Encrypted malicious traffic identification method, equipment and device
A malicious traffic and identification method technology, applied in the field of equipment and devices, encrypted malicious traffic identification method, can solve the problems of inaccurate features, affecting the effect of machine learning, inaccurate selected features, etc., to achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
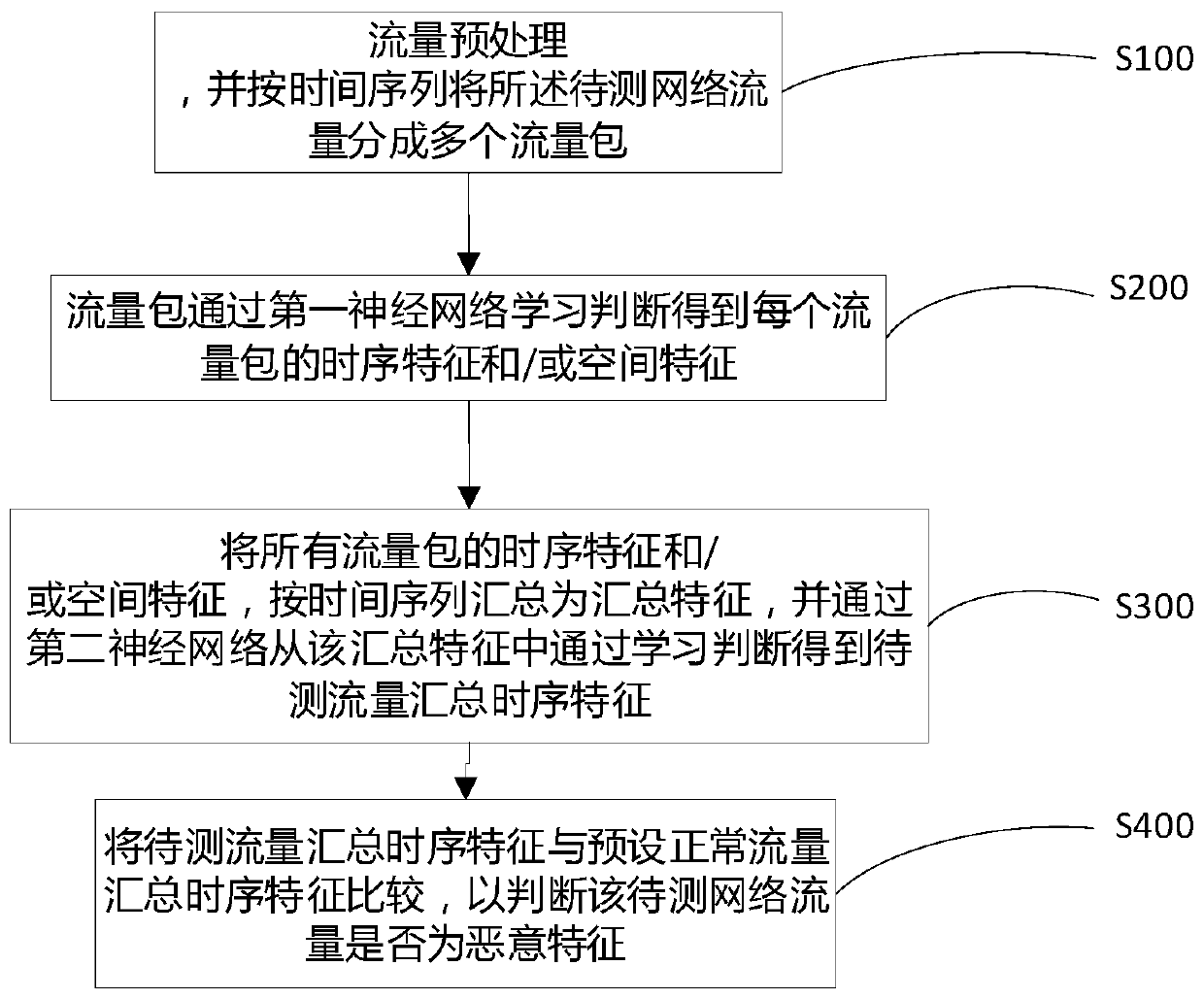
[0040] Please refer to the attached figure 1 , figure 1 It is a schematic flowchart of a method for identifying encrypted malicious traffic provided in the embodiment of the present application, and the method includes the following steps:
[0041] S100: Traffic preprocessing, and dividing the network traffic to be tested into multiple traffic packets according to time series;
[0042] S200: The traffic packets are learned and judged by the first neural network to obtain the timing features and / or spatial features of each traffic packet;
[0043] S300: Summarize the timing features and / or spatial features of all traffic packets into a summary feature in time series, and obtain the summary timing feature of the traffic to be measured by learning and judging from the summary feature through the second neural network;
[0044]S400: Comparing the summary time series feature of the traffic to be tested with the preset normal traffic summary time series feature to determine whethe...
Embodiment 2
[0079] This embodiment discloses a device for identifying encrypted malicious traffic. It includes a memory and a processor, the memory is used to store a computer program, and the processor is used to implement the method for identifying malicious traffic disclosed in Embodiment 1 when executing the computer program.
Embodiment 3
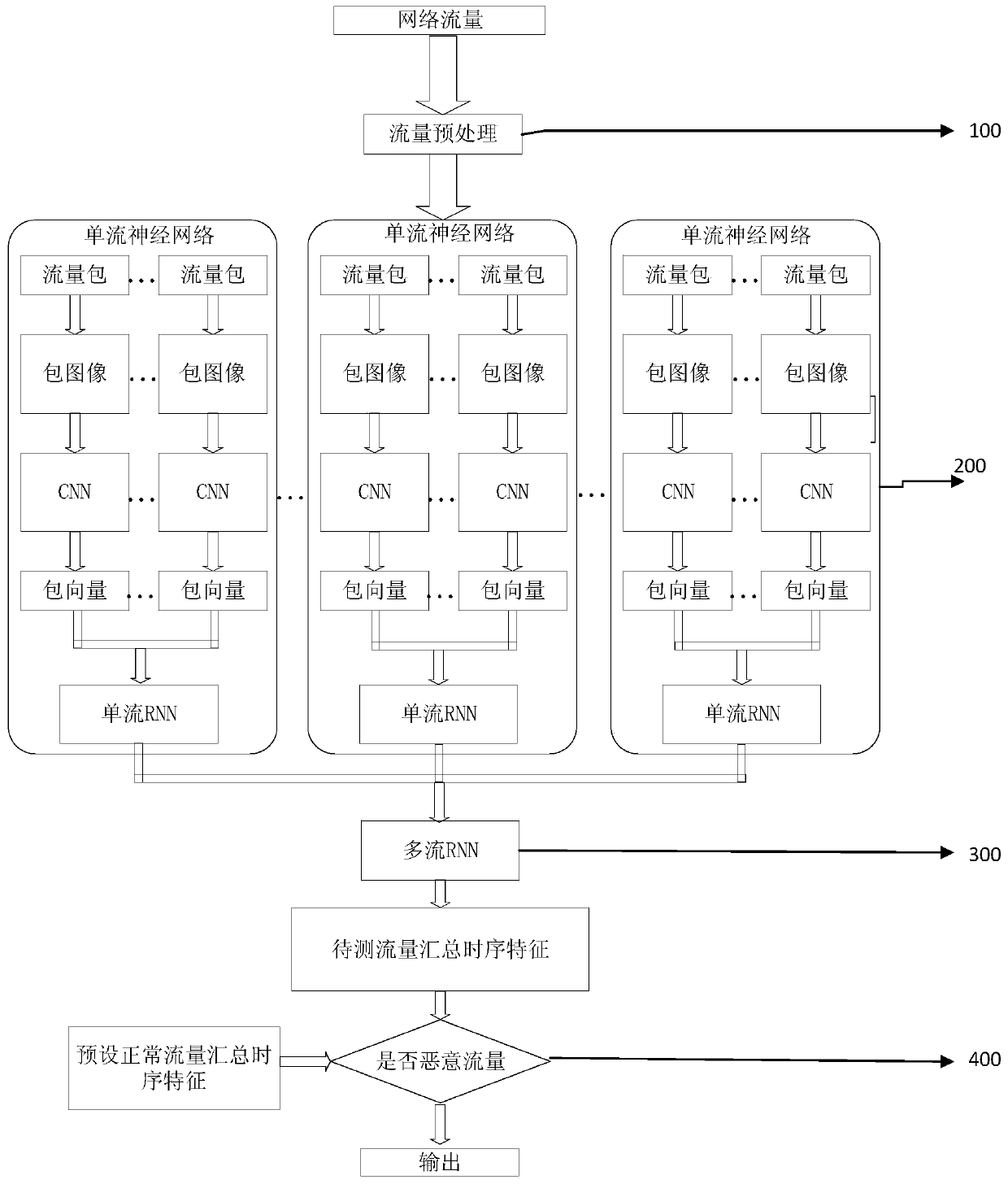
[0081] This embodiment discloses a device for identifying encrypted malicious traffic. Such as Figure 7 As shown, the method for identifying encrypted malicious traffic disclosed in Embodiment 1 includes:
[0082] A preprocessing module 100, configured to separate encrypted network traffic to be tested from network traffic, and divide the network traffic to be tested into multiple traffic packets in time series;
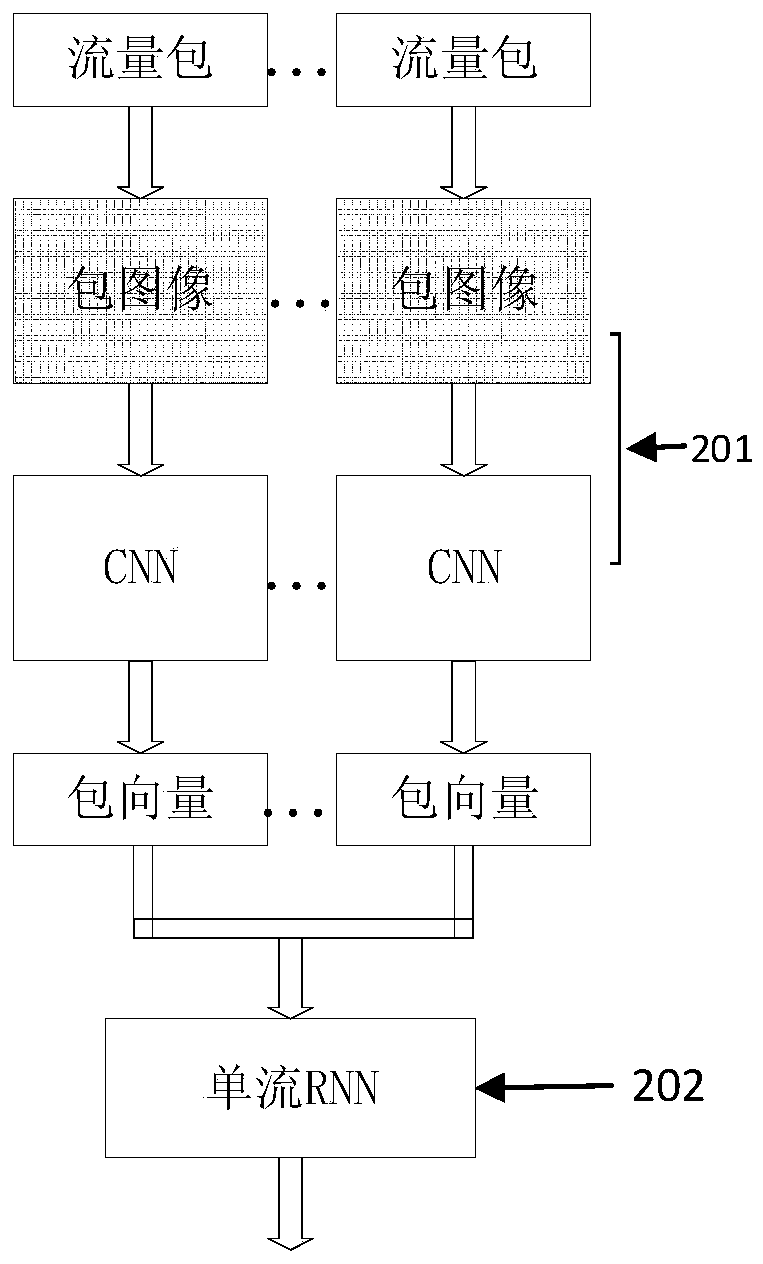
[0083] The first learning module 200 includes a first neural network for learning and judging the traffic packets through the first neural network to obtain the timing characteristics and / or spatial characteristics of each traffic packet;
[0084] The second learning module 300 includes a second neural network, and the second judging module summarizes the timing features and / or spatial features of all traffic packets of the first judging module into summary features in time series, and through the second The neural network obtains the summary timing characteristic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com