Secret information transmission method based on BitTorrent protocol Have message
A technology of secret information and transmission method, which is applied in the field of secret information transmission based on the BitTorrent protocol Have message, to achieve the effect of improving concealment and robustness and avoiding communication load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further explained below in conjunction with the accompanying drawings.
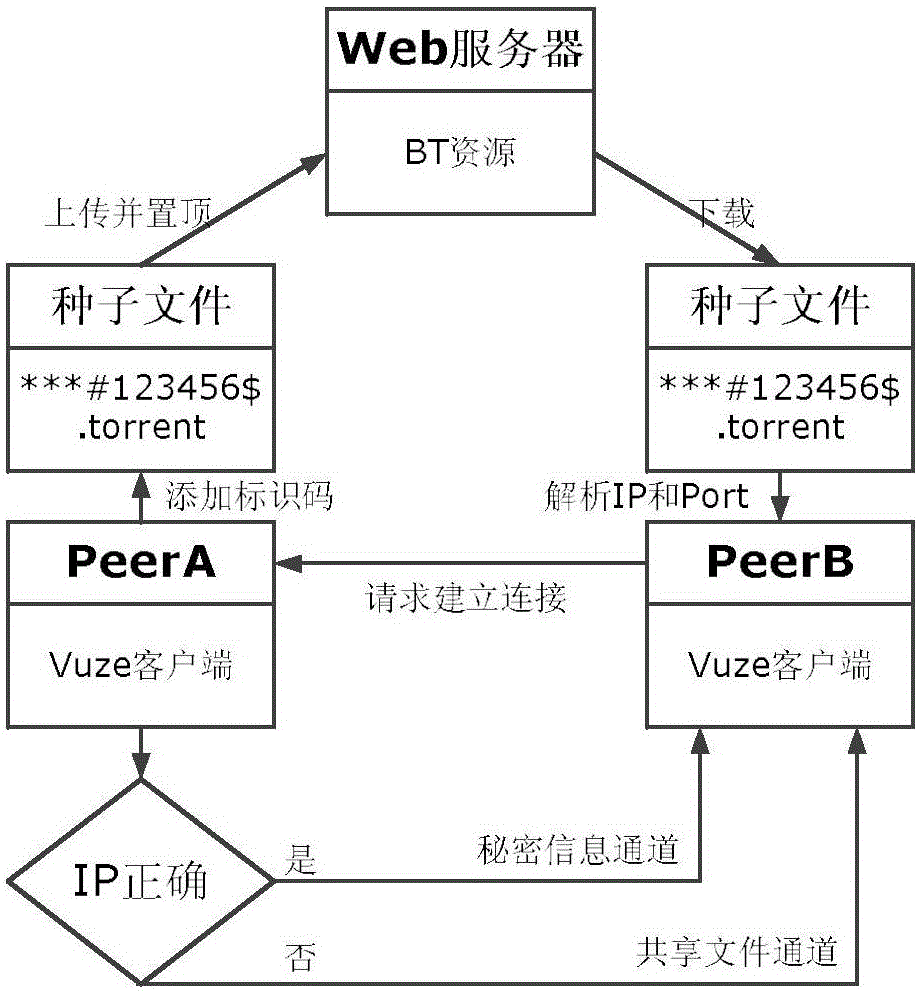
[0034] Taking the client software Vuze4.4 as an example, an information hiding method based on BitTorrent protocol Have message sorting of the present invention is further clarified.
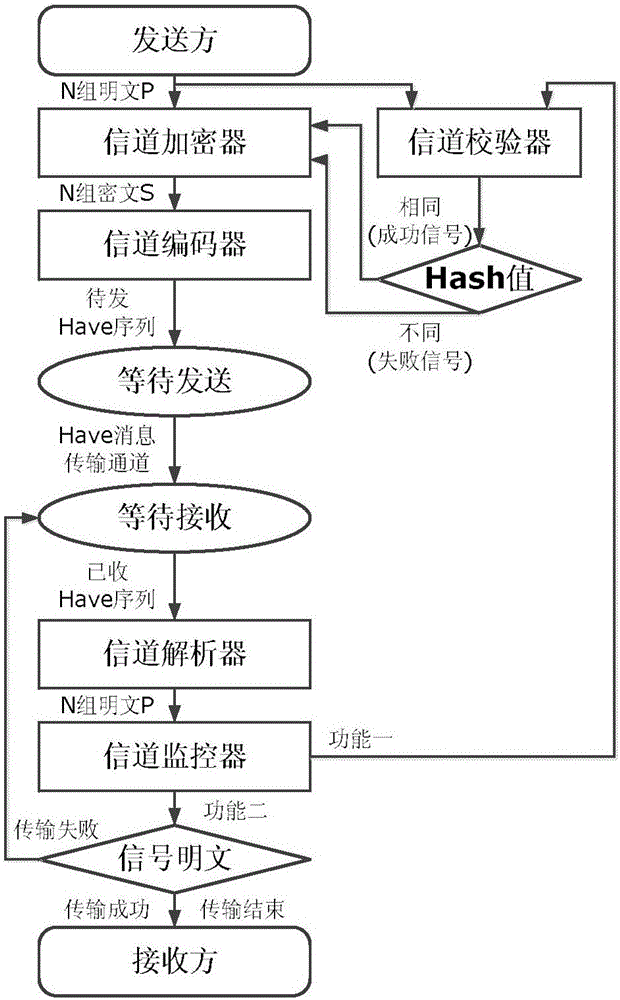
[0035] figure 1 It is an overall flowchart of the information hiding method of the present invention. The hidden channel is constructed based on the transmission channel of the BT protocol Have message. The sender undergoes two processes of encryption and encoding, and adjusts the order of the Have messages in the N groups of Have message sequences according to the N groups of secret information ciphertext S, thereby completing the N groups of The embedding of the secret information ciphertext S, the secret information is transmitted together with the Have message. The receiver obtains N groups of secret information plaintext P through reverse decoding and decryption, and submits it to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com