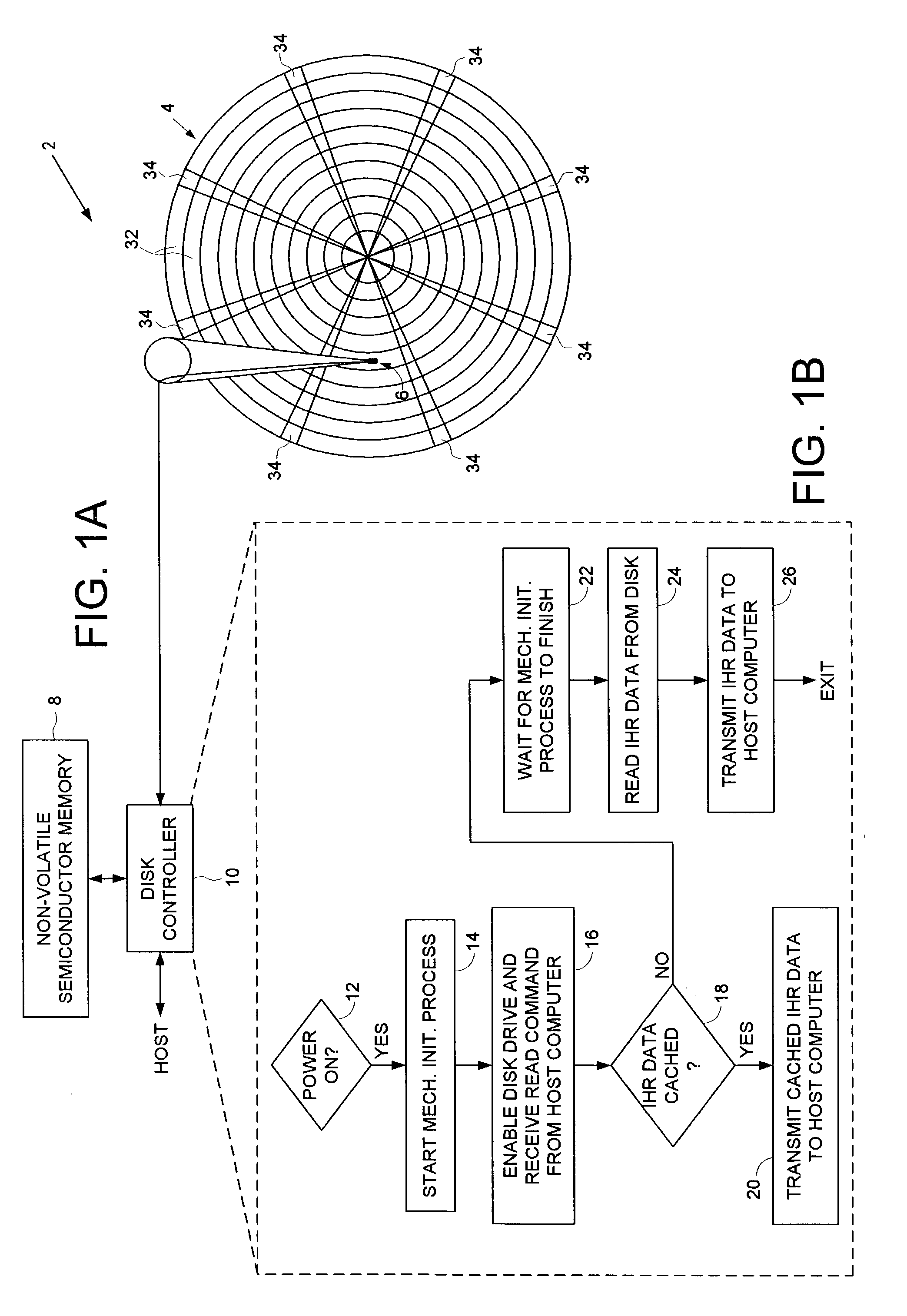
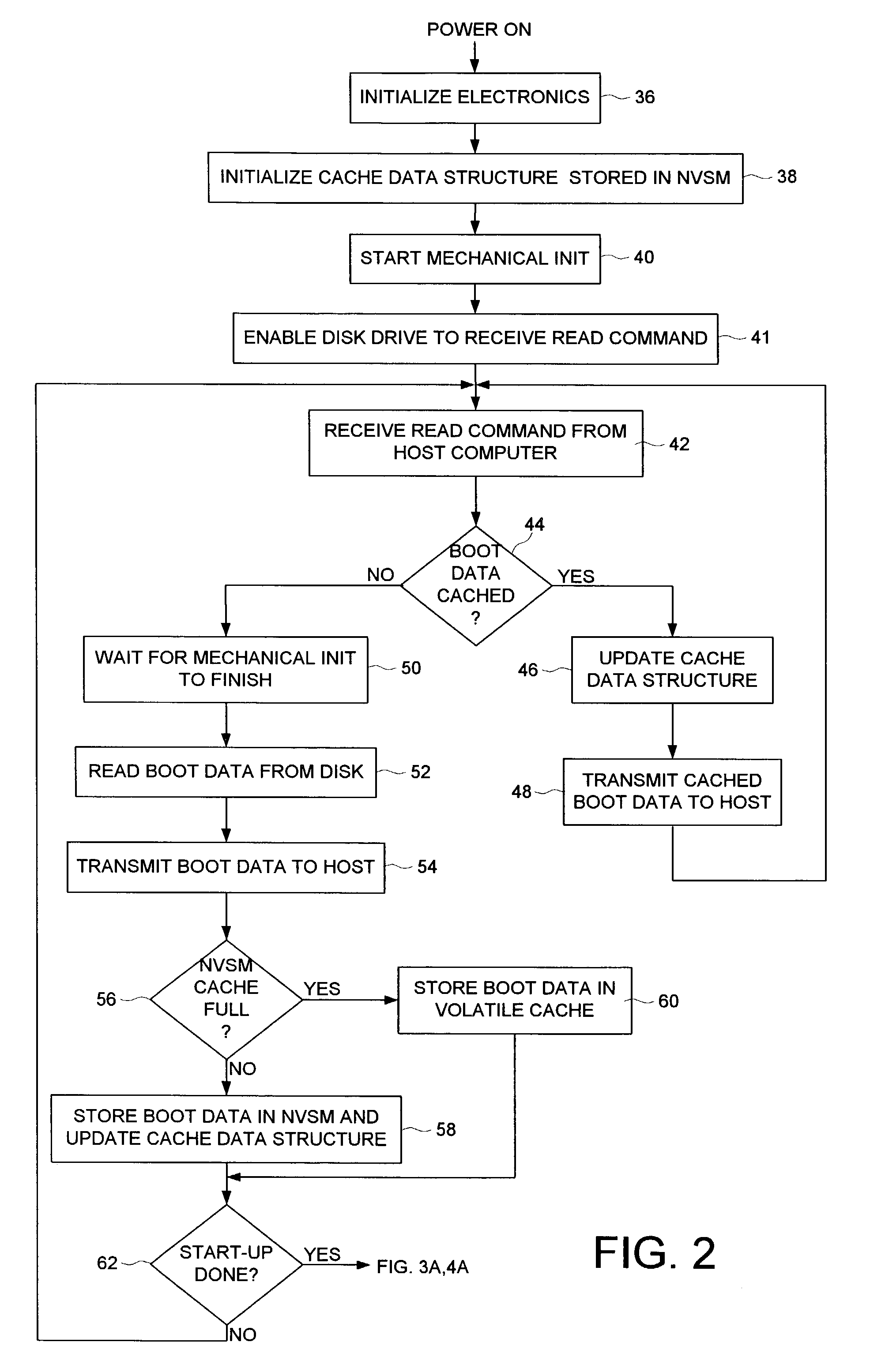
Disk drive caching initial host requested data in non-volatile semiconductor memory to reduce start-up time of a host computer
A disk drive is disclosed comprising a disk for storing initial host requested (IHR) data requested by a host computer during a start-up process of the host computer, a head actuated radially over the disk, and a non-volatile semiconductor memory (NVSM) for caching at least part of the IHR data. The disk drive transmits the cached IHR data from the NVSM to the host computer during the start-up process thereby avoiding the delay associated with initializing the mechanics of the disk drive as well as conserving battery power for mobile applications.
Owner:WESTERN DIGITAL TECH INC
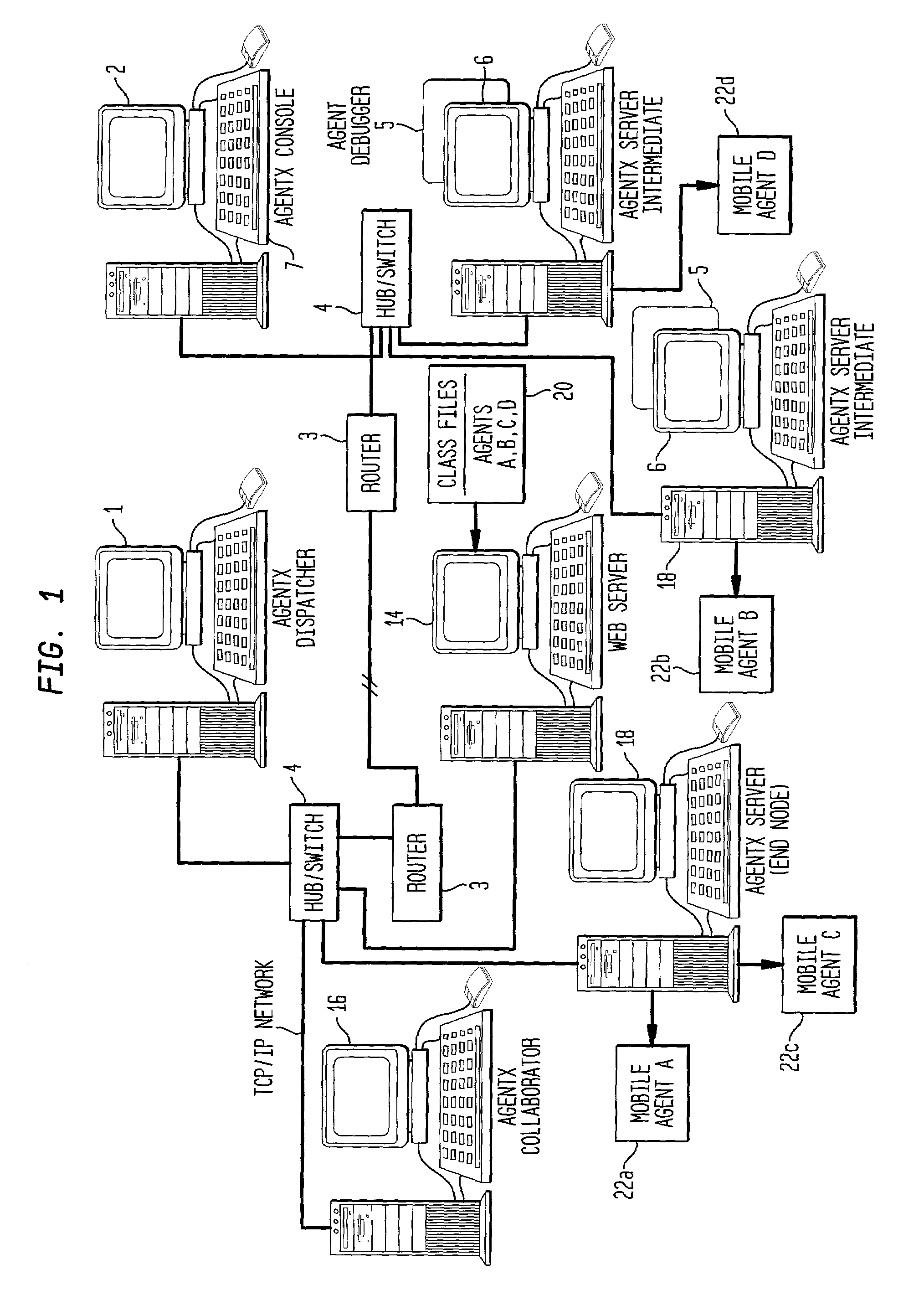
Method and apparatus for breaking down computing tasks across a network of heterogeneous computer for parallel execution by utilizing autonomous mobile agents
InactiveUS7082604B2Ease of parallel processingProgram initiation/switchingResource allocationApplication softwareLarge applications
A method and apparatus is provided for breaking down computing tasks within a larger application and distributing such tasks across a network of heterogeneous computers for simultaneous execution. The heterogeneous computers may be connected across a wide or local area network. The invention supports mobile agents that are self-migrating and can transport state information and stack trace information as they move from one host to another, continuing execution where the mobile agents may have left off. The invention includes a server component for providing an execution environment for the agents, in addition to sub-components which handle real-time collaboration between the mobile agents as well as facilities monitoring during execution. Additional components provide realistic thread migration for the mobile agents. Real-time stack trace information is stored as the computing tasks are executed, and if over-utilization of the computing host occurs, execution of the computing task can be halted and the computing task can be transferred to another computing hosts where execution can be seamlessly resumed using the stored, real-time state information and stack trace information.
Owner:MOBILE AGENT TECH
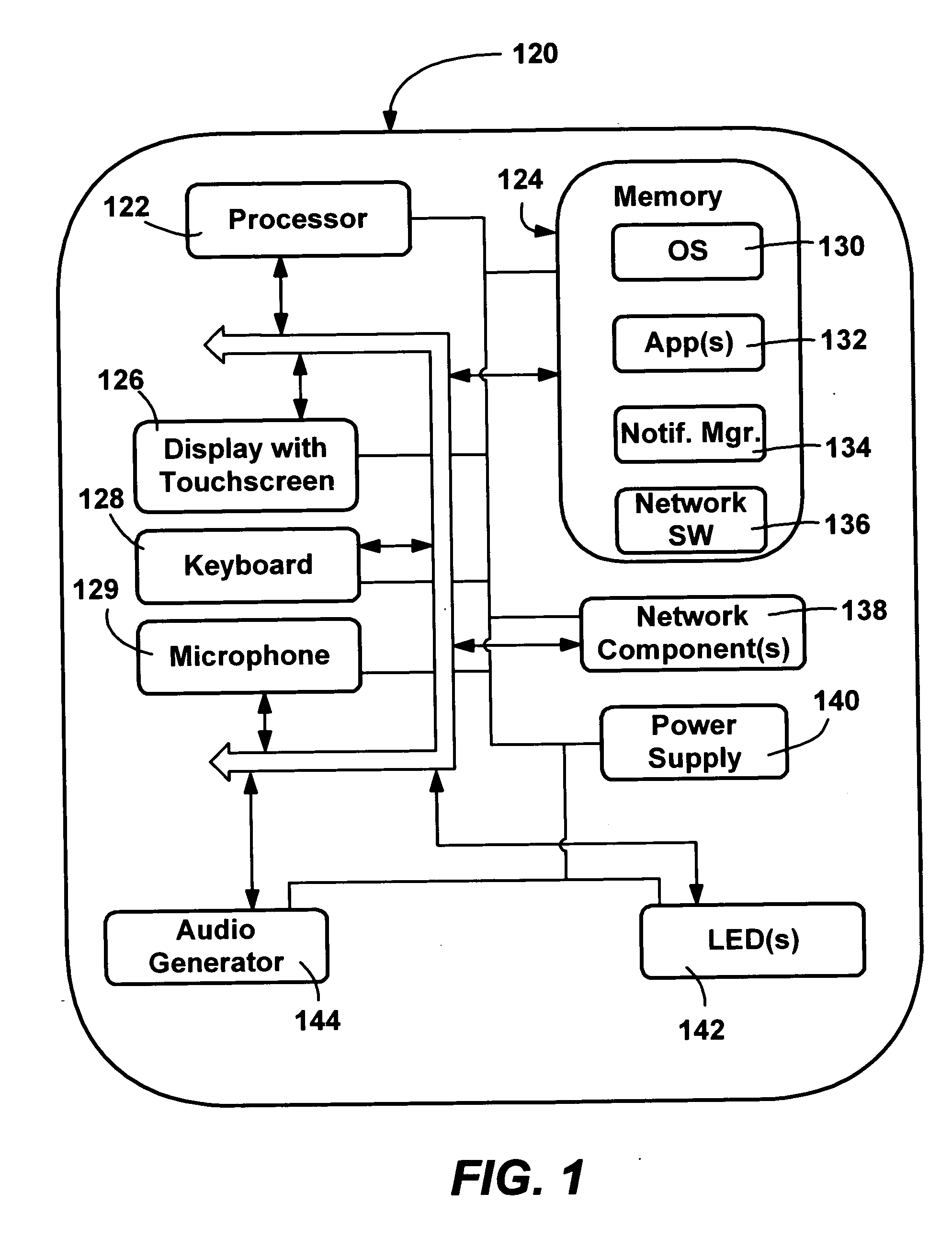
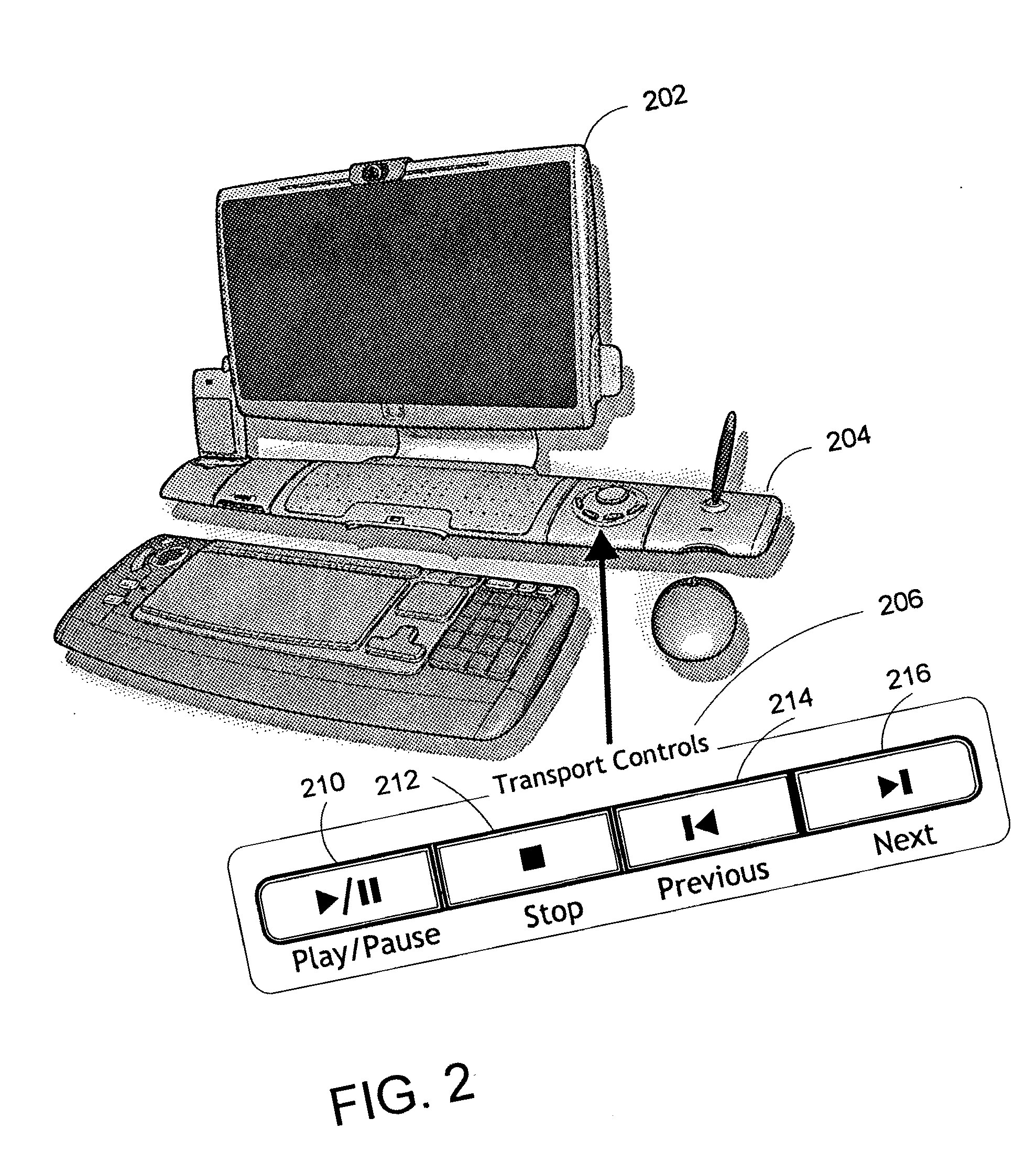
Method and system for navigation using media transport controls
ActiveUS20050071437A1Improve playbackSimple systemInput/output for user-computer interactionDigital computer detailsRemote controlElectronic form
A system and method for improved navigation and access of computer media content using media transport controls is provided. These transport controls may be placed in various locations such as on the computer housing, on a keyboard, on a monitor or a remote control. With these controls, a user may easily play multimedia content and navigate to individual tracks or segments of an audio and / or video stream. The transport controls include a play / pause button, a stop button, a previous button, and a next button. A user may intuitively activate and interact with media content in a variety of applications using these transport controls. For example, users may play recordings such as voice mail and review their recorded replies using the transport controls. Users may similarly play and / or review multimedia annotations made to any application files, including traditional computer files such as spreadsheets, documents and presentations.
Owner:MICROSOFT TECH LICENSING LLC
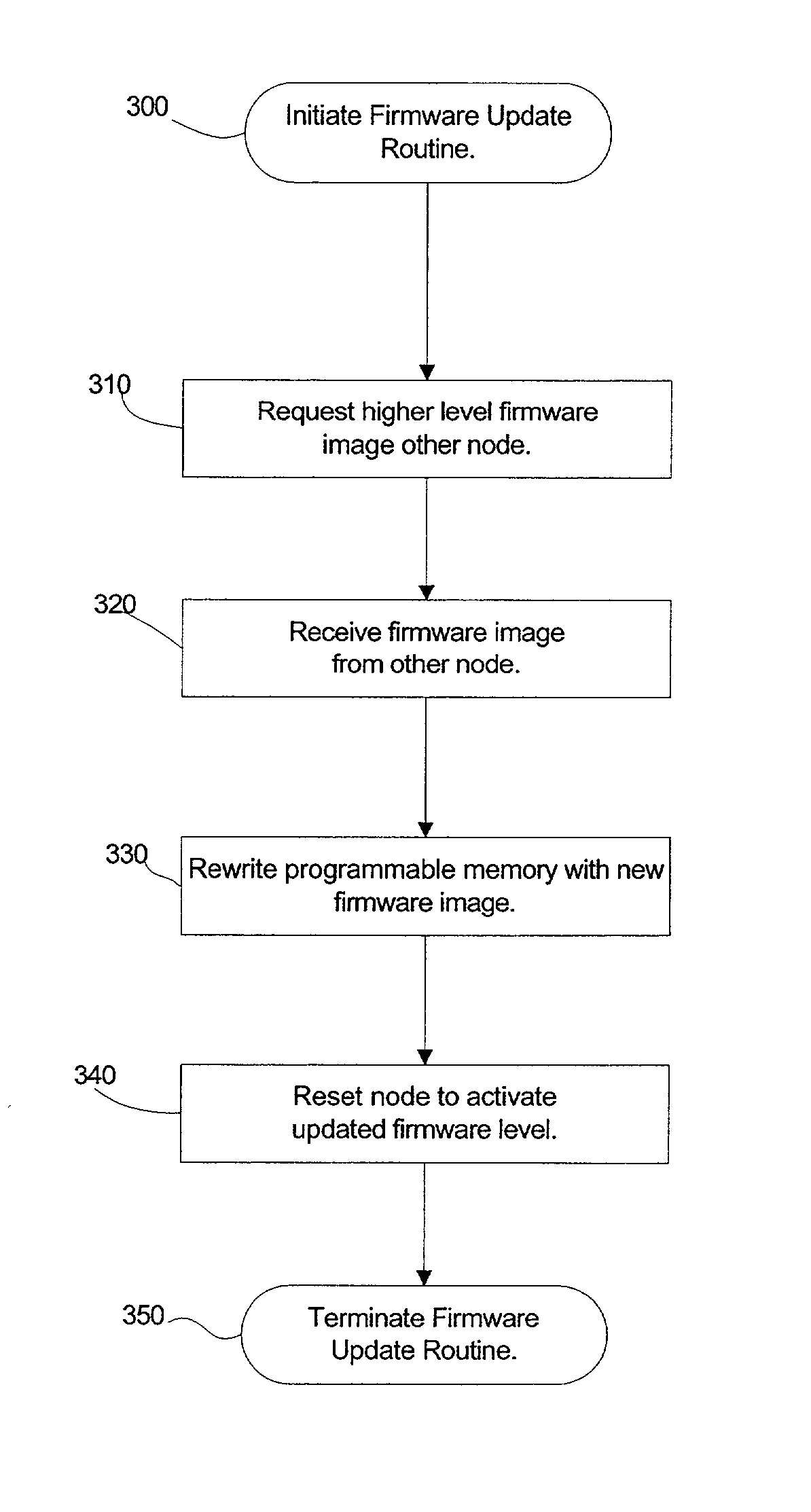
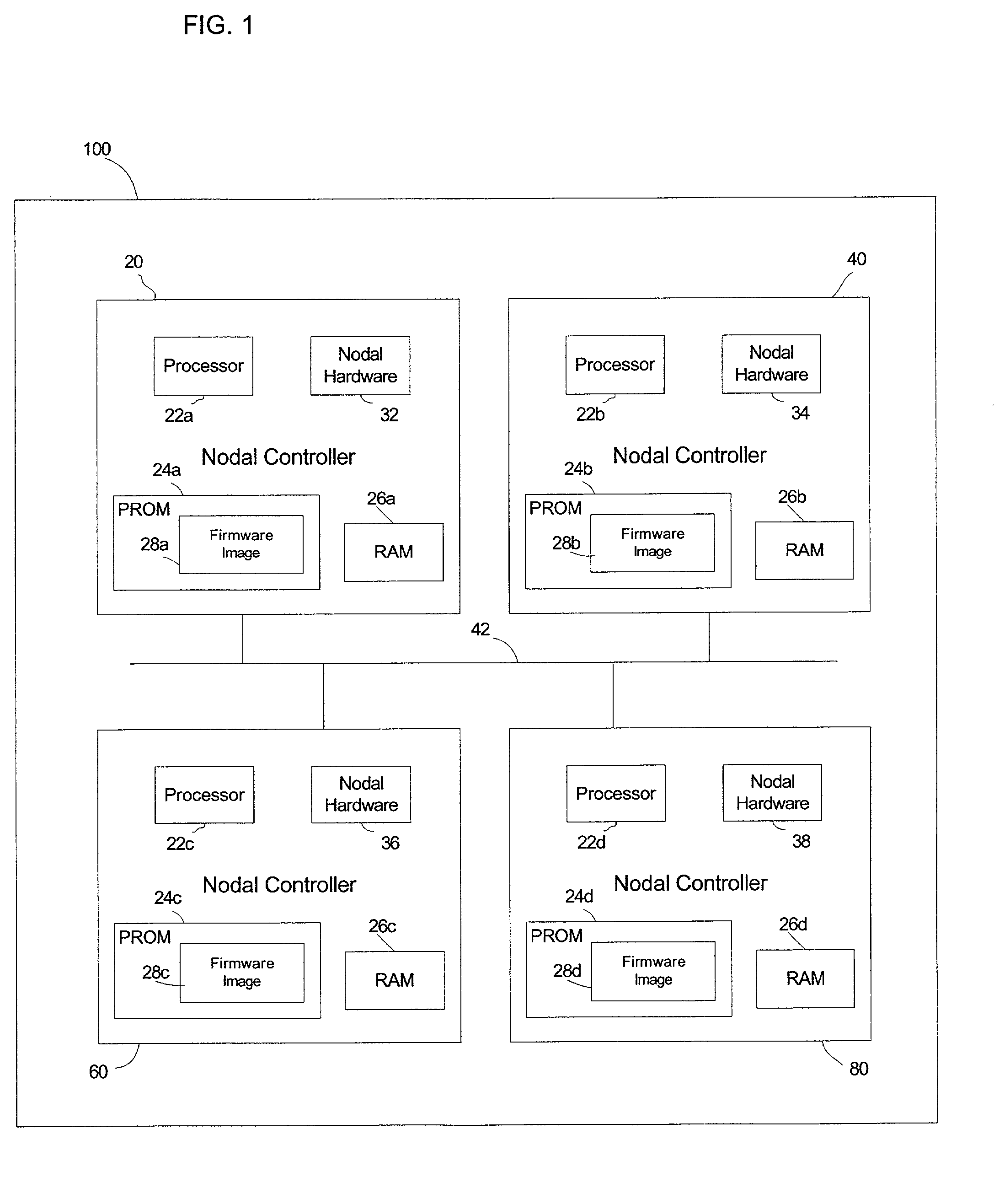
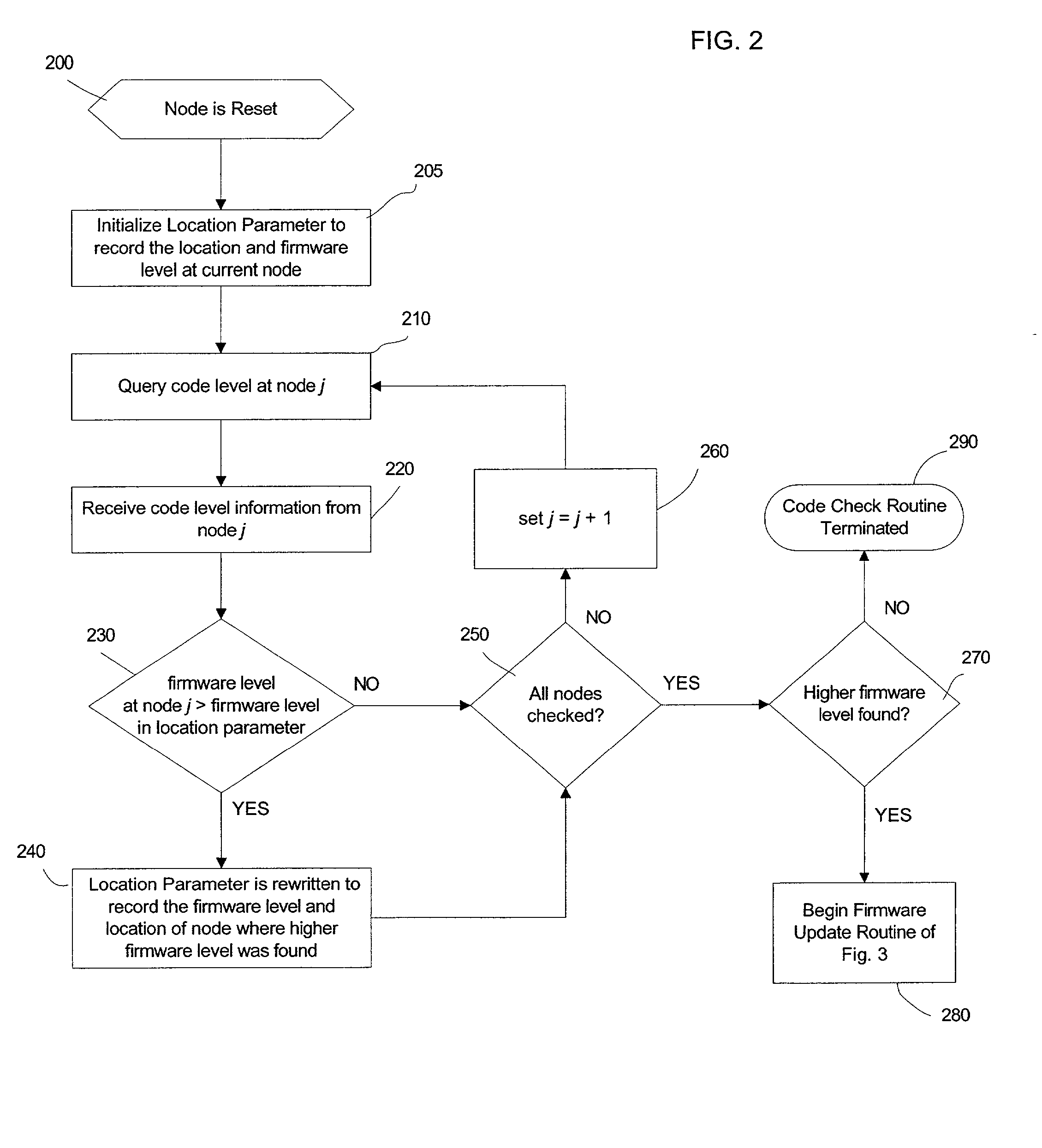
Automatic firmware update of processor nodes
InactiveUS20020091807A1Raise the possibilityAvoid incompatibilitiesDigital computer detailsData resettingCommunication interfaceProcessor node
Provided is a method, system, and program for updating the firmware in a nodal system. The nodal system includes at least two nodes, wherein each node includes a processing unit and a memory including code. The nodes communicate over a communication interface. At least one querying node transmits a request to at least one queried node in the nodal system for a level of the code at the node over the communication interface. At least one node receives a response from the queried node receiving the request indicating the level of code at the queried node over the communication interface. The node receiving the response determines whether at least one queried node has a higher code level.
Owner:IBM CORP
Secure Booting A Computing Device
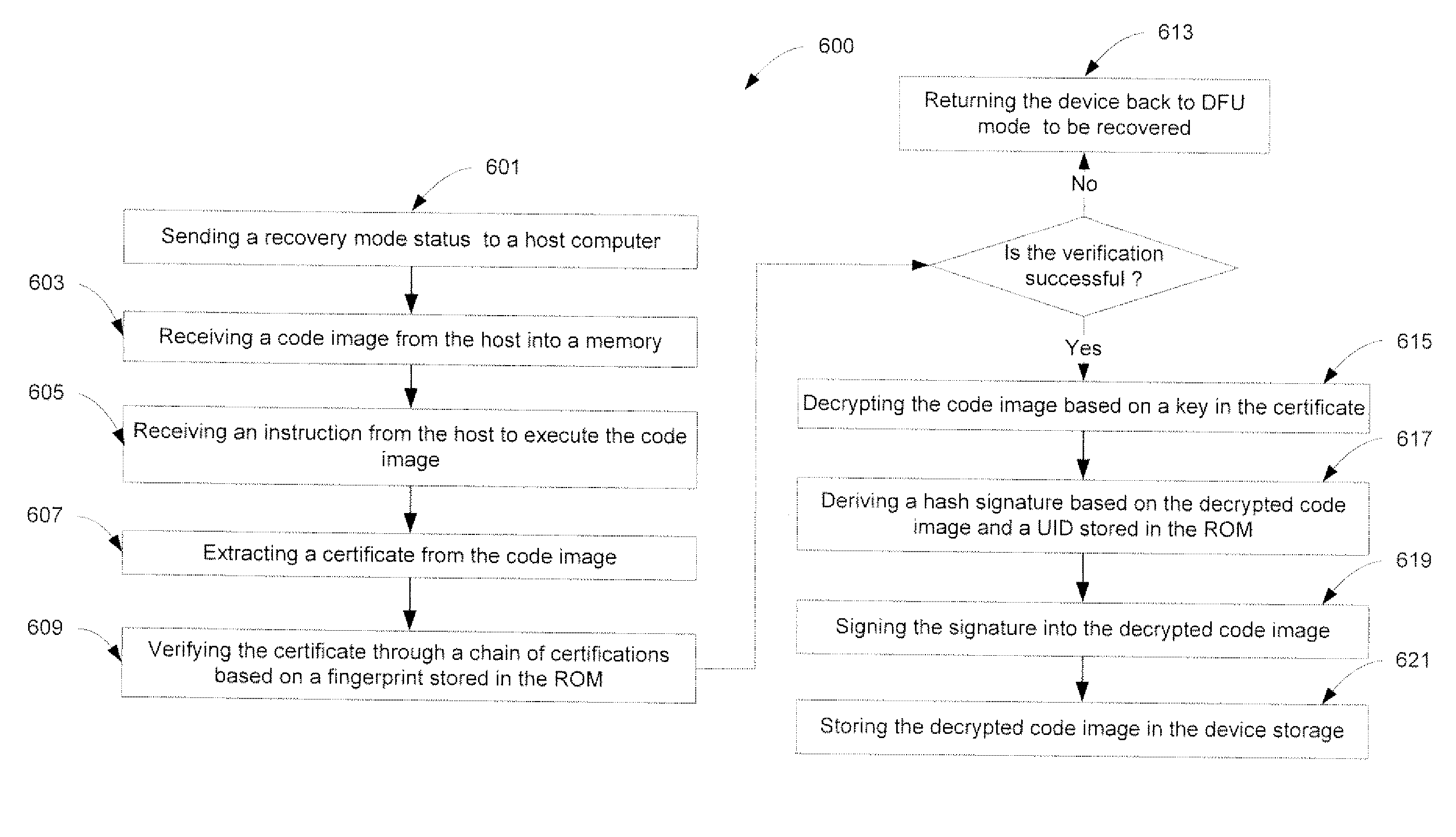
ActiveUS20080165952A1Multiple keys/algorithms usageDigital computer detailsRead-only memoryOperating environment
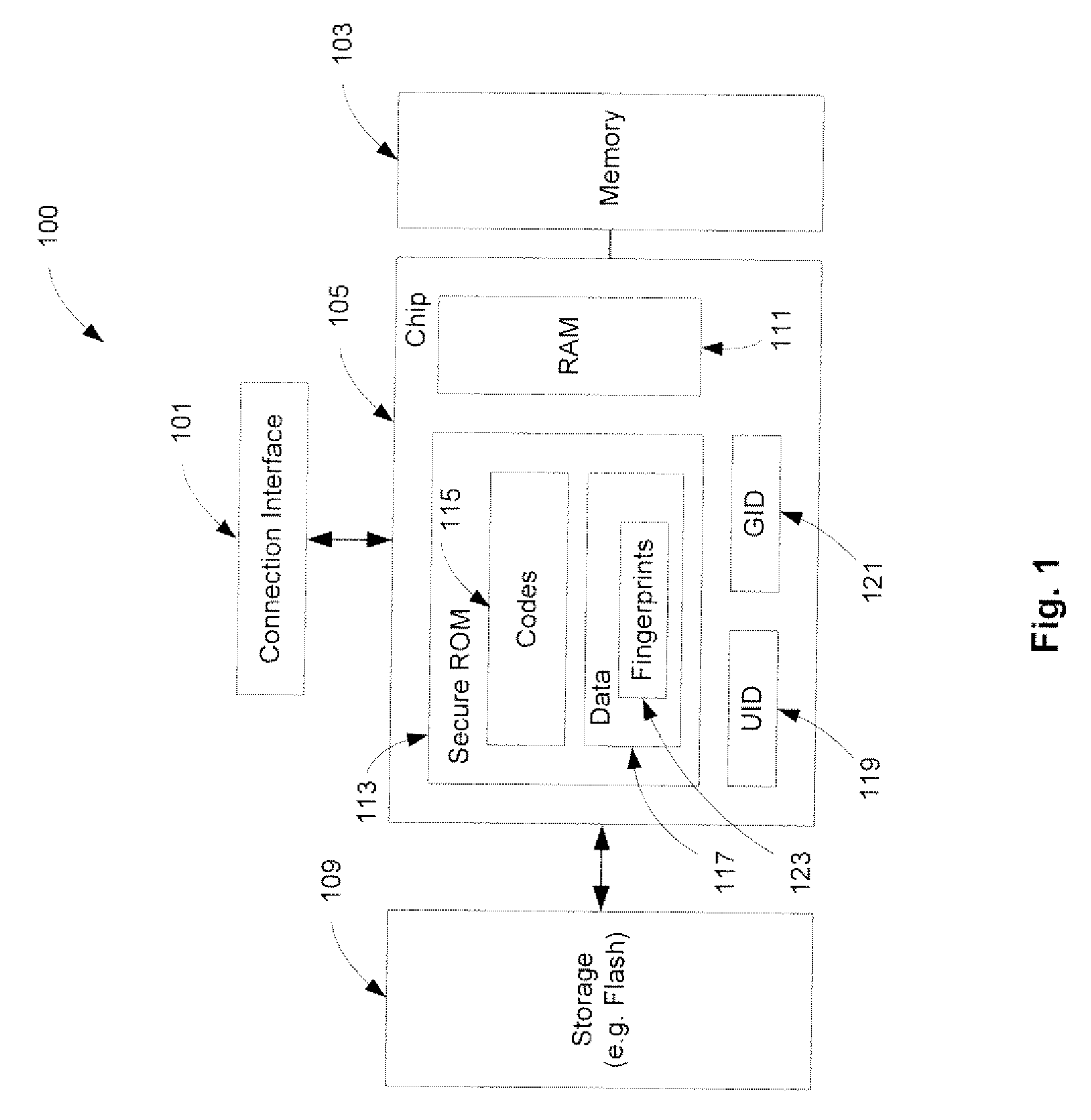
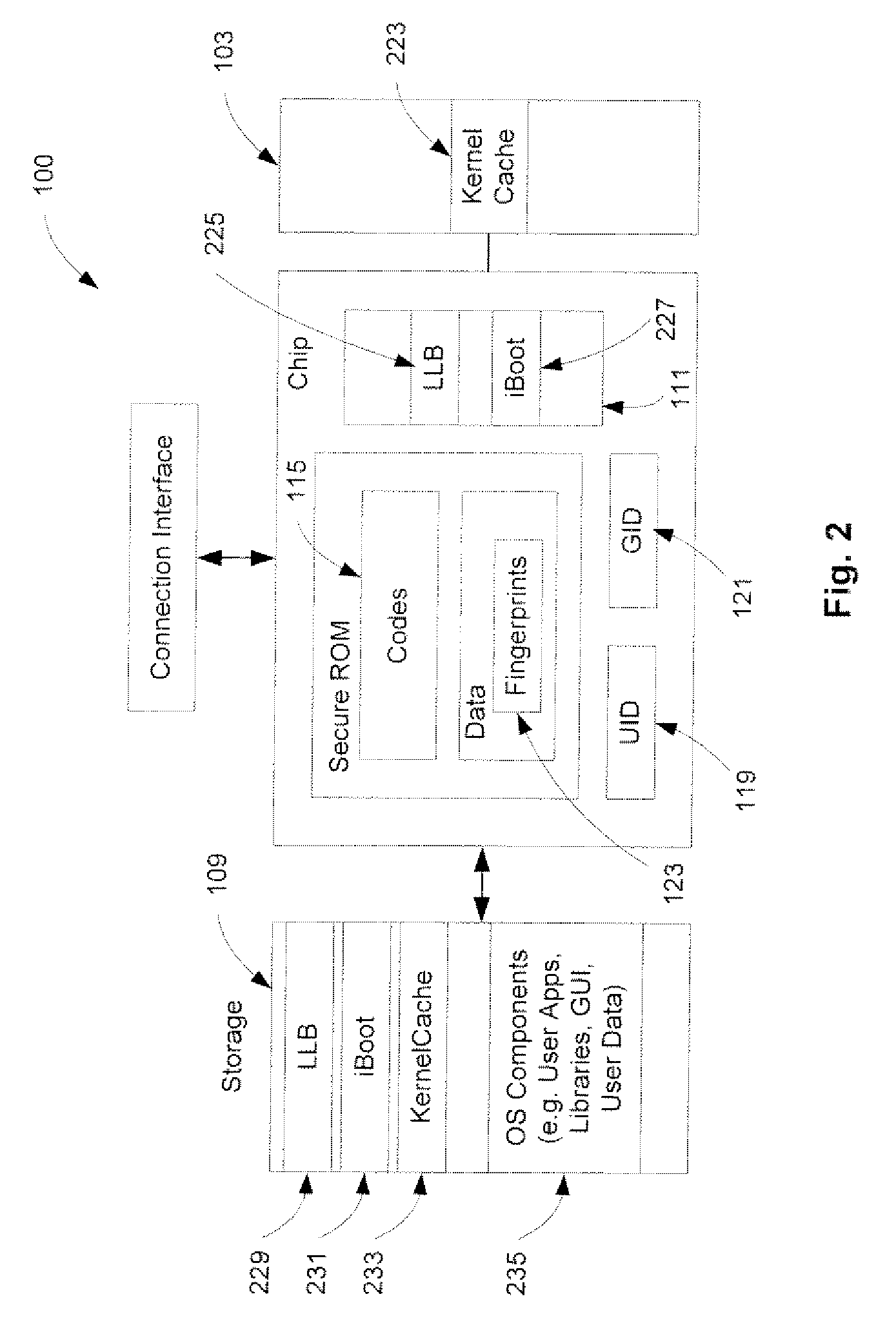
A method and an apparatus for executing codes embedded inside a device to verify a code image loaded in a memory of the device are described. A code image may be executed after being verified as a trusted code image. The embedded codes may be stored in a secure ROM (read only memory) chip of the device. In one embodiment, the verification of the code image is based on a key stored within the secure ROM chip. The key may be unique to each device. Access to the key may be controlled by the associated secure ROM chip. The device may complete establishing an operating environment subsequent to executing the verified code image.
Owner:APPLE INC
Methods and systems for running multiple operating systems in a single mobile device
ActiveUS20060010314A1Reduce memory usageError detection/correctionDigital computer detailsOperational systemEngineering
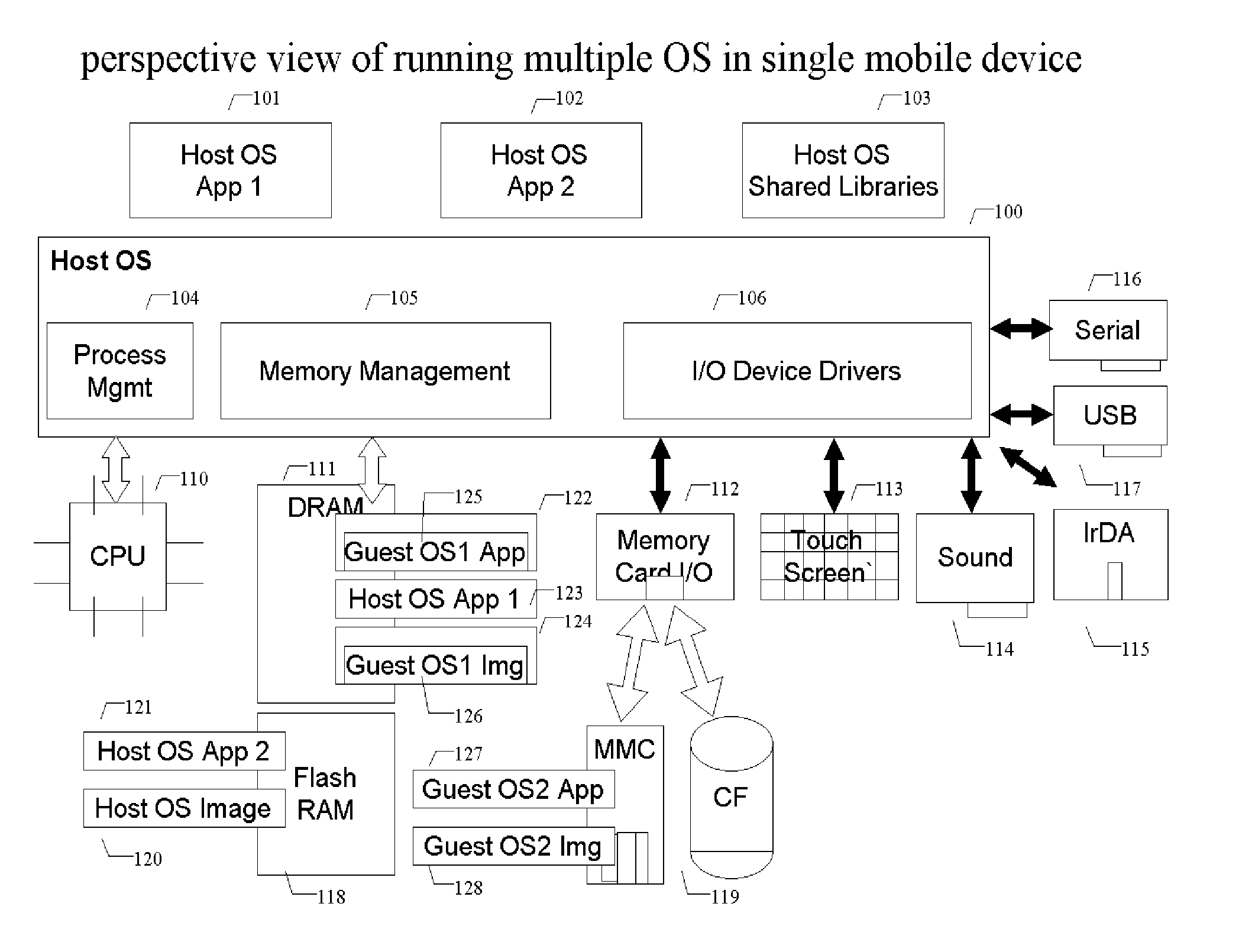
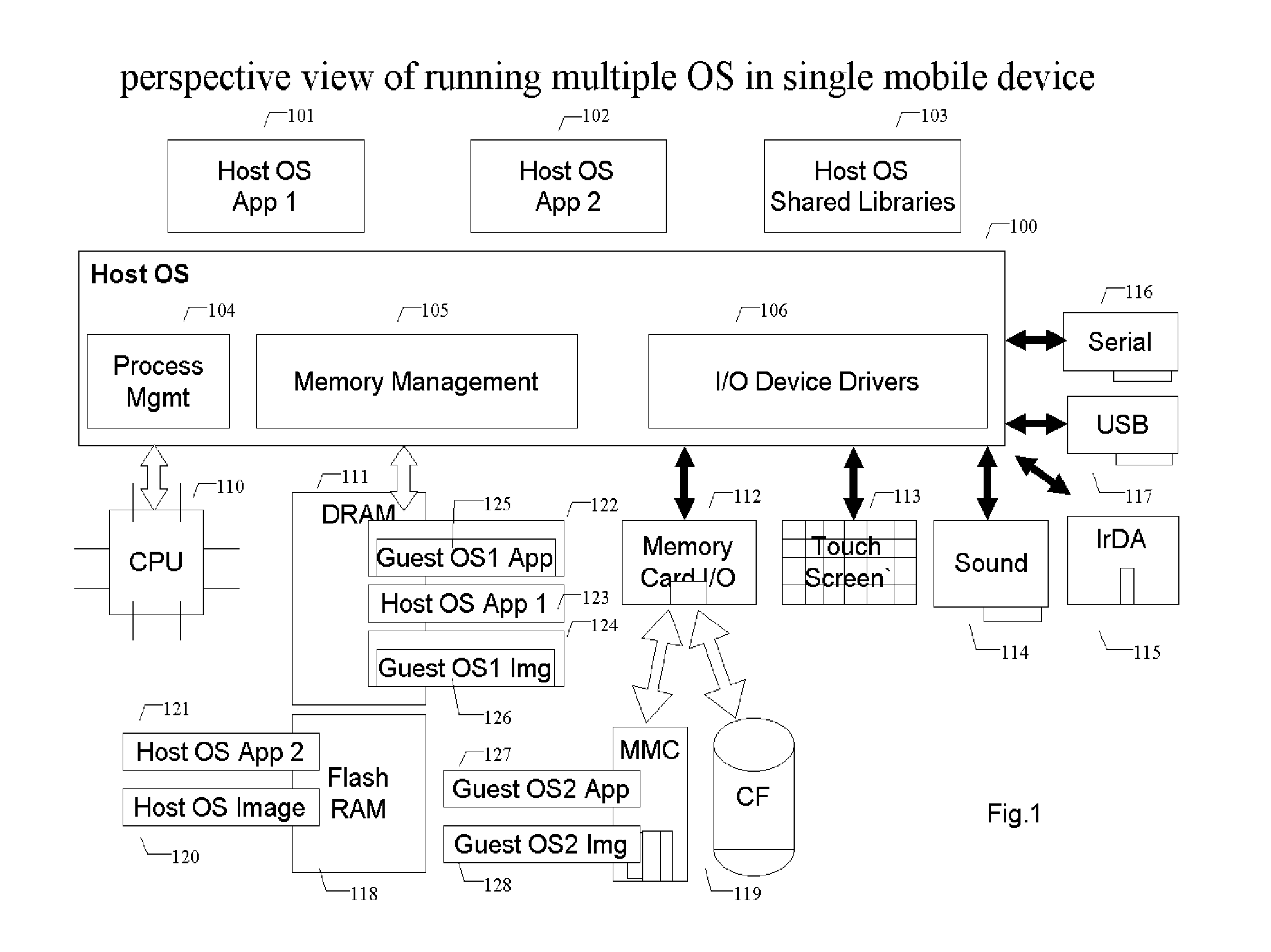
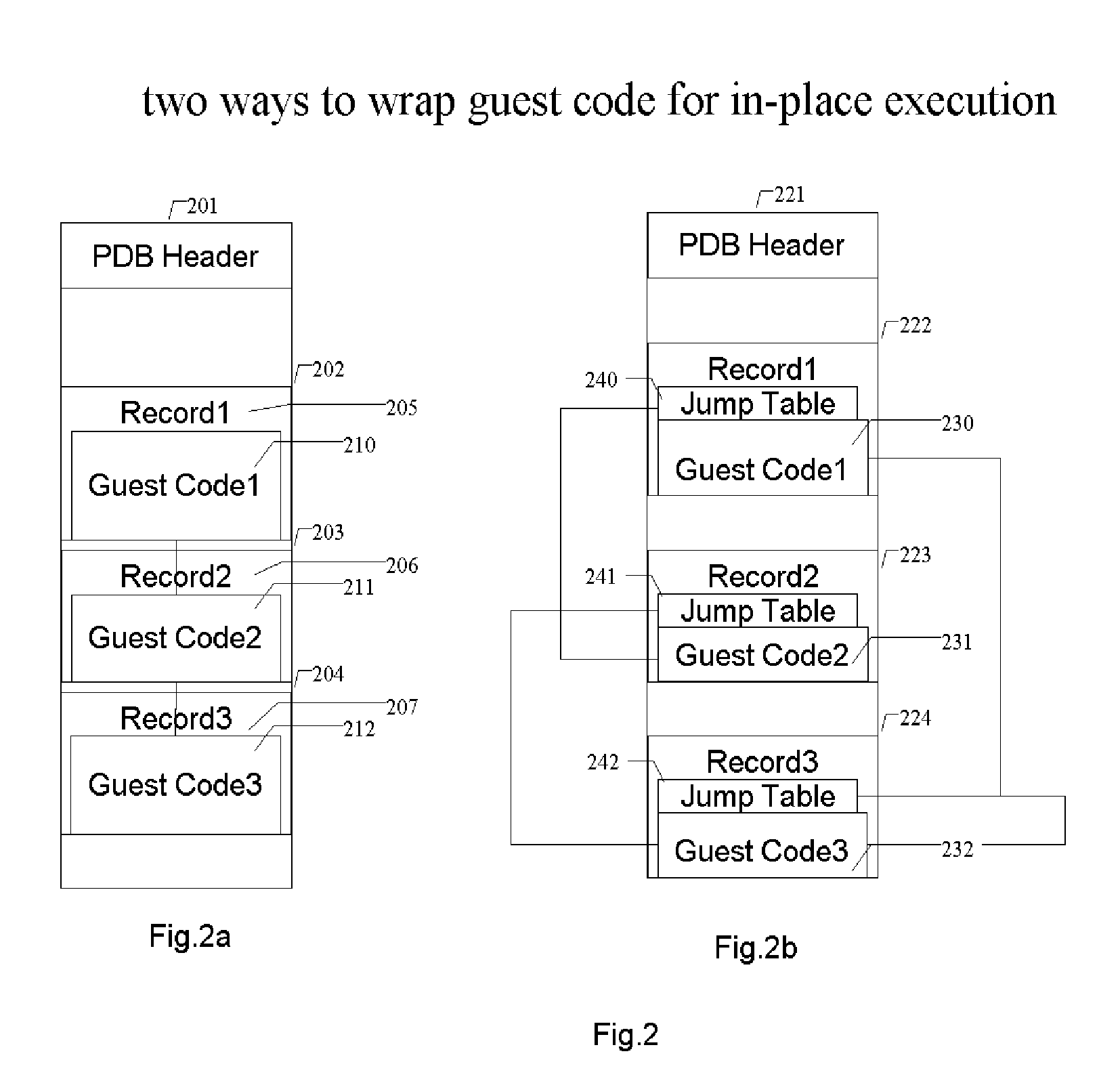
Methods and systems for running multiple operating systems in a single embedded or mobile device (include PDA, cellular phone and other devices) are disclosed. The invention allows a mobile device that normally can only run a single operating system to run another operating system while preserving the state and data of the original operating system. Guest OS is packaged into special format recognizable by the host OS that still can be executed in place by the system. The Methods include: •Change the memory protection bits for the original OS; •Fake a reduced physical memory space for guest OS; •Use special memory device driver to claim memories of host OS; •Backup whole image of the current OS and data to external memory card.
Owner:INTELLECTUAL VENTURES HOLDING 81 LLC
Reconfigurable computer architecture using programmable logic devices
A method and system for computing using reconfigurable computer architecture utilizing logic devices is disclosed. The computing may be accomplished by configuring a first programmable logic unit as a system controller. The system controller directs the implementation of an algorithm in a second one of the programmable logic units concurrently with reconfirguring a third one of the programmable logic units. In another aspect, the computing system may include a pair of independent, bi-directional busses each of which is arranged to electrically interconnect the system controller and the plurality of programmable logic devices. With this arrangement, a first bus may be used to reconfigure a selected one of the programmable logic devices as directed by the system controller while the second bus is used by an operational one of the programmable logic devices.
Owner:ALTERA CORP
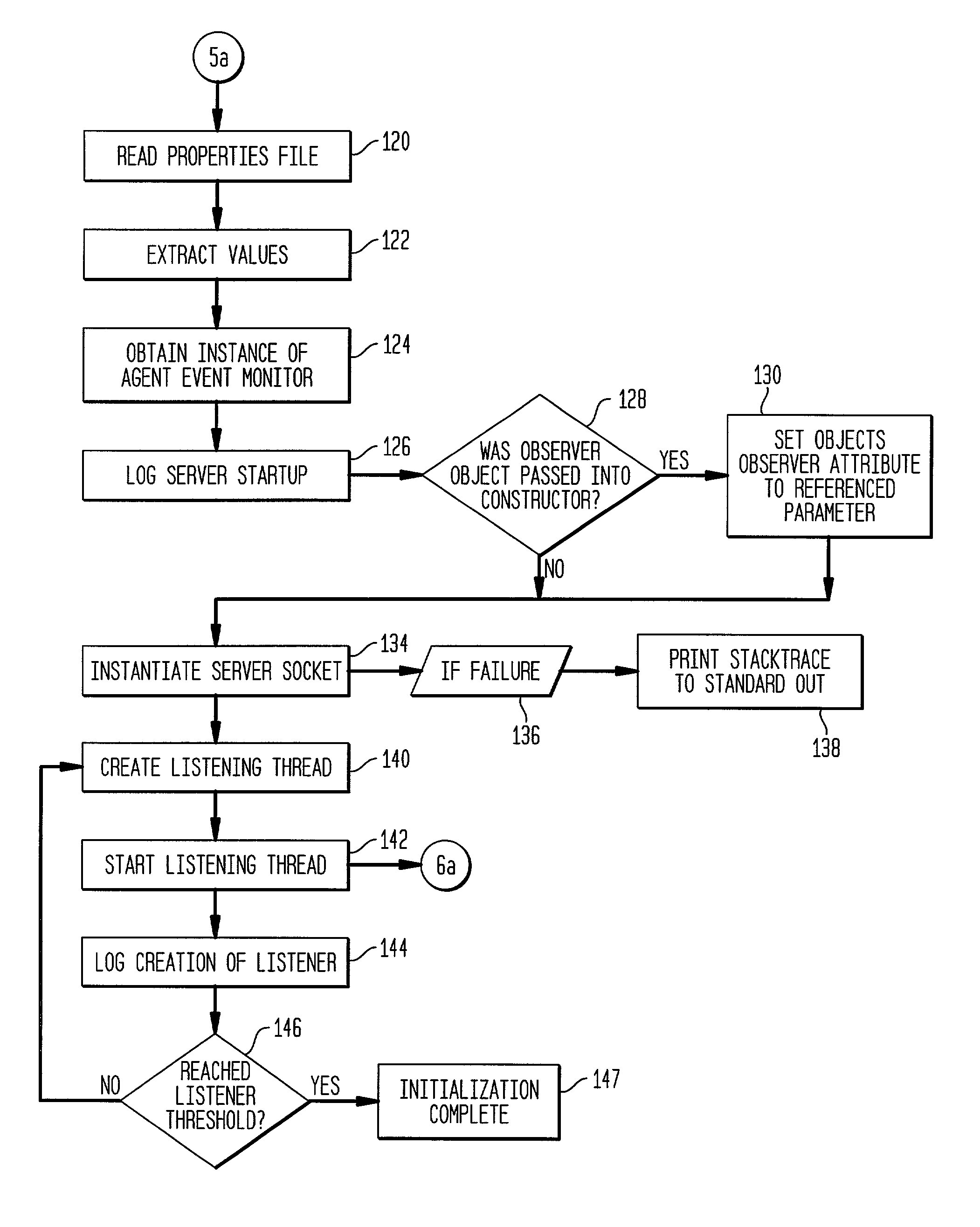
Agent framework for mobile devices
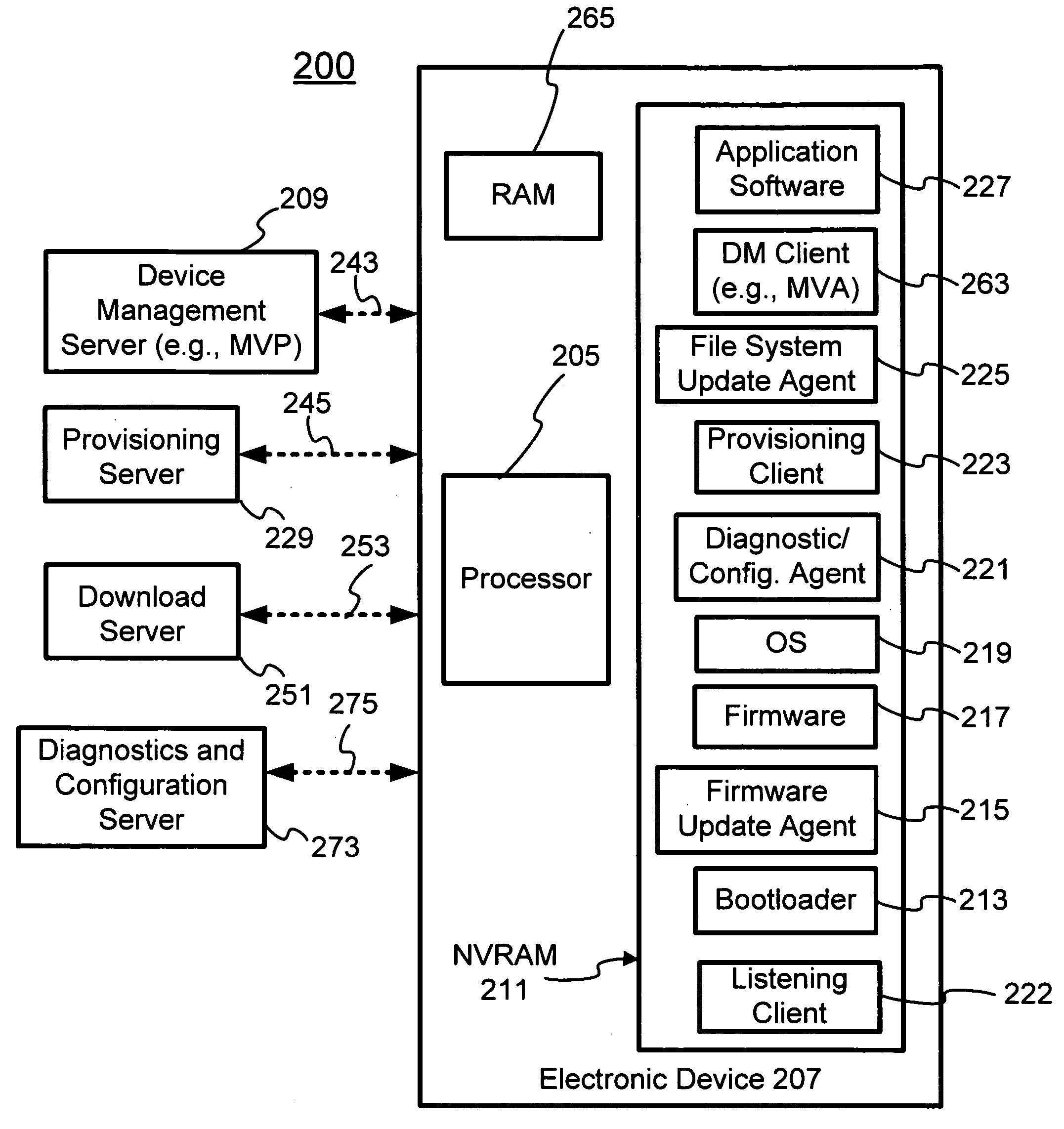
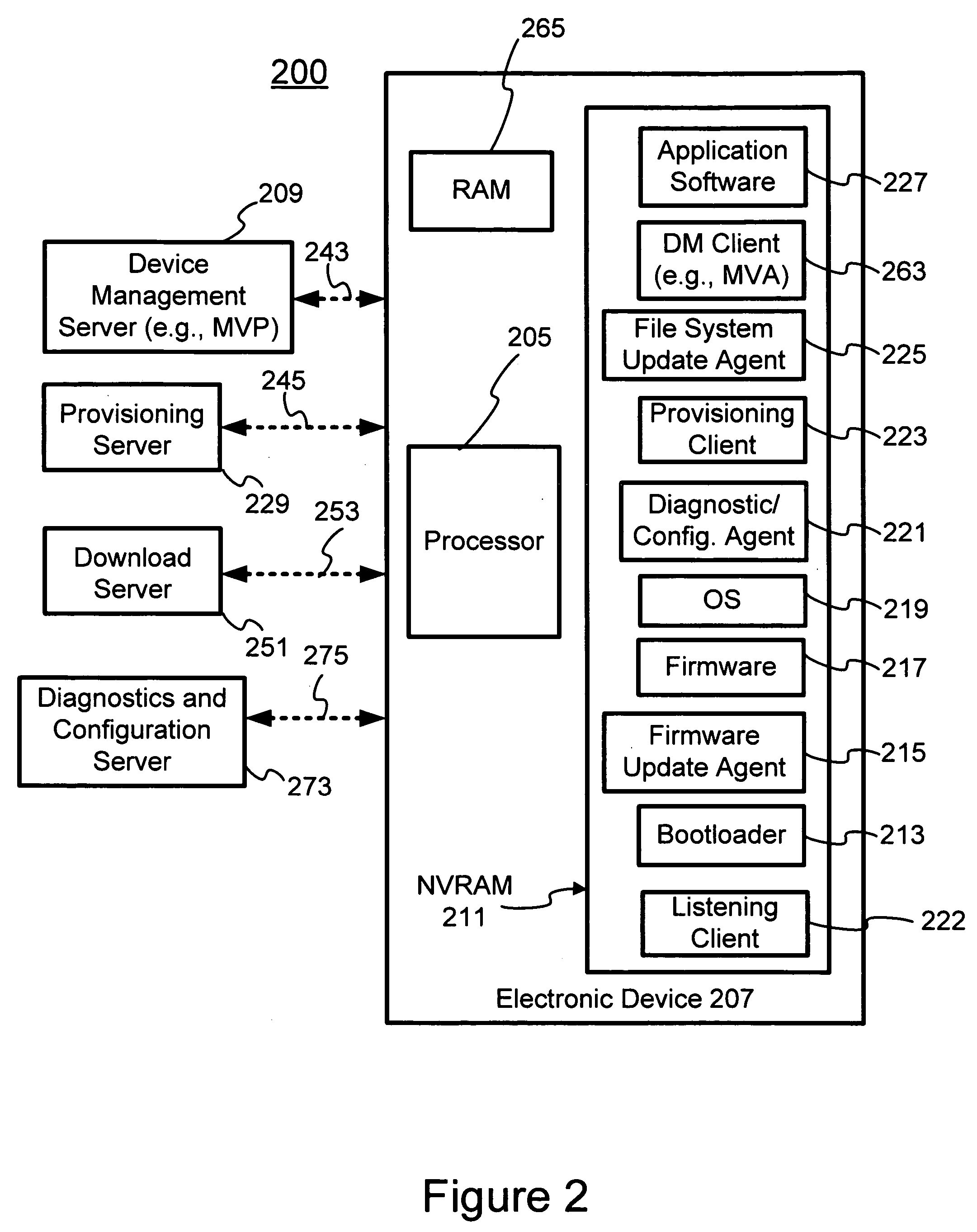
Herein described is an agent support framework used in a mobile communication device. The agent support framework provides a set of commonly used features that may be used by various client applications. The client applications may comprise one or more diagnostic / configuration agents that are used in monitoring device status, performing problem diagnosis, and obtaining configuration information from the mobile electronic device. Should a firmware or file system update be required, one or more update agents may be used to download one or more data files. The set of commonly used features provides shared resources to the various client applications. New client applications may be easily designed based on the set of commonly used features. The integration of new agents and / or clients to the agent support framework is facilitated by the ability of the agent support framework to provide shared resources when necessary.
Owner:HEWLETT PACKARD DEV CO LP
Method and apparatus for adaptive CPU power management
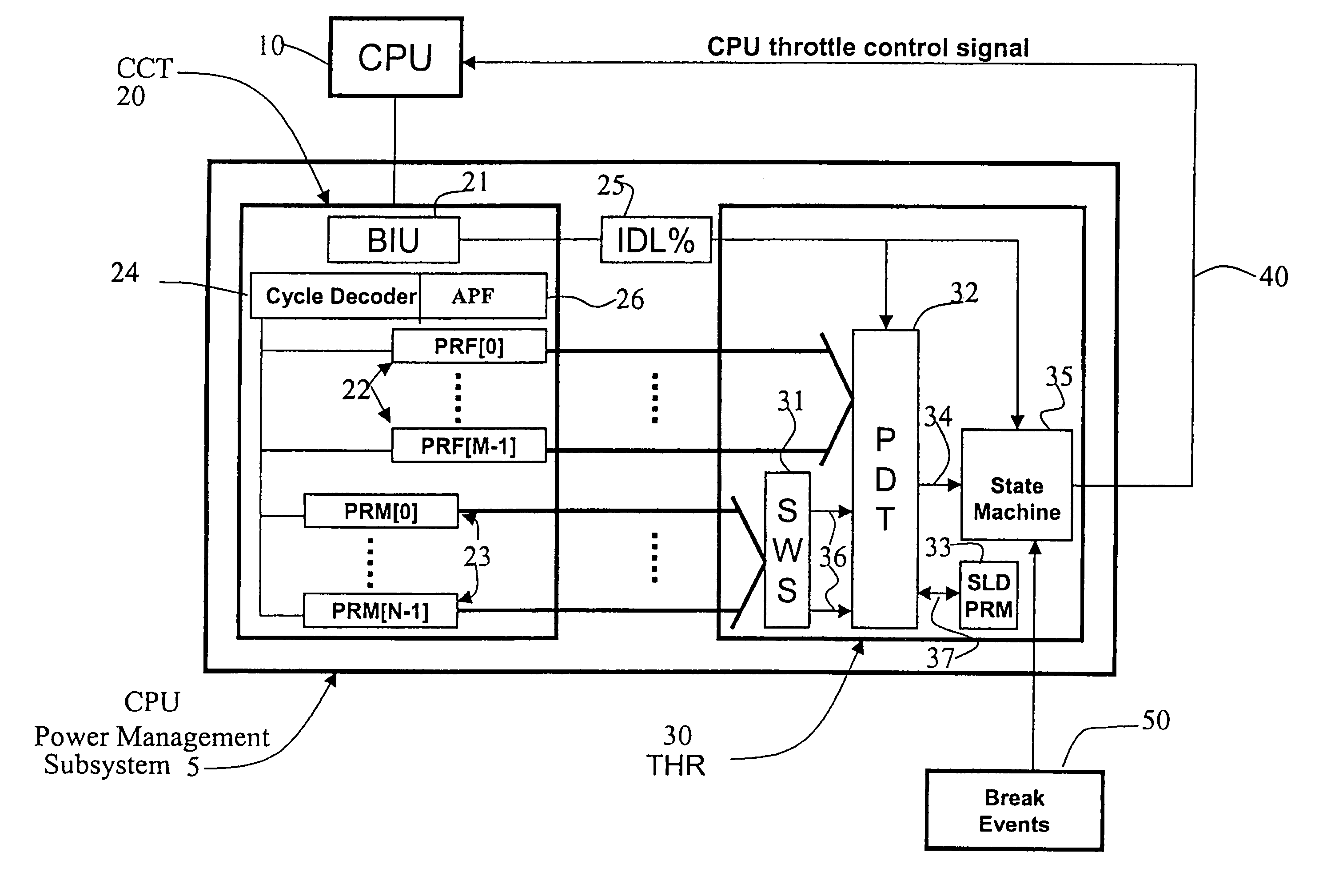
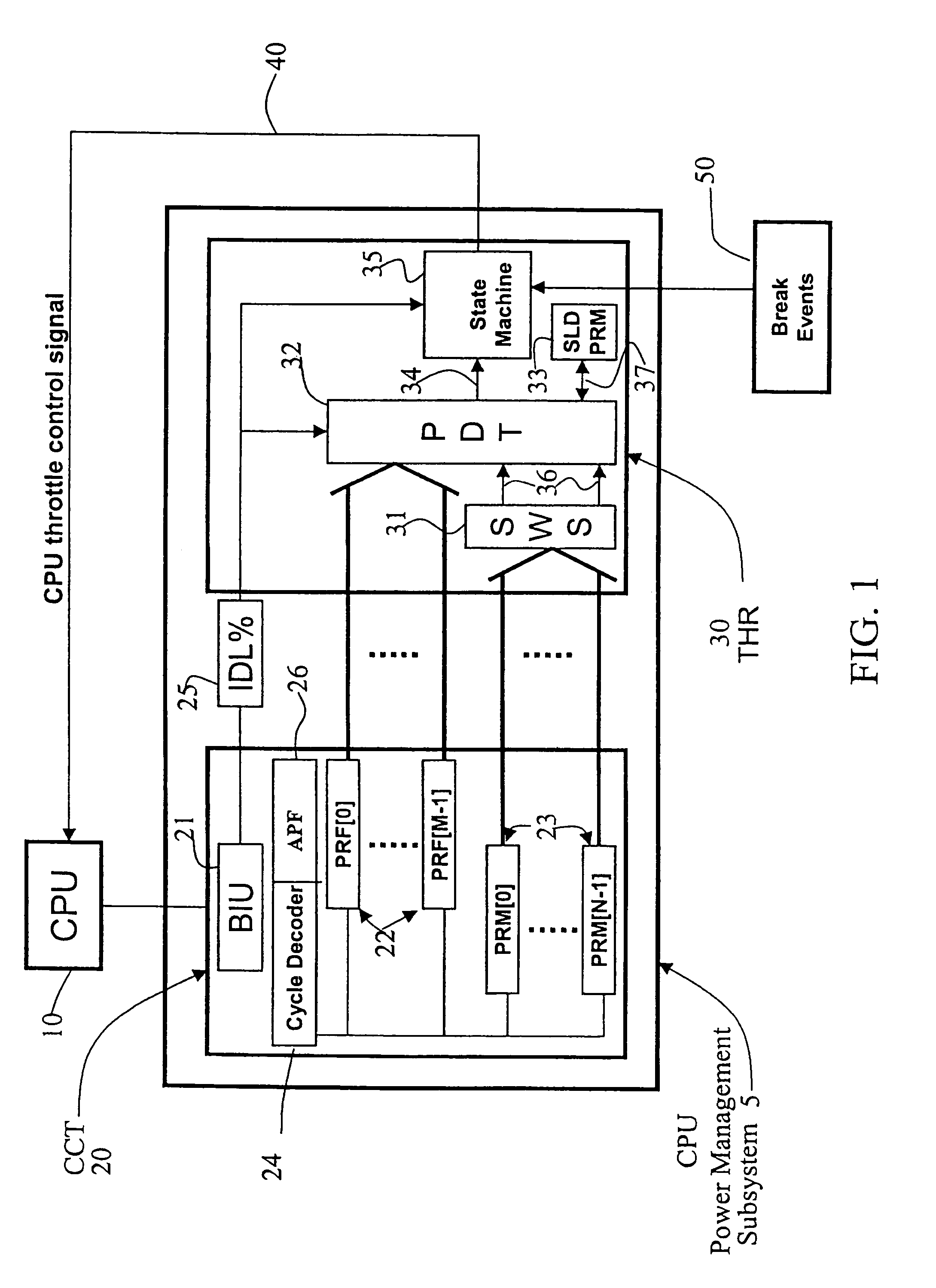
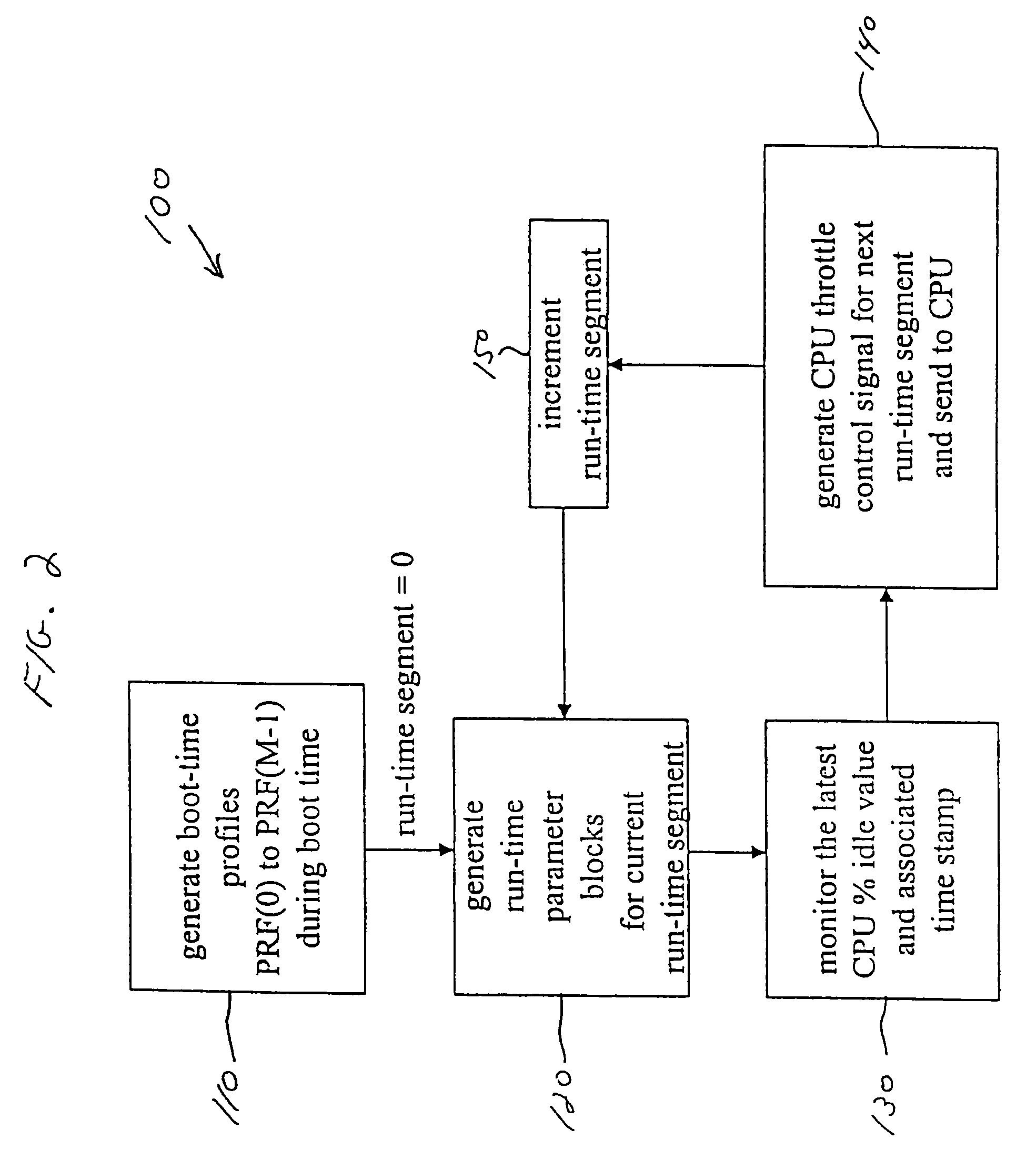
A method and apparatus are disclosed for performing adaptive run-time power management in a system employing a CPU and an operating system. A CPU cycle tracker (CCT) module monitors critical CPU signals and generates CPU performance data based on the critical CPU signals. An adaptive CPU throttler (THR) module uses the CPU performance data, along with a CPU percent idle value fed back from the operating system, to generate a CPU throttle control signal during predefined run-time segments of the CPU run time. The CPU throttle control signal links back to the CPU and adaptively adjusts CPU throttling and, therefore, power usage of the CPU during each of the run-time segments.
Owner:AVAGO TECH INT SALES PTE LTD
Task scheduling apparatus in distributed processing system
InactiveUS20050278520A1Raise the processing temperatureReduce heatEnergy efficient ICTProgram initiation/switchingProcessing elementHandling system
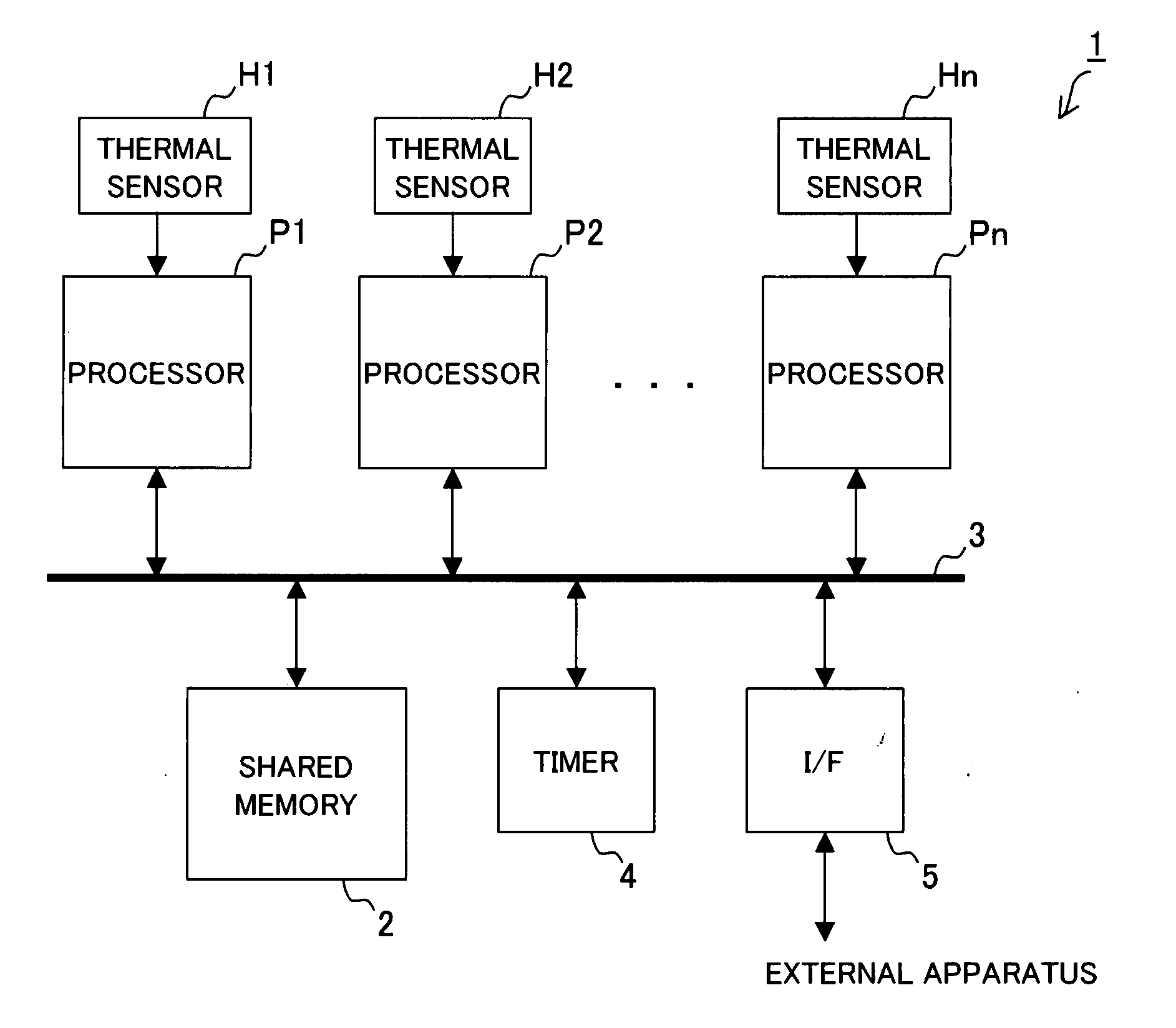
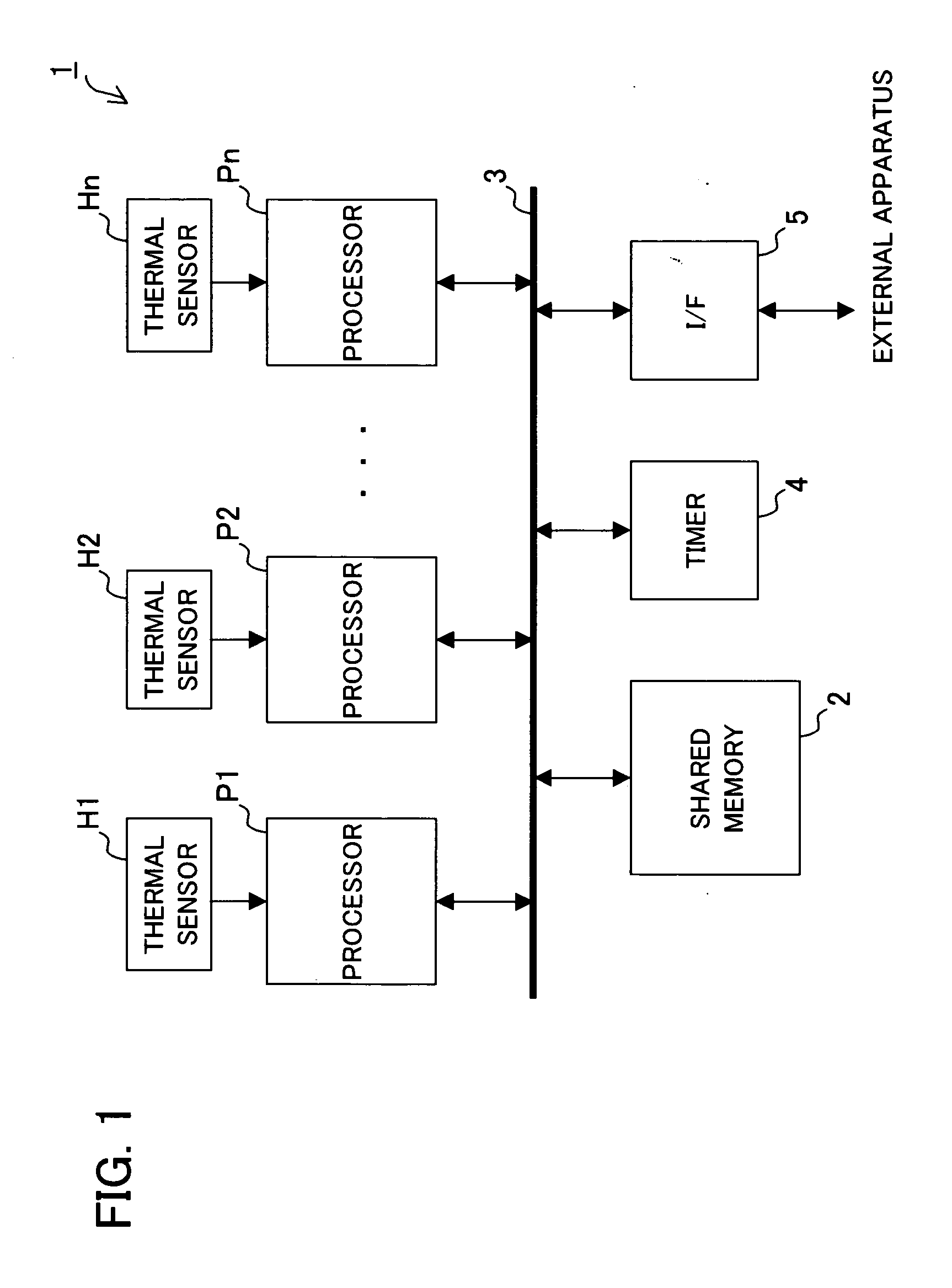
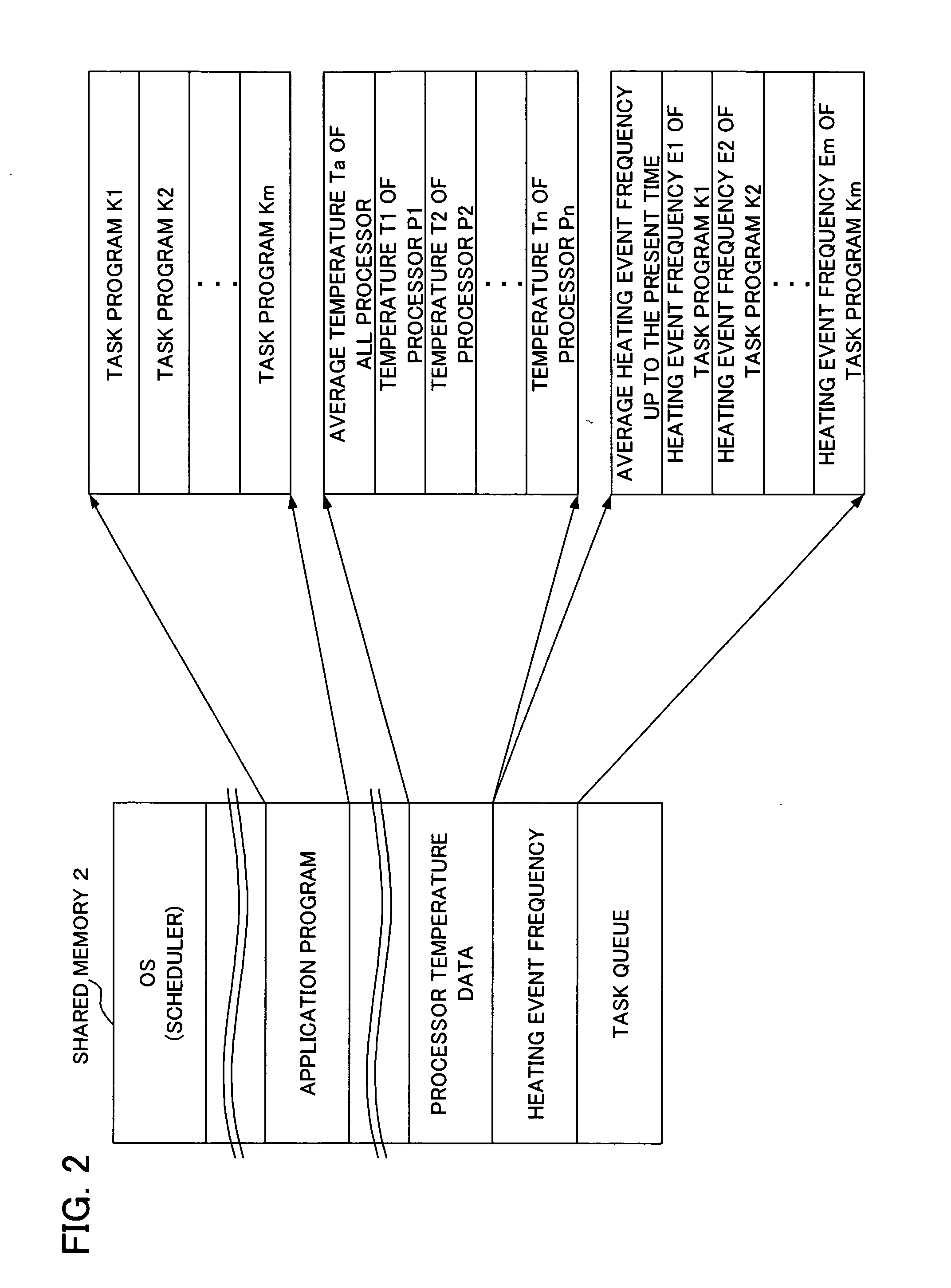
A task scheduling apparatus of a distributed processing system having a plurality of processing units for processing a plurality of distributed tasks is provided. As a first task scheduling method, the task scheduling apparatus allocates a task to a processing unit having the lowest temperature. As a second task scheduling method, the task scheduling apparatus selects a task based on both temperature of each processing unit and characteristic values of tasks related to degree of temperature rise or consumption power increase caused by execution, and allocates the selected task to the object processing unit. For example, as the second task scheduling method, a task producing a large degree of temperature rise (for example, a task having a number of instructions to be processed per unit time) is allocated to a processing unit having a low temperature. With such a scheduling method, uniform temperature of each processing unit can be obtained.
Owner:FUJITSU LTD
Disk drive having a protected partition configured to load an operating system for performing a user-selected function
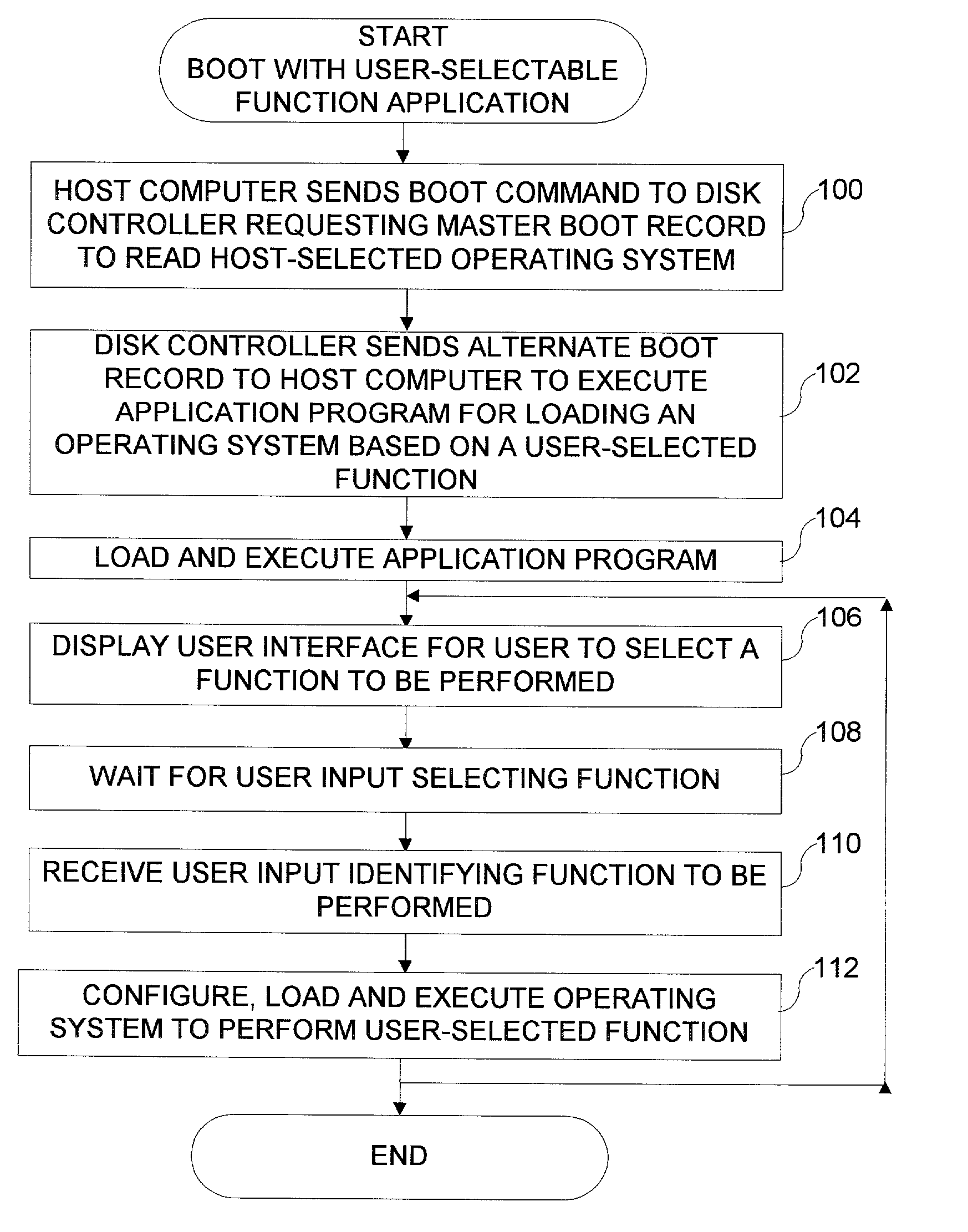
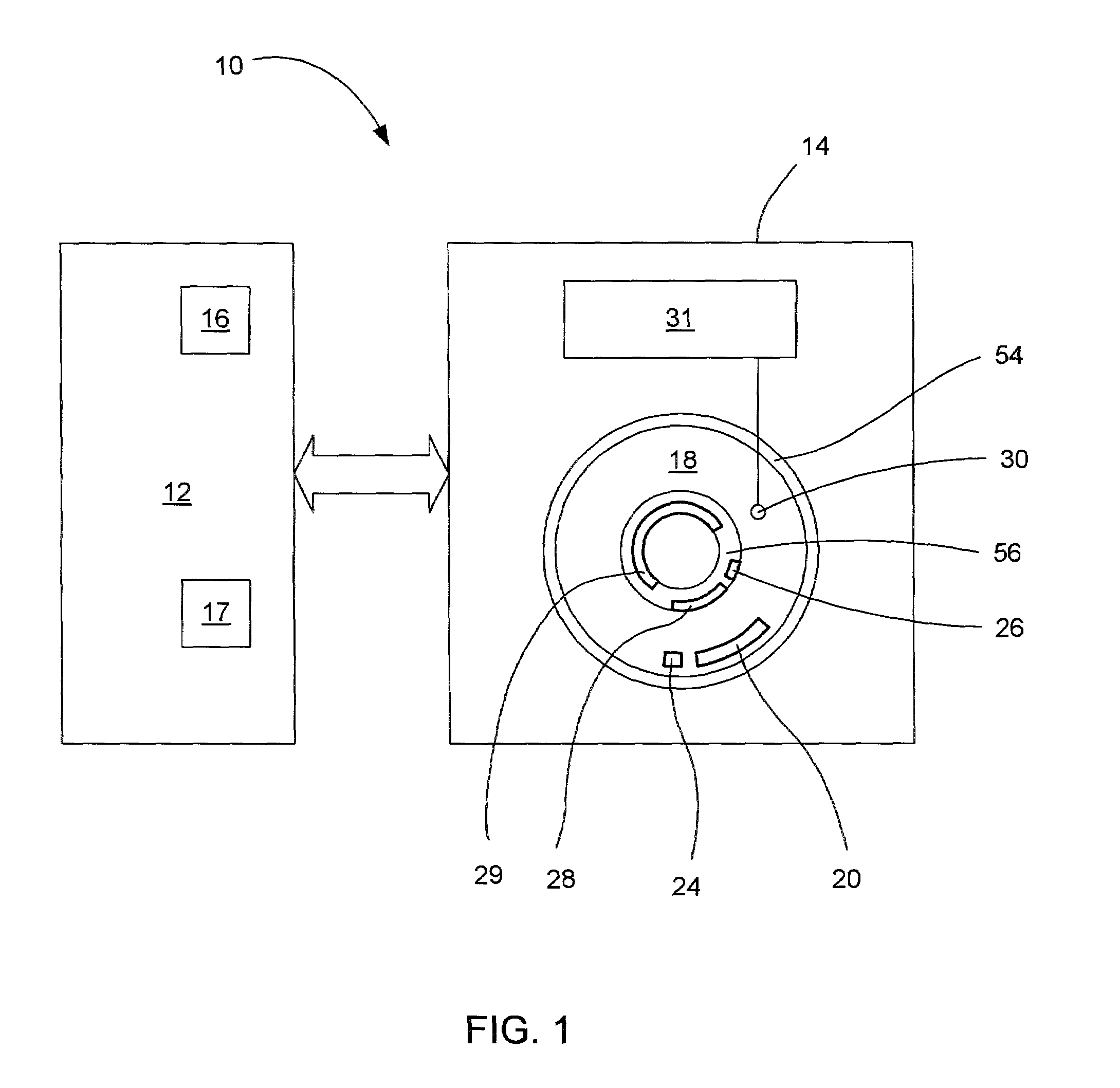
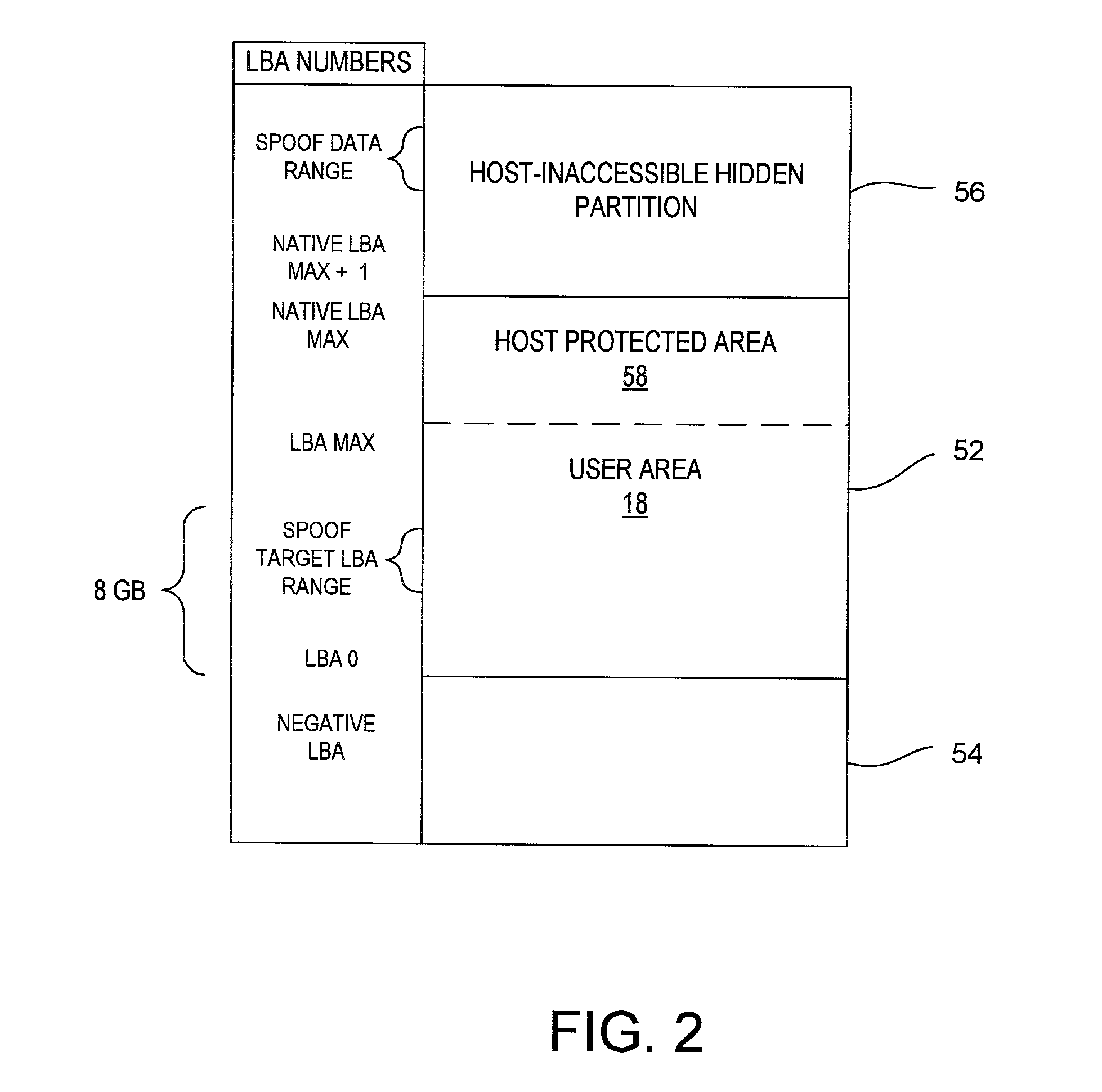
A system for configuring, loading and executing an operating system for performing a user-selected function is disclosed. The system includes a disk drive including: a host-accessible user partition; a host-inaccessible hidden partition independent of the host-accessible user partition; and a disk controller. The user partition includes: a user partition address range; a host-selected operating system; and a host-selected master boot record. The host-inaccessible hidden partition includes: a hidden partition address range outside the user partition address range; an application program for allowing a user to select a function to perform and configuring, loading and executing an operating system to perform the selected function; and a drive-selected boot record for loading and executing the application program that allows the user to select a function and configures, loads and executes an operating system for performing the function.
Owner:WESTERN DIGITAL TECH INC
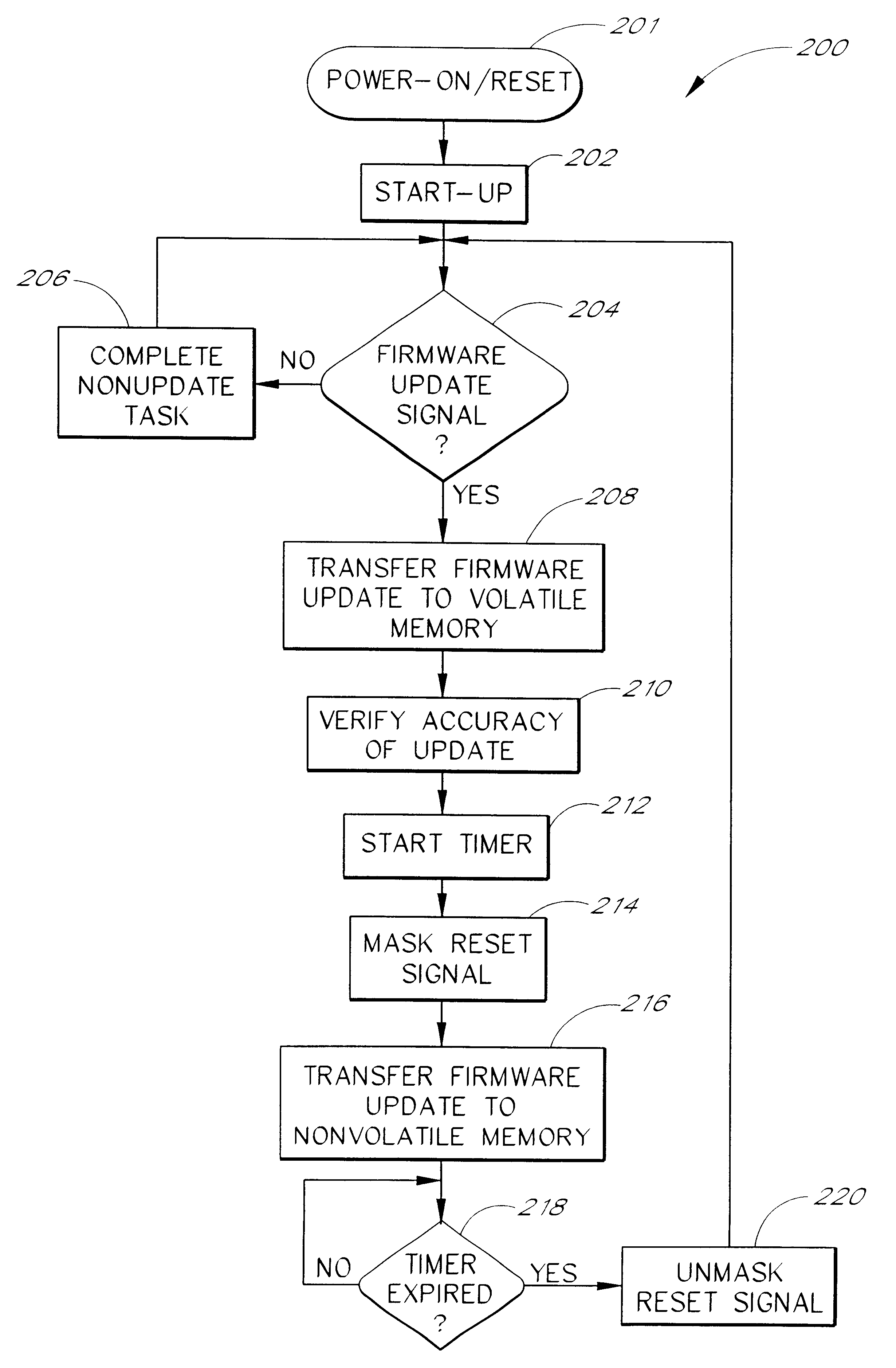
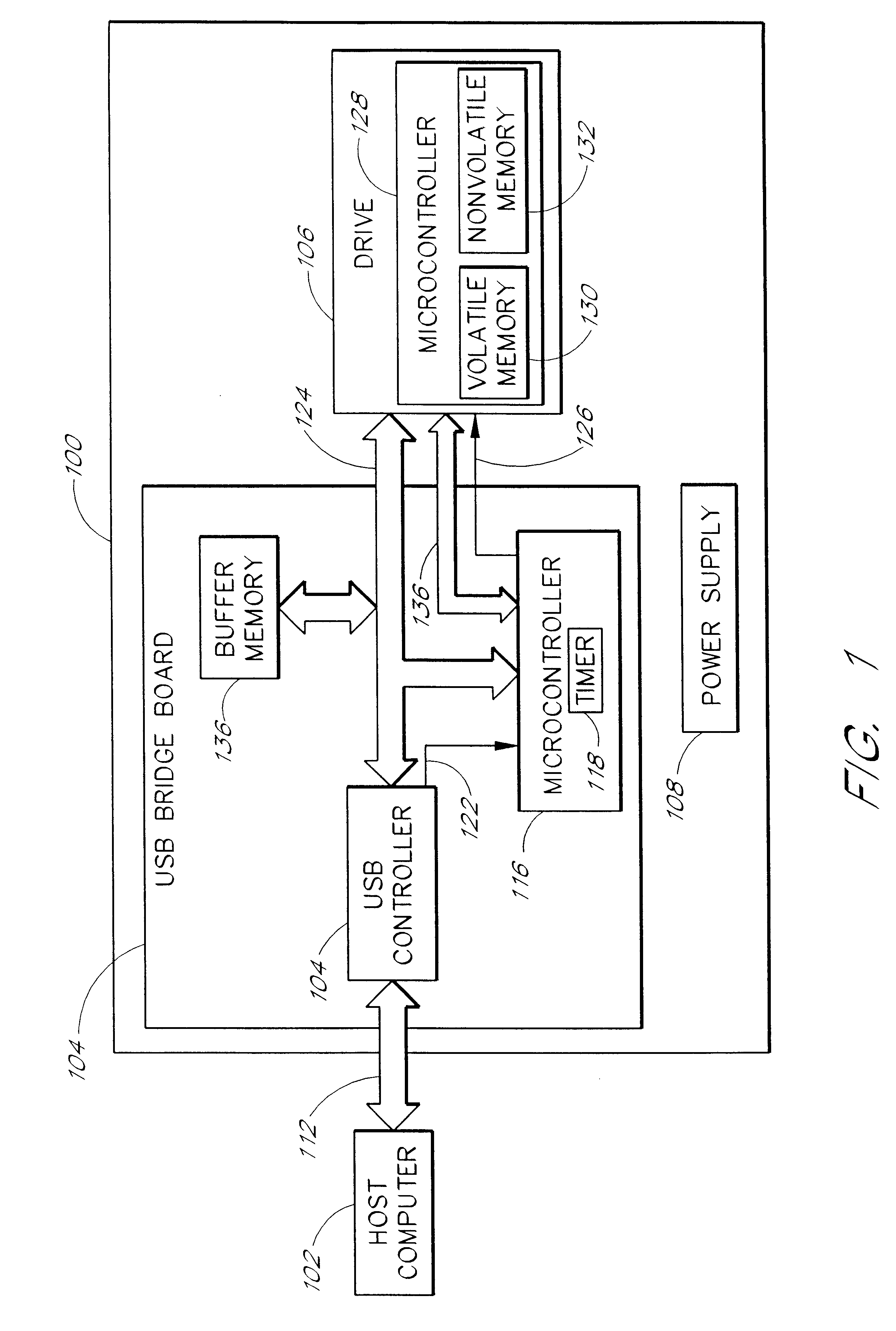
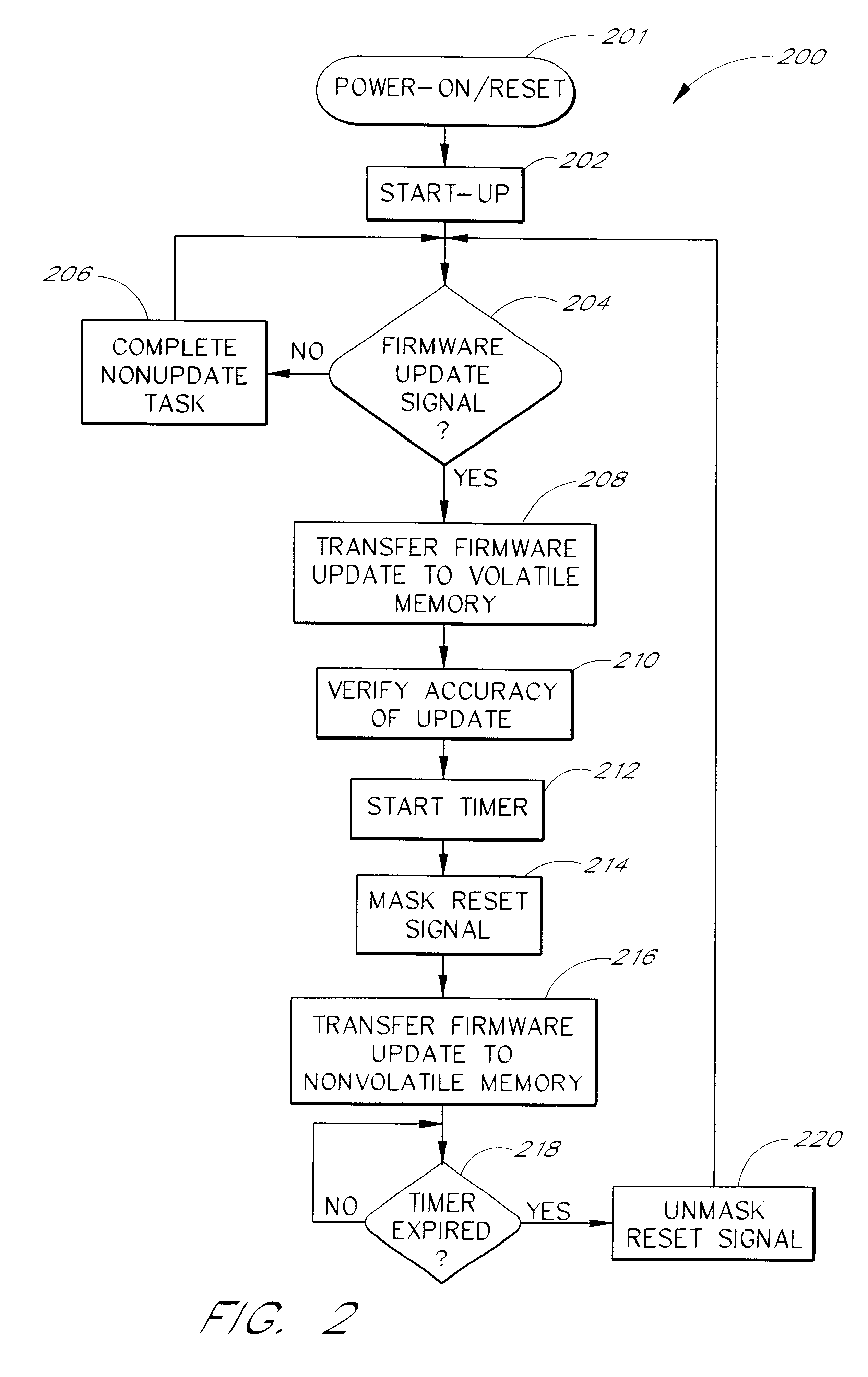
Method and system for performing a peripheral firmware update
The present invention provides systems and methods for performing a firmware update. In one embodiment, a peripheral reset signal is masked in response to a peripheral firmware update command. The firmware update is loaded into a peripheral's nonvolatile memory while the reset signal is masked.
Owner:MITSUMI ELECTRIC CO LTD
Inter-partition message passing method, system and program product for managing workload in a partitioned processing environment
InactiveUS20020129085A1Easy to moveDirect to transferResource allocationMultiple digital computer combinationsOperational systemResource assignment
A partitioned processing system capable of supporting diverse operating system partitions is disclosed wherein throughput information is passed from a partition to a partition resource manager. The throughput information is used to create resource balancing directives for the partitioned resource. The processing system includes at least a first partition and a second partition. A partition resource manager is provided for receiving information about throughput from the second partition and determining resource balancing directives. A communicator communicates the resource balancing directives from the partition manager to a kernel in the second partition which allocates resources to the second partition according to the resource balancing directives received from the partition manager.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com