Attack defense method
An attacker and encryption algorithm technology, applied in the field of network security, can solve the problem that the server cannot effectively identify and defend against SYNFlood attacks, and achieve the effect of avoiding SYNFlood attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
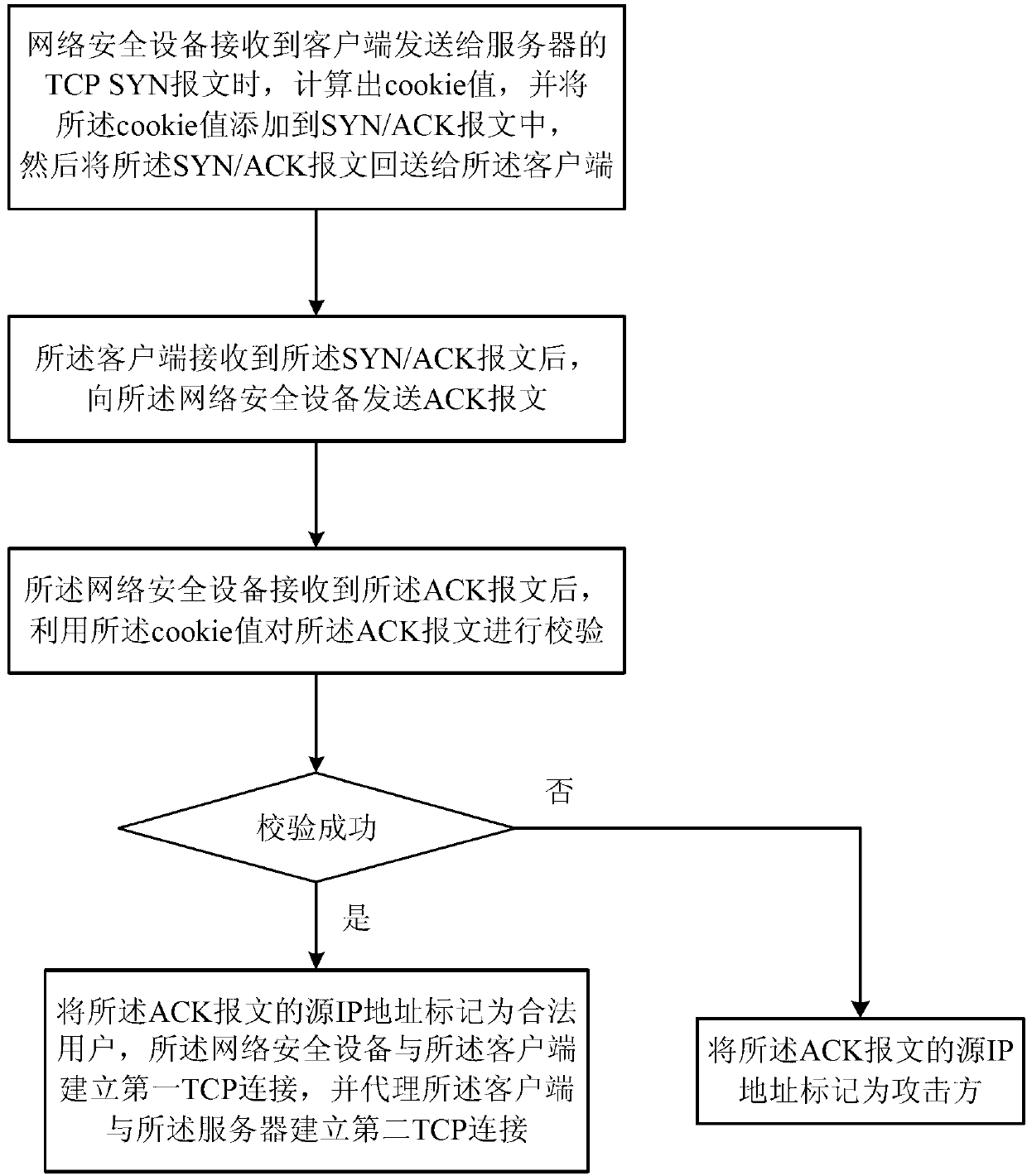
[0037] figure 1 Represent a specific implementation of the defense method of the attack proposed by the present invention, the method includes the following steps:
[0038] When the network security device receives the TCP SYN message sent by the client to the server, it calculates the cookie value, adds the cookie value to the SYN / ACK message, and then sends the SYN / ACK message back to the client;
[0039] After receiving the SYN / ACK message, the client sends an ACK message to the network security device;
[0040] After the network security device receives the ACK message, it uses the cookie value to verify the ACK message, and if the verification is successful, the source IP address of the ACK message is marked as a legitimate user, The network security device establishes a first TCP connection with the client, and establishes a second TCP connection with the server on behalf of the client, or marks the source IP address of the ACK message as an attacker.
[0041] In the ...
Embodiment 1
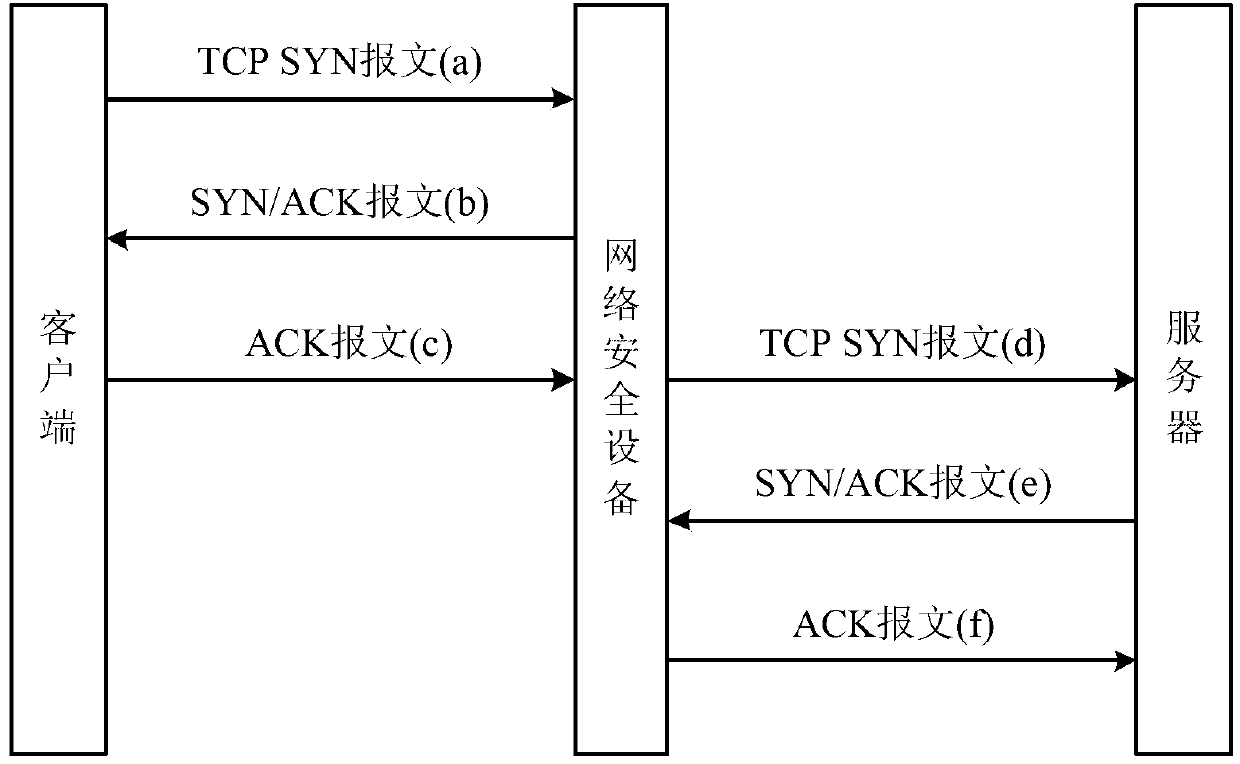
[0052] figure 2 It is the system schematic diagram of embodiment 1. like figure 2 As shown, the process of establishing a TCP connection between the client and the server is:
[0053] In the first step, the client first sends a TCP SYN message (that is, message a);
[0054] In the second step, after the network security device receives the message a, it starts the proxy function, and according to the local time in the TCP header of the message a, uses the md5 encryption algorithm to calculate the cookie value, and then fills the cookie value as SYN / The serial number in the TCP header of the ACK message (that is, message b), and then send the message b back to the client;
[0055] In the third step, after receiving message b, the client calculates a new serial number based on the received cookie value, then adds the new serial number to the TCP header of the ACK message (that is, message c), and puts Packet c is sent to the network security device;
[0056] Step 4: Afte...
Embodiment 2
[0060] The first three steps of embodiment 2 are identical with embodiment 1, difference is:
[0061] Step 4: After receiving message c, the network security device checks whether the sequence number in the TCP header of message c and the cookie value generated by itself can be verified according to a certain algorithm. When the verification fails, the network security device Mark the source IP address of message c as an attacker and add it to the blacklist;
[0062] In the fifth step, the network security device establishes a first TCP connection with the client, and establishes a second TCP connection with the server on behalf of the client, and adopts the traditional three-way handshake mechanism when establishing the second TCP connection;
[0063] In the sixth step, when the network security device receives the request message sent by the client to the server, it first judges whether the IP address of the client is in the blacklist, and if it is found, it directly interce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com