Depth defense system for effectively responding to APT (Advanced Persistent Threat) attacks
A defense-in-depth, firewall technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problems of poor network sharing capability, loss of security, heavy burden on central nodes, etc., to reduce attack paths, improve service life, The effect of reducing equipment cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
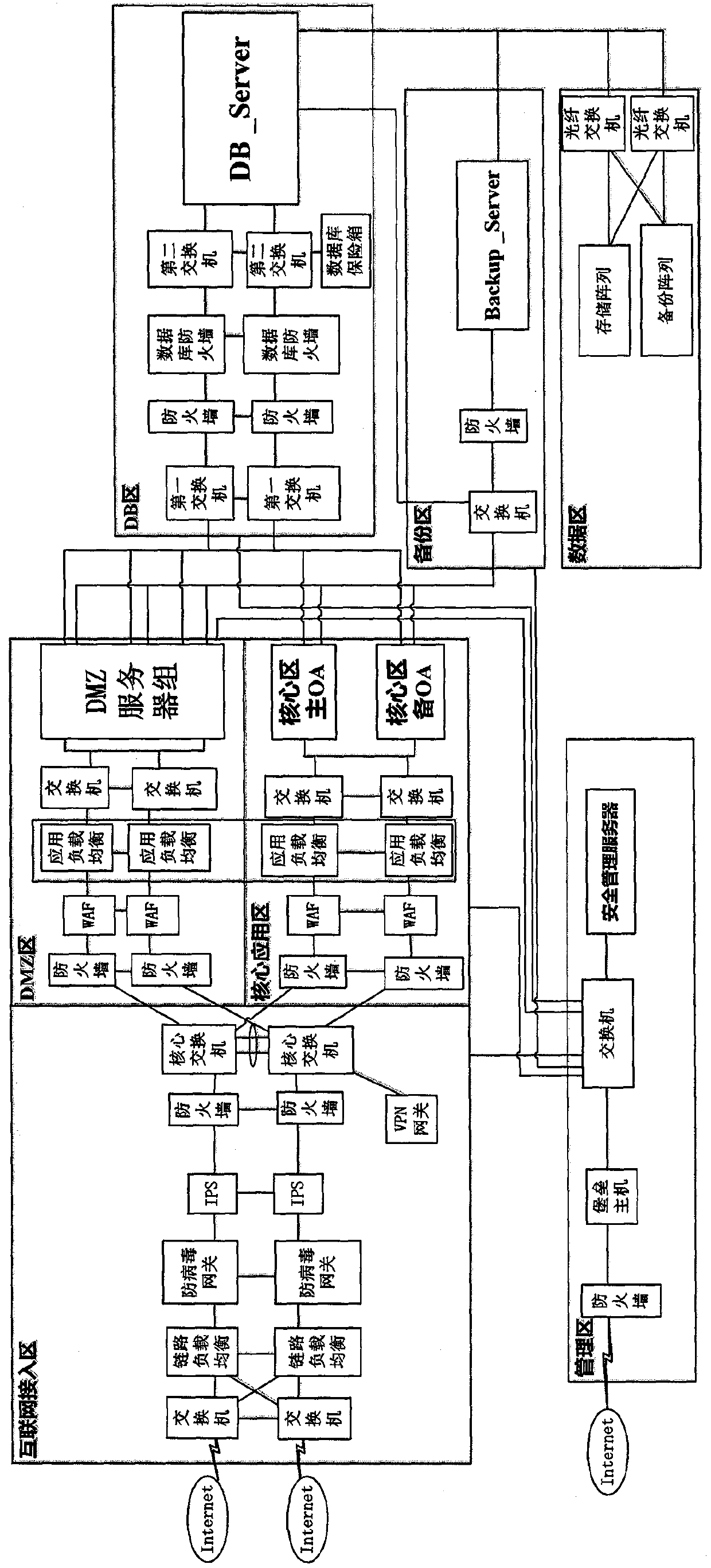
[0037] Such as figure 1 As shown, a defense-in-depth system that effectively responds to APT attacks includes Internet access area, DMZ area, core application area, DB area, data area, backup area, and management area;
[0038] The Internet access area includes two interconnected switches, two interconnected link load balancers, two interconnected antivirus gateways, two interconnected IPSs, two interconnected firewalls, and two interconnected Core switch, a VPN gateway; the link in the Internet access area is the active and standby link;
[0039] In the Internet access zone, each switch is connected to two link load balancers, and the two link load balancers are connected to two antivirus gateways in a one-to-one manner, and each link load balancer is connected to an antivirus gateway ; Two anti-virus gateways are connected one-to-one with two IPS, and each anti-virus gateway is connected to one IPS; two IPS are connected to two core switches one-to-one, and each IPS is conn...
Embodiment 2
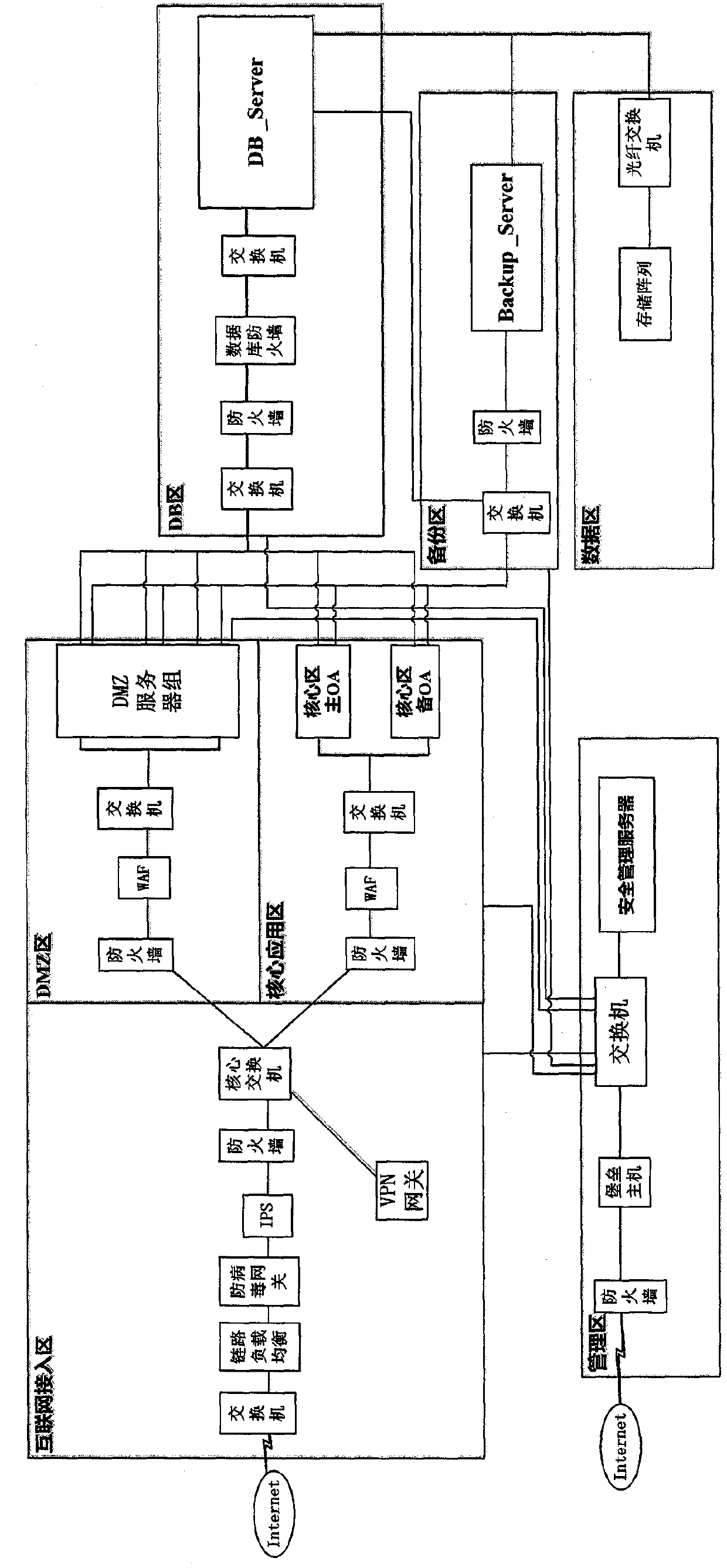
[0051] Such as figure 2 As shown, a defense-in-depth system that effectively responds to APT attacks includes the Internet access area, DMZ area, core application area, DB area, management area, backup area, and data area.
[0052] The Internet access area includes switches, link load balancing, antivirus gateways, IPS, firewalls, core switches, and VPN gateways connected in sequence.
[0053] The DMZ area includes firewalls, WAFs, switches, and DMZ server groups connected in sequence.
[0054] The core application area includes firewalls, WAFs, switches, the main OA in the core area connected in sequence, and the standby OA in the core area connected to the switch.
[0055] Both the firewall in the DMZ area and the firewall in the core application area are connected to the core switch in the Internet access area.
[0056] The DB area includes switches, firewalls, database firewalls, switches, and DB_Server connected in sequence. The switch in the DB area is connected to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com