Encrypted traffic identification method based on load adjacent probability model
A probabilistic model and traffic identification technology, applied to electrical components, transmission systems, etc., can solve the problem of low accuracy of encrypted traffic identification methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] Embodiments of the present invention will be further described in detail below in conjunction with examples.
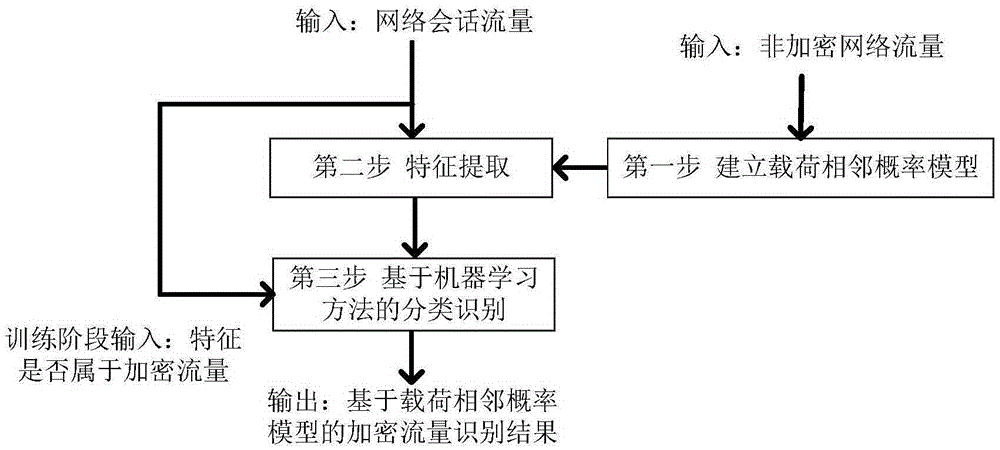
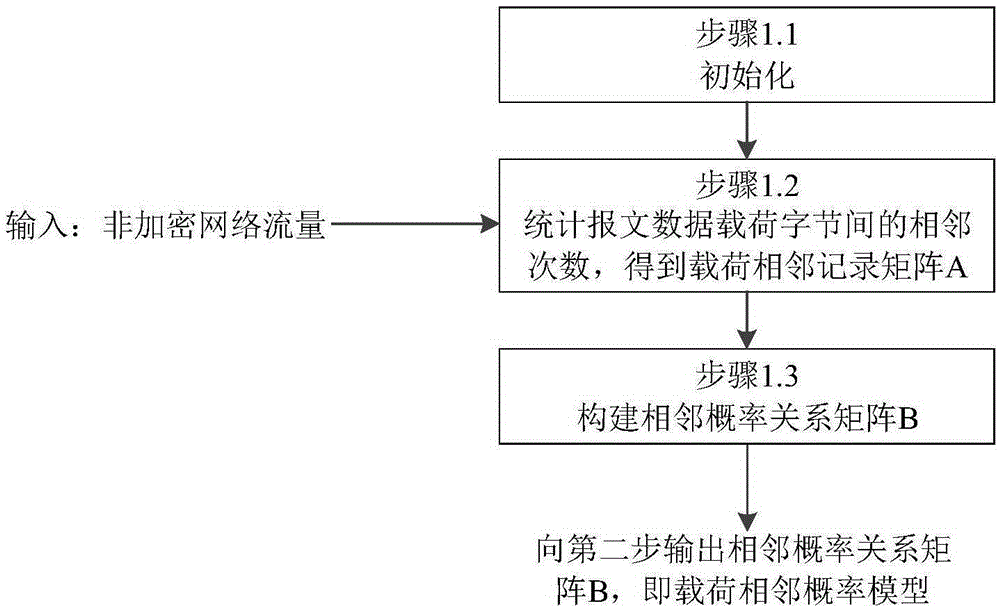
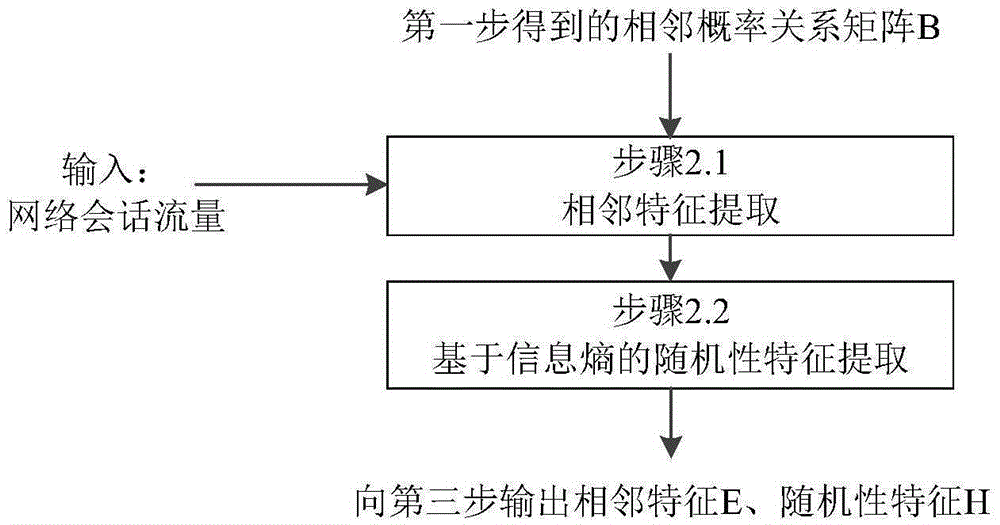
[0046] The first step is to establish a load adjacent probability model.
[0047] The processing is described using a single packet network session as input. For ease of expression, the specially constructed data payload cannot reflect the real unencrypted traffic characteristics, but only shows the processing process.
[0048] Step 1.1 Initialization. Initialize the load adjacent record matrix A[256][256] and the adjacent probability relationship matrix B[256][256]. The initial values of the matrix A and B are all 0.
[0049] Step 1.2 makes the input message data load DATA1="0x000x000x010x010x000x000x010x01" (hexadecimal representation, a total of 8 bytes), to obtain the adjacent times matrix A, see Table 1, wherein "0x00" is adjacent to "0x00" twice , "0x00" is adjacent to "0x01" twice, "0x01" is adjacent to "0x00" once, "0x01" is adjacent to "0x01" twic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com