Peer-to-peer network traffic identification method of inseparable-wavelet support vector machine
A support vector machine and traffic identification technology, applied in the network field, can solve the problems of harming the security of interests, increasing the difficulty of P2P traffic, affecting the rights of users of non-P2P applications, etc., and achieving the effect of efficient identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
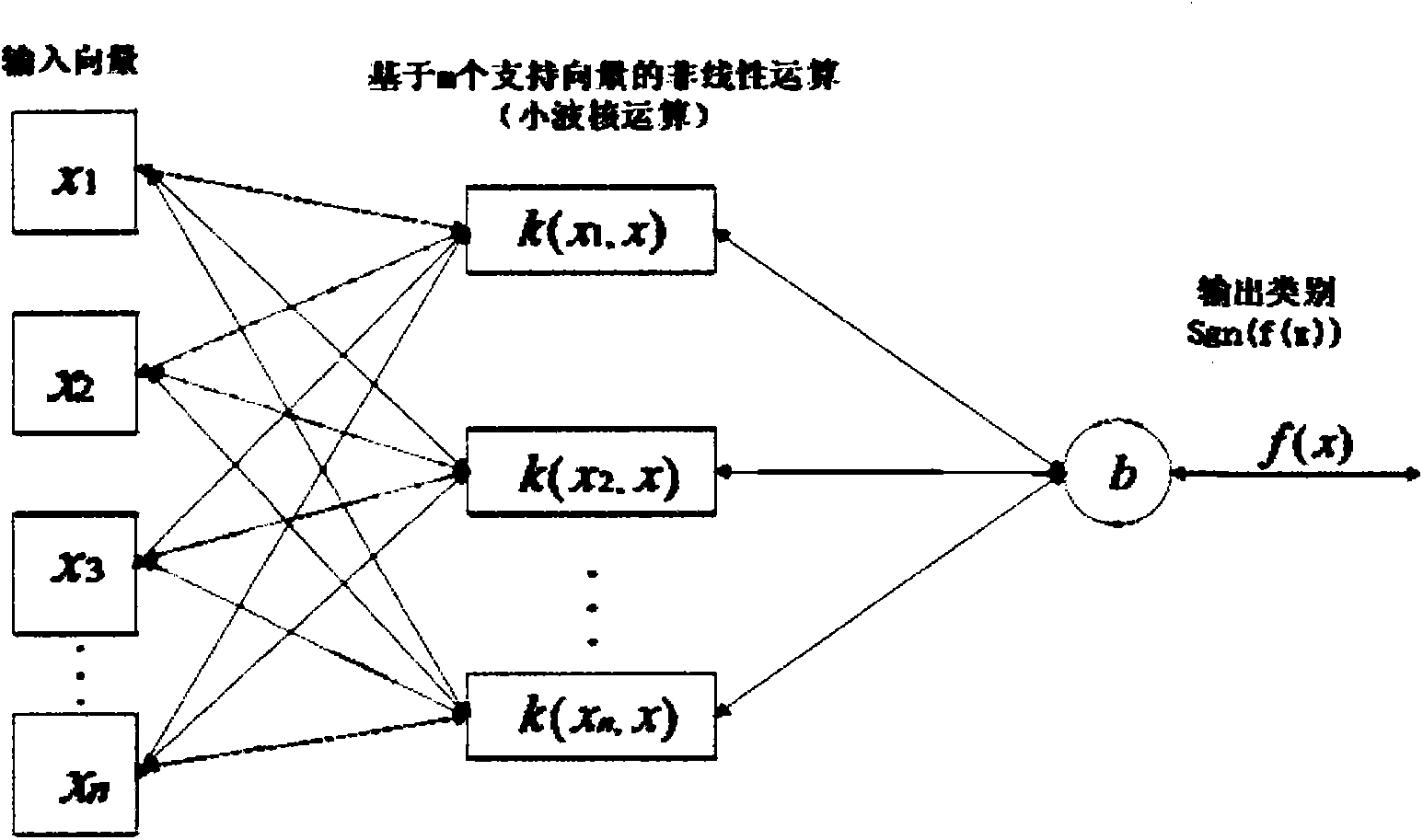
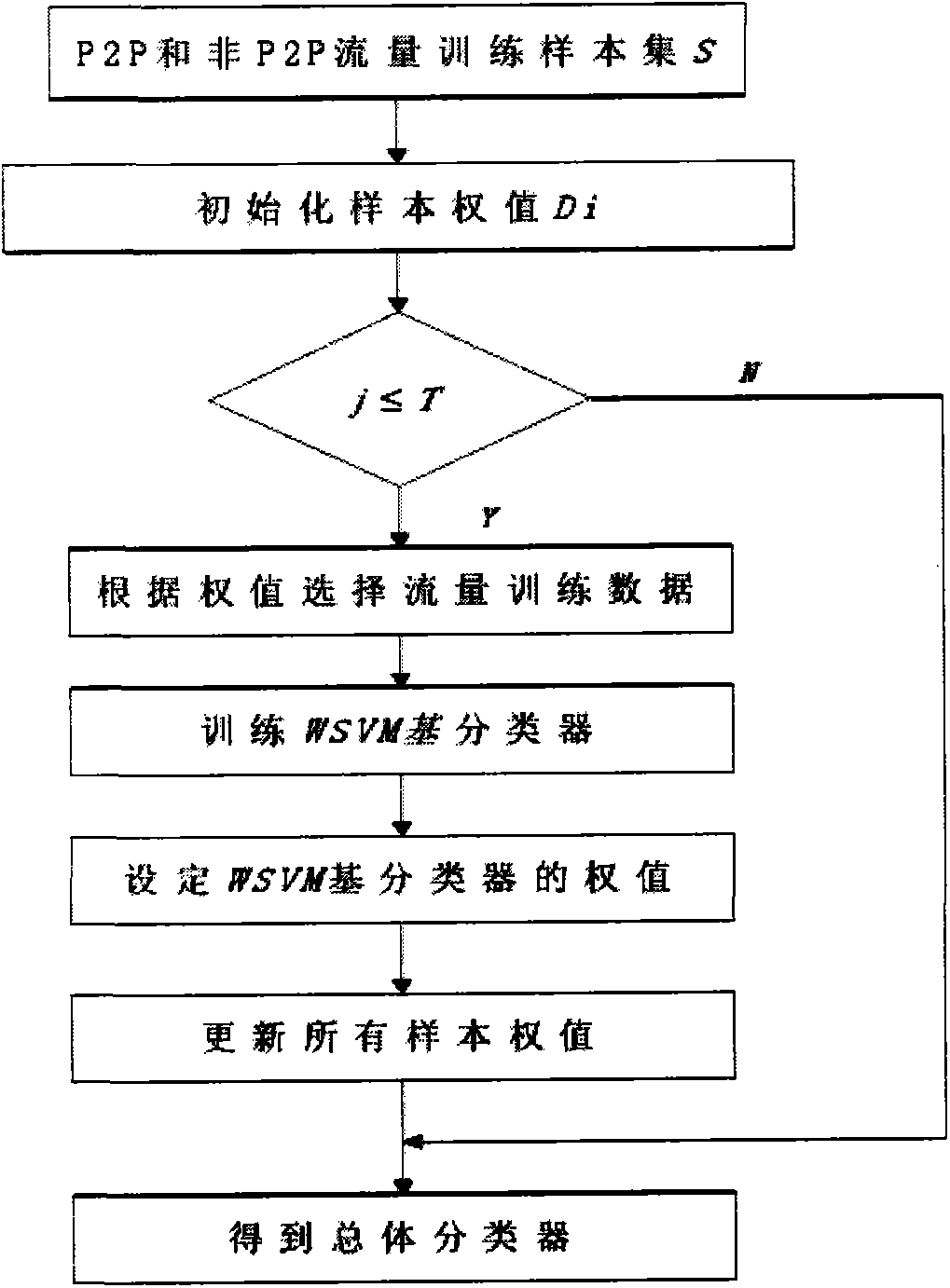
[0050] An inseparable wavelet support vector machine peer-to-peer network traffic identification method, including:
[0051] 1. Select feature vector:
[0052] Selecting the appropriate feature vector is an important aspect of identifying P2P network traffic. When selecting features for P2P network traffic, two principles should be followed: (1) The traffic of nodes with different functions and providing different services shows differences. Therefore, choose the behavioral characteristics of node traffic as much as possible. (2) The selection of features should reflect the difference between P2P traffic and non-P2P traffic so as to shorten the training time and improve the accuracy of recognition. When there are enough feature vectors, it can provide a more accurate recognition rate for the classifier, but providing too many features will make the training time longer and increase the computational complexity. According to statistics, if in the algorithm based on machine learning...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com