Behavior-detection-based network traffic identification method and device
A network traffic and behavior technology, applied in the field of network security, can solve problems such as unsatisfactory analysis results, large amount of session uploaded data, limited session feature information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
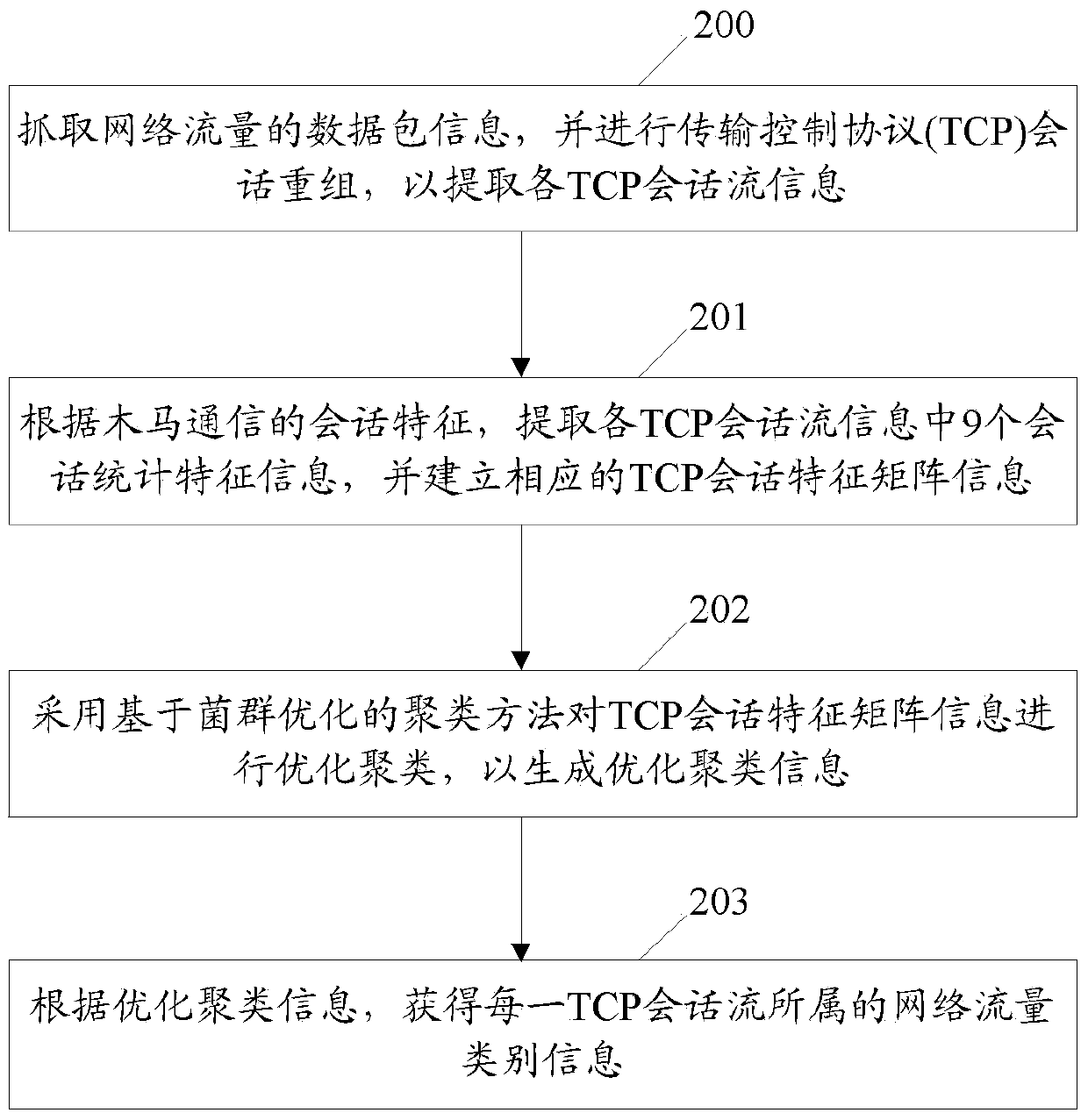
[0046] figure 2 It is a flowchart of an embodiment of realizing network traffic identification based on behavior detection in the present invention, such as figure 2 shown, including:
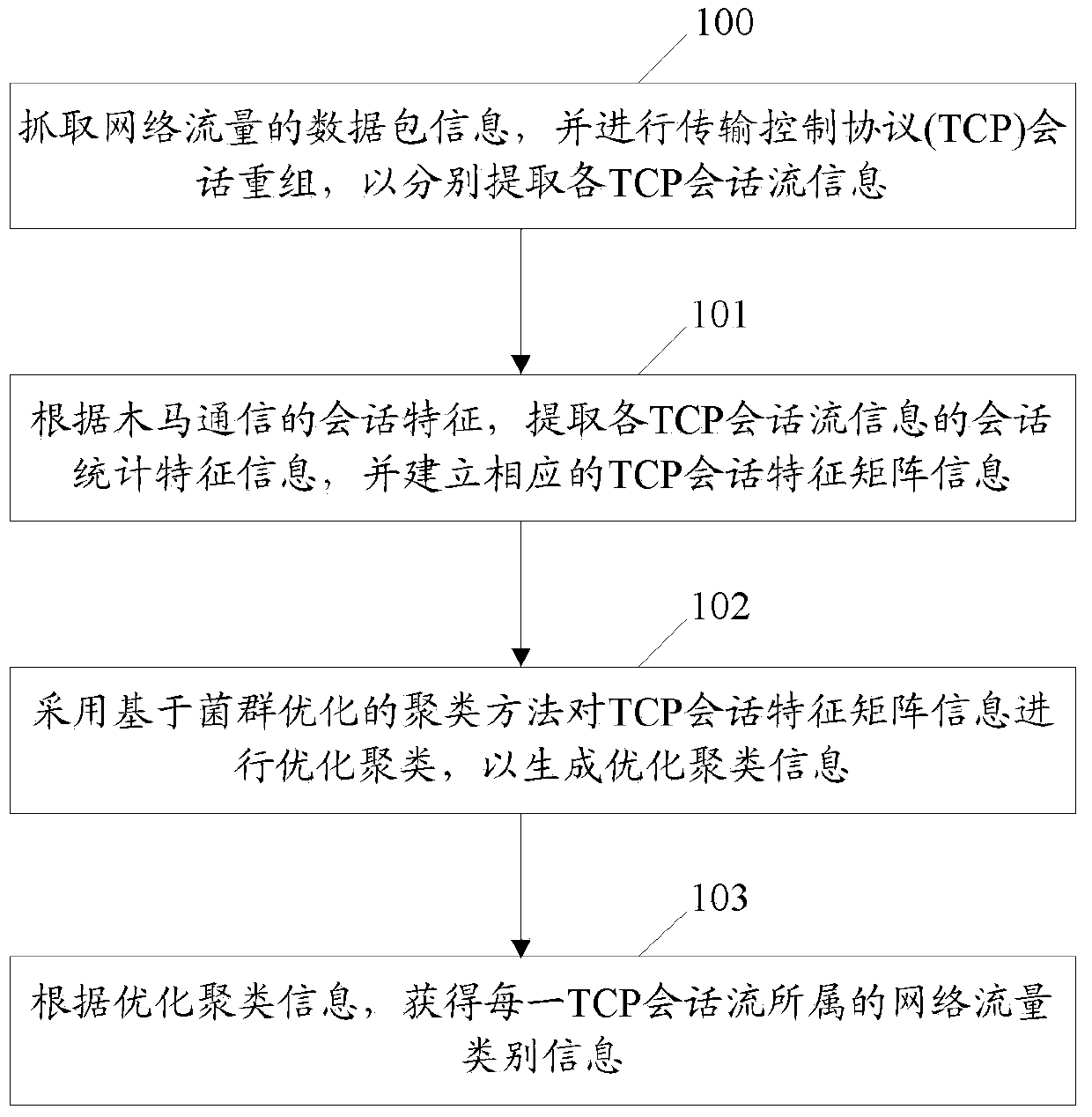
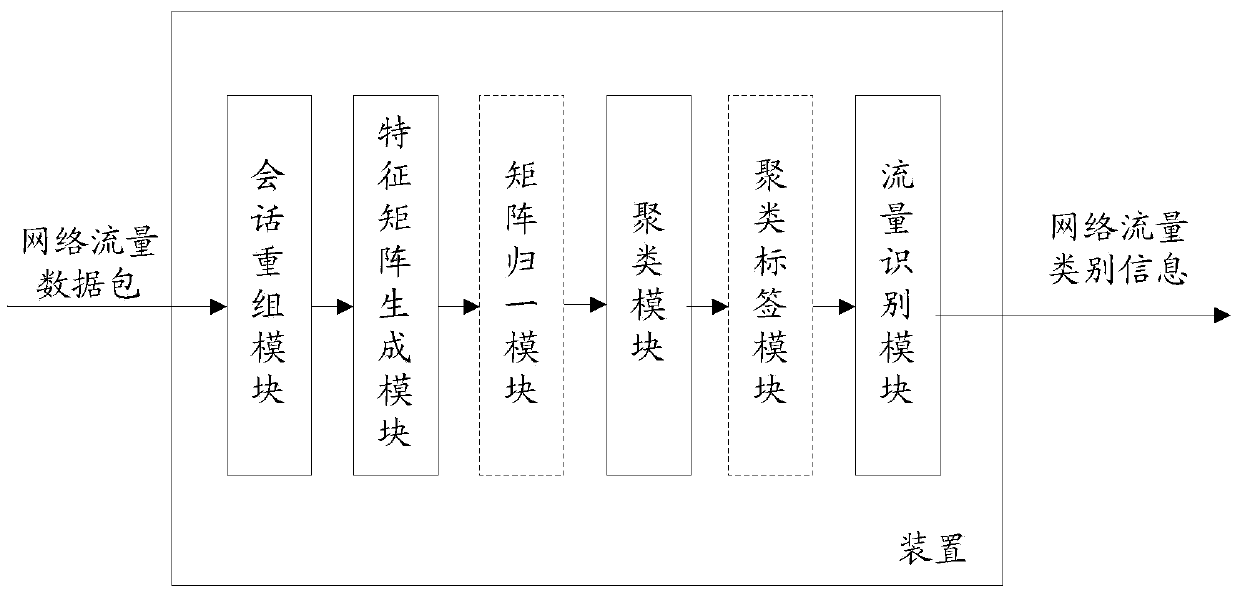
[0047] Step 200 , capturing data packet information of network traffic, and performing Transmission Control Protocol (TCP) session reassembly, so as to extract information of each TCP session flow.
[0048] It should be noted that capturing network data packet information will carry out TCP protocol analysis, which is common knowledge, even if the present invention is not described, those skilled in the art should be clear about this step.
[0049] According to the communication behavior characteristics of the Trojan horse in the interactive connection stage, the statistical characteristics of the TCP session are extracted, and the TCP session feature matrix is established;
[0050] Step 201, according to the session features of the Trojan horse communication, extract 9 session statistica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com