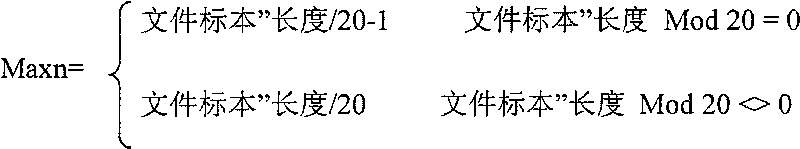Patents
Literature
61 results about "BitTorrent" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
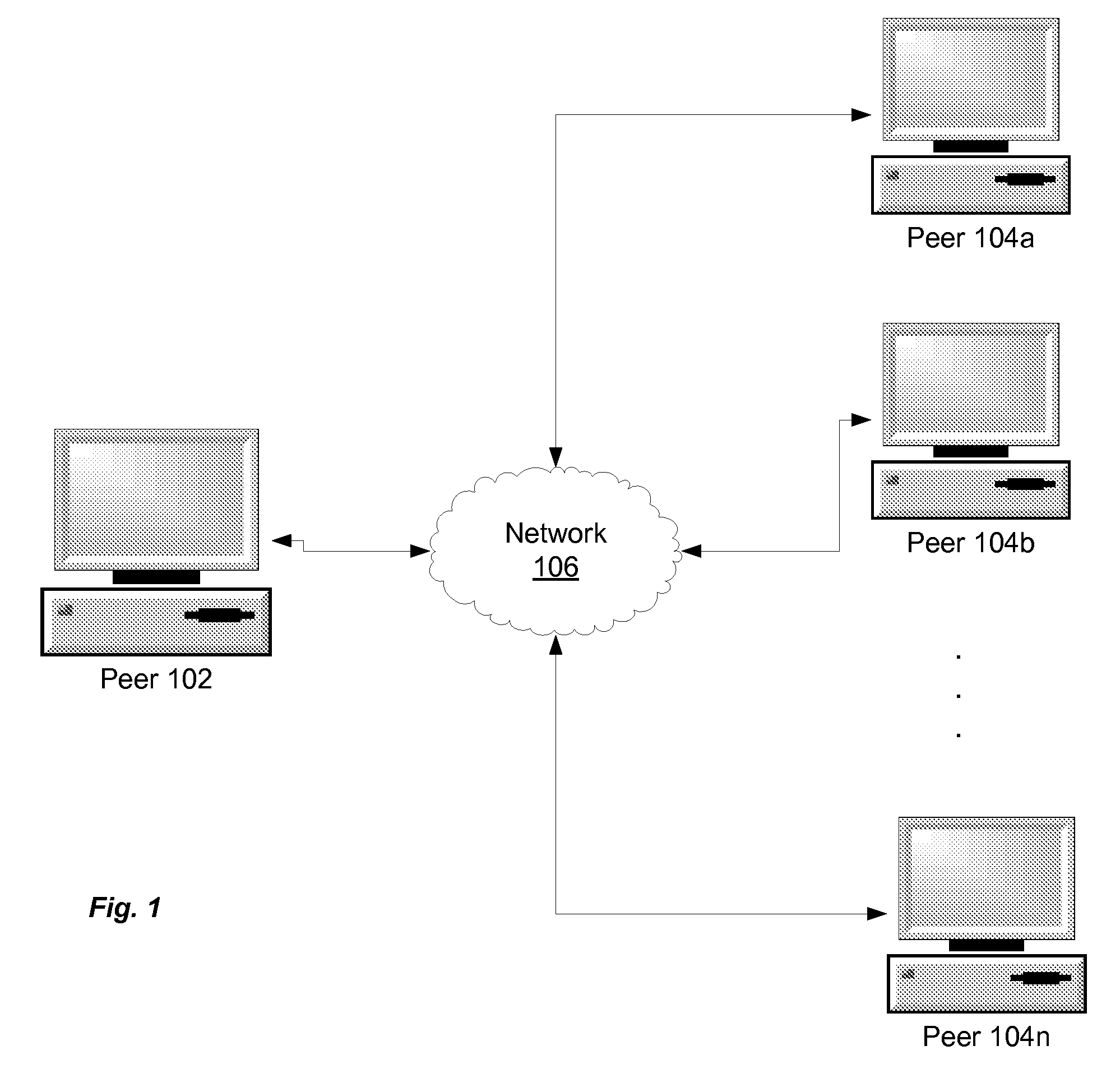
BitTorrent (abbreviated to BT) is a communication protocol for peer-to-peer file sharing (P2P) which is used to distribute data and electronic files over the Internet. BitTorrent is one of the most common protocols for transferring large files, such as digital video files containing TV shows or video clips or digital audio files containing songs. Peer-to-peer networks have been estimated to collectively account for approximately 43% to 70% of all Internet traffic (depending on location) as of February 2009. In February 2013, BitTorrent was responsible for 3.35% of all worldwide bandwidth, more than half of the 6% of total bandwidth dedicated to file sharing.
Systems and methods for managing data assets associated with peer-to-peer networks
ActiveUS20140289862A1Digital data processing detailsAnalogue secracy/subscription systemsIp addressComputer science
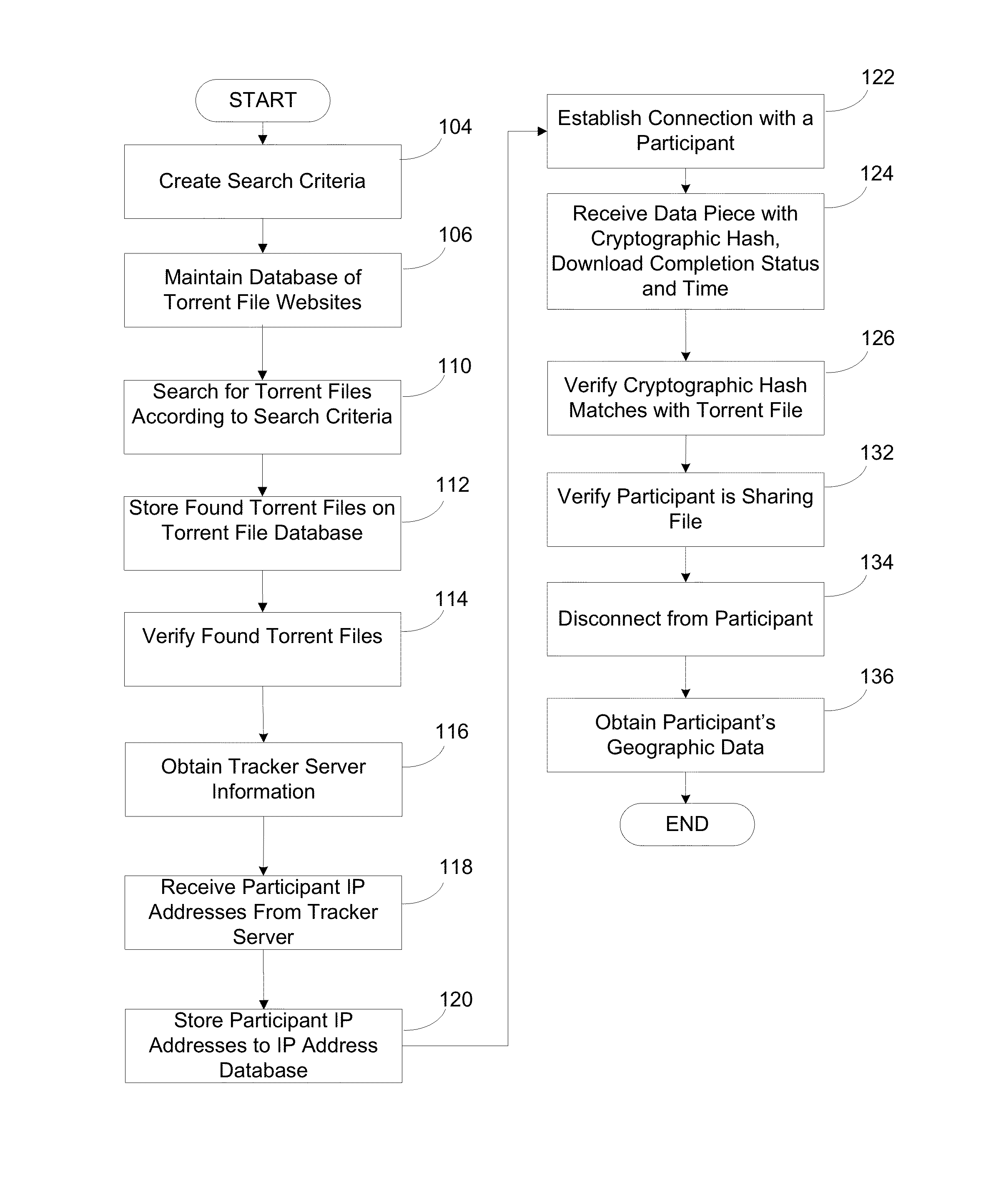
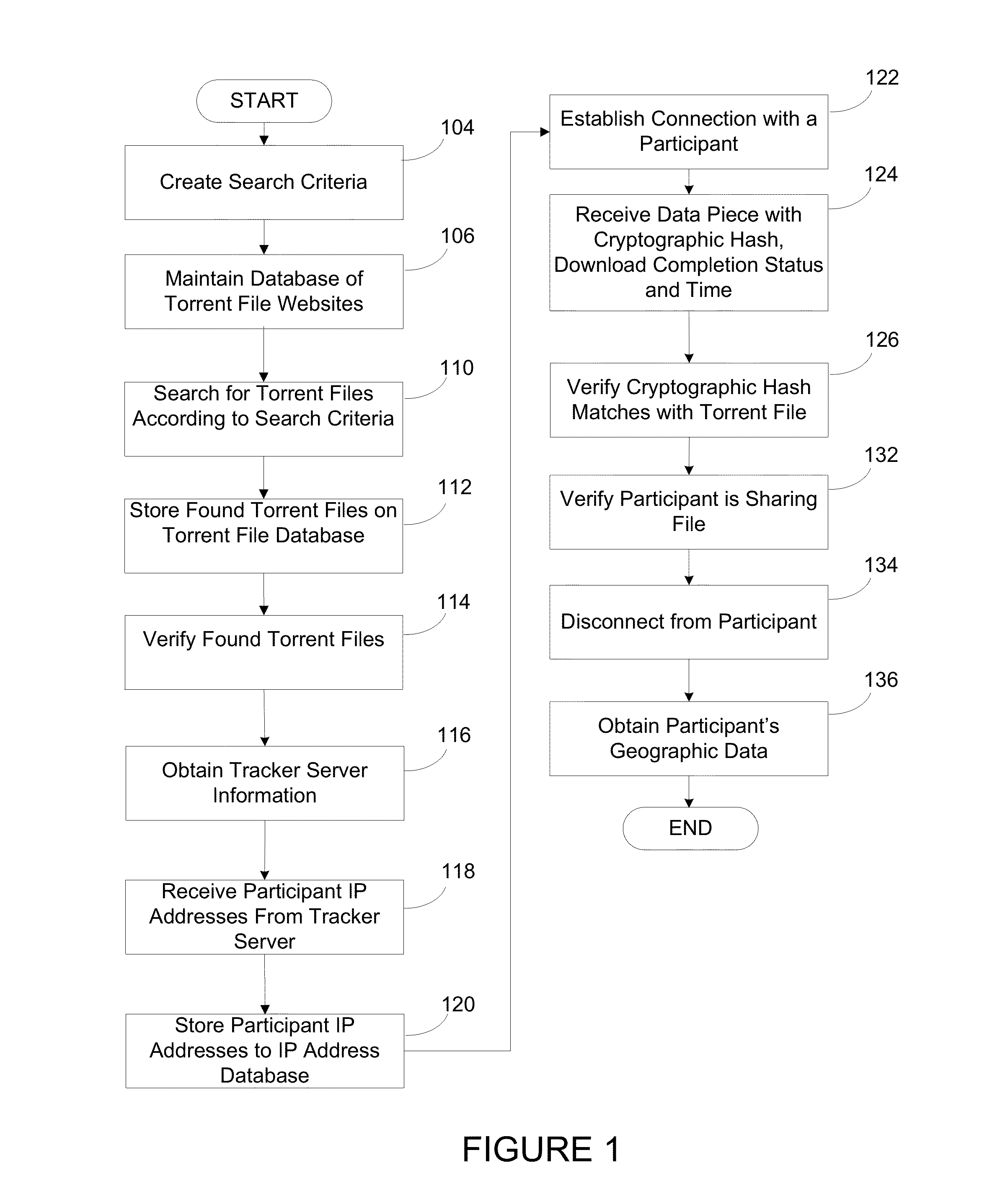
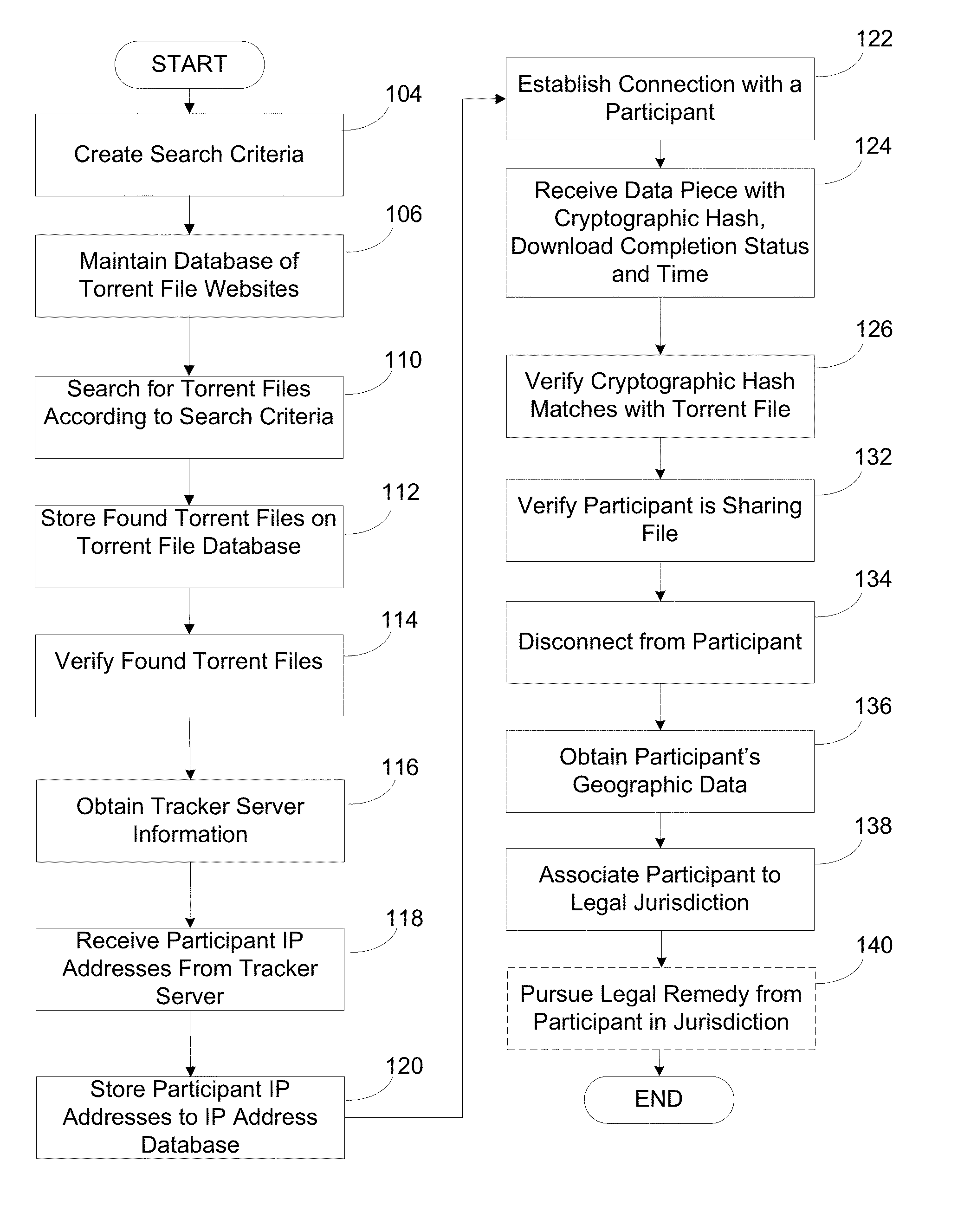
A system and method for targeting content to BitTorrent users is presented. The system searches torrent file websites for a torrent file according to specified search criteria and verifies that the torrent file corresponds to a media file containing the copyrighted work. The system obtains tracker server information from the torrent file and obtains the IP addresses of participants currently connected to the torrent file from the tracker server, attempts to establish a connection with a participant based on an IP address selected from the IP addresses and, if successful, receives a data piece with a cryptographic hash from the participant. The cryptographic hash is verified to correctly match with the torrent file. The system provides for correlation of information about participants in the peer-to-peer network and using the information to provide targeted campaign to each user based on the user's preferences.
Owner:IP SQUARED TECH HLDG
Systems and methods for managing data assets associated with peer-to-peer networks
Owner:IP SQUARED TECH HLDG
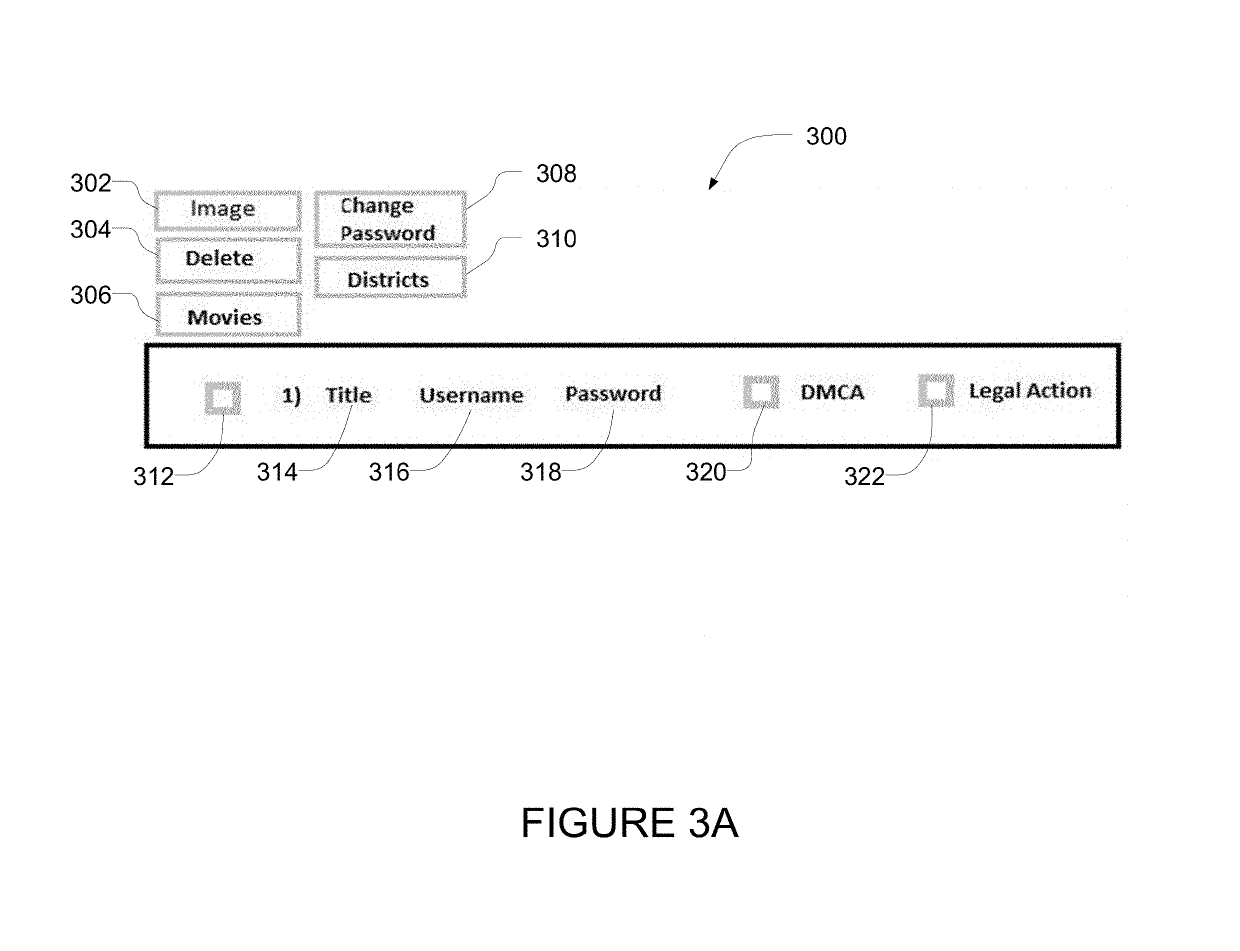
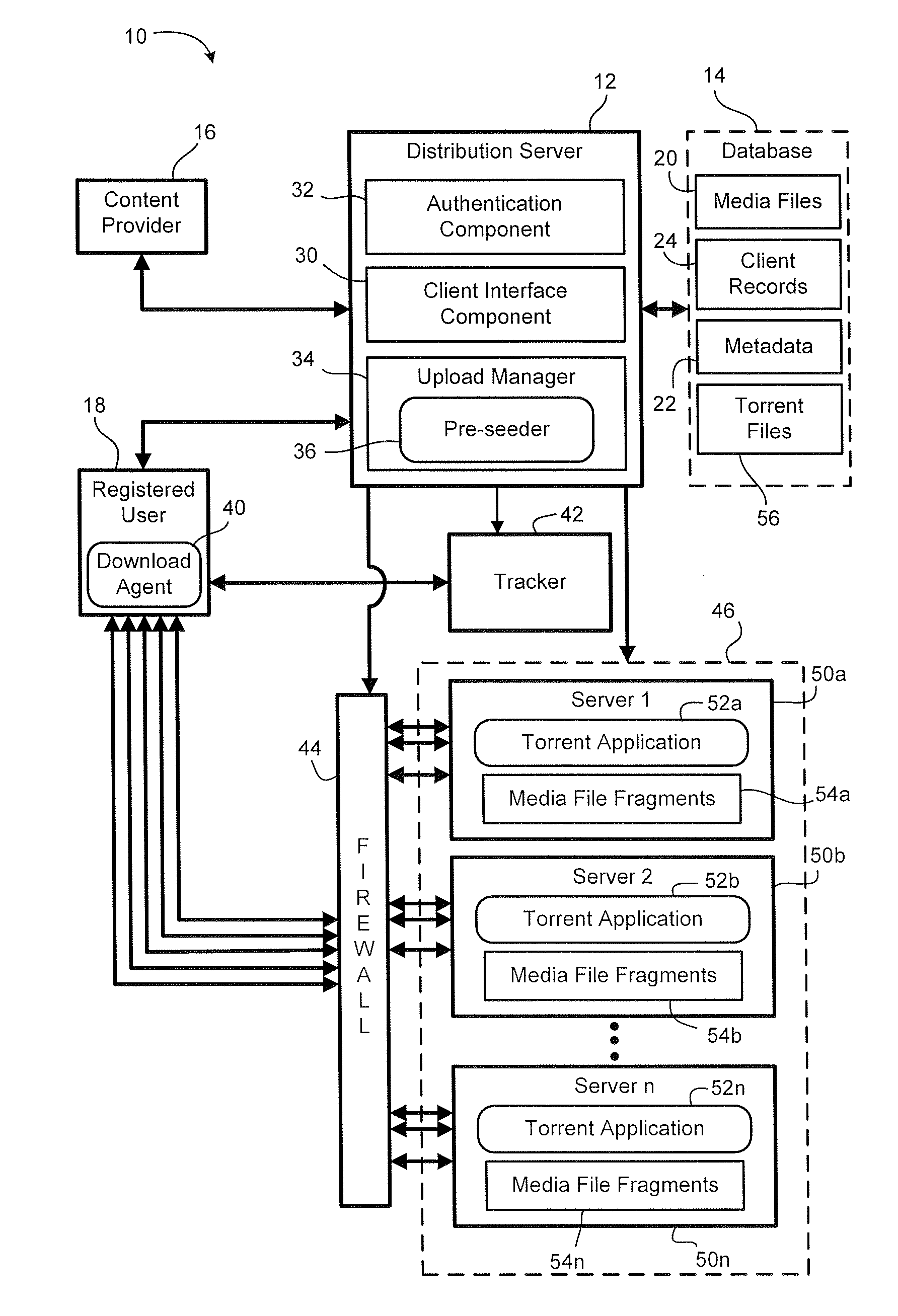
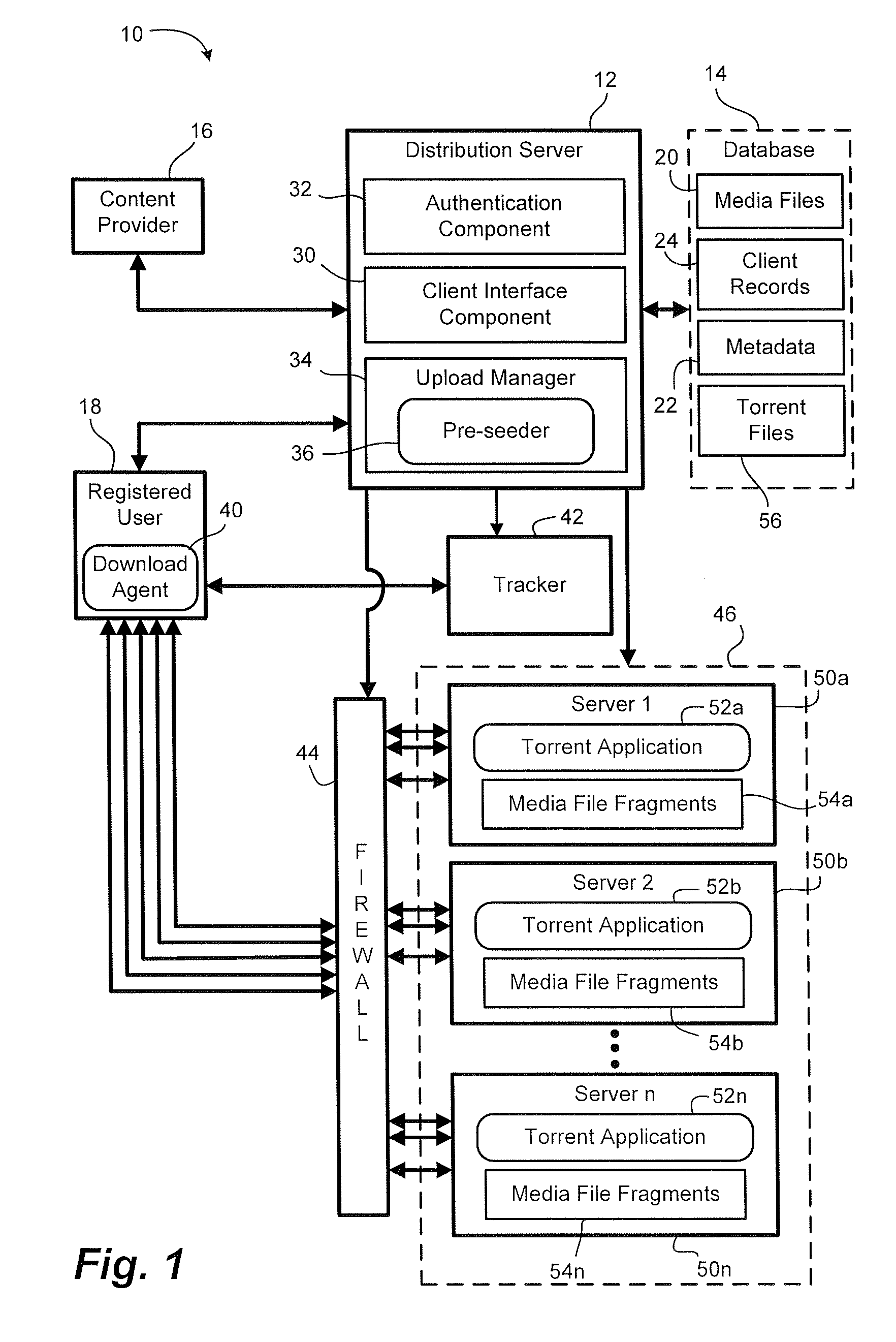
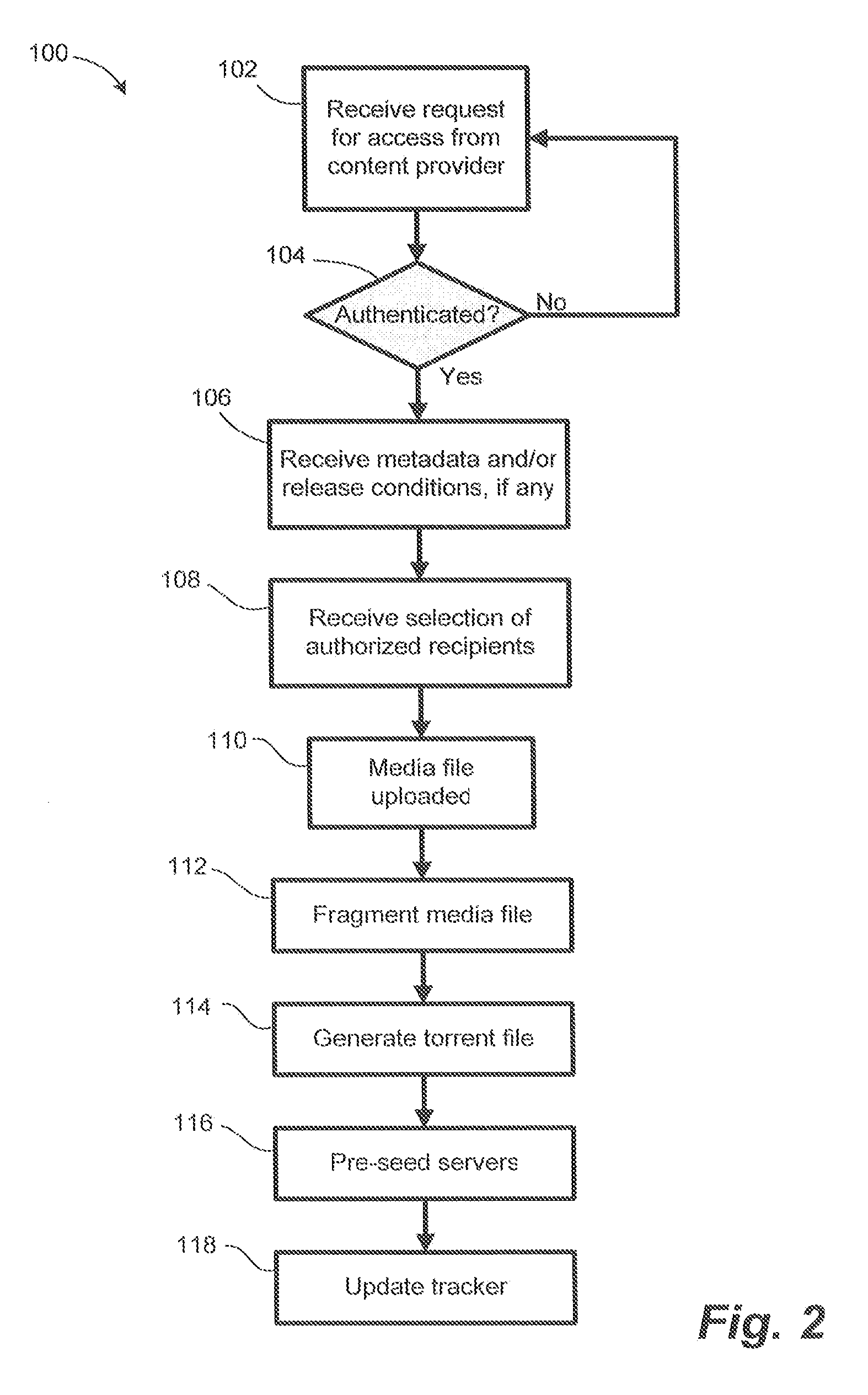
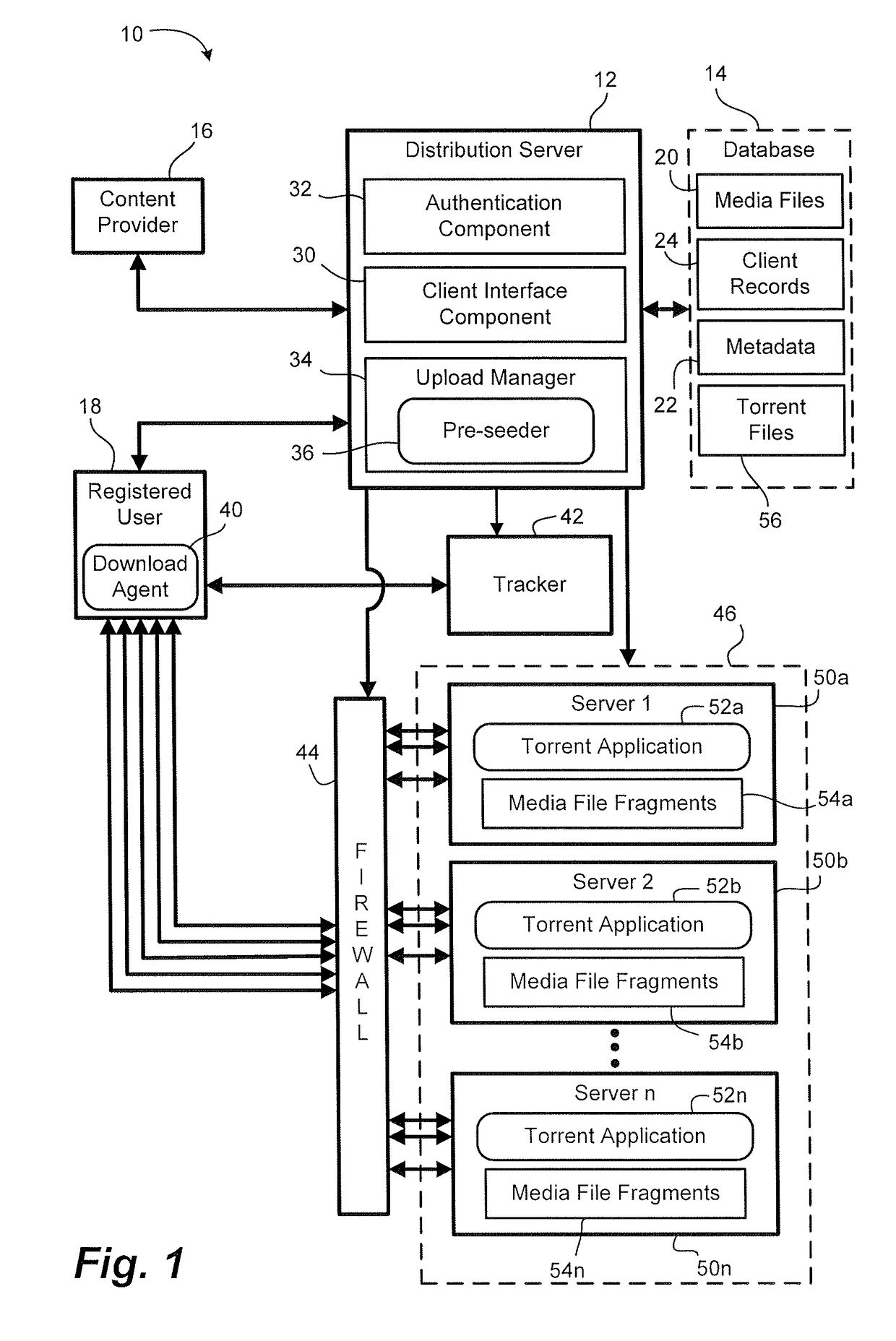
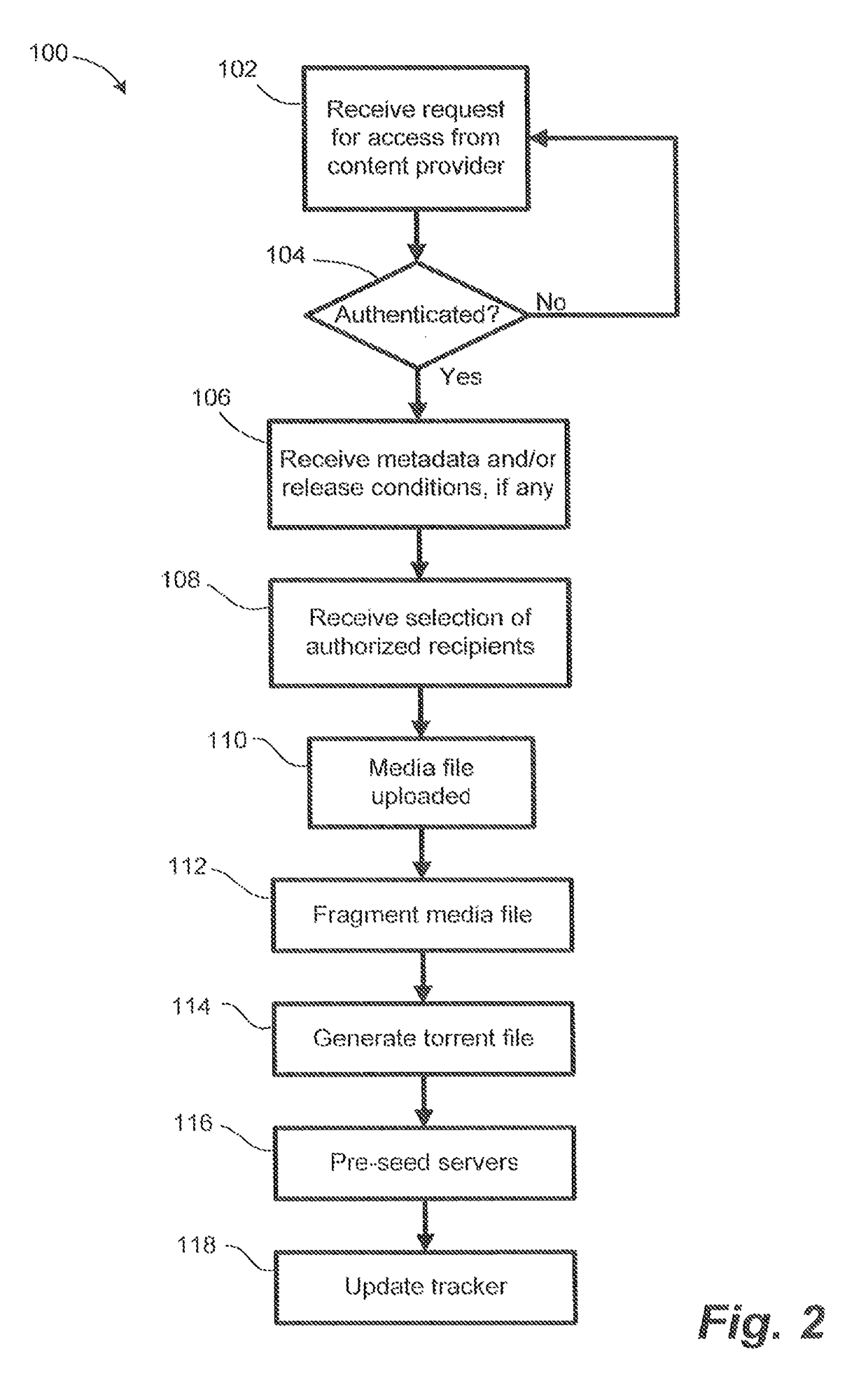
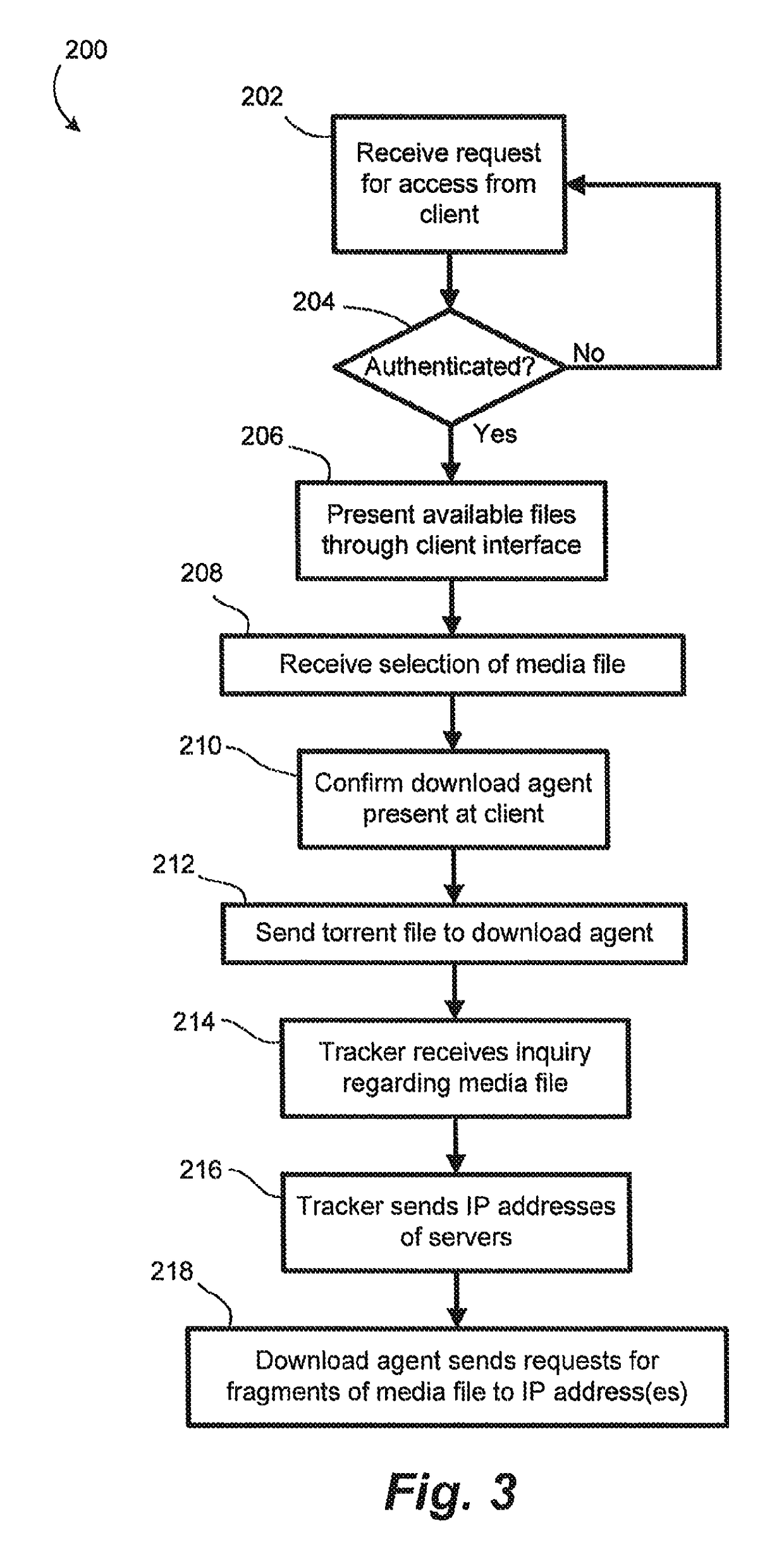
Media file distribution system and method
ActiveUS20080289006A1Maintain securityMaintain controlDiscounts/incentivesDigital data processing detailsIp addressDistribution method
A file distribution method and system for distributing media files to authorized recipients. The method and system exploit the advantages of peer-to-peer file distribution protocols, such as BitTorrent, while maintaining security and control over the file distribution. A server farm containing a plurality of servers is placed behind the security of a distribution system, preventing unauthorized client devices from accessing the media files stored on the server farm. Media files are fragmented and stored on each of the plurality of servers within the server farm. Each server on the server farm features at least one IP address and each server is pre-seeded with a complete copy of the fragmented media file. Fragments are distributed to requesting authorized clients in accordance with a peer-to-peer file distribution protocol.
Owner:YANGAROO
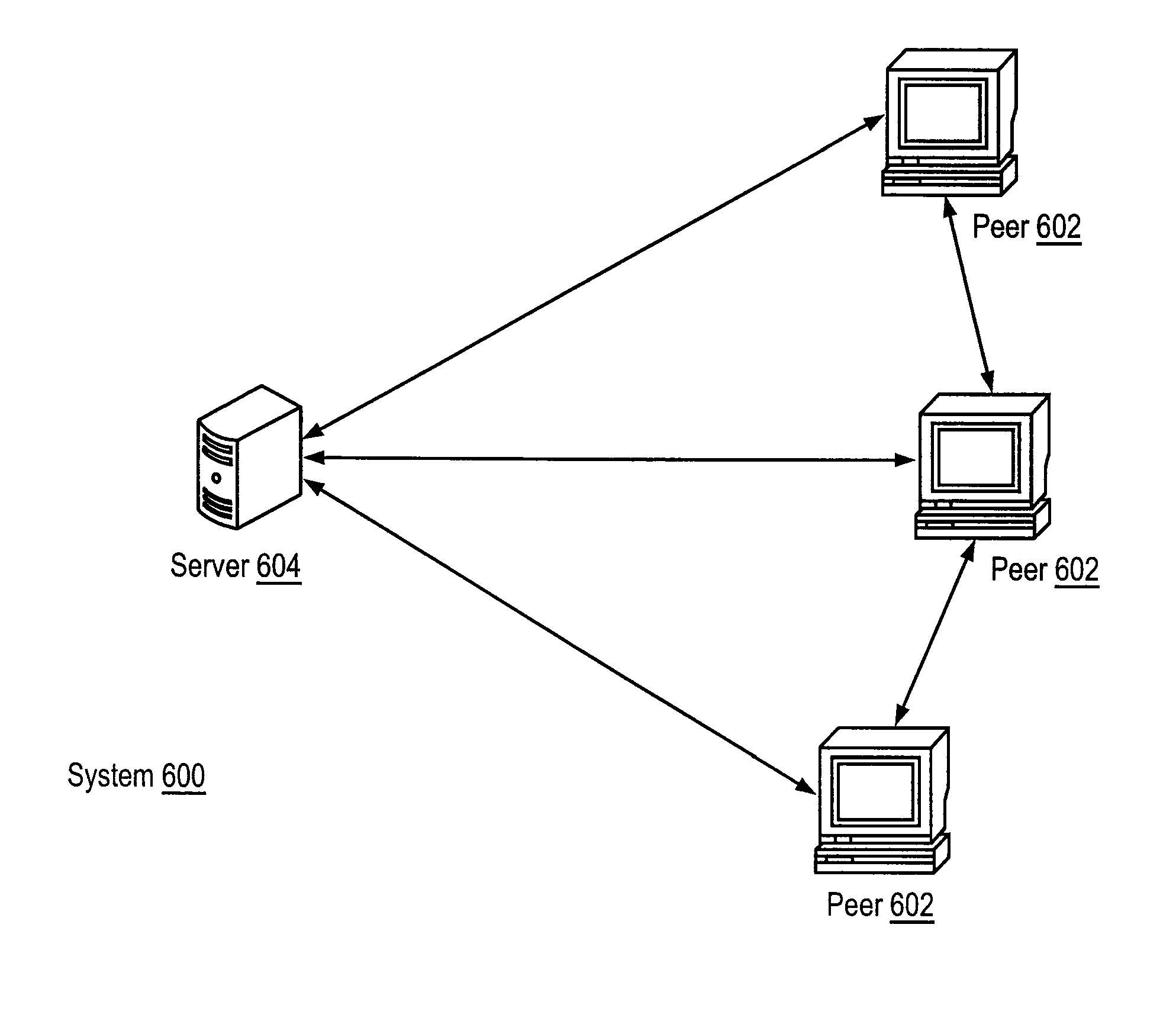
Peer-to-Peer Streaming Of Non-Live Content
ActiveUS20080140853A1Minimal impactEasy to scaleMultiple digital computer combinationsTransmissionPoint-to-Point ProtocolEnd system
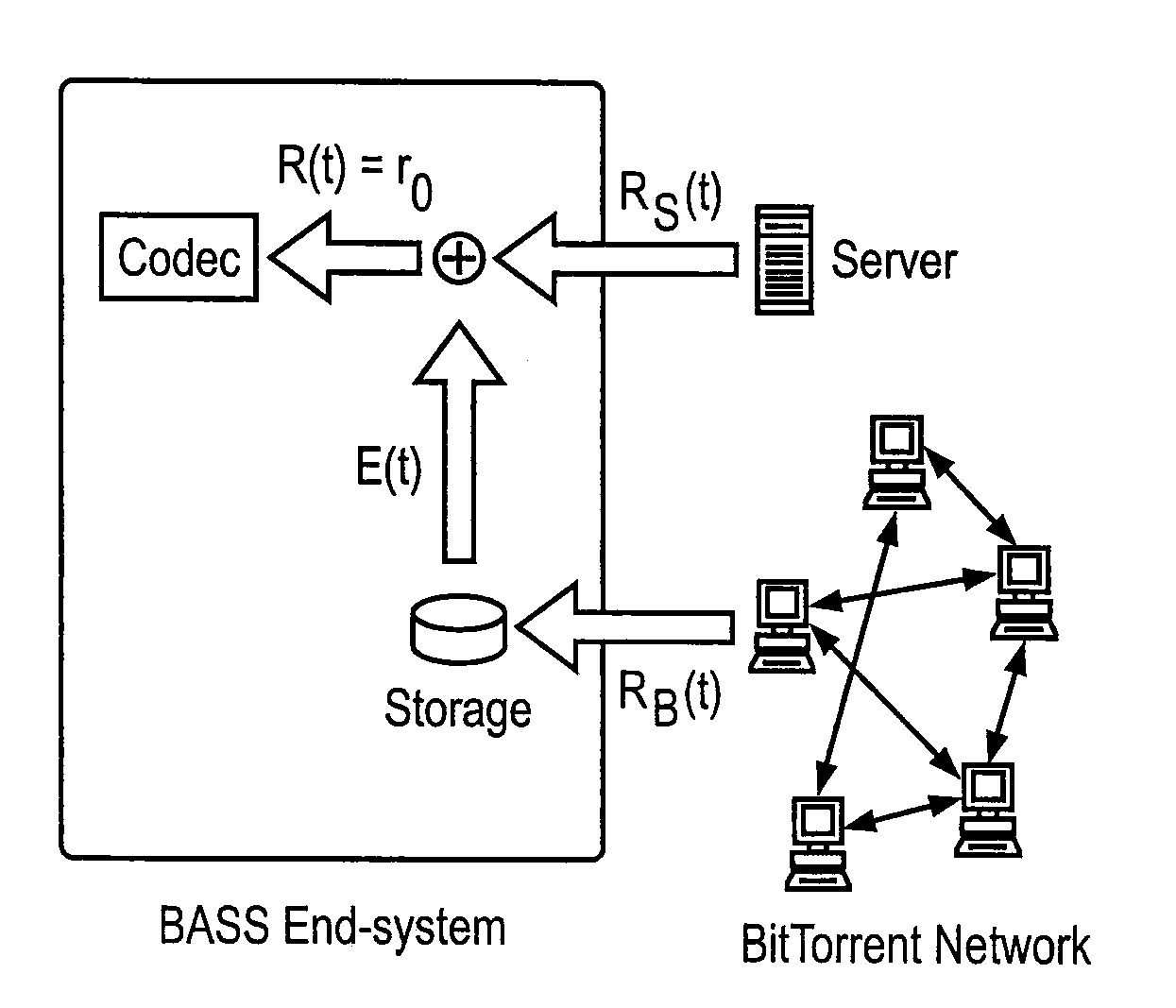
A Peer-to-Peer protocol such as BitTorrent is used to assist streaming. Peers download streaming content from the P2P network while simultaneously playing the downloaded content. As the stream plays, an end system downloads any missing pieces directly from a server or other infrastructure node. This method roughly squares server capacity and can be refined to require on average 0(1) servers regardless of the number of concurrent users. Thus BitTorrent assisted streaming scales better than traditional server-client and other infrastructure-only solutions, each of which requires a number of infrastructure nodes that scale linearly as a function of the number of users. Unlike End-System-Multicast, BitTorrent assisted streaming does not subject users to the vagaries of intermediate unreliable, potentially bandwidth-constrained end-systems; the departure of any single end-system has minimal impact on overall performance; and BitTorrent has a well-crafted incentive mechanism for encouraging users to contribute their upstream capacity.
Owner:BITTORRENT
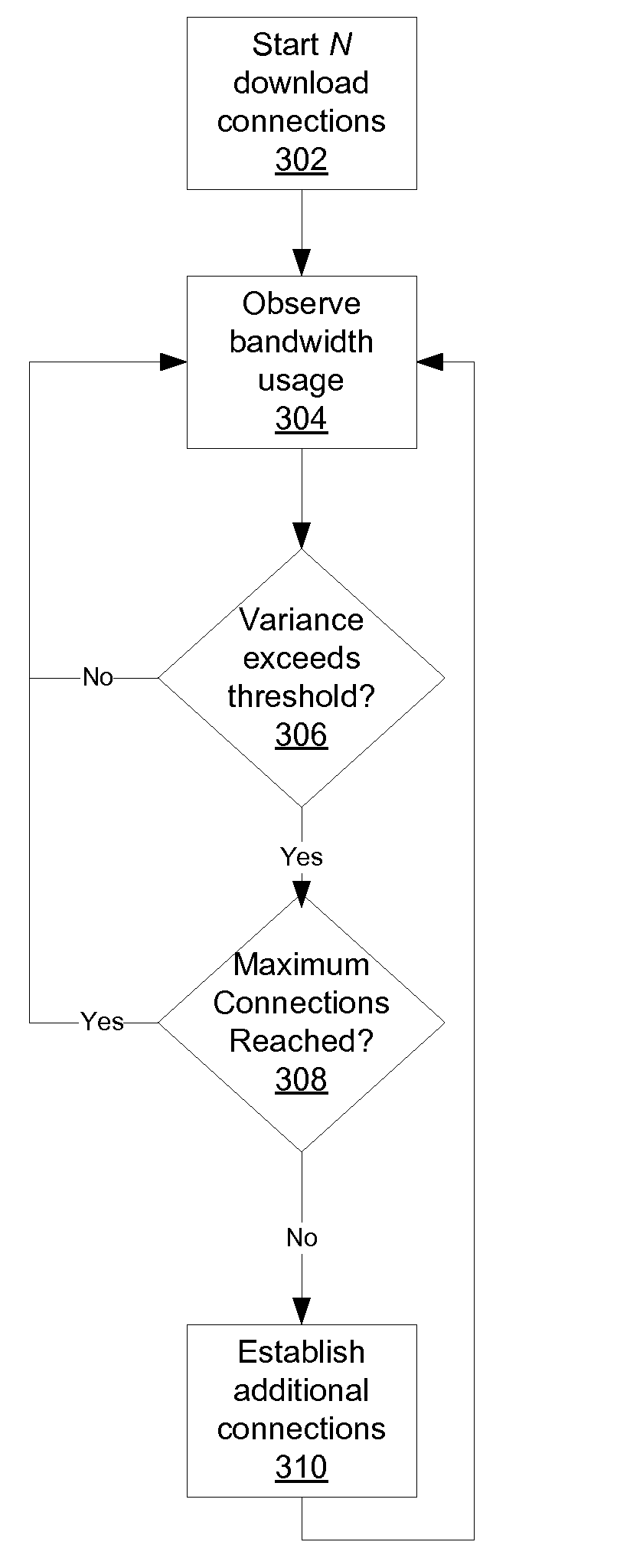
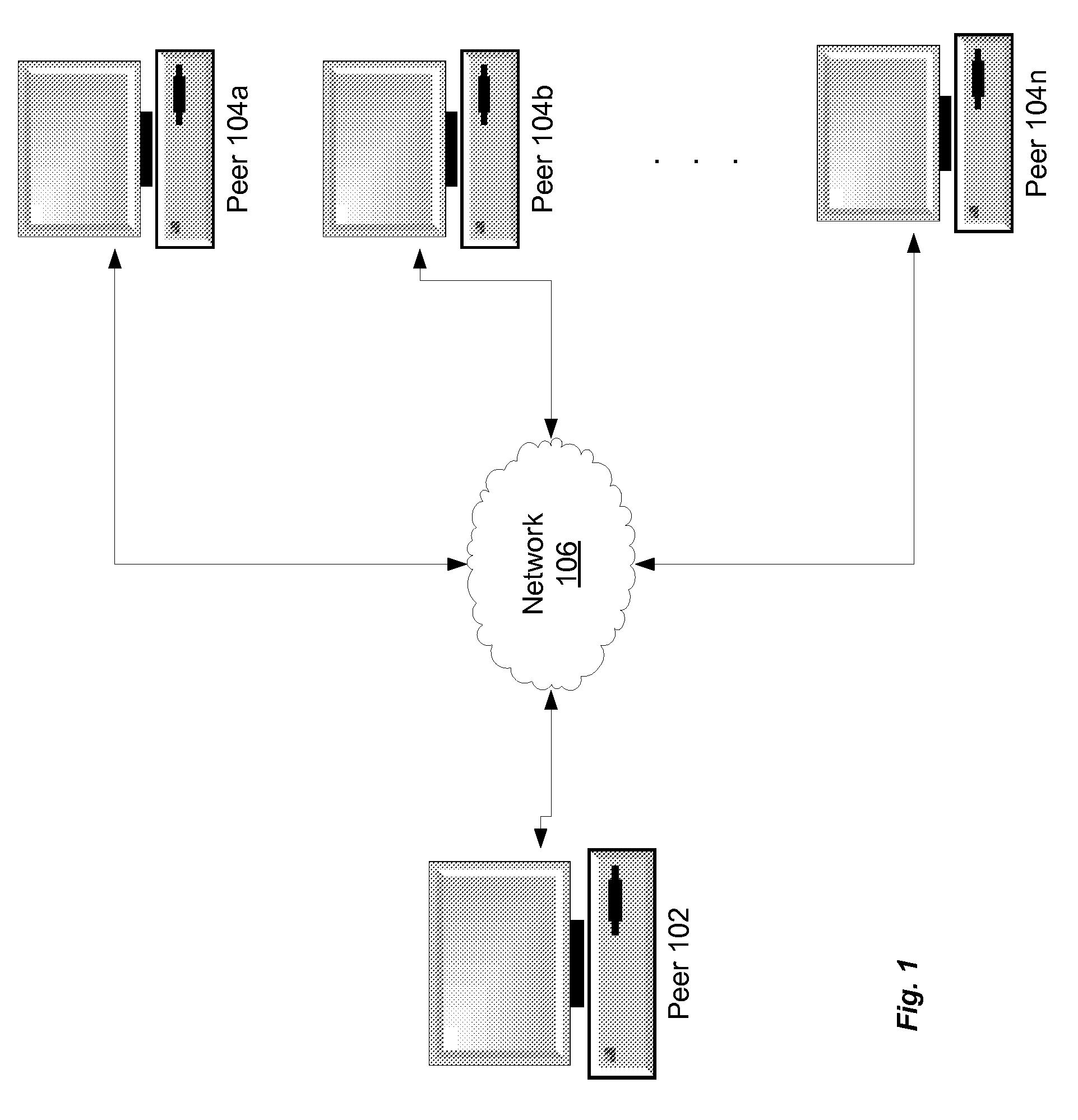
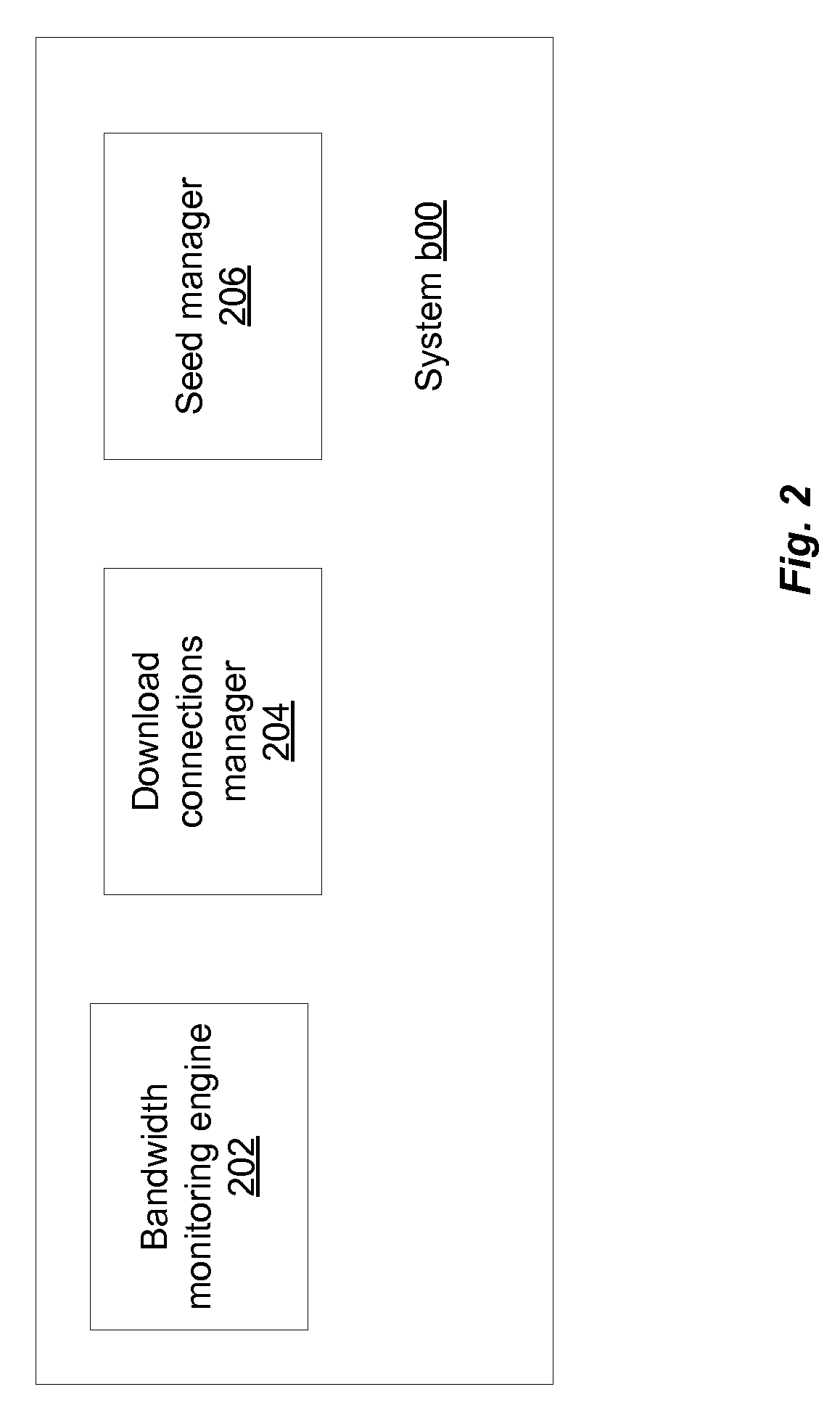
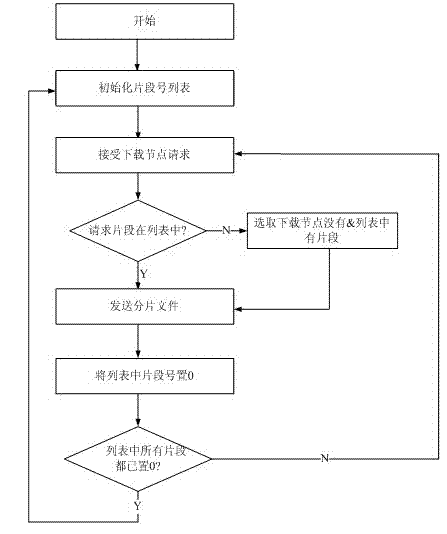
Peer-to-Peer Download And Seed Policy Management
ActiveUS20080005336A1Multiple digital computer combinationsTransmissionDistributed computingBitTorrent
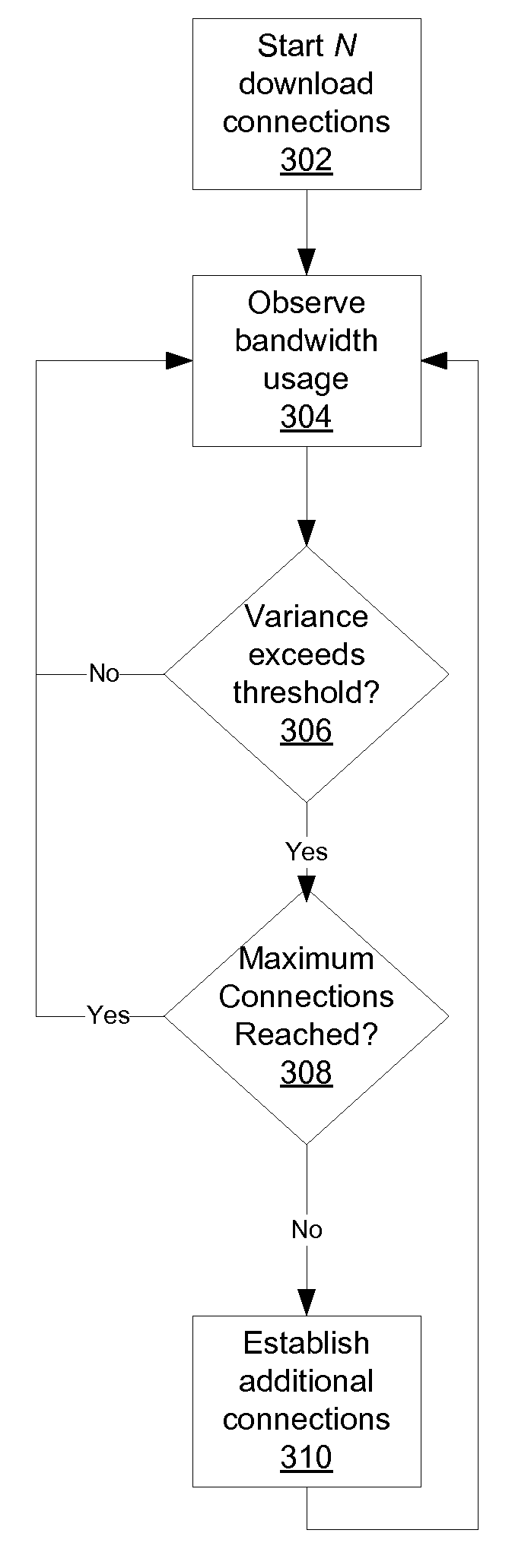
Transfer policy management methods in a peer-to-peer networking environment such as BitTorrent are provided. A download TPM maximizes the usage of available bandwidth, while focusing on as few torrents as possible. For a given list of torrents, a peer in accordance with the present invention determines how many download connections to maintain at a given time in order to maximize usage of bandwidth. If the variance of per-connection bandwidths exceeds a threshold, more connections are added until either variance does not exceed the threshold or a maximum number of connections are established. A seeding peer determines when to reduce the number of files being seeded by monitoring its average upload rate per torrent. If its average rate falls below a threshold, then the peer stops seeding a file. The file that the peer stops seeding is one to which the peer is making the smallest overall contribution.
Owner:BITTORRENT
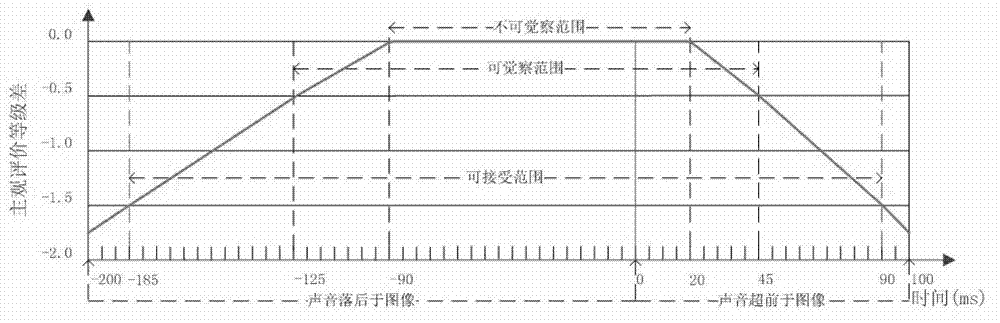
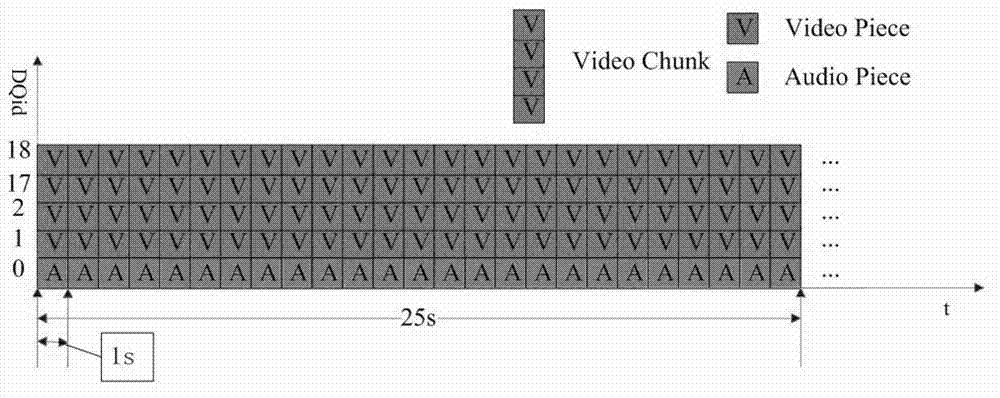
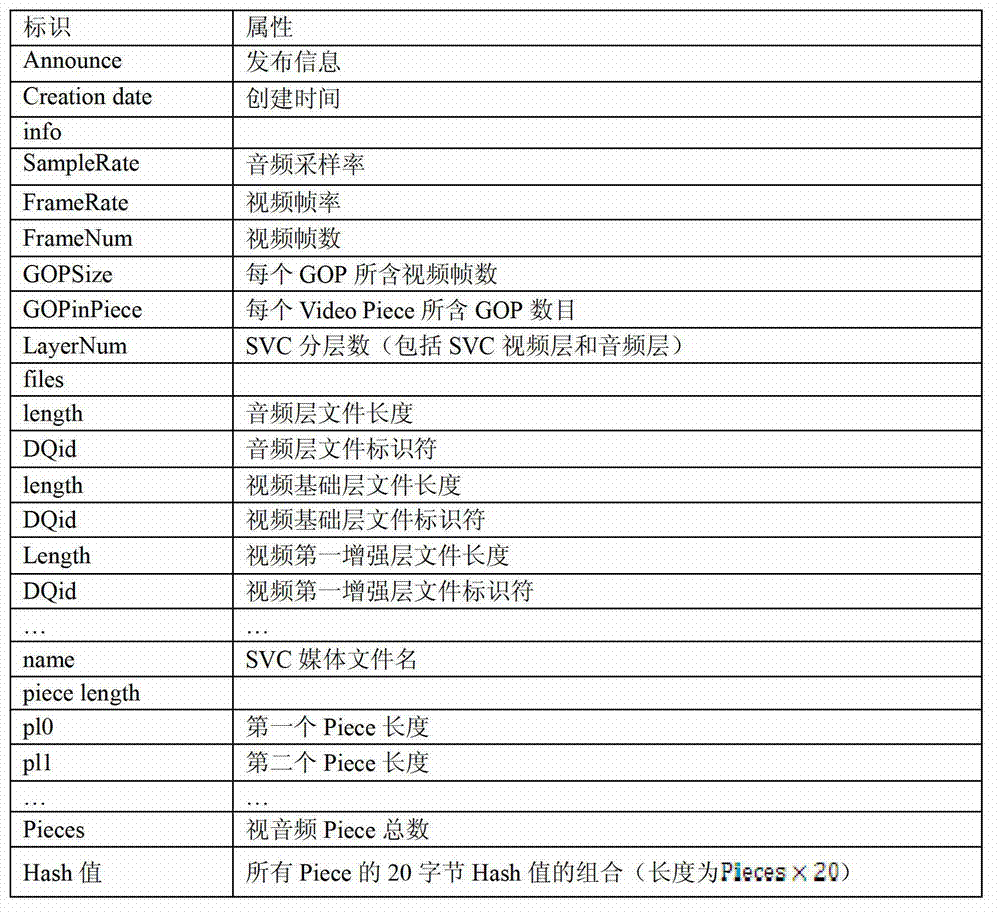
Video and audio synchronizing method of P2PVoD (peer-to-peer video on demand) system based on SVC (scalable video coding)
InactiveCN102761776AIsochronous transferGuaranteed fluencySelective content distributionAudio MediaTime information
The invention provides a video and audio synchronizing method based on an SVC (scalable video coding) P2PVoD (peer-to-peer video on demand) system, belonging to the field of multimedia internet application. The video and audio synchronizing method comprises the following steps of: compositing an audio stream into an SVC video stream, combining an SVC video coding feature with a Bittorrent protocol, and improving a package formate of a Torrent file, thus ensuring SVC-based video and audio data transmission synchronization; utilizing a manner combining cache-based quality self adapting with sequential downloading to ensure the video and audio play smoothness and improve the video and audio play quality, and realizing scheduling synchronization of an SVC video and audio segment; and taking an SVC video as a main media stream and an audio as a secondary media stream, updating and synchronizing a clock according to playing time information of the video segment during playing, and synchronously decoding and playing corresponding audio segments by the clock, thus realizing play synchronization of video and audio medias.
Owner:CHONGQING UNIV
Peer-to-peer streaming of non-live content
ActiveUS9210085B2Minimal impactEasy to scaleMultiple digital computer combinationsData switching networksPoint-to-Point ProtocolEnd system
A Peer-to-Peer protocol such as BitTorrent is used to assist streaming. Peers download streaming content from the P2P network while simultaneously playing the downloaded content. As the stream plays, an end system downloads any missing pieces directly from a server or other infrastructure node. This method roughly squares server capacity and can be refined to require on average 0(1) servers regardless of the number of concurrent users. Thus BitTorrent assisted streaming scales better than traditional server-client and other infrastructure-only solutions, each of which requires a number of infrastructure nodes that scale linearly as a function of the number of users. Unlike End-System-Multicast, BitTorrent assisted streaming does not subject users to the vagaries of intermediate unreliable, potentially bandwidth-constrained end-systems; the departure of any single end-system has minimal impact on overall performance; and BitTorrent has a well-crafted incentive mechanism for encouraging users to contribute their upstream capacity.
Owner:BITTORRENT
Method for calibrating integrity of P2P download files
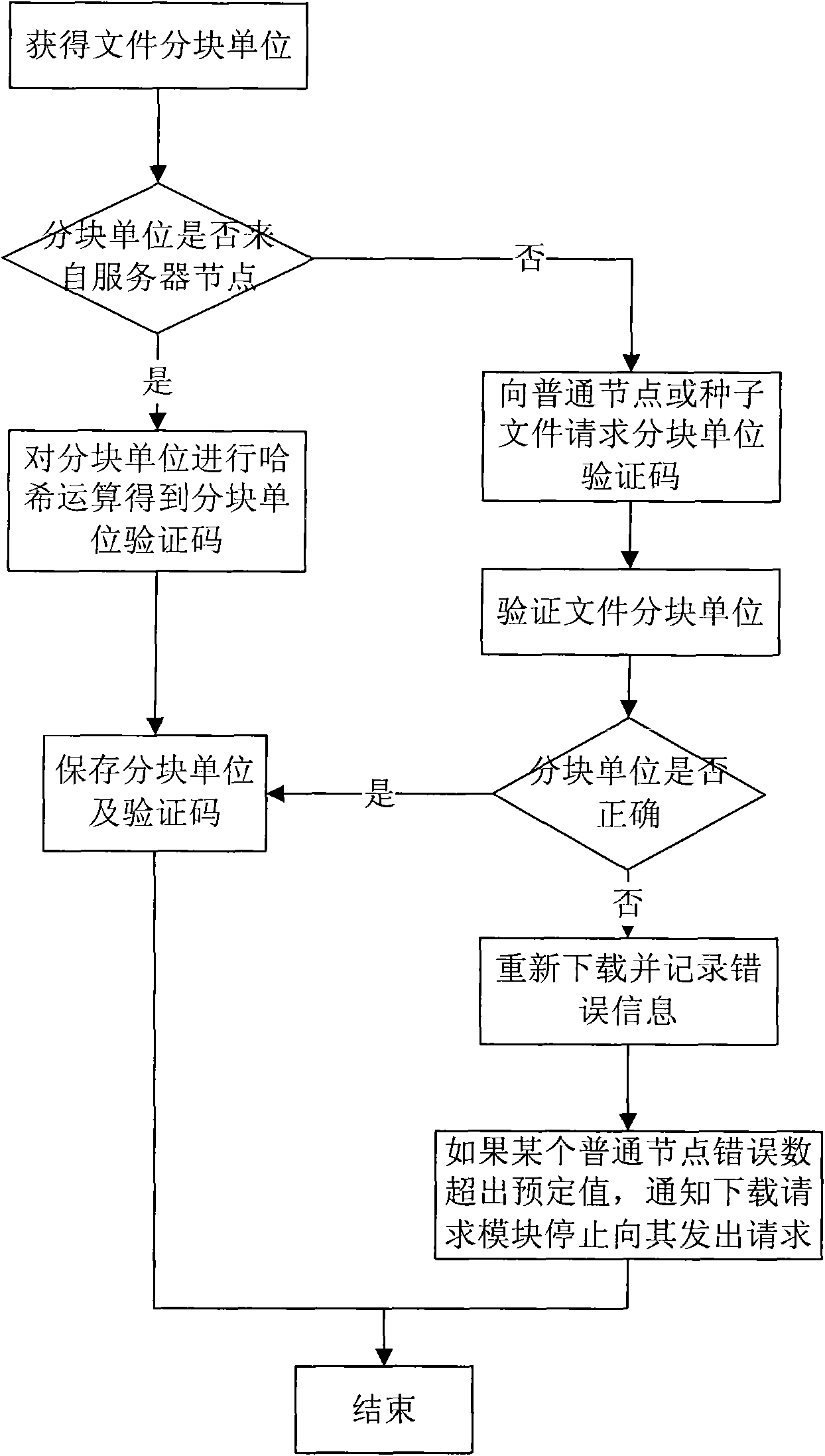
ActiveCN101651709AImprove download efficiencyReduce overall download timeError detection/correctionTransmissionComputer hardwareClient-side
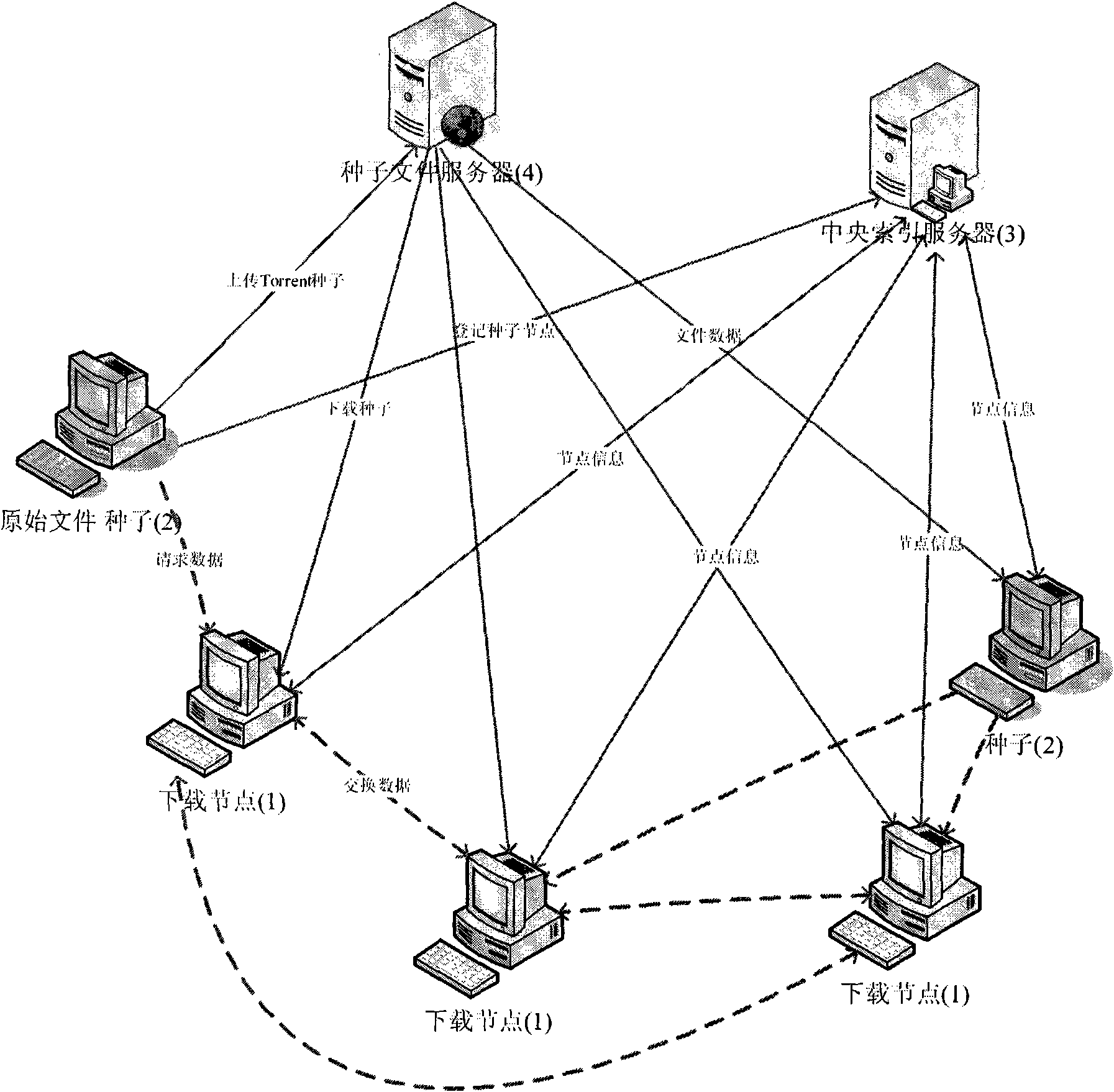
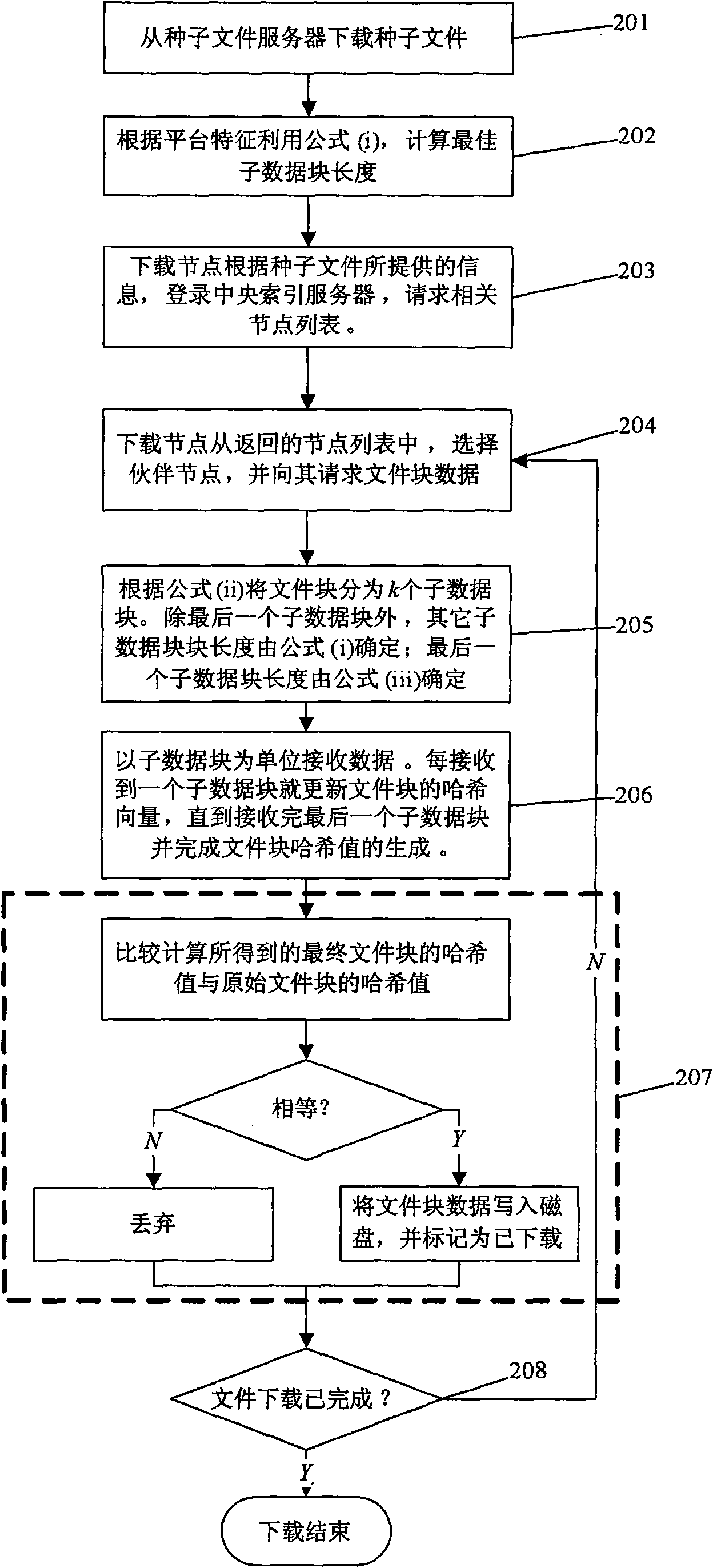
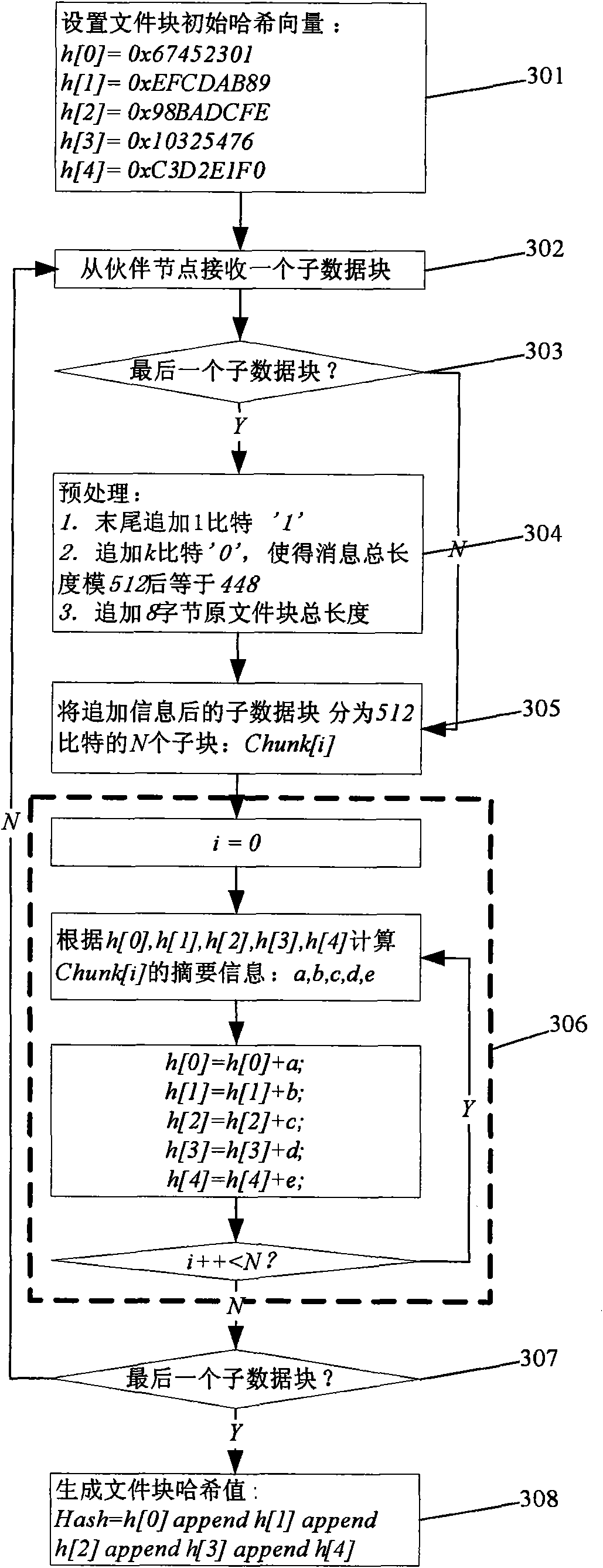
The invention relates to a method for calibrating integrity of P2P download files. The method comprises the following steps: dividing file blocks into sub data blocks according to characteristic parameters of a download client; when receiving a sub data block, calculating a Hash abstract of the sub block by using Hash algorithm and updating Hash vectors of a new file block; when downloading and calculating Hash values of last sub block, generating Hash values of file block immediately; and hiding delay of integrity calibration of files during download process. The invention uses a TCP asynchronous receiving buffer region so that delay of calibration during P2P download process can be hidden completely, the efficiency of P2P download is improved effectively, especially the efficiency of P2Pdownload on an embedded platform is improved. Furthermore, the invention is independent from specific calibration frame or protocol. Specially, core thought of the method can be applied directly to prior P2P download protocol, for instance eMule protocol and BitTorrent protocol, which has greater practicability.
Owner:ZHENGZHOU SEANET TECH CO LTD
Heterogeneous wireless peer-to-peer (P2P) network file sharing system and file transmission acceleration method
InactiveCN102594926AEasy to shareImprove the acceleration functionTransmissionStructure of Management InformationHeavy load
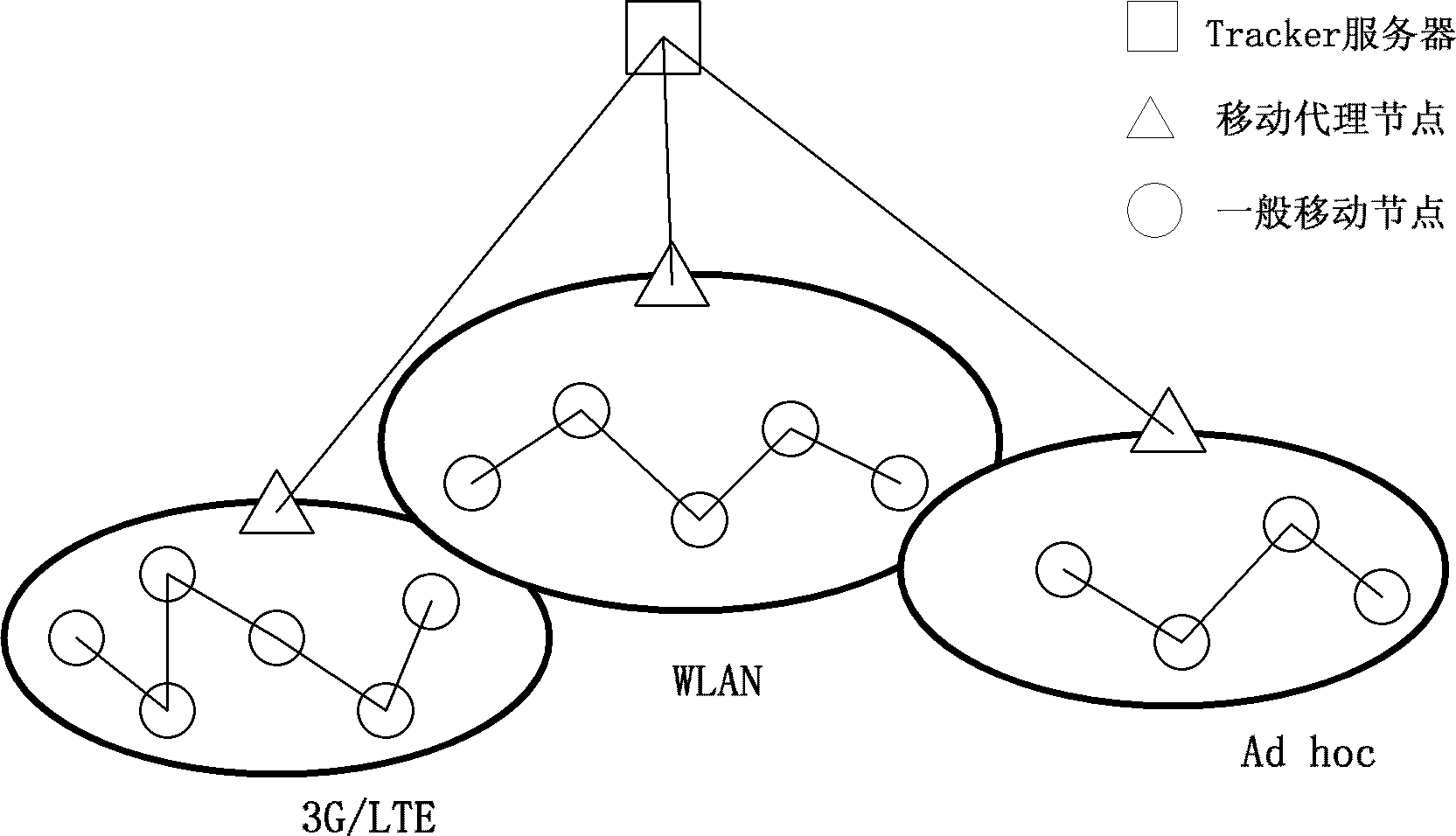
The invention discloses a heterogeneous wireless peer-to-peer (P2P) network file sharing system and a file transmission acceleration method. In a heterogeneous wireless fusion network access environment, factors such as an access network type, a terminal node downloading rate, an inter-node network distance and round-trip time are comprehensively combined for the characteristics of a fusion network, and a seed node is selected by utilizing an optimization theory in engineering to provide an acceleration method for a file sharing service of a terminal on the basis of an extended P2P-Bittorrent protocol. A proper seed node is selected, and a network service with high data traffic and a heavy load is transferred into an idle network, so that the load balance of the whole network structure is realized, and the resource efficiency of a plurality of heterogeneous fusion networks is optimized.
Owner:HUAZHONG UNIV OF SCI & TECH
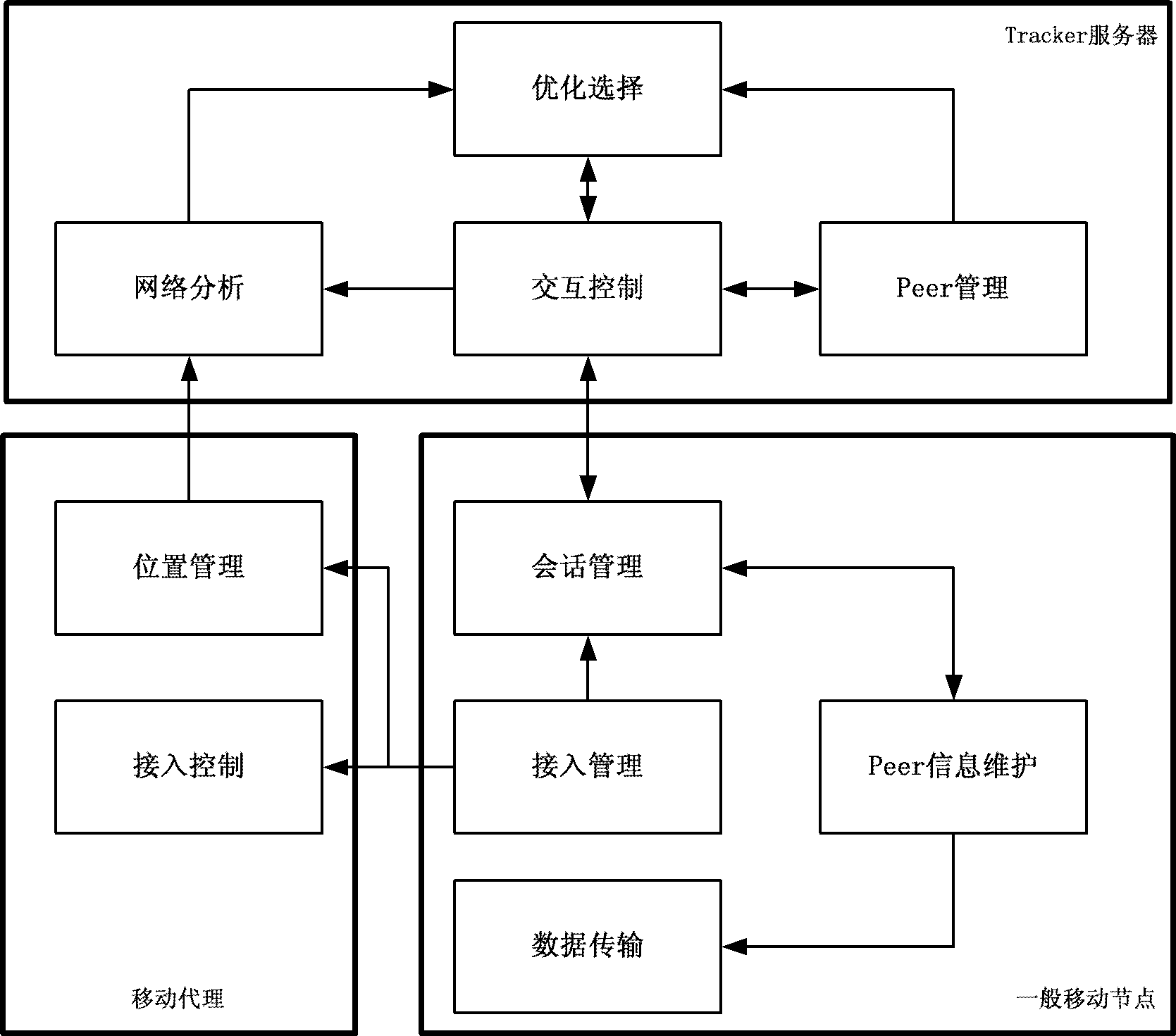
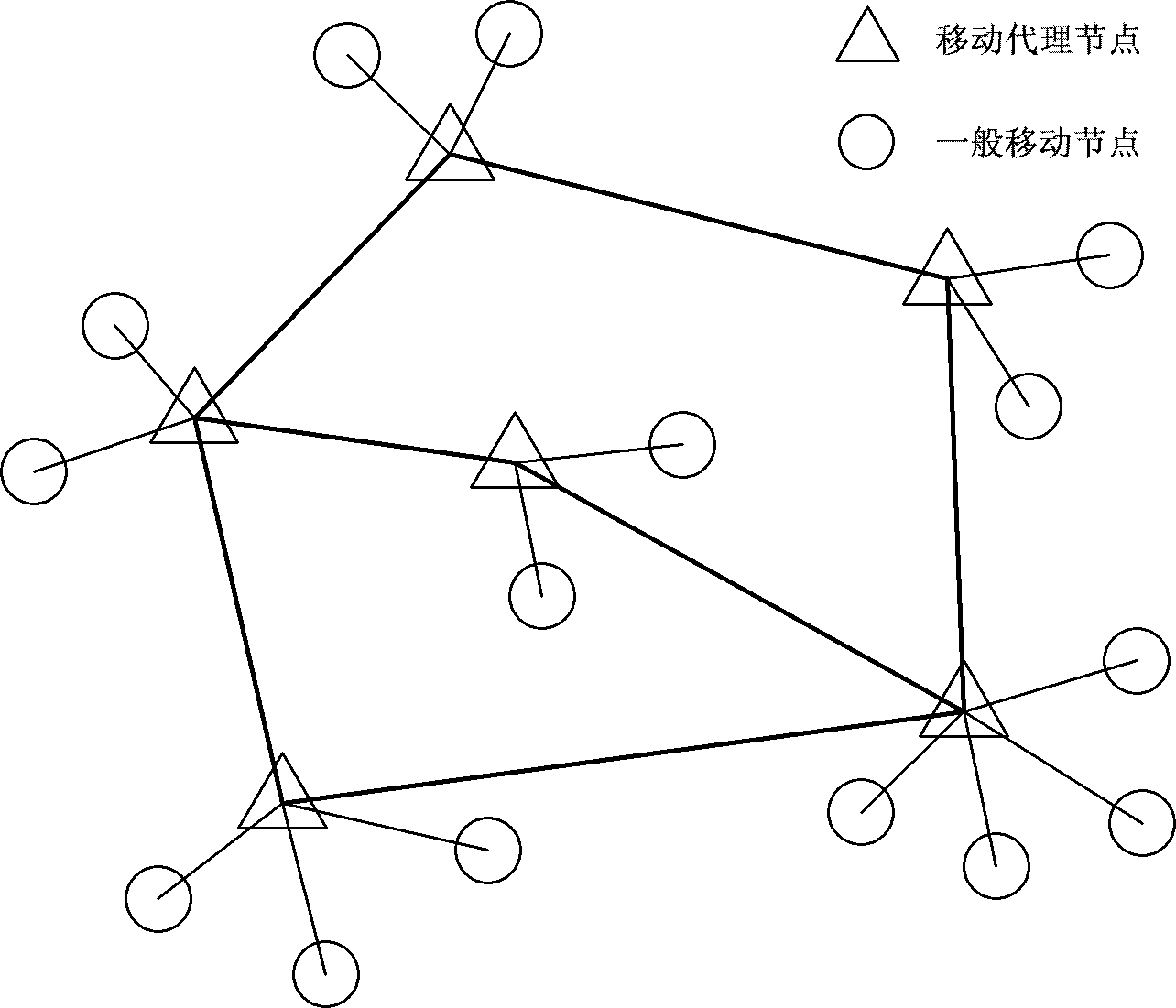
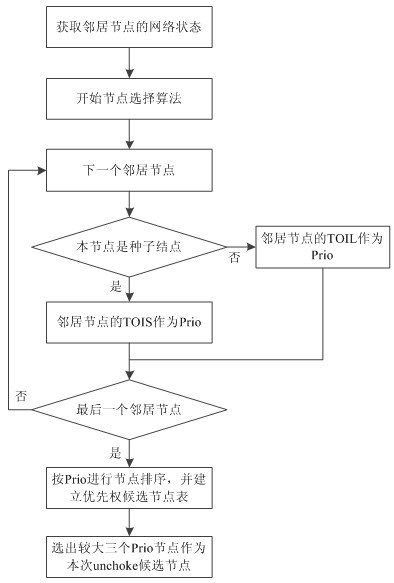
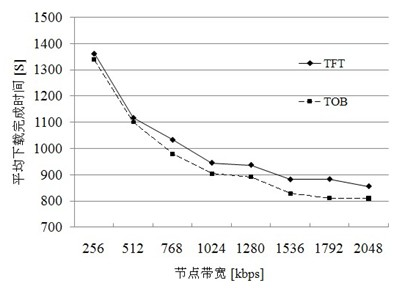
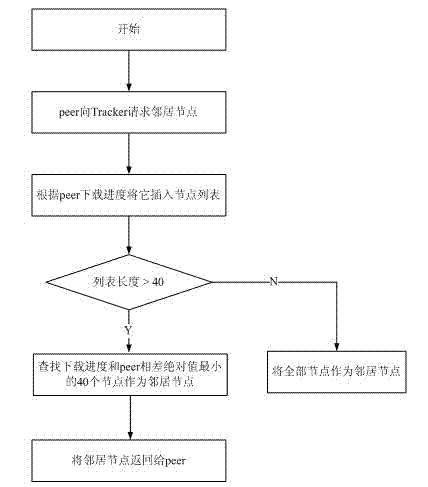
BitTorrent node selecting method based on node performance
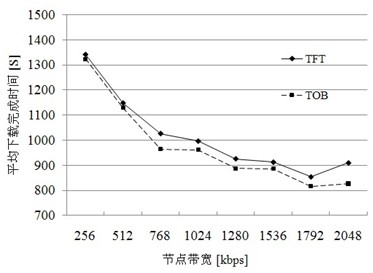
The invention discloses a BitTorrent node selecting method based on node performance. A BitTorrent node selecting strategy suitable for differentiated node network states is proposed in the method, network delay of a node, bandwidth and network contribution of the node are used as the basis of a node selection algorithm unchoke in the policy, file uploading service is preferentially provided for an adjacent node with low delay, high bandwidth and great contribution, and the bandwidth of the node with the favorable performances is effectively utilized, so that the average file downloading time is shortened finally. A simulation experiment proves the effectiveness of the strategy and shows that sharing files at high efficiency in a P2P (Point-to-Point) way can be realized under the conditions of fluctuated delay and limited bandwidth by using the policy.
Owner:ZHEJIANG UNIV
Media file distribution system and method
ActiveUS8122488B2Maintaining security and controlAvoid accessDiscounts/incentivesDigital data processing detailsDistribution methodIp address
Owner:YANGAROO
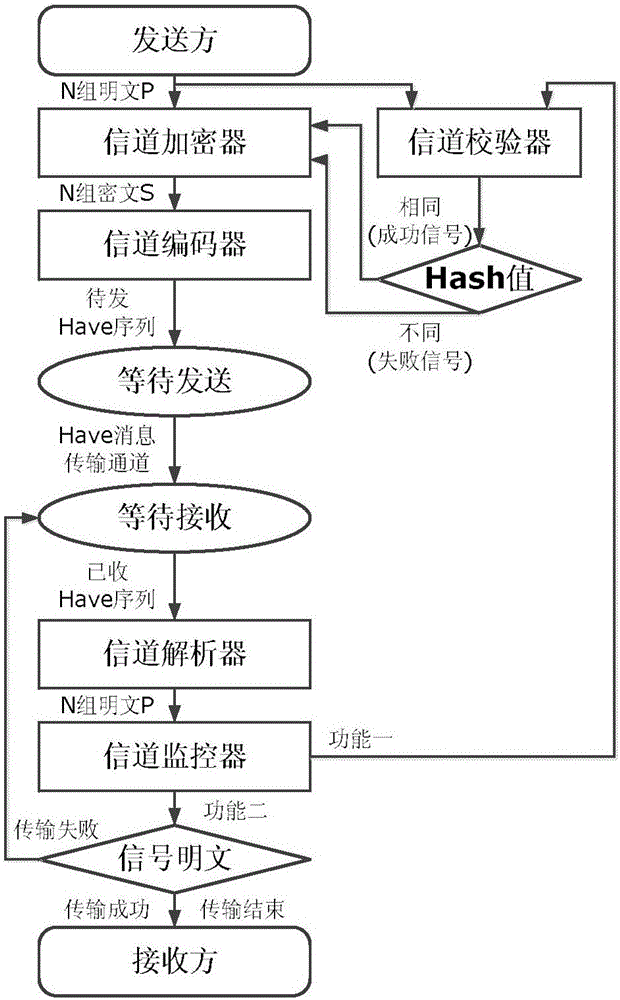
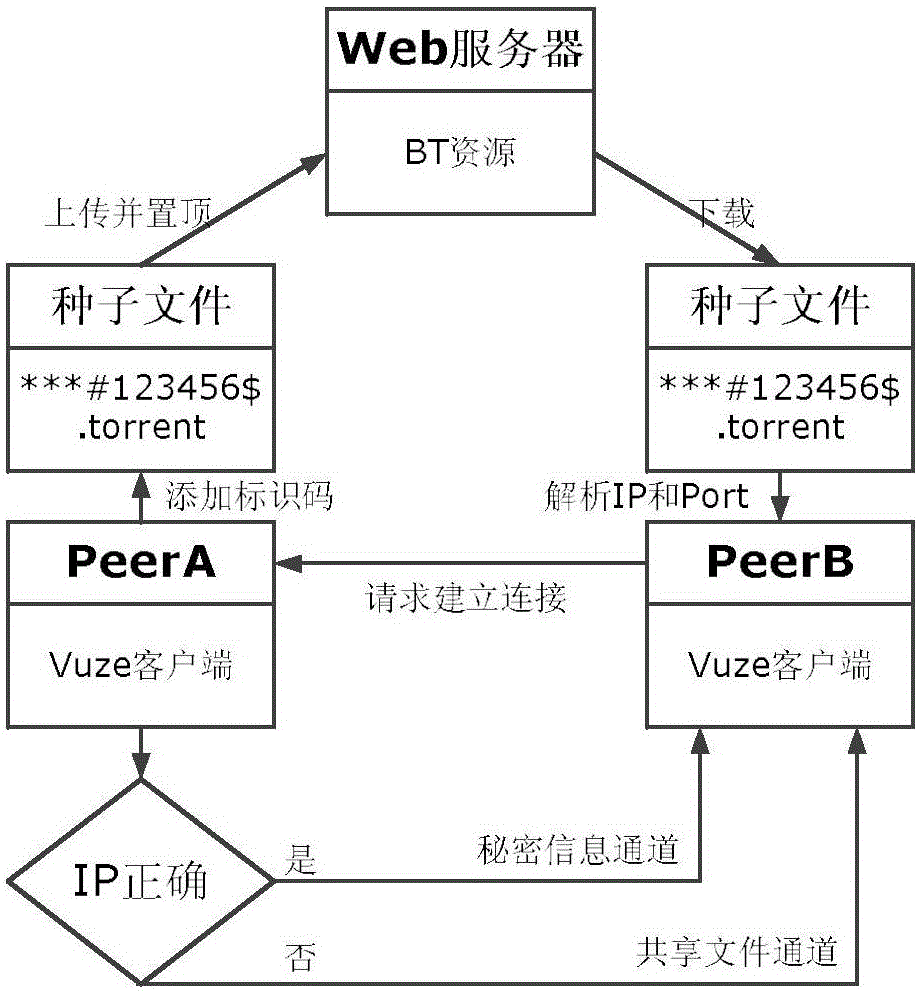
Secret information transmission method based on BitTorrent protocol Have message
ActiveCN105763317AConducive to efficient transmissionImprove concealmentEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareInformation transmission
The invention belongs to the computer network and information safety technology field and mainly discloses a secret information transmission method based on a BitTorrent protocol Have message. A transmission channel of the BT protocol Have message is taken as a basic-construction hidden channel. According to secret information coding, a sequence of the Have message in an Have message sequence is adjusted so as to complete embedding of secret information so that the secret information is transmitted along with the Have message. In the invention, during BT protocol Have message sorting, an information coding technology is introduced to construct the hidden channel; transmission of the secret information is simple and high-efficient; an extra communication load brought for an existing Have message channel is avoided; and an information coding position circulation shift mechanism and an information verification mechanism are introduced so as to further increase concealment and robustness of secret information transmission.
Owner:JIANGSU UNIV OF SCI & TECH
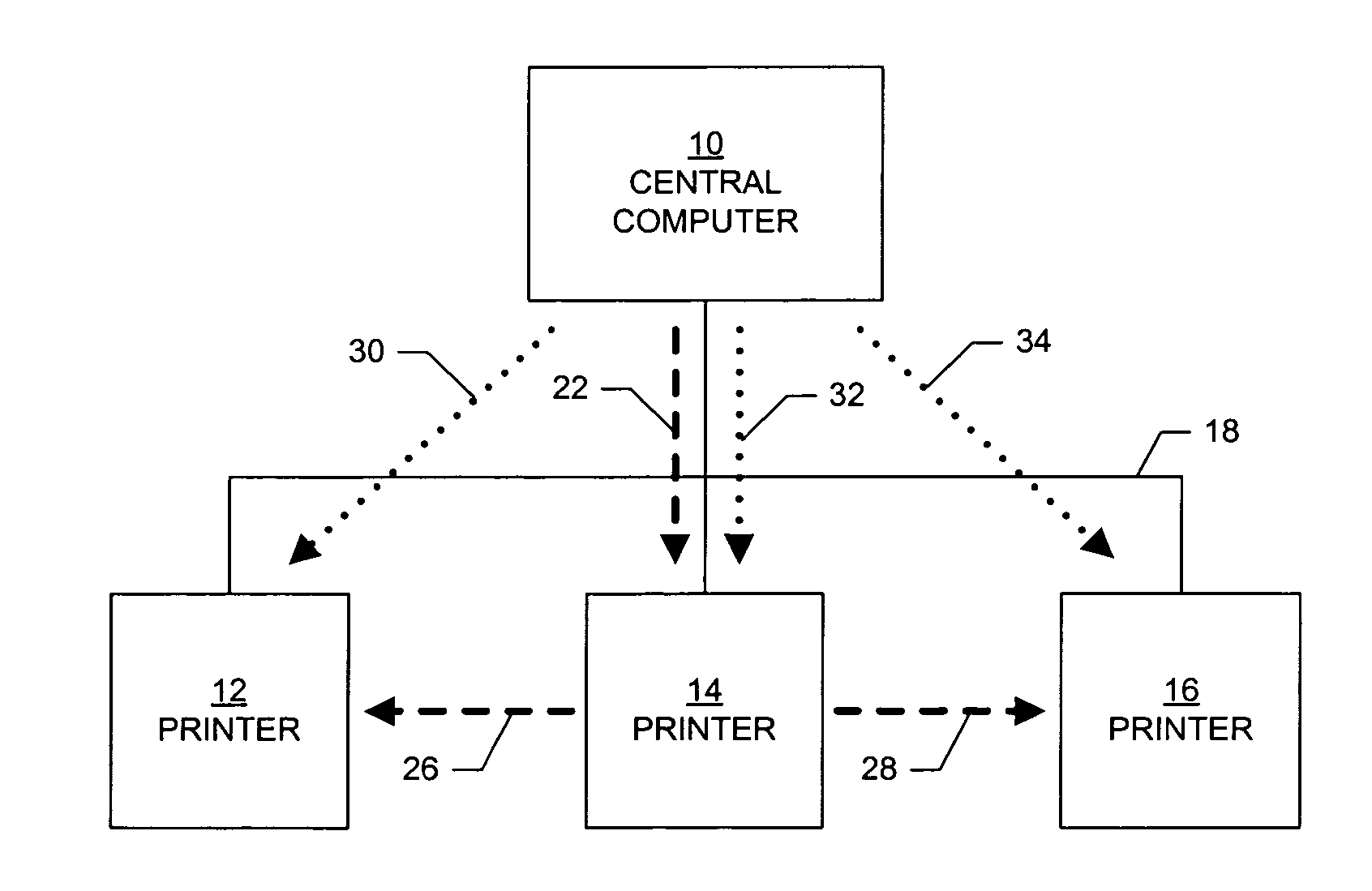
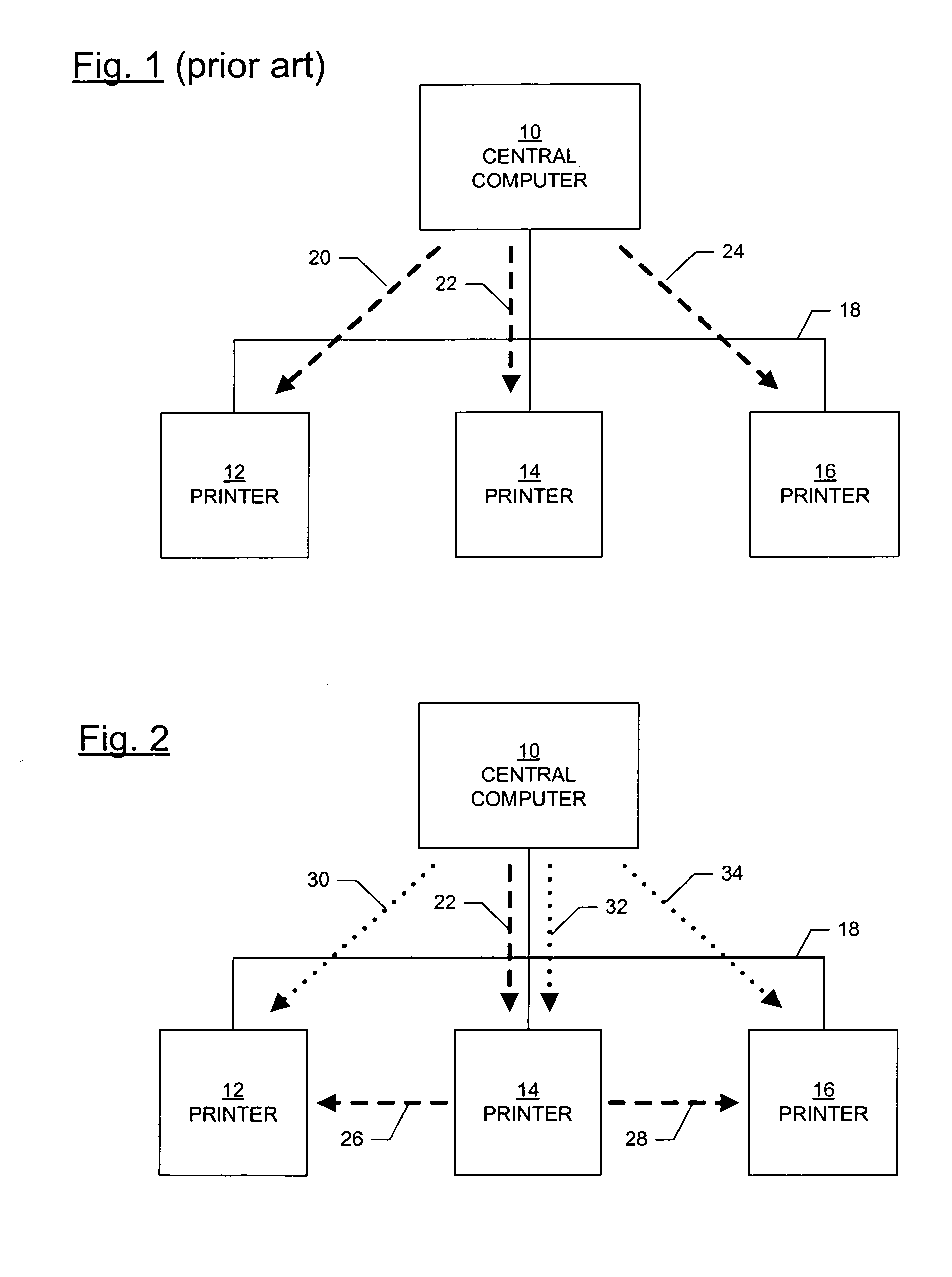
System, printer, and method for distributing data to a plurality of printers
InactiveUS20070013941A1Fast transferData is very largeTransmissionPictoral communicationData packComputer printing
A system, printer, and method utilize a peer-to-peer packet sharing protocol that enables a large data file to be quickly and efficiently transferred to a large number of printers. A system for distributing data to a plurality of printers comprises a computer connected to a network, a first printer connected to the network, and a second printer connected to the network. The computer transmits a data packet over the network to the first printer. The first printer and the second printer each execute a peer-to-peer packet-sharing protocol, such as the BitTorrent Swarmcast, and Swarmstreaming protocols. The first printer transmits the data packet to the second printer.
Owner:ZIH CORP
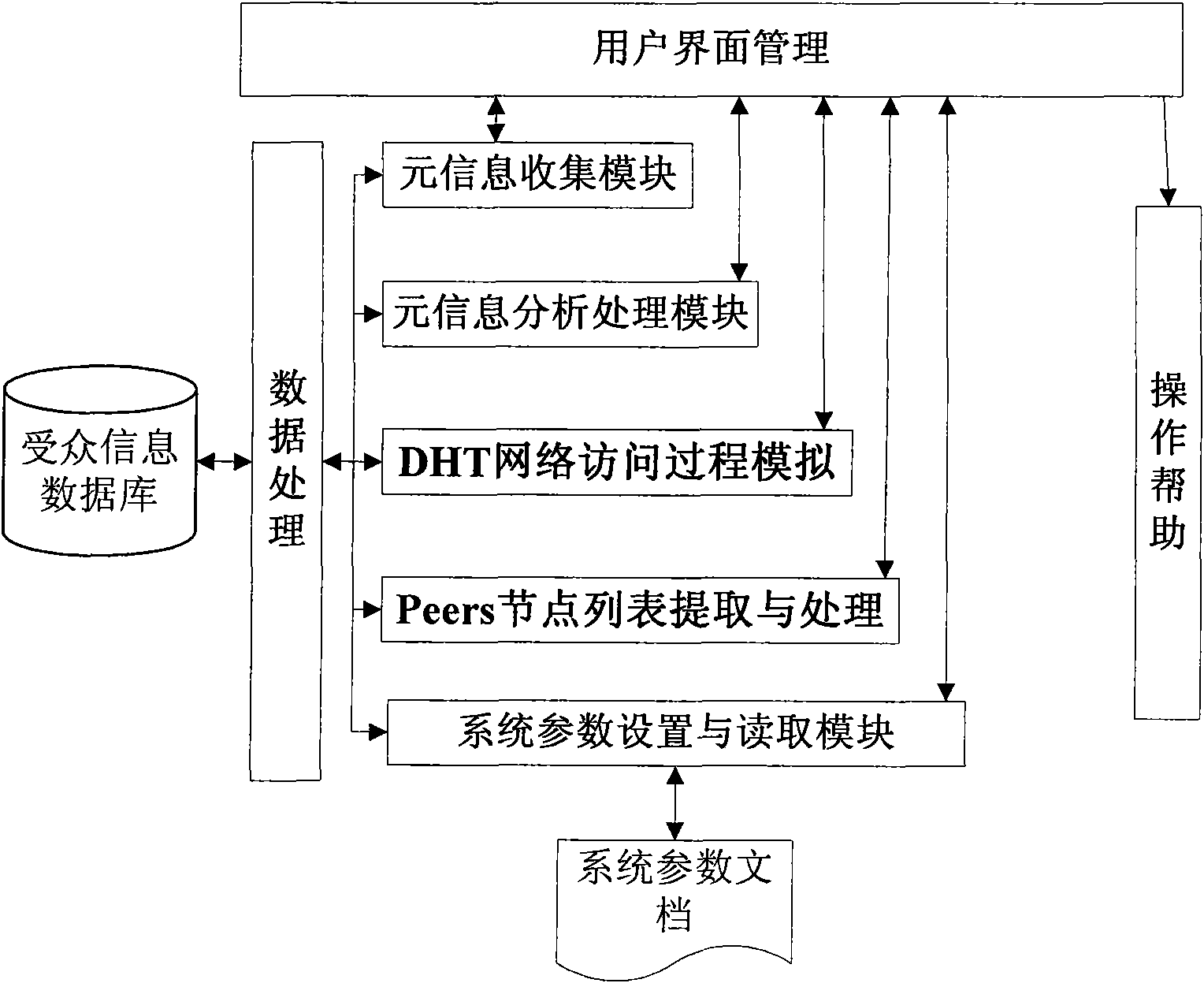
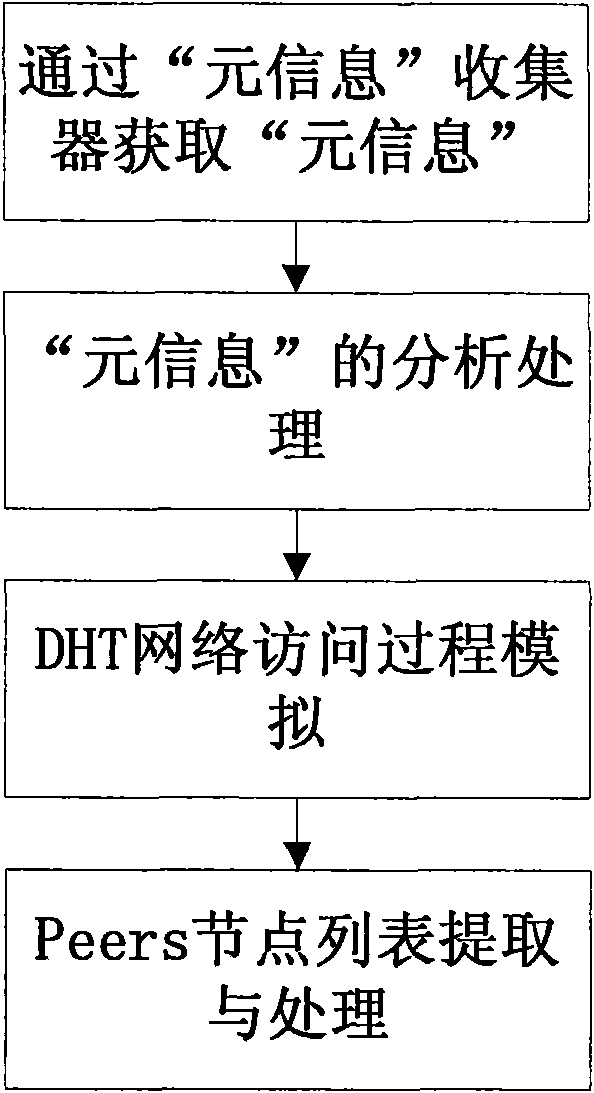
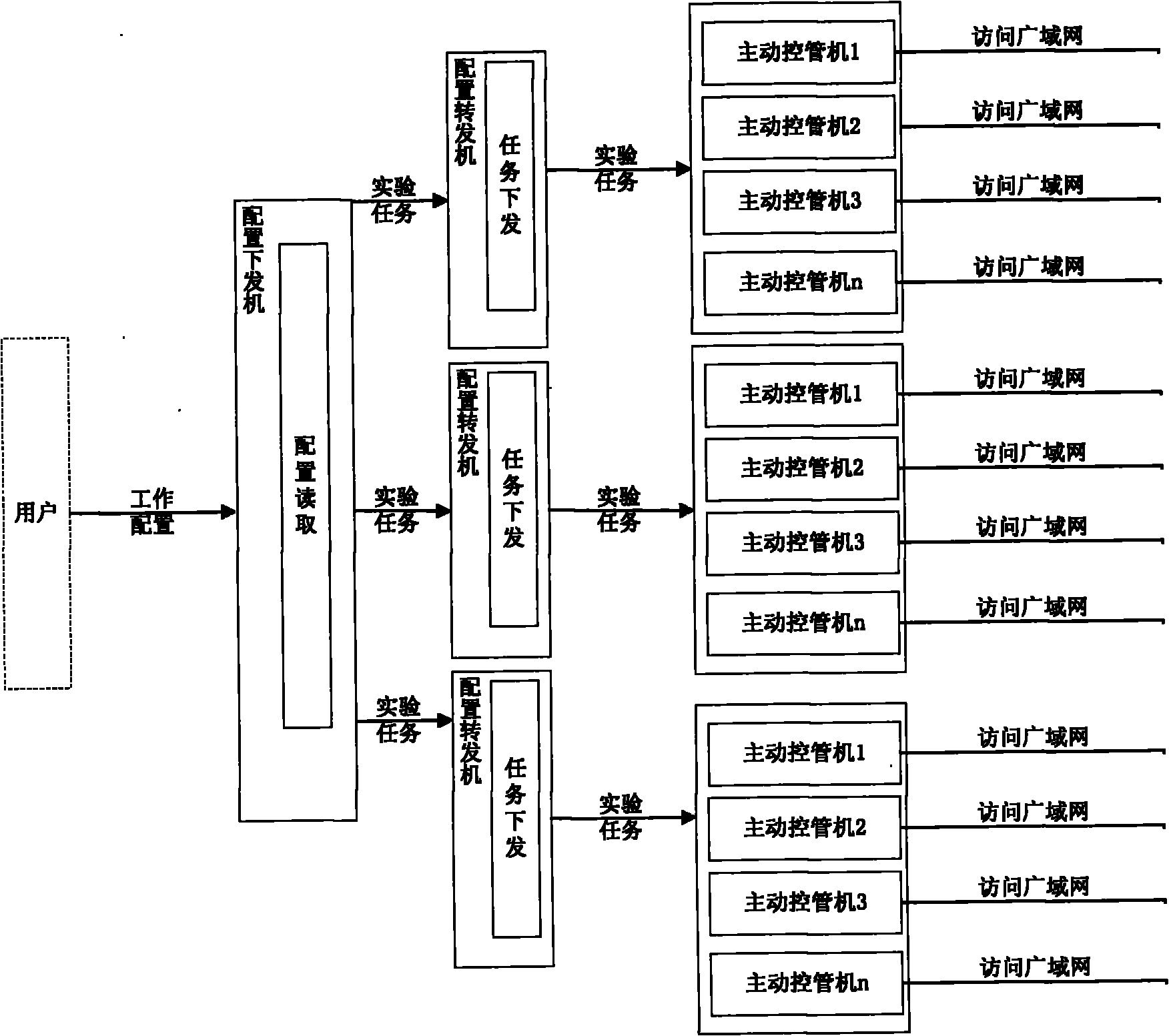
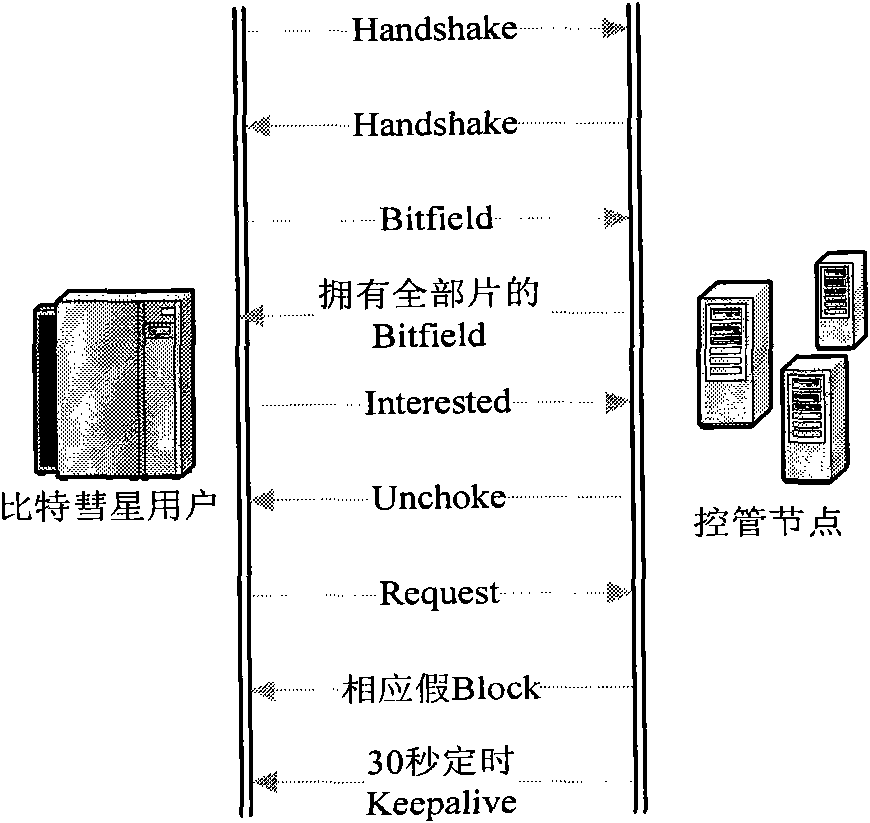
Active type specific information transmission monitoring method based on BitTorrent
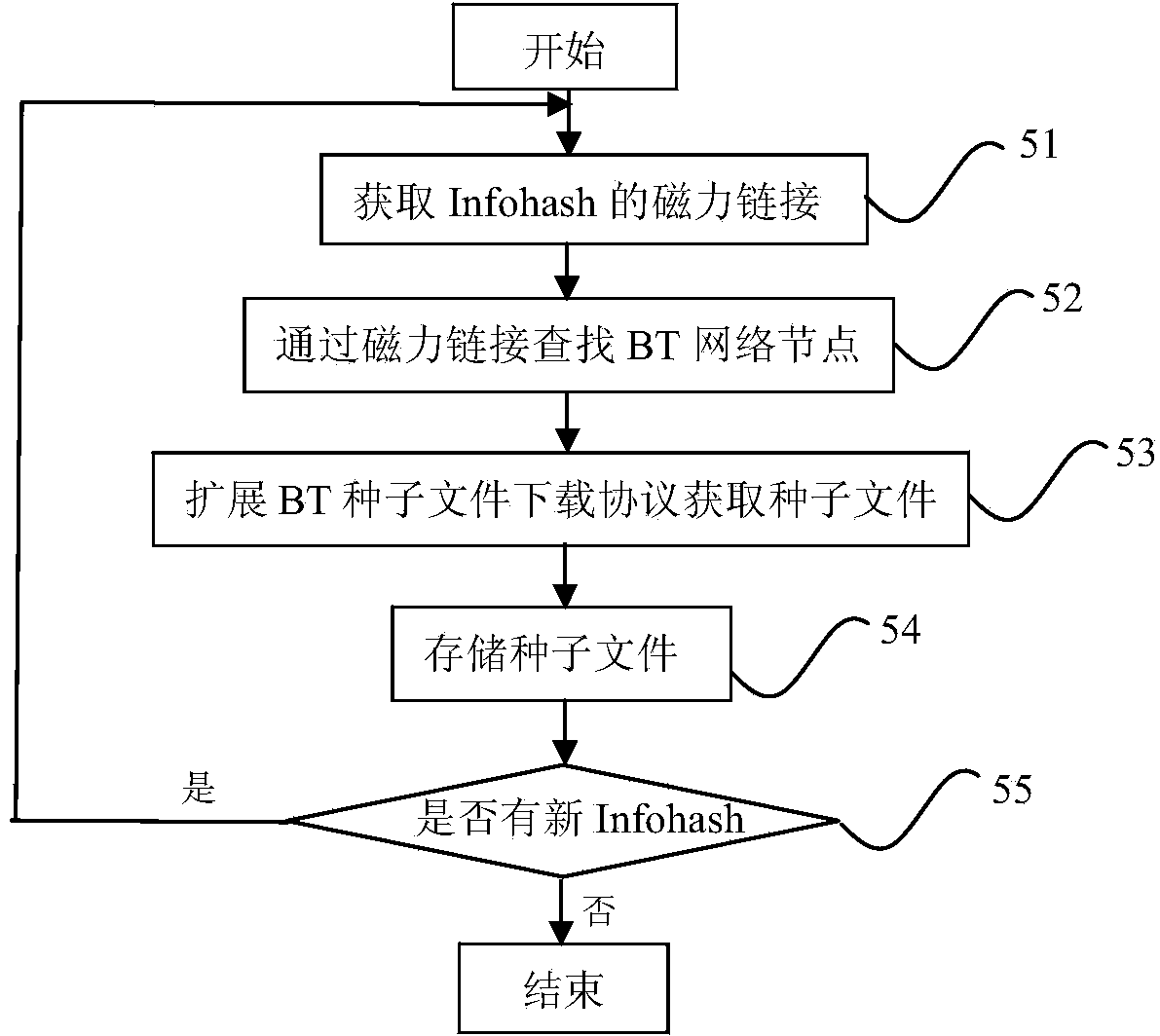
ActiveCN101567811AResolve spreadSolve the monitoring problem of its audienceData switching networksInformation dispersalType specific
The invention discloses an active type specific information transmission monitoring method based on BitTorrent. Metainformation is read from a system by a metainformation collector; the metainformation obtained by the metainformation collector is analyzed; an analog data packet is actively sent to a fake client to obtain audience information; and through simulation of a DHT network accessing process, a Peers node list is extracted and processed. As the analog data packet is actively sent to the fake client to obtain the audience information, the audience information can be obtained as much as possible; and compared with the prior art, in the method, through the search and the obtaining of the metainformation of BitTorrent in the internet, the fake client obtains the audience information participating in the transmission of the specific information and forms a specific information transmission audience database so as to provide an audience information monitoring and evidence-obtaining means for a network security supervision department and provides basic data and decision-making basis for the macroanalysis and prewarning prediction of the network security situation.
Owner:JIANGSU HUAYI GARMENT CO LTD +1
System for downloading files based on Bittorrent protocol
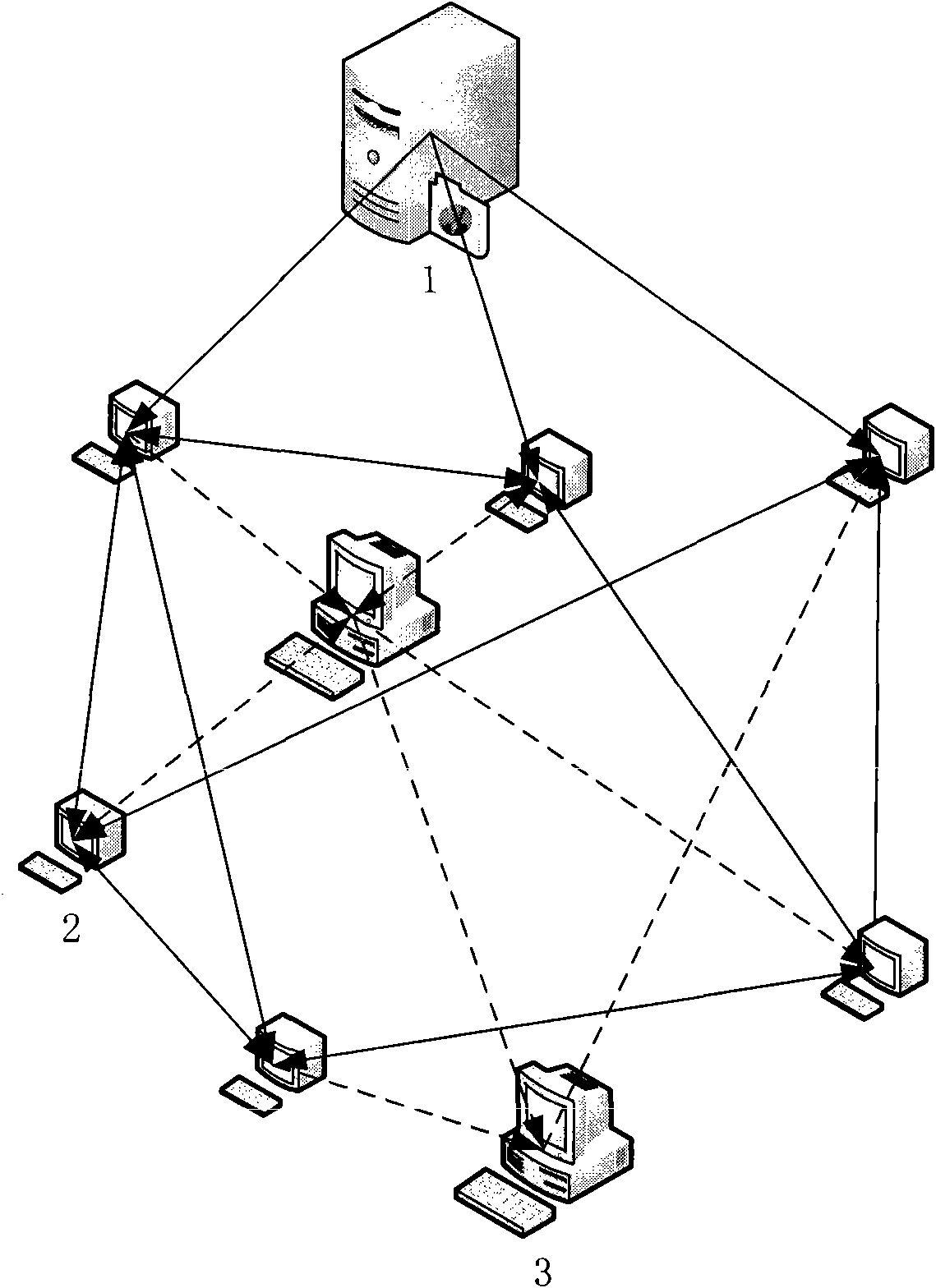
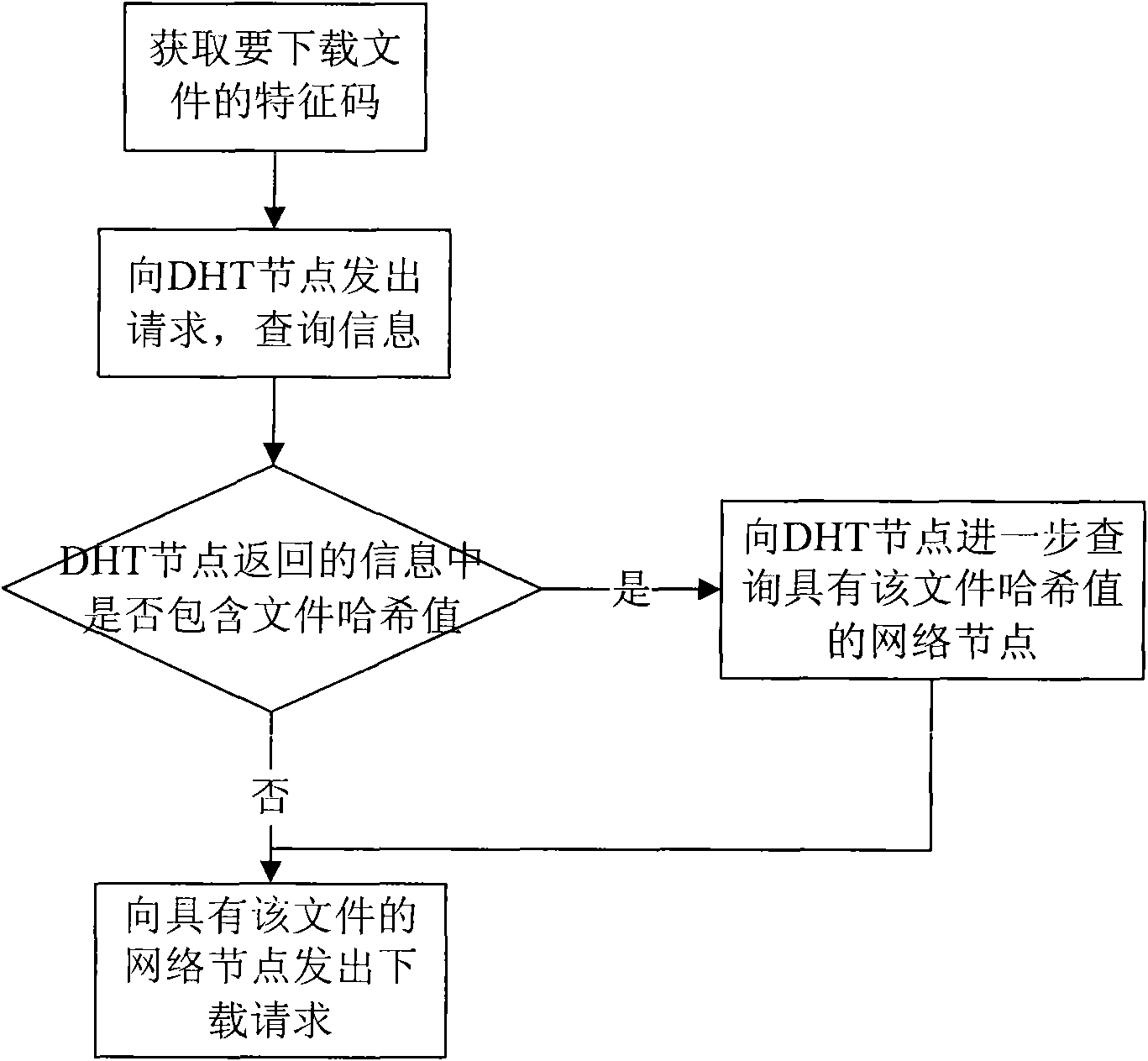
InactiveCN101626397ARelieve pressureTake advantage ofSpecial service provision for substationComputer networkBitTorrent
The invention provides a system for downloading files based on Bittorrent protocol so as to realize the aim that the resources of a server such as a FTP or HTTP server are introduced to the form of Bittorrent protocol; the system comprises a network set according to the Bittorrent protocol and network nodes used to connect the network; wherein, the network nodes comprise common nodes, DHT nodes arranged and distributed in the network and server nodes; the server nodes perform the following steps: receiving a download request from a common node and transferring a file block unit which is requested to download to the common node. A common upload module is arranged on each common node, and the common upload module is used to receive the download requests from other common nodes and sent the file block units which are requested to download to the corresponding to common nodes. Message retain modules are arranged on the DHT nodes to record the information of files which can be downloaded in the network nodes.
Owner:POWERLAYER MICROSYST HLDG
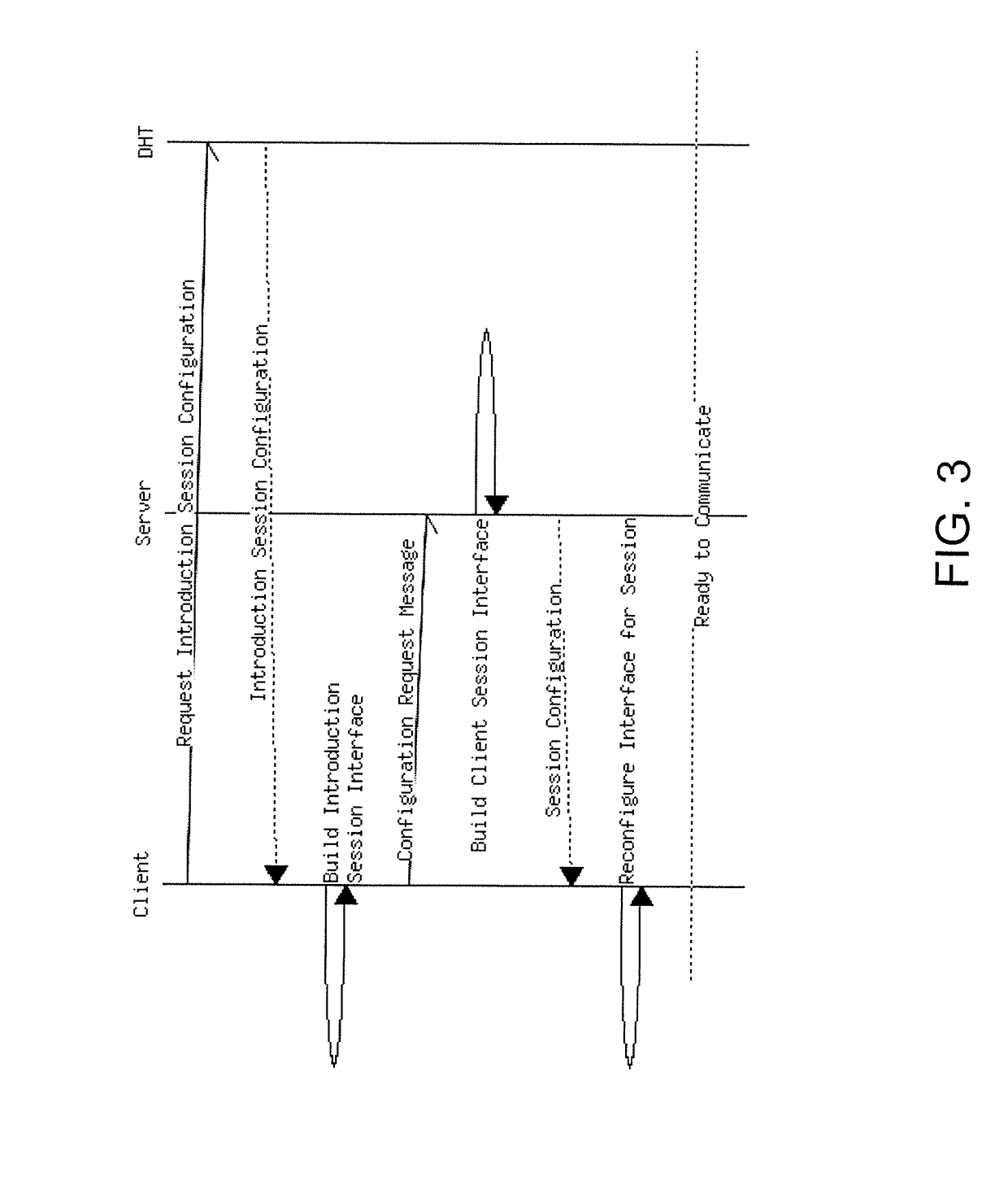
Process and system for establishing a moving target connection for secure communications in client/server systems
ActiveUS20170272242A1Avoid detectionImprove securityKey distribution for secure communicationMultiple keys/algorithms usageKey exchangeSecure communication
A system and method performs a moving target blind rendezvous by exchanging data through a distributed hash table. The system allows users to securely send small pieces of information over a network while only requiring an exchange of public keys ahead of time. The system relies on the size and resilience of the BitTorrent Distributed Hash Table and the security properties of cryptographic constructions such as Elliptic Curve Diffie-Hellman key exchange and secure one-way hash functions.
Owner:VIRGINIA TECH INTPROP INC
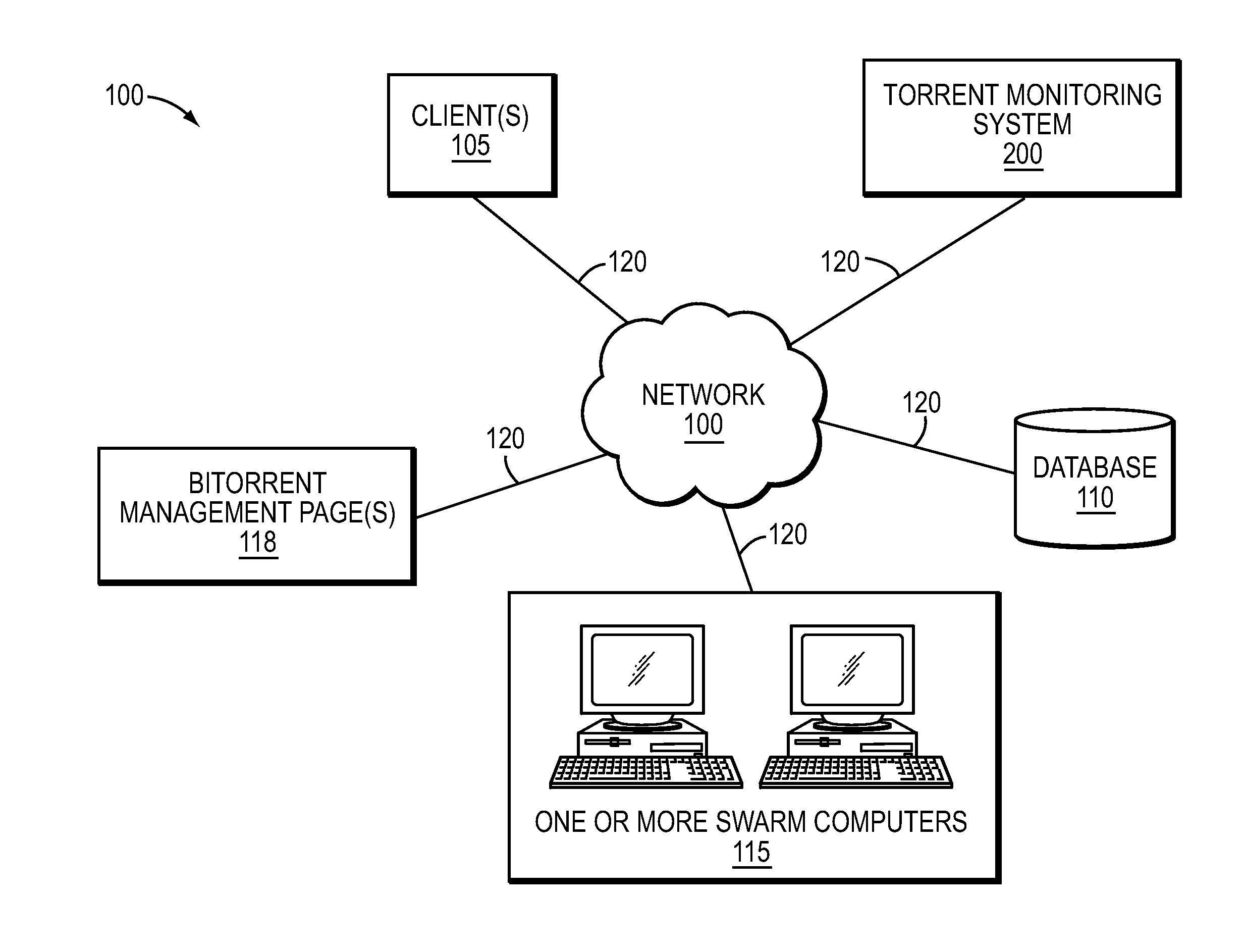
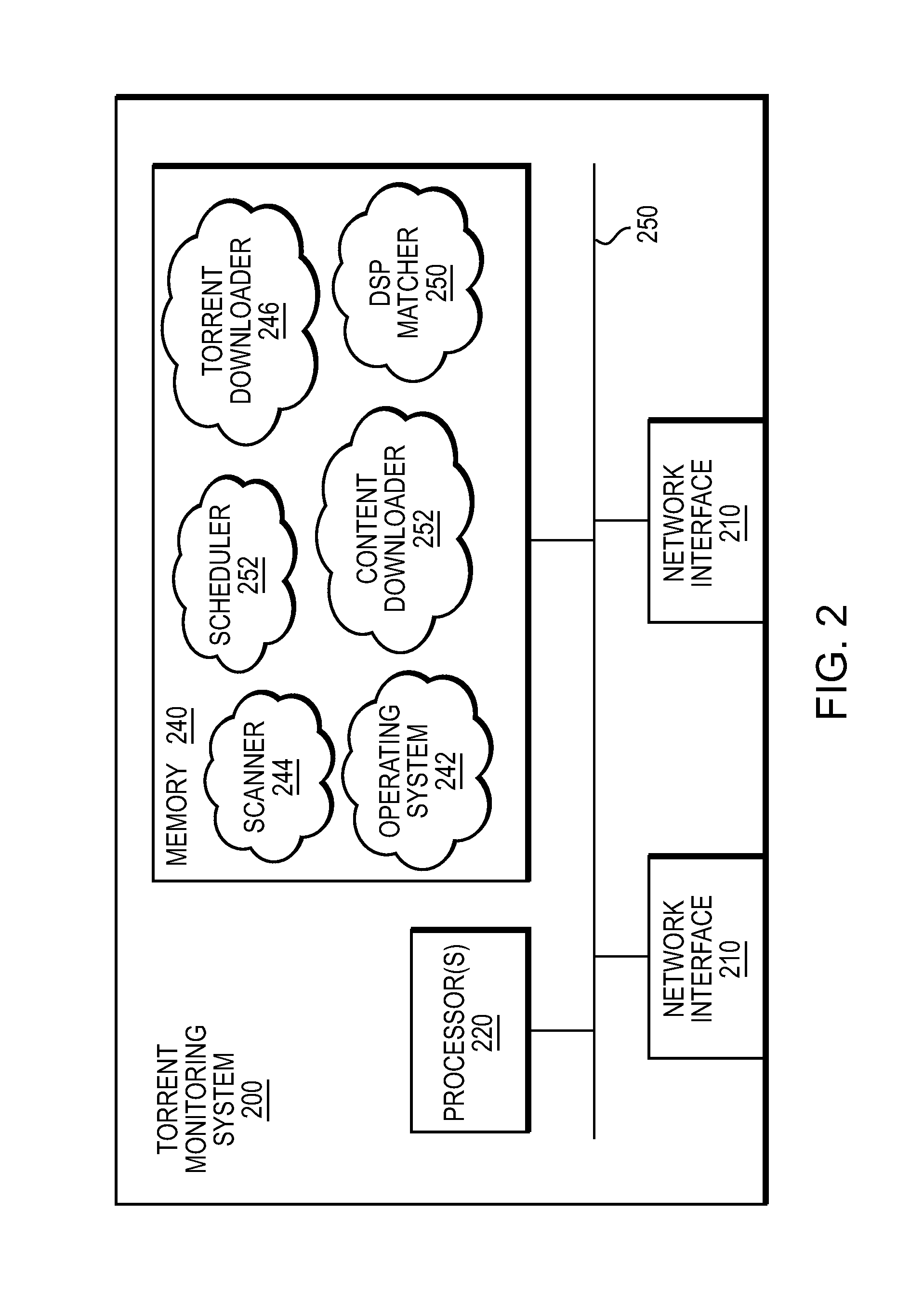
System and method for monitoring bittorrent
ActiveUS20140025728A1Effective monitoringData switching networksSpecial data processing applicationsClient-sideSearch terms
In one embodiment, one or more BitTorrent management pages, such as an index site or a Rich Site Summary (RSS) feed, may be scanned for indicia of a torrent file that is associated with one or more search terms. After the torrent file is located, information associated with the torrent file may be utilized to initiate the downloading of one or more portions of the content indicated by the torrent file over a network from swarm computers utilizing a BitTorrent Protocol. As the content is being downloaded from the swarm computers, identification information associated with each swarm computer may be obtained. Data associated with the torrent file and the identification information may be stored at a database. Thereafter, a client may search the database to locate one or more swarm computers that may be sharing, for example, unauthorized or illegal information.
Owner:KROLL INFORMATION ASSURANCE LLC
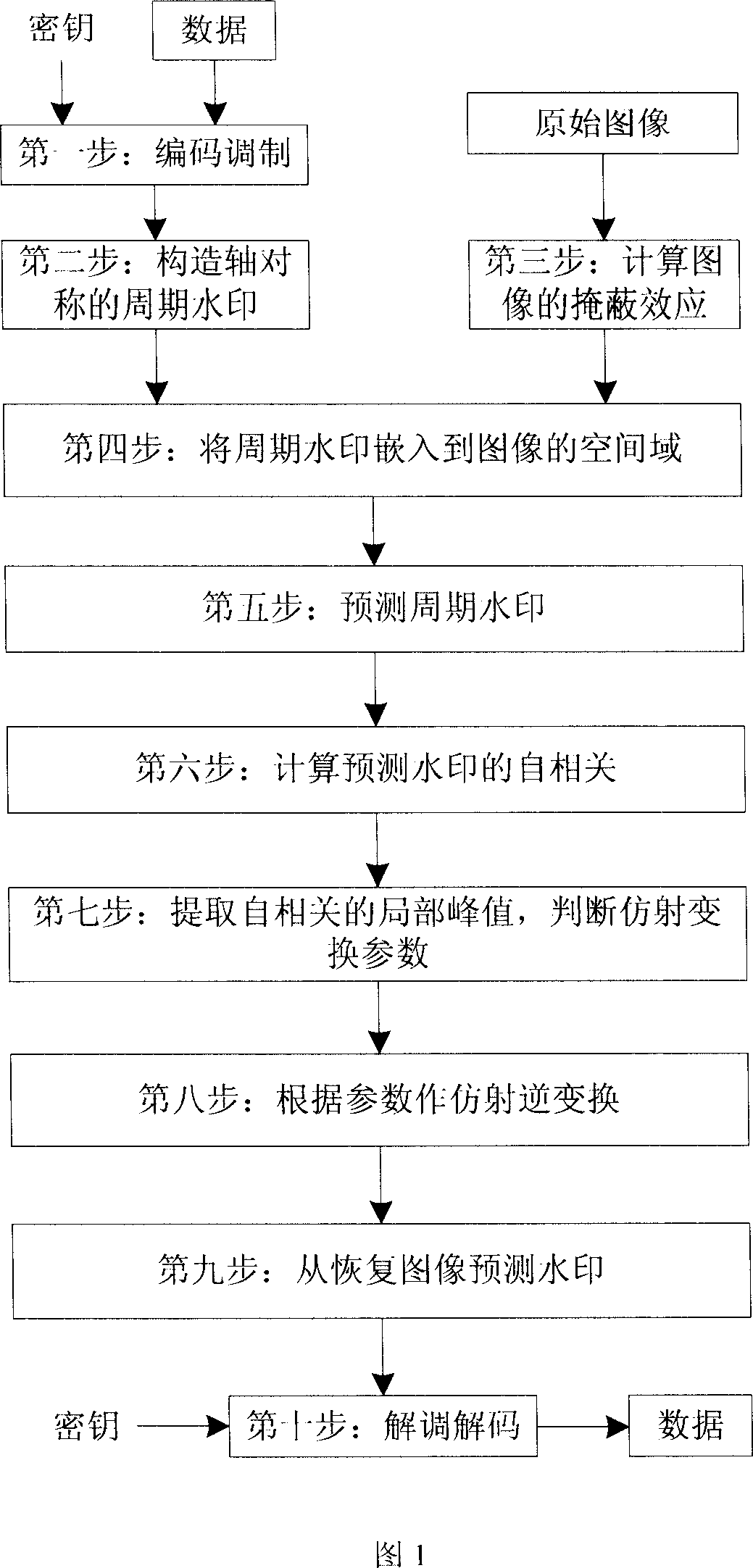
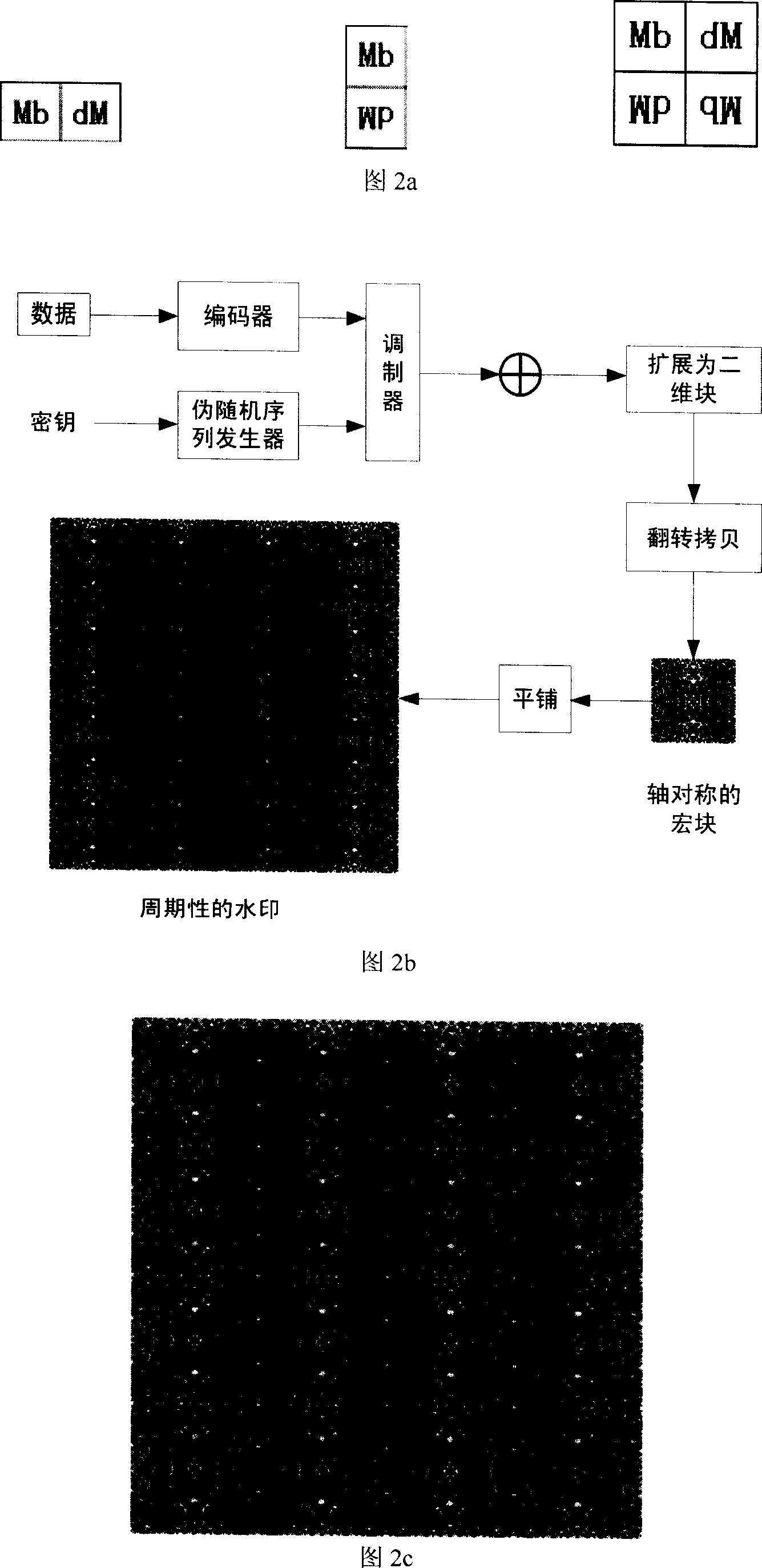
Method for embedding bittorrent Robust digital figure watermark and testing method and apparatus
ActiveCN1971613AEliminate the effects ofReliable synchronization informationImage data processing detailsPattern recognitionTransformation parameter
A detecting method and device for the embedding of bit flow robust digital image watermark are disclosed that belongs to the digital image watermark technique, the data is embedded in the digit image and can be extracted accurately, even if the picture is processed by image operation, for example, magnification, contraction, rotating, inverting, mirroring, printing-scanning and so on. It includes two parts of embedded digit watermark and detecting digit watermark. A method and device for embedded digit watermark include: the data is encoded and modulated, and the encoded signal form an axial symmetry cycle watermark are embed into the digit image self-adaptively. The method and device for detecting the watermark include: calculating the auto-correlation function of forecasting watermark, judging the affine transformation parameter which the image undergo by the coordinate of auto-correlation function local peak value, and recovering the image according to the parameter. Finally, forecasting the watermark from the recovered image, and the data is extracted after demodulation and decoding.
Owner:HUAQI RES INST OF IMAGE COMPUTING
Peer-to-peer download and seed policy management
Transfer policy management methods in a peer-to-peer networking environment such as BitTorrent are provided. A download TPM maximizes the usage of available bandwidth, while focusing on as few torrents as possible. For a given list of torrents, a peer in accordance with the present invention determines how many download connections to maintain at a given time in order to maximize usage of bandwidth. If the variance of per-connection bandwidths exceeds a threshold, more connections are added until either variance does not exceed the threshold or a maximum number of connections are established. A seeding peer determines when to reduce the number of files being seeded by monitoring its average upload rate per torrent. If its average rate falls below a threshold, then the peer stops seeding a file. The file that the peer stops seeding is one to which the peer is making the smallest overall contribution.
Owner:BITTORRENT
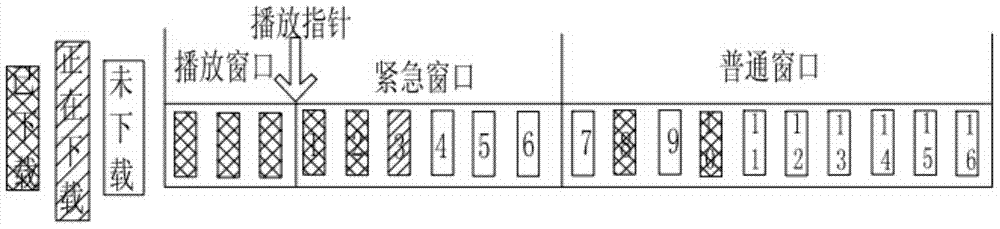
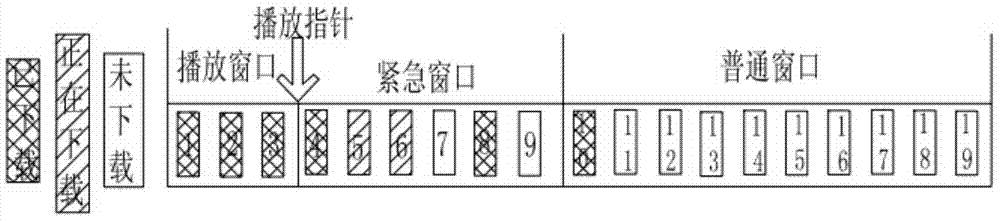
Hybrid data scheduling method for P2P (peer to peer) systems
InactiveCN104506929ASmooth playbackImprove distributionSelective content distributionSlide windowMedia on demand
The invention discloses a hybrid data scheduling method for P2P (peer to peer) systems and relates to the technical field of broadcasting application devices or methods directly related to broadcast information or broadcast time and space. According to the method, a required data window in the P2P video-on-demand system is divided into a playing window, an emergency window and a common window, and nodes in the P2P video-on-demand system can acquire data from a film source server and can also share data with other nodes; meanwhile, a BitTorrent protocol is introduced to a streaming media video-on-demand service, and the nodes communicate with other nodes through the modified BitTorrent protocol. The BitTorrent protocol has the priority of downloading fewest data blocks, thus distribution of the data in a whole network is improved; data transmission with limited playing time is not supported. According to the method, emergency data is downloaded prior through a sliding window. The method has the advantages that downloading speed is increased and the P2P video-on-demand system plays more smoothly.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Hot seed file acquisition method in BT (BitTorrent) network
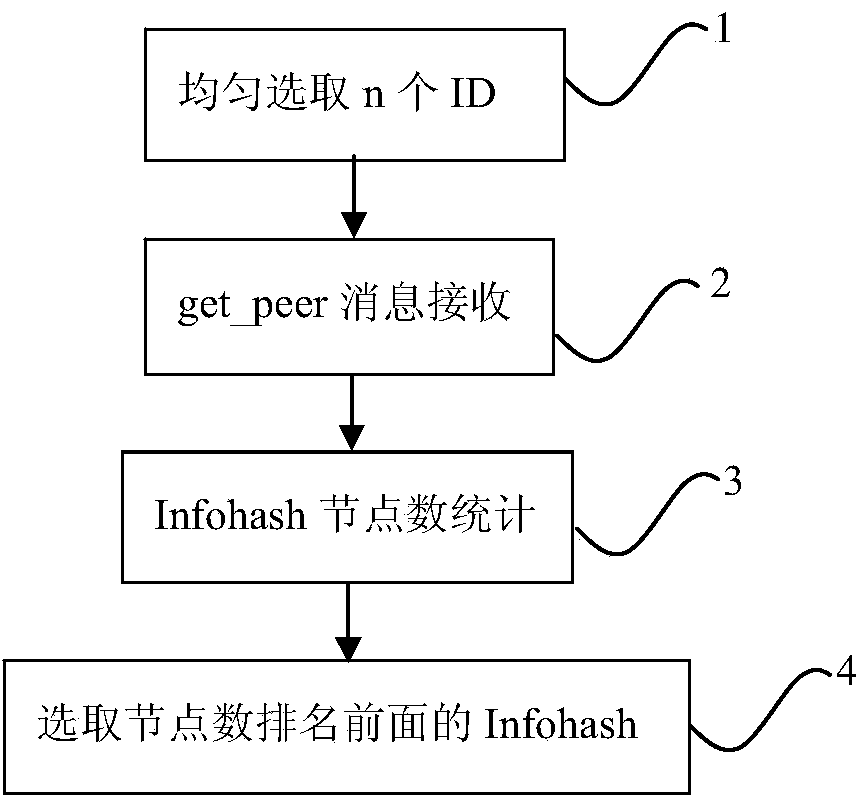
ActiveCN103533048AAccurate acquisitionHelps download node adjustmentsTransmissionClient-sideDistributed computing
The invention provides a hot seed file acquisition method in a BT (BitTorrent) network. The hot seed file acquisition method in the BT network comprises the following steps of 1) constructing a plurality of virtual BT client sides, wherein the IDs (Identity) of the virtual BT client sides are evenly distributed in a BT network ID logic space; 2) monitoring get_peers messages in the BT network by each virtual BT client side, and calculating the number of received get_peer messages corresponding to each infohash; 3) calculating the number of the get_peer messages which are received by all virtual BT client sides and correspond to each infohash in a fixed time; according to the number of the get_peer messages, determining whether the corresponding infohash is hot infohash or not. After adopting the hot seed file acquisition method in the BT network, which is disclosed by the invention, the hot seed files in the whole BT network range can be comprehensively and accurately obtained.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
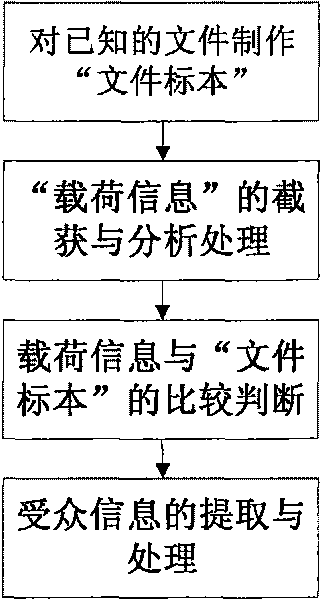
Passive load information monitoring method based on BitTorrent
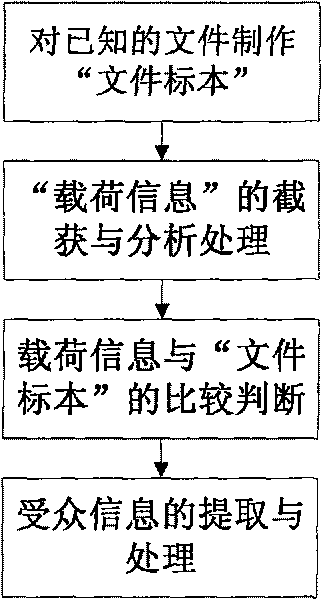
ActiveCN101719907AReduce processing timeAccurate acquisitionData switching networksComputer hardwareInformation dispersal
The invention discloses a passive load information monitoring method based on BitTorrent, which is used for monitoring and analyzing P2P network customizing information spreading and audiences thereof based on the BitTorrent. The method comprises the steps of: downloading required files into a local hard disk by using BitTorrent software; generating information of file samples according to existed file information; carrying out Hash processing on the information of file samples, carrying out Hash processing in load information; comparing the film samples subjected to the Hash processing with the load information subjected to the Hash encryption; comparing the load information with the load samples by adopting a character string matching method for judging; and extracting and processing obtained audience information. Because of adopting the way of carrying out the Hash encryption on the captured load data, the mode matching is carried out on the data subjected to the Hash encryption without recovering original content of the files or considering the format of a transmitted file, a plenty of computer processing time is saved.
Owner:NANTONG CHANG RONG MECHANICAL & ELECTRICAL CO LTD +1
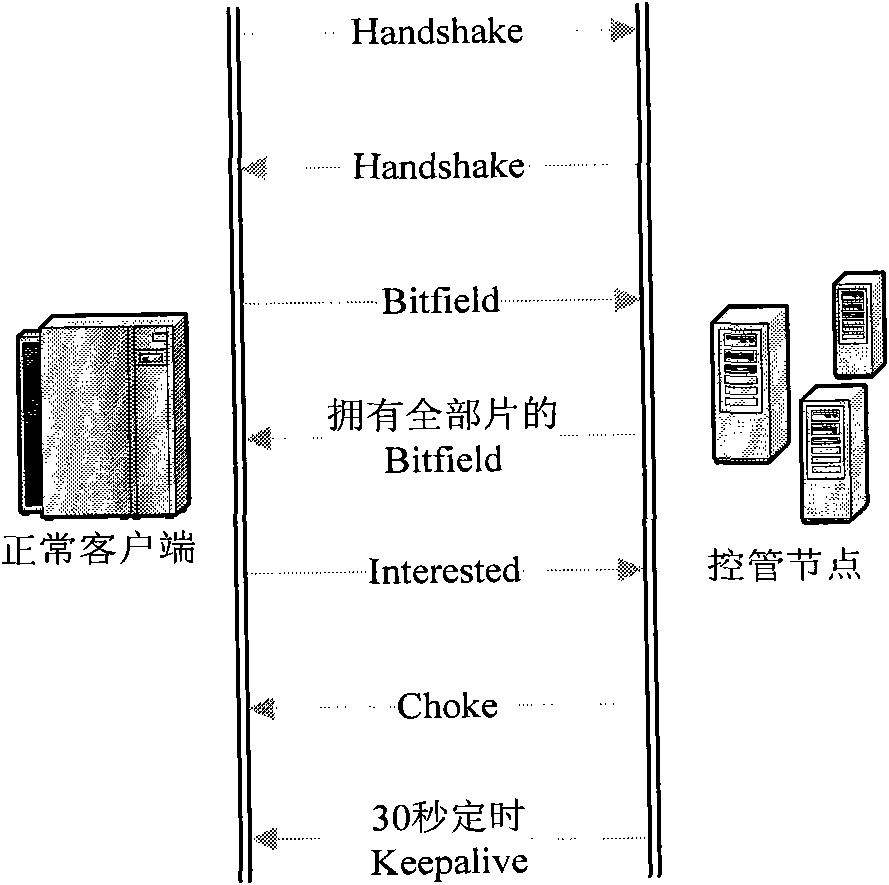
Active propagation control method in bittorrent (BitTorrent) file shared network
InactiveCN102035677ALimit downloadLimit upload capacityData switching networksResource basedClient-side
The invention relates to an active propagation control method based on resource occupancy in a bittorrent (BitTorrent) file shared network. In the method, a control management node is disguised into a legal shared node to carry out interaction with other shared nodes; recognition is carried out on the versions of bittorrent client sides of other shared nodes by the control management node; a control strategy for the client side corresponding to the recognized version is selected; and the control strategy is used for invading and occupying connection or bandwidth resources of other shared nodes. By utilizing the method, the downloading or uploading capability of the shared user is limited in the shared propagation process of the BitTorrent files, so that the downloading of all nodes participating in the whole downloading process of the shared files is extremely slow, even can not be carried out. By adopting the BitTorrent network oriented file shared propagation control technology, the technical effects of delaying the propagation process or the downloading time of the shared files as long as possible and reducing the resources or cost spent by control management as little as possible are achieved from the aspect of control management.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
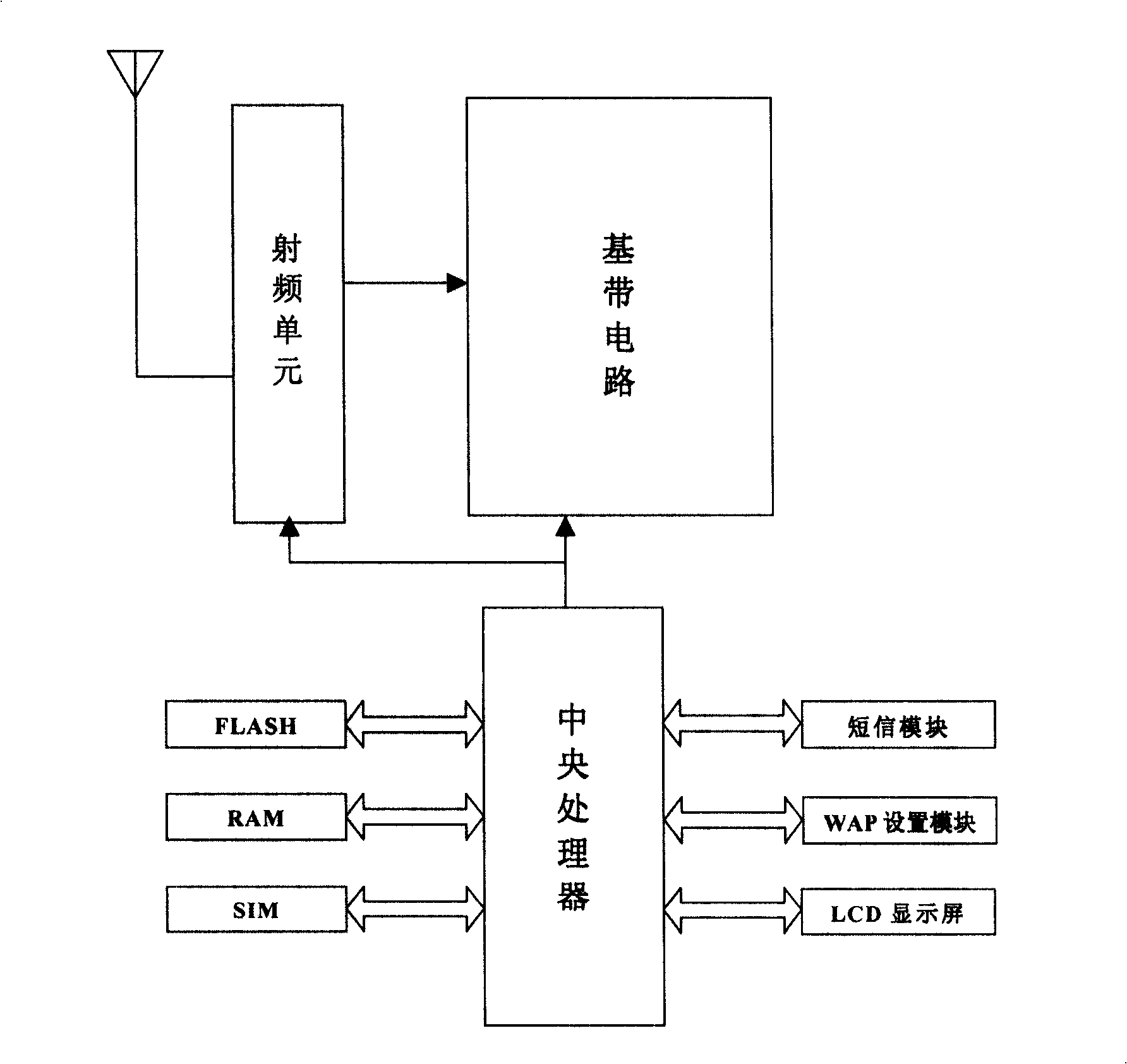
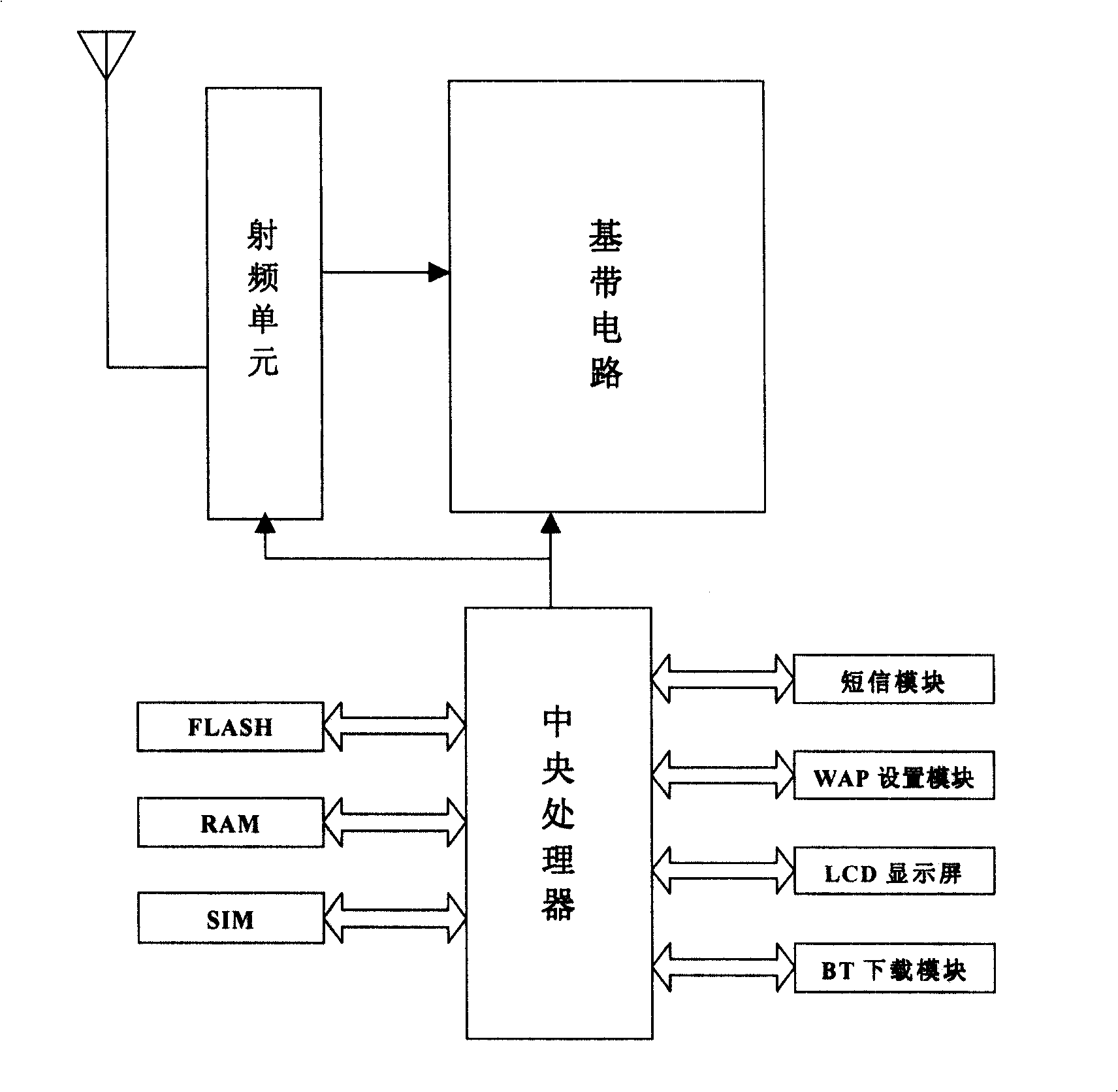
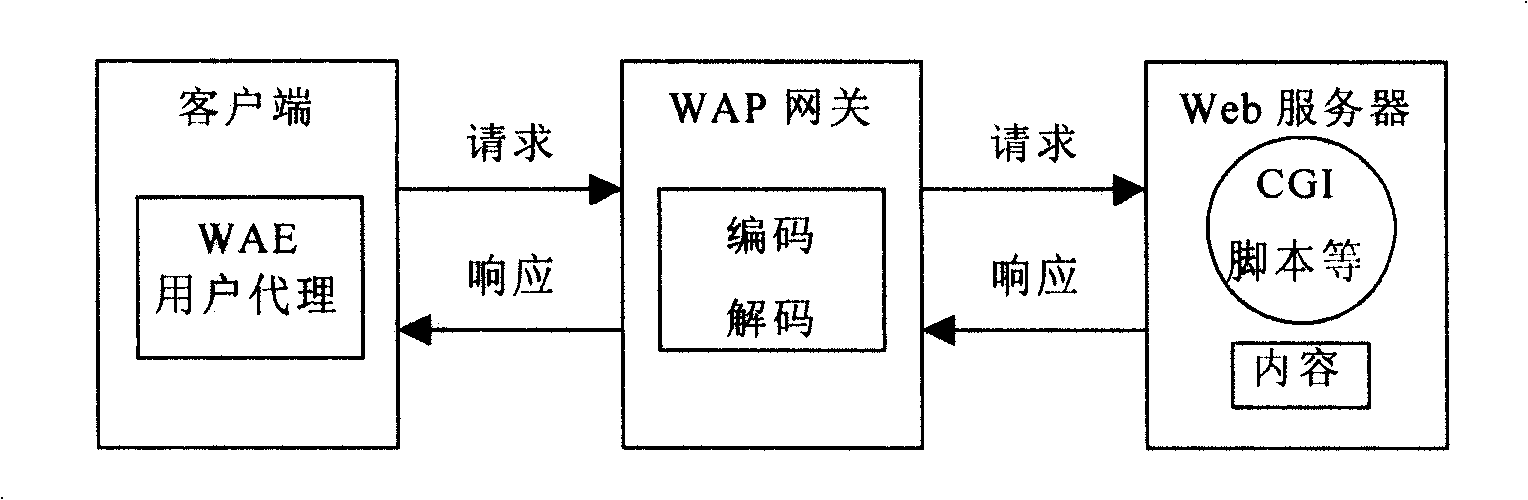
Mobile phone downloading method based on WAP protocol and mobile phone adopting the same
InactiveCN101247582AHigh speedRadio/inductive link selection arrangementsTransmissionComputer hardwareMobile phone
The invention is related to a phone download method based on WAP protocol and mobile phone with the method, including the following steps of installing BitTorrent download software in the mobile phone; making WAP settings in the mobile phone; connecting the mobile phone to the internet by WAP; starting the BitTorrent download software of the mobile phone; selecting object files to download; disconnecting the mobile phone from the internet when the download is complete. The invention achieves a substantial increase in download speed and breakthrough in the limit of downloaded information size.
Owner:LG ELECTRONICS (CHINA) R&D CENT CO LTD
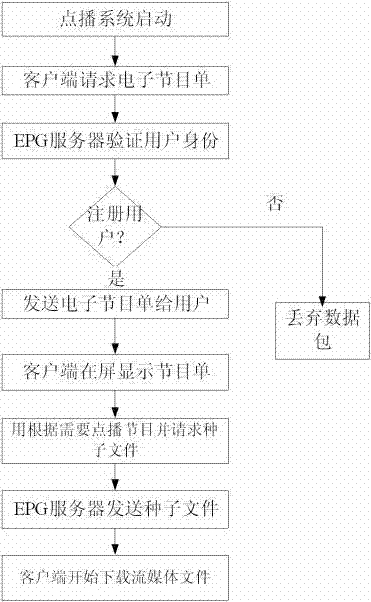
Improved video on demand (VOD) transmission method based on peer-to-peer computing core algorithm
InactiveCN102821316ASolve the problem of excessive load pressure and low efficiencyImprove download speedTransmissionSelective content distributionEngineeringMedia server
Disclosed is an improved VOD transmission method based on a peer-to-peer computing core algorithm. An adopted topological structure comprises a torrent file producing server, an electronic program guide (EPG), an improved tracker, a streaming media server and an improved BitTorrent client. According to the method, a piece selection algorithm and a node selection algorithm in the BitTorrent protocol are improved, a self-adaptive sliding window mechanism is introduced, efficient file distribution capacity of the BitTorrent protocol is fully used, and requirements of the VOD for timeliness can be satisfied simultaneously, not only the problems of single point of failure of the server and bottleneck of server connection are solved, but also the load pressure of the server can be reduced.
Owner:NANJING UNIV OF POSTS & TELECOMM
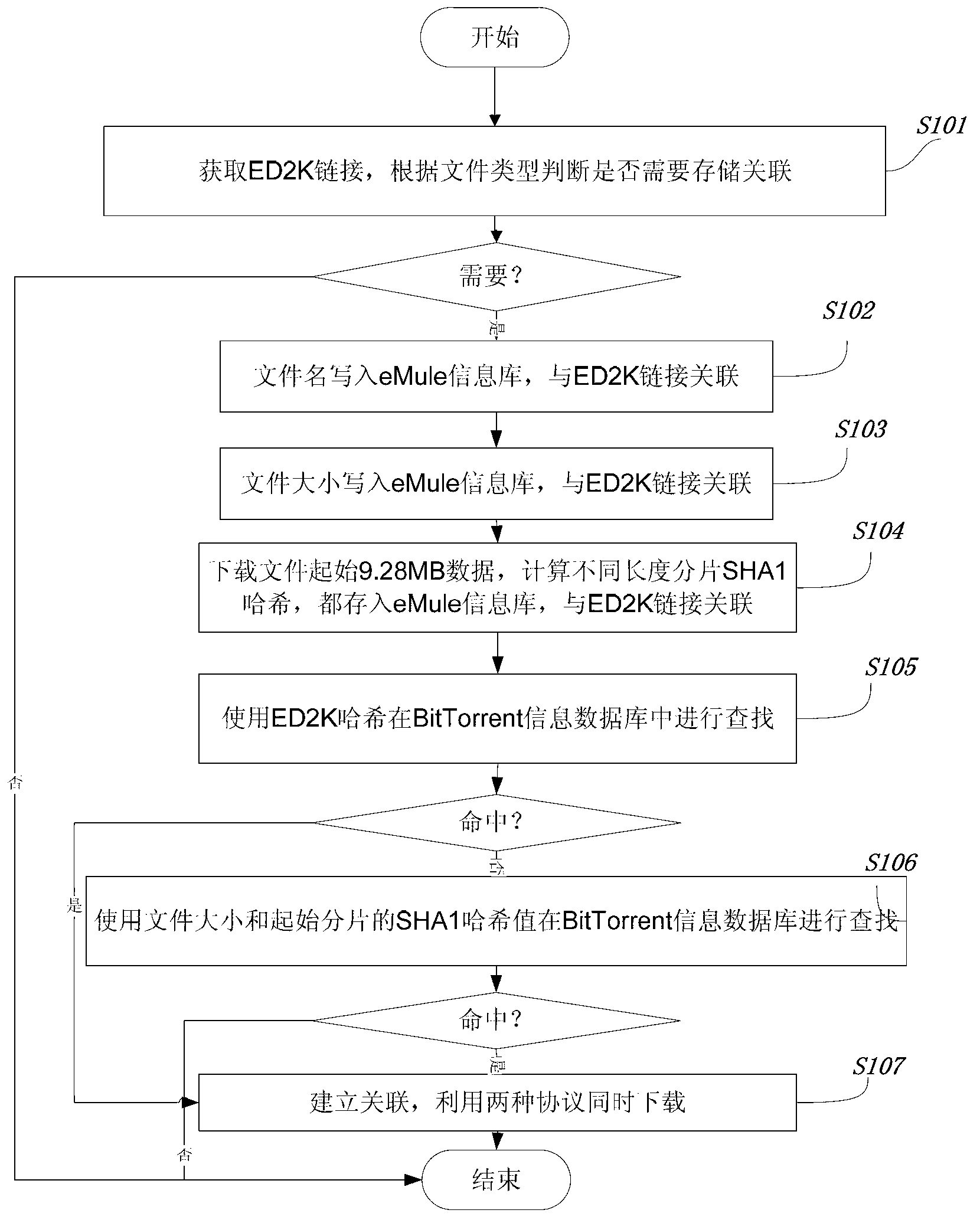
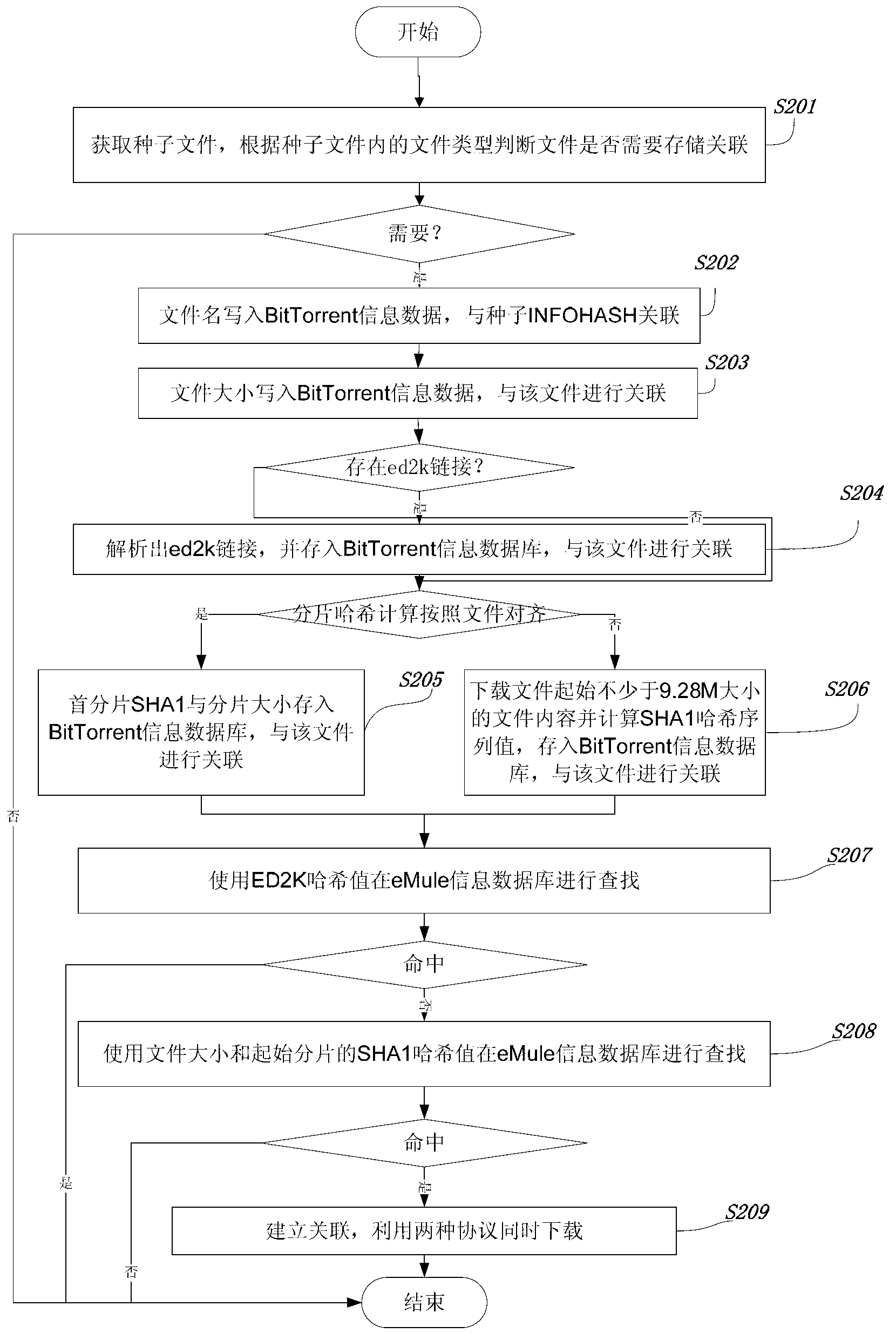
Association method of BitTorrent and eMule download files
The invention provides an association method of BitTorrent and eMule download files. The association method comprises the following steps of: 1) building an eMule information database, wherein the information recorded by the eMule information database comprises collected ED2K link, data size of a resource file corresponding to the ED2K link, and SHA1 value sequences of different sizes of initial file fragments; the sizes of the different sizes of initial file fragments are 2nKB; and the value of n is an integer ranging from 4 to 13; and 2) searching the ED2K link in the eMule network at present according to the file size of the file corresponding to the ED2K link and SHA1 hash values of initial fragments in a BitTorrent information database; and associating a target seed file with current ED2K link. By adopting the association method, repeated downloading of resources files of two P2P spaces of BitTorrent and eMule can be avoided; and the downloading speed can be effectively fastened by utilizing the resources of the P2P spaces of BitTorrent and eMule.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
On-line video-on-demand system based on P2P
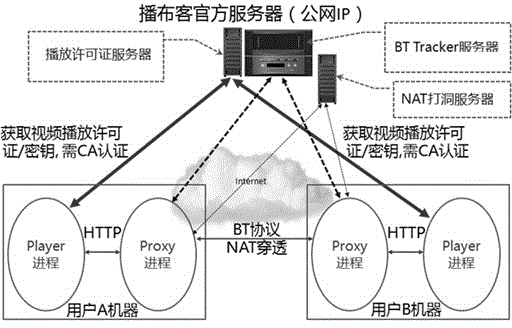
InactiveCN104980815AGuaranteed fluencyMore profit pointsSelective content distributionNAT traversalEngineering
The invention discloses an on-line video-on-demand system based on P2P, comprising a server terminal and client terminals. The server terminal comprises a secret key providing server, a Tracker server of the BT protocol, and an NAT boring server. Each client terminal is composed of a Proxy process and a player process. Each Proxy process establishes connection with the Tracker server of the BT protocol and an Internet through a BitTorrent P2P protocol so as to obtain encrypted video data. Each player process communicates with the Proxy process through a hyper text transport protocol (HTTP) and communicates with the secret key providing server through hyper text transport protocols (HTTPS) to obtain a secret key. The Proxy processes also communicate with the NAT boring server which is in charge of NAT traversal communication with the two client terminals. The on-line video-on-demand system based on P2P performs one-time static encryption of video files at a background, and distributes the video files to users through P2P; and secret keys required for videos on demand are obtained from the secret key providing server.
Owner:NANJING HUIZHI MINGHUA INFORMATION TECH CO LTD
System and method for terminating copyright infringment by bittorrent users
ActiveUS20140289860A1Digital data processing detailsAnalogue secracy/subscription systemsIp addressTorrent file
A system and method that tracks copyright infringing BitTorrent users is presented. The system searches torrent file websites for a torrent file according to specified search criteria and verifies that the torrent file corresponds to a media file containing the copyrighted work. The system obtains tracker server information from the torrent file and obtains the IP addresses of participants currently connected to the torrent file from the tracker server, attempts to establish a connection with a participant based on an IP address selected from the IP addresses and, if successful, receives a data piece with a cryptographic hash from the participant. The cryptographic hash is verified to correctly match with the torrent file. The system then verifies that the participant is sharing the media file, obtains the participant's geographic data and associates the participant to a legal jurisdiction based on the geographic data.
Owner:IP SQUARED TECH HLDG
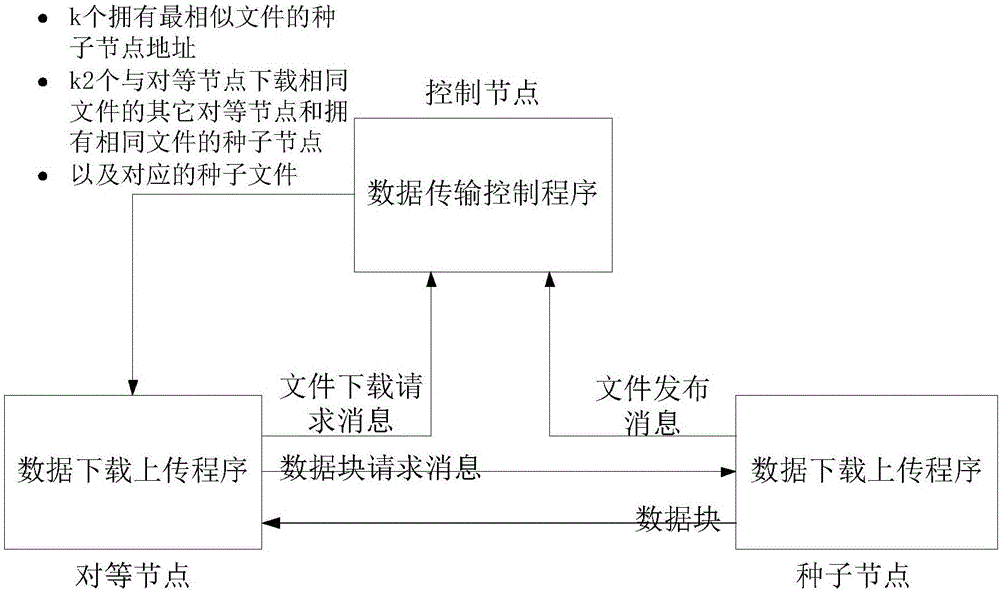
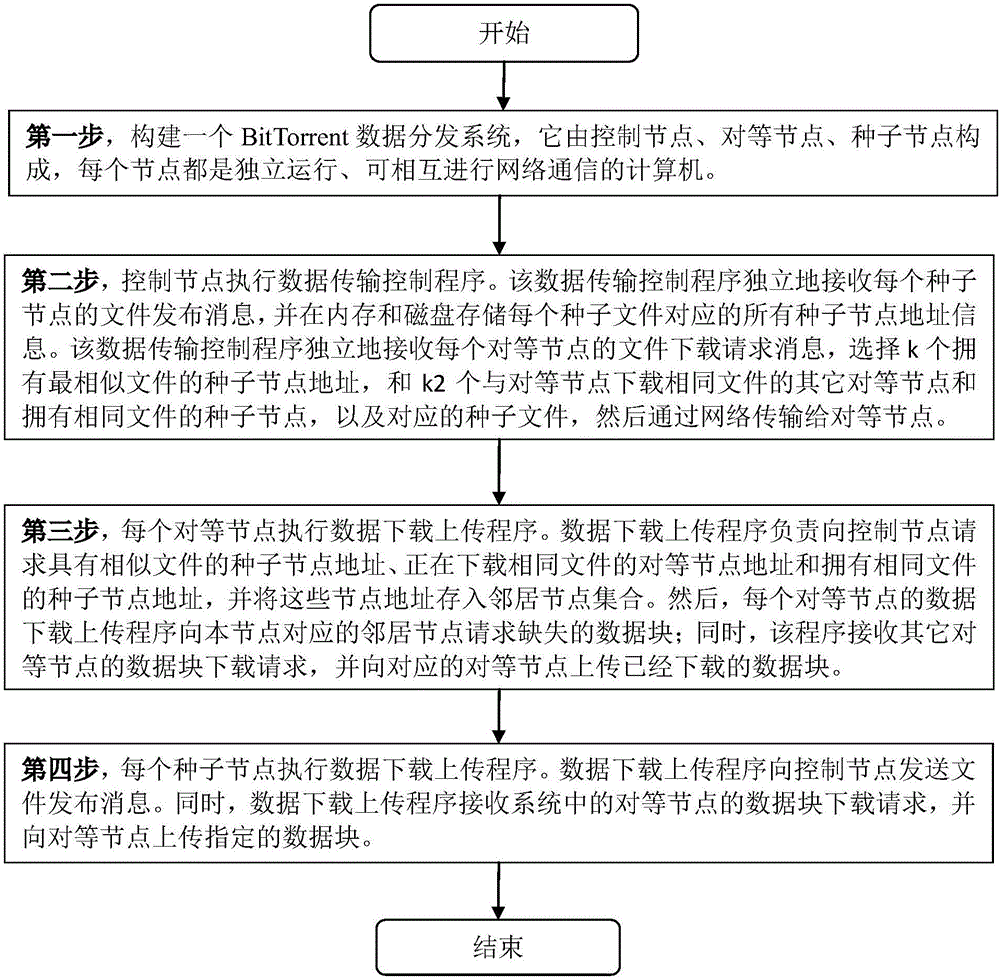
BitTorrent data distribution system and method based on similar file collaboration
ActiveCN106487931ARealize the exchange functionImprove distribution efficiencyDatabase distribution/replicationTransmissionTransmission protocolDistribution method
The invention discloses a BitTorrent data distribution system based on similar file collaboration, the system is formed by a control node, a peer node and a seed node, the control node actively discovers a set of files with highest similarity with a to-be-downloaded file of the peer node, and address information of the seed node having the files is transmitted to the peer node; and the peer node asks the seed node for downloading a data block and acquires the data block from other peer nodes which download the same file and the seed node having the same file. The invention also discloses a BitTorrent data distribution method based on similar file collaboration. According to the invention, the system and the method have the following beneficial effects: a downloaded node inherits a BitTorrent transmission protocol and realizes a function of data block exchange crossing similar files, the downloaded node exchanges data with other nodes which download the same file from the seed node having the similar file, and the data distribution efficiency can be effectively improved.
Owner:NAT UNIV OF DEFENSE TECH
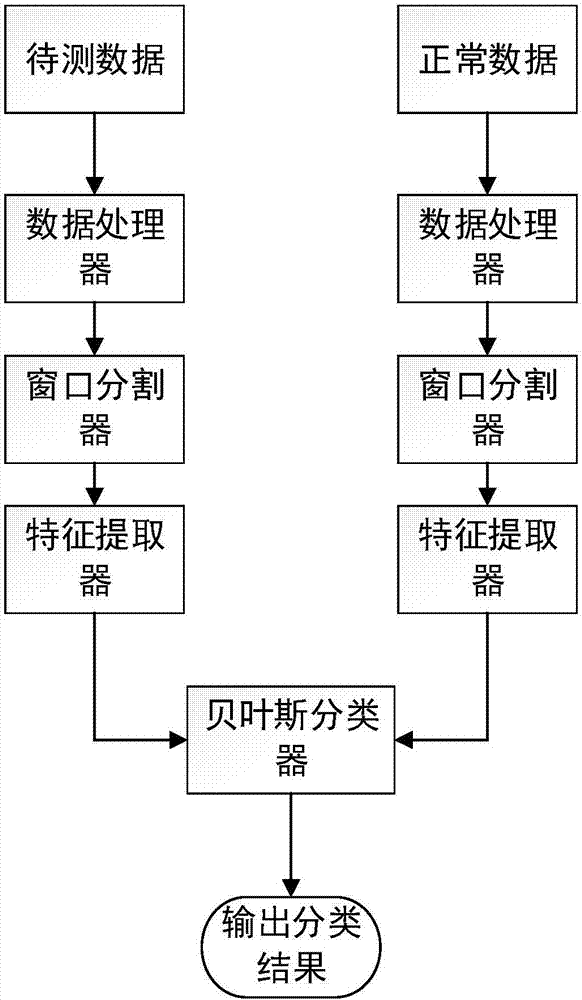
Convert communication detection method based on Have message encoding for BitTorrent file sharing process
ActiveCN107172024AOvercome the problem of high false alarm rateReliable test resultsTransmissionData streamMessage encoding
The invention discloses a convert communication detection method based on a Have message encoding for a BitTorrent file sharing process. The method comprises the following steps of capturing normal data and to-be-measured data; respectively extracting three features, namely information entropy, epsilon similarity and a variance, of the normal data and the to-be-measured data; taking the normal data as training data; taking the to-be-measured data as test data to be input into a Bayes classifier; judging whether the to-be-measured data is similar to the normal data through the Bayes classifier, if yes, judging that the to-be-measured data is normal, otherwise judging that the to-be-measured data is abnormal. Through adoption of multi-feature detection of data streams, a problem of high false alarm rate caused by the single feature can be effectively overcome and a reliable detection result is given.
Owner:JIANGSU UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com