Method of preventing syn flood and router equipment
A flood attack, router technology, applied in the direction of digital transmission system, data exchange network, electrical components, etc., can solve the problems of exhaustion of server resources, affecting servers, consuming server resources, etc., to improve utilization, save resources, improve safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
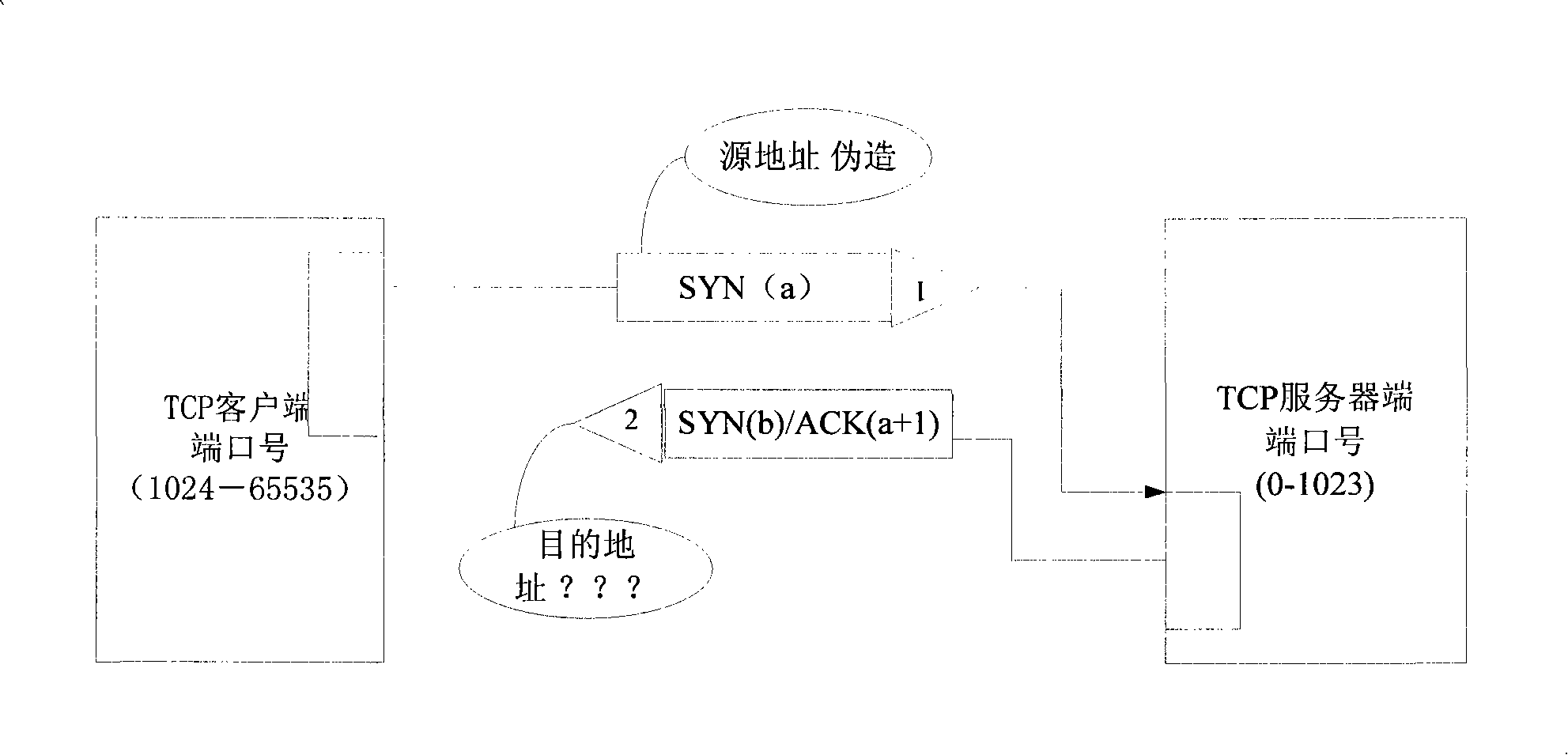
[0040] In order to solve the disadvantages of the traditional technical solution, the present invention further elaborates a method for preventing syn flood attack when establishing a TCP connection through the following specific examples. Limitations of Invention.
[0041] According to the present invention, the router equipment uses the router simulation server to respond to the link request of the client computer, and the main steps are as follows:
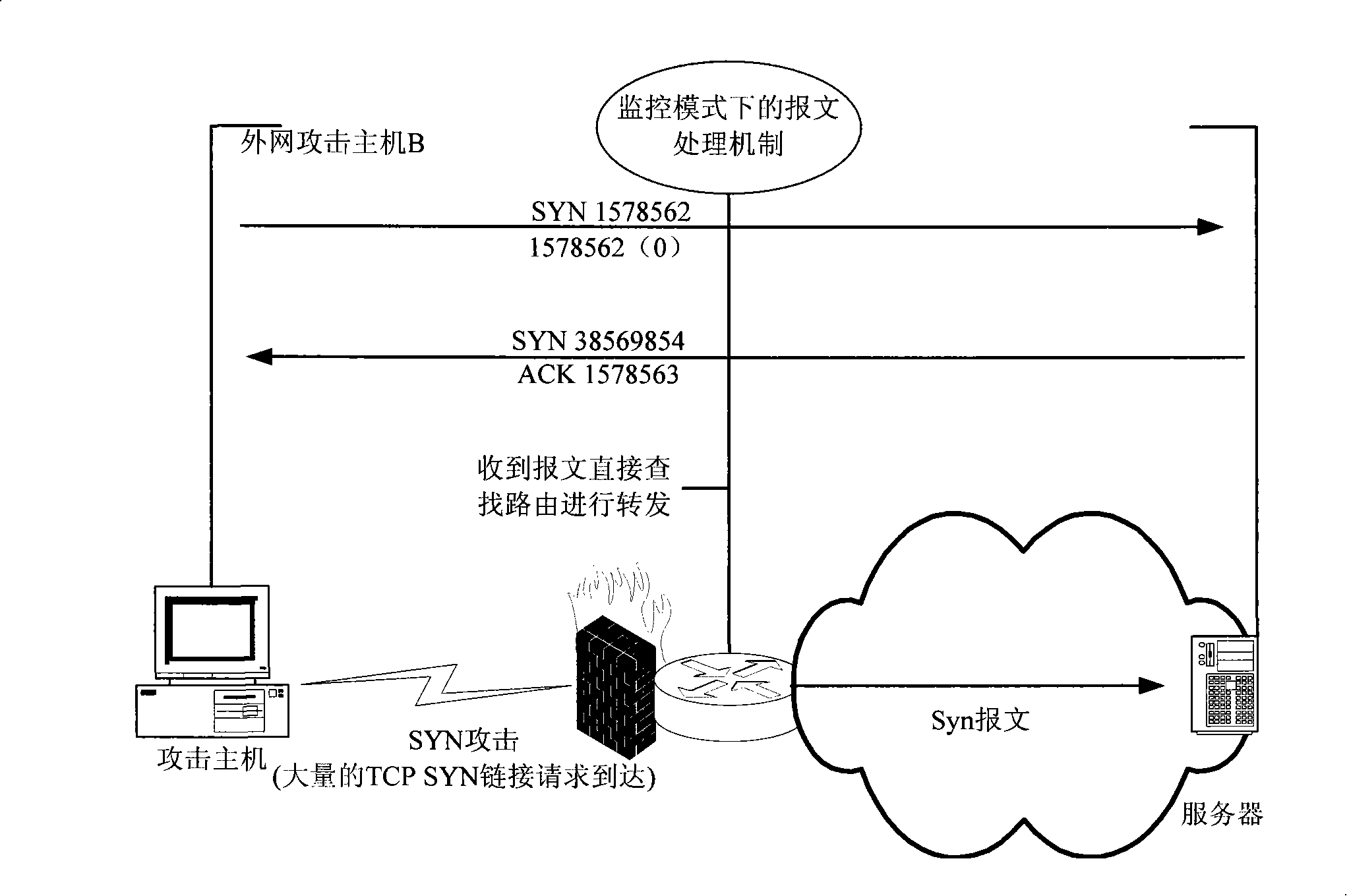
[0042] first step, such as figure 2 As shown, it is a schematic diagram of work under the monitoring mode in the embodiment of the present invention; under normal circumstances, it is in the monitoring mode, and the syn message sent by the client computer is received to directly search for the route and send it;
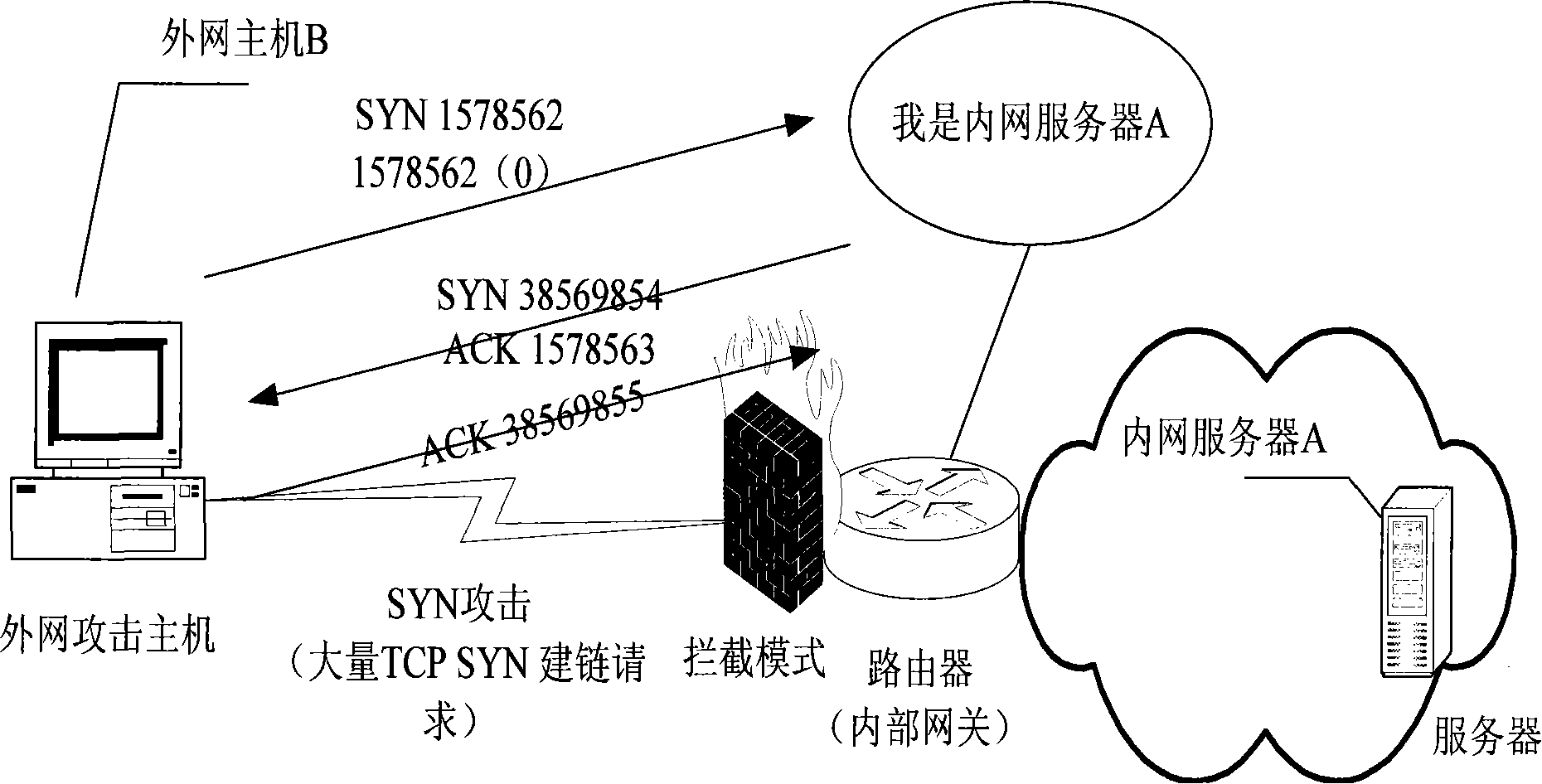
[0043] The second step is to enter the interception mode when the number of semi-links exceeds the proxy waterline;
[0044] In the monitoring mode, in order to achieve the maximum forwarding efficiency, the router...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com